Maritime Cyber Security in the Commercial Cargo Control sector
advertisement

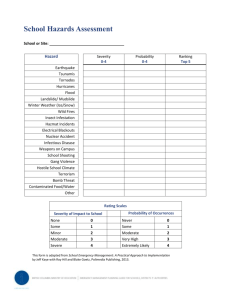
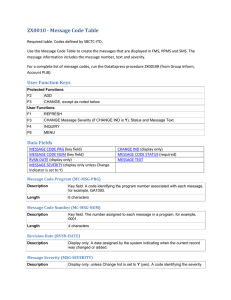
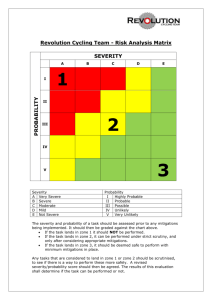
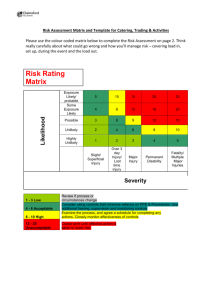
Maritime Cyber Security in the Commercial Cargo Control sector Justin Dunning The Mission • Follow the cargo through its voyage • Observe all of the touch points that a container goes through • Determine if those touch points are susceptible to a cyber attack • Once vulnerabilities are detected, determine the following: • • Possibility Severity Who Would Disturb the Flow? • Drug Cartels • • Drug trade is worth $435 Billion Increased from $320 Billion in 2005 • Arms Distributors • Arms trade is worth between $45-60 Billion a year • Thieves • Can make a decent amount of money on the black market Who and What are Vulnerable? • RFID Tags • Possibility: High • • No uniformity= easily counterfeited Severity: High • Could contribute to drug, arms trade, and theft • Freight Forwarder/3PL • Possibility: High • • Email information is easily attackable Severity: High • Contribute to high confusion in ports halting operations Who and What are Vulnerable? • Algorithms • Possibility: Low • • Must be highly skilled to decrypt these Severity: High • Could alter the position on the vessel • Electronic Data Interchange (EDI) • Possibility: Medium • • Makes it possible for many people to view Severity: Medium • Has the potential to effect the flow of supply chain because information is not confidential to necessary personnel Who and What are Vulnerable? • The Ports • Possibility: Low • • Take measures to protect but wont be 100% protected Severity: High • If this happens, halting the port for numerous days would affect the local economy • DDoS Attack • Possibility: Low • • Measures put in place to protect their servers Severity: High • This would shut down every port function at the same time