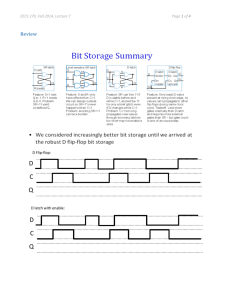
Stu-Chapter10
advertisement

Personnel and Security EECS 711 Philip Mein "Prakash" Pallavur Sankaranaraynan Annette Tetmeyer Outline • • • • • • Introduction Staffing the Security Function Information Security Professional Credentials Employment Policies and Practices Conclusion Questions 2 EECS 711 Spring 2008 Chapter 10 Introduction • InfoSec department must be carefully structured and staffed with appropriately skilled and screened personnel • Requires Human Resources to have the proper policies integrated into its procedures (hiring, training, promotion, and termination) • What to look for in personnel (certifications) • IT security job descriptions • How to integrate InfoSec policies into an organizations hiring practices 3 EECS 711 Spring 2008 Chapter 10 Staffing the Security Function • Supply and Demand of qualified staff – many economic forecasters expect the deferred demand to become active in the InfoSec field 4 EECS 711 Spring 2008 Chapter 10 Qualifications and Requirements • General management community of interest should learn more about the requirements and qualifications for both IT and InfoSec positions • Upper management should learn more about InfoSec budgetary and personnel needs • The IT and general management communities of interest must grant the InfoSec function an appropriate level of influence and prestige 5 EECS 711 Spring 2008 Chapter 10 Hiring InfoSec Professionals • Understand how organizations are structured and operated • Recognize the InfoSec is a management task that cannot be handled with technology alone • Work well with people in general (written and verbal) • Acknowledge the role of policy in guiding security efforts • Understand the essential role of InfoSec education and training • Perceive the threats facing an organization, understand how these threats can be transformed into attacks, and safeguard the organization from these attacks • Understand how technical controls can be applied to solve specific information security problems • Demonstrate familiarity with mainstream information technologies • Understand IT and InfoSec terminology and concepts 6 EECS 711 Spring 2008 Chapter 10 Entering the InfoSec Profession • Traditional Career Path to InfoSec was from Technology or Military/Law enforcement • Modern Path to InfoSec is from a security education background EECS 711 Spring 2008 Chapter 10 Information Security Positions • Complete job descriptions for InfoSec positions can be found in Charles Cresson Wood's book Information Security Roles and Responisibilities Made Easy • Definers – Provide the policies, guidelines and standards – Do the consulting and risk assessment – Develop the product and technical architectures • Builders – Techies who create and install security solutions • Administrators – Operate and administer the security tools – Security monitoring function – Continuously improve the process 8 EECS 711 Spring 2008 Chapter 10 InfoSec Positions • CISO – Top InfoSec officer – Must be conversant in all areas (technology, planning, and policy) – Responsible for the overall InfoSec program • Security Manager – Responsible for policy development, risk assessment, contingency planning, and operational and tatical planning – Understanding of technology administered but not necessarily proficiency in its configuration or operation • Security Technician – Technically qualified individuals who configure and maintain security technology – Are likely to be IT technicians who have adopted a different career path 9 EECS 711 Spring 2008 Chapter 10 Other Position Titles • Many noninformation security job descriptions must define information security roles and responsibilities • Community of interest with security roles and responsibilites – Information Security Community – IT Community – General Business Community • Building and Facilities Guard • Office Maintenance Worker • Human Resources Dept manager • CFO • CEO 10 EECS 711 Spring 2008 Chapter 10 Social Engineering • • An attacker uses human interaction (social skills) to obtain or compromise information about an organization or its computer systems Top 4 hacking moments on film 1. Independence Day: Using an old space ship as cover for two humans to infiltrate the alien mother ship and upload a virus to destroy it. 2. Hackers: Dumpster diving in the target company's trash in order to obtain financial data from printouts. 3. War Games: Password cracking the military computer system by studying its creator. 4. Ferris Bueller's Day Off: Faking a grandmother's death to get Ferris's girlfriend excused from school through multiple phone calls and answering machine recordings. 5. Sneakers: Intercepting the call from the security guard to bypass the alarm and rob the bank. <Sneakers> Question: Which of the above hacks did not employ a social engineering technique? 11 EECS 711 Spring 2008 Chapter 10 Social Engineering • SE Attack Detection – Employees need to be trained to detect anomalies in conversation, e-mail, and pop-up windows • SE Attack Prevention – Preparation (SETA) – Table 10-3 • SE Attack Defense – Organizations should have an established procedure for reporting suspected SE attacks – IR team should log attacks and treat them no differently than other attacks 12 EECS 711 Spring 2008 Chapter 10 Information Security Professional Credentials • Professional certifications ascertain the level of proficiency possessed by different candidates. • Employers struggle to match certifications to position requirements. • Potential infosec workers try to determine which certificates will help them in the job market 13 EECS 711 Spring 2008 Chapter 10 Information Security Professional Credentials • The widely recognized certification programs are: – Certified Information Systems Security Professional (CISSP) – Systems Security Certified Practitioner (SSCP) – Certified Information Systems Auditor (CISA) – Certified Information Security Manager (CISM) – Global Information Assurance Certification (GIAC) – Security Certified Program (SCP) – Security+ – Certified Computer Examiner (CCE) – Certified Forensics Investigator (CIFI) 14 EECS 711 Spring 2008 Chapter 10 Certified Information Systems Security Professional (CISSP) • Considered the most prestigious certification for Security Managers and CISO’s. • Offered by the International Information Systems Security Certification Consortium (ISC)2. • Recognizes mastery of an internationally identified common body of knowledge (CBK) in information security. • Candidates must have at least 3 years of direct, full-time security professional work experience. • The test covers 10 domains of information security and consists of 250 multiple choice questions to be completed in 6 hours. 15 EECS 711 Spring 2008 Chapter 10 Certified Information Systems Security Professional (CISSP) • The 10 domains of information security knowledge are: 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. 16 Access control systems and methodology Applications and systems development Business continuity planning Cryptography Law, investigation and ethics Operations security Physical security Security architecture and models Security management practices Telecommunications, network and Internet security EECS 711 Spring 2008 Chapter 10 Certified Information Systems Security Professional (CISSP) • CISSP certification requires the successful completion of the exam and an endorsement by a qualified 3rd party to ensure that the applicant meets the experience requirement. • It is the most challenging of information security certifications. • Holders of the CISSP must earn a specific number of continuing education credits every 3 years to retain their certification. 17 EECS 711 Spring 2008 Chapter 10 Systems Security Certified Practitioner (SSCP) • Also offered by the (ISC)2. • Less rigorous than the CISSP. • More applicable to security managers than the technicians. • Most of the questions focus on the operational nature of information security. • Focuses on practices, roles and responsibilities as defined by experts from major IS industries. • The SSCP exam consists of 125 multiplechoice questions covering 7 domains on information security to be completed in 3 hours. Spring 2008 18 EECS 711: EECS Security 711 Spring Management 2008 Chapter and Audit 10 18 Systems Security Certified Practitioner (SSCP) • The 7 domains are: 1. 2. 3. 4. 5. 6. 7. 19 Access controls Administration Audit and monitoring Risk, response and recovery Cryptography Data communications Malicious code/malware EECS 711 Spring 2008 Chapter 10 Systems Security Certified Practitioner (SSCP) • Like the CISSP, a SCCP holder must earn continuing credits to retain certification, or else retake the exam. • Slightly more technical than the CISSP. 20 EECS 711 Spring 2008 Chapter 10 CISSP Concentrations • ISSAP: Information Systems Security Architecture Professional • ISSEP: Information Systems Security Engineering Professional • ISSMP: Information Systems Security Management Professional 21 EECS 711 Spring 2008 Chapter 10 Certified Information Systems Auditor (CISA) • Not specifically a security certification but includes many information security components. • Sponsored by the Information Systems Audit and Control Association (ISACA). • Certification appropriate for auditing, networking and security professionals. • Requires experience as an information systems auditor, with a minimum of 5 years professional experience. • Requires agreement to the Code of Professional Ethics. • Requires a minimum of 20 hours of continuing education annually and 120 hours during a fixed 3 year period. • Adherence to the Information Systems Auditing Standards. 22 EECS 711 Spring 2008 Chapter 10 Certified Information Systems Auditor (CISA) • The exam covers the following areas: 1. IS audit process (10%) 2. IT governance (15%) 3. Systems and infrastructure lifecycle management (16%) 4. IT service delivery and support (14%) 5. Protection of information assets (31%) 6. Business continuity and disaster recovery (14 %) 23 EECS 711 Spring 2008 Chapter 10 Certified Information Security Manager (CISM) • Also offered by the ISACA. • Geared towards the experienced information security manager and other with information security management responsibilities. • This certification assures executive management that the candidate has the required background knowledge needed for effective security management and consulting. • The exam is offered annually. • Requires the applicant to adhere to ISACA code of ethics. • Requires pursuing continuing education. • Applicants must have at least 5 years of information security experience with at least 3 years in information security management. 24 EECS 711 Spring 2008 Chapter 10 Certified Information Security Manager (CISM) • The CISM exam covers: 1. Information security governance (21%) 2. Risk management (21%) 3. Information security program management (24%) 4. Response management (13%) 25 EECS 711 Spring 2008 Chapter 10 Global Information Assurance Certification (GIAC) • Developed by Systems Administration, Networking and Security (SANS) organization. • Tests both for knowledge and applicants ability to demonstrate application of that knowledge. • Offers the only advanced technical certifications. • The GIAC family of certifications can be pursued independently or combined to earn a comprehensive certification called GIAC Security Engineer (GSE). • Only when practical assignment is complete is the candidate allowed to take the online exam. • GIAC now offers two types of certifications: Silver and Gold. 26 EECS 711 Spring 2008 Chapter 10 Global Information Assurance Certification (GIAC) • Requirements for Silver certification: – Completion of exams – Full certifications require 2 exams; certificates require a single exam • Requirements for Gold certification: – Complete Silver certification – Passing a technical paper review, the paper demonstrates real world, hands on mastery of security skills 27 EECS 711 Spring 2008 Chapter 10 Global Information Assurance Certification (GIAC) • The individual GIAC certifications are as follows: 1. 2. 3. 4. 5. 6. GIAC Information Security Fundamentals (GISF) GIAC Security Essentials Certification (GSEC) GIAC Certified Firewall Analyst (GCFW) GIAC Certified Intrusion Analyst (GCIA) GIAC Certified Incident Handler (GCIH) GIAC Certified Windows Security Administrator (GCWN) 7. GIAC Certified UNIX Security Administrator (GCUX) 8. GIAC Certified Forensics Analyst (GCFW) 9. GIAC Securing Oracle Certification (GSOC) 10. GIAC Intrusion Prevention (GIPS) 11. GIAC Cutting Edge Hacking Techniques (GHTQ) 28 EECS 711 Spring 2008 Chapter 10 EECS 711 Spring 2008 Chapter 10 28 Security Certified Program (SCP) • SCP offers two tracks: Security Certified Network Professional (SCNP) and the Security Certified Network Architect (SCNA). • Both designed for the security technician. • While not as detailed as the GIAC certifications, these programs provide the knowledge needed to work in new areas of security, while developing a vendor neutral core of practitioner knowledge evaluation. • The SCNP track targets firewalls & intrusion detection, and requires 2 exams: – Hardening The Infrastructure (HTI) – Network Defense & Countermeasures (NDC) • The SCNA program includes the following: – Enterprise Security Implementation (ESI) which covers: • Advanced Security Implementation (ASI) • Enterprise Security Solutions (ESS) – The Solution Exam (TSE) covering all facets of the SCP courses 29 EECS 711 Spring 2008 Chapter 10 Security+ • Offered by CompTIA a vendor neutral certification program. • Tests for security knowledge mastery of an individual with 2 years on the job networking experience. • CompTIA Security+ curricula is being taught at colleges, universities and commercial training centers. • Exam covers industry-wide topics including: 1. 2. 3. 4. 5. 30 General Security Concepts Communication Security Infrastructure Security Basics of Cryptography Operational/Organizational Security EECS 711 Spring 2008 Chapter 10 Certified Computer Examiner (CCE) • Is a computer forensics certification provided by the International Society of Forensic Computer Examiners • To complete the certification the applicant must: – Have no criminal record – Meet minimum experience, training or self-training requirements – Abide by certification’s code of ethical standards – Pass an online exam – Successfully perform actual forensic exams on 3 test media 31 EECS 711 Spring 2008 Chapter 10 Certified Computer Examiner (CCE) • The CCE certification process covers the following areas: 1. Acquisition, marking, handling, and storage of evidence procedures 2. Chain of custody 3. Essential “core” forensic computer examination procedures 4. The “rules of evidence” as they relate to computer examinations 5. Basic PC hardware construction and theory 6. Very basic networking theory 7. Basic data recovery techniques 8. Authenticating MS word documents and accessing and interpreting metadata 9. Basic optical recording processes and accessing data on optical media 10. Basic password recovery techniques 11. Basic internet issues 32 EECS 711 Spring 2008 Chapter 10 Certified Information Forensics Investigator (CIFI) • The Information Security Forensics Association (ISFA) is developing an examination for a Certified Information Forensics Investigator (CIFI). • This program will evaluate expertise in tasks and responsibilities of a security administrator or security manager, including incident response, working with law enforcement, and auditing. 33 EECS 711 Spring 2008 Chapter 10 Certified Information Forensics Investigator (CIFI) • Although the certification exam has not been finalized, the body of knowledge has been tentatively defined to include the following aspects of information security: 1. 2. 3. 4. 5. 6. 34 Countermeasures Auditing Incident response teams Law enforcement and investigation Traceback Tools and techniques EECS 711 Spring 2008 Chapter 10 Certification Costs • Certifications can be expensive. • The high costs deter those who might take the exam just to see if they can pass. • Most experienced professionals find it difficult to do well on them without at least some review. • Most programs require between 2 & 3 years of work experience. • Often structured to reward candidates who have significant hands-on experience. 35 EECS 711 Spring 2008 Chapter 10 Approaches to prepare for security certification 36 EECS 711 Spring 2008 Chapter 10 Employment Policies and Practices 37 EECS 711 Spring 2008 Chapter 10 Employment Policies and Practices • • • • Hiring and Firing Contracts Personnel Security Practices Security Considerations for Nonemployees 38 EECS 711 Spring 2008 Chapter 10 Hiring • • • • • Job Descriptions Interviews New Hire Orientation On-the-Job Security Training Security Checks 39 EECS 711 Spring 2008 Chapter 10 Security Checks • • • • Identity checks Education and credentials Previous employment Reference checks 40 EECS 711 Spring 2008 Chapter 10 Security Checks • • • • • • Worker’s compensation history Motor vehicle records Drug history Medical Credit Civil Court Criminal Court Make sure to comply with regulations 41 EECS 711 Spring 2008 Chapter 10 Contracts and Employment • Require employees to agree in writing by signing monitoring and nondisclosure agreements • Sign before other employment contracts are made • Existing employees may not be compelled to sign 42 EECS 711 Spring 2008 Chapter 10 Security as Part of Performance Evaluations • How can performance evaluations be used to motivate employees concerning security practices? 43 EECS 711 Spring 2008 Chapter 10 Termination Issues Need to protect information to which an employee had access • Disable system access • Retrieve removable media • Secure hard drives (network drives?) • Change locks: file cabinets, offices, etc. • Revoke keycard access • Remove personal items • Finally, escort from premises 44 EECS 711 Spring 2008 Chapter 10 Termination Issues • Conducting Exit Interviews – Remind of contractual obligations – Discuss consequences if failure to comply with contractual obligations – Gather feedback from employee • Termination brings a level of risk exposure to the organization, regardless of level of trust in employee 45 EECS 711 Spring 2008 Chapter 10 Immediate Severance • Forgo the customary two-week notice • Sensitive areas or positions of trust may require this • Do you have any experience with this? 46 EECS 711 Spring 2008 Chapter 10 Outprocessing Hostile or friendly departure? • Hostile – termination, downsizing, layoff, quitting – Revoke system access first, then notify employee – Collect sensitive items – Escort from facility 47 EECS 711 Spring 2008 Chapter 10 Outprocessing Hostile or friendly departure? • Friendly – retirement, promotion, relocation – May be a bit tricky to manage – Set expirations dates for system access or phase out access – Collect company assets – Employees typically have more latitude in removing personal items 48 EECS 711 Spring 2008 Chapter 10 Outprocessing Hostile or friendly departure? • For both scenarios complete the following: – Inventory offices and info – Archive, return to stores or destroy – Review logs for possible system misuse (and follow-up as an incident if warranted) – What do you do about materials at the employees home? 49 EECS 711 Spring 2008 Chapter 10 Personnel Security Practices Monitor and control employees to minimize opportunities for misuse of info • Separation of duties – Checks and balances mitigates collusion • • • • Two-person control Job and task rotation Mandatory vacations Least privilege 50 EECS 711 Spring 2008 Chapter 10 Personnel Security Practices 51 EECS 711 Spring 2008 Chapter 10 Security of Personnel and Personal Data Comply with laws regarding protecting sensitive or personal info (employees, customers, business partners, etc.) • Names, addresses, phone numbers • SSN • Medical info There are more regulations that tend to cover this type of information 52 EECS 711 Spring 2008 Chapter 10 Security Considerations for Nonemployees • Nonemployees may have access to sensitive info • Need to carefully manage these relationships 53 EECS 711 Spring 2008 Chapter 10 Temporary Workers • Brought in to fill positions temporarily or to supplement workforce • Usually retained through an outside agency • Contractual obligations/polices may not apply or may not be enforceable • Agencies may not be liable for lossses 54 EECS 711 Spring 2008 Chapter 10 Temporary Workers To mitigate security concerns • Follow good security practices – Clean desk – Securing classified data • Least privileges, limited access to data Temps should not be employed at the cost of sacrificing information security 55 EECS 711 Spring 2008 Chapter 10 Contract Employees • Hired to perform specific services via third party organizations • Escort employees in secure areas • Background check all employees • Require advance notice for maintenance visits or cancellation/rescheduling 56 EECS 711 Spring 2008 Chapter 10 Consultants • Self-employed • Hired for a specific task or project • Pre-screen and require nondisclosure agreements • Explicitly give permissions to use company info for marketing/references • Apply least privileges 57 EECS 711 Spring 2008 Chapter 10 Business Partners • Strategic alliances for the sake of: – Information exchange – Systems integration – Other mutual advantage • Specify levels of exposure that the organization will endure – What info will be exchanged? – With whom? – In what format? 58 EECS 711 Spring 2008 Chapter 10 Business Partners System connection means that a vulnerability on one system becomes a vulnerability for all linked systems 59 EECS 711 Spring 2008 Chapter 10 Conclusion • Use standard job descriptions to increase the degree of professionalism in staffing • Professional certifications help to identify levels of proficiency • Integrate security concepts and practices into employment activities 60 EECS 711 Spring 2008 Chapter 10 Questions 61 EECS 711 Spring 2008 Chapter 10 References 62 EECS 711 Spring 2008 Chapter 10