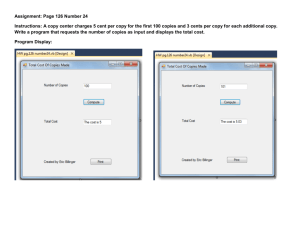
History of Operating Systems - Ritz Hospitality Management College
advertisement

UNIT 1 Computing Devices,Software and Operating System Computer and IT application Page 1 What are the Advantage and Disadvantage of Networking? Advantage of Networking 1. File Sharing: Networks offer a quick and easy way to share files directly. Instead of using a disk or USB key to carry files from one computer or office to another, we can share files directly using a network. 2. Software Cost and Management: Many popular software products are available for networks at a substantial savings in comparison to buying individually licensed copied for all of our computers. We can also load software on only the file server which saves time compared to installing and tracking files on independent computers. Upgrades are also easier because changes only have to be done once on the file server instead of on individual workstations. 3. Security: Specific directories can be password protected to limit access to authorized users. Also, files and programs on a network can be designated as "copy inhibit" so we don’t have to worry about the illegal copying of programs. 4. Resource Sharing: All computers in the network can share resources such as printers, fax machines, modems, and scanners. 5. Communication: Even outside of the internet, those on the network can communicate with each other via electronic mail over the network system. When connected to the internet, network users can communicate with people around the world via the network. 6. Flexible Access: Networks allow their users to access files from computers throughout the network. This means that a user can begin work on a project on one computer and finish up on another. Multiple users can also collaborate on the same project through the network. Disadvantage of networking 1. Security Issues One of the major drawbacks of computer networks is the security issues involved. If a computer is a standalone, physical access becomes necessary for any kind of data theft. However, if a computer is on a network, a computer hacker can get unauthorized access by using different tools. In case of big organizations, various network security software’s are used to prevent the theft of any confidential and classified data. 2. Rapid Spread of Computer Viruses If any computer system in a network gets affected by computer virus, there is a possible threat of other systems getting affected too. Viruses get spread on a network easily because of the interconnectivity of workstations. Such spread can be dangerous if the computers have important database which can get corrupted by the virus. Computer and IT application Page 2 3. Expensive Set Up: The initial set up cost of a computer network can be high depending on the number of computers to be connected. Costly devices like routers, switches, hubs, etc., can add up to the bills of a person trying to install a computer network. He will also have to buy NICs (Network Interface Cards) for each of the workstations, in case they are not inbuilt. 4. Dependency on the Main File Server: In case the main File Server of a computer network breaks down, the system becomes useless. In case of big networks, the File Server should be a powerful computer, which often makes it expensive. What do we mean by transmission media? Transmission media is the means or pathway by which data is transmitted and received from one computer to another computer. There are two types of transmission media, they are:1) Guided media 2) Unguided media 1) Guided Media: - Guided media is such type of media by which data/information is sent and received through some end to end connection like wire. Example:- Twisted pair cable, coaxial cable, optical fiber cable 2) Unguided Media: - Unguided media is such media by which data/information is sent and received through some frequency or some wave like radio wave, satellite etc Wireless communication: - Communication with the help of unguided media is called wireless communication. a) Twisted pair cable:- It is one of the cheapest and most popularly used communication media in guided system. In this cable a pair of copper wires is twisted to each other in a helical path making the same structure as a DNA molecule. The reason for twisting is to reduce electrical interference. It is mostly used telephone systems. These cables are available in varieties of grade level called levels. Level 5 cables is most expensive but has bandwidth (100 mbps), level 4 cable has 20 mbps bandwidth and level 3 has 16 mbps bandwidth. There are two types of twisted pair cable, they are:A) Shielded twisted pair (STP) B) Unshielded twisted pair (UTP) b) Coaxial Cable: - It is the most popular cable which is being used in TV in our homes. A coaxial cable consists of a thick copper wire in the core, surrounded by an insulating plastic with a net of thin copper wires used as earthing and in the outermost part it is insulated by a thick plastic cover. Generally it comes in two categories. -thin coaxial cable -thick coaxial cable Computer and IT application Page 3 Thick coaxial cable has 100base5 bandwidth which means 10-100mbps bandwidth with distance 500 m. thin coaxial cable has 10base2 bandwidth which means 10-100 bandwidths with distance 100-200m. It is better than twisted pair cable and has high bandwidth but expensive in comparison to twisted pair cable. c) Fiber optics cable/ Optical fiber: - It is the most advanced media in communication. It has the highest bandwidth 100baseFX (which means 100 mbps with distance 2000m) and 1000baseLX (which means 1000mbps with distance 3000m) and has highest speed and is most expensive media in comparison to any other media. It uses light rather than electricity to transmit information. It is very thin media which is measured in microns and is very hard to identify with our necked eye. It has two layers-clad and core. Both the clad and core are made up of same material (glass and plastic). The light is passed through an optical fiber by the process of total internal reflection. Light source for it is ‘Laser’ or ‘Led’ and detector id ‘Pin’. At the source, electrical pulses generated by computer or electronic devices, is converted into light by ‘Laser’ or ‘Led’ which flows from fiber optics in the form of light. At the destination, the light rays are again converted into electrical pulses by ‘Pin’. It doesn’t have any danger of leakage and electrical interference. So it can be used in any environments like under big factories, grounds or airports .It has the highest bandwidth and the highest speed in comparison to any other media and is most expensive than other media. Satellite: - Satellite acts as relay station for communication signals. The satellite accept data and signals transmitted from an earth station, amplifies them and then retransmit them to another earth station. History of Internet The US department of defense laid the foundation of the internet roughly 30 years ago with a network called ARPNET (Advance Research Projects Agency Net). During the 1970’s work an ARPANET consisted of connecting the various networks and developing the necessary internet software. During the early 1980’s the network became known as the internet and it was during that period that business firms began using it but the general public started using internet after the development of world wide web in the early 1990’s. In 1993 there were only 130 websites all over the world now there are millions of websites all over the world. What is Internet? What are the uses of internet? Internet is not just like one network, it is a coordinated union of a multitude of networks all over the world or we can say internet is the world largest computer networking, the network of networks. Internet is global LAN where millions of computers are connected to each other. any computer user on internet can contact another user on the internet anywhere in the world, very much like telephone user communicates with another user Computer and IT application Page 4 anywhere in the world. Internet is an information superhighway and has seemingly compressed the world into a cyber colony. Internet is available to anyone who wants to use it. A majority of internet users are college students, businessmen, professionals etc and accessing internet has become a way of life. Uses of Internet 1. We can exchange e-mail with millions of people with e-mail address in the internet. 2. We can get information about people, products, organizations and many other things from the internet. 3. We can get search facilities in the internet (such as- google.com) by the help of which we can search lots of information regarding any topic within a second. 4. We can send or receive data files, programs, images, sound, and animation through the internet from very distant places. 5. We can sell or buy products and services through the interent( Such as E-commerce, E-business) 6. We can give information about our organization and institution by launching homepage and keeping in the internet which let the other people around the world to know. 7. We can conduct surveys; get opinions of people around the world on particular topics through the internet. 8. We can learn or we can do courses through the internet, we can give online exam through the internet such as MCSE(Microsoft Certified System Engineering), OCP (Oracle Certified Professional) etc The important thing to realize is that the internet permits almost anything but our imagination is the only limit. What are the different types of Networking? Networking is categorized according to the size of network, speed of data transmission, distance covered, technology used, architecture used, structure of the network etc. There are three types of Networking, they are:a) LAN (Local area Network):- A LAN connects network devices over a relatively short distance. A networked office building, school, or home usually contains a single LAN, though sometimes one building will contain a few small LANs (perhaps one per room), and occasionally a LAN will span a group of nearby buildings. The media (e.g., wire) used in LAN must be of the same type and the protocol used in it is generally same. It is simpler and cheaper than any other networking system. Major advantage of this system is the security provided because no any outsider’s can’t access the resources of a private network. Major disadvantage of this system is that it can’t cover more than few kilometers Computer and IT application Page 5 b) Metropolitan Area Network - a network spanning a physical area larger than a LAN but smaller than a WAN, such as a city. When LAN grows and spreads in area then it becomes MAN. It is called metropolitan network because it is extended up to a city or a larger geographical area. MAN is typically owned and operated by a single entity such as a government body or large corporation. In this system different communication media can be adopted and different types of protocols can be used. Instead of using guided media (e.g. wire), it can use unguided media (e.g. wireless media). It has more flexibility than the LAN has many advantages over LAN but has very high chances of data leakage or security break. c) WAN:-It is the network that is extended to a large area (e.g. throughout the world or even more) and the communication is done through satellite. A WAN is a geographically-dispersed collection of LANs. A network device called a router connects LANs to a WAN. In IP networking, the router maintains both a LAN address and a WAN address. A WAN differs from a LAN in several important ways. Most WANs (like the Internet) are not owned by any one organization but rather exist under collective or distributed ownership and management. It is the combination of many different types of LAN and MAN networks, so it has massive amount of heterogeneous systems(e.g. operating systems, devices, hardware, topologies, protocols, transmission media etc). Instead of centralizing the transmitting devices in a particular location such devices are distributed in different parts of the world. The largest WAN in existence is internet. Other types of networking are: Wireless Local Area Network - a LAN based on WiFi wireless network technology Campus Area Network - a network spanning multiple LANs but smaller than a MAN, such as on a university or local business campus. Storage Area Network - connects servers to data storage devices through a technology like Fibre Channel. System Area Network - links high-performance computers with high-speed connections in a cluster configuration. Also known as Cluster Area Network. Difference between LAN and WAN LAN ( Local Area Network 1. LAN are smaller networks, usually within an office base 2. The distance between the nodes is limited in LAN, there upper limit of 3 km or less and lower limit of 2m. 3. The data rate speed of LAN normally operate at 1to 100 mbps Computer and IT application 1. 2. 3. 4. WAN(Wide Area Network) WAN, or wide area networks, are broader geographic networks WAN can spread throughout the world covering 1000s of kms WAN normally operate at the speed of 1 to 4 mbps In WAN error rate is higher than LAN Page 6 4. In LAN error rate are much lower in comparison to WAN 5. Transmission media used in LAN are generally wired media (wireless LAN also exists such WiFi) using coaxial cable, fiber optic cable. 6. LANs are owned by single organization. 7. LAN is operated at low cost 5. WAN uses satellite and wireless media for transmission media. 6. WAN is owned by multiple organizations. 7. WAN is operated at high cost Explain different types of Networking Architecture There are two types of networking architecture, they are 1) Peer-to –Peer architecture (Point-to Point) 2) Client-Server architecture (Broadcasting) Peer-to –Peer architecture (Point-to Point):In peer-to-peer architecture, computers are connected individually in pair (one-to-one connection). When the computer A wants to send message to computer C then it must be passed through B, when packet reaches to computer B it first of all matches the receiver address attached with the message to its own address. If it matches, then only accepts the message otherwise it discards it and forwards to the computer C. When the communication is being done between any two computers, then other channels remain free. So, there is not so much problem of traffic. As we have seen that each of the computers get equal priority and each behave like a server on one time and the same becomes client in other time. Client- server architecture:It is also called broadcasting architecture, in this architecture computers are connected to a central device and communication is done through it. When computer A wants to send message to computer C then message is sent to the central device. The message is first of all received by the server and the message is broadcasted by the server. All the computers attached to the network receive such packet; each of them read the receiver’s address and compares their own address with the address written on the packet. If it matches, then only the computer accepts it otherwise the packet is discarded or rejected. So in this case, computer C address matches with the packet address, so computer C accepts, other computer discard it. In this architecture server is always fixed which control all other computers and the communication is done through server. All other computers are called clients. The big disadvantage of this architecture is high traffic problem created by broadcasting, because at the time of broadcasting, all the computers remain busy. Its big advantage is its speed. Computer and IT application Page 7 Protocol: Protocols are the rules of transmission. As we know that for a transmission of data/information to be successful, each of the devices/computers attached to both ends must speak the same set of languages, must have same set of devices and same types of software. But practically it is impossible in this distributed world. To overcome this limitation, certain set of rules which are common and acceptable by both the parties are developed which play a role of interpreter between the sender and the receiver, which is known as protocols. For example: - TCP/IP, SMTP, HTTP etc Intranet: Intranet is also network of networks. But it is not public it is private network group and owned by a particular organization, only those persons who are authorized and authenticated users of that organization can only use this net. Intranet is based on internet technology to build information system with an organization or enterprise. It also uses the same protocols as used by the internet (HTTP, TCP/IP). It inherits all the features of Internet. It is useful for promoting business, education etc. If permission is given to access intranet from remote location then it is termed as extranet. What is network topology? What are the different types of LAN topology? Explain ANS: - The physical layer of local area network is called network topology. In other word network topology is the logical way of explaining how computer are connected to each other and shows physically how they are linked. The major goal of network topology is to find out the most economical and efficient way to connect all the users to the network. There are all together six types of LAN topology, they are as follows:a) Bus Topology b) Star Topology c) Ring Topology d) Tree Topology e) Mesh Topology f) Hybrid Topology a) Bus Topology: - This is the most popular topology. In this topology a single cable is connected with each computer. The single cable at the middle of all the computers is called ‘Bus’ from which other nodes are connected by some connectors and that node is connected on the LAN port of each computer. In this topology server is located on either side and a terminator is located on other side of the bus. It is based on broadcasting architecture Advantage of Bus Topology It is relatively easy to install and extend the network If any of the computers in network is down, then other computers can continue their work Computer and IT application Page 8 It is more flexible because we can connect any number of computers by using a connector in the bus It is not expensive to install Disadvantage of Bus Topology Data traffic is high in this topology because it is based on client/ server architecture Data collision is high If the backbone cable fails the entire network is unusuable. Finding out fault and troubleshooting is hard b) Star Topology:In this topology a central connecting device known as ‘Hub’ connects all the computers in the network to each other, which is connected to a powerful central computer known as server. It is based on client/server architecture. Advantage of Star Topology: It is flexible because in this topology it is easy to add computer and remove existing one. In this topology it is easy to diagnose fault because of the use of ‘Hub’ In this topology if any of the computers in the network is down, then other computers can carry out their functions as usual Disadvantages of Star Topology In this topology if the server or hubs fail it makes the whole system unavailable. In this topology cost of cable is more because all the cable from all the clients must be connected to the server through hub It is based on client/server architecture so in this topology data traffic is high c) Ring Topology:In this topology each computer is connected in a circular structure. Each computer is connected to other two computers in either side. It is based on point to point or peer to peer architecture Advantage of Ring topology There is no dependence on the central server. So, each computer is capable of acting as server as well as client. Computer and IT application Page 9 Since data travels in one direction, there is less chance of collision and there is less chance of data- traffic. Every computer has equal access facility to the resources. Disadvantage of Ring topology Failure of any one of the computer on the network makes the whole network down Very hard to find out the errors and troubleshooting Non- flexible because adding new computer on the network and removing existing computer is very hard d) Tree Topology: The tree topology arranges computers and links into distinct hierarchical structure in order to allow greater control and easier troubleshooting. A computer acting as a server in upper level can act as client in lower lever. It minimizes traffic drastically because broadcasting is done only within one level. Data and traffic can flow from up to down or vice versa. If any of the computers is down, then it affects only those computers which are under its control. Advantage of Tree topology The tree topology is flexible to extend and reduce. The failure of the leaf node does not affect the whole network. Disadvantage of Tree topology Failure to any of the hierarchical node will cause the failure to the network on that node. The performance of the root node and other hierarchical nodes will affect the performance of the network. It is not easy to install. It is not easy to troubleshoot the network problem. e) Mesh topology: Mesh topology arranges all the computers where each of the computers is connected to all computers .If any of the computer is down then other computer can still continue to work. It is very much complex and troubleshooting much harder. Advantage of Mesh topology Because of the multiple paths to reach the nodes the failure of any node will not affect the operation of the entire network. There is no traffic problem as it has multiple paths. Disadvantages of Mesh topology It is very complex network and is difficult to find the faults and troubleshoot problems. A lot of network cable is needed, so it is costly. It is difficult to install and extend the network. Computer and IT application Page 10 f) Hybrid topology: Hybrid topology is the combination of two or more topologies together. It has advantages of more than one topologies as well as disadvantages, too What are the different networking devices? Explain each of them in brief. ANS:The different networking devices are Hub Bridge Repeater Router Modem Hub: Hub is a device with multiple ports for connecting different computers on the network. Usually, each file servers has only one NIC. Therefore, it would be impossible to connect every workstation directly to the file server. To solve this problem, LANs use hubs, which are very common networking devices. So, it has the following properties: It operates on Physical layer of OSI model It accepts data, amplify them and then transmit It is used to split network segments and propagate signals through it. It does not need path determination and switching Its big disadvantage is that it can’t filter network traffic and it imposes limitation to the number of computer that can be connected Bridge: It is a device, which connects different network segments and passes data with the same communication protocols. It is the connecting device between two or more hubs. Some of the characteristics are: It operates at layer 2 ( Data Link) of OSI model It reduces unnecessary traffic problem by controlling broadcasting Bridges are more intelligent then hubs because they maintain MAC address tables in them and forward data looking on it. Bridges collect and pass packets between 2 network segments Repeater: It is another network connecting device. It increases the distance over which a network can extend. For example, using a category 5 twisted pair cable, we can send data up to maximum of 100 meters only without amplification. If data travels beyond that distance without amplification, then it becomes weaker and after some time the Computer and IT application Page 11 signal will be destroyed. A repeater provides solution for such problem. Some of the characteristics of repeaters are: It operates at layer-1 (Physical layer) of OSI model It receives signals, amplifies them and sends it. If the signals are weakened because of long wire, then repeater can amplify, clean the signal and we can increase length of cable. Router: It is also a type networking device which are used to connect separate network and to access internet. It is similar to Bridge in many ways Some of the characteristics of routers are: It operates at layer -3 (Network layer). Router finds the shortest and the best path to forward data between different paths available It use IP address for accessing and forwarding data packets It is just like bridge or hub but provides more functionality and is more intelligent Modem (modulator and demodulator): It is a device that interprets digital and analog signals enabling data to be transmitted over voice-grade telephone lines. At the source, digital signals are converted to a form suitable for transmission over analog communication facilities At the destination, these analog signals are returned to their digital form It is used in multimedia, networking and internet to transmit data(text ,data ,voice, picture etc) from copper wire because copper wire can transmit only analog signals but the signals produced by a computer is digital. In other words modem is a device which has responsibility of modulating (coding) the data before transmission and demodulating (decoding) the same data with the same rule at the receiving end. Analog and digital signals A signal is called analog signal if the signal is continuously varying with respect to time. The example of analog signal is the voice signals, music signals, human voice, temperature etc. A signal is called digital signal if the signal is discrete or discontinuous. Digital signals are the language of modern day computers. Digital signal is represented only by digits that are 1 and 0.The examples of digital signal are the digitized audio and video signals stored in media such as CD/DVD. The digital signaling has more advantages than analog signaling. The advantage of the digital signaling is that it is cheaper than analog signaling and is more tolerant to noise interference. Modulation:- Modulation is a technique used in transmission of a signal. It is the process used to describe how the digital signal is changed so it can be transmitted across the analogue link. Modulation can be amplitude, frequency or phase modulation depending on the fact that whether the amplitude, frequency or phase has been changed. Computer and IT application Page 12 Types of modulation:Amplitude modulation:-The modulation which is suitable for low speed transmission is called amplitude modulation. Frequency modulation:-The modulation which uses two carrier signals. High frequency signals for high and low frequency signal for low is called modulation. Phase modulation:-The modulation that uses a single carrier frequency and alters the phase of the carrier is called phase modulation. Define Direction of communication flow Depending on the direction of flow of signals during the communication, mode of communication can be divided into three types. They are:-simplex, half duplex and full duplex. Simplex communication:- when data flows in only one direction from sender to receiver, then the communication flow is known as simplex communication. For example:-radio and television broadcast. Half duplex Communication:-When data flows in both the direction from sender to receiver and receiver to sender, but the transmission is one way only at a time, then the communication flow is known as half duplex communication. When the sender is transmitting the signal, the receiver can’t transmit back to the source at the same time. For example:-Talking with friends using landline or mobile phone, sending fax etc. Full Duplex Communication:When data flows in both the direction from sender to receiver and receiver to sender simultaneously then the communication flow is known as full duplex communication. For example:-email and web chatting etc. Define protocol. What are the different types of protocol? Protocol Protocols are the rules of transmission. In other words protocol is a set of rules which is used by computer to communicate with each other across the network. As we know that for a transmission of data/information to be successful, each of the devices/computers attached to both ends must speak the same set of languages, must have same set of devices and same types of software. But practically it is impossible in this distributed world. To overcome this limitation, certain set of rules which are common and acceptable by both the parties are developed which play a role of interpreter between the sender and the receiver, which is known as protocols. The different types of protocols are as follows:a) IP ( Internet Protocol) b) TCP ( Transmission Control Protocol) c) UDP (User Datagram Protocol)\ d) HTTP( Hypertext Transfer Protocol) e) FTP( File Transfer Protocol) f) SMTP ( Simple Mail Transfer Protocol) g) Telnet( Terminal Network) h) POP ( Post Office Protocol) Computer and IT application Page 13 a) IP (Internet Protocol):- It is a protocol defined in the internet layer of the TCP/IP protocol suite. The main task of IP is the best effort delivery of the packets. It is responsible for moving packet of data from node to node. IP forwards each packet based on a four byte destination address (the IP number). The Internet authorities assign ranges of numbers to different organizations. The organizations assign groups of their numbers to departments. IP operates on gateway machines that move data from department to organization to region and then around the world. b) TCP (Transmission Control Protocol):- It is one of the main protocol of the internet protocol suite. The function of TCP is the reliable, ordered delivery of stream of bytes from a program on one computer to another computer. It is responsible for verifying the correct delivery of data from client to server. Data can be lost in the intermediate network. It adds support to detect errors or lost data and to trigger retransmission until the data is correctly and completely received. c) UDP (User Datagram Protocol):-It is one of the core members of the Internet Protocol Suite, the set of network protocols used for the Internet. It is a simple OSI transport layer protocol for client/server network applications based on Internet Protocol (IP). UDP is the main alternative to TCP and one of the oldest network protocols in existence, introduced in 1980. It is often used in videoconferencing applications or computer games specially tuned for real-time performance. It is useful in applications where reliability is not a major concern but speed is a major concern. d) HTTP (Hypertext Transfer Protocol):- It is one of the popular application layer protocols which specify the rules for the interlinked documents called hypertext documents which contain text images, videos and other multimedia contents. HTTP is the foundation of data communication for the World Wide Web. The standards development of HTTP has been coordinated by the Internet Engineering Task Force (IETF) and the World Wide Web Consortium (W3C). The HTTP protocol is designed to permit intermediate network elements to improve or enable communications between clients and servers. e) FTP (File Transfer Protocol):- It is a reliable and secure file transfer protocol which requires user to log into the system before file transfer. It helps us to upload the files to the websites which we are maintaining. Transferring a file require two participants – FTP client program and FTP server program. FTP client program run in our computer and FTP server program run on the server computer. f) Telnet (Terminal Network):-Telnet is the internet tool or protocol that let us travel from our own workstation out into cyberspace to land on another computer. Telnet is useful for the remote administration of internet hosts over the internet. g) SMTP (Simple Mail Transfer Protocol):- It is specified for outgoing mail from one email server to another. The SMTP is extended to send other type of information such as text, picture, and video and other multimedia program and data files. Computer and IT application Page 14 h) POP (Post Office Protocol):- It is used to receive email from a remote mail server. It is designed to support offline mail processing. Using POP mail is delivered to a central server and the user uses a mail program like Eudora, outlook, Netscape Messenger etc that connects to the server and downloads all of the new emails to the users own computer. Operating System How do you define operating system? What are the different functions of operating system? Ans: - Operating System is an organized set or collection of software programs that control the overall operation of the computer system. In other word operating system is a program which controls the hardware and establishes the coordinated relationship between hardware and other software We can also say operating system is a system oriented software programs which acts as an interface between a user and the hardware (i.e. all computer resources) An operating system control the way in which the computer system functions. The operating system performs the following function:1) It provides the platform to install application software into the computer 2) It co-ordinates or control the input and output devices such as monitors, printers , disk drives 3) Protect data, hardware and software from improper use 4) It raises the interrupt and handle the interrupt as and when requires 5) It provides access to compilers or interpreters to translate programs from high level language into machine languages 6) It manages the memory carefully. The part of the operating system that manages the memory is called memory manager. 7) It manages the resources efficiently (for example hard disk, printer) 8) It provides long term storage of user information in the form of files and folders by creating table of each file and folders in the storage device. For example FAT in DOS, NTFS in Windows and ext3 in Linux. 9) It maintains authority over files by allowing different types of access permission and priority. 10) It provides a continuous job processing sequence by scheduling and loading of programs and sub programs. 11) It loads different jobs into the memory in a very efficient manner using a paging mechanism 12) It provides data security so that one program isn’t allowed to capture the program or data space of other program. (For that it maintains the boundary of each job in the memory and each jobs are allowed to run only in that boundary) 13) It interprets commands and instructions given by the user. Computer and IT application Page 15 14) It records the entire event that happen in the computer system which is useful for tracing the past records and troubleshoot (problem detection and correction) if something goes wrong known as event logging. What is the difference between GUI and CUI (command user interface or text based interface or control user interface) Explain the advantage of GUI over text based interface Ans:- Graphic user interface is defined as the interface of computer with users which provides the users with facilities of pull down menus, pointing devices, drag and drop features, clicking and double clicking of mouse, taskbar buttons , check box buttons , multimedia facilities etc . In graphic user interface user can select and run the program by using mouse pointer, copy files and folders from one location to another location simply by dragging and dropping and interaction normally take place with the help of dialogue boxes For example: Window ( Window 95, Window 98 , Window ME , Window 2000, Window XP, and the latest one Window Vista ) Command User interface (Control user interface): It is defined as the interface in which the user must interact with computer by typing command in the keyboard Example:- MS- DOS Advantage of GUI over Text Based Interface Graphic User Interface(GUI) CUI ( Command User Interface or Text Based Interface or Character User Interface) 1) The appearance of GUI is very attractive 2) It is more efficient than CUI 3) In GUI we can work with pointer and pointing device which is much easier 4) It is easier to remember the graphic symbol 1) The appearance of CUI is not attractive 2) It is not as efficient as GUI 3) In CUI we must enter or type the command using Keyboard so we must remember all the commands 4) It is almost impossible to know or remember all the command of CUI 5) It is easier for new user to work in GUI 6) In GUI we can have a facilities of multimedia and internet 5) It is very difficult for new user to work in CUI. They have to remember all the commands which is much more difficult 6) In CUI we don’t have a facilities of multimedia and internet 7) In GUI every interaction is done 7) In CUI every interaction is done Computer and IT application Page 16 through dialog boxes 8) In GUI we can have DOS program 9) GUI supports multiprogramming facilities or In GUI more task can run simultaneously 10) It is user friendly 11) Require more memory 12) Application written for GUI are device independent 13) More threat of virus in GUI 14) 9) Example: Window 98, Window XP etc through typing commands 8) In CUI we don’t have Window program 9) CUI does not have multiprogramming facilities or In CUI one task run at a time 10) It is not user friendly as GUI 11) Require less memory 12) Application written for CUI are device dependent 13) No threat of Virus in CUI 14) Example:- DOS,UNIX etc What are the different types of operating system? Explain each of them in brief. Ans: - The different types of operating system are as follows:1. single user operating system 2. Multi-user operating system 3. Multitasking operating system 4. Real- time operating system 5. Multiprocessing operating system 6. Timesharing operating system 7. Batch operating system 8. Distributed operating system 9. Networked operating system 1. Single user operating system: - single user operating system is the one in which one user can work at one time. A single user operating system provides access to the computer system by a single user at a time. It another user wants to use the computer he or she must have to wait till the current use finish the job. Example- DOS 2. Multi-user operating system: - A multi-user operating system is such system where more than one user use the computer system at one time access to the computer system is normally provided through network. example: UNIX, Linux etc 3. Multitasking operating system: - A multitasking operating system is such system through which we can run more than one task (program) at once .It means multitasking operating system let the user run more than one task at once. Suppose we can run word, we can print the document; we can play the song at one time using such system. Example :- Window XP, Window 2000, Window vista etc 4. Real-time operating system: - Real time operating systems are those systems which are used by such program which require very fast response time. The execution time is the most critical issue in the real time operating system and they must finish the execution of job within Computer and IT application Page 17 pre-defined time-boundary. They are used to control machinery, scientific instruments and industrial systems. Real time operating system typically has very little user-interface capability, and no enduser utilities. A very important part of an Real time operating system is managing the resources of the computer so that a particular operation executes in precisely the same amount of time every time it occurs In other word we can say that real time operating system are on-line system that respond to input immediately which is given by the user. It is a multitasking operating system that aims at executing real-time applications. Example:- the program which require real time operating system to get install and run are missile guiding system, medical monitoring system , flight simulation system etc 5. Multiprocessing operating system: - Multiprocessing operating system is such system which runs on the computer having more than one processor. This operating system simultaneously executes two or more jobs at single time. It contains two processor so the controlling mechanism of this operating system is more complex. A multiprocessing operating system is a computer hardware configuration that included more than one independent processing unit. Example- UNIX 6. Time sharing operating system:-This is such type of operating system in which processor time is divided into small units called time slices and shared in turn between users to provide multi-access. Time sharing refers to sharing a computing resource among many users by multitasking. The idea of multiprogramming was further used in time sharing system .The operating system is responsible for switching between the jobs in such a way that every terminal feels that it is occupying the entire computer resources. Another important concept in time sharing system is priority, interrupt and input and output management. Important jobs can be given high priority so as to execute it fast. 7. Batch operating system:-Batch processing operating system allowed running only one program at a time. Batch processing operating system works as series of programs which are held in a queue. The jobs with similar requirements were batched together and run as a group is called batch processing. This is one of the oldest operating system .it was designed in mid 50’s and mid 60’s. In this type of operating system the job (data +program) is not processed until all the data is fully input. The jobs are stored in a disk in batch in a queue and run one or more at one time under the control of the operating system. A job may wait in a batch queue for minutes or even for hour depending upon the load on the system. Before it could begin to execute the job it need to read the deck of the card. (data was punched in the punched card) So, CPU and the peripherals remained idle most of the time. Computer and IT application Page 18 8. Distributed Operating System: An operating system that manages a group of independent computers and makes them appear to be a single computer is known as a distributed operating system. The development of networked computers that could be linked and communicate with each other, gave rise to distributed computing. Distributed computations are carried out on more than one machine. When computers in a group work in cooperation, they make a distributed system. Some truly distributed systems have dozens of servers around the globe. If traffic is high in any server the job is transferred to other server known as load balancing. 9. Network operating system:-A network operating system (NOS) is a computer operating system that is designed primarily to support workstation, personal computer, and, in some instances, older terminal that are connected on a local area network (LAN). Most of the network operating system works under the principle of Client-server mechanism. Client server is a mechanism in which co-operation and intercommunication between various elements of network takes place and one machine serves others for various functions. In this operating system user doesn’t have to sit in front of machine in which he or she wants to work on. A network operating system provides printer sharing, common file system and database sharing, application sharing, and the ability to manage a network name directory, security, and other housekeeping aspects of a network. 10. Embedded Operating System: Computer system that performs a dedicated function or is designed for use with a specific embedded software application is called embedded system such as micro wave ovens, robots, TV sets, router, digital cameras, washing machine, mobile phones, ATM machine and other automatic digital equipments etc.The operating systems designed for being used in embedded computer systems are known as embedded operating systems. They are capable of operating with a limited number of resources. They have some characteristics of real time operating system but also have size memory and power restrictions that make them special. Unlike, a desktop operating system, the embedded operating system does not load and execute application. This means that the system is only able to run a single application. Examples of such operating system are Windows CE, Palm OS, Free BSD, Minix3, Window ES, and Router OS etc. History of Operating Systems Operating systems have evolved through a number of distinct phases or generations which corresponds roughly to the decades. Computer and IT application Page 19 The 1940's - First Generations The earliest electronic digital computers had no operating systems. Machines of the time were so primitive that programs were often entered one bit at time on rows of mechanical switches (plug boards). Programming languages were unknown (not even assembly languages). Operating systems were unheard of. The 1950's - Second Generation By the early 1950's, the routine had improved somewhat with the introduction of punch cards. The General Motors Research Laboratories implemented the first operating systems in early 1950's for their IBM 701. The system of the 50's generally ran one job at a time. These were called single-stream batch processing systems because programs and data were submitted in groups or batches. The 1960's - Third Generation The systems of the 1960's were also batch processing systems, but they were able to take better advantage of the computer's resources by running several jobs at once. So operating systems designers developed the concept of multiprogramming in which several jobs are in main memory at once; a processor is switched from job to job as needed to keep several jobs advancing while keeping the peripheral devices in use. For example, on the system with no multiprogramming, when the current job paused to wait for other I/O operation to complete, the CPU simply sat idle until the I/O finished. The solution for this problem that evolved was to partition memory into several pieces, with a different job in each partition. While one job was waiting for I/O to complete, another job could be using the CPU. Another major feature in third-generation operating system was the technique called spooling (simultaneous peripheral operations on line). In spooling, a high-speed device like a disk interposed between a running program and a low-speed device involved with the program in input/output. Instead of writing directly to a printer, for example, outputs are written to the disk. Programs can run to completion faster, and other programs can be initiated sooner when the printer becomes available, the outputs may be printed. Another feature present in this generation was time-sharing technique, a variant of multiprogramming technique, in which each user has an on-line (i.e., directly connected) terminal. Because the user is present and interacting with the computer, the computer system must respond quickly to user requests, otherwise user productivity could suffer. Fourth Generation With the development of LSI (Large Scale Integration) circuits, chips, operating system entered in the system entered in the personal computer and the workstation age. Microprocessor technology evolved to the point that it becomes possible to build desktop Computer and IT application Page 20 computers as powerful as the mainframes of the 1970s. Two operating systems have dominated the personal computer scene: MS-DOS, written by Microsoft, Inc. for the IBM PC and other machines using the Intel 8088 CPU and its successors, and UNIX, which is dominant on the large personal computers using the Motorola 6899 CPU family. Disk Operating System 1) DOS (Disk operating system):- DOS is a set of control programs which manages the computer’s resources and creates a well defined software environment for applications. It is an operating system which was written to control hardware. Word perfect, LOTUS, dbase, TURBO C/C++ etc are softwares which run under DOS. There are two types of DOS commands. They are:a) Internal DOS commands b) External DOS commands a) Internal DOS commands:- Internal commands are built in the COMMAND.COM file. It can be executed from any DOS prompt because each of the internal commands are memory resident. As long as the computer is running, we are ready to give internal commands. Example of internal commands are:- DIR, CLS, COPY, REN, DATE etc. b) External DOS commands: - External commands are on the disk as separate program files. Therefore they must be read from disk before they are executed. They are comparatively slower in execution than internal commands. Example of external commands is: - TREE, FORMAT, LABEL etc. 2) Booting:- Loading of system files into the memory of computer and to initialize every hardware components of the computer system is called booting. There are two type of booting. They are:- cold booting and warm booting i) Warm boot:- restarting of the computer using reset button, restart option or ctrl+alt+del key is called warm boot. ii) Cold boot:- Starting of the computer from power off state to power on state is called cold boot. Cold boot can be performed by switching on the computer. Algorithm of Booting Step1: Trun on the computer Step2: ROM is activated and the BIOS is loaded Step3: POST (Power on self test) Step4: Boot records load the initial system files (IO.SYS) into RAM from disk Step5: Then the computer gets start File:- A file is a collection of related information. It has a name with the extension that specifies type of file. Executable files are also called program files and often have extension like .EXE and .COM. Example: practical.doc where practical is a file name and .doc is an extension. Directory: - A directory is a table of contents of files, directories and sub- directories. Directory name may or may not have extension. Directory contains information about all files stored on a disk. A sub directory is a directory within directory. Number of sub directories can be created on the disk, but the basic directory on the disk is always the main directory called the root directory and sub directory can be sub divided into a more sub directories, each divided from its parent directory by a backslash. Command: DIR, it is use to display files, directories and subdirectories. Computer and IT application Page 21 Batch file:- A batch file is a file in which series of DOS commands are saved and they are executed one after another. A batch file is an unformatted text file that contains one or more commands and has a .bat or .cmd file name.AUTOEXE.BAT is a file which is executed during the startup of a computer. What are the advantages and disadvantages of MS-DOS? Advantages: 1. 2. 3. 4. 5. 6. 7. It will run on a much smaller system. (entire OS can be placed in a single modern ROM chip) Gives you more "direct" control of the processes. Because of smaller size it will boot much faster than any windows version. It is cheap and free if you go on the internet. Very fast even on a relatively slow machine. It supports different disk like floppy, hard disk,CD etc It is single user operating system but can work on Local Area Network using Novel software Disadvantages: 1. It is single user, single tasking operating system 2. It does not support advanced application software 3. Very few "new" programs available, therefore you need to be able to write programs in many cases. 4. Not nearly as fancy in the graphics department. 5. Not compatible with current "browsers" and most internet. 6. It is not so user friendly like windows system and cannot support advance computer peripheral devices even mouse. Computer and IT application Page 22 UNIT 2 Programming Language (Introduction, Generation of Programming Language, Flowchart and Algorithms) Computer and IT application Page 23 Introduction A Computer cannot perform any job or task without program. A Computer is a dead machine without program. So to make it live and working it requires a program. Like operating system is needed to initiate or boot computer and application software is needed to perform various tasks. A program is a set of instruction written sequentially and in a logical way to tell the computer to do a specific task or to solve a given problem. The process of developing a program is called programming and the language that is used to develop the program is called programming language also who does a programming is called programmer. The language which is used to have communication between machine and human being is called programming language. Programming concept:The thorough understanding regarding the entire process of development of programs is called programming concept. It includes the overall understanding and application of different computer programming languages, compiler, interpreter, control structures program design tools, syntax, semantic, programming techniques and different stages involved in a program development. Explain Machine language, Assembly language, High level language with their advantage and limitation (disadvantage) Machine language: - The language which is called the language of CPU and which is written in binary code (composed of 0 and 1) is called Machine language. In this language computer can understand every instruction only in the form of 0 and 1 . All the valid computer operation are performed in terms of binary operation Example: - If we want to write and instruction “Add 2 and 3 “then we have to write “01100001 (ADD) 00000010 (2) 00000011(3)” Assembly language:- The language in which program is written in short codes like ADD, MUL or SUB instead of writing instruction in binary number (0 and 1) is called assembly language. It is also called low level language. Assembler converts the assembly language to the machine language to make it understandable by computer hardware because computer can understand the instruction written only in binary form. It is not user friendly language. This language is also processor dependent language. A Program written for Intel processor does not work in Motorola processor. Computer viruses are mostly written in assembly language High Level Language: - The languages which are quite similar to written English and are therefore very easier to use in compare to machine language and assembly language is called high level language. Program written in high level language is translated into machine language by a program is called compiler or interpreter (first this program checks the program’s syntax if it is free from errors translator translates into an equivalent code). High level languages are machine independent language i.e. the Computer and IT application Page 24 program written for Intel processor easily run on Motorola processor. It is very easy to understand. It is user friendly language. It is a problem oriented language. Advantage of assembly language 1) Assembly language is easier to understand as compared to machine language 2) It is easier to modify as compared to Machine language 3) Chances of error is less than machine language 4) In Assembly language program execution time is faster than program written in high level languages 5) It is easier to understand as compared to machine language 6) We do not need to take care of storage location of data and instruction while writing program in assembly language Limitation/Disadvantage of Assembly language 1) It is a processor(Machine dependent language ) 2) Since it is a Machine dependent language it requires the knowledge of hardware also while writing program is assembly language 3) There is one to one correspondence between the assembly language and machine language instruction Advantage of machine language 1) The program written in machine language does not need any translation 2) Though it is very difficult to write program in machine language but the program written in machine language runs faster than any other program Disadvantage/ Limitation of machine language 1) Machine language is machine dependent. The program written for one processor cannot be run in another processor i.e. a machine code of intel processor doesn’t work for Motorola processor 2) Machine language has to be written in the form of 1 and 0. So it is very difficult to do program in machine language 3) Chances of error is high while writing program in machine language 4) It is very difficult to debug the program written in machine language Advantage of high level language - High level language is machine independent language. So it is portable ( ie program written in one processor easily run on another processor A program written in high level language is easier to learn because it is similar to English language It is user friendly language Chance of error is less and it is very easy to debug Programming in high level language requires less time and effort as compared to low level language. Computer and IT application Page 25 Limitation/ disadvantage of high level language 1) The program written in high level language in less efficient as compared to the program written in assembly and machine language because it require more memory and more time to execute. 2) The task related to the computer hardware can be programmed or handled only by either machine or assembly language so for these purposes high level language cannot be used Differentiate between compiler and Interpreter Compiler i) ii) iii) iv) v) vi) vii) Interpreter It translates a complete high level language program into machine language at once It finds the syntax errors after compiling the whole program i) The compiling process is faster than interpreter. It creates the object code after compiling the whole program iii) Debugging process is complicated in compiler Compiler demands more resources (memory, CPU time etc) than interpreter. Example:- C, C++, Visual Basic, java etc v) ii) iv) vi) vii) It translates high level language program into machine language line by line. It finds the syntax errors after translating each line of the program. The interpreting process is slower than compiler. It creates the object code after translating each line of the program. Debugging process is easy in interpreter. Interpreter requires low resources. Example:- BASIC, GWBASIC etc. QBASIC, What do you mean by 4GL? Give example Ans: - The language which works at a higher level than normal high level languages such as COBOL, Pascal, C, and C++ is called 4GL language. These are result oriented language and have heavy data processing and query capability. 4GL permits programs to be constructed using short English like easily understood and easily remembered commands. 4GL programs are also needed to be translated either by compiler or interpreter. There are inbuilt and ready to use GUI-objects like forms, command buttons, radio buttons reports etc. 4GL are dedicated for some particular application development. Example of 4Gl is oracle, MS-SQL, Sybase etc what are the advantage of 4GL? Ans: - The advantages of 4GL (Fourth generation language) are as follows:1. One line of 4GL code is equivalent to many lines of 3 GL code 2. System development is faster Computer and IT application Page 26 3. Program maintenance is easier because the program source code is smaller 4. Program developed in 4th generation language is more portable than those developed in 3rd generation languages. 5. Better communication with user with very less effort 6. End user can often develop the program. All the user need to do is click the button, drag and drop the components etc. Disadvantage of 4GL are:1. Needs longer time to convert into machine language than other languages. 2. Execution speed is slower than other languages Define Programming statement. Explain the different types of programming statement. Ans:- An instruction or expression ( also called code) written in high level language to do a specific task in a program is called programming statement. Each programming statement commands the computer to do some specific task such as input, output, calculation or some logical decision. One program statement in high level language may results in several instructions in machine language when the program is compiled. Programming statement may consists of keyword, variables, operators, control structures, data type , library function, user defined function etc. There are three types of programming statement used in program. They are:1. Simple statement:- It is a basic part of program and it is a single line expression which is used to carry out assignment, calculation or to test logical decision. Example:X=10 - assign integer values 10 to x variable a>=50 - logical statement to check whether a is greater than or equals to 50 or not. 2. Compound statement:-Compound statement is defined as a statement which consists of two or more individual instruction. Example:- A= l*b; where one instruction is for multiplication of l and b and other instruction is for assigning multiplication value to the variable A. 3. Control Statement:- A statement that affects the flow of execution through a program is called control statement. Control statements are also called control structures in high level languages. They are the basic building blocks of high level languages. There are three types of control statements. They are:-Sequence, Selection and Iteration (Repetition). Define control structures. Explain different types of control structures. Ans:- The structure which regulate the order in which program statements are executed are called control structures. There are types of control structure. They are:Sequence :- It is the set of program instruction which follow one another and are to be executed unconditionally (not dependent on any program conditions) Computer and IT application Page 27 Instructions are put in a predefined sequence (just like a queue in a cinema hall) and the next instruction is executed by CPU only after the execution of previous instruction ( C never comes before B) Selection: It is the set of instructions which are to be executed conditionally that is they are executed based in condition that can be either true or false. Commonly used logic for selection are if condition, if else condition, if else if condition and select case condition Iteration: - These are the computer instructions which are to be performed repeatedly and conditionally that is loop statement are driven by the loop condition. Commonly used logic for iteration are while loop, do while loop and for loop Algorithm, Flowchart and Pseudo code Algorithm: - An algorithm is a sequence of instructions or step by step instruction to find the solution of a problem. Algorithm should be simple and clear. It must be to the point and should lead to the solution of the problem in finite number of steps. In other words the set of rules that define how a particular problem can be solved in finite number of steps is known as algorithm. An algorithm is composed of a finite set of steps, each of which may require one or more operations. Each operation must be definite, effective and finite A program is the expression of an algorithm in a programming language. Thus, the success of a program depends upon the algorithm. Therefore the logic of the problem must be clearly expressed in an algorithm. In other we can say an algorithm is a collection of finite number of instructions arranged in a sequence to find the solution of a problem. Example: Algorithm for adding the two numbers Step1: Start the program Step2: Input number x, y Step3: Read x, y Step4: Z←x+y Step5: Print Z Step6: Stop the program Example:An algorithm to go to the cinema and see a movie Step1: Start the program Step2: Go to the cinema hall Step3: Is the ticket counter open? Step4: If it is not open, return home Step5: If it is open, buy a ticket Step6: Get into the cinema hall Step7: Watch the movie Step8: Return home Computer and IT application Page 28 Step9: End the program Flowchart: A flowchart is a pictorial representation of an algorithm. We can also define it as a program planning tool for organizing the sequence of steps necessary to solve a problem which is shown in terms of symbols. Flowchart use symbols that has geometrical shapes to indicate the different operation and these symbols connected by flow lines which indicate the order of execution of the various activities. It is used by the programmers to develop the program and system designer to represent the overall system while analyzing and developing the system. Example:Flowchart of adding the two numbers Start Input X, Y Read X, Y Z=X+Y Print Z End Advantage of flowchart It is an independent language .so, the flowchart we design for programming in one language is applicable for programming in another language Once the flowchart is prepared it is very easy to do the coding by looking at the flowchart It is very easy to understand the logic of program by designing the flowchart. Even people who don’t know the coding can understand the logic of program with the help of flowchart Systematic debugging and testing is easily possible with the help of flowchart It provide good documentation for organization It is useful in debugging the program It provides valuable information which cannot be expressed by thousands of words It is user friendly. It can be more easily understood Computer and IT application Page 29 It expresses clearly the logic of a given procedure. It is unambiguous as there can be only one direction of logic at any one time It is used as working models in the design of a new programs and system. Disadvantage of flowchart Preparing flowchart is a time consuming process If there is a change in logic again we have to develop the new flowchart Flowchart do not provide any convenient means to highlight the more important operation Flowchart are quite costly to produce and difficult to use and manage Complex and detailed charts can be laborious to plan and draw The translation of flowchart into computer programs is not easy Preparation of flowchart is a very slow process Most software developers believe that flowcharts are a waste of time and that these slow down the process of software development and they do not start the software development with flowchart, flowchart are only use for the purpose of documentation Pseudo-Code: The general meaning of pseudo code is false code or fake code. Before we write a real program, we write a program that look like a code on the basis of algorithm and flowchart, which may not be syntactically correct but looks like program code is called pseudo code. The instruction of pseudo code is written by using English phrase and mathematical expression. It has no hard and fast rules for writing instruction in pseudo code but the instruction are closer to high level language instructions. The pseudo code designers should have basic knowledge about high level language before writing pseudo code. It is also independent of any programming language. Example: Pseudo code for calculating area of rectangle Input length, breadth Calculate area= length*breadth Output area Differentiate between syntax and semantics. Synatx:The rules that we use while writing code is called syntax. Syntax is the grammatical rules of writing the programming statement. In other word syntax is the rules that tells us whether a string is a valid program or not. The error which is detected by the computer if we violate the rule of writing programming statement is called syntax error. Semantics:The rule that gives the meaning to programs are called semantics. The error which occurs in program logic is called semantical error or logical error. The semantical error is not detected by the computer and the compiler compiles it successfully. We can only see the error after the program is being executed and give wrong output. So it is very difficult to find the semantical or logical error. Because no satisfactory method has been found yet to detect the logical error Computer and IT application Page 30 For example:- if we have to find out the sum of two number say x and y but we subtract the number, then it is called the logical error. Actually the computer assumes that we are going to subtract but actually we want to find the sum of two number so there exist an error . So, instead of writing Z=X+Y if we write Z= X-Y, the computer will not so the error, but the result which we want we will not get. Let us consider another example: “Ram eats Television “grammatically it correct because it is in the form of subject + verb object (i.e. syntactically it is correct) but doesn’t provide any sense. So, this is semantically incorrect Why it is very difficult to find logical error in comparison to syntactical error? Ans:- It is very difficult to find out the logical error in comparison to syntactical error because syntax error violates the rule of writing the programming statement and is detected by compiler at the time of compiling by showing total error occur in computer screen but the logical error is not detected at the time of compiling , after it get executed when we get the wrong output , seeing that wrong output we have to find out the error in logic. On other hand there is no any satisfactory method has been found through which we can detect the logical error For example: - if we have to find out the sum of two number say x and y but we subtract the number, then it is called the logical error. Actually the computer assumes that we are going to subtract but actually we want to find the sum of two numbers so there exist an error. So, instead of writing Z=X+Y if we write Z= X-Y, the computer will not so the error, but the result which we want we will not get. What are the symbols used in flowchart. Mention their name with symbol, shape purpose and description There are various flowchart symbols that carry different messages and are used for different purposes. These symbols are shown below: Symbol Shape Purpose Oval Start /end Parallelogram Input/output Computer and IT application Description This symbol indicates the beginning or end of the program. every flowchart begins with a start symbol and ends with a stop symbol This symbol indicates an input or output operation. It will appear at any point where a data is to be entered into the computer or at Page 31 times when data is to be obtained from the computer Rectangle Process It indicates any calculation or manipulation .i.e processing of data Diamond Decision/condition Line with direction Flow-line It is used to check logical conditions. It has one entry and two exit point which are for true or false It is used to indicate direction of flow of information. Circle Connector End of page A A Beginning of page Large bracket with line Computer and IT application Comment box Connectors are used for the long flowchart that does not fit in the same page. In this condition the flowchart can be broken into parts and an arrow is drawn into a connector symbol containing a unique number or letter Comment box can be used to indicate any comments for better documentation, clarity and in case of explanatory notes Page 32 System Flowchart:A flowchart that gives information about a system is called system flowchart. The system can be data processing system, production system, reservation system, inventory system, accounting system, evaluation system. In system flowchart, the information flow from one section of the organizational unit to another section or form one processing machine to another. It is drawn by the system designer while developing the new system. It plays a very important role in analysis and designing of new system. It does not focus on the process to solve a particular problem. In other words A system flowchart describes the data flow and operations for a data processing system. The flowchart shows how the data processing is to be accomplished. Program Flowchart:The program flowchart describes the sequence of operations and decisions for a particular program In other words we can say that a diagrammatical or pictorial sequence of instruction used by a programmer to solve any problem is called Program Flowchart A flowchart which is used by the programmer to solve a problem is called program flowchart .It is the detailed program which is shown in the form of picture that how program processing steps will be performed within the computer to convert input data into the desired output. Differentiate between flowchart and algorithm Flowchart Algorithm It is a diagrammatic representation of a It is a finite set of step by step instruction program of a program It takes time because we need to draw the It takes less time to write the steps of symbol instruction To understand the program flow one Simple English language is used to write should understand the meaning of symbols algorithm, so easy to understand. Need special knowledge to draw flowchart No need of special knowledge to write algorithm Maintaining a flowchart is difficult Maintaining an algorithm is not as difficult as compare to flowchart At a glance, one can understand the It is difficult to understand the program program flow very easily flow at a glance Differentiate between system flowchart and program flowchart System flowchart Program flowchart It gives broad overview of overall system It gives specific view of control flow of a program It shows the data flow of a system It shows the instruction flow of a program It is designed by system designer It is designed by programmer It consist of different kinds of symbols, one It consist of limited symbols, so it is easy must have good knowledge to understand to understand the program flowchart the flowchart It does not focus on the process to solve a It focus on the process to solve a particular particular problem problem It diagrammatically shows the elements It diagrammatically shows the elements Computer and IT application Page 33 and characteristics of the whole system. and characteristics of the whole program. It plays a vital role in analyzing and It plays the vital role in developing, testing designing the new system and debugging a new program Program Debugging Program debugging is the discovery and correction of programming errors. A program cannot be 100% correct throughout its life time and a very few programs run correctly for the first time. So, debugging is an important and time consuming stage of software development Debugging is basically done to find 1. Syntax error 2. Semantic error 3. Run-time error 1. Syntax error:- The error which occurs when the instruction of program does not match the structural rule of the programming language is called syntax error 2. Semantic error: - The error which causes the wrong output due to wrong calculation or wrong input of data is called semantic error. 3. Run- time error: - The error which appears during the execution or runtime of program is called runtime error. Such errors appear when the computer is asked to divide by zero or when the variable is assigned large value which is beyond its capacity. The run-time error causes the termination of program execution. Procedures and Program Procedure is a mechanism of doing or performing job or task in a well suited manner or in a correct way. A program is a set of instruction written sequentially and in a logical way to tell the computer to do a specific task or to solve a given problem. Structured programming Structured programming is a subset of procedural programming based on the idea of modularity, where the entire program is divided into modules. Again, each module is composed of one or more procedures also called as functions. So, it is also called modular programming. Example:-C, Pascal etc.It follows top down programming approach. Advantages of Structured programming are: It is easier to write even a complex program because of modular programming technique. It is easy to use, test, debug and modify. It has only one main function so it is easy to maintain. It is easy to learn It uses top down approach for program development A function written t o perform one task can be used in another program It provides various control structures. Computer and IT application Page 34 Object Oriented Programming The programming which gives more emphasis on data that is object (combination of data and related function) rather than procedures is called object oriented programming It uses bottom up approach for program development. Nowadays almost all the programming languages are using object oriented techniques, even scripting languages are also using this technique such JavaScript. This technique of programming is perfectly matched with the real world object. Important features of Object-Oriented Programming are as follows:1) Emphasis is given on data rather than procedures 2) Programs are divided into different groups known as objects 3) Data structures are designed such that they characterize the objects 4) Functions and data are tied together 5) Data is hidden and can’t be accessed by external function 6) Functions are communicated between each other through objects. 7) New data and function can easily be added 8) Follow Bottom up approach Advantages and disadvantages Object-Oriented Programming:OOP contributes greater programmer productivity Better quality of software and lesser maintenance cost. The main advantages are:1) Making the use of inheritance, redundant code is eliminated and the existing class is extended 2) Through data hiding programmer can build secure programs. 3) System can be easily upgraded from small to large systems 4) Software complexity can be easily managed 5) Message passing technique for communication between objects makes the interfaces description with external system much simpler 6) Code reusability is much easier than conventional programming language Disadvantage of OOP 1) It demands more computer resources. 2) Requires the mastering in software engineering and programming methodology. 3) Benefits only in long run while managing large software projects Application areas of OOP 1. 2. 3. 4. 5. 6. Games Expert system Object-oriented databases Artificial Intelligence AI and expert systems Most important areas of application is design of user interface such as window Computer and IT application Page 35 7. Computer based training and educational systems Scripting language A high level programming language that is interpreted by another program at runtime rather than compiled by the computer's processor as other programming languages (such as C and C++) are. Scripting languages, which can be embedded within HTML, commonly are used to add functionality to a Web page, such as different menu styles or graphic displays or to serve dynamic advertisements. These types of languages are clientside scripting languages, affecting the data that the end user sees in a browser window. Other scripting languages are server-side scripting languages that manipulate the data, usually in a database, on the server. Scripting languages become popular because of the development of the Internet as a communications tool. Example:-PHP, JavaScript, ASP etc Types of Scripting Language Client -side scripting language:-The language affecting the data that the end user sees in a browser window is called client side scripting language. Client-side refers to the side of end users. So, client-side scripts are programs that is written and attached to HTRML documents that run on a user’s browser while viewing the documents. Scripts allow HTML forms to process input as it is entered and the result is displayed by the web browsers like Mozilla, Opera etc. Example:-JavaScript, VBScript etc. Server- side scripting language:-The language that manipulates the data, usually in a database, on the server is called server side scripting language. Server-side scripting is a web server technology in which a user’s request is fulfilled by running a script directly on the web server to generate HTML pages. The primary advantage to server-side scripting is the ability to highly customize the response based on the user’s requirements, access rights or queries into database. Example:-PHP, ASP etc Computer and IT application Page 36 UNIT 3 Word Processor Computer and IT application Page 37 Object Linking and Embedding (OLE):-It is a technology developed by Microsoft that allows embedding and linking to documents and other objects. It allows users to integrate data from different applications. Object linking allows users to share a single source of data for a particular object. The document contains the name of the file containing the data, along with a picture of the data. When the source is updated, all the documents using the data are updated as well. With object embedding, one application (referred to as the "source") provides data or an image that will be contained in the document of another application (referred to as the "destination"). The destination application contains the data or graphic image, but does not have the ability to edit it. It simply displays, prints or plays the embedded item. To edit or update the embedded object, it must be opened in the source application that created it. Object Linking and Embedding is a technique used to insert data, it is called Embedding; if we do want the data to update, it is called Linking. Example:-If it is linked then when the data in the spreadsheet is changed, that change will show in the Word document. If it is embedded, then changes in the spreadsheet will not have any effect on the figures in the Word document. Differentiate between Object linking and embedding Embedding It is the process to objects(picture,file,vedio etc) Linking the It is the process to insert the objects but by establishing the relation between source object and working object. After inserting the objects there is no After inserting the object, we can double relation between source object and working click over it to go into source place, when object. we modify the source object it automatically modify the working object It does not have the ability to edit it. It It has the ability to edit it. simply display, print or plays the embedded item. insert What is macro? What are the uses of macro? A macro is a series of commands and instructions that we group together as a single command to accomplish a task automatically. Uses for macros are: To speed up routine editing and formatting Computer and IT application Page 38 To combine multiple commands — for example, to insert a table with a specific size and borders, and with a specific number of rows and columns To make an option in a dialog box more accessible To automate a complex series of tasks Write down the steps for creating macro. 1. 2. 3. 4. 5. 6. Click the Microsoft Office Button, and then click Word Options. Click Customize. Next to Keyboard shortcuts, click Customize. In the Categories list, click Macros. In the Macros list, click the macro that we want to change. In the Press new shortcut key box, type the key combination that we want to choose. 7. Check the Current keys box to make sure that we aren't assigning a key combination that we already use to perform a different task. 8. In the Save changes in list, click the option that matches where we want to run our macro. 9. Click Close. What is hyperlink? What are the uses of hyperlink? A hyperlink is a word, phrase, or image that we can click on to jump to a new document or a new section within the current document. Hyperlinks are found in nearly all Web pages, allowing users to click their way from page to page. When we move the cursor over a hyperlink, whether it is text or an image, the arrow should change to a small hand pointing at the link. When we click it, a new page or place in the current page will open. A hyperlink is a connection from one slide to another slide in the same presentation or to a slide in another presentation, an e-mail address, a Web page, or a file. Hyperlinks are a great way to connect our presentation to other slides, presentations, documents, and the Web. We can use hyperlinks for the following: To enable us to jump to other slides quickly To switch to another presentation To open another file, such as a Word document or Excel spreadsheet To display a Web page To open an e-mail to someone Computer and IT application Page 39