Digital Citizenship Project
advertisement

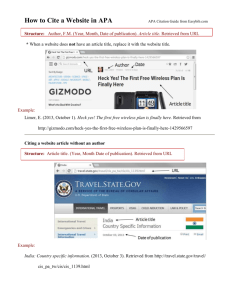
Digital Citizenship Project Elle Wagner ED 505 Netiquette on Social Media Sites Netiquette: the actions that are socially and morally acceptable for an online or digital setting or situation Do Don’t Be professional Post illegal activity Share accurate information Bully others Respect Privacy Trash your teacher Show love Post confidential information Copyright : the exclusive right to make copies, license, and otherwise exploit a literary, musical, or artistic work, whether printed, audio, or video. • Law • These laws protect creators from other people claiming that the creators work is their own without paying for it. Fair Use: The condition under which you can use material that is copyrighted by someone else without paying royalties • • • • • • Law You do not have to ask permission to use someone else’s work when in certain circumstances Print: articles, chapters, or pages of text can be printed and copied. These do not replace text books or other teaching materials. • Poetry: Less than 250 words or an excerpt of not more than 250 words Music: Can copy sheet music (not more than 10% of the whole work) Video: must be discarded after 45 days Photographs: One copy is allowed to be made for each student. Note copyright. Plagiarism • What is it? Using someone else’s work as your own without citing it. • How do I avoid it? Use quotation marks when you use someone else’s words exactly. Cite the source that you gained your information from. • How can teachers stop plagiarism in student work? Teachers can use www.turnitin.com or www.grammarly.com/Plagiarism_Check when their students are turning in their work. These websites run plagiarism checks. Safety on the Internet Safety on the Internet Cont… Internet Safety Cont…. Cyberstalking: using any sort of communication device to stalk someone. • Do not share personal information in a public forum • Do not use your real name as a screen name or email address • Block users that you may suspect on your email or from viewing your Facebook • Contact local police in appropriate cases Safety on your computer • Viruses- a computer program that works like a virus, infecting your computer. – Prevent them by: • Have a virus scanning program • Do not open any files from unknown emails • Do not download from strangers • Phishing- a technique used to gain personal information – Prevent phishing by: • Look for misspelling of words or bad grammar • Be cautious when there is a strange URL – @ symbols in the URL – “O’s” that are replaced with zeros • Trojan Horse- similar to a virus; usually pretends to be ridding your computer of viruses – Prevent trojan horses by: • Do not open anything from an unknown source • Do not click on any unknown links • Worms- Similar to a virus; cause by security problems on the targeted computer – Prevent worms by: • • Have a security system installed Do not open unexpected email. Sources • Buck, S. (2012, September 4). 12 Things Students Should Never Do on Social Media. Retrieved September 5, 2012, from Mashable Lifestyle website: http://mashable.com/2012/09/04/ students-social-media-warnings/ • Social Media Netiquette. (n.d.). Retrieved September 5, 2012, from Netiquette website: http://www.networketiquette.net/socmed.htm • McWhinney, J. E. (2010, May 3). Identity Theft: How To Avoid It. Retrieved September 5, 2012, from Investopedia website: http://www.investopedia.com/articles/pf/05/051805.asp#axzz25e79pkO0 • Reputation Management. (n.d.). Retrieved September 5, 2012, from Wikipedia website: http://en.wikipedia.org/wiki/Reputation_management • Dicker, R. (2011, July 9). How to Create a Safe, Memorable Online Password. Retrieved September 5, 2012, from Daily Finance website: http://www.dailyfinance.com/2011/07/09/ how-to-create-a-safe-memorable-online-password/ • Aftab, P. (n.d.). Stop Cyberbullying: Prevention. Retrieved September 5, 2012, from Stop Byberbullying website: http://www.stopcyberbullying.org/tweens/take_5.html • CyberGuards. (2012). CyberStalking. Retrieved September 5, 2012, from CyberGuards website: http://www.cyberguards.com/CyberStalking.html • McAfee. (2012). Anti-Virus Tips. Retrieved September 5, 2012, from McAfee website: http://home.mcafee.com/virusinfo/anti-virustips?ctst=1 • Trojan Horse. (2012). Retrieved September 5, 2012, from Webopedia website: http://www.webopedia.com/ TERM/T/Trojan_horse.html • Kay, R. (2004, January 19). Quick Study: Phishing. Retrieved September 5, 2012, from ComputerWorld website: http://www.computerworld.com/s/article/89096/Phishing • Computer Worm. (n.d.). Retrieved September 5, 2012, from Wikipedia website: http://en.wikipedia.org/ wiki/Computer_worm#Protecting_against_dangerous_computer_worms Sources • Glassbergen, R. (2008, September 23). [Cartoon]. Retrieved September 5, 2012, from Linda's Computer Stop website: http://personal-computer-tutor.com/abc/humor.htm • Spielman, M. (n.d.). [Cartoon]. Retrieved September 5, 2012, from LSU.edu website: http://www.lsu.edu/departments/safety/2008campaign.shtml • Staford University Libraries. (2010). Copyright and Fair Use. Retrieved September 5, 2012, from SU Lair website: http://fairuse.stanford.edu/Copyright_and_Fair_Use_Overview/chapter7/7-b.html