CIS-496 / I.S. Auditing
advertisement

Chapter 2:
Computer Operations
STRUCTURING THE IT FUNCTION
Centralized data processing
(as opposed to DDP)
Database administrator
Data processing manager/dept.
Data control
Data preparation/conversion
Computer operations
Data library
2
STRUCTURING THE IT FUNCTION
Segregation of incompatible IT functions
Systems development & maintenance
Participants
End users
IS professionals
Auditors
Other stakeholders
3
STRUCTURING THE IT FUNCTION
Segregation of incompatible IT functions
Objectives:
Segregate transaction authorization from
transaction processing
Segregate record keeping from asset
custody
Divide transaction processing steps among
individuals to force collusion to perpetrate
fraud
Separating systems development from
computer operations
4
STRUCTURING THE IT FUNCTION
Segregation of incompatible IT functions
Separating DBA from other functions
DBA is responsible for several critical tasks:
Database security
Creating database schema and
user views
Assigning database access authority to users
Monitoring database usage
Planning for future changes
5
STRUCTURING THE IT FUNCTION
Segregation of incompatible IT functions
Alternative 1: segregate systems analysis from
programming
Two types of control problems from this approach:
Inadequate documentation
Is a chronic problem. Why?
Not interesting
Lack of documentation provides job security
Assistance: Use of CASE tools
Potential for fraud
Example: Salami slicing, trap doors
6
STRUCTURING THE IT FUNCTION
Segregation of incompatible IT functions
Segregate data library from operations
Physical security of off-line data files
Implications of modern systems on use of data
library:
Real-time/online vs. batch processing
Volume of tape files is insufficient to justify full-time
librarian
Alternative: rotate on ad hoc basis
Custody of on site data backups
Custody of original commercial software and licenses
7
STRUCTURING THE IT FUNCTION
Segregation of incompatible IT functions
Audit procedures:
Obtain and review security policy
Verify policy is communicated
Review relevant documentation (org. chart, mission
statement, key job descriptions)
Review systems documentation and maintenance
records (using a sample)
Verify whether maintenance programmers are also
original design programmers
Observe segregation policies in practice
Review operations room access log
Review user rights and privileges
8
Computing Models
Centralized Processing
Client Server Processing
Distributed Computing
thin or fat clients
2 to n tiered
using idle processing time
Distributed Database Computing
replicated or divided
9
STRUCTURING THE IT FUNCTION
The distributed model
Risks associated with DDP
Inefficient use of resources
Mismanagement of resources by end users
Hardware and software incompatibility
Redundant tasks
Destruction of audit trails
Inadequate segregation of duties
Hiring qualified professionals
Increased potential for errors
Programming errors and system failures
Lack of standards
10
STRUCTURING THE IT FUNCTION
The distributed model
Advantages of DDP
Cost reduction
End user data entry vs. data control group
Application complexity reduced
Development and maintenance costs reduced
Improved cost control responsibility
IT critical to success then managers must
control the technologies
Improved user satisfaction
Increased morale and productivity
Backup flexibility
Excess capacity for DRP
11
STRUCTURING THE IT FUNCTION
Controlling the DDP environment
Audit objectives:
Conduct a risk assessment
Verify the distributed IT units employ
entity-wide standards of performance that
promotes compatibility among hardware,
operating software, applications, and data
12
STRUCTURING THE IT FUNCTION
Controlling the DDP environment
Audit procedures:
Verify corporate policies and standards are
communicated
Review current organization chart, mission
statement, key job descriptions to determine if any
incompatible duties exist
Verify compensating controls are in place where
incompatible duties do exist
Review systems documentation
Verify access controls are properly established
13
THE COMPUTER CENTER
Computer center controls
Physical location
Avoid human-made and natural hazards
Example: Chicago Board of Trade
Construction
Ideally: single-story, underground utilities,
windowless, use of filters
If multi-storied building, use top floor (away from
traffic flows, and potential flooding in a basement)
Access
Physical: Locked doors, cameras
Manual: Access log of visitors
14
THE COMPUTER CENTER
Computer center controls
Air conditioning
Especially mainframes
Amount of heat even from a group of PCs
Fire suppression
Automatic: usually sprinklers
Gas, such as halon, that will smother fire by
removing oxygen can also kill anybody trapped there
Sprinklers and certain chemicals can destroy the
computers and equipment
Manual methods
Power supply
Need for clean power, at a acceptable level
Uninterrupted power supply
15
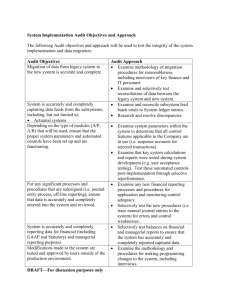
THE COMPUTER CENTER
Computer center controls
Audit objectives
Verify physical security controls are reasonable
Verify insurance coverage is adequate
Verify operator documentation is adequate in case
of failure
Audit procedures
Tests of physical construction
Tests of fire detection
Tests of access control
Tests of backup power supply
Tests for insurance coverage
Tests of operator documentation controls
16
PC SYSTEMS
Control environment for PCs
Controls
Risk assessment
Inherent weaknesses
Weak access control
Inadequate segregation of duties
Multilevel password control – multifaceted access
control
Risk of physical loss
Laptops, etc. can “walk off”
Risk of data loss
Easy for multiple users to access data
End user can steal, destroy, manipulate
Inadequate backup procedures
Local backups on appropriate medium
Dual hard drives on PC
External/removable hard drive on PC
17
PC SYSTEMS
Control environment for PCs
Risk associated with virus infection
Policy of obtaining software
Policy for use of anti-virus software
Verify no unauthorized software on PCs
Risk of improper SDLC procedures
Use of commercial software
Formal software selection procedures
18
PC SYSTEMS
PC systems audit
Audit objectives
Verify controls are in place to protect data,
programs, and computers from unauthorized
access, manipulation, destruction, and theft
Verify that adequate supervision and operating
procedures exist to compensate for lack of
segregation between the duties of users,
programmers, and operators
Verify that backup procedures are in place to
prevent data and program loss due to system
failures, errors
Verify that systems selection and acquisition
procedures produce applications that are high
quality, and protected from unauthorized changes
Verify the system is free from viruses and
adequately protected to minimize the risk of
becoming infected with a virus or similar object
19
FIGURE 2.8 – Password Policy
Proper Dissemination – Promote it, use it during employee training or orientation, and find
ways to continue to raise awareness within the organization.
Proper Length: Use at least 8 characters. The more characters, the more difficult to guess
or crack. Eight characters is an effective length to prevent guessing, if combined with below.
Proper Strength: Use alphabet (letters), numbers (at least 1), and special characters (at
least 1). The more non-alpha, the harder to guess or crack. Make them case sensitive and
mix upper and lower case. A “Strong” password for any critical access or key user.
Password CANNOT contain a real word in the content.
Proper Access Levels or Complexity: Use multiple levels of access requiring multiple
passwords. Use a password matrix of data to grant read-only, read/write, or no access per
data field per user. Use biometrics {such as fingerprints, voice prints}. Use supplemental
access devices, such as smart cards, or beeper passwords in conjunction with remote logins.
Use user-defined procedures.
Proper Timely Changes: At regular intervals, make employees change their passwords.
Proper Protection: Prohibit the sharing of passwords or “post-its” with passwords located
near one’s computer.
Proper Deletion: Require the immediate deletion of accounts for terminated employees, to
prevent an employee from being able to perpetrate adverse activities.
SYSTEM-WIDE CONTROLS
E-mail risks
Spoofing
Spamming
Hoax virus warnings
Flaming
Malicious attachments (e.g., viruses)
Phishing
Pharming
21
SYSTEM-WIDE CONTROLS
Malicious objects risk
Virus
Worm
Logic bomb
Back door / trap door
Trojan horse
Potential control procedures
Audit objective
Audit procedures
22
SYSTEM-WIDE CONTROLS
Controlling electronic audit trails
Keystroke monitoring (keystroke log)
Event monitoring (key events log)
Audit trail objectives
Detecting unauthorized access
Reconstructing events
Personal accountability
Implementing an audit trail
Transaction logs
23
SYSTEM-WIDE CONTROLS
Disaster recovery planning
Critical applications identified and
ranked
Create a disaster recovery team
with responsibilities
24
SYSTEM-WIDE CONTROLS
Disaster recovery planning
Site backup
“Hot site” – Recovery Operations
Center
“Cold site” – empty shell
Mutual aid pact
Internally provided backup
Other options
25
Disaster Recovery Plan
1.
2.
3.
4.
5.
6.
7.
8.
9.
10.
Critical Applications – Rank critical applications so an orderly and effective restoration of
computer systems is possible.
Create Disaster Recovery Team – Select team members, write job descriptions, describe recovery
process in terms of who does what.
Site Backup – a backup site facility including appropriate furniture, housing, computers, and
telecommunications. Another valid option is a mutual aid pact where a similar business or branch of
same company swap availability when needed.
Hardware Backup – Some vendors provide computers with their site – known as a hot site or
Recovery Operations Center. Some do not provide hardware – known as a cold site. When not
available, make sure plan accommodates compatible hardware (e.g., ability to lease computers).
System Software Backup – Some hot sites provide the operating system. If not included in the site
plan, make sure copies are available at the backup site.
Application Software Backup – Make sure copies of critical applications are available at the
backup site
Data Backup – One key strategy in backups is to store copies of data backups away from the
business campus, preferably several miles away or at the backup site. Another key is to test the
restore function of data backups before a crisis.
Supplies – A modicum inventory of supplies should be at the backup site or be able to be delivered
quickly.
Documentation – An adequate set of copies of user and system documentation.
TEST! – The most important element of an effective Disaster Recovery Plan is to test it before a
crisis occurs, and to test it periodically (e.g., once a year).
SYSTEM-WIDE CONTROLS
Disaster recovery planning
Audit objectives
Verify management’s DRP is adequate
Audit procedures
Verify a second-site backup is adequate
Review the critical application list for
completeness
Verify backups of application software are stored
off-site
Verify that critical data files are backed up and
readily accessible to DRP team
Verify resources of supplies, documents, and
documentation are backed up and stored off-site
Verify that members listed on the team roster are
current employees and that they are aware of their
responsibilities
27
SYSTEM-WIDE CONTROLS
Fault tolerance
Definition
44% of IS down-time attributable to system failures!
Controls
Redundant systems or parts
RAID
UPS
Multiprocessors
Audit objective
To ensure the organization is employing an
appropriate level of fault tolerance
Audit procedures
Verify proper level of RAID devices
Review procedures for recovery from system failure
Verify boot disks are secured
28
Client Server Systems
29
Firewalls
30
Proxy Servers
31
Demilitarized Zone
32
Chapter 2:
Computer Operations
Excerpts from …
An Introduction to Computer Auditing
(online reading)
34
Computer Auditing
Examples of Computer Abuse
Unauthorized disclosure of confidential
information
Unavailability of key IT systems
Unauthorized modification of IT systems
Theft of IT hardware and software
Theft of IT data files
Use of IT resources for personal use
35
Problems with Computer
Auditing
Technology continually evolves
IT can be a black box and attacks may not be
apparent
Auditors lack of IT skills
Data can be difficult to access
Computer logs and audit trails may be incomplete
On-line real time systems can support frauds that
occur rapidly without sufficient time to react
Electronic evidence is volatile
36
Systems Development
Use of project management
Use of methodology such as SDLC, RAD
Steering Committee
Continuous monitoring of progress
(milestones)
Prototyping
37
IT Application Controls
Input Controls: all data entered is authorized,
complete, accurate, and entered only once
Processing Controls: transactions are
processed completely, accurately, and in a
timely manner
Output Controls: results are communicated to
the authorized persons in a timely and
efficient manner
38
General Controls
Identification, prioritization and development
of new systems and modification of existing
systems
Ongoing operations and maintenance
Physical access
Access rights and privileges
Change management control
Segregation of incompatible duties
Contingency planning
39
The basic principles of good
project management are:
clearly defined management responsibility
clear objectives and scope
effective planning and control
clear lines of accountability
steering committee oversight
milestones
40
good project management
(cont.)
end-user involvement
methodology such as SDLC or RAD
possible use of prototypes
possible use of phased development
41
Be sure to read the entire article!
42