Facts Sheet - MTTS123
advertisement

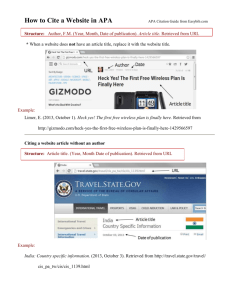
MTTS 1, 2, & 3 Synthesis of Information & Multimedia Facts Sheet Alianna Walbert Salisbury University Facts Sheet 1.) Ethical Issues for Safety and Security Social Networking: - Some local schools have implemented Edmodo, which has a layout similar to Facebook, but is more educationally friendly. Students are becoming more familiar with different types of social networks, like Facebook or Twitter. Teachers may be able to use this to their advantage with networks like Docsity, StudyBlue, Chegg, Lynda, and Sophia (James, 2014). Acceptable Use Policies “Rules applied by many transit networks which restrict the use to which the network may be put. Enforcement of AUPs varies with the network.” - Acceptable use policies help protect school resources, limit liability, and clarify the expectations of students and staff members (“Acceptable use policies,” n.d.) Components include clear specific language, detailed behavior standards, enforcement guidelines, internet policy statement, list of acceptable uses compared to unacceptable uses, online etiquette descriptions, parent consent forms, privacy statement, disclaimer of liability (“Acceptable use policies,” n.d.) Netiquette: “The rules of etiquette that apply when communicating over computer networks, especially the Internet” - - Netiquette guidelines are to be polite, use appropriate language, do not reveal or request personal information, do not use systems in a way that would disrupt network use by others, and respect the intellectual property of other users and information providers. (“Acceptable use policies,” n.d.) Students should be taught about netiquette and how to act appropriately on the internet to avoid issues like cyberbullying Cyberbullying: “When a child is tormented, harassed, humiliated, embarrassed or otherwise targeted by another child, preteen, or teen using the internet, interactive and digital technologies or mobile phones.” (www.stopcyberbullying.org). Cyberbullying may cause mental harm to students that are bullied. It may also cause them to feel alone or helpless or deter them from internet or technology use. - Teachers should encourage students to respect one another, especially when using the internet or other interactive sources. - Teachers need to teach students to use methods like “Think before you post,” or “Take 5!” which will help students think about what they post and what they respond too. Teachers need to make themselves available and trustworthy to students experiencing cyberbullying in order to help them with any issues they may be facing. Teachers should provide examples of cyberbullying, as many students don’t realize the things they post could be hurtful to those who read it. Student Data: - Student data should never be posted online or in online gradebooks with their name. Teachers should use a number system in order to protect student’s privacy even if the system is hacked or passwords are forgotten. Student information should never be disclosed via e-mail or other internet communication sources (Willard, 2002). Student work or examples of teacher’s work should never be posted on any social network by the teacher, parents, or students. Internet Privacy - Students should be taught about internet privacy in order to protect both themselves and their peers. Students should never disclose personal information over the internet Students should never disclose information about other students over the internet. Teachers should encourage students to protect their own information and respect their peers enough to keep any personal information of others private as well. Teachers need to explain to students the consequences and dangers of revealing private information over the internet. 2.) Digital Divide: “The socioeconomic and other disparities between those people who have opportunities and skills enabling them to benefit from digital resources, especially the Internet, and those who do not have these opportunities or skills.” (“Digital divide,” n.d.). Statistics Gender Socio-Economics Racial - Women have 35% fewer opportunities and benefits than men with regard to ICT (Hafkin & Huyer, 2007). - Out of the 52% of women who use technology regularly, only 50% use the internet regularly, in the United States (Hafkin & Huyer, 2007). - The proportion of female internet users in most countries is below 50% (Hafkin & Huyer, 2007). -Men tend to like accessing technology more and use technology for mostly online games and other recreational activities, while women don’t necessarily like accessing technology and tend to use it more for communication (Bain and Rice, 2006). - 66% of people in urban areas have internet access, while only 51% of people in rural areas have internet access. This gap is closing (“Socio-Economic Factors,” 2010). - 94% of households with annual income of over $100,000 have internet access, while only 36% of households with an annual income of under $25,000 have internet access. (“SocioEconomic Factors,” 2010). - 77.3% of Asian households have broadband access; 47.9% of Hispanic households have broadband access; 68% of white households have broadband access, 49.4% of African American households have broadband access; 48.3% of Native American households have broadband access (“Socio-Economic Factors,” 2010). - Races with less internet access use the internet for social media and networking more than research and exploration, like races with more internet access (“Getting Past the ‘Digital Divide,’” 2011). Effects of Digital Divide on Students: Students don’t have access to out of school learning activities or opportunities Leads to learning gaps and disadvantages. Women tend to have discomfort using the internet due to all the dangers that lie on the internet. Resource Equity: Use whatever technology is made available to students – such as cell phones (“Getting past the ‘digital divide,’” 2011) Offer students high quality internet resources that are pertinent to their ethnical, gender, and social interests (Cavin, n.d.) Provide students with take home technologies (Green, 2000). Teacher Bias: Teachers should consider that not all students have the same amount of access that they do in their own homes; some may have more, some may have less. Teachers need to provide equal opportunities in terms of technology and realize that not all students have a firm understanding of technology and how to utilize it. 3.) Copyright, Fair Use, and Creative Commons Copyright: “Protects works from unauthorized copying, performance, or display.” (“Copyright and Education,” n.d.) The Copyright Act can help teachers use works protected by copyright for educational instances (“Copyright and Education,” n.d.). Allows teachers and students to use and reproduce portions of copyrighted material without having to purchase a license (“Copyright and Education,” n.d.). Teachers must realize, and teach students, what constitutes “fair” when using other’s work. Fair Use: Section 107 of the Copyright Law explains factors that determine whether resources are being used fairly: 1.) The purpose and character of the use, including whether such use is of commercial nature or is for nonprofit educational purposes. 2.) The nature of the copyrighted work. 3.) The amount and substantiality of the portion used in relation to the copyrighted work as a whole. 4.) The effect of the use upon the potential market for, or value of, the copyrighted work. (Library of Congress, 2012). If use does not seem fair, it is important to obtain permission from the copyright owner before reproducing (Library of Congress, 2012). Creative Commons: Publishing under a Creative Commons gives others the opportunity to share, use and build on your original work (creativecommons.org). About. (n.d.) Creative Commons. Retrieved from http://creativecommons.org/about Acceptable use policy. (n.d.) Education Service Center, Region 2. Retrieved from http://www.esc2.net/links/aup.htm Acceptable use policy. (n.d.). The free on-line dictionary of computing. Retrieved from http://dictionary.reference.com/browse/acceptable use policy Bain, C. D., & Rice, M. L. (2006). The influence of gender on attitudes, perceptions, and uses of technology. Journal of Research on Technology in Education, 39, 119-132. Retrieved from http://files.eric.ed.gov/fulltext/EJ768873.pdf Carvin, A. (n.d.). Mending the breach: Overcoming the digital divide. Retrieved from http://www.edutopia.org/mendingbreach-overcoming-digital-divide Copyright and education. (n.d.). FindLaw. Retrieved from http://smallbusiness.findlaw.com/intellectual-property/copyrightand-education.html?DCMP=ADC-BUS_CopyrightBoardModifier-Classroom Cyber bullying statistics. (2013). Bullying statistics. Retrieved from http://www.bullyingstatistics .org/ content/cyberbullying-statistics.html Digital divide. (n.d.). Dictionary.com unabridged. Retrieved from http://dictionary.reference.com/browse/digital divide Evidence of an online digital divide in the U.S., January-February 2011. [Chart]. (2011). Retrieved from http://healthpopuli.com/2011/04/14/the-online-digital-health- divide-persists-for-african-americans-and-hispanicsimplications-for-health-reform/ Getting past the ‘digital divide.’ (2011). Teaching tolerance. Retrieved from http://www.tolerance.org/magazine/number-39-spring-2011/feature/getting-past- digital-divide Green, L. C. (2000). Bridging the digital divide in our schools – Achieving technology for all students. Retrieved from http://www.idra.org/IDRA_Newsletter/May_2000 _Equity_and_Excellence/Bridging_the_Digital_Divide_in_Our_ Schools/ Hafkin, N. J., & Huyer, S. (2007). Women and gender in ICT statistics and indicators for development. The MIT Press, 4, 25-41. Retrieved from http://itidjournal.org/itid/article/viewFile/254/124 Hilbert, M. (2011). Digital gender divide or technologically empowered women in developing countries? A typical case of lies, damned lies, and statistics. Women’s Studies International Forum, 34, 479-489. Retrieved from http://dx.doi.org/10.1016/j.wsif.2011.07.001 James, C. (2014, January 6). 5 social networks for students to get academic help. Retrieved from http://www.edudemic.com/social-networks-for-students/ Johns, J. (2011). Eggo learns a lesson on cyber safety. [Audio file]. Retrieved from http://www.teachertube.com/music.php?music_id=4960 Johns, J. (2012). The Autumn and Logan show. [Audio file]. Retrieved from http://www.teachertube.com/music.php?music_id=7762 Johns, J. (2012). The G.R.E.H. radio show. [Audio file]. Retrieved from http://www.teachertube.com/music.php?music_id=7763 Johns, J. (2011). The KSJ radio show on internet safety. [Audio file]. Retrieved from http://www.teachertube.com/music.php?music_id=4961 Library of Congress. (n.d.). Copyright and primary sources. Retrieved from http://www.loc.gov/teachers/usingprimarysources/copyright.html Library of Congress. (2012). Fair Use. Washington DC: U.S. Copyright Office. Retrieved from http://www.copyright.gov/fls/fl102.html Library of Congress. (2010). Help: Registration tips. Washington DC: U.S. Copyright Office. Retrieved from http://www.copyright.gov/eco/help-registration-steps.html Netiquette. (n.d.). Dictionary.com Unabridged. Retrieved from http://dictionary.reference.com/browse/Netiquette Peterson, J. (n.d.). Acceptable use policies. Retrieved from http://education.illinois.edu /wp/www.sjfschool.net/whitepages/acceptableusepolic y.htm Socio-Economic factors continue to impact digital divide in the US – new report. (2010, November 12). Information policy. Retrieved from http://www.i-policy.org/2010/11/socio-economic-factors-continue-to-impact-digital-divide-inthe-us-new-report.html Willard, N. (2002). Ensuring student privacy on the internet. Retrieved from http://www.educationworld.com/a_tech/tech120.shtml Video Magazine. (2012). Creative commons & copyright info [Video file]. Retrieved from http://www.youtube.com/watch?v=8YkbeycRa2A