Two Protocol Case Studies
advertisement

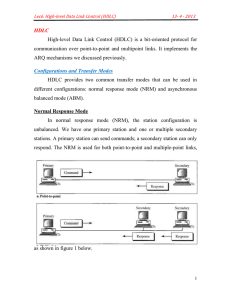
Two Protocol Case Studies HDLC & Kermit HDLC • A multi-functional protocol. • Works in lots of modes. • Forms the basis for MANY of the current protocols in use. • When studying this protocol consider it is like a vehicle that you can use to fly, drive, or ride on the water; you may not see how to use all of the parts. Classifications of stations • Primary – tells other stations what to do • Secondary – more reactive – doesn’t initiate on it’s own • Combined – same station can be either Basic Configurations Primary Secondary Combined Combined Point to Point Primary Secondary Multipoint Secondary Basic Modes - NRM NRM - Normal Response Mode Primary Secondary Secondary Whether in point-to-point or multipoint, the primary dictates/controls response of secondary. Basic Modes - ABM ABM - Asynchronous Balanced Mode Combined Combined Point to Point Using combined stations, the relationship is peer to peer. Neither is on control of the other ARM - Asynchronous Response Mode Similar to ABM but primary/secondary roles exist. Secondary can initiate certain types of responses. Ignore this. HDLC Frame Format Focus on what you can learn about the protocol from the frame! 8 8/16 8/16 flag address control Typically source & destination Status or commands variable 16/32 8 INFO CRC flag Not always present Flag Field & Bit Stuffing Marking beginning and end is important! flag 01111110 head frame contents 01111110 tail What do you do if the sequence 01111110 appears in the frame? Bit Stuffing In this case 6 ones in a row is the sequence to consider. When sending the flag, nothing special is done. When sending data, look for the sequence of 6 ones. When found, insert an extra 0. Data intended 01111110 01111110 Data sent 01111110 011111010 01111110 01111110 Bit stuffed If receiver gets 5 ones followed by a 0, throw away the 0. Can you figure out what happens if the sender sends 0111110 ? HDLC Frame Types 0 N(S) P/F N(R) Information 0 1 S P/F N(R) Supervisory 1 1 M P/F Unnumbered M Information Frames 0 N(S) P/F N(R) Information •See Figure 5.30 part b •This is the MIDDLE of the exchange •setup •TALK •disconnect •Examine the symmetric nature of the sequence numbers •Is the scenario using go-back-n or selective repeat? •RR is a supervisory frame to send a reverse ACK when no reverse data exists Supervisory Frames Supervisory 0 1 S P/F N(R) •2 bits •RR : Receive ready (ACK when no returning data) •REJ : Reject (NAK) •RNR : Receive not ready Flow control (buffers full) •SREJ : Selective Reject Resend that one frame number (not exactly as done in the general case) Unnumbered Frames 3 2 1 1 M P/F M Unnumbered Although broken, total field size of M is 5 bits -> 32 values. This identifies the frame type. See Table 5.2 This defines most of the message types/interactions. Classified as C (command) or R (response). Beginning and Ending The entire exchange has to also have a beginning and an end. See Figure 5.30 again •Connection Establishment •Data Exchange (b) •Disconnect (c) (a) Connect Station A Station B Send RIM Send SIM Send UA Send SARM Send UA Information Exchange Station A Station B SEND I Frames N(R)=0 N(S)=0 SEND I Frames N(R)=0 N(S)=1 N(R)=0 N(S)=0 N(R)=0 N(S)=1 N(R)=1 N(S)=2 Frame Damaged Frame Rejected Send REJ with N(R)=1 SEND I Frames N(R)=2 N(S)=1 (no activity) N(R)=2 N(S)=2 N(R)=2 N(S)=3 Send RRJ with N(R)=3 Disconnect Station A Station B Send DISC Send UA Kermit A quick look What is Kermit? • Before FTP • Used to transfer files in an interactive session • Just focus on the higher level interaction. •Run telnet-like program •Log in and go to the directory where file is stored •run KERMIT •go to your window on local machine and set in receive mode •(protocols connect and download) •log off A typical interaction Station A S Y S - Send Initiation Y - ACK F - File Header D - Data Frame Z - End of File B - End of transmission F Y DATA Z Y B Y Station B