chap 1-intro - WordPress.com
advertisement

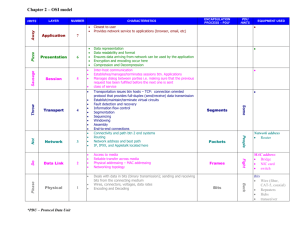
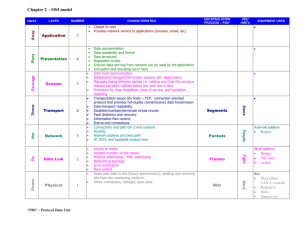
Data Communications DNT 1013 Prepared By: Mdm Noor Suhana Bt Sulaiman FKMT-NT, TATiUC Introduction to Data Communications Chapter 1 What is data communication? Not to be confused with telecommunication— – Any process that permits the passage from a sender to one or more receivers of information of any nature, delivered in any easy to use form by any electromagnetic system. Data communication– Defined as a subset of telecommunication involving the transmission of data to and from computers and components of computer systems. • More specifically data communication is transmitted via mediums such as wires, coaxial cables, fiber optics, or radiated electromagnetic waves such as broadcast radio, infrared light, microwaves, and satellites. History of Telecommunications Invention of telegraph Samuel Morse – 1837 Invention of telephone- Alexander Graham Bell – 1876 Development of wireless By ??? – 1896 Concept of universal access and growth of AT&T Divestiture of AT&T—what year?? History of Telecommunications Continued…. Telecommunications Act of 1996 Three main developments that led to the growth of data communications systems: – Large-scale integration of circuits reduced the cost and size of terminals and comm equipment – Developments of software systems made establishment of communication networks easy – Competition among providers of transmission facilities reduced the cost of data circuits History of Data Communication Transistor developed by Bell Labs (which is now ???) 1947 Hush-a-Phone Case Carterphone case MCI and Long Distance Creation of networks (LAN’s and WAN’s) Data Link Protocols Microcomputers Framework for Global Electronic Commerce A Framework for Global Electronic Commerce was released in 1997 It’s release underscores the importance of Internet-based commerce in the global economy It outlines several guiding principles for e-commerce planners and strategists Table 1-3 Table 1-4 Features of Communication Four things required – Sender, receiver, medium, and message Types of messages – – – – – – File Request Response Status Control Correspondence Understandability Error Detection Network Applications The network applications environment consists of several important components: – Application programs – Operating systems – Data communication systems – Database management systems The application environment is illustrated in Figure 1-10 Figure 1-10 Online System Requirements Response Time Throughput Consistency Flexibility Online Systems Requirements Continued Availability Reliability – Mean time between failure (MTBF) – Mean time to repair (MTTR) – Fault Tolerance Recovery Security Business Data Communication Applications Major data communication applications include: – E-mail – Groupware – Knowledge management systems – E-commerce and e-business applications – Wireless applications Groupware Applications Group calendar systems Electronic filing cabinets Project management software Group support systems Electronic meeting and videoconferencing systems Document management systems (image processing systems) Other Data Communication Applications Batch applications Data entry applications Distributed applications Inquiry/response applications Interactive applications Sensor-based applications Combined applications Application Service Providers Many businesses have turned to third-party services for some or all of their business and data communications applications Application service providers (ASPs) are third-party organizations that manage and distribute software and services to other companies over the Web Many ASPs specialize in integrated ecommerce and e-business applications Business Data Communications Issues Major data communications issues include: – Cost-effectiveness – The Internet – Bandwidth – Evolving technologies – Convergence – Standards – Privacy and security Important Standard-Setting Organizations Table 1-5 Business Data Communication Careers There are numerous job opportunities and career paths for individuals interested in data communications and networking Table 1-6 includes examples of data communication job titles Table 1-7 summarizes some of the major professional certifications for networking and data communications specialists Table 1-6 Table 1-7 Introduction to Networks Can be defined as a single computer , called a host, together with communication circuits, communication equipment, and terminals. There are many different types of network configurations (see figures1-4 to 1-8) Key Data Communication Concepts Session: communication dialog between network users or applications Network: interconnected group of computers and communication devices Node: a network-attached computer Link: connects adjacent nodes (see Figure 1-4) Path: end-to-end route within a network Circuit: the conduit over which data travels Packetizing: dividing messages into fixed-length packets prior to transmission over a network’s communication media Routing: determining a message’s path from sending to receiving nodes. Store-and-Forward Systems Messages may be stored at intermediate nodes along the transmission path between sender and receiver in store-and-forward systems – This helps ensure message delivery without obligating the sender to wait until a message is delivered before transmitting other messages – It also helps ensure message delivery in the case of link or destination failure while the message is in transit – Store-and forward algorithms are valuable in timestaged delivery systems and in networks that assign priorities to different messages Network Topology, Architecture, and Complexity Network topology refers to the physical layout of a network, the way that nodes attach to the communication medium Network architecture refers to the way in which media, hardware, and software are integrated to form a network Network complexity is concerned with extent to which network architectures are simple or diverse in their make – Figures 1-5, 1-6, and 1-7 illustrate various levels of complexity Figure 1-5 Figure 1-6 Figure 1-7 Data Communication Frameworks Two major data communication frameworks have been developed to help ensure that networks meet business and communication requirements: – Open Systems Interconnection (OSI) reference model developed by the International Standards Organization (ISO) – Transmission Control Protocol/Internet Protocol (TCP/IP) suite History of the OSI Model Open Systems Interconnected Model – was created in the 70’s by the ISO (although the CCITT came up with their own model) • 10 different people got together and considered all functions of communications – was created because people realized that our computers needed to talk to each other(and there was no one dominant computer system) – ISDN was a big factor – 7 layers = 4 upper and 3 lower OSI Reference Model in Practice The OSI reference model is used in many ways: – To provide assistance when troubleshooting network problems – To provide a common terminology and framework for networking technology developers – To facilitate the development of connectivity standards needed for flexible open architectures – To enable the development of protocol stacks that allow network nodes to communicate with one another Network Models Using a formal model allows us to deal with various aspects of Networks abstractly. We will look at a popular model (OSI reference model). The OSI reference model is a layered model. Layering Divide a task into pieces and then solve each piece independently (or nearly so). Establishing a well defined interface between layers makes porting easier. Major Advantages: Code Reuse Extensibility Layering Example: Federal Express Letter in envelope, address on outside FedX guy adds addressing information, barcode. Local office drives to airport and delivers to hub. Sent via airplane to nearest city. Delivered to right office Delivered to right person FedX Layers Letter Addressed Envelope Letter Addressed Envelope OSI MODEL Established in 1947, the International Standards Organization (ISO) is a multinational body dedicated to worldwide agreement on international standards. An ISO standard that covers all aspects of network communications is the Open Systems Interconnection (OSI) model. It was first introduced in the late 1970s. ISO is the organization. OSI is the model Why the structure of network need Network Model -OSI Model? Cont.. The OSI model describes how information or data makes its way from application programmes (such as spreadsheets) through a network medium (such as wire) to another application programme located on another network. The OSI reference model divides the problem of moving information between computers over a network medium into SEVEN smaller and more manageable problems . This separation into smaller more manageable functions is known as layering. Cont.. The OSI Reference Model is composed of 7 layers, each specifying particular network functions. The process of breaking up the functions or tasks of networking into layers reduces complexity. Each layer provides a service to the layer above it in the protocol specification. Each layer communicates with the same layer’s software or hardware on other computers. The lower 4 layers (transport, network, data link and physical —Layers 4, 3, 2, and 1) are concerned with the flow of data from end to end through the network. The upper four layers of the OSI model (application, presentation and session—Layers 7, 6 and 5) are orientated more toward services to the applications. Data is Encapsulated with the necessary protocol information as it moves down the layers before network transit. Figure 1.0: OSI Model Layer 7: Application The application layer is the OSI layer that is closest to the user. It provides network services to the user’s applications. It differs from the other layers in that it does not provide services to any other OSI layer, but rather, only to applications outside the OSI model. Examples of such applications are spreadsheet programs, word processing programs, and bank terminal programs. The application layer establishes the availability of intended communication partners, synchronizes and establishes agreement on procedures for error recovery and control of data integrity. Layer 6: Presentation The presentation layer ensures that the information that the application layer of one system sends out is readable by the application layer of another system. If necessary, the presentation layer translates between multiple data formats by using a common format. Provides encryption and compression of data. Examples :- JPEG, MPEG, ASCII, EBCDIC, HTML. Layer 5: Session The session layer defines how to start, control and end conversations (called sessions) between applications. This includes the control and management of multiple bi-directional messages using dialogue control. It also synchronizes dialogue between two hosts' presentation layers and manages their data exchange. The session layer offers provisions for efficient data transfer. Examples :- SQL, ASP(AppleTalk Session Protocol). Layer 4: Transport The transport layer regulates information flow to ensure end-to-end connectivity between host applications reliably and accurately. The transport layer segments data from the sending host's system and reassembles the data into a data stream on the receiving host's system. The boundary between the transport layer and the session layer can be thought of as the boundary between application protocols and data-flow protocols. Whereas the application, presentation, and session layers are concerned with application issues, the lower four layers are concerned with data transport issues. Layer 4 protocols include TCP (Transmission Control Protocol) and UDP (User Datagram Protocol). Layer 3: Network Defines end-to-end delivery of packets. Defines logical addressing so that any endpoint can be identified. Defines how routing works and how routes are learned so that the packets can be delivered. The network layer also defines how to fragment a packet into smaller packets to accommodate different media. Routers operate at Layer 3. Examples :- IP, IPX, AppleTalk. Layer 2: Data Link The data link layer provides access to the networking media and physical transmission across the media and this enables the data to locate its intended destination on a network. The data link layer provides reliable transit of data across a physical link by using the Media Access Control (MAC) addresses. The data link layer uses the MAC address to define a hardware or data link address in order for multiple stations to share the same medium and still uniquely identify each other. Concerned with network topology, network access, error notification, ordered delivery of frames, and flow control. Examples :- Ethernet, Frame Relay, FDDI. Layer 1: Physical The physical layer deals with the physical characteristics of the transmission medium. It defines the electrical, mechanical, procedural, and functional specifications for activating, maintaining, and deactivating the physical link between end systems. Such characteristics as voltage levels, timing of voltage changes, physical data rates, maximum transmission distances, physical connectors, and other similar attributes are defined by physical layer specifications. Examples :RJ45 TCP/IP Protocol Suite The TCP/IP suite provides insights into the inner workings of the Internet Like the OSI model, the TCP/IP suite is layered – Because the protocols found at each layer are independent of those at the other layers, a given protocol can be modified without affecting those found at other layers – TCP/IP layers and layer-specific protocols are illustrated in Figure 1-9 TCP/IP TCP-Transmission Control Protocol In OSI reference model terminology -the TCP/IP protocol suite covers the network and transport layers. TCP/IP can be used on many data-link layers (can support many network hardware implementations). The TCP/IP protocol suite is made of five layers: physical, data link, network, transport, and application. The first four layers provide physical standards, network interface, internetworking, and transport functions that correspond to the first four layers of the OSI model. The three topmost layers in the OSI model, however, are represented in TCP/IP by a single layer called the application layer. Cont.. Relationship of layers and address in TCP/IP Cont.. TCP/IP is the basic communication language or protocol of the Internet. It can also be used as a communications protocol in a private network (either an intranet or an extranet). When user are set up with direct access to the Internet, your computer is provided with a copy of the TCP/IP program just as every other computer that you may send messages to or get information from also has a copy of TCP/IP. Cont.. TCP/IP is a two-layer program. The higher layer, Transmission Control Protocol, manages the assembling of a message or file into smaller packets that are transmitted over the Internet and received by a TCP layer that reassembles the packets into the original message. The lower layer, Internet Protocol, handles the address part of each packet so that it gets to the right destination. Each gateway computer on the network checks this address to see where to forward the message. Even though some packets from the same message are routed differently than others, they'll be reassembled at the destination. Cont.. Many Internet users are familiar with the even higher layer application protocols that use TCP/IP to get to the Internet. These include the World Wide Web's Hypertext Transfer Protocol (HTTP), the File Transfer Protocol (FTP), Telnet (Telnet) which lets you logon to remote computers, and the Simple Mail Transfer Protocol (SMTP). These and other protocols are often packaged together with TCP/IP as a "suite." The IP in TCP/IP IP is the network layer – packet delivery service (host-to-host). – translation between different data-link protocols. IP provides connectionless, unreliable delivery of IP datagrams. – Connectionless: each datagram is independent of all others. – Unreliable: there is no guarantee that datagrams are delivered correctly or even delivered at all. Moving Bits through the Network Analog Signal 1 0 Digital Signal 1 1 1 0 0 digital Computer 0 analog Modem digital Modem telephone lines Computer Putting It all Together Data Communications Supports Applications The Operating System manages the resources of the computer. There must however, be a system that provides a bridge between applications and the devices so they can communicate—this is called a Transaction Control Process (TCP)