Router/Switch Security
advertisement
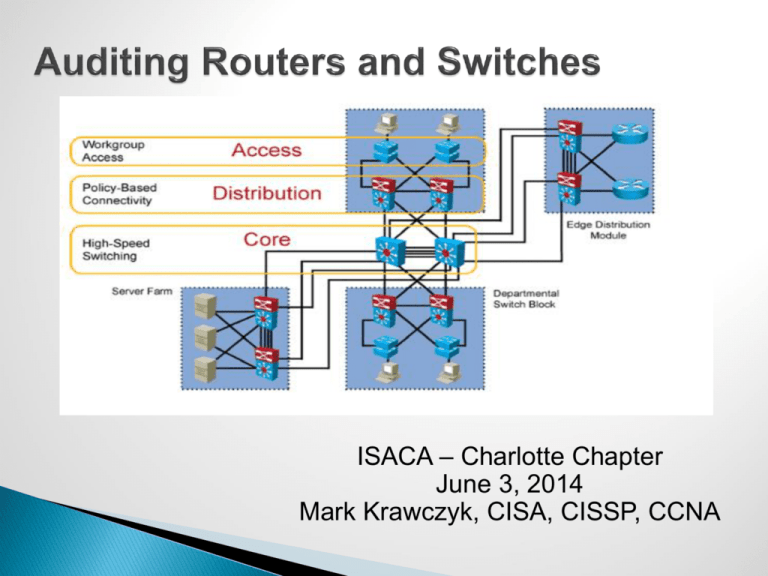
ISACA – Charlotte Chapter June 3, 2014 Mark Krawczyk, CISA, CISSP, CCNA • • • Routers and Switches direct and control much of the data flowing across computer networks. The services provided are critical to the proper functioning and secure operations of Corporate networks. Properly configured secure routers and switches can greatly improve the overall security posture of a network. • Network devices are subject to various attacks: • Unauthorized access – compromise device, routing tables, MAC tables. • Session hijacking - an attacker can insert falsified IP packets after session establishment via IP spoofing. • Rerouting - manipulating router updates to cause traffic to flow to unauthorized destinations (route injection). • Masquerading - manipulates IP packets to falsify IP addresses. • Denial of Service (DoS) - flooding the router with traffic or requests designed to consume all of some limited resource. • Eavesdropping – insecure protocols, packet sniffers • • Routing is accomplished using the IP addresses of the source and destination hosts and intermediary network devices such as Routers or Multilayer switches. The router examines the destination network address for each packet and then checks the routing table for forwarding information. • The routing table stores information about connected and remote networks. • Connected networks are directly attached to one of the router interfaces. • Remote networks are not directly connected to the router. Routes to these networks can be manually configured on the router or learned automatically using dynamic routing protocols. • • Static Routing - Routes to remote networks are manually configured on the router. A default route can be statically configured. Dynamic Routing- As routers become aware of changes to the networks this information is passed on to other routers. When a router receives information about new or changed routes, it updates its own routing table and, in turn, passes the information to other routers.