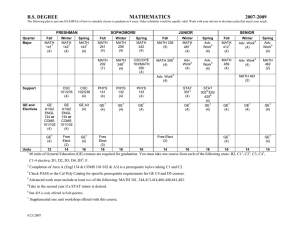
Practical Broadcast Authentication in Sensor Networks Presenter: Tong Zhou 6/24/2016
advertisement

Computer Science
Practical Broadcast Authentication in
Sensor Networks
Presenter: Tong Zhou
6/24/2016
CSC 774 Adv. Net. Security
1
Outline
•
•
•
•
•
Background
Basic Approach
Various Extensions
Implementation Results
Conclusion & Future Work
Computer Science
CSC 774 Adv. Net. Security
2
Background
• Wireless Sensor Network
– Large number of resource constrained sensor nodes
– A few powerful control nodes (Base Station)
• Broadcast Authentication in Sensor Network
– TESLA
– Multilevel TESLA
Computer Science
CSC 774 Adv. Net. Security
3
Review of Multilevel TESLA
Ki-1
Ki
F01
Ki-2,m Ki-1,1
F01
F1
Ki-1,2
F1
...
F1
Ki-1,m Ki,1
F01
F1
...
...
F1
F1
Ki,m Ki+1,1
...
F1
F1
Ki-1,0
Ki,2
F1
F1
Ki+1,0
Ki,0
Time
CDMi=i|Ki+1,0|H(Ki+2 ,0) |MACK’i(i|Ki+1 ,0|H(Ki+2 ,0 ))|K i-1
Computer Science
CSC 774 Adv. Net. Security
4
Review of Multilevel TESLA (cont.)
• Benefits:
– Trade-off between key chain length and broadcast
time
– Resistant to packet loss
• Problems left:
– Remove the long delay after CDMs are lost
– Allow multiple senders
– Revoke broadcast senders
Computer Science
CSC 774 Adv. Net. Security
5
Practical Broadcast Authentication in
WSN: Basic Scheme
• Use Merkle tree to distribute the key chain
commitments – referred to as parameter distribution
tree
– The tree root is pre-distributed
– Each commitment is a leaf of the tree
K14
Pre-distributed root
K12
K34
K1
K2
K3
K4
s1
s2
s3
s4
Computer Science
Key chain commitments
CSC 774 Adv. Net. Security
6
Practical Broadcast Authentication in
WSN: Basic Scheme (Cont.)
• If the 2nd TESLA instance will be used:
– Sender broadcasts the parameter certificate
ParaCert2 = { s2, K1, K34}
– Receivers immediately authenticate the commitment s2 by
verifying
K14
K14 = H( H( H(s2) K1 ) | K34)
K12
Computer Science
K34
K1
K2
K3
K4
s1
s2
s3
s4
CSC 774 Adv. Net. Security
7
Practical Broadcast Authentication in
WSN: Basic Scheme (Cont.)
• The basic scheme has achieved:
– Security:
• Attacker cannot send forged packet unless compromising the sender
• The parameter certificates are immune to DoS attack
– Overhead:
• Storage: each receiver node needs to store the root of the parameter
distribution tree, and the parameters of the senders that are
communicating
• Computation: each receiver node needs 1 log 2 m hash functions to
validate the key chain commitment, where m is the number of
TESLA instances
– Allows multiple senders:
• Senders can be added dynamically by generating enough instances
for late-joined senders
Computer Science
CSC 774 Adv. Net. Security
8
Scheme for Long-lived Senders
• Basic idea:
– two-level parameter distribution tree
• Pre-Distribution
– Fix the interval length that each TESLA key chain uses, denote such
an interval as (TESLA) instance interval. Assume each key chain has
length L.
– Assume sender j needs nj instance intervals through out its life: use the
nj key chain parameters {s j ,i }1in j as leaves to construct a lower level
tree, denoted as Treej. When generating key chains for each sender:
ki+1, L = F’(ki, 0), where F’ is a pseudo random function.
– With the roots of Treejs as leaves, an upper level parameter distribution
tree is generated, denoted as TreeR
– TreeR’s root is pre-distributed to receivers, while the parameter
certificate of TreeR of sender j, denoted as ParaCertj and all the key
chains generated for sender j is pre-distributed to sender j.
Computer Science
CSC 774 Adv. Net. Security
9
Scheme for Long-lived Senders: Example
K14
K12
Pre-distribution:
K34
K1
K2
K3
s1
s2
s3
TreeR
K4
Sender3:
s4
ParaCert3={s3, K4,
K12}, and Sender3’s
key chains
R3
K’12
K’34
K’1
K’2
K’3
K’4
s’1
s’2
s’3
s’4
Computer Science
Receivers: K14
Treej
CSC 774 Adv. Net. Security
10
Scheme for Long-lived Senders: Example
R3
K’12
K’34
K’1
K’2
K’3
K’4
s’1
s’2
s’3
s’4
k1,0
k2,0
k3,0
k4,0
k1,1
k2,1
k3,1
k4,1
k1,L
k2,L
k3,L
k4,L
F’
F’
Computer Science
Tree3
F’
CSC 774 Adv. Net. Security
11
Scheme for Long-lived Senders (Cont.)
• The above scheme has achieved:
– Security:
• Same as in the basic scheme
– Overhead:
• Storage: receivers’ are same as in the basic scheme, sender j needs
to store ParaCertj besides all the key chains.
• Computation: 1 log 2 n j for validation of each key chain
commitment, and 1 log 2 m for validation of each sender, where m
is the number of senders.
– Benefit over basic scheme:
• Fixed key chain length
• Two ways to validate the key chain commitments
Computer Science
CSC 774 Adv. Net. Security
12
Distributing Parameter Certifications
• Due to the low bandwidth and small packet size, ParaCertj
must be delivered in several packets.
– Each packet must be authenticated independently and immediately
– Assume that each ParaCert contains L hash values, each packet can
hold b hash values. Adopt the idea of distillation codes.
Computer Science
CSC 774 Adv. Net. Security
13
Distributing Parameter Certifications:
Example
K18
K14
K58
K12
K34
K1
K2
s1
s2
K3
s3
K56
K4
s4
K78
K5
K6
K7
s5
s6
s7
K8
s8
ParaCert3 = {K58, K12, K4, s3}, assume that each
packet can hold 3 hash values,
P1 = {K58, K12, K34}, verify: K18 = H(H(K12| K34)|K58)
P2 = {K4, s3}, verify: K34 = H(K4|H(s3))
Computer Science
CSC 774 Adv. Net. Security
14
Revoking TESLA Instances
• Revocation tree
– Similar to the parameter distribution tree, the central server
generates a revocation message for each TESLA instance,
and use all the messages to construct a Merkle tree, whose
root is pre-distributed.
– Advantages:
• Guarantees a non-compromised sender not be revoked.
– Disadvantages:
• Cannot guarantee each receiver receives the revocation message
due to the unreliable communication
• Revoked senders must be remembered by receivers, which
introduces large storage overhead.
Computer Science
CSC 774 Adv. Net. Security
15
Revoking TESLA Instances (Cont.)
• Proactive Refreshment of Authentication Keys
– Central server sends TESLA key chains to the senders
when senders are broadcasting, instead of pre-distributing
all the key chains. Central server can revoke a sender by
stop sending TESLA key chains to it.
– Advantages:
• Guarantees a compromised sender be revoked
• Receivers do not need storage overhead
– Disadvantages:
• A non-compromised sender may be revoked if it does not receive
the key chains due to some communication problem.
Computer Science
CSC 774 Adv. Net. Security
16
Experimental Results: Authentication Rate
Authentication rate under 0.2 loss rate and 200 forged
parameter distribution packet per minute.
Computer Science
CSC 774 Adv. Net. Security
17
Experimental Results: Channel Loss Rate
Channel loss rate: 0.2; # forged commitment distribution: 200
per minute; distribution rate: 95%.
Computer Science
CSC 774 Adv. Net. Security
18
Experimental Results: Average Failure
Recovery Delay
Average failure recovery delay. Assume 20 parameter
distribution packet per minute.
Computer Science
CSC 774 Adv. Net. Security
19
Conclusion & Future Work
• Developed practical broadcast authentication
techniques
– Distribution of TESLA key chain parameters
– Revocation of compromised senders
• Future Work
– Other schemes based on the basic scheme
– Remove the constraint of loosely synchronization
of senders and receivers
Computer Science
CSC 774 Adv. Net. Security
20
Questions?
Computer Science
CSC 774 Adv. Net. Security
21