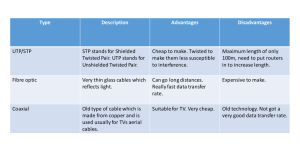
4.4.1 The 802.11 Protocol Stack
advertisement

4.4 WIRELESS LANS 4.4.1 The 802.11 Architecture • The main wireless LAN standard is 802.11. • Informally the technology is called WiFi (wireless fidelity). • 802.11 networks can be used in two modes. – infrastructure mode. – ad hoc mode. • Infrastructure mode is the most popular mode which is used to connect clients, such as laptops and smart phones, to another network, such as a company intranet or the Internet. 2 Infrastructure Mode • In infrastructure mode, each client is associated with an AP (Access Point) that is in turn connected to the other network. The client sends and receives its packets via the AP. • Several access points may be connected together, typically by a wired network called a distribution system, to form an extended 802.11 network. In this case, clients can send frames to other clients via their APs. 3 4.4.1 The 802.11 Architecture 4 Ad Hoc Mode • The ad hoc mode is a collection of computers that are associated so that they can directly send frames to each other. • There is no access point. Since Internet access is the killer application for wireless, ad hoc networks are not very popular. 5 4.4.1 The 802.11 Architecture 6 4.4.1 The 802.11 Protocol Stack(Data Link Layer) • The data link layer In 802.11 as well as in all the 802 protocols is split into two or more sublayers: – the MAC (Medium Access Control) sublayer determines how the channel is allocated, that is, who gets to transmit next. – Above it is the LLC (Logical Link Control) sublayer, whose job it is to • hide the differences between the different 802 variants technologies • and make them indistinguishable as far as the network layer is concerned (provide an interface to the network layer). 7 4.4.1 The 802.11 Protocol Stack (physical layer) • Several transmission techniques have been added to the physical layer as 802.11 has evolved since it first appeared in 1997. – infrared in the manner of television remote controls. – frequency hopping in the 2.4-GHz band. – direct sequence spread spectrum at 1 or 2 Mbps in the 2.4-GHz band, It is now known as 802.11b. 8 4.4.1 The 802.11 Protocol Stack • To give wireless junkies a much-wanted speed boost, new transmission OFDM (Orthogonal Frequency Division Multiplexing)scheme introduced in 1999 and 2003. – 802.11a and uses a different frequency band, 5 GHz. – 802.11g with 2.4 GHz. Both give rates up to 54 Mbps. • Most recently, transmission techniques that simultaneously use multiple antennas at the transmitter and receiver for a speed boost were finalized as 802.11n in Oct. 2009. With four antennas and wider channels, the 802.11 standard now defines rates up to a startling 600 Mbps. 9 4.4.1 The 802.11 Protocol Stack 10 4.4.5 Services • The 802.11 standard defines the services that the clients, the access points, and the network connecting them must be a conformant wireless LAN. These services cluster into several groups. 11 4.4.5 Services • The association service – Used by mobile stations to connect themselves to APs. – It is used just after a station moves within radio range of the AP. – The capabilities include • • • • the data rates supported security arrangements power-saving capabilities quality of service support, and more. – The station sends a request to associate with the AP. The AP may accept or reject the request. 12 4.4.5 Services • The Reassociation service – lets a station change its preferred AP. – useful for mobile stations moving from one AP to another AP in the same extended 802.11 LAN, like a handover in the cellular network. 13 4.4.5 Services • The Authentication service – Stations authenticate before they can send frames via the AP, but authentication is handled in different ways depending on the choice of security scheme. If the 802.11 network is ‘‘open,’’ anyone is allowed to use it. Otherwise, credentials are needed to authenticate. – The recommended scheme, called WPA2 (WiFi Protected Access 2) – With WPA2, the AP can talk to an authentication server that has a username and password database to determine if the station is allowed to access the network. 14 4.4.5 Services • The integration service – handles any translation that is needed for a frame to be sent outside the 802.11 LAN, or to arrive from outside the 802.11 LAN. – The common case here is connecting the wireless LAN to the Internet. • Data delivery service. – This service lets stations transmit and receive data using the protocols described earlier. 15 4.4.5 Services • The privacy service – Wireless is a broadcast signal. For information sent over a wireless LAN to be kept confidential, it must be encrypted. – manages the details of encryption and decryption. – The encryption algorithm for WPA2 is based on AES (Advanced Encryption Standard). – The keys that are used for encryption are determined during the authentication procedure. 16 4.4.5 Services • QOS traffic scheduling service. – To handle traffic with different priorities, It uses the protocols we described to give voice and video traffic preferential treatment compared to besteffort and background traffic. • A companion service – provides higher-layer timer synchronization. This lets stations coordinate their actions, which may be useful for media processing.. 17 4.4.5 Services • The transmit power control service – gives stations the information they need to meet regulatory limits on transmit power that vary from region to region. • The dynamic frequency selection service – give stations the information they need to avoid transmitting on frequencies in the 5-GHz band that are being used for radar in the proximity. 18 4.5 BROADBAND WIRELESS broadband • broadband refers to telecommunication in which a wide bandwidth of frequencies that are available to transmit information. • Broadband can allow remote stations(devices) to connect to a central station at high speeds. 20 Broad Band Technologies • Telephone System Broad Band Technologies – Plain old telephone service (POTS) – Integrated Services for Digital Network (ISDN) – Digital subscriber line (DSL) • Cable Television Technology • Satellites Technology • Cellular Communication Technology – (BroadBand Wireless) 21 4.5 BROADBAND WIRELESS • The problem is that running fiber or coax to millions of homes and businesses is prohibitively expensive. What is a competitor to do? • The answer is broadband wireless. Erecting a big antenna on a hill just outside of town is much easier and cheaper than digging many trenches and stringing cables. 22 4.5 BROADBAND WIRELESS • Thus, companies provide multimegabit wireless communication services for voice, Internet, movies on demand, etc. • The Broadband Wireless standard metropolitan area network (MAN) is 802.16. • Informally the technology is called WiMAX (Worldwide Interoperability for Microwave Access). 23 4.5.1 Comparison of 802.16 with 802.11 (similarities) • At this point you may be thinking: why devise a new standard? Why not just use 802.11? – Like 802.11, WiMAX connect devices to the Internet at megabit/sec speeds wirelessly, instead of using cable or DSL. The devices may be mobile, or at least portable. – The packets may carry traffic, VoIP calls, or streaming media to support a range of applications. – Also like 802.11, 802.16 is based on OFDM technology to ensure good performance in spite of wireless signal different problems. 24 4.5.1 Comparison of 802.16 with 802.11 (differences) • However, WiMAX unlike 802.11. WiMAX achieves high capacity by the efficient use of spectrum, so that a large number of subscribers in a coverage area can all get high throughput. How? – WiMAX base stations are more powerful than 802.11 Access Points (APs)( The typical distances are at least 10 times larger than for an 802.11 network). – The WiMAX base station uses more power and better antennas, and it performs more processing to handle errors and weaker signals over larger distances. – WiMAX maximizes throughput, by carefully schedules transmissions by the base station for each particular subscriber. 25 4.5.2 The 802.16 Architecture • The 802.16 architecture : Base stations connect directly to the provider’s backbone network, which is in turn connected to the Internet. • The base stations communicate with stations over the wireless air interface. Two kinds of stations exist: – Subscriber stations remain in a fixed location, for example, broadband Internet access for homes. – Mobile stations can receive service while they are moving, for example, a car equipped with WiMAX. 26 4.5.2 The 802.16 Architecture 27 4.5.2 The 802.16 Protocol Stack (Physical Layer) • The general structure is similar to that of the other 802 networks, but with more sublayers. • The bottom layer (physical layer) deals with transmission, and here we have shown only the popular offerings of 802.16, fixed and mobile WiMAX. – There is a different physical layer for each offering. Both layers operate in licensed spectrum below 11 GHz and use OFDM, but in different ways. 28 4.5.2 The 802.16 Protocol Stack 29 4.5.2 The 802.16 Protocol Stack (Data Link Layer) • The data link layer consists of three sublayers. – Security layer – MAC common layer – The service-specific convergence sublayer • The bottom one (Security layer) deals with privacy and security, which is far more crucial for public outdoor networks than for private indoor networks. It manages encryption, decryption, and key management. 30 4.5.2 The 802.16 Protocol Stack (Data Link Layer)2 • The MAC common sublayer. This part is where the main protocols, such as channel management, are located. • the base station completely controls the system; It can schedule the downlink (i.e,base to subscriber) channels very efficiently and plays a major role in managing the uplink (i.e., subscriber to base) channels as well. • An unusual feature of this MAC sublayer is that, (unlike those of the other 802 protocols), it is completely connection oriented, in order to provide quality of service guarantees for telephony and multimedia communication. 31 4.5.2 The 802.16 Protocol Stack (Data Link Layer)3 • The service-specific convergence sublayer takes the place of the logical link sublayer in the other 802 protocols. Its function is to – provide an interface to the network layer. – Different convergence layers are defined to integrate seamlessly with different upper layers. (hide the differences between the different 802 technologies) 32 4.6 BLUETOOTH Wireless Networks PAN 802.15.x 10m LAN 802.11 100m MAN 802.16 2-6km WAN 2G, 3G 2km/link national areas Overview of wireless networks 34 Bluetooth • Bluetooth wireless technology is a short-range communications technology intended to replace the cables connecting portable and/or fixed devices while maintaining high levels of security. • The key features of Bluetooth technology are – Short Range and Small Networks – robustness, – low power, – and low cost. • IEEE 802.15 is the 15th working group of the IEEE 802 which specializes in Wireless PAN (Personal Area Network including Bluetooth) standards. • The Bluetooth specification defines a uniform structure for a wide range of devices to connect and communicate with each other. www.bluethooth.com 35 Bluetooth Application Areas • Data and voice access points – Real-time voice and data transmissions • Cable replacement – Eliminates need for numerous cable attachments for connection • Ad hoc networking – Device with Bluetooth radio can establish connection with another when in range 36 What does Bluetooth do for you? Landline Cable Replacement Data/Voice Access Points Personal Ad-hoc Networks 37 4.6.1 Bluetooth Architecture • The basic unit of a Bluetooth system is a piconet; – A Piconet: it consists of a master node (for synchronization purposes) and up to seven active slave nodes within a distance of 10 meters. • Multiple piconets can exist in the same (large) room and can even be connected via a bridge node that takes part in multiple piconets; – A Scatternet : is interconnected collection of piconets. 38 4.6.1 Bluetooth Architecture 39 4.6.1 Bluetooth Architecture • In addition to the seven active slave nodes in a piconet, there can be up to 255 parked nodes in the net. These are devices that the master has switched to a low power state to reduce the drain on their batteries. • In parked state, a device cannot do anything except respond to an activation or signals from the master. 40 4.6.1 Bluetooth Architecture • The reason for the master/slave design is that the designers intended to facilitate the implementation of complete Bluetooth chips for under $5. • The consequence of this decision is that the slaves are fairly dumb, basically just doing whatever the master tells them to do. • All communication is between the master and a slave; direct slave-slave communication is not possible. 41 Features of Bluetooth Technology • Bluetooth is based upon small, high performance integrated radio transceivers, each of which is allocated a unique 48-bit address derived from the IEEE 802 standards. • It operates in the unrestricted 2.4 GHz ISM "free band", which is available globally, although slight variation of location and width of band apply. • Bluetooth uses the unlicensed ISM (Industrial, Scientific and Medical) band, 2400 - 2483.5 MHz, thereby maximizing communication compatibility worldwide • The range is set at 10 meters to optimize for target market of mobile and business user. The range can, however, be increased to 100 meters. • Gross data rate is 1Mbit/s, with second generation providing increase to 2Mbit/s, and further to 3Mbits/s 42