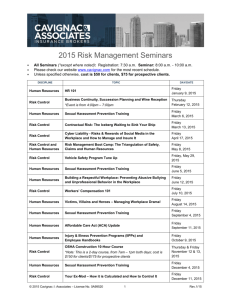
- Sacramento - The California State University
advertisement

ENGAGEMENT AMONG STUDENTS AND UNKNOWN PERSONS WHILE USING SOCIAL NETWORKING WEBSITES A Thesis Presented to the faculty of the Division of Criminal Justice California State University, Sacramento Submitted in partial satisfaction of The requirements for the degree of MASTER OF SCIENCE in Criminal Justice by Brandon Jess Jaimes SPRING 2012 ENGAGEMENT AMONG STUDENTS AND UNKNOWN PERSONS WHILE USING SOCIAL NETWORKING WEBSITES A Thesis by Brandon Jess Jaimes Approved by: __________________________________, Committee Chair Timothy Croisdale, Ph.D. __________________________________, Second Reader Dimitri Bogazianos, Ph.D. ____________________________ Date ii Student: Brandon Jess Jaimes I certify that this student has met the requirements for format contained in the University format manual, and that this thesis is suitable for shelving in the Library and credit is to be awarded for the thesis. __________________________, Graduate Coordinator Yvette Farmer, Ph.D. Division of Criminal Justice iii ___________________ Date Abstract of ENGAGEMENT AMONG STUDENTS AND UNKNOWN PERSONS WHILE USING SOCIAL NETWORKING WEBSITES by Brandon Jess Jaimes The advent of technology inherently creates problems as much as it lends efficiency, and unfortunately, the internet plays a pivotal role in a few of the major problems it has created. Current research reveals possible connections between social networking websites and increased likelihood of interpersonal victimization. The following is an analysis of 288 students who completed a survey measuring their use of internet communication services and engagement with unknown persons. Analyses showed that a large portion of students place themselves at high risk for a suitable target and lack of guardianship. Variations were found measuring the variable for motivated offender. Few subject responses indicated students engage with unknown persons whether or not they feel safe, but an overwhelming majority of the students do not feel safe engaging with strangers. _______________________, Committee Chair Timothy Croisdale, Ph.D. _______________________ Date iv ACKNOWLEDGEMENTS It is a pleasure to thank the many people who made this thesis possible. I would like to sincerely thank my thesis advisor, Dr. Tim Croisdale who decided to lend me his hand when I needed it most. Dr. Croisdale, thank you for making it easier to put the pieces in place. I am eternally indebted to your acceptance and kindness. I am grateful to have Dr. Bogazianos assist with this thesis. Dr. B., your persuasive belief in my ability encouraged me to grow and analyze elaborate theory. I now have the confidence to tackle the utmost difficult task. I am blessed to have had Dr. Farmer be the graduate coordinator during this life-changing experience. Dr. Farmer, your devotion, enthusiasm, patience, and compassion made my journey much easier. I could not have asked for a better mentor. I would like to thank the people who have taught me persistence: my grandfather, Charlie Jaimes Sr., your love and support has guided me in the darkest of times, my father, Charlie Jaimes Jr., thank you for providing the most valuable secret in life, Jaimes power, and my mother, Beverly Jaimes, for being so loving and proud. I am honored to acknowledge my extended family and my best friends. Thank you for being there during the most difficult and happiest moments in my life. Most importantly, I wish to thank my brothers, Brishen and Bryce Jaimes. Collectively, they have helped me become the person I am today. Thank you. v TABLE OF CONTENTS Page Acknowledgements ................................................................................................................... v List of Tables ........................................................................................................................ viii List of Figures .......................................................................................................................... ix Chapter 1. INTRODUCTION……………………………………………………………………….. 1 Statement of the Problem ............................................................................................. 3 Need and Purpose of Study .......................................................................................... 5 Hypotheses ................................................................................................................... 6 Theory.. ........................................................................................................................ 8 Methodology .............................................................................................................. 11 Scope and Limitations ............................................................................................... 13 Organization of the Study .......................................................................................... 13 2. REVIEW OF LITERATURE ........................................................................................... 15 Introduction................................................................................................................ 15 Sexual Harassment ..................................................................................................... 15 Stalking ...................................................................................................................... 24 Sexual Exploitation .................................................................................................... 33 Identity Theft ............................................................................................................. 42 Summary .................................................................................................................... 49 3. METHODOLOGY ........................................................................................................... 54 Subjects ...................................................................................................................... 54 Instrument .................................................................................................................. 56 Data Collection .......................................................................................................... 57 Testable Hypotheses .................................................................................................. 61 Data Analysis ............................................................................................................. 61 Limitations of Research Design ................................................................................. 64 4. FINDINGS ........................................................................................................................ 66 Suitable Target ........................................................................................................... 66 vi Lack of Guardianship................................................................................................. 69 Motivated Offender.................................................................................................... 70 Predictors of Interpersonal Victimization: Combination of Suitable Target, Motivated Offender, and Lack of Guardianship ........................................................ 82 Subject Response ....................................................................................................... 86 Summary ..................................................................................................................... 88 5. SUMMARY AND CONCLUSIONS ............................................................................. 90 Implications for Future Research ............................................................................... 95 Appendix A. Questionnaire ..................................................................................................... 99 Appendix B. Script Used Prior to Questionnaire Distribution ............................................... 109 Appendix C. Use of E-mail Services over 24-hour Period .................................................... 111 Appendix D. Use of Instant Messenger Services over 24-hour Period.................................. 112 Appendix E. Use of Chat-room Services over 24-hour Period .............................................. 113 Appendix F. Use of Social Networking Website Services over 24-hour Period ................... 114 Appendix G. Privatization of Social Networking Websites and Student’s Perception of Safety .................................................................................................. 115 Appendix H. Collapsed Data for Subjects Contacted by Unknown Persons and Their Perception of Safety ................................................................................ 116 Appendix I. Collapsed Data for Subjects who were Requested Permission to View Their Social Networking Website ................................................................... 117 Appendix J. Subjects who were Asked Permission by Unknown Persons to View Their Private Social Networking Website and Their Perception of Safety ............. 118 Appendix K. Subjects who Conversed with Unknown Persons and Their Perception of Safety .................................................................................................. 119 References ............................................................................................................................. 120 vii LIST OF TABLES Tables 1. Page Table 3.1: CSUS Criminal Justice Undergraduate Courses Selected………………………………… ....... .……………………………….58 2. Table 3.2: Demographics………………………… .. …………………………60 3. Table 3.3: Ages 15-25 by Age………………………………………………...60 4. Table 4.1: Use of Internet……………………………….…………………….67 5. Table 4.2: Social Networking Website Use…………………………………...68 6. Table 4.3: Frequency of Mobile Device Use………………………………….69 7. Table 4.4: Guardianship of Computer Use……………………………………70 8. Table 4.5: Amount of Students Reporting Online Behaviors by Suitable Target, Motivated Offender, Lack of Guardianship, and by Demographics………………………………………………………....85 viii LIST OF FIGURES Figures 1. Page Type of Personal Information Posted on Social Networking Website………………………………… ....... .……………………………….71 2. Access of Personal Information Provided to an Unknown Person on Social Networking Websites……………………………………………………...…..72 3. Indication of Suitable Target: Social Networking Website and Internet Use…………………………………………….………………………………82 4. Contribution of Personal Information and Experiences with Unknown Persons on Social Networking Websites………………………………………83 5. Location of Computer Use and Guardianship………………………..………..84 ix 1 Chapter 1 Introduction The continual technological advancement that allows for efficient communication methods through e-mail, instant messengers, chat-rooms, and websites are just a few ways that the internet can be used to facilitate communication (D'Ovidio, Mitman, ElBurki, & Shumar, 2009). For example, the benefit of e-mail allows users an alternative way to sending postal mail in an electronic form in just a matter of seconds and instant messenger programs allow for real-time text communication, which provides an alternative to other out-dated forms of communication (D'Ovidio et al., 2009). Lastly, social networking websites allow users to interact with each other through several means of electronic picture sharing, instant messaging, e-mailing, or providing links to other websites. However, in addition to the multiple benefits provided by these advancements in technology, they have also provided predators with alternative and anonymous methods for victimizing individuals (Marcum, 2008). Victimization, or more specifically, interpersonal victimization, has become a major concern throughout society today. According to Davis, Lurigio, & Herman (2007), interpersonal victimization can be defined as "harms that occur to individuals because of other human actors behaving in ways that violate social norms" (p.10). We often refer to multiple forms of victimization that do not adequately represent interpersonal victimization (Davis et al., 2007). For example, motor vehicle accident victims or victims of natural disasters are not categorized as interpersonal victims (Davis et al., 2007). The more general referent for the term victimization is interpersonal victimization. With this 2 in mind, Davis et al. address interpersonal victimization and the issues of malice, deception, injustice, and morality compared to impersonal forms of accidents or disasters that occur during general forms of victimization. There are many contributing factors to interpersonal victimization; however, the most common method of interpersonal victimization occurs through face-to-face encounters (Combs-Lane& Smith, 2002). Prior to the advent of the internet, interpersonal victimization occurred among acquaintances, friends, family members, and complete strangers without the assistance of computers (Cassell & Cramer, 2007). However, with the belief that there was a rise in sexual victimization, eventually a form of "moral panic" was prescribed by the media and researchers began to produce studies in an effort to identify victimization risk characteristics (Ben-Yehuda & Goode, 1994). For example, according to Parks and Miller (1997), "interpersonal victimization risks may be greater in certain social settings, such as bars, where alcohol is consumed and aggression is more likely" (p.513). Also, personal and property crime victimization studies suggest that participating in leisure activities away from home and other lifestyle choices were likely to increase victimization risk factors (Arnold, Keane, & Baron, 2005). In another study, research has shown that a combination of behavioral factors (alcohol use) and leisure activities (going to the mall or eating out) are associated with increased risk of criminal victimization among college women (Mustaine & Tewksbury, 1999). Another study found that the exposure to potential predators serves as a risk factor for future sexual victimization, particularly in interpersonal situations where the individual is perceived as a vulnerable target (Parks & Miller, 1997). Lastly, a study determined that women in college have an 3 increased risk of sexual victimization because they tend to provide opportunities in time and space with potential offenders while having little to no guardianship (Fisher, Cullen, & Turner, 2002). Therefore, several studies revealed that with an increase in social activities among face-to-face encounters there was a proportional increase in victimization risk factors (Ben-Yehuda & Goode, 1994; Parks & Miller, 1997; Arnold, Keane, & Baron, 2005; Mustaine & Tewksbury, 1999; Fisher, Cullen, & Turner, 2002). Statement of the Problem The emerging innovations of the internet have created a more efficient and clever avenue of interpersonal victimization for predators, and unfortunately, research on internet use has demonstrated that internet use has significantly increased in the past 10 years (Addison, 2001). Furthermore, the advent of the internet has created an environment of sexual exploitation in the forms of chat-rooms, blogs, instant messengers, webcam chats, picture exchanges, and most importantly for this study, social networking websites. As new developments of technology emerge, society and its activity patterns are constantly transforming (Madriz, 1996). A recent report discovered that 87 percent of youth are using the internet and that percentage of youth is projected to grow (Rainie, 2006). With this in mind, as innovative technologies emerge, the creation of different methodological victimization tactics also emerge (Wolak, Mitchell, & Finkelhor, 2006). For example, according to several studies on internet use by youth, it has been found that increasing numbers of users are experiencing unwanted exposure to sexual material, sexual solicitation, and unwanted non-sexual harassment (Marcum, 2008). Moreover, not only are there a greater number of users accessing the internet to socialize, these 4 individuals are also spending more time on the internet. Unfortunately, it is evident that while the use of social networking websites can produce positive interaction and develop enjoyable relationships for its users, these individuals are spending extensive amounts of time online and are also placing themselves at an elevated level of interpersonal victimization risk (Izenberg & Lierbman, 1998). The recent popularity of social networking websites has created fear among law enforcement agencies, users, and guardians (Marcum, 2008). The issue with the frequent use of social networking websites is the increased risk for interpersonal victimization (Marcum, 2008). It has been shown that the deceptive capability of the internet has created a sense of fear among users (Choo, 2008). In fact, according to Johnson (2006), "many sexual predators use fake identities complete with false pictures and information to mask their true identities in order to seem more enticing to those with whom they wish to interact" (p.4). Unfortunately, these predators, or "cybercriminals" can hide their history of communication, digital pictures, and video files by using password authentication, encryption and stenographic techniques (Choo, 2008). These efforts often hinder law enforcement and investigators in their attempts to decrease online victimization of users and other acts of sexual exploitation (Choo, 2008). Furthermore, anonymity of communication can be provided through the use of the Onion Router, an "anonymising protocol" that allows data to be routed through numerous servers. According to Marks (2007), "the device uses cryptography to obscure the data path and hence make it untraceable for law enforcement” (p. 25). With these methods of masking identity in mind, the fear among the use of social networks has produced multiple beliefs 5 that social networking websites are the new street corner of our society, and that they are a predator's dream come true (Apuzzo, 2006). Collectively, the underlying issue is that even though identities are masked, the users then begin to believe that through constant contact or social interaction through the internet that the stranger may actually be completely honest or sincere. However, multiple studies show that this is not true. This study examines why social networking website users may want to interact with strangers and why they may feel comfortable doing so. Need and Purpose of Study The current study focuses upon social networking websites in order to examine why users may want to interact with strangers that they encounter while using such sites. A questionnaire will be administered to survey the use of a computer and the internet by undergraduate students majoring in criminal justice at California State University, Sacramento. This study will investigate the purpose and intention of the user(s) social networking profile before collecting data on how often these individuals are e-mailed, instant messaged, or asked to be common "friends" on the site by complete strangers. In addition, it is pertinent in this study to understand whether or not these users have privatized their user profiles, for it may be hypothesized that those with privatized user profiles may have a lower rate of victimization risk. Following, it must be noted whether or not users interacted with strangers while using social networking websites. If the users have interacted with strangers among the websites, it is important to determine if the users are aware of interpersonal victimization risk factors described previously. 6 Currently there is a perception that there are numerous dangers associated with the use of social networking websites creating a "moral panic" (Perkel, 2008). However, even though there is a copious amount of literature supporting the correlation with increased use of social networking websites there is an increased risk for potential victimization, few studies have analyzed the rates of interpersonal victimization while using such websites. More importantly, few emerging studies have hypothesized that social networking websites are being used for individuals to explore their identity and sexuality; however, there are no studies that have analyzed why individuals interact with strangers among these sites. This may provide additional understanding of prevention, awareness, and theory involving the interaction of strangers and users of social networking websites. First, this study may create or provide more effective preventative strategies for users when encountering strangers while using social networking websites. Also, this study may create awareness among guardians who monitor individuals while accessing such websites. Finally, this will apply Cohen and Felson's 1979 Routine Activities Theory to progressing technologies and alternate forms of solicitation between strangers and social networking website users. Hypotheses It is suggested that with the advent of the internet, interpersonal victimization may have increased due to the use of social networking websites (D'Ovidio et al., 2009). Most notably, previous research has suggested that increasing numbers of users are experiencing unwanted exposure to sexual material, sexual solicitation, and unwanted 7 non-sexual harassment (Marcum, 2008). It is also unfortunate that the internet provides the ability for predators to mask their true identity or block law enforcement’s capability of tracking their data path and server route (Ogilvie, 2001). In addition, sufficient amounts of research support the notion that with increased use of social networking sites there is increased risk for potential victimization, but this research will focus on a different aspect of interpersonal victimization. This current research will determine if users of social networking websites have ever been contacted by an unknown person, and more specifically, why these users may want to interact with these strangers that they encounter while using such sites. The research will focus on three independent variables as three dimensions of interpersonal victimization: motivated offenders, suitable targets of criminal victimization, and capable guardians of persons or property. The three dimensions are concerned with the rates of interpersonal victimization as they relate to the motivated offenders that are involved, how the subjects are targeted for suitable victimization, and if there is a lack of guardianship over desired persons or things. The researcher has developed three hypotheses for the current study: Motivated Offenders H1A: Interpersonal victimization rates will increase when there is an increase in the number of motivated offenders encountered. H0A: Interpersonal victimization rates will not differ depending on the increase of motivated offenders encountered. 8 H1B: Interpersonal victimization rates will increase when there is an increase in the number of suitable targets (subjects who provide personal information) that are easy to access by an offender. H0B: Interpersonal victimization rates will not differ depending on the increase of suitable targets that are easy to access by an offender. H1C: Interpersonal victimization rates will increase when there is a lack of capable guardianship of persons or security measures present. H0C: Interpersonal victimization rates will not differ depending on the lack of capable guardianship of persons or security measures present. Theory The hypotheses enable the researcher to: first, determine if there are specific predictors that may increase one’s likelihood to engage with strangers among social networking websites. For it is believed that when the variables are combined, they produce a heightened effect on the level of interpersonal victimization rates (Cohen & Felson, 1979); Second, to provide more awareness strategies for users when encountering strangers while using social networking websites. Additionally, this may create awareness among guardians who monitor individuals while accessing such websites. Routine activities theory, developed by Cohen and Felson (1979), may help explain why variability may be present in victimization. This theory states that changes in crime are due to the opportunities of offenders (Cohen & Felson, 1979). Furthermore, these changes may be a result of a convergence in time and space of motivated offenders, targets that are viewed as being suitable by the offender, and a lack of guardianship over 9 the desired persons or things (Cohen & Felson, 1979). According to Cohen and Felson (1979), many theories only take into consideration specific time periods and groups, whereas routine activities theory attempts to explain all fluctuations in crime. Routine activities theory is based on the presumption that individuals performing daily routines may encounter an incident of victimization (Cohen & Felson, 1979). The incident may only occur if the convergence of those with criminal motivations or intentions are present (Cohen & Felson, 1979). Daily routines are acts that are considered to be essential to someone’s life, such as going to the gym, accessing his or her e-mail account, or working. Many criminologists suggest that a person’s lifestyle increases their risk of being exposed to criminals and criminal activities (Parks & Miller, 1997). Therefore, those seen as being the easiest targets due to their lifestyle choices will face higher crime rates compared to those who place themselves at unequivocal risk (Arnold, Keane, & Baron, 2005). Collectively, the opportunities presented to violators to perform criminal acts must be removed in order to eliminate victimization. Cohen and Felson (1979) suggest that increased guardianship will eliminate the opportunity for criminal acts. Before the introduction of the internet, interpersonal victimization occurred among acquaintances, friends, family members, and complete strangers in a traditional face-to-face manner (Cassell & Cramer, 2007). Over time, reports of sexual victimization were on the rise, and researchers began to produce studies in hope to identify victimization risk factors (Ben-Yehuda & Goode, 1994). For example, Parks and Miller (1997) reported that risks are greater in specific social settings, such as bars. It was found 10 that participating in leisure activities away from home and other lifestyle choices were likely to increase victimization risk factors (Arnold, Keane, & Baron, 2005). Mustaine and Tewksbury (1999) suggested a combination of behavioral factors (i.e. alcohol use) and leisure activities (i.e. going to the mall or eating out) are associated with increased risk of criminal victimization among college women. The exposure to potential predators serves as a risk factor for future sexual victimization, particularly in interpersonal measures where the individual is perceived as a vulnerable target (Parks & Miller, 1997). Moreover, increased victimization occurs because opportunities in time and space with potential offenders converge while having little to no supervision (Fisher, Cullen, & Turner, 2002). While referring to the variables comprised of Cohen and Felson’s (1979) routine activities theory, interpersonal victimization is possible to occur while using social networking websites. However, due to the assembly of the internet, the risk of victimization while using social networking websites may be presented differently. In this thesis, the researcher focuses on the concept of motivated offenders to a broader degree. For those accessing social networking websites, it will be useful to divulge victimization rates for online crimes of harassment, stalking, sexual exploitation, and identity theft. As stated above, the three variables in discussion are the presence of motivated offenders, the appearance of a suitable target, and the lack of guardianship over something or someone that may be desired by an offender. Furthermore, in this thesis a suitable target will be defined by crimes committed against those while accessing the internet, or more specifically, those using social networking websites. In this study, the 11 internet is viewed as a suitable target for offenders because there is an ease of access to individuals. A motivated offender has the advantage of grooming numerous individuals at one time and may remain anonymous if desired. In addition to anonymity, a motivated offender has the ability to appear as any person that they desire. For example, the internet may allow an adult to portray him or herself as being much younger than they are in reality. Lastly, the lack of guardianship occurs when individuals do not use social networking websites with caution due to the belief that conversing with someone over the internet is not a potential threat, and recent studies by Pierce (2006) suggest that there is a correlation between trusting strangers online and giving out personal information. Therefore, those who access the internet and social networking websites at a higher rate are at a higher risk of interpersonal victimization. Methodology A sample of California State University, Sacramento undergraduate students enrolled in criminal justice courses completed an anonymous questionnaire about their use of social networking websites and engagement with unknown persons. Current research reveals possible connections between social networking websites and increased likelihood of victimization. Therefore, the questionnaire was designed to collect information on why some individuals may feel comfortable engaging with unknown persons through social networking websites. This study utilized a random cluster sampling technique selecting California State University, Sacramento students enrolled in criminal justice undergraduate courses. Undergraduate criminal justice courses were selected as individual clusters, simple 12 random sampling was applied to each course offered, and then the fifty clusters were randomly selected with the use of a random sampling generator. Data were collected from students enrolled in the randomly selected courses through a voluntary questionnaire. The questionnaire (see Appendix A) consisted of 20 close-ended questions and one open-ended question requesting subjects to indicate the types of activities performed on the internet, the location of their computer use, how often the internet is used, whether or not there is presence of another person while using the computer, whether or not they are registered to social networking websites, information they may have posted on their personal social networking website, whether or not their personal social networking website is privatized, how often they have been requested or have “friended” an unknown person, whether or not they have conversed with the unknown person they have “friended,” whether or not they have given personal information beyond what is accessible on their personal social networking website, whether or not they do any of the aforementioned activities with the use of a mobile device, whether or not they feel safe engaging with unknown persons among social networking websites, their gender, their age, and their marital status. SPSS will produce figures suggesting whether specific predictors may increase one’s likelihood to engage with strangers among social networking websites. The variables will be measured through a survey polling personal use of a computer and behaviors while using social networking websites, privatization of social networking websites, and types of interpersonal victimization that may occur because of social networking website use. 13 Scope and Limitations The study attempts to analyze engagement with unknown persons with the ambition of unveiling occurrences of interpersonal victimization due to the use of social networking websites. There are several limitations to this study. The primary limitation is that those surveyed were students from criminal justice courses offered through California State University, Sacramento. The survey was not offered to the general public. This limits the ability to generalize all academic majors, as well as other college campuses and college-aged youth in general. Further research examining interpersonal victimization on social networking websites throughout the nation would be interesting. Another limitation to this study is the omission or integrity of data from each reporting subject. With an interviewer not being present it is problematic because it will be difficult to clarify incomplete answers, control the quality of answers provided, or further explain the survey if questions of clarification are asked by individual subjects. Organization of the Study The remainder of this study will examine the presence of predictors that may increase one’s likelihood to engage with strangers among social networking websites. The subsequent chapters will proceed as follows. Chapter two reviews current research illustrating interpersonal victimization through traditional offline environments, as well as, contemporary online environments. Described in chapter three are the methods used to create a data collection instrument, the action of surveying subjects, and the analysis of the data obtained. Chapter four presents the findings of the research. Lastly, chapter five 14 will conclude presenting a summary of the research, discuss the results, and provide further implications of the research. 15 Chapter 2 Review of Literature Introduction The advent of technology inherently creates problems as much as it lends efficiency, and unfortunately, the internet plays a pivotal role in a few of the major problems it has created (D'Ovidio, Mitman, El-Burke, & Shumar, 2009). Since Licklider created and implemented the electronic global communication system known as the internet, there has been a consistent exponential growth of users (Licklider & Clark, 1962). Recently this growth has raised concerns among researchers focusing on developing social problems and the use of the internet (Mitchell, Becker-Blease, & Finkelhor, 2005). There are a considerable amount of problems concerning the internet that have not yet been discussed because they continue to develop along with technology (Mitchell et al., 2005). Therefore, to demonstrate the need for a review of emerging internet victimization, this study examines the issues within offline and online avenues among the following areas of harassment, stalking, sexual exploitation, and identity theft. Sexual Harassment Sexual harassment is a form of interpersonal victimization that is historically associated with environments such as the workplace and educational systems (LaRocca & Kromrey, 1999; Rubin, 1995). The topic of sexual harassment and its definition has been under continual modification and will continue to change as new forms of harassment emerge (Bradenburg, 1997; Dansky & Kilpatrick, 1997; Dziech, 2003; Dziech & Hawkins, 1998; Hall, Graham, & Hoover, 2004; Paludi, 1997; Williams, Lam, 16 & Shively, 1992). The issue of harassment comes in many forms of behaviors and actions. A social psychological framework for sexual harassment was researched by Pryor, LaVite, & Stoller (1993) describing that both situational factors and factors of an individual person contribute to sexual harassment. In this study, Pryor et al. (1993) used two large scale surveys, one from the U.S. Department of Defense and the other from an organizational assessment. Ultimately, this study focused on the incidence of sexual harassment and hoped to answer a series of questions indicating the frequency that subjects experienced 10 different types of “uninvited, unwanted sexual attention over the last 12 months” (Pryor et al., 1993, p.70). This framework is a fundamental connection towards understanding the variables linked to sexual harassment. This framework illustrates sexual harassment as an interpersonal behavior containing both social and personal elements. In addition, sexual harassment is a behavior that is not always displayed by all individuals. With this in mind, only some individuals may be predisposed to behave in a sexually harassing manner. Plus, only particular situations (not all) may trigger the sexually harassing behavior. However, when the facilitating person and situation factors are present together, this creates a possible opportunity for sexual harassment. Therefore, those who are more likely to sexually harass a victim are only likely to do so if the situational factors are present (Pryor et al., 1993). A historical piece by Koss, Gidycz, & Wisniewski (1987) within sexual harassment literature was one of the first to discuss the nature of sexual victimization among female college students linking person and situational factors together. Koss and 17 colleagues (1987) found that female college students were being sexually harassed within a higher educational environment. Also, Gutek (1981) was one of the first researchers to demonstrate that the majority of sexual harassment offenders were men while majority of the victims were women. Collectively, numerous studies have confirmed that sexual harassment is typically pursued by males against females and that females are most often victims of sexual harassment (Cortina, Swan, Fitzgerald, & Waldo, 1998; Dziech, 2003; Gutek, 1981; Kalof, Eby, Matheson, & Kroska, 2001; Paludi, 1997; Russell & Oswald, 2001). Furthermore, research implies that sexual harassment is most likely to occur among “females, graduate students, women in nontraditional fields, minority females, disabled persons, divorced women, young and naïve females, persons who were sexually abused, and homosexuals” (Clodfelter, Turner, Hartman, & Kuhns, 2010, p.457). In order to further confirm findings from sexual harassment research, Clodfelter et al. (2010) studied a random sample of 750 college students from a southeastern university. E-mails were initially sent to the subjects, and then another e-mail was sent giving a link to a website that would host a survey (Clodfelter et al., 2010). The study sample consisted of 65 percent females and 35 percent males and the majority were White (Clodfelter et al., 2010). The research revealed that 22.7 percent of the subjects reported experiencing a form of sexual harassment (Clodfelter et al., 2010). Among those subjects that were sexually harassed, 92.9 percent were by other students and 50.0 percent were by strangers (Clodfelter et al., 2010). More specifically, most of the offenders were males, most often the offenders were White, most of the victims were victimized while alone, and almost all of the victims did not consume alcohol prior to their incident (Clodfelter et al., 2010). 18 The finding that almost all of the victims did not consume alcohol prior to their harassment is significant because it contradicts most literature documenting the prevalence of alcohol during more serious types of victimization (Fisher, Cullen, & Turner, 2000; Testa & Parks, 1996). Lastly, proximity and guardianship were two areas that were also related to experiencing sexual harassment (Clodfelter et al., 2010). A routine activities theory explanation of sexual harassment was produced by DeCoster, Estes, and Mueller (1999) which focused on the areas of proximity, guardianship, and target attractiveness. The research tested hypotheses using data from a national company in the industry of telecommunications (DeCoster et al., 1999). As previously noted by Pryor et al. (1993), the opportunity for sexual harassment is greatest when a person or group of people have routines or daily activities that bring them and their property in contact with motivated offenders. Similarly, Cohen and Felson (1979) speculated that with the absence of guardians, victimization is elevated during routine and daily activities while in the presence of motivated offenders. Therefore, DeCoster et al. (1999) aimed to apply Cohen and Felson’s routine activities theory to sexual harassment in an effort to explain victimization. Within DeCoster et al.’s study (1999), a total of 6,485 employees (3,316 males and 3,169 females) completed a questionnaire which was designed to measure sexual harassment among the workplace. It was discovered that the presence of guardianship plays a critical role in sexual harassment victimization (DeCoster et al., 1999). Specifically in this study, both supervisors and coworkers were supportive in protecting women from sexual harassment (DeCoster et al., 1999). It was also found that proximity 19 to motivated offenders increased the possibility for sexual harassment (DeCoster et al., 1999). For example, women who are among male-dominated jobs are more likely to experience sexual harassment than those in female-dominated settings (DeCoster et al., 1999). With this in mind, it can also be noted that smaller work environments and a high volume of employees also increases their likelihood of sexual harassment due to increased probable exposure (DeCoster et al., 1999). Lastly, individual characteristics “indicative of target attractiveness” were deemed critical for understanding sexual harassment (DeCoster et al., 1999, p.42). Although the findings were not concrete in this study, it was suggested that the most attractive subjects are considered more powerful than their counterparts (DeCoster et al., 1999). Therefore, the preliminary evidence suggests that power-threat issues may be important in understanding the behavior behind possible motivated offenders (DeCoster et al., 1999). In contrast, DeCoster and his colleagues (1999) also suggested that this phenomenon of target attractiveness may also apply to vulnerable-victims perspective in that “the finding that single women are at increased risk of harassment may indicate that these women are viewed as threatening to traditional female roles (power threat) or that these women are less protected than their married counterparts (vulnerable victim)” (DeCoster et al., 1999, p.42). Unfortunately, the research was unable to clarify either of these two findings; however, it is conclusive that proximity, guardianship, and target attractiveness serve as critical roles in creating sexual harassment opportunities (DeCoster et al., 1999). In addition to the previous examples of face-to-face sexual harassment, with the advent of technology, online forms of sexual harassment are now taking place 20 (Anonymous, 2009). Mitchell et al. (2005) found that individuals reported being victimized while using online sites in sexual and nonsexual forms. One type of harassment includes posting defamatory or embarrassing personal information about others (Mitchell et al., 2005). Also, it appears that online harassment is rarely reported to law enforcement because most individuals perceive that the victimization is not that serious (Finn, 2004). Furthermore a study conducted by the Internet Safety Task Force, led by Berckman Center for Internet Society at Harvard University aimed to determine which of today's technologies could best address online safety risks (Anonymous, 2009). Before the task force began its work on technology, it studied research to determine the actual threats youths face (Anonymous, 2009). According to the final report requested by 50 state Attorney Generals, online harassment and cyber-bullying appear to be the most common risks youths face online rather than online solicitation (Anonymous, 2009). In another study, nonrandom samples of 354 criminal justice students from the University of Nevada, Las Vegas were surveyed on victimization while using social networking websites (Taylor, 2008). The sample contained 60.5 percent females and 39.3 percent males, and the majority of the subjects were less than 21 years of age (Taylor, 2008). Also, the subjects were predominantly White (Taylor, 2008). According to Taylor (2008), there were more non-threatening sexual harassment behaviors occurring outside of the internet. However, when comparing verbal sexual harassment while on and offline, the rates were about equal (Taylor, 2008). In addition, sexual harassment behaviors that were considered “fear-inducing” or “threatening” had higher rates offline than online (Taylor, 2008). However, most importantly, according to Taylor (2008), a majority of the 21 subjects stated that they have experienced an overwhelming amount of sexual harassment online rather than offline. In a 1999 Youth Internet Safety Survey, the prevalence of teenage victimization on social networking websites was examined (Mitchell, Finkelhor, & Wolak, 2001). The study surveyed 1,501 youths between the ages of 10 and 17 who were considered frequent internet users visiting chat-rooms and talking to strangers online (Mitchell et al., 2001). It was found that 56 percent frequently visited chat-rooms, 56 percent talked to strangers while online and nearly 20 percent of the youths were sexually solicited while online (Mitchell et al., 2001). Those who were between the ages of 14 and 17 were solicited more often than those 10 to 13, however, a follow-up Youth Internet Safety Survey conducted in 2005 found that the frequency in the number of sexual solicitations had decreased (Mitchell et al., 2001). Furthermore, in the 2005 survey, 82 percent of those non-aggressively sexually solicited were between the ages of 14 and 17 (Mitchell et al., 2001). Almost 75 percent had posted personal information online, and nearly 50 percent used the internet solely for chat-room use (Mitchell et al., 2001). In contrast, the small percentage of those who were aggressively solicited online, 81 percent posted personal information and almost 70 percent used the internet solely for chat-rooms (Mitchell et al., 2001). The survey concluded that risk factors for online solicitations included being female, using chat-rooms, engaging in conversation about sex, and revealing personal information (Mitchell et al., 2001). Another study employed a sample of 1,501 youths between the ages of 10 and 17 who had used the internet at least once a month for the previous 6 months were 22 interviewed about their experiences while using the internet (Mitchell, Ybarra, & Finkelhor, 2007). In this study, the subjects were 53 percent boys and 47 percent girls, most were non-Hispanic/White (73 percent), and 63 percent of the youth lived with both of their parents at the time of the interview (Mitchell et al., 2007). Also, more than three fourths of the parents reported at least some college education and half of those surveyed had an annual income of $50,000 or higher (Mitchell et al., 2007). The authors suggested it was important to recognize that online sexual harassment may be an extension of existing experiences prior to the advent of the internet (Mitchell et al., 2007). For example, research suggests that for some youth, there may be no real distinction between online and offline sexual harassment (Mitchell et al., 2007). Moreover, others feel that the internet may have introduced a new form of a problem that requires new responses or interventions (Mitchell et al., 2007). Conclusively, the authors of this interpersonal victimization study found that 64 percent of the youths experienced at least one online or offline victimization in the past year (Mitchell et al., 2007). More specifically, 23 percent of the youth reported at least one of the two forms of online victimization (Mitchell et al., 2007). They also found that 6 percent reported online harassment, and that 19 percent had experienced online sexual solicitation (Mitchell et al., 2007). This finding is significant because it contradicts the Internet Safety Task Force's finding that online harassment is more common than online solicitation. Finn (2004) examined online harassment at the University of New Hampshire through a survey of undergraduate students. Finn developed a survey that focused on the types of online harassment that occurred through the use of e-mail and instant messengers 23 to insult, harass, threaten, or send pornography (Finn, 2004). Students were asked whether or not they reported online harassment, their frequency of computer use, and demographic questions (Finn, 2004). A majority of the students received pornography at 58.7 percent (Finn, 2004). Further results indicated that approximately 10 percent to 15 percent of students had experienced online harassment from strangers, an acquaintance, or a significant other (Finn, 2004). More specifically, the most frequent portion of harassment reported by the students was from strangers at 16.2 percent through e-mail and 19.3 percent through an instant messenger (Finn, 2004). Also, over 14 percent reported that they received harassing e-mails even after they requested the action to stop, whereas over 13 percent received similar instant messages after they requested the action to stop (Finn, 2004). Finally, over 81 percent reported using instant messengers once or more a week, over 88 percent reported never using a chat-room, no demographic differences were found in relation to the use of e-mail, instant messengers, or chartrooms, and no differences in online harassment were associated with the frequency of internet use (Finn, 2004). According to Kennedy and Taylor (2010), a 77-question self report survey study was conducted at a Southwest university. The study focused on personal use of social networking websites, personal activities conducted while online, and the types of victimizations that may have been experienced due to the use of social networking websites (Kennedy & Taylor, 2010). The subjects were 354 undergraduate criminal justice students (60 percent male and 40 percent female) who received course credit for their participation; however, participation was voluntary and the students could choose 24 not to complete a portion of the survey and still receive full credit (Kennedy & Taylor, 2010). Respondents were debriefed after completing the survey if they felt they had found the survey to be discomforting (Kennedy & Taylor, 2010). The participant's average age was 22 while 25 percent of the sample was 18 and the remaining majority being under 21 (Kennedy & Taylor, 2010). Most of the students were Caucasian (60 percent), 13 percent Hispanic, 10.5 percent African-American, 8.8 percent Asian, and 7.7 percent being of other (Kennedy & Taylor, 2010). The study concluded that sexual harassment and a pestering form of harassment occurred most frequently online (Kennedy & Taylor, 2010). Verbal harassment appeared to occur equally online and offline (Kennedy & Taylor, 2010). Fearful threats also occurred more frequently online rather than offline (Kennedy & Taylor, 2010). It was found that those with private profiles received far less harassment than those with semi-private or non-private profiles (Kennedy & Taylor, 2010). Furthermore, over 31 percent of the students had an online relationship that later lead to a face-to-face meeting and an offline relationship (Kennedy & Taylor, 2010). In contrast, 29 percent of the students had blocked a contact online to prevent future contact (Kennedy & Taylor, 2010). Stalking Stalking is a form of interpersonal victimization that can be defined as the same person repeatedly exhibiting pursuit behaviors that appear obsessive and therefore makes a respondent afraid or concerned for his or her safety (Fisher, Cullen, & Turner, 2002). Recently, in the past two decades, stalking has emerged as a major concern nationwide, and has most notably become a concern after actress Rebecca Shaeffer was shot to death 25 in 1989 by an obsessed fan (McAnaney, Curliss, & Abeyta-Price, 1993). The emergence of this social problem has created policy intervention and lead to the implementation of several educational organizations, victim service organizations, and state and federal laws (Fisher et al., 2002). In short, the issue of stalking is documented to precede other forms of violence and will be greatly discussed (Dietz et al., 1991). In 1989 an obsessed fan had stalked actress Rebecca Shaeffer for two years before murdering her. That same year, five other women were murdered within Orange County after being stalked by former boyfriends or spouses (McAnaney et al., 1993). The following year the first anti-stalking law was passed in California (Fisher et al., 2002). Currently all 50 states and the District of Columbia have enforced anti-stalking laws (Fisher et al., 2002). In addition to states implementing anti-stalking laws, the federal system has incorporated anti-stalking laws that do the following: enforce anti-stalking laws to serve as a model for the states, requires the Attorney General to compile an annual report that will be submitted to Congress containing all of the incidents and information of stalking and how effective anti-stalking legislation has been compared to previous stalking statistics, and prohibit stalking between numerous states and stalking on federal property or jurisdictions (Fisher et al., 2002, p.258). According to an early study regarding stalking by Holmes (1993), it was determined that stalking is a social condition that is attracting attention within areas of the criminal justice system, social sciences, and behavioral sciences. Holmes (1993) concluded that "As criminal justice practitioners, we are concerned with the early identification of those who stalk their victims" (p.326). This is most notable because it 26 has been determined that stalking is presumed to precede other forms of violence (Dietz et al., 1991).Therefore, stalking may lead to more and possibly many other forms of violence such as sexual harassment, sexual assault, domestic violence, and homicide (Fisher et al., 2002). A collection of stalking behaviors, stalking characteristics, and stalking victims have been linked throughout several studies. In general, stalking is mostly directed towards women, the vast majority of offenders are male, most stalkers are young (20 to 34 years of age), stalkers vary in their socioeconomic background, offenders have an above- average intelligence level, and stalking may lead to other forms of violence (Mustaine & Tewksbury, 1999). According to Norris (1988) stalking may lead to sexual assault, according to Keeney and Heide (1994), stalking may lead to homicide, according to Coleman (1997), stalking may lead to domestic violence (Coleman, 1997; Harrell, Smith, & Cook, 1985). Also, it has been shown that on some occasions the offender is a well-known acquaintance of the victim (Coleman, 1997; Harrell et al. 1985). Several studies throughout the years have attempted to estimate the numbers of stalkers within the United States. For example, the National Institute of Justice (1996) and National Victim Center (1997) estimated that there were somewhere between 20,000 and 200,000 offenders. In 1997 the Stalking Victim's Sanctuary estimated that there were more than 500,000 offenders. In contrast, studies also attempt to estimate the numbers of victims. According to the National Victim Center in 1997, it was projected that one in twenty women would be a victim during her lifetime, and in 2000 the National Violence Against Women Survey (NVAW) estimated that more than one million women and 27 almost 200,000 men were stalked that year (Jasinski & Mustaine, 2001). According to Fremouw, Westrup, & Pennypacker (1996), 30.7 percent of their subjects were victims to stalking behaviors, Mustaine and Tewksbury (1999) reported that 10.5 percent of their female subjects had been a victim of stalking, Bjerregaard (2000) found that 24.7 percent of the female respondents were victims of stalking, Tjaden and Thoennes's (1998) study discovered that 8 percent of their female subjects had been stalked at least once in their lives, and Fisher and her colleagues determined that 13.1 percent of their female students were victims of stalking. A study of undergraduate women enrolled at the West Virginia University was conducted to determine the acquaintance and prevention of stalkers that they had encountered (Fremouw, Westrup, & Pennypacker, 1996). Fremouw et al. (1996) surveyed two sets of subjects first acknowledging if they had ever been stalked and then if they had known their offenders. The combination of the subjects revealed that 30.7 percent of them had been stalked and over 40 percent of the subjects were acquainted with the offenders (Fremouw et al., 1996). In addition, according to Fremouw et al. (1996), the subjects primarily chose to simply ignore those who were stalking them or would hang up during their telephone calls. Some subjects confronted the stalker or changed their schedule to avoid the stalker as other means of coping with their obsession (Fremouw et al., 1996). Shockingly, seeking the police or courts for help were often methods of last resort (Fremouw et al., 1996). Another study, led by Coleman (1997) designed a survey which was modeled after Florida's anti-stalking statutes. This small sample study attempted to determine how 28 often women were stalked after ending a relationship (Coleman, 1997). Out of the 141 female undergraduate students that were surveyed from psychology classes, 29.1 percent revealed that they had received repeated and unwanted attention from their former partner after ending the relationship (Coleman, 1997). In addition to the previous examples of offline stalking, with the advent of technology, online forms of stalking are now taking place (D’Ovidio et al., 2009). The same features of the internet that allow people to access new opportunities for education, shopping, entertainment, and love provide new opportunities for crime or influence one to commit crime. For example, Maine's Computer Crimes Task Force reported a rise in reports of online stalking of children. Task Force cases of internet crimes against children soared 237 percent in 2010 (Anonymous, 2004). Overall, the unit's caseload doubled to 1,216 (Anonymous, 2004). The internet and its community provide an avenue for victimization for those who might otherwise not be viable targets for crime if they were not present online (D’Ovidio et al., 2009). The first online stalking law went into effect in 1999 in California, and the current US Federal Anti-Cyber-Stalking law is found at forty seven United States Code section two hundred and twenty three (Hancock, 2000). Cyber-stalking is defined as repeated threats or harassing behavior over e-mail, the internet, or other electronic communications (Hancock, 2000). Moreover, internet stalking can be carried out in the same room as the victim, or as far away as another state or country (Hancock, 2000). Technology allows for stalkers to harass their victims in a manner that allows no need to physically confront them (Hancock, 2000). Unfortunately, there are no clear statistics on 29 the number of internet stalking victims, but an August 1999 report from the Department of Justice estimates that there could be hundreds of thousands affected, and the numbers continue to grow (Hancock, 2000). Since the internet is such a new innovation, there is minimal legislation governing the internet or subsequent research available (Goodwin, 2003). Initiatives to deal with individuals who use the internet for criminal behavior are sparse (Goodwin, 2003). Also, legal institutions are trying to combat the ability for internet crime to cross state and international borders (Goodwin, 2003). However, such operations are difficult (Goodwin, 2003). In addition, the place where the most cyber-stalking information is available is on the internet itself (Goodwin, 2003). Unfortunately, there are few studies surrounding cyber-stalking, but it appears that men are the predominant perpetrators in this form of behavior (Goodwin, 2003). This difference is attributed to the higher number of men “trolling” on the internet (Goodwin, 2003). A nonprofit organization, Working to Halt Online Abuse (WHOA), reports that it receives about 100 requests a week seeking information on how to stop internet stalking from occurring (Finn, 2004). As more people use the internet, the amount of cyberstalking is likely to increase (Finn, 2004). In fact, the construction of the internet may promote cyber-stalking (Finn, 2004). Online environments can lend to a false sense of intimacy or intentions and may potentially promote more cyber-stalking behaviors (Finn, 2004). Also, the sense of anonymity and the lack of social status cues may lead to greater risk-taking behaviors (Finn, 2004). 30 Cyber-stalking is similar to traditional forms of stalking in that it incorporates persistent behaviors that instill fear (Ogilvie, 2001). For example, a woman in Queensland, Australia received multiple e-mails that became more and more threatening after she asked for the e-mails to stop (Ogilvie, 2001). Ultimately, she received death threats from the perpetrator claiming that he was going to video-tape raping her and then upload the video onto the internet (Ogilvie, 2001). In the U.S., a college student harassed five other female students after purchasing information about each of the girls over the internet (Ogilvie, 2001). This stalker sent over 100 messages including death threats and was able to describe their daily activities (Ogilvie, 2001). Each of these offenders' e-mail accounts could be traced and their identities could be established in the same way a letter could be traced through the postal system (Ogilvie, 2001). A majority of these cases did not involve complex forms of stalking, and e-mail was simply being used as an alternative form of communication (Ogilvie, 2001). Unfortunately there are now anonymous remailers that can halt this traceability (Ogilvie, 2001). Anonymous remailers allow the sender's identity to be masked and allow the e-mail content to be concealed (Ogilvie, 2001). As with offline stalking, few examples of stalking are confined to one form (Ogilvie, 2001). While e-mail stalking may be similar to traditional stalking in some instances, it is not restricted to this format (Ogilvie, 2001). Many would assume that personal use of the internet would be needed in order to be victimized by a cyber-stalker; however, the following incident proves otherwise (Goodwin, 2003). A woman met a 51 year old male through church (Goodwin, 2003). Eventually the man decided to ask the woman out on continuous dates but the woman 31 always refused (Goodwin, 2003). Soon after, the man retaliated by posting the woman's personal details on the internet, including her physical description, address, telephone number, and details of how to bypass her home security system (Goodwin, 2003). In addition, he posted false rape and sexual fantasies to forums online (Goodwin, 2003). Multiple men soon arrived at her home to take advantage of these alleged fantasies, as well as leaving sexual phone messages on her machine (Goodwin, 2003). The woman then posted messages to her door stating these requests were false, and the perpetrator followed by posting messages online that these were simply tests to determine who was in fact worthy of her fantasies (Goodwin, 2003). The victim was eventually forced from her home, suffered from weight loss, lost her job, and developed a fear of going outside (Goodwin, 2003). Another example of online stalking includes a female school teacher who decided to meet a man (Andrew) from the internet offline that she originally met while online (Goodwin, 2003). After she met Andrew, she began to get nervous when he wanted to get married right away (Goodwin, 2003). Therefore, she immediately made it clear that she had no romantic interest (Goodwin, 2003). However, he persisted with email messages, letters, packages, and telephone messages (Goodwin, 2003). He began to watch her through the windows of her work and began to develop friendships with other people in her life (Goodwin, 2003). He called her mother, neighbor, and friends, and only stopped after she contacted the police and he was later prosecuted for harassment (Goodwin, 2003). Youths are especially involved in online socialization with various methods of internet communication, such as e-mail, chat-rooms, instant messaging, and social 32 networking websites (Marcum, 2008). Moreover, not only are there more teens using the internet to socialize, they are also spending more time online (Marcum, 2008). Unfortunately, while the use of the internet can produce positive interaction and relationships for its users, these youths that are spending extensive amounts of time online are also placing themselves at risk for victimization (Marcum, 2008). The study by Marcum indicated that communicating with people online and providing personal information to online contacts increased the likelihood of victimization in the form of stalking (Marcum, 2008). Students attending colleges are increasingly dealing with cases of cyber-stalking (Finn, 2004). It is believed that students are especially vulnerable to stalking and/or cyber-stalking because they interact within a small community where class schedules, phones, and e-mails are easily accessed (Finn, 2004). Most college students are in the age range of 18 to 29 which coincides with stalking profiles (Finn, 2004). It is also argued that stalking may become a problem on college campuses because most college students are at the age where they are seeking a sexual relationship (Finn, 2004). A study conducted by Rosen examined 1,257 users of the social networking website, MySpace (Rosen, 2006). It was found that only 1.5 percent of the sample reported being stalked and only 4.6 percent of that sample reported being solicited for sex (Rosen, 2006). It was also found that women were more likely to have been solicited for sex while online (Rosen, 2006). Consequently, those who had been actively using the website for an extended period of time increased their likelihood of victimization (Rosen, 2006). 33 Finally, nonrandom samples of 354 criminal justice students from the University of Nevada, Las Vegas were surveyed on victimization while using social networking websites (Taylor, 2008). This study concluded that more subjects had been victimized offline than online (Taylor, 2008). Similar to Kennedy and Taylor's 2010 study, no students claimed they had changed their daily activities due to a stalking incident offline; however, several students changed some of their personal information, including phone numbers, address, or e-mail address due to online stalking (Taylor, 2008). Sexual Exploitation Sexual exploitation is a form of interpersonal victimization that can be defined as the use of another person in non-consensual and/or consensual sex for profit (Mitchell, Jones, Finkelhor, & Wolak, 2011). Unfortunately, there are an abundance of forms of sexual exploitation, and together, they vary considerably in terms of frequency, severity, implication, prevention, and intervention (Mitchell et al., 2011). Some examples of sexual exploitation include the production and sale of pornography, prostitution, trafficking of individuals for sex, the mail order bride trade, forced marriages, and forced performances in strip clubs (Mitchell et al., 2011). Sexual exploitation is a form of interpersonal victimization driven by exploiters (Fontana-Rosa, 2001). An exploiter is a person who is exclusively interested in a monetary profit (Fontana-Rosa, 2001). Even though the exploiter may not be a pedophile, he can be considered a sex offender in that he specifically exploits others for a profit (Fontana-Rosa, 2001). Most literature describes sexual exploitation as being driven by financial or economic benefit for another person, and financial benefits may include monetary and nonmonetary profits (Mitchell et 34 al., 2011). Nonmonetary items include food, shelter, drugs, and other forms of commodities for trade (Mitchell et al., 2011). It should also be noted that this form of victimization is becoming increasingly popular among children, and most importantly for this study, on the internet (Mitchell et al., 2011). Sexual exploitation is one of the biggest and fastest growing businesses of organized crime in the world (Walker-Rodriguez& Hill, 2011). It is estimated that nearly 293,000 American youths are at risk of falling victims to sexual exploitation each year (Walker-Rodriguez& Hill, 2011). The majority of these youths are those who have runaway and have succumbed to the life of prostitution through mechanisms of sexual exploitation, and research concludes that these children generally come from abusive homes (Walker-Rodriguez& Hill, 2011). Additionally, other victims of sexual exploitation are forced into the prostitution lifestyle through abduction (WalkerRodriguez& Hill, 2011). Sexual exploitation is a notoriously vague topic for researchers within the United States, the inherently concealed operation of this victimization makes it difficult for researchers to obtain data on the number of individuals affected by these crimes. With this in mind, the lack of literature on sexual exploitation reflects that challenge. However, there is some research that has revealed the characteristics of sexually exploitive predators and the demographics of the victims at hand (Walker-Rodriguez & Hill, 2011). The media often has highlighted extreme forms of sexual exploitation, reporting stories of how victims who have trusted strangers have been raped and murdered, and the offline 35 exploitation methods of predators hanging out by schools and parks, looking for specific victims to prey upon (Walker-Rodriguez & Hill, 2011). Over the past couple of decades, research shows a convergence of similar characteristics among those victimized by sexual exploitation (Kramer & Berg, 2003). They include those who are most likely to share similar characteristics of being from single-parent households, being isolated, having family problems, having low selfesteem, poor social skills, and are introverted (Kramer & Berg, 2003). One of the most common forms of entrance into sexual exploitation is prostitution. According to Kramer and Berg (2003), common risk factors associated with entry into prostitution includes childhood abuse, behaviors reflecting running away from home, homelessness, and drug addiction. Furthermore, entry into prostitution can occur first and increase the likelihood of experiencing other forms of sexual violence (Kramer & Berg, 2003). It has been well documented that those involved in prostitution have high rates of sexual abuse, and in turn, victims of sexual abuse have been shown to be particularly vulnerable to becoming involved in abusive and sexually exploitive relationships as adults (Kramer & Berg, 2003). According to Simons and Whitbeck (1991), an analysis of 40 adolescent runaways and 95 homeless women revealed that sexual abuse has a significant impact on the probability of entry into prostitution. In 2000, Tyler, Hoyt, and Whitbeck reaffirmed these previous findings when concluding that sexual abuse in the home has a direct positive effect on sexual victimization of adolescents on the streets. It is a trend that women in prostitution often report a history of childhood physical abuse as well as sexual 36 abuse (Kramer & Berg, 2003). In recent studies, 60-70 percent of prostitutes report being abused as children (Kramer & Berg, 2003). For example, through the use of event-history analysis, it is possible to assess the impact of childhood risks and the likelihood of entry into prostitution (Kramer & Berg, 2003). According to Kramer and Berg (2003), educational level, homelessness, poverty, and many other lower social class characteristics also have a significant effect on the entry into prostitution (Kramer & Berg, 2003). It is well documented that those who were victims to sexual and physical abuse often portray fear, anxiety, depression, selfdestructive behavior, anger, aggression, guilt and shame, an impaired ability to trust, an increased likelihood of re-victimization in adulthood, sexually inappropriate behavior, educational problems, and running away (Kramer & Berg, 2003). Ultimately, the negative and influential events that have occurred in these victim’s lives help understand how sexually exploitive predators operate. It is suggested that sexually exploitive predators prey upon the outcomes of abuse in an individual’s past and coerce individuals into prostitution (Kramer & Berg, 2003). It has become evident that the majority of exploited victims are lured into prostitution as a result of deception, and coercion on behalf of the predators (Blackburn, Taylor, & Davis, 2010). It is also understood that these predators may approach a victim under the pretense of providing a legitimate job, but when the job does not materialize, it becomes obvious that the exploited individual is expected to perform acts of prostitution in order to repay exploiters for food and shelter that they have been providing (Blackburn et al., 2010). Collectively, repayment, rape, 37 physical violence, and other means of control are powerful methods to keep the victim in a lifestyle of prostitution (Blackburn et al., 2010). Another common form of sexual exploitation is sexual trafficking. Recently there have been reports on the news of individuals from all over the world traveling to foreign countries to partake in illegal sexual acts. For example, in March of 2009, three men from Australia were arrested for child sex tourism and possession of child pornography (Blackburn et al., 2010). Also, in July of 2009, a Canadian male was arrested for child sex tourism and the production and distribution of child pornography (Blackburn et al., 2010). Lastly, late in 2009, three American men were expelled from Cambodia for pursuing sexual acts with a ten year old girl and two young boys. The review of these news reports illustrates the problem of child sexual exploitation. Trafficking for the purposes of sexual exploitation is a social problem that has grown exponentially around the world (Blackburn et al., 2010). Unfortunately, data regarding trafficking and sexual exploitation remains sparse, but it is understood that thousands of women and children are being sexually trafficked (Blackburn et al., 2010). It was found that one third of those sexually exploited are younger than the age of 18, and it was also discovered that girls as young as 5 years old are in the sex trade business (Blackburn et al., 2010). It is estimated that profits from child sexual exploitation are roughly a billion dollars a year. Unfortunately, there are no known specific estimates to the extent of the trafficking problem worldwide, and the industry continues to be elusive. Although, it is estimated that 40,000 to 500,000 prostitutes are currently working in areas such as Cambodia (Blackburn et al., 2010). Even though there are no hard statistics 38 representing the true amount of women and children in the sex trade, the estimates at hand clearly illustrate the magnitude of the sexual exploitation problem. A research team facilitated by Blackburn et al. (2010) used interviews and observations in Cambodia and Thailand from June of 2004 throughout 2006 to reveal the complexity and inner workings of sexual exploitation. Over 100 interviews with government officials and another 80 interviews with adult prostitutes and victims of sexual trafficking of children were conducted (Blackburn et al., 2010). The victims that were interviewed were those who were rescued from the sex trade within Cambodia and Thailand (Blackburn et al., 2010). Also, trips to massage parlors, strip clubs, and brothels were conducted to observe real scenarios and settings of the sex trade (Blackburn et al., 2010). In the study it was found that sexual services were commonly coming from females ranging from 7 to 16 years of age (Blackburn et al., 2010). Also, prices ranged from $2 for oral sex up to $35 for vaginal intercourse (Blackburn et al., 2010). In contrast to other research studies, most of the individuals in this sexual market were found not to be forced or kidnapped and then sold into the market (Blackburn et al., 2010). According to the majority of the individuals interviewed, sexual exploitation does occur, but it is not as common as those entering into the trade by themselves (Blackburn et al., 2010). This is believed to be due to the extreme poverty found in Southeast Asia and may not be applicable to the rest of the world (Blackburn et al., 2010). Notably, it was found that 2 girls out of the 80 interviewed had been bought and sold into the trade (Blackburn et al., 2010). 39 Ultimately, sexual exploitation is driven by money (Blackburn et al., 2010). According to the study by Blackburn et al. (2010), extreme poverty and the desire to make money is one of the driving factors behind entering the sex trade. However, not all those entering the sex trade enter as a personal choice (Blackburn et al., 2010). Unfortunately, for those who enter willingly or unwillingly, exploiters often promise legitimate work but then fail to provide (Blackburn et al., 2010). Moreover, victims are afraid to come forward because they may not understand the criminal justice system, speak the language of origin, may be embarrassed, may be afraid of their exploiters, and/or may be without money or passports (Bernat & Zhilina, 2010). Fundamentally, profit is the motivating factor for those who sexually exploit others, and disturbingly, those who are seeking sexual pleasure are often financially supporting sexual exploitation (Blackburn et al., 2010). It is found that places like Cambodia and Thailand in particular are overwhelmed with sexual exploitation due to inexpensive rates, and these rates can often be found on the internet (Blackburn et al., 2010). In addition to offline sexual exploitation, the advance of computer technology has fostered an extreme growth of sexual exploitation among the internet (D’Ovidio et al., 2009). In fact, the internet is currently the primary facilitator of sexual exploitation (Blackburn et al., 2010). The internet allows individuals to discover multiple destinations quickly and easily in search of sex tourism (Blackburn et al., 2010). Also, it has been found that through websites and chat-rooms over the internet, sex tourists share details about the best countries to visit for prostitution (Blackburn et al., 2010). These details go as far as revealing how well the prostitutes performed, the costs for the services, and the 40 individual’s physical characteristics (Blackburn et al., 2010). Interviews provided in the Blackburn et al. (2010) study revealed that men found out about specific areas in Cambodia and Thailand on the internet. The study also found that it was easy to find sex tourism in Cambodia and Thailand on the internet through a general search engine web search (Blackburn et al., 2010). Likewise, it was found that host websites catering to child sex advocates, such as North American Man/Boy Love Association, promote package tours to select countries (Blackburn et al., 2010). As these are only a few examples proliferated by the use of the internet, it is important to review why the internet has flourished as a sexual exploitation medium. The internet has allowed access to information quickly, efficiently, and anonymously for business and communication; however, is has also created a means of seduction for individuals, and lures individuals into potential danger while accessing “friendly” environments, such as chat-rooms and social networking websites allowing for the sexual exploitation of individuals (Marks, 2007). It should be noted that a horrifying feature of sexual exploitation is that the internet provides an additional mechanism of interpersonal victimization (Mitchell et al., 2011). Traditional forms of offline sexual exploitation still occur, but now with the advent of the internet, there are additional forms of seduction and forms of solicitation for individuals to utilize (Mitchell et al., 2011). A rampant form of sexual exploitation that is being dispersed by the internet is child pornography (Lanning, 1984). Child pornography has become one of the most prevalent forms of sexual exploitation since the introduction of the internet (Lanning, 1984). In addition, child pornography is directly linked to the sexual abuse of children 41 (Lanning, 1984). However, the sexual abuse of children during pornographic production is only part of the exploitation (Lanning, 1984). One aspect of child pornography is its intention to lower the inhibitions of children and encourage children to engage in similar activities (Lanning, 1984). According to Lanning (1984), pornography helps to groom children and persuade them that they would enjoy certain sexual acts. Furthermore, such sexual images help exploiters rationalize their requests and help neutralize the abuse (Lanning, 1984). However, all of these uses by exploiters help trap children in abusive situations (Lanning, 1984). Also, sexual exploiters may blackmail individuals by threatening disclosure of photographs they may have shared with them (Lanning, 1984). Exploiters use the internet to make contacts with other exploiters to trade and share homemade or commercial illegal pornography around the world (Blackburn et al., 2010). An exploiter may now disperse pornography from one end of the world to the other with little risk involved with the assistance of the internet (Marks, 2007). Currently hundreds of thousands of sites capitalize from the dispersion of exploitive material, and many pornographers have developed websites, databases, forums, and chat-rooms dedicated to illegal child pornography and pedophilia (Blackburn et al., 2010). Furthermore, criminologists believe that child pornography is the predecessor to further sexual exploitation (Kramer & Berg, 2003). To illustrate the severity of sexual exploitation, Quayle and Taylor (2001) conducted a case study showing how offenders move through a range of offending behaviors. In addition, the researchers discussed how the internet is significant in supporting sexual exploitation by potentially victimizing children through the trading of 42 child pornography and child seduction (Quayle & Taylor, 2001). In the study, the internet was the primary means of communication with others and that communication mostly took place through chat-rooms (Quayle & Taylor, 2001). It is important to note that a participant in the study was able to maintain anonymity and portray himself through deceptive personas (Quayle & Taylor, 2001). For example, he would display himself either as a boy or an adult (Quayle & Taylor, 2001). Furthermore, it was found that the participant initially engaged in conversations and met individuals through chat-rooms (Quayle & Taylor, 2001). After establishing a relationship, he would then attempt to engage in cyber-sex to fulfill his sexual fantasies (Quayle & Taylor, 2001). Interestingly, the participant would use gestures that appeared to be genuine but these efforts were often deceptive in that they were only used to victimize the individual (Quayle & Taylor, 2001). For example, in order to meet victims offline he would present them with gifts in hope to gain further (sexual) contact (Quayle & Taylor, 2001). Conclusively, many researchers believe that the online community supports most sexual deviance (Kramer & Berg, 2003). Moreover, it is suggested that the internet facilitates the sexual exploitation of individuals by providing a new, effective, convenient, and more anonymous environment for predators to access and groom victims, produce and distribute illegal pornography, contact and stalk individuals to engage in sexual acts, and sexual tourism for personal and commercial purposes (Marks, 2007). Identity Theft According to Reisig, Pratt, & Holtfreter (2009), in 2008 there was an estimated 221.3 million people in the United States accessing the internet. Also, in 2007, the 43 internet generated over $136 billion in sales, an increase of 19 percent from the previous year, and annual surveys reveal an overwhelming increase in internet use and online sales (Reisig et al., 2009). On the other hand, the use of the internet can also expose innocent victims to those who access the internet in search of criminal opportunities (D’Ovidio et al., 2009). As previously mentioned, the internet allows for the efficiency of managing emails, obtaining news quickly, or managing finances; however, in spite of the benefits studies show that a majority of internet users and consumers believe the risks associated with internet use are extremely dangerous (Reisig et al., 2009). In fact, reports suggest that nearly 70 percent of internet users believe they are more likely to become a victim of an internet related crime rather than a physical crime (Reisig et al., 2009). Identity theft is a form of interpersonal victimization that can be defined as the unlawful use of another’s personal identifying information, such as their Social Security Number (SSN), date of birth, or mother’s maiden name (Allison, Schuck, & Lersch, 2005). Most literature describes identity theft as being driven by financial gain by fraudulently establishing credit, running up debt, or taking over someone else’s existing financial accounts (Allison et al., 2005). Unfortunately, there is an abundance of forms of identity theft, and they vary in frequency, severity, implication, and prevention. For decades, identity thieves have been obtaining personal information in numerous ways (Allison et al., 2005). For example, traditional offline methods may include stealing a wallet or purse, or digging through someone else’s trash (Allison et al., 2005). In fact, thieves can obtain extremely sensitive information by digging through another person’s garbage (Allison et al., 2005). Additionally, this form of victimization is becoming 44 increasingly popular due to the introduction of the internet and the severity of identity theft has become worse. Identity theft has become a serious problem because it can take a long period of time before a victim is aware that a crime has taken place against them (Allison et al., 2005). Often time, substantial harm has been done to a victim’s credit rating well before they are aware of it (Allison et al., 2005). In some instances, identity theft victims are able to resolve their victimization quickly; however, others face detrimental effects to their financial records (Allison et al., 2005). For example, individuals have been refused loans, have lost job opportunities, or have been arrested for crimes they did not commit (U.S. General Accounting Office, 2009). Many theorists suggest that identity theft is one of the greatest threats to the U.S. economy (Allison et al., 2005). According to the U.S. General Accounting Office (USGAO) (2002) in 1995, identity theft accounted for over $442 million dollars. In 1997, identity theft accounted for over $745 million dollars (U.S. General Accounting Office, 2002). In addition, the Federal Trade Commission estimates that 10 million people or 4.6 percent of the U.S. adult population will become victimized through identity theft within the year (Federal Trade Commission, 2000). This estimate projects possible losses exceeding $50 billion dollars (Federal Trade Commission, 2000). Recently several agencies have introduced bills to prevent identity theft and enforce laws prohibiting such crimes. The Federal Trade Commission is one of the main agencies that collect information regarding identity theft. In 1998, the Identity Theft and Assumption Deterrence Act passed forcing the Federal Trade Commission to keep a log of all complaints made by individuals regarding identity theft (Federal Trade 45 Commission, 2000). According to the Federal Trade Commission (2003), there were 31,117 cases of reported identity theft in 2001, 86,198 in 2002, and 161,819 in 2003. This is a reported increase of 277 percent and 187 percent respectively. In addition, the Federal Trade Commission also compiled victim and offender demographics concerning identity theft (Federal Trade Commission, 2003). Data indicated that the mean age for a victim was 41 years old, the majority of the victims did not know their offender, and it took 12 to 14 months before the victim realized that a crime had been committed against them (Federal Trade Commission, 2003). Despite efforts to prevent identity theft, vulnerabilities remain due to security weaknesses in information systems, and most importantly for this study, through the availability and display of personal information on the internet (Allison et al., 2005). Since the introduction of the internet, individuals have posted personal information for others to view through social networking websites, chat-rooms, instant messengers, and dating service websites (Allison et al., 2005). The development of the internet has created alternate venues for romantic encounters, and internet daters enjoy the interaction through these new technological environments (Rege, 2009). Some of the factors that make online dating attractive are that individuals do not have to leave their home and may access the dating site at any time, they can access the site privately and remain anonymous, they can interact using new forms of interaction, such as, live chats, instant messaging, and they can potentially find their “perfect match” quickly (Rege, 2009). In fact, internet dating has become so popular due to these features that there are now over 1,400 dating sites in North America 46 today (Rege, 2009). Also, it was estimated that individuals spent over $245 million dollars on dating services in 2005, and in 2008, the online dating industry grossed over $957 million dollars making it the fourth highest grossing internet industry (Rege, 2009). However, this industry of successful love match making is also an environment filled with scammers and identity thieves (Rege, 2009). For example, according to the National Consumers League (2008), on average, a victim being scammed lost more than $3,000 dollars in 2007. The digital environment for internet daters allows users to remain anonymous, be instantaneous, alterable, and open to interpretation, making online dating attractive and stimulating (Rege, 2009). However, one of the most recent forms of fraud taking place on the internet is romance scams through dating service websites (Rege, 2009). Romance fraud on the internet is a scam where victims believe that scammers have strong emotional feelings for them, and the romance component of the scam act, acts as bait to lure the victim. Once the scammer has lured the victim, the scammer then persists with identity theft or financial fraud. Researchers have discovered that the process all begins with the creation of a fake profile by the scammer. First, the scammer creates a profile page containing a list of hobbies, a well-articulated biography, and includes a picture. Then the scammer skims the dating website to initiate conversation with a potential victim. This is in an effort to establish a strong bond with the victim to generate trust, confidence, and romance. Over time, the scammer will then request money from the victim through alleged stories of tragic events. These may include recent theft, unexpected hospital expenses from an illness, or to secure funds to meet the victim. The 47 scammer always claims that they need more assistance as the alleged circumstances intensify. The more successful the scammer is in convincing victims of these stories, the more the victim is lured into the scam. Therefore, the scam continues until the victim loses patience or eventually realizes that they are being taken advantage of. Additionally, if victims do not comply with the scammer’s requests the use of emotional blackmail and extortion are used. For instance, if victims are unwilling to send money, then scammers argue that the victim does not have any feelings for them or claim that they were wrong to believe that they were establishing a meaningful relationship. This is only a trick to lure the victim back into the scam. Also, in cases where webcams are used, the scammers record the webcam video and later use these to extort money to prevent broadcast of the films and pictures on the internet. Researchers believe that due to the amount of time taken to establish the relationship with the victim, many victims do not believe they are being scammed making it extremely profitable for the scammer (Rege, 2009). According to Rege (2009), scammers exhibit certain traits in order to take advantage of their victims. For example, they use extreme patience in grooming their victims and establishing trust, they possess basic computer skills and an internet connection, they follow their routines thoroughly, they belong to networks to take advantage of specific resources, and they use neutralization techniques to rationalize their activities (Rege, 2009). All of these traits are important to successfully scam their victims. Consider the fraudulent cases involving Patrick Giblin (Rege, 2009). Giblin created several accounts where he claimed he was a law enforcement officer and he 48 would make contact with individuals online (Rege, 2009). After creating a relationship with a victim, he would then establish further contact through the telephone where he would state he had interest in pursuing a serious sexual relationship (Rege, 2009). Eventually Giblin would request financial help to relocate to the victim’s community (Rege, 2009). Over time, the women would wire him money through Western Union (Rege, 2009). Eventually Giblin was caught and charged in 2005 for defrauding nearly 130 women through dating sites (Rege, 2009). Collectively he gained $320,241 dollars from victims throughout nine different states (Rege, 2009). In another case, Robert Frost was a victim whose identity was stolen and used among various dating websites (Rege, 2009). In this case scammers retrieved pictures that were easily available on the internet (Rege, 2009). Robert Frost was a professional racecar driver, and in 2007, Frost noticed on several occasions women were acting strange towards him (Rege, 2009). For example, he was tracked down, sent flowers, and recognized at several public airports by women he had never met in the past (Rege, 2009). Unaware to Frost, his photos had been uploaded on several different dating websites by scammers to lure women (Rege, 2009). There were images of Frost on over 90 websites, and almost 80 different e-mail addresses and aliases were used (Rege, 2009). Eventually an internet security consultant was hired by Frost to understand the severity of his identity theft (Rege, 2009). At one point the consultant physically traveled to Nigeria and met with one of the “Robert Frosts” being used on the internet (Rege, 2009). When the consultant met with the man, he was a 24 year old whose true identity was George McCall (Rege, 2009). McCall claimed that he had not stolen the photo and used it 49 illegally because he had retrieved the photograph from the internet legally (Rege, 2009). Conclusively, the internet allows scammers to access all of the personal information needed to assume someone else’s identity (Allison et al., 2005). Scammers can access social networking websites and dating website profiles and sift through online identity databases to find suitable targets to victimize (Allison et al., 2005). The internet provides access to all of the sufficient information needed to victimize others (Allison et al., 2005). Summary To demonstrate the need for a review of interpersonal victimization on social networking websites, the current study broadly reviewed the issues of sexual harassment, stalking, sexual exploitation, and identity theft, and their transformation from traditional environments to the internet. Numerous studies have examined the specific characteristics and demographics of offenders as well as defined the risk-taking behaviors that many victims have exhibited. Currently there is a perception that there are dangers associated with the use of social networking websites (Perkel, 2008). Also, there is a copious amount of literature supporting that with increased use of social networking websites there is an increased risk for interpersonal victimization. Recognizing the need to focus on interpersonal victimization and the characteristics of risk-taking behaviors has provided more effective preventative strategies for users when encountering strangers on social networking websites. Studies have shown that sexual harassment is typically perpetrated by males against females, with higher rates of sexual harassment occurring when females engage in situations where there is a higher exposure to motivated offenders (DeCoster et al., 50 1999). Studies have also shown that sexual harassment may occur in many places and across various situations (Fisher et al., 2002). For example, the main form of sexual harassment that occurs online is posting personal information and sharing unwanted sexual photographs of others (Mitchell et al., 2005). One form of interpersonal victimization that is closely associated with sexual harassment due to the common traits that are exhibited between the two crimes is that of stalking. The issue of stalking was not a highly recognized problem until actress Rebecca Shaeffer was murdered in 1989 by a man who had been stalking her (McAnaney, Curliss, & Abeyta-Price, 1993). Studies have shown that women are the primary victims of stalking while men are typically the offenders (Mustaine & Tewksbury, 1999). Yet, despite the recent increase in the number of anti-stalking statutes, little is known about the extent of stalking due to a lack of research in the area. In addition to sexual harassment and stalking, another detrimental crime in society is that of sexual exploitation. Previously reviewed examples of sexual exploitation consisted of prostitution, sexual trafficking, and child pornography. Sexual exploitation is a form of interpersonal victimization driven by exploiters (Fontana-Rosa, 2001). Ultimately, sexual exploitation is driven by money (Blackburn, Taylor, & Davis, 2010). Over the past couple of decades, research shows a convergence of similar characteristics among those victimized by sexual exploitation (Kramer & Berg, 2003). Those who are most likely to share similar characteristics are from single-parent households, are isolated, have family problems, have low self-esteem, exhibit poor social skills, and are introverted (Kramer & 51 Berg, 2003). Ultimately, the negative and influential events that have occurred in these victim lives help understand how sexually exploitive predators operate. The motivated offenders seek suitable targets on the internet in an effort to sexually exploit them. Another form of interpersonal victimization that is similarly destructive like sexual exploitation is that of identity theft due to its common drive for money. Most literature describes identity theft as being driven by financial gain through fraudulently establishing credit, running up debt, or taking over someone else’s existing financial accounts (Allison et al., 2005). Identity theft has become a serious problem because it can take a long period of time before a victim is aware that a crime has taken place against them (Allison et al., 2005). The Federal Trade Commission estimates that 10 million people or 4.6 percent of the U.S. adult population will become victimized through identity theft within the year (Federal Trade Commission, 2000). This estimate projects possible losses exceeding $50 billion dollars (Federal Trade Commission, 2000). However, one of the most recent forms of fraud taking place on the internet is romance scams through dating service websites (Rege, 2009). The digital environment for internet daters allows users to remain anonymous, be instantaneous, alterable, and open to interpretation, making online dating attractive and stimulating (Rege, 2009). Romance fraud on the internet is a scam where victims believe that scammers have strong emotional feelings for them, and the romance component of the scam act, acts as bait to lure the victim. Once the scammer has lured the victim, the scammer then persists with identity theft or financial fraud. Conclusively, the internet allows scammers to access all of the personal information needed to assume someone else’s identity (Allison et al., 52 2005). Scammers can access social networking websites and dating website profiles and sift through online identity databases to find suitable targets to victimize (Allison et al., 2005). The internet provides easy access to all of the sufficient information needed to victimize others in numerous ways (Allison et al., 2005). The routine activities theory has been frequently applied to the issues of sexual harassment, stalking, sexual exploitation, and identity theft, and the majority of studies have found that the actions of victims have a significant impact on their risk of interpersonal victimization. The three variables that generally comprise the theory are the presence of motivated offenders, suitable targets, and the lack of guardianship over a person or thing. The concept of motivated offenders can be applied to social networking websites and can also be useful in explaining interpersonal victimization rates on the internet. According to researchers, it is likely that there will be individuals on social networking websites looking to commit criminal acts (Pierce, 2006). Additionally, the concept of a suitable target may be applied to the use of computers and the internet because there is easy access to victims. There are an abundant amount of users on the internet at one time and the offenders can relatively remain anonymous. Finally, the concept of guardianship is significant because users may perceive the internet as a safe place. For example, Pierce (2006) found that there was a correlation between trusting strangers on the internet and giving out personal information. During the past 20 years, the number of individuals using the internet has increased dramatically. For instance, individuals accessing social networking websites 53 are more likely to come into contact with potential motivated offenders. The rise in popularity of the internet has essentially changed their routine activities. Rather than using traditional forms of communicating in person, individuals now have the option of using the internet, and they are using it more often. This shift in the routine activities of these individuals will likely impact the types of crimes that are perpetrated against them. According to the routine activities theory crimes will likely increase when there is a convergence in time and space (cyber-space) of motivated offenders, suitable targets, and lack of guardianship. By understanding why individuals exhibit risk-taking behaviors and interact with strangers among social networking websites, preventative measures may be created to eliminate online interpersonal victimization. 54 Chapter 3 Methodology Traditionally, sources of data involving criminal events have been police department records. Unfortunately, police records only include reported events. With regard to victims, surveys attempt to provide reliable rates at which crime occurs and may also provide distinguishable characteristics of common victims. Over time, surveys have become one of the most popular ways of measuring people's concerns and fears about crime. There are numerous studies involving offline victimization and behaviors that lead to increased victimization; however, there are few studies that examine victimization occurring while individuals use the internet. Recently, moral panic has instilled fears about victimization as a result of using social networking websites. This study was designed to gauge interaction among strangers and the potential for victimization using social networking websites. This study intends to understand prevention, awareness, and theory involving the interaction of strangers among such websites. This chapter will discuss the methodology used by the researcher. The methodology will describe the process used to select the sample, the instrument used to collect the dataset, the variables used for the analysis, the coding of data, testable hypotheses, and the types of analyses to follow. Subjects It was estimated for the 2010-2011 academic year that were approximately 1,600 criminal justice major undergraduate students enrolled at California State University, Sacramento. Only the undergraduate students majoring in criminal justice were asked to 55 participate in a survey measuring personal computer and internet use. Moreover, by implementing a confidence interval of 5.0 percent and confidence level of 95.0 percent, a sample size of up to 310 subjects was necessary. In addition, according to the CSUS academic programs website (www.csus.edu/HHS/cj/History-of-the-Division.html), class sizes average fewer than 30 students; however, some criminal justice classes may now have up to 75 students. With the class average of 30 students in mind, it was estimated that 10 to 11 classes would be surveyed in an attempt to accommodate the approximate 310-subject sample size. Lastly, due to the possibility of instructors not accommodating access to their classes, simple random sampling generating classes with overlapping time schedules, and students being in multiple clusters, an estimated sample size of 310 subjects was only be used as an estimated target. A simple random sampling technique was used to select classes at CSUS of criminal justice major students enrolled in criminal justice undergraduate courses. First, undergraduate criminal justice courses were selected as individual clusters. The clusters were randomly selected with the use of a random sampling generator. The generator is designed for researchers and students to generate random numbers or assign participants to experimental conditions. The range of numbers were limited to the number of classes that were being offered for the semester (each course code was numbered in chronological order pertaining to its ascending number to eliminate any gaps that may be present in course codes). With the use of the generator, one set of 50 classes was generated. This process included grouping undergraduate students through criminal justice courses. Simple random sampling was applied to the population of the 56 undergraduate criminal justice courses to provide for a random sampling of undergraduate criminal justice courses. While only 10-11 classes were needed, 50 were selected randomly to fill the sample in case some instructors refused access to their classes. Student participation was completely voluntary and the students were free to end their participation at any time without prejudice. All surveys were anonymous. Instrument A questionnaire was developed and administered to collect information on why some students feel comfortable engaging with unknown persons through social networking websites (see appendix A). The questionnaire included 20 close-ended items and one open-ended comment prompt. These close-ended questions contained requests for the subjects to indicate the types of activities performed on the internet, the location of their computer use, how often the internet is used, whether or not there is presence of another person while using the computer, whether or not they are registered to social networking websites, information they may have posted on their personal social networking website, whether or not their personal social networking website is privatized, how often they have been requested or have "friended" an unknown person, whether or not they have conversed with the unknown person they have "friended," whether or not they have given personal information beyond what is accessible on their personal social networking website, whether or not they do any of the aforementioned activities with the use of a mobile device, whether or not they feel safe engaging with unknown persons among social networking websites, their gender, their age, and their marital status. After each question is a list of responses that the respondent is asked to 57 mark as their most fitting response. A full set of exhaustive and mutually exclusive responses are supplied. Other examples of questions simply ask the respondent to choose "yes" or "no”, fill in a blank space with a number, and/or circle a spot on a continuum. One open-ended question within the questionnaire allows respondents to offer comments. They are asked to fill in this space only if they have circled a spot on a continuum indicating whether or not they feel safe engaging with unknown persons among social networking websites. Data Collection California State University, Sacramento undergraduate students enrolled in criminal justice courses were asked to complete a questionnaire about their use of social networking websites and engagement with unknown persons. Current research reveals possible connections between social networking websites and increased likelihood of victimization. The questionnaire was designed to explain why some individuals may feel comfortable engaging with unknown persons through social networking websites. Instructors of the classes that had been selected from the use of the random number generator were e-mailed asking for permission to administer the survey indicated in Table 3.1. If permission was granted, the survey was arranged to be administered at the beginning of each scheduled class. Once the class began, the subjects were briefed from a script by the researcher (see appendix B), and a student volunteer from each of the scheduled class sessions was asked to pass out the self-administered survey to all of the students. During this time the researcher waited directly outside of the classroom while the volunteer distributed the questionnaires. This ensured anonymity. Once the 58 questionnaire was completed, the subject passed the survey to the front of the class where it was placed in a sealed envelope by the volunteer (the volunteer was also allowed to participate in the study). After all of the questionnaires had been collected, the volunteer then returned the sealed envelope to the researcher. The complete survey process averaged 14 minutes in length. Table 3.1:CSUS Criminal Justice Undergraduate Courses Selected Course # Course Description CRJ-2 CRJ-101 Law of Crimes Introduction to Criminal Justice Research Methods Crime and Punishment Sexual Offenses and Offenders The Structure and Function of American Courts Law of Arrest, Search, and Seizure Police Administration Contemporary Issues CRJ-102 CRJ-114 CRJ-121 CRJ-123 CRJ-142 CRJ-144 # of Students Enrolled 50 31 45 60 60 49 60 60 A total of 415 surveys were delivered to eight different selected courses as indicated in Table 3.1, but only a total of 288 completed surveys were returned. Additionally, demographic information for the sample is presented in Table 3.2. The current sample was 49.7 percent male, 48.3 percent female, and 2.1 percent (N=6) of the population declined to specify their gender. The average age of the participants was 25 and the median was 22 years of age. As indicated in Table 3.3, the majority of the participants were 21 years of age, making up 24.7 percent of the population. Only 3.5 percent (N=10) of the population declined to specify their age. Table 3.2 also shows that the subjects 59 were predominantly White (42.0 percent), while 19.1 percent of the population were Hispanic, 11.8 percent were Asian, 6.3 percent were Black, 2.8 percent were Pacific Islander, 0.3 percent were American Indian, 8.7 percent were multiracial, 4.2 percent identified themselves as being of other ethnicities, and 4.9 percent (N=14) of the population declined to specify their ethnicity. In addition, Table 3.2 shows that the subjects were predominantly single (85.1 percent), 6.3 percent were married, 4.2 percent were in a domestic partnership, 1.7 percent were separated, 0.3 percent were divorced, and 2.4 percent (N=7) of the population declined to specify their marital status. 60 Table 3.2:Demographics Variables Values Gender Age Ethnicity Marital Status Percentage Male Female Declined 15-25 26-35 36-45 46-55 Declined American Indian Asian Black Hispanic White Pacific Islander Multiracial Other Declined Married Divorced Separated Single Domestic Partner Declined 49.7% 48.3% 2.1% 81.3% 13.5% 1.4% 0.3% 3.5% 0.3% 11.8% 6.3% 19.1% 42.0% 2.8% 8.7% 4.2% 4.9% 6.3% 0.3% 1.7% 85.1% 4.2% 2.4% Table 3.3:Ages 15-25 by Age Variable Values Percentage Age 17 19 20 21 22 23 24 25 N 0.3% 2.8% 12.5% 24.7% 14.9% 11.5% 10.1% 4.5% 143 139 6 234 39 4 1 10 1 34 18 55 121 8 25 12 14 18 1 5 245 12 7 N 1 8 36 71 43 33 29 13 61 Testable Hypotheses This study tests three hypotheses: one hypothesis for each of the dimensions of the dependent variable; interpersonal victimization. Dimension one of the dependent variable: Motivated Offenders. H1A: Interpersonal victimization rates will increase when there is an increase in the number of motivated offenders encountered. Dimension two of the dependent variable: Suitable Target. H1B: Interpersonal victimization rates will increase when there is an increase in the number of suitable targets (subjects who provide personal information) that are easy to access by an offender. Dimension three of the dependent variable: Presence of Guardianship. H1C: Interpersonal victimization rates will increase when there is a lack of capable guardianship of persons or things present. Data Analysis Completed questionnaire responses were coded and then entered into SPSS for analysis. Analysis would examine if there were patterns concerning computer use, internet use, and encounters with unknown persons of those utilizing social networking websites. More specifically, this study sought to determine if there were specific predictors that may increase one’s likelihood to engage with unknown persons among social networking websites. The variables in this study were measured through a 21question survey on personal computer use, location of computer use, social networking 62 website use, types of personal information released, and experiences involving unknown persons on the internet. The dependent variable in this study was interpersonal victimization accessing the internet for California State University, Sacramento undergraduate students. The independent variables included activities performed on the computer, location of computer use, frequency of internet use, accessible personal information, and social networking website privatization. Furthermore, the dependent variable tests Cohen and Felson’s (1979) routine activities theory suggesting that when the independent variables are combined (suitable target, motivated offender, and lack of guardianship), they produce a heightened effect on the level of interpersonal victimization rates. It was hypothesized that one’s likelihood to engage with strangers among social networking websites would have an effect on interpersonal victimization rates. As outlined in the literature review, these interpersonal victimization rates include sexual harassment, stalking, sexual exploitation, and identity theft. The testable hypotheses for this study suggest that there will be variance in the interpersonal victimization rates with each addition of the dependent variables (motivated offenders, suitable targets, and lack of guardianship). To test these hypotheses, the data reflecting the dependent variable was analyzed for incidence rates. The questionnaire (see appendix A) can be broken down into three sections outlining Cohen and Felson’s (1979) variables concerning a suitable target, motivated offender, and a lack of guardianship. For instance, personal computer use, which includes using social networking websites and the estimated amount of time using the internet, were analyzed to determine the incidence 63 rate of a suitable target. The types of personal information released and the experiences involving unknown persons were analyzed to determine the incidence rate of a motivated offender. Lastly, the location of computer use, restrictions of use, and the presence of monitoring one’s use of a computer were analyzed to determine the incidence rate for a lack of guardianship. SPSS produced the rates and percentages to determine the presence of the aforementioned. To further define these terms, the incidence rates are the percentage of those who indicated computer and internet use, indicated the release of personal information and encounters with unknown persons, and indicated a lack of guardianship. The incidence rates express the number of experiences for each of the independent and dependent variables expressed by each of the subjects from the 288-sample population. Once the rates for the selected responses from the questionnaires were generated for each subject, various tables were compiled to express the incidence rates of each question on the survey. One table was compiled expressing personal information released and further access to personal information by an unknown person to compare these rates with each subject’s perception of safety. Another table was compiled expressing rates of page privatization, rates of contact by unknown persons, rates asking to view a private page, rates giving permission to view their pages, and rates of interaction with an unknown person and then comparing these rates with each subject’s perception of safety. An additional table expressing the percentages for the combined indicators of a suitable target, motivated offender, and lack of guardianship was compiled; and finally, the rates of a suitable target, motivated offender, and lack of guardianship were generated and a 64 table was compiled comparing the incidence rates with each demographic variable (gender, age, ethnicity, and marital status) as a means to produce possible predictors of interpersonal victimization. After all of the incidence rates and tables were compiled, a few responses from the open-ended question were analyzed and reported. Only select responses were reported illustrating perceptions of safety or unsafe experiences while accessing the internet. Limitations of Research Design One of the most significant limitations to the research design is the small sample size. There were approximately 1,600 criminal justice major undergraduate students enrolled at California State University, Sacramento, and only these criminal justice major undergraduate students were asked to participate in a survey. By implementing a confidence interval of 5.0 percent and confidence level of 95.0 percent, this projected an approximate sample size of up to 310 subjects; however, only 288 responses were retrieved. A sample size of only 288 students could largely affect the findings of this study by increasing the margin of error. Another limitation is the truthfulness and accuracy of responses supplied by the respondents. The dishonesty or inaccurate responses could significantly alter the findings of this research. As discussed in chapter one, a limitation to this study is the omission of data from each reporting subject. With an interviewer not being present, it is problematic because it will be difficult to clarify incomplete answers. This could potentially affect the findings of this research. Another limitation to this study is that the findings of this research may not be generalized to all academic majors, as well as other college campuses and college- 65 aged youth in general. Applying specific rates of interpersonal victimizations found in this research to other locations may not be possible or accurate. Lastly, criminal justice majors may also be more aware of becoming potential victims. This may skew the results in comparison to other academic majors that are not as aware. Further research examining interpersonal victimization on social networking websites throughout the nation could prove otherwise. 66 Chapter 4 Findings This study examines the interactions between unknown persons and the potential for interpersonal victimization while accessing the internet. Tables and figures in this chapter indicate the rates of interpersonal victimization for 288 criminal justice major undergraduate students from California State University, Sacramento. Various methods of examination including descriptive and bivariate analyses were conducted to test the hypotheses outlined in chapter three. Suitable Target Table 4.1 shows the breakdown of internet use for the students. An overwhelming majority (95.5 percent) of participants reported using the internet for e-mail, 95.1 percent used it for research, 83.0 percent accessed the web for shopping and social networking websites, 62.2 percent planned travel, 43.8 percent played games, and 40.6 percent communicated through an instant messenger. Despite the high levels of use, only 18.1 percent of the students accessed the internet for other purposes. Very few responded using the internet for chat-room use (9.0 percent) and website design (5.6 percent). 67 Table 4.1:Use of Internet Variables E-mail Research Social Networking Websites Shopping Planning Travel Gaming Instant Message Other Chat-rooms Website Design Percentage 95.5% 95.1% 83.0% 83.0% 62.2% 43.8% 40.6% 18.1% 9.0% 5.6% N 275 274 239 239 179 126 117 52 26 16 Personal computer use was compiled to understand the amount of time students use the internet throughout a day. Appendices C through F show the time spent on the internet over a 24-hour time period accessing e-mail, instant messenger services, chatrooms, and social networking websites. Numerous locations in the table are empty because these times were not selected. Appendix C depicts the use of e-mail services. The most common frequency of e-mail use was 1 hour (28.8 percent) and 2 hours (19.1 percent). Appendix D shows the use of instant messenger services, and an overwhelming amount of the students (70.1 percent) suggested that they do not use instant messenger services. Only 16.3 percent of the subjects indicated using an instant messenger leaving 12.2 percent of students utilizing instant messenger services over 2-6, 8, 10, and 24-hour time periods. In Appendix E, 94.0 percent of the students indicated they do not use the internet for chat-room purposes. Appendix F suggests a wide spectrum of social networking website use. One of the highest single percentages (16.7 percent) of subjects reported not using a social networking website page, although this does not mean that the majority of the population does not access one. For instance, 24.0 percent access their 68 social networking website pages for at least 1 hour, 15.6 percent for 2 hours, 11.8 percent for 3 hours, 4.2 percent for 4 hours, 9.4 percent for 5 hours, 3.5 percent for 6 hours, 1.0 percent for 8 hours, 5.2 percent for 10 hours, 0.3 percent for 12 hours, and 6.6 percent of the students access their pages 24 hours a day. Social networking websites are widely used by criminal justice major undergraduate students at California State University, Sacramento. Table 4.2 shows that a majority of the students (83.0 percent) access Facebook, 34.7 percent have a MySpace account, 13.5 percent use Twitter, 7.3 percent of the students use another unnamed version of a social networking website, and 3.5 percent of the students have a Friendster or Xanga account. Table 4.2:Social Networking Website Use Variables Percentage N Facebook MySpace Friendster Twitter Xanga Other 239 100 10 39 10 21 83.0% 34.7% 3.5% 13.5% 3.5% 7.3% Since the introduction of mobile phones, there has been a vast increase in the use of internet and its offerings of e-mail, instant messenger services, chat-rooms, and social networking websites. The subjects indicated whether or not they engaged in any of the aforementioned activities using a mobile device such as a smart phone. Table 4.3 indicates that 60.1 percent of the subjects use a mobile device to access the internet and other services. 69 Table 4.3:Frequency of Mobile Device Use Value Yes No Declined Percentage N 37.5% 60.1% 108 173 2.4% 7 Lack of Guardianship Table 4.4 illustrates the level of guardianship while using a computer. For example, the location of computer use represents guardianship. The computer was most often used (97.9 percent) within the subject’s home, 78.5 percent of the subjects reported using the computer at school, 31.6 percent use a computer at a friend’s, 19.1 percent at another location, and 16.7 percent at a coffee shop. Additionally, students were asked to indicate their primary location of computer use. Tables 4.4 indicates that the majority of the students (87.5 percent) used a computer at their home, and the remaining students accessed a computer at school (7.6 percent), at a different location (3.1 percent), at a friend’s (1.0 percent), or at a coffee shop (0.7 percent). Another component representing more guardianship is the presence of another person in the same room while using a computer. Table 4.4 points out that 37.5 percent of the subjects use a computer while someone else is present in the room. Only one subject declined to answer this question. Restrictions of computer use are the last component in Table 4.4 representing a lack of guardianship. Table 4.4 implies that 3.8 percent of the students are not restricted from specific content or the amount of time spent on a computer while using it. Only three subjects declined to answer to their restrictions while accessing a computer suggesting that a majority of the students (95.1 percent) are not restricted while using a computer. 70 Table 4.4:Guardianship of Computer Use Variables Values Location of Computer Use Primary Computer Location Presence of Other Restrictions Home School Friend's Other Coffee Shop Home School Friend's Coffee Shop Other Presence Declined Presence Declined N 282 226 91 55 48 252 22 3 2 9 108 1 11 3 Percentage 97.9% 78.5% 31.6% 19.1% 16.7% 87.5% 7.6% 1.0% 0.7% 3.1% 37.5% 0.3% 3.8% 1.0% Motivated Offender Individuals post various kinds of personal information on social networking websites. Figure 1 indicates the distribution of information posted on each subject’s social networking website. Five specific characteristics were posted most often, pictures (81.3 percent), gender (80.2 percent), age (66.7 percent), relationship status (65.4 percent), and hobbies (50.3 percent). The remaining characteristics were not as prevalent, for instance, extracurricular activities were posted by 32.0 percent, goals by 21.5 percent, a telephone number by 8.7 percent, descriptive characteristics such as eye color were posted by 8.3 percent, other characteristics by 8.0 percent, distress problems by 6.6 percent, and a home address was posted by 5.2 percent. 71 Number of Participants Figure 1: Type of Personal Information Posted on Social Networking Website 300 250 200 150 100 50 0 Yes No Personal Information Posted on Website Figure 2 indicates that subjects who provide unknown persons with descriptive information further than what is accessible on their website. Comparing Figure 2 with Figure 1, it is apparent that the level of information released from a private social networking page to an unknown person is very small. Figure 2 shows that personal information given to an unknown person beyond what is accessible on their website decreased significantly when compared to Figure 1. A subject’s age was the most common characteristic given to a stranger (10.8 percent), and the least common was the other category by only 1.4 percent. 72 Number of Participants Figure 2: Access of Personal Information Provided to an Unknown Person on Social Networking Websites 300 250 200 150 100 50 0 Yes No Personal Information Released to an Unknown Person Crosstabulation tables were compiled in order to analyze the perception of safety expressed by each subject (see Appendices G through K). The analysis indicated various levels of safety that the student’s experience while accessing social networking websites. Furthermore, the analysis compared the rates of each characteristic posted by subjects on their social networking website with their perception of safety. These analyses also compare the rates of each characteristic that was granted further access to unknown persons by subjects on their social networking website with their perception of safety. One of the most common characteristics (age) posted on a social networking website was also one of the most feared characteristics to be accessible to strangers. In spite of the fear, 43 subjects posted their age while 21 subjects who indicated feeling unsafe did not post their age. In contrast, eight subjects felt safe posting their age while only one subject who did not post their age felt safe. Six subjects who reported feeling 73 unsafe did permit further access to the characteristic of age to an unknown person while 60 of the subjects who reported feeling unsafe did not permit further access. In contrast, two people felt safe permitting further access to age by an unknown person while seven subjects who did not permit further access to age indicated feeling safe. Collectively, the majority of the students indicated they did not feel safe whether they did or did not post their age or allow further access to the characteristic of age. Gender was another one of the most common characteristics feared to be accessible on a social networking website, and despite feeling unsafe, 52 subjects posted their gender, and 12 subjects who indicated feeling unsafe did not post their gender. Only eight subjects felt safe posting their gender while one subject who did not post their gender felt safe. Six subjects who reported feeling unsafe did permit further access to the description of gender to an unknown person while 60 of the subjects who reported feeling unsafe did not permit further access. Meanwhile, two people felt safe permitting further access to gender by an unknown person while seven subjects who did not permit further access to gender indicated feeling safe. Overall, the majority of the students felt unsafe whether they did or did not post their gender or allow further access to the characteristic. While they reported feeling unsafe, two subjects posted descriptive characteristics on a social networking website and 62 subjects who indicated feeling unsafe did not post descriptive characteristics. It was also found that four subjects felt safe posting their descriptive characteristics while only five subjects who did not post descriptive characteristics felt safe. Three subjects who reported feeling unsafe did permit further access to descriptive characteristics to an unknown person while 63 of the subjects who 74 reported feeling unsafe did not permit further access. Only one person felt safe permitting further access to descriptive characteristics by an unknown person while eight subjects who did not permit further access to descriptive characteristics indicated feeling safe. The subjects expressed a lack of safety even if they did or did not post their descriptive characteristics or allow further access to the characteristic. Hobbies were found to be one of the most common characteristics posted on a social networking website, and it was found to be one of the most common descriptive characteristics that made subjects feel unsafe for others to possess. Twenty-nine of the students that felt unsafe posted their hobbies on a social networking website while 35 subjects who indicated feeling unsafe did not post their hobbies. In contrast, five subjects felt safe posting their hobbies while only four subjects who did not post their hobbies felt safe. It was indicated that three subjects who reported feeling unsafe did permit further access to the characteristic of hobbies to an unknown person while a majority of the subjects who reported feeling unsafe did not permit further access. In addition, two people felt safe permitting further access to hobbies to an unknown person while seven subjects who did not permit further access to hobbies indicated feeling safe. In short, most students indicated feeling unsafe posting or not posting their hobbies, or providing further access to strangers about their hobbies. Pictures were found to be one of the most common personal identifiers posted by students on their social networking website as well as one of the most feared characteristics to be accessible to strangers. Fifty-four subjects felt unsafe posting their pictures on a social networking website and ten subjects who did not post their pictures 75 also felt unsafe. Nine subjects felt safe posting their pictures while zero subjects did not post their pictures in order to feel safe. Five subjects who reported feeling unsafe did permit further access to their pictures by an unknown person while 61 of the subjects who reported feeling unsafe did not permit further access. In contrast, two people felt safe permitting further access to pictures by an unknown person while seven subjects who did not permit further access to pictures indicated feeling safe. Students felt unsafe on the internet if they did or did not post personal pictures or give them out to unknown persons. In spite of feeling unsafe, six subjects posted their telephone number on a social networking website while 20 percent indicated feeling unsafe did not post telephone number. Very few subjects (2) felt safe posting their telephone number while seven subjects who did not post their telephone number felt safe. Four subjects who reported feeling unsafe did permit further access to their telephone number by an unknown person while most (62) of the subjects who reported feeling unsafe did not permit further access. Only one person felt safe permitting further access to their telephone number by an unknown person while eight subjects who did not permit further access to their telephone number indicated feeling safe. Nearly all of the subjects report feeling unsafe by either posting or not posting their telephone number or by providing their telephone number to an unknown person. Only five subjects posted their home location on a social networking website even though they felt unsafe, and a majority of the subjects (59) did not post their home location also feeling unsafe. Two subjects felt safe posting their home location while seven subjects who did not post their home location felt safe. Almost none of the subjects 76 (one) reported feeling unsafe, but did permit further access to their home location by an unknown person; however, 65 of the subjects who reported feeling unsafe did not permit further access. It was indicated that one person felt safe permitting further access to their home location by an unknown person while eight subjects who did not permit further access to their home location indicated feeling safe. Almost all of the subjects feel unsafe posting or not posting their home address on a social networking website or permitting further access to the characteristic. Even though they felt unsafe doing so, twelve subjects posted their extracurricular activities on a social networking website while 52 subjects who indicated feeling unsafe did not post their extracurricular activities. In contrast, seven subjects felt safe posting their extracurricular activities while two subjects who did not post their extracurricular activities felt safe. Only one subject who reported feeling unsafe did permit further access to their extracurricular activities by an unknown person while 65 of the subjects who reported feeling unsafe did not permit further access. One person felt safe permitting further access to extracurricular activities by an unknown person while eight subjects who did not permit further access to their extracurricular activities indicated feeling safe. Most subjects feel threatened for their safety if they did or did not post their extracurricular activities or allow further access to the activities. In spite of feeling unsafe, nine subjects posted their goals on a social networking website while 55 subjects who indicated feeling unsafe did not post their goals. In contrast, four subjects felt safe posting their goals while five subjects who did not post their goals felt safe. Only one subject who reported feeling unsafe did permit further 77 access to their goals by an unknown person while a large portion (65) of the subjects who reported feeling unsafe did not permit further access. Two people indicated feeling safe and permitted further access to their goals by an unknown person while seven subjects who did not permit further access to their goals indicated feeling safe. Subjects that did or did not post their goals or allow further access to the characteristic of goals expressed feeling unsafe. While they reported feeling unsafe, four subjects posted their distress problems on a social networking website while 60 subjects who indicated feeling unsafe did not post their distress problems. One subject felt safe posting their distress problems while eight subjects who did not post their distress problems felt safe. None of the subjects permitted further access about their distress problems to an unknown person because they felt unsafe while 64 of the subjects who reported feeling unsafe did not permit further access. In addition, none of the subjects felt safe permitting further access to their distress problems by an unknown person while nine subjects who did not permit further access to their distress problems indicated feeling safe. Collectively, a pattern of feeling unsafe was indicated by the subjects whether they did or did not post their distress problems or allow further access to the characteristic. A subject’s relationship status was found to be one of the most common descriptive characteristics posted on a social networking website. Despite feeling fearful, 38 subjects posted their relationship status on a social networking website while 26 subjects who indicated feeling unsafe did not post their relationship status. In contrast, eight subjects felt safe posting their relationship status while one subject who did not post 78 their relationship status felt safe. Few subjects (3) who reported feeling unsafe did permit further access to their relationship status by an unknown person while most (63) of the subjects who reported feeling unsafe did not permit further access. Only two people felt safe permitting further access to their relationship status by an unknown person while seven subjects who did not permit further access to their relationship status indicated feeling safe. A majority of the subjects feel unsafe whether they did or did not post their relationship status or allow further access to their status. Despite feeling unsafe, six subjects posted other information on a social networking website while 58 subjects who indicated feeling unsafe did not post other information. Two subjects felt safe posting other information while seven subjects who did not post other information felt safe. None of the subjects permitted further access to other information by an unknown person because they felt unsafe while a large portion (66) of the subjects who reported feeling unsafe did not permit further access. In contrast, none of the students felt safe permitting further access to other information by an unknown person while nine subjects who did not permit further access to other information indicated feeling safe. The subjects expressed a lack of safety even if they did or did not post other information or allow further access to other descriptive characteristics. Comparing the tables of descriptive information posted willingly by subjects with the tables representing the data when students permit further access to descriptive information by unknown persons demonstrates a trend of feeling unsafe. Several descriptive categories reveal a large number of subjects that post information willingly on 79 their social networking website. A shocking discovery is that they do so while feeling unsafe. In addition, several descriptive categories reveal an extremely small number of subjects who permit further access to personal information by an unknown person because they do not feel safe doing so. The few who permit further access to strangers are trusting of unknown persons and exhibit risk-taking behaviors. Similar to the previous analyses illustrating each subject’s perception of safety are Appendices G to K. Appendices G through K were compiled to illustrate the level of safety subjects perceive while having their social networking website private, being requested by unknown persons to view their privatized website, allowing strangers permission to view their privatized page, and conversing with unknown persons through the introduction of a social networking website. Appendix G shows that 54 subjects felt unsafe even though their website was privatized whereas seven subjects felt unsafe not having their social networking website privatized. Unfortunately, it is not known why these subjects had an unsecured page while they felt unsafe. Additionally, Appendix G shows that only six subjects felt safe having their website privatized whereas three subjects felt safe not having their page privatized. Collectively, a majority of the students felt unsafe even if their page was or was not privatized. Appendix H indicates how many strangers contacted a subject through their social networking website and whether or not the student felt safe during these contacts. Appendix H shows that 66 students were contacted up to 100 times and that they felt unsafe during these contacts. In contrast, Appendix H also points out that only eight 80 students were contacted up to 100 times by a stranger but they felt safe, and only one student felt safe being contacted by a stranger within 901 and 1000 times. A majority of the students demonstrated feeling unsafe when being contacted by a stranger. Appendix I approximates how many times a person unknown to the subject requested permission to view his or her profile and if the subject felt safe or unsafe during these requests. As indicated in Appendix I, 66 subjects indicated being requested up to 100 times by a stranger and feeling unsafe. In contrast, Appendix I also points out that seven subjects were requested by a stranger up to 100 times, one subject requested by a stranger 201-300 times, and one subjects requested by a stranger 901-1000 times. Most students indicated feeling unsafe when being requested permission by a stranger to access their personal social networking website. Appendix J indicates how many times a stranger was granted permission to view his or her website and whether or not the subject felt safe or unsafe doing so. Of the times when someone unknown to the student requested their permission, the student indicated whether none, a few, some, most, or all were granted access. As indicated in Appendix J, approximately 56 students felt unsafe being requested permission and therefore did not allow the stranger access to their page. Appendix J also shows that only three students felt unsafe while permitting a few strangers to view their profile. It is unknown why these three students provided the strangers access to their privatized page even though they felt unsafe. In contrast, Appendix J illustrates that only seven students for each of the categories in all felt safe denying permission or granting permission to the requesting 81 stranger. It is evident that the majority of the students felt unsafe being requested permission by a stranger to view their personal website. Appendix K provides the perception of safety experienced by a subject while deciding to converse with an unknown person at a social networking website. This appendix indicates that a majority of the students experienced feeling unsafe and therefore did not converse with a stranger through the website. For instance, 58 students felt unsafe and did not converse with the unknown person whereas five students did even though they felt unsafe. It is not known why the five subjects decided to converse with the unknown person while feeling unsafe. In addition, Appendix K also shows that four subjects would feel safe conversing with a stranger at a social networking website but never have, and only five subjects have conversed with strangers while experiencing a level of safety. It is evident in the data depicted in Appendices G to K that a majority of the students do not feel safe engaging with unknown persons at a social networking website. Students are commonly approached by strangers to view their privatized website or to converse, but the students expressed not feeling comfortable granting permission or making further contact. Only a few students indicated feeling safe when contacted, giving permission, or conversing with an unknown person. These select individuals who interact with strangers are trusting of unknown persons and exhibit risk-taking behaviors. 82 Predictors of Interpersonal Victimization: Combination of Suitable Target, Motivated Offender, and Lack of Guardianship A figure was generated to show how often a subject uses e-mail services, instant messenger services, chat-rooms, and social networking websites. As shown in Figure 3, uses of internet were combined with the use of a social networking account to indicate the likelihood of becoming a suitable target. Figure 3 illustrates that 88.2 percent of the students possess a social networking account and use e-mail services at least once a day, 82.0 percent of the students have a social networking account and use it regularly, and 38.2 percent have a social networking website and use an instant messenger commonly. In contrast, chat-room services were rarely used for those who have a social networking account (84.0 percent). Number of Participants Figure 3: Indication of a Suitable Target: Social Networking Website and Internet Use 300 250 200 150 100 SNW Account No 50 SNW Account Yes 0 No Yes No Yes No Yes No Yes E-mail Instant Message Chatroom SNW Use of Internet By comparing further access to personal information and the number of times a subject conversed with an unknown person through a social networking website, will 83 indicate how likely a subject is to place themselves within proximity of a motivated offender. Figure 4 illustrates the presence of a motivated offender by combining the subjects who permitted further access to personal information and the subjects who conversed with a stranger at a social networking website. It was hypothesized that interpersonal victimization rates will increase when there is an increase in the combination of dependent variables. Presence of a motivated offender is indicated in Figure 4 illustrating the level of risk that subjects place themselves to experience interpersonal victimization. Figure 4 shows that 21.5 percent of the subjects released personal information and conversed with an unknown person while only 8.3 percent of the students conversed with an unknown person but did not give out personal information about themselves. In contrast, Figure 4 also suggests that the majority of the students did not converse with an unknown person or give out personal information. Number of Participants Figure 4: Contribution of Personal Information and Experiences with Unknown Persons on Social Networking Websites 120 100 80 Provided Further Access to Personal Information No 60 Provided Further Access to Personal Information Yes 40 20 0 No Yes Conversed with Unknown Person 84 A lack of restrictions and guardianship along with the location of computer use describes the level of guardianship over each of the subjects. An overwhelming majority of the students did not have restrictions or another person present in the same room while using a computer in their home. Figure 5 shows that 84.0 percent of the students do not have restrictions while using their computer in their home, and 54.5 percent of the students do not have a person monitoring their computer use in the home. Figure 5: Location of Computer Use and Guardianship Number of Participants 250 200 Computer Location Home 150 Computer Location School 100 Computer Location Coffee Shop 50 Computer Location Other 0 No Yes Guardian No Yes Restrictions Presence of Guardianship The percentages for the combined indicators of a suitable target, motivated offender, and lack of guardianship are shown in Table 4.5. This table also compares those rates with the incidence rates with each demographic variable (gender, age, ethnicity, and marital status) to produce possible predictors of interpersonal victimization. Even though percentages were used to simplify the presence of a predictor for interpersonal victimization, high percentages for the combination of all three independent variables 85 (suitable target, motivated offender, lack of guardianship, were not present. Despite this finding, the data strongly suggest that students are indeed suitable targets, experience motivated offenders at various rates, and lack a great amount of guardianship placing them at a high level of risk for interpersonal victimization. Table 4.5: Amount of Students Reporting Online Behaviors by Suitable Target, Motivated Offender, Lack of Guardianship, and by Demographics Suitable Motivated Target Offender Lack of Guardianship Gender Male Female 48.9% 49.6% 52.4% 46.6% 46.7% 52.0% 15-25 26-35 36-45 46-55 82.4% 13.3% 1.2% 0.4% 85.4% 12.1% 1.5% 0.3% 86.3% 10.1% 0.8% 0.4% 0.4% 11.7% 5.6% 18.4% 43.2% 3.0% 9.0% 4.5% 0.6% 10.7% 8.6% 16.6% 42.4% 2.6% 11.2% 5.5% 0.1% 13.0% 10.9% 21.6% 33.1% 1.1% 11.0% 3.0% 6.0% 0.4% 1.9% 86.5% 3.0% 4.6% 0.3% 1.2% 90.3% 3.5% 5.4% 0.4% 1.3% 84.2% 7.3% Age Ethnicity/Race American Indian Asian Black Hispanic White Pacific Islander Multiracial Other Marital Status Married Divorced Separated Widowed Single Domestic Partner 86 Subject Response After evaluating the encounters with unknown persons and the rates of perceived safety while accessing the internet for California State University, Sacramento undergraduate students, it has become clear that a majority of the students feel unsafe. In addition, the preceding tables and figures showed that a majority of the students possess a social networking account, use it often, and access them with the use of a mobile device. Even though a majority of the subjects are placing themselves at risk with heightened levels of being a suitable target, allowing further access to personal information by an unknown person was estimated to be significantly low. However, an overwhelming majority of the students expressed a lack of guardianship. The computer was often used at home without the presence of another or having restrictions limit computer function. Conclusively, there were subjects who placed themselves at risk by exhibiting risky behaviors and combining the variables of a suitable target, motivated offender, and a lack of guardianship, but the number of subjects who collectively placed themselves at risk was extremely low. To demonstrate why these subjects feel safe placing themselves at risk, a few of the open-ended questions will be reviewed. The following will analyze responses to the open-ended question asking to explain why the subject may feel safe or unsafe engaging with unknown persons over the internet. The first section will review those who expressed feeling safe. Five responses were selected due to their unique remarks of safety. It was found that many respondents felt safe using the internet to search for relationships. For example, a respondent chose a seven on the safety continuum and expressed, “I only talk to girls my age that I find 87 attractive, so I feel safe in the fact that I am just trying to get to know them for potential dating purposes.” Another respondent selected an eight on the safety continuum and expressed, “I usually keep it simple. I only talk to them because we both game or have the same interest I keep it to that.” Oddly, one respondent chose a nine on the continuum even though he expressed “the way technology is used today and what can be traced and found scares me.” The most notable respondent circled the highest level of safety on the continuum (10), and stated, “Because if anyone has cause for concern it would be them not me.” This response is alarming as a potential victim that there is no consequence for them, they don’t need to be careful. In contrast to the previous responses, the following will review those who expressed feeling unsafe engaging with unknown persons over the internet. Six responses were selected due to their unique remarks. After selecting a four on the safety continuum, one respondent stated, “I feel unsafe for the reason I don’t know who they are. They might have fake pictures? I don’t engage with nobody that I don’t know.” Another respondent circled a three on the safety continuum and remarked, “I did an essay in an English class regarding a young girl Judy Cajuste who was murdered, believed by a man on MySpace.” Next, a subject marked a three on the safety continuum and expressed, “Once, one guy told me, he knew where I lived. So I’m scared that some of them know more about me than I want them to know. So I feel unsafe with most of them especially guys.” Another subject only selected a three on the safety continuum even though he had previously “been a past victim of identity fraud.” Additionally, many responses indicated that males often contact females over social networking websites. For example, a 88 respondent felt unsafe and indicated so by selecting a three on the safety continuum, she stated that, “Usually the unknown people contacting me are males. They usually contact me because they think I am attractive. Many females are hurt from communicating with males they don’t know.” The last response selected indicated the highest level of feeling unsafe (1) on the safety continuum. This respondent stated, “I had some guy that wouldn’t leave me alone and it’s scary.” Summary Incidence rates of interpersonal victimization were analyzed to address the phenomenon of moral panic discussed in previous research about social networking websites. The testable hypotheses stating interpersonal victimization rates will increase when there is an increase in the number of motivated offenders (H1A), suitable target (H1B), and presence of guardianship (H1C) were not supported by the data. The majority of the subjects indicated a high level of personal computer use, which includes using social networking websites and an estimated amount of time using the internet suggesting an increased likelihood of becoming a suitable target. Only a few subjects (N=62) indicated releasing personal information and conversing with unknown persons while using social networking websites which increases their likelihood of being placed with proximity of a motivated offender. Most of the subjects indicated computer use within the home, minimal restrictions of use, and a limited presence of monitoring one’s use of a computer while using social networking websites suggesting an overall lack of guardianship. Cohen and Felson’s (1979) routine activities theory suggesting that when the variables are combined (suitable target, motivated offender, and lack of 89 guardianship), they produce a heightened effect on the level of interpersonal victimization rates; however, it was not clear whether all three variables were present in combination and interpersonal victimization rates were not accounted for. It was not feasible to construct a questionnaire asking subjects to recall incidents of victimization because of the level of risk involved. Furthermore, the goal of the current study was to determine why subjects engage with unknown persons among social networking websites, so the frequencies of interpersonal victimizations were not surveyed. However, the questionnaire was created with an open-ended question in hope that subjects would disclose incidents of interpersonal victimization. Only a few respondents included experiences of victimization as outlined in the subject’s response section. 90 Chapter 5 Summary and Conclusions Reports from media have raised fears about internet use and a person’s general safety. Moral panic initiated research focusing on the safety of uses of the internet such as interacting with strangers, posting personal information, and accessing social networking websites. Researchers suggest that the internet may facilitate victimization by making suitable targets more accessible to motivated offenders and creating opportunities for predators to be alone with victims. It is possible that motivated offenders can find suitable targets more easily online than through conventional social networks. The efficiency of email services, instant messenger services, chat-room services, and social networking websites allow for fast and private exchanges of personal information, which motivated offenders can use to develop relationships and seduce victims. The routine activities theory is applicable to the current study because of the presence of three variables, suitable target, motivated offender, and lack of guardianship. This theory states that changes in crime are due to the opportunities of offenders, and is based on the presumption that individuals performing daily routines may encounter an incident of victimization. This study suggests that a person’s lifestyle increases their risk of being exposed to motivated offenders and interpersonal victimization. In this study, the students were viewed as a suitable target for offenders because there was an ease of access to individuals through social networking websites. A motivated offender has the advantage of grooming numerous individuals at one time, so the types of personal information released and the experiences involving unknown persons were analyzed to 91 determine the incidence rate of a motivated offender. Lack of guardianship occurs when individuals do not use social networking websites with caution due to the belief that conversing with a stranger over the internet is not a potential threat; therefore, the location of computer use, restrictions of use, and the presence of monitoring one’s use of a computer were analyzed to determine the incidence rate for a lack of guardianship. The computer was most often used (97.9 percent) within the subject’s home, a majority of the students (95.1 percent) are not restricted while using a computer, and 37.5 percent of the subjects use a computer while someone else is present in the room. The current study has shown that there is a high rate of California State University, Sacramento criminal justice major students who use social networking websites. Facebook is the most commonly used social networking website accessed by 83.0 percent of the subjects. It is possible the remaining 17.0 percent may not use social networking websites as a result of protecting oneself from unwanted individuals viewing personal information. Surprisingly, only 13.9 percent of the subjects with an account displayed their personal information publicly, while 77.4 percent had private pages. When analyses were conducted to see if online exposure affected the incidence rates for solicitation, it was expected that there would be a relationship with those having the lowest levels of privacy being contacted the most, and those with private profiles would be contacted the least. The current research found that many individual internet behaviors are not associated with higher rates of unsafe solicitations by unknown persons, but there is increased risk associated with engaging in online risk-taking. The following behaviors indicate a risky pattern of internet use. Over 91.0 percent of the 92 subjects posted personal information online and only 6.3 percent did not. Furthermore, of those who posted personal information, 60.1 percent gave further access to personal information to strangers, and only 34.4 percent did not permit further access to personal information. It was found that of the 60.1 percent that granted access to personal information, only small amounts were distributed through various descriptive categories. Further access to age was distributed by 10.8 percent of the subjects, gender by 10.4 percent, descriptive characteristics by 5.6 percent, hobbies by 8.7 percent, pictures by 8.0 percent, telephone number by 7.3 percent, home location by 2.1 percent, extracurricular activities by 4.5 percent, goals by 4.9 percent, distress problems by 2.4 percent, relationship status by 9.0 percent, and other information by 1.4 percent. Permission to view a subject’s privatized social networking website by an unknown person were analyzed. None of the strangers were granted permission by 66.3 percent of the subjects, a few were granted permission by 17.4 percent, some were granted permission by 3.8 percent, most were granted permission by 1.7 percent, and all were granted permission by 1.0 percent. Subjects indicated conversing with these unknown persons 30.6 percent of the time. Students who create profiles or posted pictures of themselves online are more likely to be contacted online by strangers, but researchers believe that these individuals aren’t at risk. The largest percentage of those contacted (18.1) indicated that they had been contacted on average by 10 separate unknown persons. It is interactive behaviors, such as conversing online with unknown people that place them more at risk of interpersonal victimization. Over 65 percent of the subjects indicated that they were 93 requested permission by a stranger to view their private social networking website, but only 24.7 percent of the subjects granted permission to these individuals. Additionally, 30.6 percent of the subjects conversed with the unknown people that requested permission to view their site. The most notable findings in the research indicate that an overwhelming majority of the students do not feel safe engaging with unknown persons on a social networking website. Students are commonly approached by strangers to view their privatized website or to converse, but the students expressed not feeling comfortable granting permission or making further contact. Only a few students indicated feeling safe when contacted, giving permission, or conversing with an unknown person. These select individuals who interact with strangers are trusting of unknown persons and exhibit risktaking behaviors. To further assess interpersonal victimization among social networking websites, the data were analyzed to see if any trends were present. Trends for the combination of a suitable target, motivated offender, and lack of guardianship would indicate predictors of interpersonal victimization. Indication of a suitable target was implied by analyzing those who had a social networking website account and used various internet communication services. Email services were used throughout a 24 hour period by 88.2 percent of the subjects, social networking websites by 82.0 percent, instant messenger services by 38.2 percent, and chat-rooms by 8.4 percent. Indication of a motivated offender was implied by analyzing those who permitted further access to personal information and conversed with unknown persons at a social networking website. Only 21.5 percent of students released information and conversed with an unknown person while 8.3 percent conversed 94 with an unknown person but did not give out personal information. Surprisingly, students did not converse with an unknown person or give out personal information (24.7 percent). Indication for a significant level of guardianship was implied by analyzing the student’s restrictions, guardianship, and location of computer use. A large portion of students (84.0 percent) did not have restrctions or the presence of a guardian while using a computer in their home. Ultimately, the combination of all three independent variables were not present at high percentages, but the data strongly suggest that students are indeed suitable targets, experience motivated offenders at various rates, and lack a great amount of guardianship placing them at a high level of risk for interpersonal victimization. The goal of the current study was to determine why subjects engage with unknown persons among social networking websites, so frequencies of interpersonal victimizations were not surveyed. However, the questionnaire was created with an openended question in hope that subjects would disclose their experiences with unknown persons on social networking websites. Few subject responses indicated students engage with unknown persons whether or not they feel safe, but an overwhelming majority of the students do not feel safe engaging with strangers. It was disclosed that some subjects interact with strangers in search of potential relationships, because they play video games together, or that they don’t mind conversing with strangers because they don’t feel threatened for their safety. 95 Implications for Future Research Those who visit online communication mediums may be more at risk than others. It is believed that those who regularly use the internet to communicate with strangers are more likely to have problems with their parents, suffer sadness, loneliness, or depression, have histories of sexual abuse, and engage in risky behavior compared to those who do not. It was found that many subjects use the internet for e-mail services, instant messenger services, and social networking websites, but rather than focusing on the types of online sites or posting personal information, prevention messages should focus on online interactions because internet-initiated crimes come about through direct communications between motivated offenders and suitable targets. Incidents of interpersonal victimization driven by the internet against individuals are believed to be underreported because victims may feel embarrassed, not view the incident as a crime, or not view themselves as being a victim. People who send personal information such as their gender, hobbies, and personal pictures to strangers are more likely to be solicited by them. However, posting personal information on the internet may not be as risky as some fear, but there is increased risk associated with the kinds of potentially risky online behaviors exhibited. There are several behaviors that are often deemed risky for people to engage in such as granting permission to unknown persons to view a privatized social networking website, conversing with unknown persons, or discussing further relations in an offline environment. It is believed that as the number of different types of these behaviors increase, so do the odds of online interpersonal victimization. Those who interact with strangers over the internet engaging in a high 96 number of risky behaviors increase their level for concern compared to those who do not exhibit risky behaviors while interacting with strangers. Further analyses should be conducted in this area calculating subject’s frequency of victimization in order to account for all incidents and determine if online crimes are underreported. This may also help determine if all online behaviors are indeed risky. Motivated offenders use internet communications such as e-mail services, instant messenger services, chat-rooms, and social networking websites to meet and develop intimate relationships with potential victims. Corrections, victimization, and psychology researchers should use the experiences of known criminals and disclose their tactics used to select victims. In addition, further research should target the demographics of criminals that use internet communications. These methods will help create messages, awareness, and strategies for prevention. It was indicated by several subjects that they use social networking websites for dating purposes. It would be interesting to know the frequency of use of social networking websites strictly for dating purposes. It would also be interesting to know the frequency of those who follow people’s personal information posted through social networking websites without ever contacting them. Further research could reveal how often strangers stalk and/or follow public or private social networking profiles, blogs, or online journals. Unfortunately, the questionnaire did not ask subjects whether or not their social networking website was initially set as a privatized page. Therefore, it is unknown whether previous victimization motivated the subject to change his or her page to private. 97 It may be assumed that a majority of the students originally had public profiles but then changed the setting to private as a result of incidents of victimization or contact by unknown persons. With a subject changing his or her privacy setting this would prevent future incidents from occurring. Future research should ask subjects whether or not their social networking website was originally open for to the public to view. In this study, levels of contact with unknown persons were considered to be low as well as the amount of permission or further access granted to personal information. It is possible that criminal justice students could have a heightened awareness of personal security and victimization. Further research examining interpersonal victimization on social networking websites throughout the nation could prove otherwise. 98 APPENDICES 99 APPENDIX A Questionnaire * If you have already participated in this survey, please, do not participate again* You are invited to participate in a study that seeks California State University, Sacramento undergraduate students to complete a questionnaire about their use of computers, the Internet, and social networking websites. The data from this questionnaire will be used to complete a thesis in partial requirement to obtain a masters degree in Criminal Justice. You were selected as a possible participant in this study through random selection of undergraduate Criminal Justice courses. Participation is completely voluntary, students may end their participation at any time, and all responses will be kept anonymous. If any of the questions make you feel uncomfortable, you may refuse to answer them. All of the information provided will only be analyzed by me and the thesis committee. Therefore results from the research will be reported with no identifiers. If you decide to participate, please complete the attached questionnaire. It may take approximately 10-15 minutes to complete the questionnaire. Participation in this study certifies that participants are 18 years of age or older. Your decision whether or not to participate will not prejudice your future relationships with the California State University, Sacramento. Your return of this questionnaire is implied consent. 100 Please feel free to ask questions regarding this study. You may contact either professor Tim Croisdale at croisdale@csus.edu or me, at bj277@saclink.csus.edu later if you have additional questions. Thank you for your participation. Brandon Jaimes 1) Please indicate your activities performed on the Internet. Check all that apply. □ Research □ Gaming □ Planning travel □ Website design □ Shopping □ E-mail □ Instant message □ Chat rooms □ Social networking websites □ Other (specify) _________________________________________________________ □ None □ Decline to Answer 2) Please indicate the location of your computer when using it. Check all that apply. □ Home (any room) 101 □ School □ Friend’s □ Coffee shop □ Other (specify) _________________________________________________________ □ Not Applicable □ Decline to Answer 3) Please indicate the location where you most frequently use a computer. Check one of the following: □ Home (any room) □ School □ Friend’s □ Coffee shop □ Other (specify) _________________________________________________________ □ Not Applicable □ Decline to Answer 4) Please indicate how often you use each of the following on a typical day. Please specify by filling in the spaces provided. E-mail: _______________ Instant Messenger: _______________ Chat Rooms: ________________ 102 Social Networking Websites: _________________ □ Decline to Answer 5) Is there a parent/guardian, friend, teacher/counselor, sibling, or someone else usually present in the same room while you are using a computer? Check one of the following: □ Yes □ No □ Decline to Answer 6) Thinking of the computer you use most often, does it have any restrictions on the amount of time you can spend online or prevent you from viewing websites with adult content, etc.? Check one of the following: □ Yes □ No □ Other (specify) _________________________________________________________ □ Decline to Answer 7) Please indicate if you have an account for any of the following social networking websites. Check all that apply. □ Facebook □ MySpace □ Friendster □ Twitter 103 □ Xanga □ Other (specify) _________________________________________________________ □ None □ Decline to Answer 8) If applicable, please indicate what information is posted on your social networking website. Check all that apply. □ Age (i.e., 21 years old) □ Gender (i.e., male, female, etc.) □ Additional descriptive characteristics (i.e., eye color, hair color, etc.) □ Hobbies (i.e., shopping, dancing, working out, etc.) □ Picture(s) of self □ Telephone number (i.e., cell phone number, home phone number, etc.) □ Home location (i.e., address) □ Extracurricular activities (i.e., playing for the school baseball team) □ Goals/aspirations (i.e., becoming a doctor, losing weight, etc.) □ Distress problems (i.e., death in the family, etc.) □ Relationship status (i.e., single, married, etc.) □ Other (specify) _________________________________________________________ □ None □ Decline to Answer 104 9) If applicable, is your social networking website page privatized or require your permission for others to view it? Check one of the following: □ Yes □ No □ Decline to Answer 10) How many times have you ever been contacted by an unknown person through a social networking website? Please specify by filling in the space provided. ________________ □ Decline to Answer 11) On any/all of your social networking websites, approximately how many times has a person unknown to you requested your permission to view your profile/ website? Please specify by filling in the space provided. ________________ □ Decline to Answer 12) Of those times when someone unknown to you requested your permission, how many times did you give them permission? Check one of the following: □ None □ A few □ Some □ Most 105 □ All □ Decline to Answer 13) Have you conversed with an unknown person at a social networking website? Check one of the following: □ Yes □ No □ Decline to Answer 14) Have you ever given personal information beyond what is accessible on your website to an unknown person? If “yes”, see below and check all that apply. □ Age (i.e., 21 years old) □ Gender (i.e., male, female, etc.) □ Additional descriptive characteristics (i.e., eye color, hair color, etc.) □ Hobbies (i.e., shopping, dancing, working out, etc.) □ Picture(s) of self □ Telephone number (i.e., cell phone number, home phone number, etc.) □ Home location (i.e., address) □ Extracurricular activities (i.e., playing for the school baseball team) □ Goals/aspirations (i.e., becoming a doctor, losing weight, etc.) □ Distress problems (i.e., death in the family, etc.) □ Relationship status (i.e., single, married, etc.) □ Other (specify) _________________________________________________________ 106 □ No □ Decline to Answer 15) Do you engage in any of the activities mentioned above using a mobile device such as a smart phone? Check one of the following: □ Yes □ No □ Decline to Answer 16) In general, how safe do you feel engaging with unknown persons? On a scale from 1 (very unsafe) to 10 (very safe), please circle a spot on the continuum provided below. □ Decline to Answer 1--------2--------3--------4--------5--------6--------7--------8--------9--------10 Very Unsafe Safe Very Safe 17) If you circled a spot on the continuum to question #16, please explain your answer as to why you may feel safe or unsafe. Please fill in the blank spaces provided unless you decline to answer. __________________________________________________________________ __________________________________________________________________ __________________________________________________________________ __________________________________________________________________ 107 18) What is your gender? Check one of the following: □ Male □ Female □ Decline to Answer 19) What is your age as of your last birthday? Please fill in the blank space provided unless you decline to answer. _____________________ Years 20) What ethnicity/race would you most identify yourself as? Check one of the following: □ American Indian □ Asian □ Black □ Hispanic □ White □ Pacific Islander □ Multiracial □ Other (specify) _________________________________________________________ □ Decline to Answer 21) Please indicate your marital status. Check one of the following: □ Married □ Divorced 108 □ Separated (Can be single, previously married, but not yet divorced) □ Widowed □ Single (Never-married) □ Domestic partner □ Decline to Answer Thank you for your participation. 109 APPENDIX B Script Used Prior to Questionnaire Distribution Hello students, today you are asked to participate in a voluntary study which will be administered by me, Brandon Jaimes, in an attempt to further understand undergraduate criminal justice student computer use, Internet use, and social networking website use. This study has been created to complete a thesis in partial requirement to obtain a masters degree in criminal justice here at the University. You have all been selected as a possible participant in this study through random sampling of scheduled class meetings. Keep in mind the following: First, if you decide to participate, you may quit the survey at anytime without prejudice. Second, participation is completely voluntary, and you, as well as your responses, will remain completely anonymous. Third, results from the research will be reported with no identifiers. Fourth, there will be no compensation for participating in the survey. Remember, if any of the questions make you uncomfortable, you may refuse to answer them. I will ask for a volunteer from the class to distribute the questionnaire while I remain outside. This volunteer will then collect the completed questionnaires, put them in an envelope, seal the envelope, and then hand the envelope to me outside the door. Remember, your return of this questionnaire is implied consent. Also, if you have already participated in this survey at a previous time, please, do not participate again. If you may have any questions regarding this study, you may contact either professor Tim Croisdale 110 at croisdale@csus.edu or me, at bj277@saclink.csus.edu. Thank you for considering participation. 111 APPENDIX C Use of E-mail Services Over 24-hour Period Frequency of E-mail Use Values (Hours) Percentage 0 1 2 3 4 5 6 or more Declined 11.8% 28.8% 19.1% 8.7% 5.5% 9.4% 15.3% 1.4% N 34 83 55 25 16 27 44 4 112 APPENDIX D Use of Instant Messenger Services Over 24-hour Period Frequency of Instant Messenger Use Values (Hours) Percentage 0 70.1% 1 16.3% 2 3.1% 3 3.1% 4 0.7% 5 1.0% 6 or more 4.2% Declined 1.4% N 202 47 9 9 2 3 12 4 113 APPENDIX E Use of Chat-room Services Over 24-hour Period Frequency of Chat-room Use Values (Hours) Percentage 0 1 2 3 4 5 6 or more Declined 94.0% 2.8% 0.7% 0.7% 0.3% 0.30% 1.40% N 270 8 2 2 1 1 4 114 APPENDIX F Use of Social Networking Website Services Over 24-hour Period Frequency of Social Networking Website Use Values (Hours) Percentage N 0 1 2 3 4 5 6 or more Declined 20.8% 19.8% 15.6% 11.8% 4.2% 9.4% 16.7% 1.4% 60 57 45 34 12 27 48 4 115 APPENDIX G Privatization of Social Networking Websites and Student’s Perception of Safety Privatization of SNW and Perception of Safety Crosstabulation Privatized Social Networking Website No Yes N/A Declined Total Level Unsafe N 7 54 0 5 66 of % 17.5% 24.2% 0.0% 23.8% 22.9% Safety 2 N 2 22 2 3 29 % 5.0% 9.9% 50.0% 14.3% 10.1% 3 N 6 40 2 6 54 % 15.0% 17.9% 50.0% 28.6% 18.8% 4 N 3 19 0 2 24 % 7.5% 8.5% 0.0% 9.5% 8.3% 5 N 9 29 0 2 40 % 22.5% 13.0% 0.0% 9.5% 13.9% 6 N 1 14 0 1 16 % 2.5% 6.3% 0.0% 4.8% 5.6% 7 N 1 11 0 0 12 % 2.5% 4.9% 0.0% 0.0% 4.2% 8 N 4 9 0 0 13 % 10.0% 4.0% 0.0% 0.0% 4.5% 9 N 2 8 0 0 10 % 5.0% 3.6% 0.0% 0.0% 3.5% Safe N 3 6 0 0 9 % 7.5% 2.7% 0.0% 0.0% 3.1% Declined N 2 11 0 2 15 % 5.0% 4.9% 0.0% 9.5% 5.2% Total N 40 223 4 21 288 % 100.0% 100.0% 100.0% 100.0% 100.0% 116 APPENDIX H Collapsed Data for Subjects Contacted by Unknown Persons and Their Perception of Safety Collapsed Data for Those Contacted and Perception of Safety Crosstabulation Collapsed Data for Contacted 0-100 101-200 901-1000 Total Level of Safety Unsafe 2 3 4 5 6 7 8 9 Safe Declined Total N % N % N % N % N % N % N % N % N % N % N % N % 66 23.2% 29 10.2% 33 18.6% 23 8.1% 40 14.0% 16 5.6% 12 4.2% 13 4.6% 10 3.5% 8 2.8% 15 5.3% 285 100.0% 0 0.0% 0 0.0% 1 50.0% 1 50.0% 0 0.0% 0 0.0% 0 0.0% 0 0.0% 0 0.0% 0 0.0% 0 0.0% 2 100.0% 0 0.0% 0 0.0% 0 0.0% 0 0.0% 0 0.0% 0 0.0% 0 0.0% 0 0.0% 0 0.0% 1 100.0% 0 0.0% 1 100.0% 66 22.9% 29 10.1% 54 18.8% 24 8.3% 40 13.9% 16 5.6% 12 4.2% 13 4.5% 10 3.5% 9 3.1% 15 5.2% 288 100.0% 117 APPENDIX I Collapsed Data for Subjects who were Requested Permission to View their Social Networking Website Collapsed Data for Requested Permission Crosstabulation Collapsed Data for Requested Permission 9010-100 101-200 201-300 1000 Total Level Unsafe N 6 0 0 0 66 of % 23.2% 0.0% 0.0% 0.0% 22.9% Safety 2 N 29 0 0 0 29 % 10.2% 0.0% 0.0% 0.0% 10.1% 3 N 54 0 0 0 54 % 18.9% 0.0% 0.0% 0.0% 18.8% 4 N 23 1 0 0 24 % 8.1% 100.0% 0.0% 0.0% 8.3% 5 N 40 0 0 0 40 % 14.0% 0.0% 0.0% 0.0% 13.9% 6 N 16 0 0 0 16 % 5.6% 0.0% 0.0% 0.0% 5.6% 7 N 12 0 0 0 12 % 4.2% 0.0% 0.0% 0.0% 4.2% 8 N 13 0 0 0 13 % 4.6% 0.0% 0.0% 0.0% 4.5% 9 N 10 0 0 0 10 % 3.5% 0.0% 0.0% 0.0% 3.5% Safe N 7 0 1 1 9 % 2.5% 0.0% 100.0% 100.0% 3.1% Declined N 15 0 0 0 15 % 5.3% 0.0% 0.0% 0.0% 5.2% Total N 285 1 1 1 288 % 100.0% 100.0% 100.0% 100.0% 100.0% 118 APPENDIX J Subjects who were Asked Permission by Unknown Persons to View Their Private Social Networking Website and Their Perception of Safety Permission to View Privatized SNW and Perception of Safety Crosstabulation Permission to View Privatized Social Networking Website None A Few Some Most All N/A Declined Level Total Unsafe N 56 3 0 0 0 0 7 66 of 2 N 22 2 0 0 0 2 3 29 Safety 3 N 39 9 1 0 0 0 5 54 4 N 14 9 0 0 0 0 1 24 5 N 23 8 2 1 1 0 5 40 6 N 8 5 1 1 0 0 1 16 7 N 3 6 3 0 0 0 0 12 8 N 10 2 0 0 0 0 1 13 9 N 5 2 2 1 0 0 0 10 Safe N 2 2 1 2 2 0 0 9 Declined N 9 2 1 0 0 0 3 15 N 191 50 11 5 3 2 26 288 Total 119 APPENDIX K Subjects who Conversed with Unknown Persons and Their Perception of Safety Conversed with Unknown Person and Perception of Safety Crosstabulation Conversed No Yes N/A Declined Total Level Unsafe N 58 5 0 3 66 of % 31.7% 5.7% 0.0% 18.8% 22.9% Safety 2 N 21 6 1 1 29 % 11.5% 6.8% 100.0% 6.3% 10.1% 3 N 36 16 0 2 54 % 19.7% 18.2% 0.0% 12.5% 18.8% 4 N 13 10 0 1 24 % 7.1% 11.4% 0.0% 6.3% 8.3% 5 N 21 15 0 4 40 % 11.5% 17.0% 0.0% 25.0% 13.9% 6 N 7 8 0 1 16 % 3.8% 9.1% 0.0% 6.3% 5.6% 7 N 5 7 0 0 12 % 2.7% 8.0% 0.0% 0.0% 4.2% 8 N 6 7 0 0 13 % 3.3% 8.0% 0.0% 0.0% 4.5% 9 N 5 5 0 0 10 % 2.7% 5.7% 0.0% 0.0% 3.5% Safe N 4 5 0 0 9 % 2.2% 5.7% 0.0% 0.0% 3.1% Declined N 7 4 0 4 15 % 3.8% 4.5% 0.0% 25.0% 5.2% Total N 183 88 1 16 288 % 100.0% 100.0% 100.0% 100.0% 100.0% 120 REFERENCES Addison, D. (2001). Youngsters Increase Time Online as Sites Seek Return Visits. Marketing 10. Allison, F.H., Schuck, A.M., & Lersch, K.M. (2005). Exploring the Crime of Identity Theft: Prevalence, Clearance Rates, and Victim/Offender Characteristics. Journal of Criminal Justice, 33, 19-29. Anonymous. (2004). Cyberstalking of Kids Jumps 237% in Maine. Juvenile Justice Digest, 32(19), 4. Anonymous. (2009). Fear of Online Sex Predators May be Overblown, Report Says. Criminal Justice Newsletter, 7. Apuzzo, M. (2006). Prosecutors: Men used myspace.com to Meet Underage Girls for Sex. Retrieved from http://www.boston.com/news/local/connecticut/articles /2006/03/02/prosecutors_men_used_myspacecom_to_meet_underage_girls_ for_sex. Arnold, R., Keane, C., & Baron, S. (2005). Assessing Risk of Victimization through Epidemiological Concepts: An Alternative Analytic Strategy Applied to Routine Activities Theory. Canadian Review of Sociology, 42(3), 345-364. Ben-Yehuda, N., & Goode, E. (1994). Moral Panics: The Social Construction of Deviance. Oxford: Blackwell. Bernat, F.P., & Zhilina, T. (2010). Human Trafficking: The Local Becomes Global. Women & Criminal Justice, 20(1/2), 2-9. 121 Bjerregaard, B. (2000). An Empirical Study of Stalking Victimization. Violence and Victims, 15, 389-406. Blackburn, A.G., Taylor, R.W., & Davis, J.E. (2010). Understanding the Complexities of Human Trafficking and Child Sexual Exploitation: The Case of Southeast Asia. Women & Criminal Justice, 20 (1/2), 105-126. Bradenburg, J.B. (1997). Confronting Sexual Harassment: What Schools and Colleges Can Do. New York: Teachers College Press. Cassell, J., & Cramer, M. (2007). High Tech or High Risk? Moral Panics about Girls Online. Digital Youth, Innovation, and the Unexpected: The MacArthur Foundation Series on Digital Media and Learning, 53-75. Choo, K.K.R. (2008). Organized Crime Groups in Cyberspace: A Typology. Trends Organized Crime, 11, 270-295. Clodfelter, T.A., Turner, M.G., Hartman, J.L., & Kuhns, J.B. (2010). Sexual Harassment Victimization During Emerging Adulthood: A Test of Routine Activities Theory and a General Theory of Crime. Crime and Delinquency, 56(3), 455-481. Coleman, F.L. (1997). Stalking Behavior and the Cycle of Domestic Violence. Journal of Interpersonal Violence, 12, 420-432. Combs-Lane, A.M., & Smith, D.W. (2002). Risk of Sexual Victimization in College Women: The Role of Behavioral Intentions and Risk-Taking Behaviors. Journal of Interpersonal Violence, 17(2). 122 Cortina, L.M., Swan, S., Fitzgerald, L.F., & Waldo, C. (1998). Sexual Harassment and Assault: Chilling the Climate for Women in Academia. Psychology of Women Quarterly. 22, 419-441. Dansky, B., & Kilpatrick, P. (1997). Effects of Sexual Harassment .In W. O’ Donohue (Ed.), Sexual Harassment: Theory, Research, and Treatment (p.152-174). Boston: Allyn & Bacon. Davis, R.C., Lurigio, A.J., & Herman, S.A. (2007). Victims of Crime. Thousand Oaks, CA: Sage DeCoster, S., Estes, S., & Mueller, C. (1999). Routine Activities and Sexual Harassment in the Workplace. Work and Occupations, 26, 21-49. Dietz, P.E., Matthews, D.B., Van Duyne, C., Martell, D.A., Parry, C.D.H, Stewart, T., Warren, J., & Crowder, J. (1991). Threatening and Otherwise Inappropriate Letters to Hollywood Celebrities. Journal of Forensic Sciences, 36, 1445-1468. D’Ovidio, R., Mitman, T., El-Burke, I, & Shumar, W. (2009). Adult-Child Sex Advocacy Websites as Social Learning Environments: A Content Analysis. International Journal of Cyber Criminology, 3(1), 421-440. Dziech, B.W. (2003). Sexual Harassment of College Campuses. In M. Paludi & C. Paludi (Eds.), Academic and Workplace Sexual Harassment: A Handbook of Cultural, Social Science, Management, and Legal Perspectives (p.147-172). Westport, CT: Praeger. Dziech, B.W., & Hawkins, M.W. (1998). Sexual Harassment in Higher Education: Reflections and New Perspective. New York: Garland. 123 Federal Trade Commission.(2000). Identity Theft. Retrieved from http://www.ftc.gov/os/2000/03/identitytheft.htm Federal Trade Commission.(2003). Fraud Complaints and Identity Theft Victims by State. Retrieved from http://www.consumer.gov/sentinel/trends.html Finn, J. (2004). A survey of online harassment at a university campus. Journal of Interpersonal Violence, 19(4), 468-483. Fisher, B.S., Cullen, F.T., & Turner, M.G. (2000). The Sexual Victimization of College Women. Washington, DC: U.S. Department of Justice, National Institute of Justice. Fisher, B.S., Cullen, F.T., & Turner, M.G. (2002).Being Pursued: Stalking Victimization in a National Study of College Women. Criminology & Public Policy, 1(2), 257308. Fontana-Rosa, J.C. (2001). Legal Competency in a Case of Pedophilia: Advertising on the Internet. International Journal of Offender Therapy and Comparative Criminology, 54, 118-128. Fremouw, W.J., Westrup, D., & Pennypacker, J. (1996). Stalking on Campus: The Prevalence and Strategies for Coping with Stalking. Journal of Forensic Sciences, 42, 666-669. Goodwin, S.L. (2003). Cyberstalking: A new criminal behavior? Women Police. 37(1), 23. Gutek, B.A. (1981). Experiences of Sexual Harassment: Results from a Representative Survey. National Institution of Mental Health. Unknown: 1-34. 124 Hall, R.F., Graham, R.D., & Hoover, G.A. (2004). Sexual Harassment in Higher Education: A Victim’s Remedies and a Private University Liability. Education and the Law. 16, 33-45. Hancock, B. (2000). Cyberstalking on the Rise. Computers & Security, 19(4), 307-308. Harrell, A.V., Smith, B.E., & Cook, R.F. (1985). The Social Psychological Effects of Victimization (Report submitted to the National Institute of Justice). Washington, DC: Institute for Social Analysis. Holmes, R.M. (1993). Stalking in America: Types and Methods of Criminal Stalkers. Journal of Contemporary Criminal Justice, 9, 317-327. Izenberg, N., & Lierbman, D. (1998). The Web, Communication Trends, and Children’s Health; How the Children Use the Web. Doing Internet Research. London: Sage. Jasinski, J.L., & Mustaine, E.E. (2001). Police Response to Physical Assault and Stalking Victimization: A Comparison of Influential Factors. American Journal of Criminal Justice, 26(1), 23-41. Johnson, D. (2006). Seven Things All Adults Should Know About MySpace. Retrieved from http://education.illinois.edu/wp/netfiles.uiuc.edu/kleckaus/www/social_ networking_sites.html Kalof, L., Eby, K.K., Matheson, J.L., & Kroska, R.J. (2001). The Influence of Race and Gender on Student Self-Reports of Sexual Harassment by College Professors. Gender and Society.15, 282-302. Keeney, B.T., & Heide, K.M. (1994).Gender Differences in Serial Murderers. Journal of Interpersonal Violence, 9, 383-398. 125 Kennedy, M.A., & Taylor, M.A. (2010). Online Harassment and Victimization of College Students. Justice Policy Journal, 7(1). Koss, M.P., Gidycz, C.A., & Wisniewski, N. (1987). The Scope of Rape: Incidence and Prevalence of Sexual Aggression and Victimization in a National Sample of Higher Education Students. Journal of Consulting and Clinical Psychology. 55, 162-170. Kramer, L.A., & Berg, E.C. (2003). A Survival Analysis of Timing of Entry into Prostitution: The Differential Impact of Race, Educational Level, and Childhood/Adolescent Risk Factors. Sociological Inquiry, 73(4), 511-528. Lanning, K,V. (1984). Child Pornography and Sex Rings. FBI Law Enforcement Bulletin, 53, 10-16. LaRocca, M., & Kromrey, J. (1999). The Perception of Sexual Harassment in Higher Education: Impact of Gender and Attractiveness. Sex Roles, 40(11/12), 921-940. Licklider, J.C.R., & Clark, W.E. (1962). On-Line Man-Computer Communication. AFIPS Conference Proceedings 21, 112-128. Madriz, E. (1996). The Perception of Risk in the Workplace. A Test of Routine Activity Theory. Journal of Criminal Justice, 24, 407-412. Marcum, C. (2008). Potential Causal Factors of Adolescent Online Victimization Produced from a Test of Routine Activities Theory. Conference Paper-American Society of Criminology, 1. Marks, P. (2007). How to Leak a Secret and Not Get Caught. New Scientist, 2586(13). 126 McAnaney, K.G., Curliss, L.A., & Abeyta-Price, C.E. (1993). From Imprudence to Crime: Anti-stalking laws. Notre Dame Law Review, 68, 819-909. Mitchell, K.J., Becker-Blease, K.A., & Finkelhor, D. (2005). Inventory of Problematic Internet Experiences Encountered in Clinical Practice. Professional Psychology, 36(5), 498-509. Mitchell, K.J., Finkelhor, D., & Wolak, J. (2001). Risk factors for and impact of online sexual solicitation of youth. Journal of American Medical Association, 285, 3011-3014. Mitchell, K.J., Jones, L.M., Finkelhor, D., & Wolak, J. (2011). Internet-Facilitated Commercial Sexual Exploitation of Children: Findings From a Nationally Representative Sample of Law Enforcement Agencies in the United States. Sexual Abuse: A Journal of Research and Treatment, 23(1), 43-71. Mitchell, K.J., Ybarra, M., & Finkelhor, D. (2007). The Relative Importance of Online Victimization in Understanding Depression, Delinquency, and Substance Use. Child Maltreatment, 12(4), 314. Mustaine, E.E., & Tewksbury, R. (1999). A Routine Activity Theory Explanation for Women's Stalking Victimizations. Violence Against Women, 5(1), 43-62. National Consumers League. (2008). Love Stinks. Consumer Group Helps Lonely Evade Scams. Retrieved from http://www.nclnet.org/news/2008/sweetheart_swindles_ 02082008.htm National Institute of Justice. (1996). Domestic Violence, Stalking, and Anti-stalking legislation. Washington, DC: Author. 127 National Victim Center. (1997). Stalking [On-line]. Retrieved from http://www. nvc.org/ddir/info43.htm. Norris, J. (1988). Serial Killers: The Growing Menace. New York: Dolphin. Ogilvie, E. (2001). Cyberstalking. Crime & Justice International, 17(50), 9-10. Paludi, M. (1997). Sexual Harassment in Schools. In W. O’Donohue (Eds.), Sexual Harassment: Theory, Research, and Treatment (p.225-249).Boston: Allyn & Bacon. Parks, K.A., & Miller, B.A. (1997). Bar Victimization of Women. Psychology of Women Quarterly, 21(4), 509-525. Perkel, D. (2008). Copy and Paste Literacy? Literacy Practices in the Production of a Myspace Profile. In K. Drotner, H.S. Jensen and K. Schroeder (Eds.), Informal Learning and Digital Media: Constructions, Contexts, Consequences. Newcastle, UK: Cambridge Scholar Press. Pierce, T. (2006). Talking to Strangers on MySpace: Teens’ Use of Internet Social Networking Sites. Journal of Media Psychology, 11(3). Pryor, J.B., La Vite, C.M., & Stoller, L.M. (1993).A Social Psychological Analysis of Sexual Harassment: The Person/ Situation Interaction. Journal of Vocational Behavior, 42, 68-83. Quayle, E., & Taylor, M. (2001). Child Seduction and Self-Representation on the Internet. Cyberpsychology & Behavior, 4(5), 597-608. 128 Rainie, L. (2006). Life Online: Teens and Technology and the World to Come. Speech to the Annual Conference of the Public Library Association. Retrieved from http://www.pewinternet.org/ppt/Teens%20and%20technology.pdf. Rege, A. (2009). What’s Love Got to Do With it? Exploring Online Dating Scams and Identity Fraud. International Journal of Cyber Criminology, 3(2), 494-512. Reisig, M.D., Pratt, T.C., & Holtfreter, K. (2009). Perceived Risk of Internet Theft Victimization: Examining the Effects of Social Vulnerability and Financial Impulsivity. Criminal Justice and Behavior, 36(4), 369-384. Rosen L. (2006). Blocking sexual predators on MySpace: The kids are Alright. Retrieved from http://www.csudh.edu/psych/lrosen.htm Rubin, P.N. (1995). Civil Rights and Criminal Justice: Primer on Sexual Harassment. Research in Action (NJC Publication No. 156663). Washington, DC: Department of Justice. Russell, B.L., & Oswald, D.L. (2001). Strategies and Dispositional Correlates of Sexual Coercion Perpetrated by Women: An Exploratory Investigation. Sex Roles, 45, 103-115. Simons, R.L., & Whitbeck, L.B. (1991). Sexual Abuse as a Precursor to Prostitution and Victimization Among Adolescent and Adult Homeless Women. Journal of Family Issues, 12, 361-379. Stalking Victim's Sanctuary. (1997). Stalking 101 [On-line]. Retrieved from http://www.ccon.com/stalkvictim/stalk.htm. 129 Taylor, M.A. (2008). Victimization on Social Networking Sites (Master’s Thesis). University of Nevada, Las Vegas. Testa, M., & Parks, K.A. (1996). The Role of Women’s Alcohol Consumption in Sexual Victimization. Aggression and Violent Behavior, 1, 217-234. Tjaden, P., & Thoennes, N. (1996). Stalking in America: How big is the Problem? Paper Presented at the Annual Meetings of the American Society of Criminology, Chicago, Illinois. Tyler, K., Hoyt, D., & Whitbeck, L. (2000). The Effects of Early Sexual Abuse on Later Sexual Victimization Among Homeless and Runaway Adolescents. Journal of Interpersonal Violence, 15, 235-250. U.S. General Accounting Office. (2009). Identity Fraud: Governments Have Acted to Protect Personally Identifiable Information, but Vulnerabilities Remain (Publication No. GA0-09-759T). Washington, DC: Author. Walker-Rodriguez, A., & Hill, R. (2011). Human Sex Trafficking. FBI Law Enforcement Bulletin; Mar 2011, 80(3). Williams, E.A., Lam, J.A., & Shively, M. (1992). The Impact of a University Policy on the Sexual Harassment of Female Students. Journal of Higher Education.63, 5064. Wolak, J., Mitchell, K., & Finkelhor, D. (2006). Online Victimization of Children: Five Years Later.Washington, D.C.: National Centers for Missing and Exploited Children.