U.S. Bank Payment Solutions
advertisement

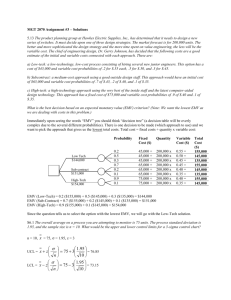
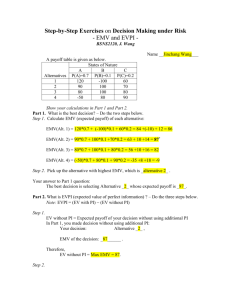
PAYMENT SOLUTIONS An Introduction to EMV Presented to: Government Finance Officers Association of South Carolina Date: May 4, 2015 First: The Proverbial Question Issuers PAYMENT SOLUTIONS Acquirers 2 The Race is On: Agenda Alphabet Soup: Definitions Chip Cards, EMV, NFC EMV: What is Driving Adoption Statistics, Fraud, Compliance, Innovation Encryption and Tokenization PAYMENT SOLUTIONS 3 Alphabet Soup: Definitions Chip Card EMV Smart Card NFC Chip + PIN PAYMENT SOLUTIONS 4 The Card Came First A chip card is a device that includes a secure, embedded integrated circuit chip (ICC) Invented in 1977 by Honeywell Bull Performs functions that validate, store, and encrypt data Data is more secure on a chip-embedded card that utilizes dynamic authentication rather than on a static mag-stripe card Mag-stripe card can be copied (“skimmed”) Chip technology combats counterfeiting by assigning a dynamic value for each transaction and preventing copying PAYMENT SOLUTIONS 5 Form Factors Contact 1. 2. 3. Chip is embedded in a card A contact card is inserted into a smart card reader The contact points on the chip make contact with the card reader Contactless or Near Field Communication (NFC) • • • The chip may be embedded in cards, key fobs, stickers, mobile phones, tablets, Apple Pay devices etc. A contactless chip requires close proximity to a reader (“tap and go”) Both the chip and the reader have an antenna and they use an RF (radio frequency) signal to communicate PAYMENT SOLUTIONS 6 The Standard Followed EMV was established in 1994 by Europay, MasterCard and Visa EMVCo’s primary purpose is to define a global standard for credit and debit payment cards based on chip card technology. Cards can be Contact or Contactless Four main functions: Card authentication to protect against counterfeit cards Cardholder verification to protect against lost/stolen cards Terminal authentication to prevent against “Trojan Horse” hacks Transaction authorization using issuer-defined rules PAYMENT SOLUTIONS 7 EMV Authentication and Verification Authentication and Authorization Methods • Online requires the transaction to be sent online for the issuer to authenticate the card and authorize the transaction • Offline is done between the chip card and terminal Cardholder Verification Methods (CVMs): • None (usually used for low value transactions) • Offline PIN (entered and stored PIN are compared offline) Online PIN (PIN is validated online – like PIN debit) Signature Verification (requires physical signature comparison) Visa and MasterCard mandate global interoperability: POS solutions must be able to support all authentication & verification methods Mexico chip card will prompt for signature; UK for PIN PAYMENT SOLUTIONS 8 Innovation Could Win the Race NFC (Near Field Communications) is a radiobased interaction protocol compatible with contactless payment standards NFC chips are embedded in mobile phones (Apple Pay) and allow the phones to act as card The “promise” of Apple Pay is driving innovation and EMV adoption PAYMENT SOLUTIONS 9 EMV: What is Driving Adoption? Statistics Fraud Compliance Innovation Globalization PAYMENT SOLUTIONS 10 EMV by the Numbers Worldwide Adoption 1.5 Billion payment cards* 20 Million POS terminals* 40% of cards and 70% of terminals are EMV U.S. Adoption – What it will mean financially 15 million point-of-sale devices = $6.75 billion to replace 360,000 ATMs = $500 million to upgrade (target date is 10/2016) 609.8 million credit cards & 520 million debit cards = $1.4 billion to reissue (Cost of mag-stripe card = 15 cents vs. EMV card = $2 - $4) Hence the U.S. “Chicken & Egg” conundrum! Unlike most countries where banks own the terminal assets, the U.S. will require merchants to make the investment PAYMENT SOLUTIONS 11 *As of 2011 Fraud Migrates to U.S. 84.4% of cards 94.4% of terminals 14.5% of cards 68.1% of terminals 28.2% of cards 51.4% of terminals 20.6% of cards 75.9% of terminals 41.1% of cards 76.7% of terminals PAYMENT SOLUTIONS 12 Fraud Reduction Stats: UK Example Fraud on debit and credit cards fell by more than 25% from 2008 to 2010 Counterfeit card fraud —skimming and cloning—fell by over half Fraud on lost and stolen cards is at their lowest levels in 10 years Source: The UK Card Association PAYMENT SOLUTIONS 13 Key EMV dates from Card Brands October 2012: TECH Innovation Program (TIP) - PCI validation relief for Level 1 and Level 2 merchants that adopt dual-interfaced solutions in any year that at least 75% of the merchant transactions originate from a chipenabled terminal Note: must be capable of actually processing EMV cards and NFC contactless payments; merchants cannot just install “EMV ready” equipment. . . .so, not really happening! April 2013: Acquirer Chip Processing Mandate - Acquirers and processors must demonstrate the ability to process EMV transactions and NFC contactless payments October 2015: Liability Shift from Issuer to Merchant - Merchants of any size will be liable for domestic and cross-border counterfeit fraud committed at the point of sale if they are not using a compliant EMV & NFC POS solution (Automated Fuel merchant liability shift in 2017) © 2012 VeriFone Systems, Inc. PAYMENT SOLUTIONS 14 “Liability Shift” will Drive Adoption A non-compliant merchant is liable for fraud that occurs on any chip card used on a magnetic swipe terminal. A non-compliant issuer is liable for fraud that occurs on any magnetic stripe card used on a chip card-enabled terminal. PAYMENT SOLUTIONS 15 What is “Liability Shift” Liability for the chargeback loss shifts to whichever party hasn’t upgraded to chip, if the use of such a device could have prevented the fraud from occurring Issuers that have not migrated to EMV will be liable for fraud at EMV devices, including transactions using listed card numbers Acquirers that have not placed EMV + PIN devices will be liable for fraud on chip cards, including transactions authorized online by the Issuer Merchants can benefit from liability shift just by installing contact EMV terminals. No impact on the customer Fraud impacted by the Liability Shift is called “Designated Card Present Fraud” The following fraud types are excluded from the liability shift: Card Not Present Fraud Account Takeover Fraudulent Application Source: Oberthur 2010 and “Overview of EMV Chip Impacts on Chargebacks” VISA March, 2011 PAYMENT SOLUTIONS 16 Magnetic Stripe vs EMV Transaction Magnetic Stripe Transaction Card is swiped, inserted, or dipped, and is returned to cardholder after magnetic stripe data has been read There is no interaction between card and terminal after magnetic stripe has been read Card does not generate a cryptogram Online request message contains no EMVspecific data Host does not perform any EMV-related processing Online response message contains no EMV-specific data There is interaction between card and terminal at the end of the transaction PAYMENT SOLUTIONS EMV Transaction Card must be inserted and remain in the terminal for the duration of the transaction Data is exchanged between card and terminal to initiate the transaction Chip card generates a unique cryptogram which is sent to the host for verification Additional EMV-specific data is in the online request message Additional processing is required by host to verify request cryptogram, generate response cryptogram, and interrogate additional EMV-specific fields in the request message Additional EMV-specific data is in the online response message Data is exchanged between card and terminal at the end of the transaction 17 Elavon Solutions for EMV PAYMENT SOLUTIONS 18 EMV Terminals: VeriFone VX Evolution VX820 VX520 • • • • • • Hand-Over Design PAYMENT SOLUTIONS • Customer Facing Countertop Dual Comm Internal PIN pad MSR EMV NFC • • • • EMV 19 NFC PIN pad Vx520 MSR EMV NFC EMV Terminals: Ingenico Telium2 iCT250 iPP320 • Countertop • Dual Comm • Internal PIN pad • MSR • EMV • NFC • Customer Facing PIN pad • iCT220 or iCT250 • MSR • EMV • NFC iWL250G • Portable - GPRS • Internal PIN pad • MSR • EMV • NFC • 3G Technology PAYMENT SOLUTIONS 20 iCT220 • Countertop • Dual Comm • Internal PIN pad • MSR • EMV iCT250 EMV Magstripe Contactless Backlit 19 key 18+ LPS printer Dual IP & Dial Dual Processor PAYMENT SOLUTIONS 21 Cable Management Small Footprint NFC Sharp Color Display Privacy Shield iPP320 Countertop PIN Pad EMV Embedded Contactless Connects to Telium Countertop Line PAYMENT SOLUTIONS 22 iWL250 Small Footprint Lightweight Charging & Comms Base 30 LPS Thermal Printer 25mm & 40mm Paper Roll Option Contactless 3G Wireless GPRS PAYMENT SOLUTIONS Dynamic SIM 30 LPS Printer Contactless 23 Smart Card Li-Ion Battery Lightweight Conclusion PAYMENT SOLUTIONS 24 Points to Remember EMV is a standard that dictates the interaction between a smart (chip) “card” and a POS payment device The “chip” stores encryption data that is used during the transaction to prove the card is authentic; it prevents cloning EMV chips can be either contact or contactless and are read & write capable NFC (Near Field Communications) is a radio-based contactless interaction protocol that is driving interest in EMV adoption The Card Brands have announced EMV incentives (carrots and sticks) that encourage issuers, acquirers, and merchants to adopt EMV © 2012 VeriFone Systems, Inc. PAYMENT SOLUTIONS 25 EMV Benefits All Parties MERCHANT • Fewer fraud-related chargebacks due to stolen cards/skimming • Increase in international customer satisfaction BENEFITS ISSUER • Fraud reduction • Global interoperability • Mobile payments facilitation CARDHOLDER • Peace of Mind (fraud reduction) • Never lose sight of their card • Global interoperability P A Y M E 26 NT SOLUTIONS 26 PCI – Tokenization - Encryption What is the difference between Security and PCI? PCI-DSS compliance is one aspect of an overall security program but on its own cannot prevent a data breach. Security measures such as encryption and tokenization provide additional layers of protection as part of a security program. What is “Point-to Point” vs “End-to-End” Encryption? They are really the same and have been used interchangeably. Since P2PE certification is available and Visa has announced their encryption program, some distinction is made in the market. Point to Point refers to encryption at the time of the swipe and decryption at a gateway of payment processor. End-to-End refers to encryption at the time of the swipe and decryption at the furthest end point in the payment processing stream, i.e. the payment brands data center. What is Tokenization vs Encryption? Encryption is generally used in card-present situations while tokenization is generally used in card not present scenarios like “card on file” and recurring billing. Encryption scrambles a card number so that the data is not usable to thieves. The card number can only be decrypted by the holder of the key. Tokenization is an ALIAS or “token” of the card number. If a customer is using encryption and/or tokenization do they have to be PCI compliant? The short answer is YES utilizing encryption and/or tokenization does not remove the requirement for PCI-DSS compliance. However, depending on the solution implemented, a customer could experience reduced effort, scope and/or cost when they do complete their annual PCI assessment PAYMENT SOLUTIONS 27 Your EMV Call to Action: Don’t Wait Read and research to keep up with EMV and NFC trends • http://www.smartcardalliance.org/ • http://www.emvco.com/ • http://www.cscu.net/index.aspx?CategoryID=294 • http://pymnts.com PAYMENT SOLUTIONS 28 EMV – Action Required Effective October 1, 2015, a date that has been determined by the credit card associations (MasterCard/VISA) if your business accepts and processes a counterfeit transaction from an EMV card on a non-EMV enabled terminal, the liability for that transaction is yours. PAYMENT SOLUTIONS 29 Thank You! Brad Hench Regional Sales Manager US Bank Merchant Solutions 678-731-4419 Bradford.hench@usbank.com Paul Anatrella Vice President & Relationship Manager U.S. Bank 704-335-2825 Paul.anatrella@usbank.com PAYMENT SOLUTIONS 30