System Implementation Audit Approach
advertisement

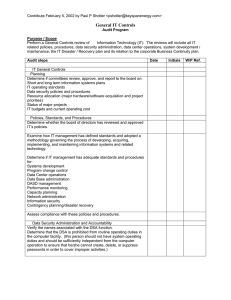
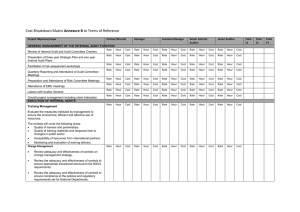
System Implementation Audit Objectives and Approach The following Audit objectives and approach will be used to test the integrity of the system implementation and data migration: Audit Objectives Migration of data from legacy system to the new system is accurate and complete. System is accurately and completely capturing data feeds from the subsystems, including, but not limited to: Actuarial systems Depending on the type of modules (A/P, A/R) that will be used, ensure that the proper system parameters and automated controls have been set up and are functioning. Audit Approach Examine methodology of migration procedures for reasonableness, including interviews of key finance and IT personnel. Examine and selectively test reconciliation of data between the legacy system and new system. Examine and reconcile subsystem feed batch totals to System ledger entries. Research and resolve discrepancies. For any significant processes and procedures that are redesigned (i.e. journal entry process, off-line reporting), ensure that data is accurately and completely entered into the system and reviewed. System is accurately and completely reporting data for financial (including GAAP and Statutory) and managerial reporting purposes. Modifications made to the system are tested and approved by users outside of the production environment. DRAFT—For discussion purposes only Examine system parameters within the system to determine that all control features applicable to the Company are in use (i.e. suspense accounts for rejected transactions). Examine that key system calculations and reports were tested during system development (e.g. user acceptance testing). Test these automated controls post-implementation through selective reperformance. Examine any new financial reporting processes and procedures for application and monitoring control adequacy. Selectively test the new procedures (i.e. trace manual journal entries to the system) for errors and control weaknesses. Selectively test balances on financial and managerial reports to ensure that the system has accurately and completely reported captured data. Examine the methodology and procedures for making programming changes to the system, including interviews. Segregation of duties exists (i.e. programmers cannot make changes directly to the production environment) within the system’s environment. Logical and access security over the system, including user access administration, is well controlled and monitored to ensure data integrity and segregation of duties within Finance. The system has appropriate job scheduling and batch processing set up and change controls. Backup and Disaster Recovery procedures have been formalized, documented, and tested. Finance staff are adequately trained and the level of reference documentation exists to support efficient use of the system. IT staff are adequately trained in maintaining and supporting the system. DRAFT—For discussion purposes only Review of documentation of all changes made to the system to ensure approval and testing. Examine the methodology and procedures for making programming changes to the system. Review of change and approval procedures, including interviews. Select several changes post-conversion to ensure change control procedures are operating effectively. Examine the security features over the system, depending on how the database is accessed (Internet, Intranet, etc) and the security administration process. Select several system users to ensure the level of access is commensurate with their duties and proper segregation exists. Examine system administrator IDs to ensure proper segregation of duties and ID activity is being logged and monitored. Examine job scheduling and batch processing controls for appropriateness. Changes to the job schedule are processed through a formal change control program. Examine backup and Disaster Recovery procedures for adequacy. Examine results of backup and disaster recovery testing. Interview key Finance personnel to determine adequacy of system skills/knowledge. Review relevant system reference and training material to ensure adequacy. Interview Finance and IT staff to determine the level of system support required and its adequacy.