Application layer
advertisement
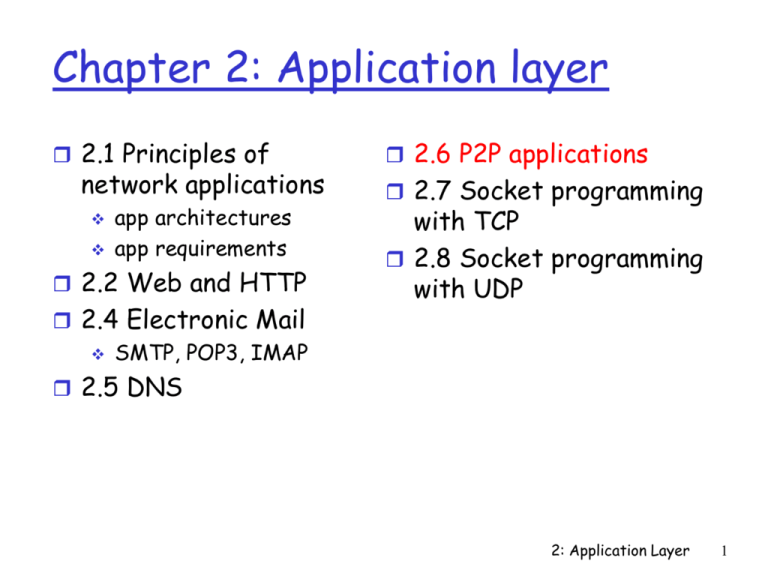
Chapter 2: Application layer
2.1 Principles of
network applications
app architectures
app requirements
2.2 Web and HTTP
2.4 Electronic Mail
SMTP, POP3, IMAP
2.6 P2P applications
2.7 Socket programming
with TCP
2.8 Socket programming
with UDP
2.5 DNS
2: Application Layer
1
Pure P2P architecture
no always-on server
arbitrary end systems
directly communicate peer-peer
peers are intermittently
connected and change IP
addresses
Three topics:
File distribution
Searching for information
Case Study: Skype
2: Application Layer
2
File Distribution: Server-Client vs P2P
Question : How much time to distribute file
from one server to N peers?
us: server upload
bandwidth
Server
us
File, size F
dN
uN
u1
d1
u2
ui: peer i upload
bandwidth
d2
di: peer i download
bandwidth
Network (with
abundant bandwidth)
2: Application Layer
3
File distribution time: server-client
server sequentially
sends N copies:
NF/us time
client i takes F/di
time to download
Server
F
us
dN
u1 d1 u2
d2
Network (with
abundant bandwidth)
uN
Time to distribute F
to N clients using = dcs = max { NF/us, F/min(di) }
i
client/server approach
increases linearly in N
(for large N) 2: Application Layer
4
File distribution time: P2P
server must send one
Server
F
u1 d1 u2
d2
copy: F/us time
us
client i takes F/di time
Network (with
dN
to download
abundant bandwidth)
uN
NF bits must be
downloaded (aggregate)
fastest possible upload rate: us + Sui
dP2P = max { F/us, F/min(di) , NF/(us + Sui) }
i
2: Application Layer
5
Server-client vs. P2P: example
Client upload rate = u, F/u = 1 hour, us = 10u, dmin ≥ us
Minimum Distribution Time
3.5
P2P
Client-Server
3
2.5
2
1.5
1
0.5
0
0
5
10
15
20
25
30
35
N
2: Application Layer
6
File distribution: BitTorrent
P2P file distribution
tracker: tracks peers
participating in torrent
torrent: group of
peers exchanging
chunks of a file
obtain list
of peers
trading
chunks
peer
2: Application Layer
7
BitTorrent (1)
file divided into 256KB chunks.
peer joining torrent:
has no chunks, but will accumulate them over time
registers with tracker to get list of peers,
connects to subset of peers (“neighbors”)
while downloading, peer uploads chunks to other
peers.
peers may come and go
once peer has entire file, it may (selfishly) leave or
(altruistically) remain
2: Application Layer
8
BitTorrent (2)
Pulling Chunks
at any given time,
different peers have
different subsets of
file chunks
periodically, a peer
(Alice) asks each
neighbor for list of
chunks that they have.
Alice sends requests
for her missing chunks
rarest first
Sending Chunks: tit-for-tat
Alice sends chunks to four
neighbors currently
sending her chunks at the
highest rate
re-evaluate top 4 every
10 secs
every 30 secs: randomly
select another peer,
starts sending chunks
newly chosen peer may
join top 4
“optimistically unchoke”
2: Application Layer
9
BitTorrent: Tit-for-tat
(1) Alice “optimistically unchokes” Bob
(2) Alice becomes one of Bob’s top-four providers; Bob reciprocates
(3) Bob becomes one of Alice’s top-four providers
With higher upload rate,
can find better trading
partners & get file faster!
2: Application Layer
10
P2P: searching for information
Index in P2P system: maps information to peer location
(location = IP address & port number)
.
Instant messaging
File sharing (eg e-mule)
Index maps user
Index dynamically
names to locations.
tracks the locations of
files that peers share.
When user starts IM
application, it needs to
Peers need to tell
inform index of its
index what they have.
location
Peers search index to
Peers search index to
determine where files
determine IP address
can be found
of user.
2: Application Layer
11
P2P: centralized index
original “Napster” design
1) when peer connects, it
informs central server:
Bob
centralized
directory server
1
peers
IP address
content
2) Alice queries for “Hey
Jude”
3) Alice requests file from
Bob
1
3
1
2
1
Alice
2: Application Layer
12
P2P: problems with centralized directory
single point of failure
performance bottleneck
copyright infringement:
“target” of lawsuit is
obvious
file transfer is
decentralized, but
locating content is
highly centralized
2: Application Layer
13
Query flooding
fully distributed
no central server
used by Gnutella
Each peer indexes the
files it makes available
for sharing (and no
other files)
overlay network: graph
edge between peer X
and Y if there’s a TCP
connection
all active peers and
edges form overlay net
edge: virtual (not
physical) link
given peer typically
connected with < 10
overlay neighbors
2: Application Layer
14
Query flooding
Query message
sent over existing TCP
connections
peers forward
Query message
QueryHit
sent over
reverse
Query
path
File transfer:
HTTP
Query
QueryHit
QueryHit
Scalability:
limited scope
flooding
2: Application Layer
15
Gnutella: Peer joining
joining peer Alice must find another peer in
Gnutella network: use list of candidate peers
2. Alice sequentially attempts TCP connections with
candidate peers until connection setup with Bob
3. Flooding: Alice sends Ping message to Bob; Bob
forwards Ping message to his overlay neighbors
(who then forward to their neighbors….)
peers receiving Ping message respond to Alice
with Pong message
4. Alice receives many Pong messages, and can then
setup additional TCP connections
Peer leaving: see homework problem!
1.
2: Application Layer
16
Distributed Hash Table (DHT)
DHT: a distributed P2P database
database has (key, value) pairs; examples:
key:
ss number; value: human name
key: movie title; value: IP address
Distribute the (key, value) pairs over the
(millions of peers)
a peer queries DHT with key
DHT
returns values that match the key
peers can also insert (key, value) pairs
Application 2-17
Q: how to assign keys to peers?
central issue:
assigning
(key, value) pairs to peers.
basic idea:
convert
each key to an integer
Assign integer to each peer
put (key,value) pair in the peer that is closest
to the key
Application 2-18
DHT identifiers
assign integer identifier to each peer in range
[0,2n-1] for some n.
each
identifier represented by n bits.
require each key to be an integer in same range
to get integer key, hash original key
e.g.,
key = hash(“Led Zeppelin IV”)
this is why its is referred to as a distributed “hash”
table
Application 2-19
Assign keys to peers
rule: assign key to the peer that has the
closest ID.
convention in lecture: closest is the
immediate successor of the key.
e.g., n=4; peers: 1,3,4,5,8,10,12,14;
key
= 13, then successor peer = 14
key = 15, then successor peer = 1
Application 2-20
Circular DHT (1)
1
3
15
4
12
5
10
8
each peer only aware of immediate successor and
predecessor.
“overlay network”
Application 2-21
Circular DHT (1)
O(N) messages
on avgerage to resolve
query, when there
are N peers
I am
0001
Who’s responsible
for key 1110 ?
0011
1111
1110
0100
1110
1110
1100
1110
1110
Define closest
as closest
successor
0101
1110
1010
1000
Application 2-22
Circular DHT with shortcuts
1
3
Who’s responsible
for key 1110?
15
4
12
5
10
8
each peer keeps track of IP addresses of predecessor,
successor, short cuts.
reduced from 6 to 2 messages.
possible to design shortcuts so O(log N) neighbors, O(log N)
messages in query
Application 2-23
Peer churn
handling peer churn:
1
peers may come and go (churn)
each peer knows address of its
3
15
4
12
5
10
two successors
each peer periodically pings its
two successors to check aliveness
if immediate successor leaves,
choose next successor as new
immediate successor
8
example: peer 5 abruptly leaves
peer 4 detects peer 5 departure; makes 8 its immediate
successor; asks 8 who its immediate successor is; makes
8’s immediate successor its second successor.
what if peer 13 wants to join?
Application 2-24
Chapter 2: Application layer
2.1 Principles of
network applications
2.2 Web and HTTP
2.3 FTP
2.4 Electronic Mail
2.6 P2P applications
2.7 Socket programming
with TCP
2.8 Socket programming
with UDP
SMTP, POP3, IMAP
2.5 DNS
2: Application Layer
25
Socket programming
Goal: learn how to build client/server application that
communicate using sockets
Socket API
introduced in BSD4.1 UNIX,
1981
explicitly created, used,
released by apps
client/server paradigm
two types of transport
service via socket API:
unreliable datagram
reliable, byte streamoriented
socket
a host-local,
application-created,
OS-controlled interface
(a “door”) into which
application process can
both send and
receive messages to/from
another application
process
2: Application Layer
26
Socket-programming using TCP
Socket: a door between application process and endend-transport protocol (UCP or TCP)
TCP service: reliable transfer of bytes from one
process to another
controlled by
application
developer
controlled by
operating
system
process
process
socket
TCP with
buffers,
variables
host or
server
internet
socket
TCP with
buffers,
variables
controlled by
application
developer
controlled by
operating
system
host or
server
2: Application Layer
27
Socket programming with TCP
Client must contact server
server process must first
be running
server must have created
socket (door) that
welcomes client’s contact
Client contacts server by:
creating client-local TCP
socket
specifying IP address, port
number of server process
When client creates
socket: client TCP
establishes connection to
server TCP
When contacted by client,
server TCP creates new
socket for server process to
communicate with client
allows server to talk with
multiple clients
source port numbers
used to distinguish
clients (more in Chap 3)
application viewpoint
TCP provides reliable, in-order
transfer of bytes (“pipe”)
between client and server
2: Application Layer
28
Client/server socket interaction: TCP
Server (running on hostid)
Client
create socket,
port=x, for
incoming request:
welcomeSocket =
ServerSocket()
TCP
wait for incoming
connection request connection
connectionSocket =
welcomeSocket.accept()
read request from
connectionSocket
write reply to
connectionSocket
close
connectionSocket
setup
create socket,
connect to hostid, port=x
clientSocket =
Socket()
send request using
clientSocket
read reply from
clientSocket
close
clientSocket
2: Application Layer
29
Stream jargon
keyboard
monitor
output
stream
inFromServer
Client
Process
process
input
stream
outToServer
characters that flow into
or out of a process.
An input stream is
attached to some input
source for the process,
e.g., keyboard or socket.
An output stream is
attached to an output
source, e.g., monitor or
socket.
inFromUser
A stream is a sequence of
input
stream
client
TCP
clientSocket
socket
to network
TCP
socket
from network
2: Application Layer
30
Socket programming with TCP
Example client-server app:
1) client reads line from
standard input (inFromUser
stream) , sends to server via
socket (outToServer
stream)
2) server reads line from socket
3) server converts line to
uppercase, sends back to
client
4) client reads, prints modified
line from socket
(inFromServer stream)
2: Application Layer
31
Example: Java client (TCP)
import java.io.*;
import java.net.*;
class TCPClient {
public static void main(String argv[]) throws Exception
{
String sentence;
String modifiedSentence;
Create
input stream
Create
client socket,
connect to server
Create
output stream
attached to socket
BufferedReader inFromUser =
new BufferedReader(new InputStreamReader(System.in));
Socket clientSocket = new Socket("hostname", 6789);
DataOutputStream outToServer =
new DataOutputStream(clientSocket.getOutputStream());
2: Application Layer
32
Example: Java client (TCP), cont.
Create
input stream
attached to socket
BufferedReader inFromServer =
new BufferedReader(new
InputStreamReader(clientSocket.getInputStream()));
sentence = inFromUser.readLine();
Send line
to server
outToServer.writeBytes(sentence + '\n');
Read line
from server
modifiedSentence = inFromServer.readLine();
System.out.println("FROM SERVER: " + modifiedSentence);
clientSocket.close();
}
}
2: Application Layer
33
Example: Java server (TCP)
import java.io.*;
import java.net.*;
class TCPServer {
Create
welcoming socket
at port 6789
Wait, on welcoming
socket for contact
by client
Create input
stream, attached
to socket
public static void main(String argv[]) throws Exception
{
String clientSentence;
String capitalizedSentence;
ServerSocket welcomeSocket = new ServerSocket(6789);
while(true) {
Socket connectionSocket = welcomeSocket.accept();
BufferedReader inFromClient =
new BufferedReader(new
InputStreamReader(connectionSocket.getInputStream()));
2: Application Layer
34
Example: Java server (TCP), cont
Create output
stream, attached
to socket
DataOutputStream outToClient =
new DataOutputStream(connectionSocket.getOutputStream());
Read in line
from socket
clientSentence = inFromClient.readLine();
capitalizedSentence = clientSentence.toUpperCase() + '\n';
Write out line
to socket
outToClient.writeBytes(capitalizedSentence);
}
}
}
End of while loop,
loop back and wait for
another client connection
2: Application Layer
35
Chapter 2: Application layer
2.1 Principles of
network applications
2.2 Web and HTTP
2.3 FTP
2.4 Electronic Mail
2.6 P2P applications
2.7 Socket programming
with TCP
2.8 Socket programming
with UDP
SMTP, POP3, IMAP
2.5 DNS
2: Application Layer
36
Socket programming with UDP
UDP: no “connection” between
client and server
no handshaking
sender explicitly attaches
IP address and port of
destination to each packet
server must extract IP
address, port of sender
from received packet
application viewpoint
UDP provides unreliable transfer
of groups of bytes (“datagrams”)
between client and server
UDP: transmitted data may be
received out of order, or
lost
2: Application Layer
37
Client/server socket interaction: UDP
Server (running on hostid)
create socket,
port= x.
serverSocket =
DatagramSocket()
read datagram from
serverSocket
write reply to
serverSocket
specifying
client address,
port number
Client
create socket,
clientSocket =
DatagramSocket()
Create datagram with server IP and
port=x; send datagram via
clientSocket
read datagram from
clientSocket
close
clientSocket
2: Application Layer
38
Example: Java client (UDP)
input
stream
Client
process
monitor
inFromUser
keyboard
Process
Input: receives
packet (recall
thatTCP received
“byte stream”)
UDP
packet
receivePacket
packet (recall
that TCP sent
“byte stream”)
sendPacket
Output: sends
UDP
packet
client
UDP
clientSocket
socket
to network
UDP
socket
from network
2: Application Layer
39
Example: Java client (UDP)
import java.io.*;
import java.net.*;
Create
input stream
Create
client socket
Translate
hostname to IP
address using DNS
class UDPClient {
public static void main(String args[]) throws Exception
{
BufferedReader inFromUser =
new BufferedReader(new InputStreamReader(System.in));
DatagramSocket clientSocket = new DatagramSocket();
InetAddress IPAddress = InetAddress.getByName("hostname");
byte[] sendData = new byte[1024];
byte[] receiveData = new byte[1024];
String sentence = inFromUser.readLine();
sendData = sentence.getBytes();
2: Application Layer
40
Example: Java client (UDP), cont.
Create datagram
with data-to-send,
length, IP addr, port
DatagramPacket sendPacket =
new DatagramPacket(sendData, sendData.length, IPAddress, 9876);
Send datagram
to server
clientSocket.send(sendPacket);
Read datagram
from server
clientSocket.receive(receivePacket);
DatagramPacket receivePacket =
new DatagramPacket(receiveData, receiveData.length);
String modifiedSentence =
new String(receivePacket.getData());
System.out.println("FROM SERVER:" + modifiedSentence);
clientSocket.close();
}
}
2: Application Layer
41
Example: Java server (UDP)
import java.io.*;
import java.net.*;
Create
datagram socket
at port 9876
class UDPServer {
public static void main(String args[]) throws Exception
{
DatagramSocket serverSocket = new DatagramSocket(9876);
byte[] receiveData = new byte[1024];
byte[] sendData = new byte[1024];
while(true)
{
Create space for
received datagram
Receive
datagram
DatagramPacket receivePacket =
new DatagramPacket(receiveData, receiveData.length);
serverSocket.receive(receivePacket);
2: Application Layer
42
Example: Java server (UDP), cont
String sentence = new String(receivePacket.getData());
Get IP addr
port #, of
sender
InetAddress IPAddress = receivePacket.getAddress();
int port = receivePacket.getPort();
String capitalizedSentence = sentence.toUpperCase();
sendData = capitalizedSentence.getBytes();
Create datagram
to send to client
DatagramPacket sendPacket =
new DatagramPacket(sendData, sendData.length, IPAddress,
port);
Write out
datagram
to socket
serverSocket.send(sendPacket);
}
}
}
End of while loop,
loop back and wait for
another datagram
2: Application Layer
43
Chapter 2: Summary
our study of network apps now complete!
application architectures
client-server
P2P
hybrid
application service
requirements:
reliability, bandwidth,
delay
specific protocols:
HTTP
FTP
SMTP, POP, IMAP
DNS
P2P: BitTorrent, Skype
socket programming
Internet transport
service model
connection-oriented,
reliable: TCP
unreliable, datagrams: UDP
2: Application Layer
44
Chapter 2: Summary
Most importantly: learned about protocols
typical request/reply
message exchange:
client requests info or
service
server responds with
data, status code
message formats:
headers: fields giving
info about data
data: info being
communicated
Important themes:
control vs. data msgs
in-band, out-of-band
centralized vs.
decentralized
stateless vs. stateful
reliable vs. unreliable
msg transfer
“complexity at network
edge”
2: Application Layer
45