Chap 9
advertisement

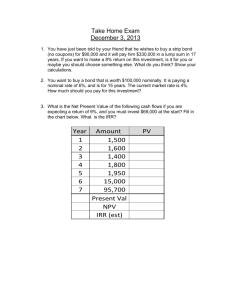
Chap 9: Economics of Cybersecurity Cybersecurity economics is a field that brings together elements of cybersecurity and economics to help decision-makers understand how people and organizations invest constrained resources in protecting their computer systems, networks, and data SE571 Security in Computing Dr. Ogara 2 Some questions worth asking • How much should an organization invest in cybersecurity to protect assets of a given value? • What is the likely impact of a security breach? • What are the costs and benefits of sharing information? SE571 Security in Computing Dr. Ogara 3 SE571 Security in Computing Dr. Ogara 4 How do you make a compelling argument about benefits of security to a business? Problem case You is getting data to support your must build a business case Business Case – A proposal that justifies the use of resources SE571 Security in Computing Dr. Ogara 5 a description of the problem or need to be addressed by the expenditure a list of possible solutions constraints on solving the problem a list of underlying assumptions analysis of each alternative, including risks, costs, and benefits a summary of why the proposed investment is good for the organization SE571 Security in Computing Dr. Ogara 6 Evaluating an existing or proposed investment in technology should be reported in several ways at once to form a “balanced scorecard” as follows: • customer view - address issues such as customer satisfaction • operational view - look at an organization’s core competencies • financial view - consider measures such as ROI • improvement view - assess how the investment will affect market leadership and added value SE571 Security in Computing Dr. Ogara 7 What is the right approach and how many companies use them to assess value of cybersecurity? • Net present value (18%) • Return on investment (ROI)(38%) • Internal rate of return (19%) (Source: CSI/FBI Computer Security Survey 2005 Report) There are practical problems with these approaches SE571 Security in Computing Dr. Ogara 8 Is the present value (PV) of the benefits minus the value of the initial investment Compares value of dollar today to future value while taking into account inflation Present value (PV) of an investment is the value today of a predicted future cash flow SE571 Security in Computing Dr. Ogara 9 It evaluates the effects of the proposed investment over the life of the project It provides a fair comparison for projects that turn profitable at different times in the future It uses a discount rate or opportunity cost, corresponding to the rate of return expected from an equivalent investment in capital markets SE571 Security in Computing Dr. Ogara 10 The discount rate reflects how much money an organization could make if it invested its money in the bank or a financial vehicle instead of in software technology. SE571 Security in Computing Dr. Ogara 11 Formula • Bt and Ct are the benefits and costs anticipated from the investment in each time period t • C0 is the initial investment, the discount rate (expected rate of return on investment) is k • n is the number of time periods over which the investment’s costs and benefits are considered • If NPV > 0, accept investment; NPV < 0 reject investment; NPV = 0, no added value SE571 Security in Computing Dr. Ogara 12 Observation: • Choice 1 is better because of higher NPV • NPV approach is sensitive to timing of the cash flows – the later the return the more the overall value is penalized SE571 Security in Computing Dr. Ogara 13 The internal rate of return (IRR) is derived from the net present value It is equal to the discount rate that makes the NPV equal to zero Example: • An IRR of 4% and discounted rate is 12% is bad – invest elsewhere • An IRR of 18% and discounted rate is 12%(less than IRR) is good SE571 Security in Computing Dr. Ogara 14 Are closely related to IRR and NPV ROI looks back at how a company or organization has performed, whereas NPV and IRR project likely future performance of new investments ROI = last period’s accounting profits (calculated from revenues and costs) /the cost of the investments required to generate those profits SE571 Security in Computing Dr. Ogara 15 Business case explains the ROI for an organization Revenue • Increased revenue due to increased trust in the web site Costs • • • • • • • Installation Operation Maintenance Cost savings e.g. fewer security breaches Cost avoidance e.g. fewer help desk calls Improved efficiency e.g. ability to handle more customers Effectiveness e.g. provide more services SE571 Security in Computing Dr. Ogara 16 Compliance • Failure to implement regulatory practices may lead to fines, imprisonment and bad publicity • Failure to comply with agreed standards may lead to lost business or competitive advantage Risks • Failure to implement proposed security measures may include: loss of market share, loss of productivity and legal exposure SE571 Security in Computing Dr. Ogara 17 Understanding the nature of the cybersecurity threat requires knowing at least the following elements number and types of assets needing protection number and types of vulnerabilities that exist in a system number and types of likely threats to a system SE571 Security in Computing Dr. Ogara 18 National and global data • Address both national and international concerns Enterprise data • How do enterprises apply security technologies against attacks and security breaches • How do enterprises balance security costs with other economic demands Technology data • Describes the threats against core infrastructure technologies SE571 Security in Computing Dr. Ogara 19 Accuracy • Close to actual values Consistency • Data gathered under same conditions • Reporting organizations apply same rules Timeliness • Current – reflect existing conditions Reliability • Credible sources SE571 Security in Computing Dr. Ogara 20 CSI/FBI Computer Crime and Security Survey • Administered by Computer Security Institute and FBI (Ca) Australian Computer Crime and Security Survey • Examines Australia’s private and public industry cybersecurity threats, records the number of cyber incidents, and attempts to raise awareness of security issues and effective methods of attack prevention Deloitte Touché Tohmatsu Global Security Survey • Focus on security practices of major global financial institutions SE571 Security in Computing Dr. Ogara 21 Ernst and Young Global Information Security Survey • Surveys companies worldwide Internet Crime Complaint Center (IC3) • Collaborative effort of FBI and National White Collar Crime Center • PProvides information to national, state, and local law enforcement agencies that are battling Internet crime The Imation Data Protection Survey • Managed by Imation Corporation • Investigates how small and mid-size U.S. companies conduct data backup, protection, and recovery. SE571 Security in Computing Dr. Ogara 22 Currently most reported data are derived from convenient surveys rather than carefully sampled populations There is no consistency in terminology or counting rules from one survey to another Thus makes it difficult to generalize the meaning of reported Dr.data and trends SE571 Security in Computing Ogara 23 Classification of attack types • Each survey measures different things e.g. one survey may report decrease in attacks of all types while another may report an increase Types of respondents • Self-selected and not representative to a larger population SE571 Security in Computing Dr. Ogara 24 Comparability of categories • No standards in defining, tracking and reporting security incidents and attacks • Data are characteristically different and answers are based on opinions, interpretations and perception • Example; “electronic attacks” (Australian Survey); “unauthorized use of computer systems” (CSI/FBI); accidental/malicious security incidence” (DTI Information Security Breaches Survey) SE571 Security in Computing Dr. Ogara 25 Sources of attack • Rate of insider attack remained constant in 2005 (Australian Survey) • Rate is rising (Deloitte Survey) Financial impact • Differences in nature of losses SE571 Security in Computing Dr. Ogara 26 Yes, for example; • Viruses, Trojan horses and worms pose serious threat • Most business concerned about inside attacks and abuse of access • Formal security policies and incidence response plans are important • Lack of education and training are major obstacle SE571 Security in Computing Dr. Ogara 27 Conclusion • The convenience surveys are therefore a good start, but for serious, useful analysis, we need statistically valid surveys administered to the same population over a period of time SE571 Security in Computing Dr. Ogara 28 Department Security of Justice and Homeland • Administered the National Computer Security Survey in 2006 • Survey was sent to thousands of businesses across 37 industry sectors • intent is to provide “national and industry-level estimates of the prevalence of computer security incidents • Enable businesses to benchmark themselves with more credible data, SE571 Security in Computing Dr. Ogara 29 The survey included the following questions • The nature and extent of computer security incidents • Monetary costs and other consequences of these incidents • Incident details such as types of offenders and reporting to authorities • Computer security measures used by companies SE571 Security in Computing Dr. Ogara 30 Transferring models • Apply standard approaches in a certain • • • • discipline to solve problems in another discipline Examples: Gordon and Loeb Model Campbell et al Model Gal-Or and Ghose Model SE571 Security in Computing Dr. Ogara 31 Gordon and Loeb Model • Uses accounting principles. • They consider 3 parameters: the loss conditioned on a breach’s occurring, the probability of a threat’s occurring, and the vulnerability SE571 Security in Computing Dr. Ogara 32 Campbell et al Model • Models incorporate the “snowball effect accruing from the resultant loss of market share and stock market value” • Nature of the breach affects the result • Unauthorized access to confidential data produces highly significant negative market reaction • Breach involving no confidential information produces no significant reaction SE571 Security in Computing Dr. Ogara 33 Gal-Or and Ghose Model • Apply game theory • Model explains costs and benefits of sharing information about security breaches • In general, there are strong incentives to share breach information, and the incentives become stronger as the firm size, industry size, and amount of competition grow SE571 Security in Computing Dr. Ogara 34 Some researchers look at other disciplines to see how human aspects of decision making can be woven in economic models • Anthropology • Sociology • Psychology SE571 Security in Computing Dr. Ogara 35 Framing the issue Group behavior Organizational culture SE571 Security in Computing Dr. Ogara 36 The way a problem is framed can make a big difference in the choices people make Example: • Cybersecurity investment choices are portrayed as risk avoidance or loss avoidance Vs • Cybersecurity investment choices are described as opportunities to establish a competitive edge as a totally trustworthy company SE571 Security in Computing Dr. Ogara 37 Driven by group identity which leads to team reasoning Decision-makers do not act alone (are NOT driven by rational choice alone) SE571 Security in Computing Dr. Ogara 38 They act as members of teams, organizations, or business sectors Individuals who are part of a team make decisions that meet collective objectives rather than individual ones SE571 Security in Computing Dr. Ogara 39 The number and nature of encounters among people also affects a decision People are willing to pay more for goods and services they trust Interpersonal relationships create and enhance trust SE571 Security in Computing Dr. Ogara 40 Trust has an effect on both the beliefs and the norms of others In cybersecurity, trust is an interpersonal or social relationship that merits special attention SE571 Security in Computing Dr. Ogara 41 Driven by group identity which leads to team reasoning Decision-makers do not act alone (are NOT driven by rational choice alone) SE571 Security in Computing Dr. Ogara 42 They act as members of teams, organizations, or business sectors Individuals who are part of a team make decisions that meet collective objectives rather than individual ones SE571 Security in Computing Dr. Ogara 43 Dimensions of Organizational Culture (Hofstede and Hofstede 2005) SE571 Security in Computing Dr. Ogara 44 Symbols are the words, gestures, pictures and objects that carry specific meanings for a group of people using them to communicate e.g. PKI, IPSEC, and cryptographic algorithms jargons as corporate security group’s culture Heroes of a culture are those people whose behaviors are highly prized, serving as role models for the others in the group e.g. ACM or IEEE Fellows SE571 Security in Computing Dr. Ogara 45 Rituals are activities performed by all the group’s members that are socially essential but not necessary to the business e.g. group meetings to introduce new members are often ways of teaching the language and symbols to newcomers Practices – consist of the above three characteristics SE571 Security in Computing Dr. Ogara 46 Values lie at the culture’s core. We can think of values as “broad tendencies to prefer certain states of affairs over others If developers, managers, or customers do not value security, they will neither adopt secure practices nor buy secure products SE571 Security in Computing Dr. Ogara 47 Organizations cultures can be characterized by where they fit along six dimensions The dimensions are polar opposite Most organizations fall somewhere in the middle These dimensions affect an organization’s cybersecurity economics These dimensions reflect the underlying organizational values and hence the type of cybersecurity investment choices SE571 Security in Computing Dr. Ogara 48 1. 2. 3. 4. 5. 6. Process versus results Employee versus job Parochial versus professional Open versus closed Loose versus tight control Normative versus pragmatic SE571 Security in Computing Dr. Ogara 49 SE571 Security in Computing Dr. Ogara 50