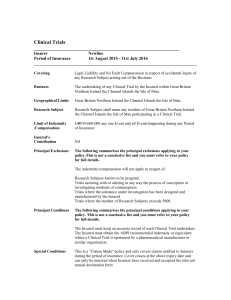
Introduction - Economics of Security
advertisement

Cyberinsurance As A Market-Based
Solution To the Problem of Cybersecurity
Jay Kesan Ruperto Majuca* William Yurcik*
College of Law
Department of Economics
NCSA
University of Illinois at Urbana-Champaign
{kesan,majuca,yurcik}@uiuc.edu
Workshop on the Economics of Information Security ‘05
Harvard University
Outline
Emergence of Cyberinsurance
Current Cyberinsurance Practices
Economic Theory
Ideal World
Real World
Summary
Outline
Emergence of Cyberinsurance
Current Cyberinsurance Practices
Economic Theory
Ideal World
Real World
Summary
The Problem
Pervasive software vulnerabilities & increased
availability of hacking tools have resulted in a
consistently increasing myriad of attacks:
host-based attacks (theft of credit card numbers, invasion
of privacy, etc.)
insider attacks that damage information assets
network DoS availability attacks
Surveys consistently show ~75% of businesses
suffer financial losses due to security breaches
InformationWeek estimates annual losses (in the
USA) due to security breaches at billions of dollars
Why Is This Happening?
Why Is This Happening?
Security Market Failure
Why Is This Happening?
Security Market Failure
1.
Imperfect information
2.
Externalities
3.
Consumers do not know security of software
Security is interdependent and damage is not
fully borne by “guilty” parties
Security as a Public Good
Risks are shared but incentive to free-ride
Correcting Market Failure
1.
Imperfect Information
2.
Perfect information may not be possible
Externalities
Assign cyber-property rights through laws
enforcement is slow with high transaction costs
3.
Security as Public Good
International regulation for broad protections
funding, long timeframe, divergent interests
Risk Management Market Solutions
1. Avoid the Risk
Disconnect from the Internet
2. Mitigate the Risk
Security processes to reduce magnitude of expected loss
3. Retain the Risk
Self-insurance or gambling
4. Transfer the Risk via Contract
Guarantees/warranties, service agreements, outsourcing
5. Transfer the Risk via an Insurance Product
Insurance premiums internalized as cost-of-doing-business
Risk Management Market Solutions
1. Avoid the Risk
Disconnect from the Internet
2. Mitigate the Risk
Security processes to reduce magnitude of expected loss
3. Retain the Risk
Self-insurance or gambling
4. Transfer the Risk via Contract
Guarantees/warranties, service agreements, outsourcing
5. Transfer the Risk via an Insurance Product
Insurance premiums internalized as cost-of-doing-business
Inadequacy of Traditional Insurance
Traditional insurance policies
designed to cover traditional perils
cyber-risks are new
time dynamics; attacks & software flaws exposed daily
Cyber-properties are without physical form
attacks do not leave physical damage
insurers dispute what constitutes “physical” damage to
“tangible” property, draft more exclusions, and offer new
insurance products to stack case against inclusion
Most cyber-torts are international
most 3rd party insurance coverage are not international
Outline
Emergence of Cyberinsurance
Current Cyberinsurance Practices
Economic Theory
Ideal World
Real World
Summary
Net Advantage
Security
e-Comprehensive
Destruction, disruption or theft of
information assets
Y
Y
Y
Internet Business Interruption
Y
Y
Y
Cyberextortion
Y
Y
Y
Fraudulent electronic transfers
N
Y
N
Denial of service attack
Y
Y
Rehabilitation expenses
Y
Y
Insurance
Coverage
Webnet
Protection
FIRST PARTY
THIRD PARTY LIABILITY
Internet Content
Y
Y
Y
Internet Security
Y
Y
Y
Defense Costs
Y
Y
Y
Inability to use or lack of performance
of software programs
Y
Y
Y
Ordinary wear and tear of insured’s
information assets
Y
Y
Y
Electric and telecommunication
failures
Y
Y
Y
EXCLUSIONS
Net Advantage
Security
e-Comprehensive
Destruction, disruption or theft
of information assets
Y
Y
Y
Internet Business Interruption
Y
Y
Y
Cyberextortion
Y
Y
Y
Fraudulent electronic transfers
N
Y
N
Denial of service attack
Y
Y
Rehabilitation expenses
Y
Y
Insurance
Coverage
Webnet
Protection
FIRST PARTY
THIRD PARTY LIABILITY
Internet Content
Y
Y
Y
Internet Security
Y
Y
Y
Defense Costs
Y
Y
Y
Inability to use or lack of performance
of software programs
Y
Y
Y
Ordinary wear and tear of insured’s
information assets
Y
Y
Y
Electric and telecommunication
failures
Y
Y
Y
EXCLUSIONS
Net Advantage
Security
e-Comprehensive
Destruction, disruption or theft of
information assets
Y
Y
Y
Internet Business Interruption
Y
Y
Y
Cyberextortion
Y
Y
Y
Fraudulent electronic transfers
N
Y
N
Denial of service attack
Y
Y
Rehabilitation expenses
Y
Y
Insurance
Coverage
Webnet
Protection
FIRST PARTY
THIRD PARTY LIABILITY
Internet Content
Y
Y
Y
Internet Security
Y
Y
Y
Defense Costs
Y
Y
Y
Inability to use or lack of performance
of software programs
Y
Y
Y
Ordinary wear and tear of insured’s
information assets
Y
Y
Y
Electric and telecommunication
failures
Y
Y
Y
EXCLUSIONS
Net Advantage
Security
e-Comprehensive
Destruction, disruption or theft of
information assets
Y
Y
Y
Internet Business Interruption
Y
Y.
Y
Cyberextortion
Y
Y
Y
Fraudulent electronic transfers
N
Y
N
Denial of service attack
Y
Y
Rehabilitation expenses
Y
Y
Insurance
Coverage
Webnet
Protection
FIRST PARTY
THIRD PARTY LIABILITY
Internet Content
Y
Y
Y
Internet Security
Y
Y
Y
Defense Costs
Y
Y
Y
Inability to use or lack of
performance of software
Y
Y
Y
“Software Aging” of
insured’s information assets
Y
Y
Y
Electric and telecommunication
failures
Y
Y
Y
EXCLUSIONS
Outline
Emergence of Cyberinsurance
Current Cyberinsurance Practices
Economic Theory
Ideal World
Real World
Summary
Ideal World (our previous work)
1. Cyberinsurance increases IT Safety because the
insured increases self-protection as rational
response to the reduction of premium
2. Cyberinsurance facilitates standards of liability
3. Cyberinsurance increases social welfare by solving
market failure (Internet risks transfer)
Measuring Welfare Gains
Income in good state
A
|Slope| =
price of insurance
Welfare gains
measure
B
Certainty line
E
I1e
expenditure
on insurance
F
I*
I**
45o
Amount of insurance
coverage
I0e
I**
I*
Income in bad state
Income in good state
A
$ 47.04 million
|slope|= .06
B
Certainty line
$ 3.14 Bn
I**
45o
$ 1.94 Bn
I**
Income in bad state
Example: 2000 DOS attacks
Calculating the Premiums
Following Cochrane (1997), total premiums insured
is willing to pay may be calculated:
1
( I m ) (1 ) p I 0e
1
(1 p) I1e
where I m p I 0e (1 p) I1e .
Solving for Π:
Im p I
e1
0
(1 p) I
1
e1 1
1
.
Calculated welfare gains and premiums for different
risk aversion levels and probabilities of cyber-loss
results: increasing social welfare and premiums with
probability of attack and risk aversion
Real World
Adverse Selection
insurers cannot distinguish between high and low risk
Moral Hazard
firms may slack in their security work after being insured
Others
lack of actuarial data, pricey premiums, interrelated risks
Adverse Selection
Separate high/low risk using risk assessment
Income in good state
Certainty line
Welfare
Loss
Measure
A
Ap
B
E
P
FL
FH
45o
I0 p
IfH
IfL
Income in bad state
Adverse Selection
Income in good state
Certainty line
Welfare
Loss
Measure
A
Ap
B
E
P
FL
FH
45o
I0 p
IfH
IfL
Income in bad state
Adverse Selection
Income in good state
Certainty line
Welfare
Loss
Measure
A
Ap
B
E
P
FL
FH
45o
I0 p
IfH
IfL
Income in bad state
Adverse Selection
Income in good state
Certainty line
Welfare
Loss
Measure
A
Ap
B
E
P
FL
FH
45o
I0 p
IfH
IfL
Income in bad state
Adverse Selection
Income in good state
Certainty line
Welfare
Loss
Measure
A
Ap
B
E
P
FL
FH
45o
I0 p
IfH
IfL
Income in bad state
Adverse Selection
Income in good state
Certainty line
Welfare
Loss
Measure
A
Ap
B
E
P
FL
FH
45o
I0 p
IfH
IfL
Income in bad state
Solution to Adverse Selection
Evaluation of applicants’ security through
offsite and on-site activities
detailed questionnaire: assesses applicant’s risks
exposure, services offered, and network security
baseline risk assessment: physical location’s
security, network’s design and activities, physical
review of security, incident response, procedures etc.
recommendations for upgrades and fixes
Solutions to Moral Hazard
Net Advantage
Security
e-Comprehensive
Failure to back-up
Y
Y
Y
Failure to take reasonable steps to
maintain and upgrade security
Y
Y
Y
Retentions
Y
Y
Y
Liability Limits
Y
Y
Y
Criminal Reward Fund/
Investigative Expenses Covered
Y
Policy Provisions
Webnet
Protection
EXCLUSIONS
OTHER RELEVANT PROVISIONS
Services by Information Risk Group to
mitigate the impact of 1st party loss,
covered
Y
Y
Representations Relied Upon
Y
Y
Y
Regular/Annual Surveys of Insured’s
Facilities
Y
Y
Y
Solutions to Moral Hazard
Net Advantage
Security
e-Comprehensive
Failure to back-up
Y
Y
Y
Failure to take reasonable steps
to maintain and upgrade security
Y
Y
Y
Retentions
Y
Y
Y
Liability Limits
Y
Y
Y
Criminal Reward Fund/
Investigative Expenses Covered
Y
Policy Provisions
Webnet
Protection
EXCLUSIONS
OTHER RELEVANT PROVISIONS
Services by Information Risk Group to
mitigate the impact of 1st party loss,
covered
Y
Y
Representations Relied Upon
Y
Y
Y
Regular/Annual Surveys of Insured’s
Facilities
Y
Y
Y
Solutions to Moral Hazard
Net Advantage
Security
e-Comprehensive
Failure to back-up
Y
Y
Y
Failure to take reasonable steps to
maintain and upgrade security
Y
Y
Y
Retentions
Y
Y
Y
Liability Limits
Y
Y
Y
Criminal Reward Fund/
Investigative Expenses Covered
Y
Policy Provisions
Webnet
Protection
EXCLUSIONS
OTHER RELEVANT PROVISIONS
Services by Information Risk
Group to mitigate the impact of
1st party loss, covered
Y
Y
Representations Relied Upon
Y
Y
Y
Regular/Annual Surveys of Insured’s
Facilities
Y
Y
Y
Solutions to Moral Hazard
Net Advantage
Security
e-Comprehensive
Failure to back-up
Y
Y
Y
Failure to take reasonable steps to
maintain and upgrade security
Y
Y
Y
Retentions
Y
Y
Y
Liability Limits
Y
Y
Y
Criminal Reward Fund/
Investigative Expenses Covered
Y
Policy Provisions
Webnet
Protection
EXCLUSIONS
OTHER RELEVANT PROVISIONS
Services by Information Risk Group to
mitigate the impact of 1st party loss,
covered
Y
Y
Representations Relied Upon
Y
Y
Y
Regular/Annual Surveys of
Insured’s Facilities
Y
Y
Y
Solutions to Moral Hazard
Net Advantage
Security
e-Comprehensive
Failure to back-up
Y
Y
Y
Failure to take reasonable steps to
maintain and upgrade security
Y
Y
Y
Retentions
Y
Y
Y
Liability Limits
Y
Y
Y
Criminal Reward Fund/
Investigative Expenses Covered
Y
Policy Provisions
Webnet
Protection
EXCLUSIONS
OTHER RELEVANT PROVISIONS
Services by Information Risk Group to
mitigate the impact of 1st party loss,
covered
Y
Y
Representations Relied Upon
Y
Y
Y
Regular/Annual Surveys of Insured’s
Facilities
Y
Y
Y
Outline
Emergence of Cyberinsurance
Current Cyberinsurance Practices
Economic Theory
Ideal World
Real World
Summary
Summary
In Theory - cyberinsurance can correct Internet risk
transfer market failure (economic modeling)
In Practice - cyberinsurers are slowly resolving realworld problems but some issues are still remain
(case study results)
Cyberinsurance is still the direction but it will take
time, patient perseverance rather than giving up on
this market solution.
Questions?
<http://www.ncassr.org/projects/econsec/>
backup slides
Insurance and Interdependent
Risks
IT security is interdependent, e.g., an infected
machine can cause infection of others
Ortzag and Stiglitz 2002:
Two distortions: interdependent risks results in care
below the social optimum & insurance coverage also
reduces the precaution level.
But if level of precaution can be observed and
insurance premium tied to precaution level, moral
hazard disappears & full insurance ensue
Suggestions (regulation, taxes and fees)
Developing Cyberliability Law
Higher standards for certain firms/activities:
Financial firms: prevent data in databases from being leaked
out or used for identity theft (GLB Act & security regulations)
Health care providers: ensure integrity/security of protected
health information (HIPAA & security regulations)
Firms that gather data relating to children to safeguard it
Those covered by consent decrees; others
Those not covered by specific regulations and
consent decrees have general common law duty to
safeguard data under their control.
Cyberinsurance, Self-Insurance and
Self-protection
Cyberinsurance
“Complements” if premiums
tied to self-protection level.
(Cyberinsurance increases
self-protection, i.e.
no moral hazard)
“Substitutes”:
(High demand
for one lowers
the other’s)
Self-insurance
“Substitutes”
(Availability of one would
discourage the other.
Self-insurance likely to
create a “moral hazard”)
Self-protection
Socially-Optimal Precaution Level
$
E(SC)=p(x)L+wx total social costs
wx
p(x)L
0
X*
precaution costs
expected losses
Precaution
Efficiency requires minimizing total costs; occurs if
w
=
- p’(x*)L
(marginal social cost)
(marginal social benefit)
Cyberinsurance Premiums
and Welfare Gains (in Millions)
Risk Aversion
1
1.5
2
2.5
3
Premium
p= γ = 0.005
0.01
0.02
0.03
0.04
0.05
0.06
$1.55
$3.08
$6.09
$9.03
$11.90
$14.69
$17.42
$2.54
$5.02
$9.90
$14.64
$19.25
$23.72
$28.07
$3.67
$7.29
$14.34
$21.17
$27.76
$34.14
$40.30
$5.03
$9.96
$19.54
$28.75
$37.60
$46.10
$54.26
$6.62
$13.10
$25.60
$37.54
$48.93
$59.79
$70.15
Welfare Gains
p= γ = 0.005
0.01
0.02
0.03
0.04
0.05
0.06
$1.59
$3.23
$6.69
$10.37
$14.28
$18.41
$22.76
$2.57
$5.19
$10.58
$16.17
$21.95
$27.92
$34.08
$3.73
$7.49
$15.12
$22.89
$30.80
$38.85
$47.04
$5.09
$10.18
$20.41
$30.70
$41.03
$51.41
$61.84
$6.69
$13.35
$26.60
$39.75
$52.81
$65.79
$78.69