Practice Final Exam Key - Cisco Networking Academy
advertisement

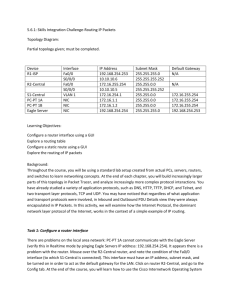
CCNA Discovery 2: Practice Final Exam Key This practice exam is not meant to be a comprehensive study guide. It is meant to give you indication of what type of questions to expect on the test. You should study your chapter quizzes and chapter review sheets as well. 1) Which is NOT true concerning the ping utility? a) It uses the icmp protocol to send echo request/ echo reply packets b) Icmp measures the time between when the echo requests are sent the echo replies are received c) Icmp guarantees datagram delivery (the network layer does not guarantee delivery that is the transport layer) d) Icmp verifies layer 3 connectivity 2) Which is NOT true when using the tracert command? a) The output displays all the inbound and outbound router interfaces that the packet passes through (it only shows the router interfaces that it enters, not exits) b) The output displays the path that a packet takes from the source to the destination host c) The output displays the time between when the packet is sent and when a reply is received from the router at each hop d) The output displays each of the ISP organizations that the packet must pass through from source to destination 3) A small company has a few mobile employees who must connect to the company network from different client sites. Which ISP connection type would be the best option for them? a) Cable b) Dialup Access c) DSL (faster than dialup, more appropriate for multiple employees, doesn’t require special installation) d) T1 4) Host A has multiple paths to the web server. Based on the output of the tracert command, which path was used to reach the destination? a) A, B, D, F b) A, D, G, F c) A, C, G, F d) A, B, E, F 5) Using a Divide and Conquer Troubleshooting method, a help desk technician suspects a problem at Layer 3 of the OSI model. Which question could be asked to isolate the problem to layer 3? a) Can you ping your default gateway? (ping tests layer 3 connectivity) b) Can you browse to www.isp.com? c) Is your network cable plugged in? d) Is there a link light on your NIC? 6) A client is having trouble checking their email. The help-desk technician is using a bottom-up approach to troubleshooting. Which would be the first question he/she should ask? a) What is the IP Address on your PC? b) Is your Windows firewall blocking port 25? c) Is you network cable securely connected? (start at the physical layer with basic connectivity) d) Do you see a link light on your NIC? 7) An ISP client can’t reach the web server at www.cisco.com. If the technician is using a top-down approach, which action should they perform first? a) Check the network cable connection b) Use the tracert command to identify any faulty routers along the path c) Use the ipconfig command to verify the IP address, subnet mask and default gateway on the host d) Enter an IP address in the browser’s address bar to determine if DNS has failed (start at the top with application functionality) 8) Which scenario is NOT a common cause of physical network connectivity problems at Layer 1? a) Faulty network cable b) Incorrect drivers installed for NIC (faulty NIC drivers are a layer 2 issue) c) Network cable plugged into wrong port d) Incorrectly terminated network cable 9) A client can’t reach the web server at www.cisco.com. Based on the output of the Technician’s troubleshooting commands, what can be determined about the problem? a) There is a problem with the web server software at the web-s1.cisco.com site b) A router is down between the source host and the web server c) There is an IP addressing conflict d) There is a DNS error (they can ping the IP address, but not the host name, so it’s a DNS host name resolution error) 10) What does a successful ping response from the 127.0.0.1 loopback address on a host indicate? a) The default gateway is configured correctly b) The DNS server is correctly configured c) The DHCP configuration loaded correctly d) The TCP/IP protocol stack loaded correctly (indicates that tcp/ip is working properly) 11) Which range of addresses could be used with NAT to provide private addressing on an internal LAN? a) 127.0.0.0 /16 b) 169.254.0.0 /16 c) 245.10.0.0 /24 d) 172.16.0.0 /16 (the only one here that is used for private addresses) 12) Which Subnet Scheme allows for 6 subnets with up to 30 hosts per subnet? a) 10.1.1.64 255.255.255.224 (.224 indicates 3 bits borrowed, which creates 3 usable subnets, 30 hosts each) b) 10.1.1.64 255.255.255.248 c) 10.1.1.64 255.255.255.240 d) 10.1.1.64 255.255.255.192 13) What type of address is 192.168.10.63 /27? a) A valid host address b) A broadcast address (/27 indicates 3 bits borrowed, so subnets increase by 32’s, so .63 is a broadcast address) c) A subnet address d) A multicast address 14) What type of address is 192.168.10.48 /28? a) A valid host address b) A broadcast address c) A subnet address (/28 indicates 4 bits borrowed, so subnets increase by 16’s, so .48 is a subnet address) d) A multicast address 15) What type of address is 192.168.10.96 /26? a) A valid host address (/26 indicates 2 bits borrowed, so subnets increase by 64’s, so .96 is a host address) b) A broadcast address c) A subnet address d) A multicast address 16) A network administrator has designed the class B network 172.16.0.0 with the Subnet Mask: 255.255.255.0. Which is NOT true? a) There are 128 subnets (8 bits borrowed, so there are 254 usable subnets) b) There are 254 usable subnets c) There are 254 usable host addresses per subnet d) 172.16.1.0 is a valid subnet address 17) The network 192.168.10.0 /24 needs to be subnetted. Which subnet mask will satisfy the required number of hosts for all of the subnets? a) 255.255.255.224 b) 255.255.255.192 (need 32 hosts per subnet, so only 2 bits can be borrowed) c) 255.255.255.240 d) 255.255.255.248 18) Which does NOT describe Horizontal cable? 32 hosts a) It terminates at a face plate in the user’s work area b) It terminates at a patch panel in the MDF or IDF c) It is most commonly UTP cable d) It connects 2 networking devices located in different IDFs (this refers to backbone cable) 19) Which does NOT describe Backbone Cable? a) It connects networking devices in the MDF to networking devices in the IDF b) It can’t exceed a length of 100 meters (this refers to UTP cable and backbone cable is usually fiber optic) c) It is also called vertical cable d) It is most commonly fiber optic cable 20) Which is NOT true about DNS? a) It relies on a hierarchy of decentralized servers b) The root servers maintain records about how to reach top-level domain servers c) When resolving DNS names, a DNS server caches the host name mappings it receives in reply to its queries d) All DNS servers maintain records about how to reach the entire DNS structure (they only maintain records about how to reach the server in the zone above them or their own zone) 21) Why does it take longer to transmit a file with an application that uses TCP (ftp), rather than one that used UDP (tftp)? a) UDP doesn’t need to add a header to the data packet b) The TCP verification/acknowledgement process adds more transmissions to the file transfer process c) UDP uses more techniques to provide reliable transfer of data (udp is unreliable) d) The UDP verification process is faster than that used by TCP 22) Communication is needed between the LANS on Sterling and Waycross. The hosts on these LANS also need connectivity to the Internet. Which set of commands will allow this network to operate properly? 172.16.2.1 /24 S0 Fa 0/0 172.16.1.1 /24 a) S2 S1 172.16.2.2 /24 172.32.1.1 /24 S0 172.16.4.2 /24 Sterling(config)# router rip Sterling(config)# network 172.16.1.0 Sterling(config)# network 172.16.2.0 172.16.4.1 /24 S1 Fa 0/0 172.16.5.1 /24 Waycross (config)# router rip Waycross(config)# network 172.16.4.0 Waycross(config)# network 172.16.5.0 Hoboken(config)# router rip Hoboken(config)# network 172.16.2.0 Hoboken(config)# network 172.16.4.0 b) Sterling(config)# ip route 172.16.5.0 255.255.255.0 S0 Waycross (config)# ip route 172.16.1.0 255.255.255.0 S1 c) Sterling (config)# ip route 0.0.0.0 0.0.0.0 S0 Waycross (config)# ip route 0.0.0.0 0.0.0.0 S1 Hoboken(config)# ip route 0.0.0.0 0.0.0.0 S2 d) Sterling(config)# ip route 172.16.5.0 255.255.255.0 S0 Waycross (config)# ip route 172.16.1.0 255.255.255.0 S1 Sterling (config)# ip route 0.0.0.0 0.0.0.0 S0 Waycross (config)# ip route 0.0.0.0 0.0.0.0 S1 Hoboken(config)# ip route 0.0.0.0 0.0.0.0 S2 (stering and waycross need static routes to reach each other’s LANS, they also need a default route to send all Internet packets to Hoboken, Hoboken needs a default route to send Internet packets to the internet) 23) A customer reports that all of their network applications are working, except for FTP. What could be the problem? a) A misconfigured firewall (if other apps are working, the firewall is probably blocking a port that ftp needs to have open) b) A bad port on the switch or hub c) A misconfigured IP address on the client’s computer d) An incorrect DNS server configured on the client’s computer 24) Which is NOT a characteristic of UDP? a) It adds a minimal amount of overhead to the data to be delivered b) It is an unreliable, connectionless transport protocol c) It requires acknowledgement of data packets received (udp has no reliability or acknowledgement) d) It is used by applications that can tolerate small amounts of missing data 25) Which best describes a reverse DNS lookup zone? a) It resolves a fully qualified domain name to an IP address b) It is the zone in which the resource records on a DNS server can be modified c) It acts as a backup for the primary lookup zone d) It resolves an IP address to a fully qualified domain name 26) Which is NOT a characteristic of TCP? a) It is a connection-oriented transport protocol b) It operates at the Internet Layer of the TCP/IP model (operates at the transport layer of TCP/IP) c) Provides reliable, guaranteed-delivery of data from end to end d) Each data segment sent with TCP requires more overhead to be added to the header 27) Which best describes a primary DNS lookup zone? a) It resolves a fully qualified domain name to an IP address (forward DNS lookup zone) b) It is the zone in which the resource records on a DNS server can be modified c) It acts as a backup for the forward lookup zone (secondary DNS lookup zone) d) It resolves an IP address to a fully qualified domain name (reverse DNS lookup zone) 28) A client is able to reach a server by pinging with the command ping 200.10.2.5, but not by pinging with the command ping www.myserver.com. What should be checked on their workstation? a) The DNS configuration on the client’s computer b) The IP address on the client’s computer c) The driver for the NIC on the client’s computer d) The default gateway on the client’s computer 29) Which is NOT true about the socket pair shown here? a) The Destination Port is identified by TCP Port 80 on the server b) The data conversation was started by an ftp application on the client c) The Internet server will send data to source port 2153 on the client d) The IP address of the Internet server is 200.10.10.2 192.168.1.10: 2153 , 200.10.0.2: 20 30) What is the purpose of an SLA provided by an ISP to a customer? a) It identifies the range of services provided by the ISP b) It provides a breakdown of the costs of the services provided by the ISP c) It outlines the management, monitoring and maintenance of the network that the ISP will provide to the customer d) It outlines the customer’s responsibilities in maintaining the network 31) Which is NOT true concerning the FTP protocol? a) It requires 2 separate connections to exist between the client and server b) The data transfer connection uses destination port 20 c) The Protocol Interpreter (PI) connection is the main control connection between the FTP client and server d) Both connections stay open until closed by the user (the control connection closes automatically when commands are done transferring) 32) Which is NOT true concerning an FTP passive data connection? a) ISPs typically don’t support passive data connections to their FTP servers because the firewall will block connection requests from an external server (ISPs usually only support passive connections because they don’t require an external request to be sent into the network- the host must initiate the connection) b) The server forwards its IP address and a random source port to the FTP client so the client can initiate a connection c) The CLIENT initiates the Data-Transfer Connection d) The client forwards data to destination port 20 on the server 33) Which statement does NOT describe the use of a proxy server? a) It can be used to filter unsuitable web content b) It allows clients to make a direct network connection to other network services (they connect indirectly through the proxy server) c) It can increase network speed by caching requested web pages d) It can increase network security by intercepting viruses before they are forwarded to internal clients 34) Which best describes the TCP 3-Way handshake? a) It is an information exchange used by the source and destination hosts in order to set up a connection b) It is used to identify each data segment with sequence numbers so the destination can determine if all data was received c) It is the process used to divide data into segments, and pass them to the Internet Layer, which places each one into a packet for transmission d) It is the process used to ensure that the destination host acknowledges all transmitted data packets, so that the source can re-transmit any not received 35) Which is NOT a characteristic of EIGRP? a) Can use many different metrics, like bandwidth and delay, to make best path decisions b) It builds a topology table based on advertisements from its neighbors c) It maintains a full database and tree topology of distant routers and how they interconnect (only link-state protocols like OSPF do this) d) It includes subnet mask information in its routing updates 36) Which is NOT a characteristic of RIP? a) A distance-vector protocol b) Sends updates only when changes occur in the network topology (sends updates every 30 seconds) c) Determines the best path to remote networks based on hop count d) Used for routing between networks in the same Autonomous System 37) Which of the following tasks does NOT need to be completed to configure dynamic routing on a router? a) Select and configure the routing protocol to be implemented b) Assign an IP address and subnet mask to the router interface c) Configure the routing protocol with the interface IP addresses and subnet mask information d) Configure the routing protocol with the network addresses to include in dynamic routing 38) What is the purpose of the network command used when configuring RIP routing protocol on a router? a) It specifies which interfaces will exchange routing updates and which networks to advertise b) It activates RIP for all routes that exist within the enterprise network c) It specifies the routing protocol to use d) It specifies the best path to the destination route 39) A network technician is configuring a new router. The interfaces have been configured with IP addressing information and turned on, but no routing protocols or static routes have been configured. What routes will be present in the routing table? a) The default routes b) Broadcast routes c) None – it will be empty d) Directly connected routes 40) Which network devices are used on the Internet to route traffic between autonomous systems? a) Border gateway routers b) PAT servers c) ISP switches d) Interior routers 41) Where will a packet destined for the host 172.32.0.2 be routed to? a) b) c) d) Out interface FastEthernet 0/0 Out interface Serial 0/0/0 Out interface FastEthernet 0/1 It will be dropped (there is no default gateway or Gateway of last resort, so unknown packets are dropped) 42) When a router learns about 2 paths to the same network, which 2 factors does it use to determine the best path? a) Route metric and administrative distance (metric measures cost to get there, AD measures reliability of route) b) As number and administrative distance c) Route metric and Number of hops away d) Route distance and route metric 43) What is used to exchange routing information between routers in different AS (autonomous systems)? a) Static routing b) IGP routing protocols c) EGP routing protocols d) Default routes 44) R1 and R2 have been configured with the IP addresses displayed and static routes to all remote networks. The show ip route command displays the result below. Why do the static routes not appear in the routing table? a) A default route has not been configured on the routers b) A dynamic routing protocol has not been configured on the routers c) The router interfaces are administratively down (if the interfaces are down, then no routes will appear in the routing table) d) The serial interfaces must be configured with IP addresses in the 10.14.14.0 network 45) The show ip route command was executed on one of the routers shown in the graphic below, and this was the result. From which router was this command executed? a) A b) B c) C (look at connected networks) d) D 46) R1 and R2 are configured with the commands that are displayed. All interfaces are properly configured, but neither router is receiving router updates. What would have to be done to fix the problem? a) Configure Rip with networks 192.168.2.0 & 192.168.4.0 on R1 b) Configure Rip with networks 192.168.1.0 &192.168.3.0 on R2 c) Configure Rip with networks 10.0.0.0 & 192.168.2.0 on R1 d) Configure Rip with network 10.0.0.0 on R1 and R2 (if the 10.0.0.0 network is not added to the RIP configuration then the serial interfaces can’t participate in the RIP routing and the routers won’t be able to send or receive updates to each other) 47) If a router’s configuration register setting is set to 0x2102, what will the router do when it boots up? a) Load the IOS from NVRAM b) Load the IOS from Flash (this is the default setting which indicates a flash load) c) Load the IOS from an external tftp server d) Boot into ROMmon mode 48) A network technician tries to boot a router and it enters into ROMmon mode. Which is NOT a possible reason for this? a) The configuration register is not set to 0x2102 b) There is not enough memory to load the IOS file c) The IOS file is corrupt d) There is no valid configuration file (if there is no config file, the router will still boot, it just wont have a configuration file and it will try to enter setup mode) 49) Which does NOT need to be configured to allow a host to communicate with devices in its own and other networks? a) A valid IP address and subnet mask b) A valid default gateway c) A valid DHCP server address (when you enable DHCP on a client, it sends out a broadcast message to find a DHCP server, so you don’t have to configure a DHCP address for the server on the client) d) A unique host name 50) Why would you use the copy tftp run command on a router? a) To restore a configuration file from a server (copies a config file from a tftp server to the running configuration) b) To back up the current configuration file to a server c) To back up the IOS image to a server d) To restore the IOS image from a server 51) Which type of network diagram would include the host names and IP addresses of hosts, routers and other network devices? a) Physical topology (shows types of devices and their exact location, like on a floor plan) b) Wiring closet diagram c) Logical topology d) Cut sheet 52) Which of these connections would NOT require the use of a crossover cable? a) Hub to switch b) Switch to router (considered 2 different types of devices, so a straight through is used) c) PC to PC d) Router Ethernet port to Router ethernet Port 53) What will be the result of using the command: ip route 0.0.0.0 0.0.0.0 192.168.1.1 on a router? a) If a route to a destination network is not known, the packet will be dropped b) If a route to a destination network is not known, the packet will be sent to 192.168.1.1 (this is the command to add a default route, or set the Gateway of last resort) c) A dynamic route to the network 192.168.1.0 is added to the routing table d) A route to the network 192.168.1.0 will be advertised to other routers 54) Which of the following is the correct order of the router bootup process? a) 1 , 2, 3, 4 1. Locate and load the configuration file b) 2, 3, 4, 1 2. Load the bootstrap program c) 4, 2, 3, 1 (post, bootstrap, IOS, config) 3. Locate and load the IOS d) 2, 4, 1, 3 4. Run the POST 55) Which of these requires the use of straight-through cables? a) A, B, C, and D b) A, C, D c) A and C (between 2 different types of devices – host to router breaks the rules and needs a crossover, router to router needs serial cable) d) A, B and C 56) Which of these will NOT be true if a router fails to find a valid IOS file to boot from? a) The prompt will look like this: rommon 1> b) The router will enter into setup mode (router boots into ROMmon mode, setup mode is when router boots but there is no valid config file) c) You can look for a valid IOS file with the command : show flash d) You can try to boot the router manually with the command: boot flash:<IOS filename> 57) How many bits have been borrowed to subnet this network? 192.168.10.72 /29 a) 2 b) 5 (default mask is /24, custom mask is /29, so 5 bits) c) 3 d) 4 58) Host A is configured with the IP address 192.168.7.35 and Host B has the IP address 192.168.7.50 Each is using the same subnet mask of 255.255.255.240, but the 2 hosts cannot ping each other. What networking device is needed for these 2 devices to communicate? a) Switch b) Hub c) NAT server d) Router (custom mask of /28 indicates 4 bits borrowed, so subnets increase by 16’s - .35 is on the .32 subnet and .50 is on the .48 subnet – they are on different subnets, so they must go through a router to talk) 59) The web server S2 needs to be accessible from the Internet. Which option would be the best way for outside hosts to access S2? a) Dynamic NAT b) Static NAT (the server needs to have a permanent translation between its private IP and one of the outside global addresses from the pool) c) Static PAT d) Dynamic PAT 60) Which best describes NAT? a) A permanent mapping is created between an inside local and an outside global address (static NAT) b) Multiple inside local addresses are mapped to 1 global address, using port numbers (PAT) c) Each inside local address is dynamically translated to an inside global address by using 1 public IP address, or a pool of addresses d) Maps inside global addresses to outside local addresses 61) The CEO of Quickclips inc. decides that the company’s backup process needs to be designed for the quickest restoration of any lost data. He is willing to accept a longer time to complete the actual backups. Which type of backup is appropriate? a) Partial b) Full c) Incremental (backup process is quicker, and takes longer to restore) d) Differential (backup process is quicker, and takes longer to restore) 62) Why would a business choose to implement an IPS instead of an IDS? a) An IDS detects and blocks malicious traffic from getting through b) An IPS can’t stop some malicious traffic from getting through c) An IDS is an in-band device that can affect network traffic d) An IPS detects and blocks malicious traffic from getting through (IPS = Intrusion Prevention System – sits in network and all packets must pass through, so it can block all malicious traffic, IDS = Intrusion Detection – must detect malicious code as it travels through network, then it can set up rules to block future similar traffic) 63) Which type of WAN connection uses packet-switched networks? a) ISDN b) Point-to-point c) Frame relay d) DSL 64) Which does NOT describes the use of port security on a switch? a) With sticky port security MAC addresses are dynamically learned and stored in the address table, they are also added to the running configuration b) With static port security MAC addresses are manually assigned to ports, are stored in the address table and added to the running configuration c) Port security is enabled by default (port security is disabled by default, the others are correct) d) With dynamic port security MAC addresses are dynamically learned and stored in the address table, they are cleared if the switch is shut down 65) Which security tool does NOT allow you to filter or control specific types of traffic from reaching a network? a) Firewall b) Port filtering c) Access control lists d) Gateway (a b and c all allow you to block or filter specific types of traffic)