Demo - H3G_211212
advertisement

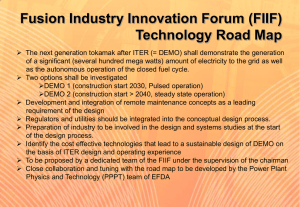
Secure and Trustworthy Composite Services Aniketos project demonstration H3G – Dec 21st, 2012 Contents and Objectives Presentation General concepts Platform description Case studies Demo Demo scenario Overview of Aniketos front-end Tools usage (live session) Discussion and feedback Overall impression (benefits/drawbacks) Appeal of telco case study and business model Suggestions for partnerships and relationships H3G demo event – Dec 21st, 2012 Aniketos Project EU (FP7/2007-2013) funded project (grant no. 257930) The project includes 17 partners from 10 different European countries. Period: Aug 2010 – Jan 2014 (42 months duration) Aiming to achieve Provide service developers and providers with a secure service development framework that includes methods, tools and security services that supports the design-time creation and run-time composition of secure dynamic services, where both the services and the threats are evolving See http://aniketos.eu for more info H3G demo event – Dec 21st, 2012 Aniketos Concepts Focusing on web services Services offered ‘in the cloud’ from Service Provider(s) multiple service providers Aniketos plus and key challenges Constantly maintaining the security and trustworthiness in a service-oriented environment evolving in the cycle of designing, provisioning, delivering and using services Security and trustworthiness Trust ? Security ? Design Time (DT) service composition Run-Time (RT) service (re)composition Services will be designed according to Service end user organizational and business views H3G demo event – Dec 21st, 2012 Aniketos Positioning H3G demo event – Dec 21st, 2012 Platform Overview Service Developers Service Providers •Use community support (design, threat analysis) •Use community support (submit, threat notification) •Service discovery & composition •Ensure trust & security •Monitor trust & security •Perform adaptation Service end users •Certification programme •Single point of trust H3G demo event – Dec 21st, 2012 Future Telecom Services H3G demo event – Dec 21st, 2012 User Story A1 (part 1) Bob accesses the WebShop application in order to purchase an electronic item he wishes. The end user (Bob) owns a mobile device which is equipped with a GPS receiver and a presence enabled VoIP client when accessing the web portal of his TLC Operator. 2 1 Application Server Platform Converged SIP/HTTP application The services involved are: a. WebShop for general electronic commerce access; b. StoreLocator for letting users to choose the store where to get the items selected. 5 Then, he decides to purchase the item of interest. 6 The StoreLocator service gives users two options: 1) a manual selection of the stores that can be selected from an offered list; 2) letting StoreLocator service propose a list of closest stores. 3 Bob asks for help of an assistant by starting a click-to-call VoIP communication. SIP servlets 4 7 Bob selects option (2) for automatic store localization. By doing so a service recomposition is started… 8 …to collect Bob’s current position information and to generate maps and addresses of the stores which are closer to Bob. H3G demo event – Dec 21st, 2012 Bob is finally asked to confirm his mail address retrieved through the IdP to inform him when he can get the purchased item . User Story A1 (part 2) Bob accesses the WebTravel by pressing the “Plan your trip” button. Bob connects to the WebTravel application in order to book a hotel and the tickets for his next business trip. 2 1 3 WebTravel is an application built using a composite service made up of two service components: 1. a web service to book the hotel; 2. a web service to buy the tickets for the trip. In order to complete the hotel reservation, an electronic form must be filled with personal data. The system detects, through the presence information, that Bob is currently using a smartphone. Application Server Platform Converged SIP/HTTP application SIP servlets 5 4 Bob is asked (optional) to give authorization for the automatic compilation of the reservation form. 6 Bob accepts and allows the retrieval of this information from the IdP in a secure manner. In this case, IdP is used for secure exchange of user’s data inside the federation. The form is filled in automatically with Bob’s personal data. H3G demo event – Dec 21st, 2012 User Story A2 Aniketos layer Resource layer Internet Marketplace open AM REST / SAML IdM Provider composite web service(s) Identity Provider atomic service User Profile IMS - Telco HSS Diameter Attribute Provider - Bridging IMS and Internet identities - Single Sign On - Multi-factor authentication - IMS Service Exposure (e.g. user’s attributes and presence) atomic service OMA Enabler(s) Presence enabler Enabler Provider SIP/XCAP atomic service H3G demo event – Dec 21st, 2012 Aniketos Benefits Aniketos provides a powerful platform for secure service developments that will bring benefits to: Service Designers / Developers: to support the creation and the delivery of new innovative services. In general, these developments are commissioned by Service Providers Service Providers: to enhance their portfolio of services and consequently increase the chance for incrementing revenues by attracting new customers or increasing customer retention End Users: to increase the appeal for services that are intrinsically secure and reliable, having a single point-of-trust with a clear customer’s relationship H3G demo event – Dec 21st, 2012 Aniketos Business Prospective Delivering of Aniketos in the cloud as PaaS "Security as a Service“ Business models and actors Brokerage model (Providers) Service Providers need to pay some fee in order to make their services (security descriptors) available in Aniketos Marketplace Pay-per-use (Consumers) Service Developers will pay in order to create and deploy composite services by using the platform from the Aniketos Provider End Users will pay for invocation of Aniketos composite services Aniketos Provider that manages the Marketplace holds a remunerative and important asset H3G demo event – Dec 21st, 2012 Aniketos Demo: Design of a trustworthy composite service Demonstration goals The demo aims to show the exploitation of the Aniketos front-end for the secure service composition in order to: express the security requirements over the services involved in the composition build the service specification of business process to realize the composite service with BPMN perform service discovery, validation and deployment Application of the design-time process to a real example taken from an industrial case study Realization of composite service (InfoService) H3G demo event – Dec 21st, 2012 InfoService overview Weather forecast Web Page Info collector Geocoding Point of Interests Map Service Designer aims to create a service that takes in input a street address and shows on a web page some information related to the provided location. H3G demo event – Dec 21st, 2012 Reference scenario The Service Provider wants the service to be trustworthy, so the Service Designer will use: STS-tool for the specification of security and trustworthiness requirements SCF tool for the design of the composite service SRE for the execution of the composite service H3G demo event – Dec 21st, 2012 Design Time Process analysis Design-time processes Generic design-time composition Specify serv ice Discov er serv ice component candidates Select serv ice components Validate serv ice Establish contracts Assemble serv ice Serv ice dev eloper H3G demo event – Dec 21st, 2012 Deploy serv ice Run-time Process H3G demo event – Dec 21st, 2012 18 Aniketos modules Interaction Layer Socio-technical security modelling tool Service runtime environment Service composition framework Business Logic Layer Trustworthiness Component Model transformation module Identity management service Secure composition planner module Verification Component Security-by-Contract Component Security property determination module Threat response recommendation module Notification module Security Requirements Compliance Module Service threat monitoring module Security policy monitoring module Data Access Layer Marketplace Community support module Training material module Threat repository module H3G demo event – Dec 21st, 2012 Aniketos front-end tools Socio Technical Security (STS) language & tool Express security needs at organizational level Role- and goal-oriented requirements modeling language (STS-ml) Graphical notation tool H3G demo event – Dec 21st, 2012 STS-tool features (ver 1.3) Extended set of supported security needs no-Repudiation (noRep - 3 types), no-Delegation (noDel), Redundancy (Red - 4 types), integrity of transmission separation of duties (SoD), binding of duties (BoD) authorization: usage (U), modification (M), production (P), disclosure (D), scope of usage (NtK), transferability Automatic derivation of Security Requirements Document Analysis (on-going) consistency analysis: check model against semantics of STS-ml security analysis: identify violations of security needs Open-source available (http://www.sts-tool.eu) for Windows/Linux/Mac H3G demo event – Dec 21st, 2012 22 STS-tool utilization error/warning analysis Modeling Activities Phase 1. Model the Social View Step 1.1 Identify stakeholders Step 1.2 Identify assets and interactions Step 1.3 Express security needs Phase 2. Model the Information View Step 2.1 Identify information and its owner Step 2.2 Represent information structure Phase 3. Model the Authorization View Step 3.1 Model authorizations to info Phase 4. Automated analysis Step 4.1 Consistency analysis Step 4.2 Security analysis Phase 5. Derive Security Requirements Step 5.1 Derive security requirements document refinement needed H3G demo event – Dec 21st, 2012 STS-tool utilization STS-tool live session ... H3G demo event – Dec 21st, 2012 Aniketos front-end tools Secure Composition Framework (SCF) Design time module available in the Aniketos environment Used by service designers to build executable composition plans Authentication is needed - once authenticated, service designers can start the BPMN modelling H3G demo event – Dec 21st, 2012 BPMN model of InfoService From the description of the service in terms of functionality, the service designer will use different atomic services and compose them according to the BPMN drafted in the SCF editor H3G demo event – Dec 21st, 2012 BMPN model annotated with trustworthiness requirement The service designer is in charge of designing a composite service with a specific requirement on trusthworthiness value The trustworthiness requirement is expressed as a consumer policy (XML file) written in ConSpec grammar The file location is included in an extensionElements tag in the XML representing the BPMN H3G demo event – Dec 21st, 2012 Annotated BPMN (1 of 2) An excerpt of the resulting XML for the annotated BPMN is shown below: H3G demo event – Dec 21st, 2012 Annotated BPMN (2 of 2) SRS document is generated by the STS-tool BPMN model is generated by using the SCF tool MTM will process both informations to generate an annotated BPMN model (EABPMN) MTM not available at this stage of the project (mapping under development) Currently, a manual intervention from the Service Designer is necessary H3G demo event – Dec 21st, 2012 Service discovery and selection of the service operation In order to make the composition plans the SCF has to bind real web services to the service tasks in the BPMN Binding process entails the following steps: 1. Discovery of services using the ServiceType as search filter 2. SCF shows the operations offered by the web services matching the request based on the ServiceType Selection of the specific operation that the service designer wants to use in order to build the composite service InfoService If the same operation is offered by different atomic services the service designer will see just one operation H3G demo event – Dec 21st, 2012 Discovery and selection: GeoCoding example (1/2) H3G demo event – Dec 21st, 2012 Discovery and selection: GeoCoding example (2/2) 2 1 The service designer discovers operations offered by GeoCoding type services ( ) and selects getCoordinates ( ) The service designer is not aware of how many web services offer that operation - SCF tool will bind the different services to the service task when making composition plans H3G demo event – Dec 21st, 2012 Creation of composition plans Once the service designer has selected an operation for each service task the SCF is ready to create the composition plans When the service designer clicks on “Create composition plans” button, the SCF shows a set of functionally valid composition plans H3G demo event – Dec 21st, 2012 Composition plans created by the SCF SCF created 12 composition plans: this is explained by the number of web services offering the same operation: Geocoding type: bound to 2 web services PointOfInterest type: bound to 3 web services WeatherForecast type: bound to 1 web service Map type: bound to 2 web services WebPageInfoCollector type: bound to 1 web service ... thus the number of composition plans is 2 X 3 X 1 X 2 X 1 = 12 H3G demo event – Dec 21st, 2012 Selection of trustworthy composition plans Composition plans ensure functionality but do not consider the trustworthiness requirement Composition plans have to be checked against the requirements specified for the trustworthiness value This check is performed by the Secure Composition Planner Module (SCPM) which receives the composition plans from the SCF and returns those ones that fulfill the trustworthiness requirement SCPM invokes the Trustworthiness prediction module (TM) to evaluate the trustworthiness value for the set of composition plans received from the SCF H3G demo event – Dec 21st, 2012 Trustworthiness prediction for composite services Trustworthiness value of the composite service is evaluated by using the weakest link principle: Trustworthiness module evaluates the trustworthiness value for each service taking part in the composition Lowest value is returned as the trustworthiness value of the composite service Trustworthiness value is evaluated by TM as a combination of: Cognitive trust of the user, based on the service and service provider reputation Non-cognitive trust, based on objective and measurable properties of the service like QoS attributes (e.g. reliability, performance, availability) H3G demo event – Dec 21st, 2012 Trustworthy composite services Service designer clicks on “Verify All” button the SCPM in order to select all the composition plans that fulfil the requirement on trustworthiness Service designer selects “Order By” Trustworthiness and clicks on “Order/Rank” button in order to visualize the Trustworthiness value of the composition plans H3G demo event – Dec 21st, 2012 Last steps: upload and deploy Finally, service designer selects one of the trustworthy composition plans in order to: Upload the BPMN to an Activiti Engine –Deploy web application st, a H3G demo event Dec 21to 2012 server SCF tool utilization SCF tool live session ... H3G demo event – Dec 21st, 2012 Thanks for your attention fausto.andreotti@italtel.it pierluigi.sciuto@selexelsag.com H3G demo event – Dec 21st, 2012