CPE_562_Second
advertisement
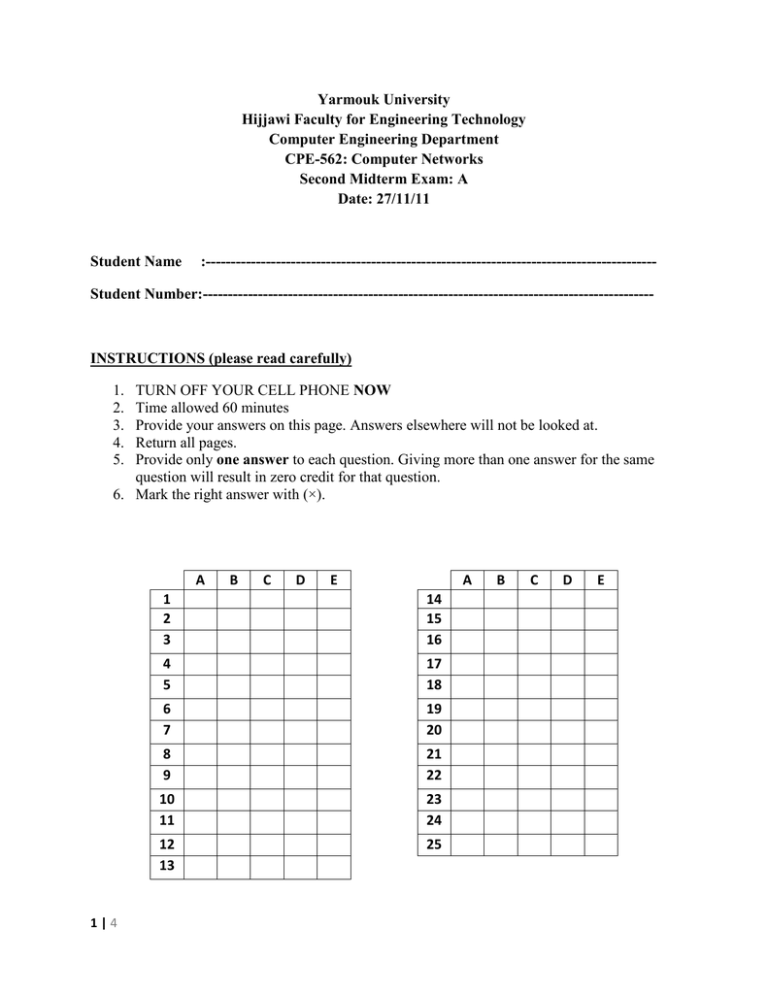
Yarmouk University Hijjawi Faculty for Engineering Technology Computer Engineering Department CPE-562: Computer Networks Second Midterm Exam: A Date: 27/11/11 Student Name :------------------------------------------------------------------------------------------ Student Number:------------------------------------------------------------------------------------------ INSTRUCTIONS (please read carefully) 1. 2. 3. 4. 5. TURN OFF YOUR CELL PHONE NOW Time allowed 60 minutes Provide your answers on this page. Answers elsewhere will not be looked at. Return all pages. Provide only one answer to each question. Giving more than one answer for the same question will result in zero credit for that question. 6. Mark the right answer with (×). A 1|4 B C D E A 1 2 3 14 15 16 4 5 17 18 6 7 19 20 8 9 21 22 10 11 23 24 12 13 25 B C D E 1. 2. 3. 4. 2|4 Which of the following statements is wrong? a. Skype is inherently a P2P application b. Skype is a public application-layer protocol c. Skype uses a hierarchical overlay with super nodes d. Skype Index maps usernames to IP addresses e. Skype peers communicate through NATs via relay In BitTorent, a peer pulls chunks from _________ trading partners. a. one b. two c. three d. four e. five Which of the following choices has correct statements? a. The alternating-bit protocol (stop-and-wait protocol) is the same as the Go-back-N protocol with a sender and a receiver size of 1. The alternating-bit protocol (stop-andwait protocol) is the same as the SelectiveRepeat protocol with a sender and a receiver size of 1. b. The alternating-bit protocol (stop-and-wait protocol) is not the same as the Go-back-N protocol with a sender and a receiver size of 1. The alternating-bit protocol (stop-andwait protocol) is not the same as the Selective-Repeat protocol with a sender and a receiver size of 1. c. The alternating-bit protocol (stop-and-wait protocol) is the same as the Go-back-N protocol with a sender and a receiver size of 1. The alternating-bit protocol (stop-andwait protocol) is not the same as the Selective-Repeat protocol with a sender and a receiver size of 1. d. The alternating-bit protocol (stop-and-wait protocol) is not the same as the Go-back-N protocol with a sender and a receiver size of 1. The alternating-bit protocol (stop-andwait protocol) is the same as the SelectiveRepeat protocol with a sender and a receiver size of 1. e. None of the given choices Suppose that the ASCII characters BDLZPXWKJANCSPUGVTKEG9T represent the application data (message) of a UDP segment. What value will the Length field of this segment have? a. 9 b. 23 c. 31 d. 248 e. Impossible to know from the given information 5. 6. 7. 8. 9. Consider a fully-connected mesh overlay network with N peers. How many messages are sent to know the immediate successor of a key? a. 1 b. N – 1 c. N d. N2 e. 𝑙𝑜𝑔2𝑁 Consider Selective-Repeat mechanism. Suppose the sender sends pkt 0. The receiver receives pkt 0 correctly and sends ACK 0, which is correctly received by the sender. Suppose then that the receiver receives pkt 1, pkt 2, pkt 3, pkt 5. Which of the following statements is correct? a. pkt 1, pkt 2, pkt 3 will be buffered. pkt 5 will be discarded b. pkt 1, pkt 2, pkt 3 will be discarded. pkt 5 will be buffered c. pkt 1, pkt 2, pkt 3, pkt 5 will be buffered d. pkt 1, pkt 2, pkt 3 will be delivered. pkt 5 will be discarded e. pkt 1, pkt 2, pkt 3 will be delivered. pkt 5 will be buffered What does SNMP stand for? a. Simple Network Management Protocol b. Source Network Message Protocol c. Service Network Management Point d. Service Network Message Provider e. Service Node Mail Protocol In BitTorent, how many “optimistically unchoked” peers does a peer have? a. 1 b. 2 c. 3 d. 4 e. 5 Which of the following statements is correct? a. In connectionless demultiplexing, IP datagrams with different source IP addresses and/or source port numbers are directed to same socket b. In connectionless demultiplexing, IP datagrams with different source IP addresses and/or source port numbers are directed to different sockets c. In connection-oriented demultiplexing, web servers use one socket for all connecting clients d. In connection-oriented demultiplexing, receiving host can direct segments to the appropriate socket using source and destination port numbers e. Multiplexing at the receiving host works by delivering received segments to the correct socket 10. Consider distributing a file of 10 Gbits to 100 peers. The server has an upload rate of 20 Mbps, and each peer has a download rate of 1 Mbps and an upload rate of 200 kbps. What is the minimum distribution time for client-server distribution? a. 10,000 s b. 5,000 s c. 50,000 s d. 100,000 s e. 60,000 s 11. The UDP segment header consists of _________ octets. a. 4 b. 8 c. 32 d. 64 e. Variable number of octets as it may contain options 12. Which of the following services does UDP provide? a. Bandwidth guarantees b. Flow control c. Connection setup d. Congestion control e. Best-effort 13. Suppose you installed and compiled the Java programs TCPClient and UDPClient on one host and TCPServer and UDPServer on another host. Which of the following choices has correct statements? a. It is ok. To run UDPClient before you run UDPServer. It is ok. To run TCPClient before you run TCPServer. b. It is not ok. To run UDPClient before you run UDPServer. It is not ok. To run TCPClient before you run TCPServer. c. It is ok. To run UDPClient before you run UDPServer. It is not ok. To run TCPClient before you run TCPServer. d. It is not ok. To run UDPClient before you run UDPServer. It is ok. To run TCPClient before you run TCPServer. e. It is ok. If you use different port numbers for the client and server sides. 14. Consider DHT with n = 4 and peers 1, 3, 4, 5, 8, 10, 12, 14. To which peer is the key 7 assigned? a. 1 b. 5 c. 8 d. 14 e. 15 15. Which of the following may represent a valid UDP port number? a. 98456 b. 81002 c. 85328 d. 74105 e. 61970 3|4 16. Consider Go-back-N mechanism. Suppose the sender sends pkt 0. The receiver receives pkt 0 correctly and sends ACK 0, which is correctly received by the sender. Suppose then that the receiver receives pkt 1, pkt 2, pkt 4, pkt 5. Which of the following statements is correct? a. pkt 1, pkt 2, pkt 4, pkt 5 will be delivered b. pkt 1, pkt 2, pkt 4, pkt 5 will be discarded c. pkt 1, pkt 2 will be delivered. pkt 4, pkt 5 will be discarded d. pkt 1, pkt 2 will be discarded. pkt 4, pkt 5 will be delivered e. ACK5 will be sent 17. Consider peer churn in a “Circular DHT”. Which of the following statements is correct? a. A peer does not need to know the IP address of any other peer b. Each peer needs to know the IP address of its immediate successor only c. Each peer needs to know the IP address of its second successor only d. Each peer needs to know the IP addresses of its immediate and second successor only e. Each peer needs to know the IP address of every other peer 18. Consider Go-back-N mechanism. What is the maximum window size if 5-bit sequence numbers are used? a. 31 b. 32 c. 15 d. 16 e. 4 19. Comparing “Circular DHT” and “Circular DHT with shortcuts”. Which of the following statements is correct? a. A peer has fewer neighbors in “Circular DHT” but fewer query messages are sent b. A peer has fewer neighbors in “Circular DHT with shortcuts” but fewer query messages are sent c. A peer has more neighbors in “Circular DHT” and fewer query messages are sent d. A peer has more neighbors in “Circular DHT with shortcuts” and fewer query messages are sent e. “Circular DHT” and “Circular DHT with shortcuts” have the same performance in terms of the number of neighbors and number of sent query messages 20. Consider distributing a file of 10 Gbits to 100 peers. The server has an upload rate of 20 Mbps, and each peer has a download rate of 1 Mbps and an upload rate of 200 kbps. What is the minimum distribution time for P2P distribution? a. 10,000 s b. 500 s c. 25,000 s d. 40,000 s e. 35,500 s 21. Calculate the checksum for the following two 16-bit values: 1000 0001 1010 1011 1101 1100 0000 1010 a. 1010 0010 0100 1010 b. 0101 1101 1011 0110 c. 1010 0010 0100 1001 d. 1001 0011 0100 0111 e. 0110 1100 1011 1000 22. Consider the stop-and-wait mechanism. Suppose that the sender sends pkt 1, which is correctly received by the receiver. The receiver sends ACK1 which is then lost in the way. What happens next? a. The receiver resends ACK1 b. The receiver sends ACK0 c. The sender continues normally by sending pkt 0 d. The sender times out and sends pkt 0 e. The sender times out and resends pkt 1 23. Which of the following statements is wrong? a. In socket programming with UDP, sender explicitly attaches IP address and port of destination to each packet b. In socket programming with UDP, server must extract IP address and port of sender from received packet c. In socket programming with TCP, client TCP establishes connection to server TCP d. In socket programming with TCP, client creates client-local datagram socket e. In socket programming with TCP, both input and output streams are attached to sockets 24. Consider the stop-and-wait mechanism. Suppose a link of 500 Mbps between the sender and the receiver, 5 ms propagation delay, and 2000-byte packet. What is the utilization at the sender? a. 0.0032 b. 0.0064 c. 0.0004 d. 0.0008 e. 0.017 4|4 25. Which of the following choices has correct statements? a. Network layer provides logical communication between hosts. Transport layer provides logical communication between processes b. Network layer provides logical communication between processes. Transport layer provides logical communication between hosts c. Network layer provides physical communication between hosts. Transport layer provides physical communication between processes d. Network layer provides physical communication between processes. Transport layer provides physical communication between hosts e. Network layer provides physical communication between hosts. Transport layer provides logical communication between processes