Firewalls
advertisement

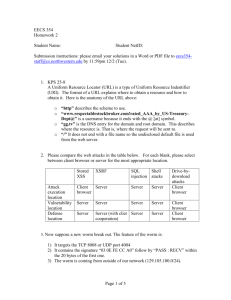
Firewalls CS461/ECE422 Spring 2012 Reading Material • Text chapter 9 • “Firewalls and Internet Security: Repelling the Wily Hacker”, Cheswick, Bellovin, and Rubin. Firewall Goal • Insert after the fact security by wrapping or interposing a filter on network traffic Inside Outside Firewall Requirements • All traffic between network section A and network section B (and visa versa) must pass through the firewall (or a consistently controlled set of firewalls) • Only authorized traffic (as specified by the security policy) is allowed to pass • The firewall itself is immune to penetration “Typical” corporate network Firewall Intranet Mail forwarding File Server Web Server Mail server DNS (internal) Demilitarized Zone (DMZ) DNS (DMZ) Web Server Firewall User machines User Usermachines machines Internet Packet Filter Firewall • Operates at Layer 3 in router or HW firewall • Has access to the Layer 3 header and Layer 4 header • Can block traffic based on source and destination address, ports, and protocol • Does not reconstruct Layer 4 payload, so cannot do reliable analysis of layer 4 or higher content Rule Scenario Example Packet Filter Rules • Rules attached to outside interface Action Source Addr Src port Dest Addr Dest Port Protocol Comment Block Outside host * * * * Don’t trust Allow * Our Mail Server 25 Tcp Allow mail traffic * • Rules attached to inside interface Action Source Addr Source Port Dest Addr Dest Port Protocol Comment Block * * Outside host * * Don’t trust Allow Our Mail Server 25 * * Tcp Allow Mail traffic Same Rules in iptables • Rules in the filter table • -A FORWARD –p ip -s outside_host –j REJECT -A FORWARD –p ip –d outside_host –j REJECT -A FORWARD –i outside –p tcp –d our_mail_server –m tcp --dport 25 –j ACCEPT -A FORWARD –i inside –p tcp –s our_mail_server –m tcp --sport 25 –j ACCEPT -A FORWARD –j REJECT More Example Pack Filter Rules • Rules attached to inside interface Action Source Addr Source Port Dest Addr Dest Port Proto Comment Allow * * * 25 TCP Allow traffic to all mail servers • Rules attached to outside interface Action Source Addr Source Port Dest Addr Dest Port Proto Comment Allow * 25 * * TCP Allow return traffic from all mail servers A Better Example • Rules attached to inside interface Action Source Addr Source Port Dest Addr Dest Port Proto Comment Allow Inside networks * * 25 TCP Allow traffic to all mail servers • Rules attached to outside interface Action Source Source Dest Addr Port Addr Allow * 25 Dest Port Inside * networks Proto Flags Comment TCP ACK Allow return traffic from all mail servers FTP Example • Rules attached to inside interface Action Source Addr Source Port Dest Addr Dest Port Proto Allow Inside * networks * 21 TCP Allow Inside > 1024 networks * * TCP Flags Comment Allow Control channel traffic out ACK Allow data traffic back • Rules attached to outside interface Action Source Source Dest Addr Port Addr Dest Port Proto Flags Comment TCP ACK Allow return traffic for FTP control channel Allow * 21 Inside * networks Allow * * Inside >1024 TCP networks Initiate data traffic Stateful Inspection Firewall • Evolved as packet filters aimed for proxy functionality • In addition to Layer 3 reassembly, it can reconstruct layer 4 traffic • Some application layer analysis exists, e.g., for HTTP, FTP, H.323 – Called context-based access control (CBAC) on IOS – Configured by fixup command on PIX • Some of this analysis is necessary to enable address translation and dynamic access for negotiated data channels • Reconstruction and analysis can be expensive. – Must be configured on specified traffic streams – At a minimum the user must tell the Firewall what kind of traffic to expect on a port – Degree of reconstruction varies per platform, e.g. IOS does not do IP reassembly Circuit Firewall • Actually creates two separate TCP connections – Completely reconstructs TCP connections – SOCKS is an example implementation Example Stateful Rules • Rules attached to outside interface Action Source Addr Src port Dest Addr Dest Port Protocol Comment Block Outside host * * * * Don’t trust Allow * Our Mail Server 25 Tcp Allow mail traffic * • Rules attached to inside interface Action Source Addr Source Port Dest Addr Dest Port Protocol Comment Block * Outside host * Don’t trust * * Same Rules in iptables • Rules in the filter table • -A FORWARD –p ip -s outside_host –j REJECT -A FORWARD –p ip –d outside_host –j REJECT -A FORWARD –m state --state ESTABLISHED, RELATED – j ACCEPT -A FORWARD –i outside –m state –state NEW –p tcp – d our_mail_server –m tcp --dport 25 –j ACCEPT -A FORWARD –j REJECT Application Proxy Firewall • Firewall software runs in application space on the firewall • The traffic source must be aware of the proxy and add an additional header • Now transparent proxy support is available (TPROXY) • Leverage basic network stack functionality to sanitize application level traffic – Block java or active X – Filter out “bad” URLs – Ensure well formed protocols or block suspect aspects of protocol Traffic reconstruction X Y FTP: X to Y GET /etc/passwd GET command causes firewall to dynamically open data channel initiate from Y to X Might have filter for files to block, like /etc/passwd Ingress and Egress Filtering • Ingress filtering – Filter out packets from invalid addresses before entering your network • Egress filtering – Filter out packets from invalid addresses before leaving your network Owns network X Inside Outside Egress Filtering Block outgoing traffic not sourced from network X Ingress Filtering Block incoming traffic from one of the set of invalid networks Denial of Service • Example attacks – Smurf Attack – TCP SYN Attack – Teardrop • DoS general exploits resource limitations – Denial by Consumption – Denial by Disruption – Denial by Reservation Teardrop Attack • Send series of fragments that don't fit together – Poor stack implementations would crash – Early windows stacks Offset 0, len 60 Offset 30, len 90 Offset 41, len 173 Address Translation • Traditional NAT RFC 3022 Reference RFC • Map real address to alias address – Real address associated with physical device, generally an unroutable address – Alias address generally a routeable associated with the translation device • Originally motivated by limited access to publicly routable IP addresses – Folks didn’t want to pay for addresses and/or hassle with getting official addresses • Later folks said this also added security – By hiding structure of internal network – Obscuring access to internal machines • Adds complexity to firewall technology – Must dig around in data stream to rewrite references to IP addresses and ports – Limits how quickly new protocols can be firewalled Address Hiding (NAPT) • Many to few dynamic mapping – Packets from a large pool of private addresses are mapped to a small pool of public addresses at runtime • Port remapping makes this sharing more scalable – Two real addresses can be rewritten to the same alias address – Rewrite the source port to differentiate the streams • Traffic must be initiated from the real side • Called masquerading in iptables if the interface IP is used for the alias address NAT example Hide from inside to outside 192.168.1.0/24 behind 128.274.1.1 Static map from inside to DMZ 192.168.1.5 to 128.274.1.5 192.168.1.0/24 Src=192.168.1.100 Dst=microsoft.com inside Enforcing Device DMZ 10.10.10.0/24 outside Internet Src=128.274.1.1 Dst=microsoft.com Static Mapping • One-to-one fixed mapping – One real address is mapped to one alias address at configuration time – Traffic can be initiated from either side • Used to statically map out small set of servers from a network that is otherwise hidden • Static port remapping is also available NAT example Hide from inside to outside 192.168.1.0/24 behind 128.274.1.1 Static map from DMZ to Internet 10.10.10.5 to 128.274.1.5 192.168.1.0/24 inside Enforcing Device DMZ 10.10.10.0/24 Src=X Dst=10.10.10.5 outside Internet Src=X Dst=128.274.1.5 Deployment • Hardware Firewall – Buy firewall from vendor • They provide software and hardware • Depending on cost, may include hardware accelerators • Software Firewall on hardened bastion server – Buy software from vendor or use open source – Harden server to reduce attack surface • Host-based firewall – Additional layer of defense for application server • Personal firewall – Protect desktops/laptops from undesired probing DMZ Network Firewall Intranet Mail forwarding File Server Web Server Mail server DNS (internal) Demilitarized Zone (DMZ) DNS (DMZ) Web Server Firewall User machines User Usermachines machines Internet VPN Network Distributed Firewalls Intrusion Prevention • Discussed in the Intrusion Detection lecture • Enables more dynamic rules and access rules that rely on more communication details – Can download new signatures or adapt anomaly rules on a daily basis Unified Threat Management (UTM) • Firewalls at the border provide a nice point for analysis – Might as well perform other analysis as long as flows have been tracked – Deploy one box instead of N boxes • Additional actions could be – – – – Virus scanning URL filtering IDS/IPS/anomaly detection Spam filtering Limits to firewalls • Cannot analyze encrypted traffic – Beyond header information • Everything is driven through port 80 – Relies on port as indicator of service – Newer firewalls dynamically analyze traffic to determine protocol • Cannot react to new attacks on protocols that must be allowed – IPS can help • Tracking IP addresses instead of people • Costs too much to manage firewalls Summary • Different types of firewalls for different needs – Packet filtering/stateful/application – Network/Host/personal • Firewalls have been a stalwart element of network security for decades – Not the end all solution – But still beneficial