Q1 (1)
Troubleshooting Methodologies
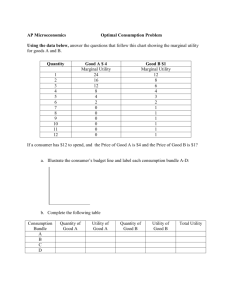
Flow chart of a structured troubleshooting approach
Chapter #
© 2007 – 2010, Cisco Systems, Inc. All rights reserved.
Cisco Public
3
Cisco Public
4
Troubleshooting Methodologies
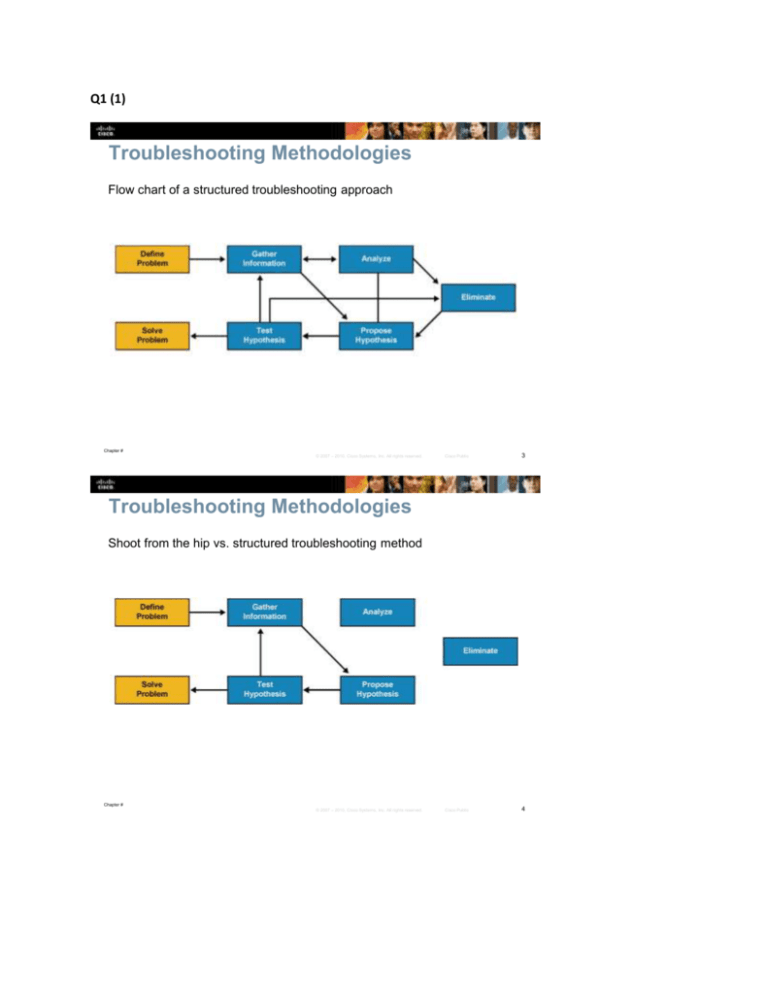
Shoot from the hip vs. structured troubleshooting method
Chapter #
© 2007 – 2010, Cisco Systems, Inc. All rights reserved.
Q1(2)
10. Ping
The most commonly used network tool is the ping utility. This utility is used to provide a basic
connectivity test between the requesting host and a destination host. This is done by using the
Internet Control Message Protocol (ICMP) which has the ability to send an echo packet to a
destination host and a mechanism to listen for a response from this host. Simply stated, if the
requesting host receives a response from the destination host, this host is reachable. This utility is
commonly used to provide a basic picture of where a specific networking problem may exist. For
example, if an Internet connection is down at an office, the ping utility can be used to figure out
whether the problem exists within the office or within the network of the Internet provider.
Figure 1 below shows an example of the ping utility being used to obtain the reachability status
of the locally connected router.
Figure 1: Ping utility
9. Tracert/traceroute
Typically, once the ping utility has been used to determine basic connectivity, the
tracert/traceroute utility can used to determine more specific information about the path to the
destination host including the route the packet takes and the response time of these intermediate
hosts. Figure 2 below shows an example of the tracert utility being used to find the path from a
host inside an office to www.google.com. The tracert utility and traceroute utilities perform the
same function but operate on different operating systems, Tracert for Windows machines and
traceroute for Linux/*nix based machines.
Figure 2: Tracert/traceroute utility
8. Ipconfig/ifconfig
One of the most important things that must be completed when troubleshooting a networking
issue is to find out the specific IP configuration of the variously affected hosts. Sometimes this
information is already known when addressing is configured statically, but when a dynamic
addressing method is used, the IP address of each host can potentially change often. The utilities
that can be used to find out this IP configuration information include the ipconfig utility on
Windows machines and the ifconfig utility on Linux/*nix based machines. Figure 3 below shows
an example of the ifconfig utility showing the IP configuration information of a queries host.
Figure 3: Ifconfig utility
7. Nslookup
Some of the most common networking issues revolve around issues with Dynamic Name System
(DNS) address resolution issues. DNS is used by everyone using the Internet to resolve
commonly known domain names (i.e. google.com) to commonly unknown IP addresses (i.e.
74.125.115.147). When this system does not work, most of the functionality that people are used
to goes away, as there is no way to resolve this information. The nslookup utility can be used to
lookup the specific IP address(es) associated with a domain name. If this utility is unable to
resolve this information, there is a DNS issue. Along with simple lookup, the nslookup utility is
able to query specific DNS servers to determine an issue with the default DNS servers
configured on a host. Figure 4 below shows an example of how the nslookup utility can be used
to query the associated IP address information.
Figure 4: Nslookup utility
6. Netstat
Often, one of the things that are required to be figured out is the current state of the active
network connections on a host. This is very important information to find for a variety of
reasons. For example, when verifying the status of a listening port on a host or to check and see
what remote hosts are connected to a local host on a specific port. It is also possible to use the
netstat utility to determine which services on a host that is associated with specific active ports.
Figure 5 below shows an example of the netstat utility being used to display the currently active
ports on a Linux machine.
Figure 5: Netstat utility
5. PuTTY/Tera Term
When connecting to a variety of different types of equipment, a telnet, SSH or serial client is
required; when this is required both the puTTY and Tera Term programs are able to provide
these functionalities. The selection of one over the other is strictly a personal preference. Figures
6 and 7 below show both puTTY and Tera Term being used to connect to a host via SSH.
Figure 6: PuTTY
Figure 7: Tera Term
4. Subnet and IP Calculator
One of the most important tools in the belt of a junior network engineer is an IP network
calculator. These can be used to unsure a correct IP address selection and with this a correct IP
address configuration. While this type of tool is used by senior level network engineers, much of
the information obtained from the tool becomes simpler to calculate the longer and more
experience you have in the field. Two of the more commonly used free IP calculators include
Wildpackets (Bitcricket) Network Calculator and Solarwinds Advanced Subnet Calculator which
can be found at the links below.
http://www.bitcricket.com/downloads/IPCalculator.msi
http://downloads.solarwinds.com/solarwinds/Release/FreeTool/SolarWinds-SubnetCalculator.zip
Figure 8: Subnet calculator
3. Speedtest.net/pingtest.net
A very easy test that can be used to both determine the Internet bandwidth available to a specific
host and to determine the quality of an Internet connection is the use of the tools available at the
speedtest.net and pingtest.net websites. The speedtest.net site provides the ability to determine
the amount of bandwidth that is available to a specific host at a specific point in time; this is
often a good tool to use when measuring how long it is going to take to upload or download
information from a local to remote host. This measurement can also be used to determine
whether the connection is offering the amount of bandwidth that was purchased from the Internet
provider; keep in mind however that some amount of bandwidth difference is expected between
the quoted bandwidth purchased and the measured bandwidth. The pingtest.net website is used to
determine the quality of the connection by measuring the ping response times and jitter amounts
over a short period of time. This information can be used to determine a likelihood of how well
the measured connection will deal with certain types of high demand traffic like Voice over IP
(VoIP) or gaming. Figure 9 and 10 below show example output from both of these sites.
Figure 9: Speedtest
Figure 10: Pingtest
2. Pathping/mtr
In an effort to take advantage of the benefits of both the ping and tracert/traceroute commands,
the pathping and mtr utilities were developed. Both of these tools take the functionality and
information that can be obtained from these types of tools and provide a more detailed single
picture of the path characteristics from a specific host to a specific destination. Figure 11 and 12
below show examples of these two tools and what information they provide.
Figure 11: Pathping
Figure 12: Mtr
1. Route
The last of the tools covered in this article is the route utility. This utility is used to display the
current status of the routing table on a host. While the use of the route utility is limited in
common situations where the host only has a single IP address with a single gateway, it is vital in
other situations where multiple IP address and multiple gateways are available. Figure 13 below
shows an example of the route utility being used on a Windows machine.
Figure 13: Route Utility
Q2 (1 and 2/half)
•
Top-down: Using this approach, you work from the Open Systems Interconnection (OSI) model’s
application layer down to the physical layer.
•
Bottom-up: The bottom-up approach starts from the OSI model’s physical layer and moves up
to the application layer.
•
Divide and conquer: Using this approach, you start in the middle of the OSI model’s stack
(usually the network layer) and then, based on your findings, you move up or down the OSI
stack.
•
Follow-the-path: This approach is based on the path that packets take through the network
from source to destination.
•
Spot the differences: This approach compares network devices or processes that are operating
correctly to devices or processes that are not operating as expected and gathers clues by
spotting significant differences.
•
Move the problem: The strategy of this troubleshooting approach is to physically move
components and observe if the problem moves with the components or not.
Q3 (http://www.cisco.com/web/about/security/intelligence/virus-worm-diffs.html)
Viruses
A computer virus is a type of malware that propagates by inserting a copy of itself into and
becoming part of another program. It spreads from one computer to another, leaving infections as
it travels. Viruses can range in severity from causing mildly annoying effects to damaging data
or software and causing denial-of-service (DoS) conditions. Almost all viruses are attached to an
executable file, which means the virus may exist on a system but will not be active or able to
spread until a user runs or opens the malicious host file or program. When the host code is
executed, the viral code is executed as well. Normally, the host program keeps functioning after
it is infected by the virus. However, some viruses overwrite other programs with copies of
themselves, which destroys the host program altogether. Viruses spread when the software or
document they are attached to is transferred from one computer to another using the network, a
disk, file sharing, or infected e-mail attachments.
Worms
Computer worms are similar to viruses in that they replicate functional copies of themselves and
can cause the same type of damage. In contrast to viruses, which require the spreading of an
infected host file, worms are standalone software and do not require a host program or human
help to propagate. To spread, worms either exploit a vulnerability on the target system or use
some kind of social engineering to trick users into executing them. A worm enters a computer
through a vulnerability in the system and takes advantage of file-transport or informationtransport features on the system, allowing it to travel unaided.
Trojans
A Trojan is another type of malware named after the wooden horse the Greeks used to infiltrate
Troy. It is a harmful piece of software that looks legitimate. Users are typically tricked into
loading and executing it on their systems. After it is activated, it can achieve any number of
attacks on the host, from irritating the user (popping up windows or changing desktops) to
damaging the host (deleting files, stealing data, or activating and spreading other malware, such
as viruses). Trojans are also known to create back doors to give malicious users access to the
system.
Unlike viruses and worms, Trojans do not reproduce by infecting other files nor do they selfreplicate. Trojans must spread through user interaction such as opening an e-mail attachment or
downloading and running a file from the Internet.
Q3 (2)
IPS - Intrusion Prevention System - inspects traffic flowing through a network and is capable of
blocking or otherwise remediating flows that it determines are malicious. Usually uses a
combination of traffic and file signatures and heuristic analysis of flows.
IDS - Intrusion Detection System - similar to IPS but does not affect flows in any way - only
logs or alerts on malicious traffic.
Firewall- prevents or allows traffic between interfaces based on configured rules. Often have a
network address translation function to isolate private (RFC 1918) network addresses from
public ones. May inspect traffic for conformance with proper protocol behavior and drop noncompliant traffic. Firewalls often have an optional IDS/IPS component based on their usually
being placed at the optimal network location to see all interesting traffic that should be subject to
further inspection and analysis as is done by IDS/IPS.
IPS:
Intrusion Prevention System that receives traffic in such a way that can prevent it from reaching
the different targets on your network.
As Marvin said works with Signatures written with high level Regex Patterns in order to identify
known threaths.
It also provideds the heuristic analysis of low by sitting inline and seeing all traffic during an
amount of time defined by the user where the IPS will build a database about what is known to
be Traffc in order and when traffic might be Out of Order.
IDS:
Security Network Appliance in charge of monitor the network and determine whether or not an
attack is in place.
Does not prevent the attack from reaching the different assets (altough there are some options to
configure it to send RST packets on some platforms).
It does NOT receives the real traffic from client to server or server to client, it basically receives
a copy from the network device attached to it (PC,SPAN session, TAP, Packet Brocker,etc)
Firewall:
The Network Security Appliance for Excellence.
Now days not just in charge of inspectioning trafic at level 3-4 and basic level 7 but actually
going from level 2 to the Deep contents of the packets at layer 7 (Known as Next Generation
Firewalls).
It's main function is to filter traffic through the network while still allowing some traffic to go
through.
Remember that now days the Firewalls come with pre-built IPS engines (known as the UTM
generation firewalls or Unified Threath Management) such as the Cisco ASA CX, SRXs,
CheckPoints and one of the most valuable todays Palo Alto Firewalls.
The line is definitely blurring somewhat as technological capacity increases, platforms are
integrated, and the threat landscape shifts. At their core we have
Firewall - A device or application that analyzes packet headers and enforces policy
based on protocol type, source address, destination address, source port, and/or
destination port. Packets that do not match policy are rejected.
Intrusion Detection System - A device or application that analyzes whole packets, both
header and payload, looking for known events. When a known event is detected a log
message is generated detailing the event.
Intrusion Prevention System - A device or application that analyzes whole packets, both
header and payload, looking for known events. When a known event is detected the
packet is rejected.
The functional difference between an IDS and an IPS is a fairly subtle one and is often nothing
more than a configuration setting change. For example, in a Juniper IDP module, changing from
Detection to Prevention is as easy as changing a drop-down selection from LOG to LOG/DROP.
At a technical level it can sometimes require redesign of your monitoring architecture.
Given the similarity between all three systems there has been some convergence over time. The
Juniper IDP module mentioned above, for example, is effectively an add-on component to a
firewall. From a network flow and administrative perspective the firewall and IDP are
functionally indistinguishable even if they are technically two separate devices.
There is also much market discussion of something called a Next Generation Firewall (NGFW).
The concept is still new enough that each vendor has their own definition as to what constitutes
a NGFW but for the most part all agree that it is a device that enforces policy unilaterally across
more than just network packet header information. This can make a single device act as both a
traditional Firewall and IPS. Occasionally additional information is gathered, such as from
which user the traffic originated, allowing even more comprehensive policy enforcement.