Slide #9
advertisement

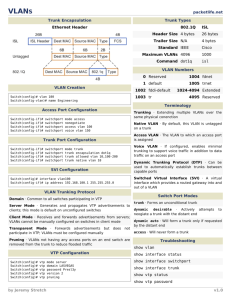
• Verify that management VLAN has been reassigned. • Verify that operational VLANs do not have access to the management VLAN. • Verify that the ports in the management VLAN are not configured as trunks. • • • A trunk is a point-to-point link between two network devices that carries traffic for more than one VLAN. A trunk allows you to extend the VLANs across an entire network. A trunk does not belong to a specific VLAN, rather it is a conduit for VLANs between switches and routers. • • • • DTP is implemented by default on Cisco switches . DTP automatically negotiates how the port will operate, trunk or access mode. By default, a Cisco Ethernet port's default DTP mode is "dynamic desirable”, which enables a port to go to trunk mode automatically. Review the switch configuration to verify that DTP is disabled. VTP is a Cisco-proprietary messaging protocol used to distribute VLAN configuration information over trunks. A switch may be in one of three VTP modes: server, transparent and client. In server mode administrators can create, modify and delete VLANs for the entire VTP management domain. By default, VTP – no authentication and the switch is in VTP Server mode. • If VTP is necessary, verify the following: • VTP management domain is established. • A strong password is assigned to the VTP management domain. • Non-management switches are configured in client mode. • • • By auditing device for these basic hardening steps, overall security of the network can be improved. However, in all cases, a comprehensive review should be performed. Reference the works cited page for links to documented security configuration benchmarks and checklists. Mark Krawczyk mwkrawczyk@charter.net Router Security Guidance Activity of the System and Network Attack Center (SNAC), 2005 http://www.nsa.gov/ia/_files/routers/C4-040R-02.pdf Cisco IOS Switch Security Configuration Guide, http://www.nsa.gov/ia/ Center for Internet Security, http://benchmarks.cisecurity.org/downloads/audit-tools/ US-Cert, https://www.us-cert.gov/security-publications Information Assurance Support Environment, http://iase.disa.mil/stigs/ SANS Institute InfoSec Reading Room - Cisco Router Hardening Step-by-Step www.sans.org Cisco Checklist - www.sans.org Configuring a Cisco Router with TACACS+ Authentication. http://www.cisco.com/c/en/us/support/docs/security-vpn/terminal-access-controlleraccess-control-system-tacacs-/13865-tacplus.html Cisco Guide to Harden Cisco IOS Devices, Document ID: 13608 http://www.cisco.com/c/en/us/support/docs/ip/access-lists/13608-21.html Various Articles related to Cisco device security, http://www.ciscopress.com/articles/ NIST – National Vulnerability Database http://web.nvd.nist.gov/ ISACA – www.isaca.org