CCNA Training – Virtual LANs
advertisement

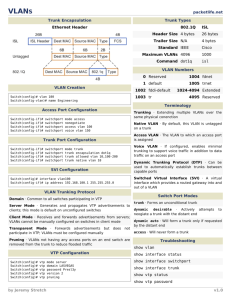
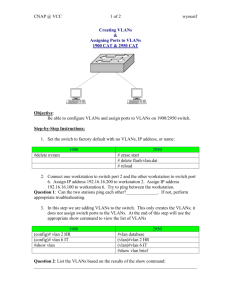
Chapter 4 Virtual LANs Version 1 Introduction By default, switches forward broadcasts, this means that all segments connected to a switch are in one broadcast domain. Virtual LANs or VLANs are used to control broadcasts as well as simplify network management: VLANs increase the number of broadcast domains while decreasing their size. Network adds, moves and changes are achieved by configuring ports into the appropriate VLAN. VLANs can enhance network security. A group of users needing high security can be placed into a VLAN so that no users outside of the VLAN can communicate with them. VLAN Memberships VLANs are created by an administrator, who assigns switch ports to each VLAN, which is called a static VLAN. A dynamic VLAN uses a database, created by an administrator, with all the MAC addresses of all the host devices. This allows a host to plug into a switch and be dynamically assigned to a VLAN based on their MAC address. Static VLANs Static VLANs are the usual way of creating VLANs and the most secure. The switch port you assign to a VLAN always maintains the association until an administrator changes the port assignment. This type of setup is easy to configure, monitor and control. When you plug a host into a switch port with static VLANs, the host must have the correct IP configuration or else it will not be able to access the network. Dynamic VLANs A dynamic VLAN determines a host’s VLAN assignment automatically using intelligent management software. When you connect a host to an unassigned port, the VLAN management database can look up the MAC address, assign and configure the switch port to the correct VLAN. This setup requires more work initially, but can be beneficial when a user moves, because the switch will assign them to the correct VLAN automatically. Administrators use the VLAN Management Policy Server (VMPS) to create a database of MAC addresses that are mapped to VLANs. Identifying VLANs Switches must be able to keep track of all the different types of frames as they are switched throughout the network, as well as understand what to do with the frames depending on the MAC address. Frames are handled differently depending on the type of link they are traversing. There are two types of links: Access links - only part of 1 VLAN and it’s referred to as the native VLAN of the port. Any device attached to an access link is unaware of VLAN membership. Switches remove any VLAN info from the frame before it’s sent to an access-link device. Access-link devices can’t communicate outside the VLAN unless the packet is routed. Trunk links - carries multiple VLANs (between 1 and 1005) across a point-to-point link between 2 switches or a switch and server. If the link between 2 switches is not trunked, then only VLAN1 info will be switched across the link. All VLANs are configured on a trunked link. Frame Tagging When multiple VLANs are spanning multiple switches in the network, there needs to be a way for each switch to keep track of all the users and frames as they travel the switch fabric. This is where frame tagging comes in. This frame identification method uniquely assigns a user-defined ID to each frame, sometimes referred to as a “VLAN ID” or “color”. Each switch that the frame reaches must first identify the VLAN ID from the frame tag, then it looks at the info in the filter table to determine what to do with the frame. If the frame reaches a switch that has another trunked link, the frame will be forwarded out the trunk-link port. When the frame reaches an access link, the VLAN identifier is removed, so the destination device can receive the frame without understanding their VLAN identification. VLAN Identification Methods There are two trunking methods that allow switches to identify which frames belong to which VLANs – inter-switch VLAN communication: Inter-Switch Link (ISL) – proprietary to Cisco switches and used for Fast Ethernet and Gigabit Ethernet links only. IEEE 802.1Q – standard method for frame tagging, if you’re trunking between a Cisco switch and another brand of switch, you have to use 802.1Q for the trunk link to work. You must designate each 802.1Q port to be associated with a specific VLAN ID. The ports that populate the same trunk create a group known as a native VLAN and each port gets tagged with an ID number that reflects its native VLAN - default is VLAN 1. ISL Protocol ISL is a Cisco proprietary protocol that tags VLAN info onto an Ethernet frame. This tagging info allows VLANs to be multiplexed over a trunk link through an external encapsulation method (ISL), which allows the switch to identify the VLAN membership of a frame. ISL functions at layer 2 by encapsulating a data frame with a 26 byte header, 4 byte frame check sequence (FCS) and a cyclic redundancy check (CRC). Remember, the ISL header is proprietary and can only be read by devices running ISL. ISL VLAN info is only added to a frame if it is forwarded out of a trunk link. Otherwise, the info is stripped when the frame is forwarded out of a access link. VTP VLAN trunking protocol (VTP) was also created by Cisco, but it isn’t proprietary. VTP manages all configured VLANs to maintain consistency throughout the network. VTP allows an admin to add, delete and rename VLANs and then propagates this info to all other switches in the VTP domain. VLAN benefits: Consistent VLAN configuration across all switches. Allows VLANs to be trunked over mixed networks (Ethernet, FDDI). Accurate tracking and monitoring of VLANs. Dynamic reporting of added VLANs to all switches in the VTP domain. Plug-and-play VLAN adding. VTP Operation Before you can get VTP to manage your VLANs, you have to create a VTP server. All VTP servers that need to share VLAN info must use the same domain name and a switch can only be in one domain at a time. VTP info is sent between switches over a trunk port. Switches advertise VTP management domain info, configuration revision number and all known VLANs with any specific parameters. VTP Operation Modes There are 3 different modes of operation within a VTP domain: Server – this is the default for all Catalyst switches. You need at least 1 server in your VTP domain to propagate VLAN info. The switch must be in server mode to create, delete or rename VLANs and those changes will be advertised to the entire VTP domain. Client – in client mode, switches receive info from VTP servers, they send and receive updates, but can’t make any changes. The ports of a client switch can be added to a new VLAN before the VTP server notifies the client switch of the new VLAN. Transparent – switches in transparent mode don’t participate in the VTP domain, but they’ll still forward VTP advertisements through trunk links. These switches don’t share info with other switches, because their VLAN databases are locally significant only. VTP Pruning VTP pruning only sends broadcasts to trunk links that need the information, which helps preserve bandwidth. By default, VTP pruning is disabled. When you enable VTP pruning, it will be set for the entire domain with VLANs 2-1005 being eligible. VLAN 1 can never be pruned because it is an administrative VLAN. Here’s an example of how it works: If switch A doesn’t have any ports configured for VLAN 5 and a broadcast is sent throughout VLAN 5, the broadcast wouldn’t traverse the trunk link to switch A. Routing Between VLANs Host can communicate within their own VLAN by default, but in order for separate VLANs to communicate, a layer 3 device is needed. There are two different ways to configure a router with VLANs. One way is to have a router configured with a VLAN per (sub)interface, so there is an individual VLAN association to the router. The other way is to have all VLANs use one router interface, which Cisco calls “router on a stick”. Router With Individual VLAN Associations Router-on-a-stick Exam Essentials Know when VLANs are used and why Understand the term “frame tagging” Understand the ISL VLAN identification method Understand the 802.1Q VLAN identification method Understand VTP operation Know the VTP operation mode END Chapter 4 Virtual LANs