Solutions to End of Chapter Problems
advertisement
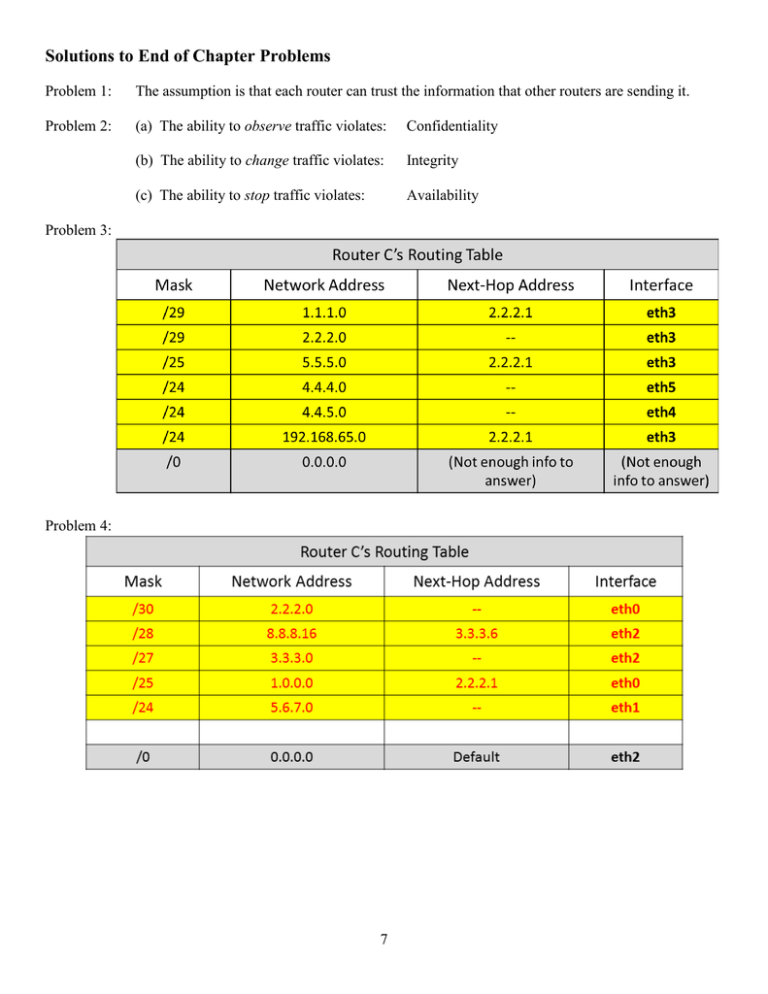
Solutions to End of Chapter Problems Problem 1: The assumption is that each router can trust the information that other routers are sending it. Problem 2: (a) The ability to observe traffic violates: Confidentiality (b) The ability to change traffic violates: Integrity (c) The ability to stop traffic violates: Availability Problem 3: Problem 4: 7 (b) (c) (d) First Address: 8.8.8.24 Last Address: 8.8.8.31 (e) Yes, 8.8.8.26 is between 8.8.8.24 and 8.8.8.31. (f) No, Router C will direct all traffic to the evil instructor using interface eth1. (g) Solution #1, an MD5-hash of a shared secret key: in OSPF, routers can send the hash of a shared secret key along with their LSP to authenticate themselves with other routers. Solution #2, passive interfaces: once a network administrator sets up a passive interface on a router, the router will ignore all routing information being sent over that interface. (h) The network administrator is responsible for implementing these security measures. Problem 5: The assumption is that each router can trust the information that other routers are sending it. Problem 6: (a)-(c): (d). No, the first and last IP addresses of the false network are 8.9.7.80 and 8.9.7.95, respectively. The webserver’s IP address does not fall within that range. Thus, all traffic destined for the website will not go to the attacker, but towards the webserver as normal. 8 (e): Solution #1 Solution #1 a simple plaintext-password: added to all LSPs so each router can authenticate the information it is receiving. Solution #2 an MD5-hash of the OSPF packet and a shared secret key: in OSPF, routers can send the hash of the OSPF packet and a shared secret key along with their LSP to authenticate themselves with other routers. Solution #3 passive interface: once a network administrator sets up a passive interface on a router, the router will ignore all routing information being sent over that interface. (f) The Network Administrator 9











