remote_access_applications
advertisement

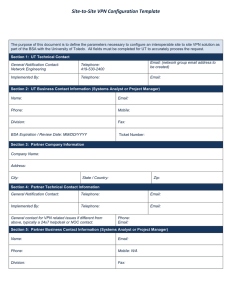
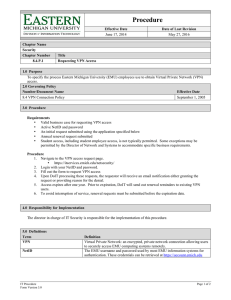
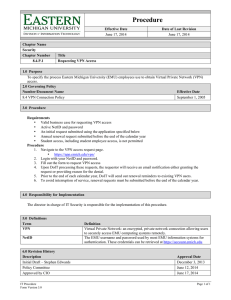
Running Head: REMOTE ACCESS APPLICATIONS Remote Access Applications Name: Course: Course code: Institution: Date: 1 REMOTE ACCESS APPLICATIONS 2 Remote Access Applications Remote access applications allows users to share information and data from one computer device to another and also the individuals can remotely get access to their computers or others within the organization. Many organizations have reformed the manner in which they operate their businesses since they are targeting an increasingly mobile and a global workforce. They therefore accessing more cost effective and secure remote access become highly crucial in order to extend their networks to clients, business partners, branch offices and/or telecommuters. Virtual Private Network is a secure connection created towards or from a computer device or a network utilizing resilient restrictions and encryption methods for private access to data. This enables the data to be secure guarding it against various other users that operate within this underlying network, since it could be a publicly accessed network such as the internet (Stewart, J. M. 2010).. They are widely used due to their robust (encrypted) form and fast interface. Common VPNs used are; Site-to-site VPN This type of VPN implements security by enabling various organizational sites to liaise together and forming a VPN from their individual real network. Encryption routing and decryption for site to site VPN is carried out by the routers on separate ends. Pont-to-Point Tunneling Protocol This is the VPN mostly used since it allows remote user with authorization to access the VPN network through an internet connection after which using password authentication, they can sign into the network. Apart from these two, other types are IPsec, SSL (Secure Socket Layer), MPLS (MultiProtocol Label Switching), among other types. Another type of a Remote Access Application is the Dial-up networking. This utilizes telecommunication providers’ services to make temporary dial-up connections by the remote access users to the physical access on the remote access REMOTE ACCESS APPLICATIONS 3 server. These remote access applications are however prone to access control threats such as DoS and DDoS attacks. Such access could be through malware sent to unsuspecting personnel to collect information and data when the servers are under attack from unwanted traffic (Stewart, J. M. 2010). REMOTE ACCESS APPLICATIONS 4 References Stewart, J. M. (2010). Network security firewalls & VPNs. Mississauga, Ont: Jones & Bartlett Learning.