Communicating Information
advertisement

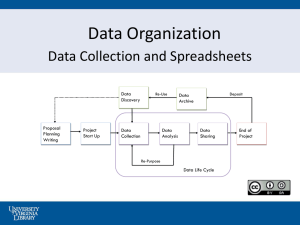
Year 11 Revision Notes Communicating Information Applications Handling Information Operating Systems and Networks Modelling Spreadsheets Social Implications Monitoring and Control Communicating Information INFORMATION TECHNOLOGY Revision Notes Audience and Purpose All information is communicated for a purpose, to an audience; – The audience is the group of people that a communication is directed at. – The purpose is the reason the communication takes place. The audience may not always be the same. The purpose may change. Emphasis A change in purpose may change the emphasis in presenting the content of a communication. The extent to which the audience is likely to understand what is being communicated should be taken into account. Make sure the information is relevant. If there is too much divergent information the audience may become confused. Word Processing Using a wordprocessor you can: write a letter, an essay, a questionnaire, etc; create, save, open, load and print documents; move around a document by scrolling insert, delete and edit text use different text fonts and sizes, and generate word art move, cut, copy and paste blocks of text import and export text, clip art, database and spreadsheet tables generate personalized mail using mail merge facility. Graphics software Using graphics software you can: create, save, open or load and print graphics files draw on a screen using a variety of colours use different brushes, sizes and densities of brush strokes draw freehand and regular shapes fill shapes with patterns and colours use different text fonts and sizes zoom in and out to edit text and graphics move, cut, copy and paste blocks of text and graphics import and export scanned images and other graphics Desk Top Publishing Using DTP software you can: lay out the pages of a newsletter, magazine, etc create, save, open or load, and print DTP pages import and export text, scanned images, clipart, database reports and spreadsheets resize images view the page in different magnifications, zoom in and out move around a page by scrolling up and down it move, cut, copy and paste blocks of text and graphics use different text fonts and sizes, and generate word art Multimedia Using multimedia software you can: – View encyclopaedias that combine text, graphics, sound etc. on a CD-ROM – Produce multimedia presentations Using e-mail, you can: – Send and receive messages using the internet – set up address books and mailing lists Using video conferencing, you can: – see people you are talking to on the screen – share screens for graphics and other documents – take part in meetings and debates with people in different places Revision Tips Remember the different ways to generate text – – – – – input using a keyboard scan form a book using OCR export from one piece of software and import copy it from a CD-ROM or the WWW download it using e-mail Remember the different ways to generate graphics – scan line drawings and photos using a scanner – take photographs using a digital camera – copy an image from a clip-art library Handling Information and Databases INFORMATION TECHNOLOGY Revision Notes Databases A database is an organised collection of information consisting of 1 or more files (or tables) A database file is a collection of related records. For example, a file of information about all the pupils in a school A record in a database file is a collection of related fields. In the records of the same type , the fields are in the same order. A field is an item of information. For example, each pupils surname. Fields A fieldname (reference) is the name given to a field. This must be a unique name. A keyfield uniquely identifies a record. This can be a record number for instance. Fields can have different data types. Common examples are: – – – – – alphanumeric (0-9, A-Z & symbols such as £) Numeric (integer - whole numbers or real) Date (in standard format e.g. DDMMYY) Multiple Choice, Ordered Choice etc Coded (first 2-3 characters only - usually text) Data Collection Data collection can be done using a questionnaire or other form. A Questionnaire should – – – – – – have a title and introduction explaining its purpose only collect the information required be clear and precise about what information is needed provide sufficient space to write in the information use character boxes to assist data entry use tick lists (multiple choice) to show what options are available Direct Data Capture Direct data capture and input can be done using: Optical Mark Recognition (OMR) e.g.National Lottery or school registers Optical Character Recognition (OCR) Bar codes Magnetic stripe card (e.g. visa or access) Verification Verification is checking that the data captured is accurately input into the computer. Information input from questionnaires or forms should be verified The double entry system involves 2 people inputting the data. The computer checks that they have both input the same information. If it is not a mistake has been made which must be corrected. Double entry verification ensures accuracy but takes longer and costs more. Validation Validation is checking that the data is reasonable, for example: a length check checks that a field is not too long or too short; a type check checks that the information is of the correct data type; a range check checks that the information is within the expected range; a check digit is recalculated to ensure that, for example, a bar code has been read accurately by a bar code reader. Database Integrity The information on a database has to be kept up-todate and secure. To do this, you: edit or amend the information stored in a field if it changes; insert or create a new record to add new information to a file delete a record to remove it if is no longer needed; backup the database by making another copy of it; restore the database from the backup copy if you lose the original. What a Database can do Using a database, you can: Keep records of customers, criminals, books, stock, pupils etc Select records that match a search condition to find the information you want. Sort the information into some order. For example, descending alphabetical order (Z to A) Print a report containing the information selected Export the results of a search into another program Import text, images etc. from other software. Teletext Teletext, e.g. Ceefax, is a simple way of handling information using a page-based system Teletext pages can be received and displayed on a TV or using a computer. Pages are broadcast in cycle. You have to wait for your page to be broadcast. Teletext is not interactive Fastext allows several pages next to the selected page to be stored in memory. Other pages are not accessed any faster. The Internet The Internet is a worldwide collection of interconnected networks. There is no one central organisation that owns or controls the Internet. It provides services such as electronic mail (e-mail). To connect at home you need a modem, a telephone line and an Internet Service Provider (ISP). An ISP provides dial-in lines so that users can connect to the Internet. It may also provide other services such as News and Weather. The World Wide Web The World Wide Web runs over the Internet. The information is stored on information servers (Web sites, Web servers) located throughout the world. You can access the web using a browser. To find information on the web, you could: Access a page by typing in its Uniform Resource Locater (URL). This is its address on the web. Use a search engine to search for particular topics. Surf the web by activating hotspots. There are usually hyperlinks on most pages leading to other pages. Modelling and Spreadsheets INFORMATION TECHNOLOGY Revision Notes Spreadsheets A spreadsheet can be used for a wide variety of tasks that involve calculations. They are often used for financial applications and in mathematics. A spreadsheet is divided into vertical columns and horizontal rows, Cells can contain different types on information: – – – – text, e.g. Mr. Jones numbers, e.g. 23 or £34.67 formulae, e.g. =SUM(A2:A11) dates and times, e.g. 20/4/99 Cell References Cell references can refer to a single cell e.g. D5 A cell reference can be a relative cell reference. This will adjust automatically when it is moved or copied to a new position A cell reference can be an absolute cell reference. This will not change when it is moved or copied. For example, suppose C3*$A$1 is in D3 and is moved to D4, the formula will change to C4*$A$1. $A$1 is an absolute cell reference, it does not change. A cell range reference refers to a group of cells. E.g. B2:D6 What Spreadsheets can do Formulae may recalculate automatically when the numbers in the cells they refer to change. Cells may be moved or copied from one part of a spreadsheet to another. Columns and rows can be deleted and inserted. Formats can be applied to cells and ranges of cells It is possible to sort groups of cells You can generate graphs that illustrate the information stored in the spreadsheet. For example, bar charts, pie charts and line graphs. You can export a range of cells to another piece of software. Modelling A model is a representation of the real world. It is not the real world. It can be used to: improve understanding of a well known situation; learn about unfamiliar situations; increase awareness and understanding of the situation modelled; help understand problems and try out solutions; experiment without danger or expense; predict what will happen. Modelling using a spreadsheet Spreadsheets can be used for modelling though they are more often used to handle information. A spreadsheet model will: allow a range of input variables to be set; use formulae to define the rules on which the model is based; output information using the variables, stored values and the rules. Common spreadsheet models Spreadsheet models commonly used are: Price Forecast Supermarket queue Break-even Predator/Prey Monitoring and Control INFORMATION TECHNOLOGY Revision Notes Sensors and Actuators A sensor is an input device used to measure environmental conditions. Different sensors can monitor temperature, humidity, light, sound, pressure, wind speed, wind direction, tilt, etc. An actuator is an output device used to adjust environmental conditions. Actuators are heaters, motors, valves, pumps, boilers, etc. Their source of power could be electricity, hydraulics, compressed air, etc. Data logging Data logging is the automatic recording and storage of the information provided by sensors. For example, weather stations automatically record and store the temperature once every hour. The stored information can then be downloaded to a computer perhaps over a network. The frequency of sampling or time interval gives the time between measurements. The period of logging is the length of time the logging takes place. Control Systems Control systems monitor and control environmental conditions using sensors to determine what is happening and actuators to change what is happening Feedback is a cycle of sensing, processing and reaction. Computer control systems use a control interface. This is the hardware that converts the signals from the sensors so that the computer can understand them and the signals from the computer so that the actuators can understand them. Computer Programs Computers themselves are controlled by programs. A computer program is a list of instructions to a computer written in a computer language. A computer language may be designed to initiate a very restricted range of actions. General purpose computer languages are harder to understand but can do a wider range of tasks, for example, BASIC. Different program structures can be used in computer programs. Examples are: – Conditional statements: IF INPUT = “YES” THEN [action] ELSE [action] – A loop is a series of instructions that is to be repeated. – A procedure is a self-contained sequence of instructions that can be run from elsewhere in the program. Flowcharts Start No Switched on? END Yes Measure the temperature Yes Too hot? Turn off the heater No Yes Too cold? No Turn on the heater A flowchart can be used to describe how a task is done or a computer program is constructed. Applications INFORMATION TECHNOLOGY Revision Notes Applications An application is using IT to do a useful task. IT is used throughout commerce and industry for a wide variety of applications. Common commercial applications include: payroll, stock control, orders and deliveries, banking, shopping, booking tickets, lottery tickets etc. An IT system is the whole system of hardware, software and human activities that is used in an application. A legacy system is an old IT system that is still in use. A manual system is a system that does not use IT. Processing Information Interactive processing takes place when the user and the computer have a ‘conversation’. It is a cycle of input, processing, output, and user reaction. Interactive IT systems react to the information input as they are being used. In batch processing, all the data to be processed is available before processing starts. Data is processed in batches. For example, a payroll system. In real time processing, data is processed as it is input. Real time systems are very fast and interactive. They are usually run on dedicated computers. The system life cycle System investigation Feasibility study System analysis and design Program design, coding and testing Implementation System documentation Evaluation Maintenance – A parallel run tests the new system by running the old system at the same time. Operating Systems and Networks INFORMATION TECHNOLOGY Revision Notes Hardware and Software Information Technology is the use of computers and other equipment to store, process and transmit information. Hardware is the physical equipment, e.g. monitor. Software are the programs that control the computer. Mainframes are large computers Microcomputers are Personal Computers (PC’s). These can be desktop PC’s, portables or laptops. Desktops typically consist of a monitor, a processor case, a hard disk, a floppy disk drive, a keyboard and a mouse. Multimedia PC’s also have a CD-ROM drive and stereo speakers. Memory and Storage Random Access Memory (RAM) is usually installed in the processor case. Programs and data is stored in RAM while they are being used. RAM is volatile, the information stored on it is lost when the computer is switched off. Backing storage is on a hard disk, floppy disk or CDROM. Backing storage is non-volatile, it is not lost when the computer is switched off. – The size of memory and backing storage is measured in bytes. 1 byte is the memory required to store 1 character. • 1 Kilobyte (Kb) = 1024 bytes • 1 Megabyte (Mb) = 1024 Kb • 1 Gigabyte (Gb) = 1024 Mb File Operations Software and data are saved on disk as files. A directory is a list of all the files on a disk. File operations are: Saving a file. Loading a file. Merging two files to form 1 file. Updating a file by editing or amending it. Deleting a file by removing it. Renaming a file. Copying a file. Input Information can be input to a PC using a mouse and a keyboard. Other input methods are: Optical Mark Recognition (OMR) and Optical Character Recognition (OCR) using a scanner. Bar codes using a light pen or laser scanner. Magnetic Ink Character Recognition (MICR), to read bank cheques. Magnetic Stripe Cards. e.g. Credit cards Microphone. Voice recognition is spoken input. Midi technology allows sound and music to be input. Touch screens using a pen or your finger. Video digitiser and digital cameras. Output Printers can be: – Impact dot matrix. Cheap to buy and run, slow with poor quality. – Ink jet. Cheap to buy but expensive to run. Slow but good quality. – Laser. Expensive to buy and run. Quick with excellent quality. A printer buffer is RAM memory built into the printer. It is used to store print jobs, releasing the computer to continue with other jobs. Spooling is the queuing of files waiting to be printed on a hard disk. Other output methods include: – Graph plotters, draws using pens. Very high quality. – Speech synthesis which is the output of human speech. Operating Systems An Operating System (OS) is software that runs between the hardware and the applications software. An OS will: Carry out OS commands. Either through the GUI or at the command line, e.g. COPY C:\ACCESS\AGENTS A:. Supervise programs. The OS will try to keep programs running, giving the user messages when there are problems. Make the hardware easier to use, so that you do not have to know the internal complexities of the hardware. Continued . . . . Operating Systems Help users decide what to do. For example, if the printer is unavailable, it will tell you and ask you what you want to do. Providing utilities to manage the computer system. For example, to format floppy disks. Optimize the use of the computer’s resources. For example, printing in the background. Support multitasking, running more than 1 piece of software at the same time. Make programs portable, so that they can be run on different computers with the same OS. Networks A network allows users to share software and hardware, and communicate with other networks. A Local Area Network (LAN) is a small network, in one building. Computers are probably connected by cables. A Wide Area Network (WAN) is a widespread network, probably national or international. Computers are probably connected to a WAN using a modem and the telephone network. Network Operating Systems A Network Operating Systems (NOS) can: Allow networked computers to communicate, e.g. e-mail Support multiaccess, allow more than 1 user to access a computer at the same time. Share software and Data. Store data on the server etc. Share hardware. For example, networked printers. Manage printer queues and spooling. Organize user identification and passwords. Keep a log of who uses the network. Security The security of IT systems is important to protect users’ data and software. To help keep your system secure you should: backup files regularly, using the ancestral system; limit access using User Identification and Passwords; use locks, ID cards and guards to control access to room; put grills and security laminates on the windows of rooms; attach computers to desks using clamps; use firewalls to prevent access from external networks; use automatic virus checks. Social Implications INFORMATION TECHNOLOGY Revision Notes Lifestyle Lifestyle and leisure are affected by developments in IT. Domestic work has been made easier, this has made it easier for people to take part in education, employment and social activities outside the home. Home entertainment has been enriched by the use of TV, teletext, PC’s with games and CD-ROM’s, the Internet etc. Personal communications has been extended through the use of mobile phones, WWW and e-mail etc. On-Line shopping and banking are both possible from home. Users can buy and sell shares, transfer money etc. Cash-less society: magnetic stripe cards have led to a dramatic reduction in the use of cash. Employment As IT is introduced into the workplace an number of changes take place. Some jobs disappear and some skills are no longer needed. Some jobs are done in new ways. For example, typists have been replaced by wordprocessor operators. New jobs are created. For example, manufacturing computer hardware and writing software. New ways of organizing work arise. For example, teleworking. Teleworking helps the housebound to work, reduces traffic congestion, and cuts employers’ expenses by reducing the costs of running a central workplace. Privacy IT systems can store large amounts of information. Personal information may be stored by doctors, local authorities, schools, the police, banks, employers etc. These systems can improve the quality of services but your privacy may suffer. The Data Protection Act (1984) regulates the use of personal information. Users of personal information must register with the Data Protection registrar, and they must comply with the principles of good practice. Freedom IT can help track individuals which could affect their freedom of movement and association. Entry control systems using stripe cards to regulate access to many places, buildings and rooms. Electronic tagging of criminals, used to limit their freedom Transport control. IT systems can identify cars that are speeding and fine their owners automatically. Closed Circuit Television (CCTV) cameras record much of what happens in town centres. Telecommunications by fax, e-mail and telephone can be automatically monitored. Implications IT systems that track individuals’ movements and monitor their activities have many beneficial uses. They help prevent unauthorized access to buildings. Criminals are constrained and more easily caught. They can help prevent antisocial behaviour. However, the same IT systems that can protect individuals’ freedom of movement and association could also be used to enforce unreasonable levels of social control.