Slides
advertisement

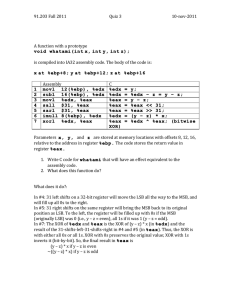
Goals: • To gain an understanding of assembly • To get your hands dirty in GDB • • • • • • • C program compilation Overview of the Binary Bomb Lab Assembly basics GDB basics GDB “bug” GDB demo Assembly/C comparison practice • Steps to building an executable file from a C source code file: 1. Preprocessing: the preprocessor takes a C source code file and replaces preprocessor directives with source code • For example, #include and #define precede preprocessor directives 2. Compilation: the compiler produces an object file based on the output of the preprocessor 3. Assembling: conversion from assembly to machine instructions 4. Linking: the linker takes the object files produced by the compiler and combines them to produce a library or an executable file • If one is available, running the Makefile (using the command “make”) can do these steps for you • Alternatively, you could use the “gcc” command • Dr. Evil has created a series of so-called “binary bombs” for you to defuse by determining the password needed to prevent an “explosion” from occurring • You will only be given your bomb’s .o file because giving you the source code would make this lab far too easy • You will be expected to look at the assembly dump of this file to help you determine the passwords • It may be useful to learn how to set breakpoints to prevent explosions • Each time you allow the bomb to explode, you will lose ¼ point • Capped at 10 points lost • Each phase is worth 10 points out of a total of 60 points • movl Souce, Destination • Ex: can move immediate value to a register or to memory, can move a register value to another register or to memory, can move memory to a register • CANNOT move memory to memory • leal Souce, Destination • Commonly used for computing arithmetic expressions • Ex: leal (%eax, %eax, 2), %eax would be the assembly version of C code that looks something like the following: x = x + x*2 • cmpl Reg1, Reg2: Reg2 “relation” Reg1 • jmpl Label • Could be of the form j“relation” (Ex: jle or jg or je) • addl Souce, Destination: Dest = Dest + Src • subl Souce, Destination: Dest = Dest - Src • • • • • %esp: stack pointer %ebp: stack base pointer %eax: function return value %ebx, %ecx, %edx: general-purpose registers %eip: instruction pointer (program counter) • • • • 0x8(%edx) => 0x8+%edx (%edx, %ecx) => %edx + %ecx (%edx, %ecx, 4) => %edx + 4*%ecx 0x8( , %edx, 2) => 2*%edx + 0x8 • Command line debugging tool • Available on many different platforms • Useful outside of classroom setting • Allows you to trace a program in execution and set breakpoints along the way • Gives you a chance to inspect register contents and the assembly breakdown of your executable • When setting a breakpoint, GDB replaces the instruction at which you are breaking with the expression “int3” as an indicator of a system interrupt so that the program will pause at that point when it is running • As a quick fix, please do the following: • Within GDB: (gdb) set code-cache off • As a permanent fix, please do the following: • Command line: $ echo "set code-cache off" >> ~/.gdbinit • • • • break: sets break point at specified location print: prints a specified variable or register’s value stepi: steps through one instruction in assembly nexti: steps through one instruction, including function calls • disas: show the disassembly of the current code • continue: continues execution after stopping at a break point • quit: exit gdb • • • • • disas [function] disas *address info break info registers x/* address: display contents of memory • x/ 4x address: display 4 32-bit hex numbers starting at address (Practice problem was adapted from Professor Mohamed Zahran’s practice exam)