Advantages and disadvantages
advertisement
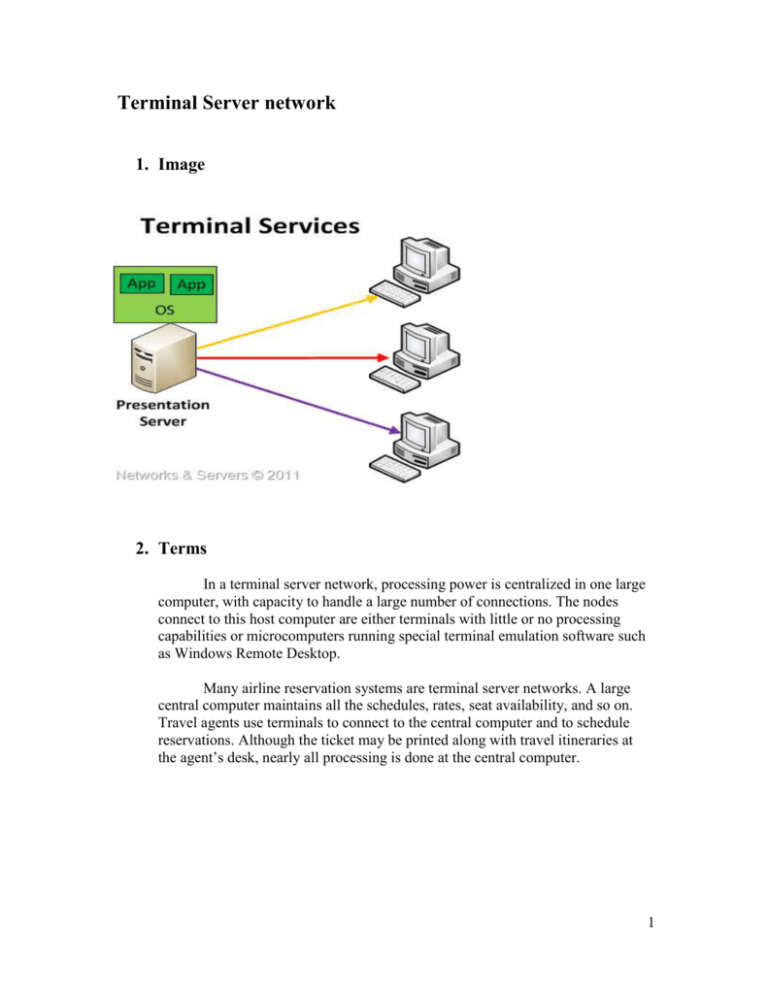
Terminal Server network 1. Image 2. Terms In a terminal server network, processing power is centralized in one large computer, with capacity to handle a large number of connections. The nodes connect to this host computer are either terminals with little or no processing capabilities or microcomputers running special terminal emulation software such as Windows Remote Desktop. Many airline reservation systems are terminal server networks. A large central computer maintains all the schedules, rates, seat availability, and so on. Travel agents use terminals to connect to the central computer and to schedule reservations. Although the ticket may be printed along with travel itineraries at the agent’s desk, nearly all processing is done at the central computer. 1 3. Advantages and disadvantages No. Advantages Disadvantages 1 One advantage of terminal server networks is the centralized location and control of technical personnel, software, and data. One disadvantage is the lack of control and flexibility for the end user. 2 Low-Bandwidth Access to Data: Terminal services reduce the amount of network baQd width that is required to access data from. The remote computer-Data only in the form of screen views are transmitted. Over this bandwidthconstrained it is very successful combination for remotely manipulating large amounts of data. Another disadvantage is that terminal server networks do not use the full processing power available with microcomputers. 3 Helps enable branch-office access to feature-rich applications using lower bandwidth. The terminal server is the major source of risk of downtime. If the terminal server fails, the whole system fails unless a fail-over terminal server is in place. 4 Centralized application hosting. Effectively deliver applications across the enterprise to meet different needs, without straining network resources or exposing corporate data to unnecessary risks. The functionality of the system as a whole is also affected by the network reliability. If the network is down, the whole system is down as well. 5 Cost-effective application management. Reduce the cost and challenges of maintaining desktop machines with applications that are frequently update, infrequently used, or hard to install- or that need to be accessed over low-bandwith connections. Running applications from a terminal server can also be an issue from performance perspective. In some cases, no matter how good the network is, the performance associated with running an application locally on a desktop workstation can still overshadow the benefits of a terminal server environment. 2 Client Server Network 1. Image 2. Terms Client/server networks use central computers to coordinate and supply services to other notes on the network. The server provides access to resources such as Web page, databases, application software, and hard ware. This strategy is based on specialized. Server nodes request the services. Commonly used server operating systems are Windows Server, Mac OS X Server, Linux, and Solaris. Client/ server network are widely used on the internet. For example, each time you open a Web browser, your computer ( the client) send out the request is routed over the internet to a server. This server locates and sends material back to your computer. 3 3. Advantages and disadvantages No. Advantages Disadvantages 1 One advantage of client/ server network strategy is the ability to handle very large networks efficiently. The major disadvantage is the cost installation and maintenance. 2 Another advantage is the availability of powerful network management software to monitor and control network activities. When the server goes down or crashes. All the computers connected to it become unavailable to use. 3 A Client Sever Can Be scaled up to many services that can also be used by multiple users. 4 A client server enables the roles and responsibilities of a computing system. This means that it can update all the computers connected to it. An example of this would be software updates or hardware updates. When everyone tries to do the same thing it takes a little while for the server to do certain tasks. An example of this would be everyone logging into their profile in an organization or a college at the same time. More expensive than a peer to peer network. You have to pay for startup cost. 5 The security is a lot more advanced than a peer to peer network. You can have passwords to your won profile so that no one can access everything when they want. 6 Many mature client-server technologies are already available which were designed to ensure security, 'friendliness' of the user interface, and ease of use. 7 When you expand the server it starts to slow down due to the Bit rate per second. Comparing client-server model to the P2P model, if one server fail, clients’ requests cannot be served but in case of P2P networks, servers are usually distributed among many nodes. Even if one or more nodes fail, for example if a node failed to download a file the remaining nodes should still have the data needed to complete the download. It functions with multiple different clients of different capabilities. 4 Peer-to-peer (P2P) network 1. Image 2. Terms Peer-to-peer (P2P) computing or networking is a distributed application architecture that partitions tasks or workloads among peers. Peers are equally privileged, equipotent participants in the application. They are said to form a peer-to-peer network of nodes. Peers make a portion of their resources, such as processing power, disk storage or network bandwidth, directly available to other network participants, without the need for central coordination by servers or stable hosts. Peers are both suppliers and consumers of resources, in contrast to the traditional client– server model where only servers supply (send), and clients consume (receive). The peer-to-peer application structure was popularized by file sharing systems like Napster. The concept has inspired new structures and philosophies in many areas of human interaction. Peer-to-peer networking is not restricted to technology, but covers also social processes with a peer-topeer dynamic. In such context, social peer-to-peer processes are currently emerging throughout society. 5 3. Advantages and disadvantages No. Advantages Disadvantages 1 A peer to peer network is inexpensive to set up. One disadvantage of P2P networks is the lack of security controls or other common management functions. So, you can set passwords for files that you don’t want people to access but apart from that the security is pretty poor. It uses the built in networking capabilities of Windows XP Professional (or Vista Business), so no special software is needed. It allows for file and printer sharing, and can be an adequate choice for a very small office. For this reason, few businesses use this type of network to communicate sensitive information. 2 You can access any file on the computer as long as it is set to shared folder. If you have not connected the computers together properly then there can be problems accessing certain files. 3 The requirements for a Peer to Peer Network are that you have a 10 Base T Ethernet cable and an Ethernet hub/ switch. This is rather cheap than having a server. It doesn’t always work if you have many computers and works better with 2 – 8 computers. 4 The architecture of the lay out (How It Connects) is simple. Lack of system administrator. 5 If one computer fails to work all the other computers connected to it continue to work. 6 Distributed processing network 1. Image 2. Term In a distributed processing network, processing capability is located and shared at different notes or locations. This type of strategy is common for decentralized organizations where divisional offices are networks to the organization’s main or centralized computer. 7 3. Advantages and disadvantages No. Advantages Disadvantages 1 Management of distributed data with different levels of transparency like fragmentation transparency, replication transparency and others. Complexity — extra work must be done by the DBAs to ensure that the distributed nature of the system is transparent. Extra work must also be done to maintain multiple disparate systems, instead of one big one. Extra database design work must also be done to account for the disconnected nature of the database — for example, joins become prohibitively expensive when performed across multiple systems. 2 Increase reliability and availability. Economics — increased complexity and a more extensive infrastructure means extra labour costs. 3 Easier expansion. 4 Reflects organizational structure — database fragments are located in the departments they relate to. Security — remote database fragments must be secured, and they are not centralized so the remote sites must be secured as well. The infrastructure must also be secured (e.g., by encrypting the network links between remote sites). Difficult to maintain integrity — but in a distributed database, enforcing integrity over a network may require too much of the network's resources to be feasible. 5 Local autonomy or site autonomy — a department can control the data about them (as they are the ones familiar with it.) Inexperience — distributed databases are difficult to work with, and as a young field there is not much readily available experience on proper practice. 6 Protection of valuable data — if there were ever a catastrophic event such as a fire, all of the data would not be in one place, but distributed in multiple locations. Lack of standards — there are no tools or methodologies yet to help users convert a centralized DBMS into a distributed DBMS. 8 For a summary of network strategies is Strategy Description Terminal Centralized processing power, location, and control. Underutilized processing power of microcomputers. Client/server Client request services. Servers provide services and coordination. Efficient network management software. Expensive. Peer-to-peer All nodes act as clients and servers. Easy and inexpensive. Lacks security controls. Distributed Nodes share resource from different locations. Used in decentralized organization. 9 References 1. http://www.google.com.my/imgres 2. Computing Essentials Complete 2011, written by Timothy J. O’Leary and Linda I. O’Leary, published by McGraw Hill 3. http://www.csc.liv.ac.uk/~dirk/Comp332/COMP332-DDB-notes.pdf 4. http://assignment1ivorfinn.wetpaint.com/page/The+Advantages+And+Disadvanta ges+of+Peer-to-peer+Network+and+client+%2Fserver+netwroks 5. http://simple.wikipedia.org/wiki/Client-server 6. http://networksandservers.blogspot.com/2011/10/virtualization-iii.html 7. http://en.wikipedia.org/wiki/Peer-to-peer# 10






