Closed-form Solution of the Bianchi Model for Member, IEEE
advertisement
Closed-form Solution of the Bianchi Model for
IEEE 802.11e EDCA and 802.11 DCF
Paal E. Engelstad, Member, IEEE and Olav N. Østerbø
Abstract— Based on some empirical observations, we present a
fairly accurate assumption about the throughput performance
under non-saturation conditions and when the system is near
saturation. This allows us to find a closed form solution for the
transmission probabilities and collision probabilities. These can
be inserted into performance expressions derived from any
available analytical model for 802.11e EDCA or 802.11 DCF.
Here, we use the delay expression of one selected model for
802.11e EDCA, and observe that the closed-form solution of the
delay matches well with the numerical calculations given by the
model.
Access Point
Station 1
(4 queues)
Station 3
(4 queues)
Station 2
(4 queues)
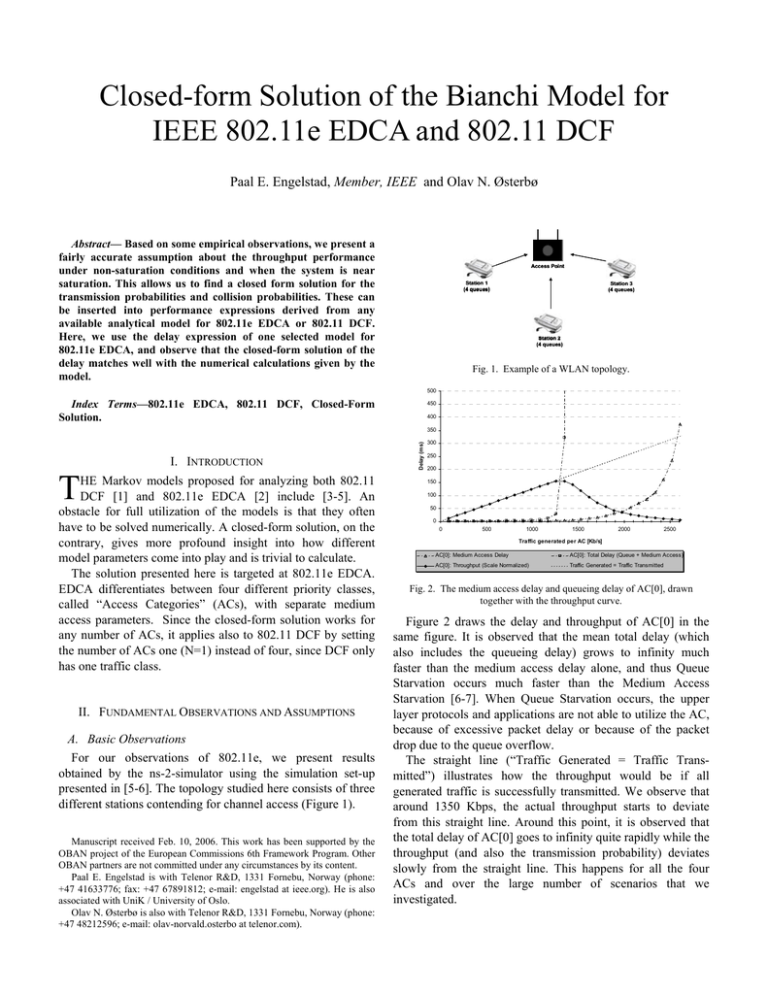
Fig. 1. Example of a WLAN topology.
500
Index Terms—802.11e EDCA, 802.11 DCF, Closed-Form
Solution.
450
400
T
I. INTRODUCTION
HE Markov models proposed for analyzing both 802.11
DCF [1] and 802.11e EDCA [2] include [3-5]. An
obstacle for full utilization of the models is that they often
have to be solved numerically. A closed-form solution, on the
contrary, gives more profound insight into how different
model parameters come into play and is trivial to calculate.
The solution presented here is targeted at 802.11e EDCA.
EDCA differentiates between four different priority classes,
called “Access Categories” (ACs), with separate medium
access parameters. Since the closed-form solution works for
any number of ACs, it applies also to 802.11 DCF by setting
the number of ACs one (N=1) instead of four, since DCF only
has one traffic class.
II. FUNDAMENTAL OBSERVATIONS AND ASSUMPTIONS
A. Basic Observations
For our observations of 802.11e, we present results
obtained by the ns-2-simulator using the simulation set-up
presented in [5-6]. The topology studied here consists of three
different stations contending for channel access (Figure 1).
Manuscript received Feb. 10, 2006. This work has been supported by the
OBAN project of the European Commissions 6th Framework Program. Other
OBAN partners are not committed under any circumstances by its content.
Paal E. Engelstad is with Telenor R&D, 1331 Fornebu, Norway (phone:
+47 41633776; fax: +47 67891812; e-mail: engelstad at ieee.org). He is also
associated with UniK / University of Oslo.
Olav N. Østerbø is also with Telenor R&D, 1331 Fornebu, Norway (phone:
+47 48212596; e-mail: olav-norvald.osterbo at telenor.com).
Delay (ms)
350
300
250
200
150
100
50
0
0
500
1000
1500
2000
2500
Traffic generated per AC [Kb/s]
AC[0]: Medium Access Delay
AC[0]: Total Delay (Queue + Medium Access)
AC[0]: Throughput (Scale Normalized)
Traffic Generated = Traffic Transmitted
Fig. 2. The medium access delay and queueing delay of AC[0], drawn
together with the throughput curve.
Figure 2 draws the delay and throughput of AC[0] in the
same figure. It is observed that the mean total delay (which
also includes the queueing delay) grows to infinity much
faster than the medium access delay alone, and thus Queue
Starvation occurs much faster than the Medium Access
Starvation [6-7]. When Queue Starvation occurs, the upper
layer protocols and applications are not able to utilize the AC,
because of excessive packet delay or because of the packet
drop due to the queue overflow.
The straight line (“Traffic Generated = Traffic Transmitted”) illustrates how the throughput would be if all
generated traffic is successfully transmitted. We observe that
around 1350 Kbps, the actual throughput starts to deviate
from this straight line. Around this point, it is observed that
the total delay of AC[0] goes to infinity quite rapidly while the
throughput (and also the transmission probability) deviates
slowly from the straight line. This happens for all the four
ACs and over the large number of scenarios that we
investigated.
http://folk.uio.no/paalee/
B. An Assumption about the Throughput
The main idea of this paper is to assume – as an
approximation - that the throughput continues to evolve along
the straight line when the Queue Starvation starts to occur.
Later in this paper, this is referred to as the Throughput
Assumption.
This simple idea makes it possible to arrive with a closedform solution to the medium access probabilities of the
Bianchi model, without making many assumptions about the
details of the actual model. Hence, we anticipate that the
presented results might be applicable to a large number of
variants of the Bianchi model.
III. THE MEDIUM ACCESS PROBABILITIES AND THE
THROUGHPUT
pi , s
,
ˆ
(1 − pb )Te + psTˆs + ( pb − ps )Tˆc
(1)
where T̂e , Tˆs and T̂c denote the real-time duration of an
empty slot; of a slot containing a successfully transmitted
packet; and of a slot containing two or more colliding packets,
respectively, divided by the average real-time required
transmitting the MSDU-part of a data packet.
Furthermore, p b in Eq. (1) is the probability that the
channel is busy:
N −1
pb = 1 − ∏ (1 − τ i )
ni
,
(2)
i =0
where τ i denotes the transmission probability, ni denotes the
number of transmission queues per AC[i], and N denotes the
total number of ACs.
Moreover, pi ,s in Eq. (1) is the probability that a packet
from any of the ni backoff instances of class i is transmitted
successfully (at probability τ i (1 − pi ) ) in a time slot:
p i , s = n iτ i (1 − p i ) ,
(3)
where p i denotes the probability that such a transmission
attempt is subject to collision on the channel. [Expressions for
p i are given later in Eq. (9) and in Eq. (19).]
Finally, p s in Eq. (1) denotes the probability that a packet
from any class i is transmitted successfully in a time slot:
N −1
p s = ∑ pi,s .
(4)
i =0
B. Expression of the Throughput Assumption
We now see that the throughput assumption presented
earlier can formally be written:
http://www.unik.no/personer/paalee
(AC[0] not starved).
(5)
However, this expression is only valid when AC[0] is not
subject to Queue Starvation. Otherwise the queue of AC[0]
will constantly grow or overflow and the stable-state
assumption behind the expression breaks down. If AC[0] is
starved, we may simply set τ 0 = 0 , and let Eq. (5) be valid
only when i = 1,..., N − 2 . Generally, if M traffic classes are
starved, the throughput assumption can then be written:
ni +1τ i +1 (1 − pi +1 ) S i
; i = M ( S ),..., N − 2
n (1 − p ) S
i
i
i +1
τi =
θi
;
i < M (S )
where
A. Common Features of the Analytical Models
Most analytical Markov models, including those in [3-5],
calculate the nominal throughput, Si , of AC i, as:
Si =
niτ i (1 − pi ) ni +1τ i +1 (1 − pi +1 ) , i = 0,..., N − 2
=
Si
S i +1
θi = 0
;
i < M (S ) .
(6)
(7)
Eq. (6) alone opens for a possible non-zero θ i . This
generalization will be discussed in Section VI. Until then, we
consider that Eq. (7) is always valid. Eq. (6) states that M is a
function of the traffic, S = {S 0 , S1 , S 2 , S 3 } , on the channel.
We will not treat this more rigorously here. Note also that
throughout this paper, we use the convention that AC[0] is of
the lowest priority and AC[N-1] is of the highest. As a result,
normally AC[0] is the first AC to face starvation as the traffic
load on the channel increases.
In some situations, an AC (for example AC[0] or AC[1]
with the recommended parameter settings of 802.11e) will
experience rapid Medium Access Starvation when the channel
load, S = {S 0 , S1 , S 2 , S 3 } , grows sufficiently large. In such
situations, setting τ i = 0 for this AC[i] (i<M(s) ) is not
problematic.
In other situations, an AC (for example, AC[2] or AC[3]
with the recommended parameter settings of 802.11e) will
face Queue Starvation with massive queue overflow even
though the medium access delay (i.e. service time) is finite.
How should τ i be modeled and estimated realistically under
such circumstances? The higher-layer protocols will not be
able to utilize the AC, so it is not realistic that much long-term
traffic will be generated for this AC. With these assumptions,
setting τ i = 0 as described above should also be
straightforward.
Now, we will first consider the τ i = 0 case expressed by
Eq. (6), while the non-zero τ i case will be addressed in
Section VI.
IV. CLOSED-FORM SOLUTION WITH VIRTUAL COLLISION
HANDLING
A. Set of Equations
We consider a scenario with w different wireless stations,
each with four different transmission queues actively
transmitting from each station. For simplicity, though without
loss of generality, we consider that all ACs transmit at the
same traffic rate. In summary:
N =4
[Example 1].
w = n0 = n1 = n2 = n3 = n
(8)
2
S 0 = S1 = S 2 = S3 = S
τM =
Since there will be virtual collisions (VCs) occurring
between the four queues at each station, we have [8]:
1 − pb
1 − p0
; 1 − p1 =
;
1−τ 0
1 −τ1
1 − p1
1 − p2
1 − p2 =
; 1 − p3 =
.
1 −τ1
1−τ 2
[with VC].
1 − p0 =
(9)
Combining this with our throughput assumption in Eq. (6)
(here assuming that no ACs are starved, i.e. M=0) gives:
τ3
τ1
τ2
[M=0]. (10)
τ0 =
(1 − τ 1 )
; τ1 =
(1 − τ 2 )
; τ2 =
(1 − τ 3 )
(
)
where p b and p s is determined by using Eq. (2) and Eq. (4).
The set of equations above leads to the closed-form
solution. We will provide some roots in closed-form in the
following subsections.
B. Linear Solution (with n=1 and Totally 4 Queues)
The n=1 case is particularly important in the downlink
scenario where the access point dominates the channel and
where the collisions mainly occurs in the virtual collision
handles of the access point. Further insight into this scenario
is provided in [8].
This linear case can be solved in terms of an explicit value
for the transmission probability, τ M , of the lowest priority AC
that is not starved, AC[M]. We find that:
S M Tˆe
1 + S M Tˆe − ( N − M ) S M Tˆs
(12)
,
where M is the number of ACs that are subject to starvation at
a given channel load, S = {S 0 , S1 , S 2 , S 3 } .
For example, for the lowest levels of the channel
throughput, no AC is starved, and we find that:
S 0Tˆe
τ0 =
.
1 + S 0Tˆe − 4S 0Tˆs
[M=0]
(13)
Under this range of channel load, the other transmission
probabilities,
{τ1,τ 2 ,τ 3} and collision probabilities
{p 0 , p1 , p 2 , p 3 } are found in a closed form by substituting the
result in Eq (13) back into Eq. (9)–Eq. (11).
In the range here only AC[0] is starved, we find that:
τ1 =
S1Tˆe
.
1 + S Tˆ − 3S Tˆ
1 e
M
[M=1]
(14)
1 s
In this way, we proceed also for higher values of M in order
to find the medium access probabilities for all levels of traffic
intensity on the wireless medium.
e
M
s
2
M
2
s
2
M
c
e
M
s
2 + ( N − M ) 2 S M Tˆc + S M Tˆe − 2( N − M ) S M Tˆs
.
This solution is applicable in a scenario where two stations
dominate the communication on the channel.
D. Cubic Solution (with n=3 and Totally 12 Queues)
In the same way, we may solve the set of equations for a
higher number of n. For n=3, we found the following solution
for N=4 and M=0:
τ0 =
.
We have seven equations and eight unknown variables. Eq.
(1) provides the last equation that is required to solve the set
of equations:
(11)
nτ 3 (1 − p3 ) = Si (1 − pb )Tˆe + psTˆs + ( pb − ps )Tˆc ,
τM =
C. Quadratic Solution (with n=2 and Totally 8 Queues)
The solution for the quadratic case is given by the root:
(15)
1 + 2 S Tˆ − ( N − M ) S Tˆ m 1 + ( N − M ) ( S Tˆ − S Tˆ Tˆ ) − 2( N − M ) S Tˆ
3
3
X3 + X4
Xo
X2
+
+
,
2 X1 3 X13 X 3 + X 4
33 2 X 2
[M=0],
(16)
where:
•
X 0 = 2 + 16 S0 T̂c + S0 T̂e - 8 S0 T̂s
•
X 1 = 3 - 16S0 Tc + S0 Te - 12S 0 Ts
•
X 2 = 9 (1 + 81S0 T̂c + 2604S02 T̂c2 + 482S02 T̂c T̂e
- 8 S0 T̂s - 320S02 T̂c T̂s + 16S02 T̂s2 )
•
X 3 = 27S 0 T̂e X 12 + 54 X 52 − 81X 1 X 5 (1 + S0 T̂e − 4S 0 T̂s )
•
X 4 = 4X + X
•
X 5 = 2 + 16S 0 T̂c + S0 T̂e - 8S 0 T̂s
3
2
(17)
2
3
Among the three roots of the cubic equation that was
solved, the one written in Eq. (16) – Eq. (17) above was the
only root that was not a complex number.
This n=3 scenario was actually used as an example in
Section II, and a corresponding topology was illustrated in
Figure 1 above. We will return to this scenario when
undertaking the validations in Section VIII.
E. Quartic Solution (with n=4 and Totally 16 Queues)
We also found the valid root of the quartic equation as the
solution to the scenario with 16-queue and n=1. Although the
closed-form solution is not given explicitly here due to the
space limitations, we will make validations of it in Section
VIII.
F. Limitations (Quintic Solution)
The proposed closed-form solution method for scenarios
with virtual collision handling is limited to a maximum of four
actively transmitting stations. A higher number of stations
result in a quintic equation, which is not immediately solved
by the coefficient of the equation. This limitation follows
directly from the Ruffino-Abel theorem. Although a closedform solution might still be found, it is quite probable that one
has to return to numerical methods.
Luckily, the scenarios without virtual collision handling
addressed in the next section, on the contrary, can be solved in
a closed form for topologies encompassing up to 16 actively
transmitting nodes.
V. CLOSED-FORM SOLUTION WITHOUT VIRTUAL COLLISION
HANDLING
Again we consider a scenario with w different wireless
stations and – as earlier – also with Nn number of actively
transmitting queues. However, now each station is actively
transmitting on only one of the four transmission queues at a
time. Hence, the active queues are distributed on N times as
many nodes as in the previous section, for a given value of n.
Thus:
N =4
n0 = n1 = n2 = n3 = n
[Example 2].
(18)
N −1
w = ∑ ni = Nn
i =0
Since there will be no virtual collisions occurring between
the queues, we have [8]:
1 − pb
1 − pb
; 1 − p1 =
;
1−τ0
1 −τ1
1 − pb
1 − pb
1 − p2 =
; 1 − p3 =
.
1−τ 2
1−τ3
1 − p0 =
[with VC].
(19)
be set to zero, either because the AC also experiences Medium
Access Starvation in which no packets will be transmitted, or
because no traffic sessions of an AC will be initiated by
upper-layer protocols when that AC is practically not usable.
When the starved AC is not subject to Medium Access
Starvation, there might be some sort of traffic being
transmitted of the starved AC for one reason or another, as
discussed earlier. To deal with this, we let θ i denote the
transmission probability of the starved AC[i] at a given traffic
load. Furthermore, we assume that we know the transmission
probabilities θ 0 ,..., θ M −1 of all the M starved ACs. Then, we can
use Eq. (6) without the restriction in Eq. (7).
It is easy to modify the closed-form solutions above to take
this into account. For the n=1 case with virtual collision
handling, for example, the closed-form solution can now be
written:
τM =
S M Tˆe + Φ M
,
ˆ
1 + S M Te − ( N − M ) S M Tˆs + Φ M
(22)
Combining this with our throughput assumption in Eq. (6)
gives:
(20)
τ 0 = τ1 = τ 2 = τ 3.
where Φ M is determined recursively by:
Like before, Eq. (1) provides the last equation that is required
to solve the set of equations:
(21)
nτ 0 (1 − p0 ) = Si ((1 − pb )Tˆe + psTˆs + ( pb − ps )Tˆc ) .
Assume for example a throughput pattern for n=1, which
actually resembles that shown in Figure 2. When calculating
the transmission probability for AC[3], where AC[3] is about
to become starved, it is observed that the transmission
probability of AC[2], θ 2 , is non-zero, while θ 0 and θ1 can be
approximately set to zero. Then, Φ 2 = θ 2 and the transmission
probability for AC[3] is found as:
The closed-form solutions can be found in the same manner
as for the virtual-collision scenarios, as described in the
previous sub-section.
Station 16 Station 1
Station 15 (AC[3])
(AC[0]) Station 2
(AC[3])
(AC[0])
Station 14
Station 3
(AC[3])
(AC[0])
Station 13
(AC[3])
Station 4
(AC[0])
Access Point
Station 12
(AC[2])
Station 5
(AC[1])
Station 11
Station 6
(AC[2])
(AC[1])
Station 10
Station 7
(AC[2]) Station 9 Station 8 (AC[1])
(AC[2])
(AC[1])
Fig. 3. Probably the biggest WLAN topology that can be solved in a closed
form.
As before, we are restricted by the quintic equation. Thus, it
might be difficult to find a closed-form solution of scenarios
consisting of more than 16 different stations that are actively
transmitting. Figure 3 shows the limiting case with 16 stations
contending for channel access, and each station transmitting
traffic of one particular AC. Although the closed-form
solution of it is not given explicitly here due to the space
limitations, we will validate it in Section VIII.
VI. CLOSED-FORM SOLUTION WITHOUT MEDIUM ACCESS
STARVATION
Until this point, we have assumed that when an AC, AC[i],
experiences Queue Starvation, its transmission probability can
Φ0 = 0
Φ i = Φ i −1 (1 + θ i −1 );
τ3 =
(23)
i = 1,..., M .
S 3Tˆe + θ 2
.
1 + S 3Tˆe − S 3Tˆs + θ 2
[M=3]
(24)
VII. USING AN EXISTING MODEL TO PREDICT THE NONSATURATION MAC DELAY IN A CLOSED FORM
A. Mean Medium Access Delay
According to the model in [5-7] that we choose to build
upon for the validations in the remaining part of the paper, the
mean non-saturation medium access delay, Di
Di NON − SAT = (1 − p Li i +1 )(Ts + Tc
NON − SAT
, is:
pi
)+
1 − pi
(25)
(W − 1)
Te + ps Ts + (1 − ps )Tc p
p j i, j
,
* ∑ i
(
1
)
2
−
p
p
p
b
i j =1
b
*
i
Li
where the contention window size Wi, j and the countdown
blocking probability, pi∗ , are defined in [5-7]. Below, we will
insert the medium access probabilities derived by the closedform solution directly into the expression for Di NON − SAT in Eq.
(25), to determine the medium access delay in a closed form.
which is described in Section V and illustrated in Figure 3.
We see that the closed-form solution performs well also when
virtual collision handling is not occurring.
12
10
Delay (ms)
8
C. Validation for M>0
Validations for M>0 (i.e. when at least AC[0] is starved)
look promising but require a detailed discussion around the
setting of the θ -value. It was therefore omitted. This case
should instead be addressed more rigorously in follow-up
work.
6
4
2
0
0
200
400
600
800
1000
1200
1400
Traffic generated per AC [Kb/s]
3 stations; 12 queues, AC[0]: Closed Form
3 stations; 12 queues; AC[0]: Numerical
VIII. CONCLUSIONS
Fig. 4. Medium access delay of AC[0] (with the scenario from Section II).
20
18
16
Delay (ms)
14
12
10
8
6
4
2
0
0
200
400
600
800
1000
1200
1400
Traffic generated per AC [Kb/s]
4 stations; 16 queues, AC[0]: Closed Form
4 stations; 16 queues; AC[0]: Numerical
Fig. 5. Medium access delay of AC[0] (with 4 stations and 16 queues).
20
18
16
Delay (ms)
14
12
10
The throughput assumption enables us to find the medium
access probabilities in a closed form. Since the presented
solution does not derive the performance values directly, it is
applicable to a large number of analytical models.
We observe that despite the underlying assumptions, the
closed-form solution is fairly accurate sufficiently close to the
saturation condition.
Validations of other performance metrics, such as the
queueing delay [6-7], should be explored in follow-up work.
We anticipate this to yield very promising results, because the
queueing delay goes sooner to infinity than the medium access
delay explored here. Thus, the accuracy of the throughput
assumption will probably be good until the point where either
the queueing delay or the queue drop probability exceeds the
upper limit for possible operation of upper-layer protocols and
applications.
A long-version of this paper will be made available at
http://www.unik.no/personer/paalee/research.htm including
the explanations that had to be dropped due to the pagelimitation of this paper.
8
REFERENCES
6
4
[1]
2
0
0
200
400
600
800
1000
1200
1400
Traffic generated per AC [Kb/s]
[2]
16 stations; 16 queues; AC[0]: Closed Form
16 stations; 16 queues; AC[0]: Numerical
[3]
Fig. 6. Medium access delay of AC[0] with 16 stations with one queue each
(as shown in Figure 3 in Section V).
B. Validations (M=0)
Figure 4 shows that the accuracy of the closed-form
solution is fairly good when compared with numerical
calculations for the topology with three stations (in addition to
the access point) as presented in Figure 1.
Figure 5 makes the same comparison between the closedform solution and numerical calculations as in Figure 4,
except that here a topology with four actively transmitting
stations is considered. Four different queues are still
implemented on each station, and virtual collision handling
occurs between these queues. Also in this scenario, we
observe that the closed-form solution performs fairly well.
Figure 6 makes a comparison with the 16-station scenario,
[4]
[5]
[6]
[7]
[8]
IEEE 802.11 WG, "Part 11: Wireless LAN Medium Access Control
(MAC) and Physical Layer (PHY) specification", IEEE 1999.
IEEE 802.11 WG, "Draft Supplement to Part 11: Wireless Medium
Access Control (MAC) and physical layer (PHY) specifications:
Medium Access Control (MAC) Enhancements for Quality of Service
(QoS)", IEEE 802.11e/D13.0, Jan. 2005.
Bianchi, G., "Performance Analysis of the IEEE 802.11 Distributed
Coordination Function", IEEE J-SAC Vol. 18 N. 3, Mar. 2000, pp. 535547.
Xiao, Y., "Performance analysis of IEEE 802.11e EDCF under
saturation conditions", Proceedings of ICC, Paris, France, June 2004.
Engelstad, P.E., Østerbø O.N., "Delay and Throughput Analysis of IEEE
802.11e EDCA with Starvation Prediction", Proceedings of the 30th
Annual IEEE Conf. on Local Computer Networks (LNC ’05), Sydney,
Australia,
Nov.
15-17,
2005.
(See
also:
http://www.unik.no/personer/paalee/research.htm .)
Engelstad, P.E., Østerbø O.N., "Queueing Delay Analysis of 802.11e
EDCA", Proceedings of The Third Annual Conference on Wireless On
demand Network Systems and Services (WONS 2006), Les Menuires,
France, Jan. 18-20, 2006. (See also: http://folk.uio.no/paalee .)
Engelstad, P.E., Østerbø O.N., "Analysis of the Total Delay of IEEE
802.11e EDCA", Proceedings of IEEE International Conference on
Communication (ICC'2006), Istanbul, June 11-15, 2006.
Engelstad, P.E., Østerbø O.N., "Differentiation of the Downlink 802.11e
Traffic in the Virtual Collision Handler", Proceedings of the 30th
Annual IEEE Conf. on Local Computer Networks (LNC ’05), Sydney,
Australia, Nov. 15-17, 2005.