CCNA 5.0
Planning Guide
Chapter 7: Securing Site-toSite Connectivity
Connecting Networks
Presentation_ID
© 2008 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
1
Chapter 7: Objectives
After completing this chapter, students will be able to:
Describe benefits of VPN technology.
Describe site-to-site and remote access VPNs.
Describe the purpose and benefits of GRE tunnels.
Configure a site-to-site GRE tunnel.
Describe the characteristics of IPsec.
Explain how IPsec is implemented using the IPsec protocol
framework.
Explain how the Anyconnect client and clientless SSL remote
access VPN implementations support business requirements.
Compare IPsec and SSL remote access VPNs.
Presentation_ID
© 2008 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
2
Chapter 7: Overview
This chapter:
Explains the concepts and processes related to VPNs
Explains the benefits of VPN implementations and the underlying
protocols required to configure VPNs
Presentation_ID
© 2008 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
3
Chapter 7: Activities
What activities are associated with this chapter?
7.0.1.2 Class Activity – VPNs at a Glance
7.1.1.3 Activity – Identifying the Benefits of VPNs
7.1.2.3 Activity – Compare Types of VPNs
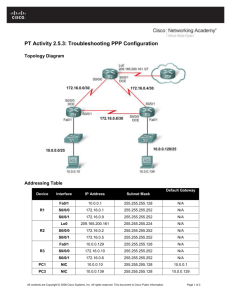
7.1.2.4 Packet Tracer – Configuring VPNs (Optional)
7.2.1.3 Activity – Identifying GRE Characteristics
7.2.2.2 Syntax Checker – Configure and Verify GRE
7.2.2.3 Packet Tracer – Configuring GRE
7.2.2.4 Packet Tracer – Troubleshooting GRE
7.2.2.5 Lab – Configuring a Point-to-Point GRE VPN Tunnel
Presentation_ID
© 2008 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
4
Chapter 7: Activities (cont.)
What activities are associated with this chapter?
7.3.2.7 Activity – Identifying IPsec Terminology and Concepts
7.3.2.8 Packet Tracer – Configuring GRE over IPsec (Optional)
7.4.1.4 Activity – Compare Cisco SSL VPN Solutions
7.4.2.5 Activity – Identify Remote-Access Characteristics
7.5.1.1 Class Activity – VPN Planning Design
7.5.1.2 Packet Tracer – Skills Integration Challenge
Presentation_ID
© 2008 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
5
Chapter 7: Packet Tracer Activity Password
The password for all the Packet Tracer activities in this chapter is:
PT_ccna5
Presentation_ID
© 2008 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
6
Chapter 7: Assessment
Students should complete Chapter 7 Exam after completing
Chapter 7.
Worksheets, labs and quizzes can be used to informally assess
student progress.
Presentation_ID
© 2008 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
7
Chapter 7: New Terms and Commands
What terms and commands are introduced in this chapter?
7.1.1.1
7.1.2.1
7.1.2.2
7.2.2.1
7.2.2.2
7.3.1.1
7.3.1.2
7.3.2.1
Presentation_ID
VPNs
Tunnel
Generic Routing Encapsulation (GRE)
Cisco Adaptive Security Appliance (ASA)
Site-to-site VPNs
VPN Gateway
Remote Access VPNs
Cisco AnyConnect Secure Mobility Client
interface tunnel number command
tunnel source command
tunnel destination command
show interface tunnel command
IP Multicast Tunneling
IPsec
Anti-replay Protection
Encryption
Decryption
© 2008 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
8
Chapter 7: New Terms and Commands
(cont.)
What terms are introduced in this chapter?
7.3.2.2
7.3.2.3
7.3.2.4
7.3.2.5
7.3.2.6
Presentation_ID
Symmetric Encryption
Asymmetric Encryption
Public Key Encryption
Diffie-Hellman Key Exchange
OAKLEY
IKE protocol
Hash
Hash-based Message Authentication Code (HMAC)
MD5
SHA
Pre-shared Key (PSK)
RSA Signature
Certificate Authority (CA)
Digital Signature Algorithm (DSA)
Authentication Header (AH)
Encapsulating Security Payload (ESP)
© 2008 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
9
Chapter 7: New Terms and Commands
(cont.)
What terms are introduced in this chapter?
7.4.1.1
7.4.1.2
7.4.2.1
Presentation_ID
Secure Sockets Layer (SSL) VPN
IP Security (IPsec) VPN
Cisco AnyConnect Secure Mobility Client with SSL
Cisco Secure Mobility Clientless SSL VPN
Cisco Easy VPN Server
Cisco Easy VPN Remote
Cisco VPN Client
© 2008 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
10
Chapter 7: Best Practices
For best practices, the instructor should:
Use this chapter as an introduction to CCNA Security.
Make this chapter as hands-on as possible.
Encourage students to complete chapter activities, labs, and to use
the Syntax Checker.
Refer to the CCNA Security curriculum for more labs and reference
materials.
Use http://www.cisco.com for additional VPN materials.
Presentation_ID
© 2008 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
11
Chapter 7: Additional Help
For additional help with teaching strategies, including lesson
plans, analogies for difficult concepts, and discussion topics, visit
the CCNA Community at
http://community.netacad.net/web/ccna/files.
If you have lesson plans or resources that you would like to
share, upload them to the CCNA Community to help other
instructors.
Presentation_ID
© 2008 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
12
Chapter 7: Topics Not in ICND2 200-101
This section lists topics covered by this chapter that are NOT listed
in the ICND2 200-101 Blueprint. Those topics are posted at
http://www.cisco.com/web/learning/exams/list/icnd1b.html.
Instructors could skip these sections; however, they should provide
additional information and fundamental concepts to assist the
student with the topic.
Presentation_ID
© 2008 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
13
Chapter 7: Topics Not in 200-101 ICND2
What sections of this chapter are NOT in the 200-101 ICND2
certification blueprint?
7.0.1
7.1
7.2
7.3
7.4
7.5
Presentation_ID
Topic - Introduction
Section - VPNs
Section – Site-to-Site GRE Tunnels
Section – Introducing IPsec
Section – Remote Access
Summary
© 2008 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
14
Presentation_ID
© 2008 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
15
Presentation_ID
© 2008 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
16