BlueCoat_Roger_Gotthardsson
advertisement

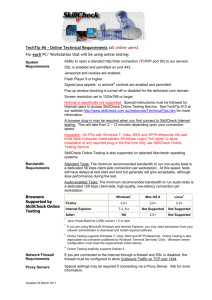
Blue Coat Systems Roger Gotthardsson Sr. Systems Engineer roger@bluecoat.com Agenda Company Corporate data Solutions Client Proxy Solution Blue Coat Webfilter SSL Proxy Reverse Proxy MACH5 Products ProxySG, ProxyAV, Director, Reporter K9, - Blue Coat Webfilter at home for free Company About Blue Coat • Innovative leader in secure content & application delivery – 500+ employees; $146M annual revenue run rate – 25,000+ appliances shipped worldwide to more than 4,000 customers – #1 (37%) market leader in Secure Content & Application Delivery (IDC) • Founded in 1996 with a focus on Acceleration – Accelerating Web applications…making Internet applications faster – Innovative proxy caching appliance with object pipelining, adaptive content refresh • Expanded in 2002 to include Policy Control & Security – Rich policy framework integrated with performance engine for visibility and control of users, content and applications • Visibility: Who, what, where, when, how • Control: accelerate, deny, limit, scan, strip, transform… Integrated Solution for Acceleration & Security About Blue Coat – Strategic Investments – March 1996 Scalable Software (HTTP and OS Kernel) – September 1999 Invertex (SSL Hardware Encryption) – June 2000 Springbank Networks (Hardware Design and Routing Protocols) – December 2000 Entera (Streaming and Content Distribution) – November 2003 Ositis (Virus scanning appliance) – 2004 – Cerberian (Content filtering) – 2006 – Permeo Technologies (SSL VPN & client security) Integrated Solution for Acceleration & Security Client Proxy Solution Client Proxy Byte Caching Authentication Logging Protocol detection BW management Policy Clients Internet Caching Antivirus Protocol optimization URL-Filtering Compression Application proxy HTTP & HTTPS Streaming Yahoo-IM AOL-IM FTP MSN-IM Internet MAPI CIFS .mp3 .xxx P2P Telnet/Shell gral.se ? DNS TCP-Tunnel SOCKS How We Secure the Web Intranet Web Server Internal Network User logs onto network AAA: and is authenticated via NTLM, AD (Single-Sign-on), LDAP, Radius, Forms, local password. Public Web Server Public Internet Authentication NT, W2000 or W2003 DC RADIUS Server Netegrity SiteMinder Policy Substitution AD Directory Directory Directory Clients Internet LDAP Client Certifficate On box Database Oblix Directory X509/CA List Directory How We Secure the Web Intranet Web Server Internal Network Public Web Server User logs onto network AAA: and is authenticated via NTLM, AD (Single-Sign-on), LDAP, Radius, Forms, local password. Policy Processing Engine: All user web application requests are subjected to granular security policy Public Internet How We Secure the Web Intranet Web Server Internal Network User logs onto network AAA: and is authenticated via NTLM, AD (Single-Sign-on), LDAP, Radius, Forms, local password. Policy Processing Engine: All user web application requests are subjected to granular security policy Content Filtering: Requests for content are controlled using content filtering based on granular policy Public Web Server Public Internet Content Filtering • Organizations need to control what users are doing when accessing the internet to protect from legal liability and productivity risks • Blue Coat and our partners enable enterprise-class content filtering – Powerful granular user control using Blue Coat’s Policy Processing Engine • By user, group, destination IP and/or URL, time of day, site, category, lots more – Multiple logging and reporting options – Integrates with all authentication (LDAP, RADIUS, NTLM, AD, 2-factor, etc) – Coaching, warnings, etc. – High performance with integrated caching – Drop-in appliance for easy to deploy and manage – De-facto industry content filtering platform Content filtering databases WebWasher Digital Arts Smartfilter InterSafe Websense Clients Optenet SurfControl IWF Proventia Internet Your lists exceptions BlueCoat webfilter DRTR How We Secure the Web Intranet Web Server Internal Network Public Internet User logs onto network Bandwidth management: AAA: and is authenticated via Compression, Bandwidth NTLM, AD (Single-Sign-on), LDAP, Radius, Forms, local password. Policy Processing Engine: All user web application requests are subjected to granular security policy Content Filtering: Requests for content are controlled using content filtering based on granular policy Public Web Server management and Streaming media Caching and Splitting. HTTP Compression ProxySG can support a mixed mode of HTTP compression operation Original Content Server (OCS) or Core ProxySG can send either (de)compressed content to edge or core ProxySG using GZIP or Deflate algorithms Core ProxySG compressed compressed compressed Edge ProxySG uncompressed uncompressed Remote Office compressed ProxySG uncompressed HQ Office compressed uncompressed Enterprise uncompressed Internet Bandwidth Management (BWM) OBJECTIVE Classify, control and limit the amount of bandwidth used by a class of network traffic BENEFITS Protect performance of mission critical applications • SAP, ERP apps Prevent bandwidth greedy applications from impacting other applications • P2P Provision bandwidth for applications that require a per-session amount of bandwidth • Streaming Balance necessary and important, bandwidth intensive, applications • HTTP, IM How We Secure the Web Intranet Web Server Internal Network Public Internet User logs onto network Bandwidth management: AAA: and is authenticated via Compression, Bandwidth NTLM, AD (Single-Sign-on), LDAP, Radius, Forms, local password. Policy Processing Engine: All user web application requests are subjected to granular security policy Content Filtering: Requests for content are controlled using content filtering based on granular policy Public Web Server management and Streaming media Caching and Splitting. Virus scanning: Web Potentially harmful content entering network via HTTP, HTTPS and FTP is stripped or scanned by ProxyAV. Virus, Code & Script scanning Other ICAP servers Clients Internet Sophos McAfee Kaspersky Panda ProxyAV ProxyAV ProxySG & ProxyAV - Large Enterprise/Network Core - Scan once, serve many (cache benefit) Internet • Purpose-built appliances for speed • “Scan once, serve many” to increase performance • High-availability & loadbalancing • Purpose built operating systems • Virus Scans HTTP, FTP with caching benefit • ProxySG Load Balances ProxyAV ProxySG Internal Network How We Secure the Web Intranet Web Server Internal Network Public Internet User logs onto network Bandwidth management: AAA: and is authenticated via Compression, Bandwidth NTLM, AD (Single-Sign-on), LDAP, Radius, Forms, local password. Policy Processing Engine: All user web application requests are subjected to granular security policy Content Filtering: Requests for content are controlled using content filtering based on granular policy Public Web Server management and Streaming media Caching and Splitting. Virus scanning: Web Potentially harmful content entering network from web is stripped or scanned by ProxyAV. Prevention is better Spyware: than a cure. BlueCoat Spyware Prevention Solution • Stops spyware installations – Detect drive-by installers Internet • Blocks spyware websites – On-Proxy URL categorization • Scans for spyware signatures ProxySG – High-performance Web AV • Detects suspect systems – Forward to cleansing agent Internal Network ProxyAV How We Secure the Web Intranet Web Server Internal Network Public Internet User logs onto network Bandwidth management: AAA: and is authenticated via Compression, Bandwidth NTLM, AD (Single-Sign-on), LDAP, Radius, Forms, local password. Policy Processing Engine: All user web application requests are subjected to granular security policy Content Filtering: Requests for content are controlled using content filtering based on granular policy Public Web Server management and Streaming media Caching and Splitting. Virus scanning: Web Potentially harmful content entering network from web is stripped or scanned by ProxyAV. Prevention is better Spyware: than a cure. IM Traffic Control: IM traffic is subjected to policies and is logged IM Control with Blue Coat ProxySG • Granular IM policy control – By enterprise, group or user level – Control by IM feature (IM only, chat, attachments, video, etc.), internal or external IM, time of day, etc. – Control IM options include deny connection, strip attachment, log chat (including attachment) – Key word actions include send alert to IT or manager, log, strip, send warning message to user • Drop-in appliance for easy to deploy and manage IM control How We Secure the Web Intranet Web Server Internal Network NTLM, AD (Single-Sign-on), LDAP, Radius, Forms, local password. Policy Processing Engine: All user web application requests are subjected to granular security policy Content Filtering: Requests for content are controlled using content filtering based on granular policy Public Internet User logs onto network Bandwidth management: AAA: and is authenticated via Compression, Bandwidth Public Web Server management and Streaming media Caching and Splitting. Virus scanning: Web Potentially harmful content entering network from web is stripped or scanned by ProxyAV. Prevention is better Spyware: than a cure. IM Traffic Control: IM traffic is subjected to policies and is logged Caching: Acceptable, clean content is stored in cache and delivered to requestor. Streaming acceleration • Streaming – – – – Microsoft Streaming & Native RTSP Live Stream split, VOD Stream cache Rich Streaming features, Unicast-Multicast Scheduling live streaming from VOD • Enhancements – Store, Cache & distribute Video On Demand – Schedule VOD content to be played as Live Content – Convert between Multicast-Unicast – Authenticate Streaming users To NTLM, Ldap, RADIUS+Onbox How We Secure the Web Internal Network NTLM, AD (Single-Sign-on), LDAP, Radius, Forms, local password. Policy Processing Engine: All user web application requests are subjected to granular security policy Content Filtering: Requests for content are controlled using content filtering based on granular policy Public Internet User logs onto network Bandwidth management: AAA: and is authenticated via Compression, Bandwidth Public Web Server management and Streaming media Caching and Splitting. Virus scanning: Web Potentially harmful content entering network from web is stripped or scanned by ProxyAV. Prevention is better Spyware: than a cure. IM Traffic Control: IM traffic Intranet Web Server is subjected to policies and is logged Caching: Acceptable, clean content is stored in cache and delivered to requestor. Reporting: All browser, streaming, IM & virus activity, can be reported using Bluecoat's highly configurable reporter. Reporter Blue Coat Webfilter The Internet The internet today consists of 350 million webservers. A large ammount of these conatain information you don’t want in your organisation. A cleaver solution would be to use Content Filtering. BlueCoat now introduces Generation 3 of content filtering, BlueCoat Webfilter. 350 Million Generation 1 The first generation of content filters consisted of static manually managed lists of popular pornographic and unproductive websites. Very often retreived from access logs, popular bad sites where banned. 1 Million The intended purpose was to save bandwidth and warn users that inapropriate behaviour was logged. People got together and distributed their lists in free lists compatible with proxies such as Squid. The distributed list where in the size of a million URL:s 349 Million Generation 2 Corporations relised they could make money of a list and started to collect lists and logs from the web, manually rating these in larger scale. More categories where added to increase value. The systems started to collect URL:S autmatically and download new lists periodicly. Some of them even many times every day. 15 Million Special categories where added for static security threats placed on known webservers, spyware phishing etc. Other than bad sites where added such as Economy, business, news etc. to present statistics of Internet usage. 335 Million Generation 2 Number of URL:s was in the numbers of 10-20 millions. Hitrates in logsystems presented was in the numbers of 50-80%. Regular expression on URL:s and other tricks sometimes gave a false picture of rating over 90%. But in fact less than 5% of the Internet was covered. 15 Million 335 Million Generation 3 The dynamics of internet and new security risks urged for a new way of categorizing the Internet, Dynamic rating of uncategorized websites can today rate most websites, the ones thats impossible to rate could be stripped down to present only html and images to reduce risk. 15 Million The static URL database are constantly updated like any Generation 2 filter. This database is cached in some systems (ProxySG) to increase performance. The rest (95%) of the Internet is categorised using dynamic rating. 335 Million Dynamic Real Time Rating Internet Servers 44µs language 1 language 2 language 3 language 4 language 5 language n DRTR Clients Customer DXD BlueCoat * The picture is simplified, all systems are redundant. To background rating G2 Language detection RS DBR HR SSL Proxy SSL Proxy: Policy Enforcement • Control web content, applications, and services…regardless of encryption – Block, allow, throttle, scan, accelerate, insert, strip, redirect, transform … – Apply the same policies to encrypted traffic as to normal traffic – Stops/controls rogue applications that take advantage of SSL • Protect the enterprise from SSL-borne threats – Stop spyware and secured phishing – SSL-secured webmail and extranets – virus transmissions – SSL-borne malicious and inappropriate content • Accelerate critical applications – Enables a variety of acceleration techniques (e.g., caching) Apps SSL Policy SSL User Internet Internal Network Blue Coat: Visibility and Context Client-Proxy Connection Client Server-Proxy Connection Proxy Algorithms I support. Connection Request. Server Algorithms I support. Connection Request. Verify certificate and extract (proxy’s) public key. Let’s use this algorithm. Emulated certificate. Complete Authentication. Complete Authentication. Tunnel Established Verify certificate and extract server’s public key. Complete Authentication. Use this algorithm. Server’s digital certificate. Complete Authentication. Tunnel Established Flexible Configurations • Trusted applications passed through – Sensitive, known, financial or health care • No cache, visibility Option 1 • Awareness of network-level information only Control Apps User SSL Internet TCP TCP Flexible Configurations • Initial checks performed – Valid user, valid application – Valid server cert • User/application traffic passed through after initial checks • No cache • Visibility and context of network-level info, certificates, user, and applications • Can warn user, remind of AUP, and offer opt-out Apps Option 2 Control User SSL Internet TCP TCP Flexible Configurations • Initial checks performed – Valid user, valid application – Valid server cert • User/application traffic proxied after initial checks • Full caching and logging options • Visibility and context of network-level info, certificates, user, applications, content, etc. Option 3 – Full termination/proxy • Can warn user, remind of AUP, and offer opt-out Control Apps User Internet SSL SSL TCP TCP Reverse Proxy Reverse Proxy Logging Policy Authentication URL-rewrite Internet Clients Servers AV SSL/Certificate Caching Reverse Proxy PROTECTS Web Servers ACCELERATES Web Content • Secure, object-based OS • Controls access to web apps • Web AV scanning • Intelligent caching • Compression and bandwidth mgt. • TCP & SSL offload Web Servers ProxySG Firewall Internal Network Users Public Internet Users SIMPLIFIES Operations • Scalable, optimized appliance • Easy policy creation & management • Complete logging & reporting Secure & Accelerate Web Applications HTTPS Termination • HTTPS Termination (Client ProxySG) – Off-load secure website or portal • HTTPS Origination (ProxySG Server) – Secure channel to content server for clients • Man-in-the-Middle (Termination & Origination) – Allows caching, policy and virus scanning • Secure credential acquisitions • SSL Hardware Acceleration Cards – 800 RSA transactions per second per card – SSL v2.0, v3.0, and TLS v1 support • Off-load web application servers to improve performance Example Scenarios for Reverse Proxy • Secure and Accelerate Public Websites – Improves content delivery with integrated caching – Services legitimate users while resisting DoS attacks – High-performance SSL • Secure Corporate Webmail – Securely isolates Web servers from direct Internet access – Proxy authentication for additional layer of protection – Plug-n-play SSL • Scanning Uploaded Files for Viruses – Simple integration with ProxyAV™ – Real-time scanning of uploaded content – Protects Web infrastructure from malware Accelerate Applications – All Users – All Locations Recipe for Branch Performance Problems Server Consolidation + Increased application traffic + Inefficient application protocols + Highly distributed users + Narrow bandwidth links = Poor Application Performance Minimum for Application Acceleration Optimize use of existing WAN bandwidth Reduce latency associated with applications Improve the efficiency of application protocols Prioritize the applications that matter most Re-use and compress data where possible Accelerate File Sharing, Email, and browserbased enterprise applications Complete Solution Requires More Platform for Application Acceleration Multiprotocol Accelerated Caching Hierarchy Bandwidth Protocol Management Optimization Object Caching Byte Caching Compression File Services (CIFS), Web (HTTP), Exchange (MAPI), Video/Streaming (RTSP, MMS), Secure Web (SSL) New Requirement: SSL Acceleration More and More SSL… • Nearly 50% of all corporate Web application traffic is SSL SSL Traffic • 70% of all mobile and teleworkers use SSL for secure application delivery Internally Hosted Apps • 68% of Blue Coat customers depend on externally hosted Web Externally applications Hosted Apps Source: Blue Coat Customer Surveys New Requirement: Video Acceleration • Enterprise users becoming more distributed – Mobile, teleworker, and branch/ remote offices – Regulatory and cost drivers • Remote employee training becoming a necessity – Live (streaming) and on-demand video • Performance quality becoming a requirement – Network and application issues must be addressed – Control and acceleration of video is needed Bandwidth Management Sales Automation App Priority 1 Min 400Kb, Max 800Kb E-Mail Priority 2 Min 100Kb, Max 400Kb File Services Priority 3 Min 400Kb, Max 800Kb General Web Surfing Priority 4 Min 0Kb, Max 200Kb • Divide user and application traffic into classes • Guarantee min and/or max bandwidth for a class • Align traffic classes to business priorities Protocol Optimization Protocol Optimization 10-100X Faster Includes CIFS, MAPI, HTTP, HTTPS, TCP Object Caching • Built on high-level applications and protocols – HTTP/Web caching – Streaming caches – CIFS cache • Advantages – Fastest response times – Offload work from servers (and networks) – Can be deployed asymmetrically • Limitations – Application-specific – All or nothing: No benefit if whole object not found or changed Byte Caching Local History Cache Remote History Cache …..11011111001110011...111001111001 …..11011111001110011...111001111001 Sequences are 100101011101100100001101001100111 100101011101100100001101001100111 They are The original 001000001111000111001100011000001 001000001111000111001100011000001 found in the local 001111000000110111101001000011011 Proxies keep 001111000000110111101001000011011 transmitted as stream is history cache 0001011111001010101011100110100111a history of all 0001011111001010101011100110100111 small reconstructed 010011110010000000000001110010111 010011110010000000000001110010111 001011011011010010101100101100111 bytes sent references over using the 001011011011010010101100101100111 10001111111111000000000 10001111111111000000000 and received the WAN 11011111001110010010010111001 10010101110110010000110100110 01110010000011110001110011000 11000001001111000000110111101 00100001101101001011111001101 00111011010011010011110010000 00000000111001011100101101101 1010010101100101100 Local LAN remote history cache [R1]0010010[R2]1001011111 00110100111011010011[R3] WAN Link 11011111001110010010010111001 10010101110110010000110100110 01110010000011110001110011000 11000001001111000000110111101 00100001101101001011111001101 00111011010011010011110010000 00000000111001011100101101101 1010010101100101100 Remote LAN Compression 110111110011100100100 110111110011100100100 101110011001010111011 101110011001010111011 001000011010011001110 001000011010011001110 010000011110001110011 010000011110001110011 000110000010011110000 000110000010011110000 001101111010010000110 1101111100111001001001011100110010101110110010000 001101111010010000110 110100101111100110100 10011001110010000011110001110011000110000010011 110100101111100110100 111011010011010011110 111011010011010011110 010000000000001110010 010000000000001110010 111001011011011010010 111001011011011010010 101100101100010100100 101100101100010100100 101010101010100010111 101010101010100010111 COMPRESSION • Industry-standard gzip algorithm compresses all traffic • Removes predictable “white space” from content and objects being transmitted MACH5 Techniques Work Together Object Caching • Caches repeated, static app-level data; reduces BW and latency Byte Caching • Caches any TCP application using similar/changed data; reduces BW Compression • Reduces amount of data transmitted; saves BW Bandwidth Management • Prioritize, limit, allocate, assign DiffServ – by user or application Protocol Optimization • Remove inefficiencies, reduce latency Object Caching • Object caches are built on higher level applications and protocols – HTTP/Web caching – Streaming caches – CIFS cache • Object cache advantages – Fastest response times – Offload work from servers – Can be deployed asymmetrically • Object cache disadvantages – Works with limited set of applications – Works on limited range of data inside applications – All or nothing: No benefit if whole object not found or changed Object vs. Byte Caching Proxy? Object Caching Byte Cache HTTP(S), FTP, Streaming, CIFS Built on TCP Protocol Optimization Integration X Server Offload X Network Offload X X Incremental Updates X No App Integration X End User Performance Scope Best Good Focused Broad Products MACH5 Ships with Blue Coat SGOS 5 Corporate Headquarters SG8000 Series SG800 Series Remote Offices SG400 Series SG200 Series • GA April 2006 • Appliances start at US$1,995 Branch Office Enterprise Core ProxyAV Appliances Corporate Headquarters 2000-E Series 400-E Series Remote Offices Connected Users Up to 250 users 100-2000 users 1000 -50,000+ users WAN Bandwidth Sub 1.5Mbps Bandwidth 1.5Mbps- 45Mbps Bandwidth 150Mbps + Bandwidth Performance 400-E1 • One Model: 400-E1 • RAM: 512 MB • CPU: 1.26GHz PIII • Disk drive 40 GB IDE • Network Interfaces (2 on board) 10/100 BaseT Ethernet • 19" Rack-mountable Software Reporter (SW) Advanced Java application to generate statistics from logs Licenced products Licensed products Streaming Real Networks, Microsoft, Quicktime Instant Messaging MSN, Yahoo, AOL Optional Security (HW+SW bundle) SSL termination/proxy Licenced products Licensed products Content filtering BlueCoat Webfilter ICAP AV Scanner ProxyAV (McAfee, Sophos, Panda, Kaspersky, Ahn Labs) The Power of the Proxy Web Security • Prevent spyware, malware & viruses • Stop DoS attacks • IE vulnerabilities, IM threats Policy Control + • Fine-grained policy for applications, protocols, content & users (allow, deny, transform, etc) • Granular, flexible logging • Authentication integration Accelerated Applications + • Multiprotocol Accelerated Caching Hierarchy • BW mgmt, compression, protocol optimization • Byte & object caching Full Protocol Termination = Total Visibility & Context (HTTP, SSL, IM, Streaming, P2P, SOCKS, FTP, CIFS, MAPI, Telnet, DNS) Ultimate Control Point for Communications Management Management • User Interface – HTTP (HTTPS), web GUI Interface – Telnet (Cisco CLI) – SSH & Serial console – Java Policy interface – CPL, Policy Language – SNMP MIBII + Traps – Monitor network status and statistics • Reporting tools – BlueCoat Reporter • Scalable management – Centralized configuration management in Director Reporting (example) 18.2 % 16.5 % 9.5 % 6.8 % Spyware (gator) Aftonbladet Ad’s (in top 40) https (encrypted) System-wide Management and Control • Blue Coat Director – Centralized configuration of Blue Coat appliances – set up, policy, etc – Centralized monitoring – appliance health, application use, user experience • Blue Coat Reporter – Enterprise roll-up and analysis of application delivery information: appliances, application use, user experience Both Director and Reporter are proven, with thousands of nodes under management… Director configuration Management Remotely and securely manage via GUI or CLI. Workstation • Configuration Management • Policy Management Director (2) Snapshot profile and save on Director “Profile” system • Disaster protection centrally Configuration Management • Monitor and control (3) Create and edit overlays using GUI or CLI. • Resource Management • Monitor network status and statistics • Profile Management (4) Push profiles and overlays to one or more systems (1) Configure and test “profile” system • Backup configuration • Create overlays using GUI or CLI. Automate changes • License Management Production systems Content Delivery Network Publish content 1 WWW Servers 4 Pull content from origin servers. Content Owners Edge Systems Director 2 Tell Director about new content 3 Tell caches to update content 5 Users Deliver the content. Director GUI K9 – For free If you want to protect your family with Content Filtering Blue Coat is now giving it away, read more at: http://www.getk9.com/refer/Roger.Gotthardsson Please send this link to anyone you want !!!!