NetLab 3
advertisement

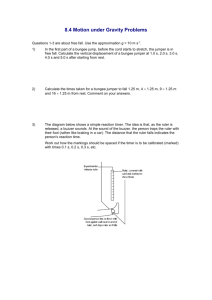
CECS 474 COMPUTER NETWORKING INTEROPERABILITY Netlab 3: Local Area Networks, ARP & Port Security Purpose: As discussed in class, every computer needs a unique address to identify itself to a network. In fact, for every network to which a computer connects, two types of address are necessary: 1. A unique IP address must be assigned to each device in the network. IP addresses are Network layer (Layer 3) virtual (software) addresses. These addresses can be assigned dynamically or statically. If the host changes networks, the IP address will also need to change. IP address blocks are assigned to ISP’s (Internet Service Providers) in a hierarchical fashion so that routing can be simplified. 2. Every network adapter on a host has a unique Media Control Access (MAC) address. The MAC address corresponds to the Link Layer (layer 2). MAC addresses are permanently assigned to a network adapter and never change, even if the host device changes networks. The purpose of this NetLab exercise is to help you understand why there are two unique addresses assigned to every device in a network. This lab will take a deeper look at LANs (Local Area Networks) and the translation between IP and MAC addresses. ). In particular, we will examine on the workings of the ARP (Address Resolution Protocol) [RFC 826]. In addition, at the end of this Lab, we explore one useful and simple way to add security to your LAN by securing ports in a managed switch. This will serve as an introduction to the managed network switches we will focus on in NetLab 4. Background: When discussing the different addresses in a LAN it is important to have a clear understanding of what each one is used for. To illustrate the difference, let’s use a simple metaphor. If you can, imagine a host machine as a person, and the LAN as a geographical location in the U.S. such as a house in Montana, or a skyscraper in New York. In this scenario, an IP address can be considered someone’s Postal Address. As long as the person stays in the same house, the Postal Address typically stays the same. However, if the person moves to a new location, then a new Postal Address is required to get in contact with that person. It doesn’t matter if the person moves one block away or to the other side of the country. A new address will be assigned either way. A host machine in a network will behave in much the same way. It doesn’t matter if the host (e.g., laptop, tablet, or smartphone) moves from the school’s library to the College of Engineering or from school to home, the mobile device will receive a new IP address in each network in joins. Continuing the analogy, a MAC address is more like a person’s Social Security number. It does not matter which part of the country a person moves to, they keep the same Social Security number for life. The ARP is considered a TCP/IP Support Protocol. ARP is used to match a Layer 3 IP address to a Layer 2 MAC address. We say that ARP resolves the IP Address. It does this using two primary functions: Request and Response. Request is used to obtain the MAC address Corresponding to a given IP address. Response is used to answer the requests received from other interfaces in the network. Switches are the primary interconnection devices used in LANs. With manageable switches, you have the ability to perform several Layer 2 functions such as Virtual LANs, MAC address security, Quality of Service (QoS) and Power over Ethernet (PoE). They are traditionally managed via terminal (typically serial) connections and most late model switches include a web-based GUI. Switches are Layer 2 meaning that they can only communicate within the LAN since routing cannot be done. They typically interconnect through a network backbone. The gateway (typically a firewall) is the only Dr. Tracy Bradley Maples (Fall 2013) Lab Design: Rogelio Cruz (mod. 10/5/13) CECS 474 COMPUTER NETWORKING INTEROPERABILITY router present in a LAN, but several switches can exist in a LAN. For SOHOs (Small Office Home Office), there is usually a hybrid device (i.e., your home router) that acts as a gateway router, LAN switch, and WLAN Access Point. NOTE: A router operating at Layer 3 does not propagate Ethernet broadcasts. ARP is used at Layer 2 in devices like switches. Prerequisites: For this and several other future labs the information that you will gather below will be useful and required to complete the assignment. Make note of the workstations in your GROUP because it will remain the same for several labs in the future. Pre-lab Setup: The following information will help you start the Wireshark capture for this exercise. o Make sure you are connected to the Big Apple COE LAN. o Notice that your workstation is labeled with both Workstation (netlabXX) and a Group (A, B, C, D or E). Your Group will be required for several labs (including this one). Be sure to use the appropriate Group. My Workstation is: _________________________________________________________ My Group is: ______________________________________________________________ o Next, launch a command prompt window and run an ipconfig /all. Look for the Ethernet adapter’s physical address. It appears in the following format (AA-AA-AA-AA-AA-11) comprised of a combination of letters and numbers (hexadecimal values). Also look for the IP address assigned to your workstation. Make note of them below. Workstation MAC Address: ___________________________________________________ Workstation IP Address: _____________________________________________________ o Next, find the two other workstations in NetLab that share your Group. Locate them and exchange only IP address information (Important). Write down the information below. IP Address of another Workstation in my Group: __________________________________ IP Address of another Workstation in my Group: __________________________________ o Finally, look at the Green Rack. Find the managed switch labeled with your Group. Write down the IP address of the corresponding switch. IP Address for my Group managed switch: ______________________________________ Exercises: Address Resolution Protocol IP to MAC Addresses translation: First the source host (say Host1) wants to resolve (or map or bind) a destination host’s (Host2) 32-bit IP address to a 48-bit MAC address. It checks its ARP Cache, which is stores previously used mappings in a table to see if it already has mapped a path to that address. If the IP address is found in the ARP Cache, the corresponding MAC address becomes the Destination Address in the frame and is sent. Dr. Tracy Bradley Maples (Fall 2013) Lab Design: Rogelio Cruz (mod. 10/5/13) CECS 474 COMPUTER NETWORKING INTEROPERABILITY If the IP address is not found in the ARP Cache, a broadcast message is sent with Host2’s IP address. The broadcast reaches every physical host on the LAN. The broadcast makes the request: “If you have IP address xxx.xxx.xxx.xxx? Let me know your MAC address.” Then Host1 waits for a response. The broadcast is a special frame that sends to every host in the network. Recall that all broadcast frames must be processed by the network interface (Comer, Chapter 13). Thus, each host must check whether the requested IP address in the broadcast matches its own IP address. When Host2 receives and processes the broadcast, it finds that requested IP address matches its own and returns its MAC address as a reply message to Host1. When any other host receives and processes the broadcast, the IP address does not match and the frame is discarded. After the exchange both Host1 and Host2 store each other’s IP-to-MAC binding (or mapping) into their ARP caches for future use. NOTE: There are two types of entries in the ARP Cache: static and dynamic. Most ARP entries are dynamic. Your network adds static entries automatically that correspond to known network entities, such as, your subnet mask, your gateway, etc. Procedure: 1. Launch a command prompt window with elevated privileges. To do so, right click on the desktop icon and choose “Run as Administrator”. 2. Launch Wireshark and after checking settings start the capture. 3. Once the capture is initiated, flush the existing table in the ARP Cache using the following command: arp –d 4. Now that the ARP Cache is empty, run the following command: arp -a 5. ping each of the other two members of your Group. 6. Do an arp –a once again to display your updated ARP Cache entries. Do not close this window yet. (Some additional questions will be asked about it later in the lab.) 7. Stop the Wireshark Capture. 8. Refine your capture by using “arp” in the filter. Answer the follow questions about ARP: How big is the MAC address space? The IPv4 space? After the ARP Cache is flushed, and you run the arp –a command, what entries appear in the table? What does that entry correspond to? For the first broadcast message, look at the info column on the message list. a. Examine the header details. What is the destination’s address? Who does that address belong to? Explain. Dr. Tracy Bradley Maples (Fall 2013) Lab Design: Rogelio Cruz (mod. 10/5/13) CECS 474 COMPUTER NETWORKING INTEROPERABILITY b. In the “info” column of the message list, what information is your workstation asking for? (Who is it looking for?) c. Why is it looking for that IP address? (HINT: DHCP server) d. The above ARP query is sent within a broadcast frame, explain why. Look for the ARP reply message to the broadcast request. a. What message does the destination reply with? b. Why is an ARP response sent within a frame with a specific destination MAC address? Now look for any other broadcasts in your capture. What triggered these inquiries? (HINT: If it is unclear, remove the “arp” filter and follow the entire capture.) Explain. On the last arp –a, what information has been added to the ARP Cache? How was it added? Explain. Exercises: Managed Switch Port security using MAC Addresses (MAC Filtering): If you have a manageable switch on your network, one useful thing you can do is to add security to your LAN by allowing only specific MAC addresses through ports. This ensures that if someone tries to connect a foreign machine to an open or exposed Ethernet port, it will not gain access to your network. Before you get started, please note that this section requires you to connect and move connections on the Green Rack. Please take extra care when removing patches from one switch to another and make sure you return the connections to their original location after you finish. Connecting to a managed switch in the Big Apple LAN via web GUI: First, go to the Green Rack and find the patch panel, located at the bottom part of the rack. Think of this patch panel as a jumper from your workstation to the rack. You will notice that each number on that patch panel corresponds to the number of your workstation. For further convenience, the same port number is matched on the core switch. For example, Netlab13 corresponds to Port 13 on both the GREEN RACK patch panel and the core switch. Now take a look at the five managed switches directly above the core switch. Each of these has a Group identifier on them. For the following section, you will need to physically connect from the green patch panel with your workstation’s corresponding port number to any of the available ports on the managed switch. You can use ports 1-8 on the smaller switches and ports 1-12 on the larger ones. Make sure you disconnect the green patch cable that connects the core switch to the patch panel from the patch panel side. Leave the core switch connected with the patch cable. Use a patch from the cable drawers to connect from the patch panel to the corresponding managed switch. Procedure: 1. Refer to the pre-lab setup section to recall the managed switch IP address for your Group. 2. Verify that you are properly setup by pinging the managed switch first, then ping the server. Dr. Tracy Bradley Maples (Fall 2013) Lab Design: Rogelio Cruz (mod. 10/5/13) CECS 474 COMPUTER NETWORKING INTEROPERABILITY 3. Next open up your web browser and type in your switch’s IP address. This will open up the web GUI. The first thing that appears is the status page with the active ports and the status log. For now make sure that the port number that you connected to is lit up (green). 4. There are several tabs in the management interface, but for now we are only interested in two: the Configuration and Security Tabs. (We will explore the interface further in the next assignment.) 5. Let’s begin by configuring the port you are using first. Go to the Configuration tab and select the “Port Configuration” sub-tab. 6. Look for the port you are connected to in the list and double click it. This will take you to the port configuration page. 7. Configure your ports with the following information: Port name (your workstation name), Port Enabled, 100FDx, Flow Control Off. a. Port Name: Use your workstation name. This will help you keep track of the port you are using. b. Port Enabled: Yes. c. Mode: This allows you to manually specify the speed of the port. For some older equipment, you need to either slow down the port or even specify a half speed for it to work. Here are the options: i. Auto: This option auto-negotiates the connection between the switch and the workstation. ii. 10HDx or 100HDx: This specifies that you want to run on either 10Mbps or 100Mbps on half duplex. This specifies bidirectional traffic, but a user my only send or receive at any given moment. This is not recommended with most current applications, unless you like getting collisions. iii. 10FDx or 100FDx: This specifies that you want to run on either 10Mbps or 100Mbps on full duplex. Sometimes there are also 1000FDx settings for gigabit ports. d. Flow Control: This feature allows you to keep a “consistent flow” on this port. This is both good and bad depending on your perspective. Consistent flow means that when your flow is going too slow, it bumps up its speed by taking some of its neighboring ports’ resources. Unfortunately, when your flow is going “too fast” it throttles back the connection. This is a trial and error setting type of setting. Some people love it, some people hate it. 8. There are additional options available in some switches, but just leave them at the default settings. (Note: You can experiment with other settings but you may not notice a difference without a “heavy” traffic load from an application like flash or VOIP. Pings and http requests will not experience a delay difference in this small, lightly loaded LAN environment.) 9. Now that the port has been configured, we’ll move to securing it. Go to the Security tab. Please leave the device username and password as is (blank). 10. Navigate to the “Port Security” sub-tab. Dr. Tracy Bradley Maples (Fall 2013) Lab Design: Rogelio Cruz (mod. 10/5/13) CECS 474 COMPUTER NETWORKING INTEROPERABILITY 11. Select the port number that you are connected to by double clicking on it. At this point you should also be able to see your workstation’s name. This should bring up the Configuration Page for the port. Here is a quick description of the options on this page. There are three options on this page: Learn Mode, Address Limit, and Violation Action. a. Learn Mode i. Continuous: Does not apply any MAC address filtering (default). ii. Static: This combined with Address Limit automatically detects the number of allowed devices and saves their MAC address. iii. Configured: This allows you to manually configure the MAC address(es) that can access the port. b. Address Limit i. As the name implies, this allows you to set the number of allowed addresses. This option is only useful in either static or configured modes. c. Violation Action i. Send Trap: This means that if a device who’s MAC address does not match is connected to this port, the switch will send out a “Trap” or an email to a specified SMTP server to notify the administrator that there is a violation. ii. Send Trap and Disable: This option additionally disables the port. 12. For our use we will choose: configured >> Address Limit: 1 >> Violation Action: None 13. After configuration, swap connections with one of the workstations next to you. Do this swap using the patch cable that connects your workstation to the ports on the wall (where the red, green, and yellow ports are). Try to ping the server and the core switch. 14. Finally, swap the patches back to your port. (Again from the patch that connects your workstation to the wall receptacle). 15. Now on the switch GUI, navigate to the status tab. 16. The last step is to return the LAN connection to its original state by removing the path cable from the managed switch and the patch panel and re-connecting the green patch coming from the core switch. Answer the follow questions about managed switches: After the patch cables were swapped with your neighbors were you able to ping successfully? Explain. Describe the difference between 10BASE-T, 100BASE-T and Gigabit Ethernet in terms of effective bandwidth? Explain how to secure the ports in your switch if you do not have a list of all the MAC addresses in your network. When would it be practical to secure the ports in your network? Dr. Tracy Bradley Maples (Fall 2013) Lab Design: Rogelio Cruz (mod. 10/5/13)