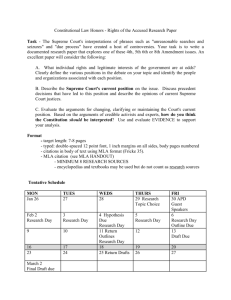
Fourth Amendment - SpartanDebateInstitute
advertisement

1AC Contention One – You’re being watched The expiration of Section 215 and the passage of the Freedom Act created a false sense of security, but federal domestic surveillance is still massive Baumann, June 9, 2015 (Ted, editor of Sovereign Investor’s Offshore Confidential and Plan B Club, specializing in asset protection and international migration issues, degrees from University of Cape Town with postgraduate degrees in Economics and History, published in a variety of international journals, including the Journal of Microfinance, Small Enterprise Development, and Environment and Urbanization, as well as the South African press, including the Cape Times, New Internationalist, Cape Argus, and Mail and Guardian; “Freedom Act: Washington Killed Privacy”; http://www.valuewalk.com/2015/06/freedom-act-privacy/ -JRS) Back in my activist days, an insightful colleague once pointed out that: “The most dangerous moment of any movement for justice is when you seem to be succeeding.” His point was this: When your adversary is more powerful than you are, they are in a position to define what “success” means — and will probably do so at your cost. For example, we were trying to get African and Asian city authorities to grant land titles to households living in “slums,” so they could invest in their homes without fear of eviction. Often, opportunistic politicians would announce a minor policy tweak with great fanfare, as if they had “granted” our wishes. Meanwhile, nothing really changed. I found myself thinking of that last week during the hoopla surrounding the passing of the USA Freedom Act, which is supposed to have ended the bulk collection of our private telephone call data by the government's spy agencies. Freedom Act: Plus Ça Change…Your privacy is no safer from government abuse today than it was last week, before Congress passed the USA Freedom Act. As one civil liberties lawyer told me: “No one should mistake this bill for comprehensive reform. The bill leaves many of the government's most intrusive surveillance powers untouched.” You can't let your guard down now, I'm afraid. Under the National Security Agency's “bulk metadata” program, which the USA Freedom Act has modified, the NSA collected information on all Americans' calls — including phone numbers called as well as dates, times and duration — without a warrant. The NSA argued that the data was “relevant” to a national security investigation under Section 215 of the USA Patriot Act because terrorists sometimes used telephones. Because the NSA didn't know which calls were from terrorists, all phone calls were considered “relevant.” The USA Freedom Act requires government to obtain a warrant before accessing call data in the hands of private companies. Custody of the metadata itself will transition from the NSA to the phone companies. The government will still be able to access it via specific queries of “a person, entity, account, address or device.” Most records will be stored for fewer than 18 months, not five years or more. But section 215 of the Patriot Act was only one of a number of overlapping surveillance authorities. The USA Freedom Act will leave the government with a range of powerful surveillance tools. These include: Section 702 of the Foreign Intelligence Surveillance Act Amendments Act (FISA): Unlike the NSA's metadata surveillance program, collection under FISA's Section 702 captures the content of communications. This could include emails, instant messages, Facebook Inc messages, Web browsing history and more. Section 702 has been used by the NSA to justify mass collection of data directly from the physical infrastructure of communications providers. Executive Order 12333: Issued by President Reagan in 1981, it allows the executive branch to spy on foreigners with no regulation by Congress. Millions of innocent foreigners' communications are collected, including any containing Americans' communications. Pen Registers: These allow the government to collect “dialing, routing, addressing or signaling information,” including telephone numbers dialed and Internet metadata, such as IP addresses and email headers. FISA's Business Records Provision: This allows the government to obtain business records from transportation carriers and storage facilities. The government routinely considers private communications to be “business records.” An ECPA “D Order”: Under Section 2703(d) of the Electronic Communications Privacy Act (ECPA), the government can get a court order for information from communications providers about their customers, including the sorts of metadata the government gets with Section 215. The government must provide “specific and articulable facts showing that there are reasonable grounds to believe that … the records or other information sought, are relevant and material to an ongoing criminal investigation.” National Security Letters (NSLs): Similar to subpoenas, NSLs allow intelligence agencies to collect records from telecommunications providers, financial institutions, credit reporting bureaus, travel agencies and other entities. Nearly all NSLs include gag orders, which prevent the target from telling anyone they have been served with an NSL. The government can use NSLs to collect much the same information as Section 215. NSLs have been routinely misused. Administrative Subpoenas: Many federal agencies have the authority to issue subpoenas for customer records in their normal course of business. These authorities are extremely widespread, comprising 335 different statutes by one count. All of these authorities continue to exist as before. Perhaps worst of all, however, an Obama administration official confirmed last Wednesday that the government would ask the secretive Foreign Intelligence Surveillance Court to certify that the NSA's Section 215 bulk records collection was part of an “ongoing” investigation, and could therefore continue indefinitely … until the “investigation” into terrorism is someday over. Freedom Act: The Law Isn't on Your Side Besides almost certainly being unconstitutional, the government's abuse of these surveillance powers since 2001 is both illegal and useless. A federal appeals court ruled the NSA's bulk metadata program illegal last month, saying most members of Congress never intended for the Patriot Act to be interpreted that way. Moreover, a presidential panel concluded that the information gleaned from the NSA's spying on Americans “was not essential to preventing [terrorist] attacks and could readily have been obtained in a timely manner using conventional [court] orders.” The law wasn't on your side under the Patriot Act, and it isn't on your side now. You need to continue to take steps to secure your own privacy and sovereignty from these outrages … and I will continue to help you to do so. Federal domestic surveillance is running rampant Green, April, 2015 (Jason Young Green, JD Candidate 2016, UNC Chapel Hill, Certified Information Privacy Professional, “Abcrailing Against Cyber Imperialism: Discussing The Issues Surrounding The Pending Appeal Of United States V. Microsoft Corp.”; North Carolina Journal of Law & Technology, Online Edition; 16 N.C. J.L. & Tech. On. 172 – JRS) Privacy rights of the individual are constantly at war with effective law enforcement principles. Alexander, as head of the NSA, was entrusted with the duty to protect the United States from terrorist threats both at home and abroad. The steps that he took to analyze and act on data that he collected that led to the reduction of U.S. soldier deaths are noteworthy. n54 However, the government did not fail in its mission to "collect it all" in its execution, but in its oversight. n55 Gen. Alexander frequently points out that the NSA collection programs are subject to oversight by Congress as well as the U.S. Foreign Intelligence Surveillance Court. n56 However, the proceedings of these two bodies are secret. n57 This lack of transparent oversight has given the NSA a wide berth in its operations, in violation of the FIPPS that both EU and U.S. privacy frameworks are based on, specifically the fundamentals of Notice and Consent. n58 By having secret FISA court orders and ECPA warrants that are rarely, if ever, unsealed, citizens targeted by NSA are never notified of the invasion of their privacy, and thus have no control over it. n59 It is this lack of oversight that has allowed the NSA collection mechanism to run rampant and is precisely what must be addressed. SQ laws allow federal domestic surveillance without any consideration for 4th amendment protections Blass 2015 (Megan; J.D. Candidate 2015, University of California, Hastings College of the Law; “The New Data Marketplace: Protecting Personal Data, Electronic Communications, and Individual Privacy in the Age of Mass Surveillance Through a Return to a Property-Based Approach to the Fourth Amendment”; Hastings Constitutional Law Quarterly; 42 Hastings Const. L.Q. 577 – JRS) Domestic and International Surveillance Regulations Do Not Protect the Public Because They Require Less Stringent Standards than the Fourth Amendment The National Security Agency’s surveillance programs are typically subject to either ECPA or FISA.25 Generally speaking, ECPA applies to domestic electronic surveillance or investigation, while FISA applies when the government is gathering intelligence on foreign targets.26 These statutes purport to place limitations on government surveillance. However, these statutes actually operate to reduce the burden the government must satisfy in order to engage in the type of investigation for the purposes of criminal prosecution generally governed by the Fourth Amendment.27 Both statutes allow the government to conduct, what I argue should constitute, searches under the Fourth Amendment, in the absence of Fourth Amendment requirements including probable cause or the lower standard of reasonable suspicion and in the absence of a warrant.28 Law enforcement should not be allowed to avoid the Fourth Amendment through the use of FISA.29 While, in theory, these statutes regulate government surveillance of electronic communications and personal data, they provide little protection without compliance from agencies, such as the National Security Agency. There’s no solution in sight: the district court in Klayman ruled that some NSA domestic surveillance violates the 4th amendment, but it will be an uphill battle on appeal Setty, 2015 (Sudha, Professor of Law and Associate Dean for Faculty Development & Intellectual Life, Western New England University School of Law; Harlan Fiske Stone Scholar from Columbia Law School and A.B. in History, concentration in comparative civil rights, with honors from Stanford University; Stanford Journal of International Law; Winter 2015; 51 Stan. J Int'l L. 69; “Surveillance, Secrecy, and the Search for Meaningful Accountability” – JRS) Klayman offers some reason for optimism among civil libertarians: Not only did an Article III court decide a post-9/11 abuse of power case on its merits, but that decision held that the NSA surveillance at issue was likely in violation of the Fourth Amendment. Whether appellate courts will follow the line of reasoning in Klayman as opposed to that of Clapper II and Smith, however, remains unclear. n99 It is also difficult to predict how the U.S. Supreme Court will respond when confronted with this matter. On the one hand, individual members of the Court have expressed skepticism as to the appropriateness of judicial review in matters of national security-related surveillance. n100 On the other, the Court as a whole has recently shown significant interest in rethinking the parameters of government surveillance. In the 2012 case United States v. Jones, the Court found that warrantless GPS tracking of an individual's movements for an extended period of time contravened the parameters set in Smith. n101 The two concurrences in Jones further suggested reworkings of the Smith framework in light of changing technology and an increased need for robust privacy protection given the government's ability to access telephonic data with ease. n102 The opinion in Klayman focused on Jones to illustrate the need to rethink the nature and scope of privacy given the vastly different use of technology of today as compared to the 1970s, when Smith was decided. n103 In mid-2014, the Supreme Court followed this rights-protective line of reasoning when it decided Riley v. California, holding that warrantless searches of the electronic contents of an arrestee's cell phone were in [*88] violation of the Fourth Amendment protections against unreasonable search and seizure. n104 These rights-protective perspectives - offered by justices with different political and theoretical perspectives - may offer a preview of a significant jurisprudential shift not only in hearing securityrelated cases on their merits, but in finding for plaintiffs alleging privacy and civil liberties infringements. However, the historically deferential attitude of courts toward matters of national security, a stance that has only compounded in the post-9/11 context, suggests that this may continue to be an uphill battle for civil libertarians. n105 District courts are split Setty, 2015 (Sudha, Professor of Law and Associate Dean for Faculty Development & Intellectual Life, Western New England University School of Law; Harlan Fiske Stone Scholar from Columbia Law School and A.B. in History, concentration in comparative civil rights, with honors from Stanford University; Stanford Journal of International Law; Winter 2015; 51 Stan. J Int'l L. 69; “Surveillance, Secrecy, and the Search for Meaningful Accountability” – JRS) Article III courts have consistently been wary of wading into the debate over surveillance, almost always dismissing cases in the post-9/11 context on procedural or secrecy grounds, n84 despite n85 the net effect of precluding even those individuals with concrete evidence that their privacy and civil liberties had been infringed from having their grievances heard. n86 Although the Snowden disclosures have given more purchase to plaintiffs challenging data collection and surveillance, some Article III courts continue to find that plaintiffs have no grounds to stop the NSA's data and metadata collection, retention, and analysis. The case of Clapper v. Amnesty International, n87 decided in early 2013, prior to the Snowden disclosures, exemplifies the traditional lack of relief available to plaintiffs in Article III courts. In Clapper, plaintiffs, including attorneys, non-profit humanitarian organizations, and journalists, alleged that their ability to communicate with and advise overseas clients and sources was severely compromised by the fact that their phone calls were likely being surveilled by the NSA or other U.S. government agencies. The United States Supreme Court dismissed plaintiffs' suit on standing grounds, holding that plaintiffs "cannot manufacture standing merely by inflicting harm on themselves based on their fears of hypothetical future harm that is not certainly impending." n88 Immediately after Snowden's June 2013 disclosures that the telephony data of all U.S. persons is being systematically collected and stored by the NSA, the ability of plaintiffs to clear the procedural hurdle of standing improved, since the "fears of hypothetical future harm" that allowed the Clapper majority to dismiss that case were no longer hypothetical, but publicly known as fact. However, the question of whether plaintiffs were granted any substantive relief is yet to be determined, since district courts have come to differing conclusions on the question of the metadata collection program's constitutionality. [*86] In American Civil Liberties Union v. Clapper ("Clapper II"), filed days after the initial Snowden disclosures, n89 the ACLU and other organizations claimed that the NSA's metadata collection and retention program violated their First and Fourth amendment rights by inhibiting their ability to speak freely with clients and by unreasonably searching and seizing their communications. n90 Judge Pauley of the Southern District of New York rejected these claims, holding that although the metadata "if plumbed ... can reveal a rich profile of every individual," n91 under the long-standing precedent of Smith v. Maryland, n92 plaintiffs had no reasonable expectation of privacy over their telephony metadata. Further, Judge Pauley accepted the government's position that the metadata was necessary in disrupting several terrorist threats, and that such counterterrorism work could not have occurred without the vast trove of data available through the NSA Metadata Program. n93 With similar facts and claims, n94 Judge Leon of the District Court of the District of Columbia in Klayman v. Obama differed from the Clapper II court and concluded that the constitutionality, statutory authority and efficacy of the NSA's bulk metadata collection program is, at best, questionable. n95 Judge Leon used these distinctions of both scope and depth of surveillance to establish that the NSA metadata program constituted a search for Fourth Amendment purposes. n96 In a particularly remarkable analysis, Judge Leon reasoned that the continuously expanding use of technology in the everyday lives of most Americans justified a greater expectation of privacy over information that is shared electronically, not an ever-shrinking realm of protection over personal privacy. n97 Having established that a search occurred, Judge Leon considered the plaintiffs' request for preliminary injunctive relief, finding that there was a [*87] significant likelihood that the plaintiffs would succeed in demonstrating that the surveillance and searches were unreasonable and, therefore, unconstitutional. To do so, he touched upon the intrusive nature of the search and, differing significantly from Judge Pauley in Clapper II, found that the government had not made a showing that the NSA Metadata Program was necessary to the government's counterterrorism efforts. n98 SCOTUS review is inevitable Farivar 2015 (Cyrus, senior business editor at Ars Technica, has reported for The Economist, Wired, The New York Times, Deutsche Welle English, the Canadian Broadcasting Corporation, Public Radio International, National Public Radio, the Australian Broadcasting Corporation, B.A. in Political Economy from the University of California, Berkeley and M.S. from the Columbia University Graduate School of Journalism; January 1, 2015; http://arstechnica.com/tech-policy/2015/01/if-the-supreme-court-tackles-the-nsa-in2015-itll-be-one-of-these-five-cases/ -- JRS) Roughly a year and a half since the first Snowden disclosures, there's already been a judicial order to shut down the National Security Agency's bulk metadata collection program. The lawsuit filed by Larry Klayman, a veteran conservative activist, would essentially put a stop to unchecked NSA surveillance. And at the start of 2015, he remains the only plaintiff whose case has won when fighting for privacy against the newly understood government monitoring. However, it's currently a victory in name only— the judicial order in Klayman was stayed pending the government’s appeal. Klayman v. Obama is only one of a number of notable national security and surveillance-related civil and criminal cases stemming fully or partially from the Snowden documents. In 2014, a handful of these advanced far enough through the legal system that 2015 is likely to be a big year for privacy policy. One or more could even end up before the Supreme Court. "I think it's impossible to tell which case will be the one that does it, but I believe that, ultimately, the Supreme Court will have to step in and decide the constitutionality of some of the NSA's practices," Mark Rumold, an attorney with the Electronic Frontier Foundation, told Ars. Rumold is one of the attorneys in First Unitarian Church, a case that is challenging government surveillance much like Klayman. Along with that pair, headline watchers should set alerts for cases such as American Civil Liberties Union (ACLU) v. Clapper, United States v. Moalin, and United States v. Muhtorov. Not only are there several other related cases that will likely be influenced by these decisions, but those five cases represent the strongest and most direct legal challenges to the current NSA surveillance state. Contention Two – The End Of Freedom Blanket collection of information is like a general warrant – gather now, look for criminality later Barnett 2015 (Randy, Carmack Waterhouse Professor of Legal Theory, Georgetown University Law Center. Director, Georgetown Center for the Constitution; “Security Vs. Freedom: Contemporary Controversies: The Thirty-Third Annual Federalist Society National Student Symposium On Law And Public Policy -- 2014: Why The NSA Data Seizures Are Unconstitutional”; Harvard Journal of Law & Public Policy; 38 Harv. J.L. & Pub. Pol'y 3; Winter 2015 – JRS) It is also worth remembering that both the English Whigs and the American Founding generation thought that the seizure of papers for later search was an abuse distinct from, but equivalent to, the use of general search warrants--which is why "papers" was included in the Fourth Amendment in addition to "effects" or personal property. n15 As University of San Diego School of Law Professor Donald Dripps has shown in a recent article, "at the heart of Whig opposition to seizing papers was the belief that any search of papers, even for a specific criminal item, was a general search. It followed that any warrant to sift through documents is a general warrant, even if it is specific to the location of the trove and the item to be seized." n16 The seizure of one's papers for later perusal was thought to be closely akin to searching through a person's mind to assess his thoughts. Seize first, then search for evidence of criminality, was considered to be the epitome of an abuse of power. n17 Putting such information permanently in the hands of government for future use is an invitation to restrict the liberties of the people whenever such restrictions become politically popular. [*7] For example, gun rights advocates have long opposed firearms registration because the brute fact that the government does not know where the guns are makes it much more difficult to confiscate them in the future. n18 Not only does this illustrate the practical danger to constitutional liberties posed by the government simply possessing vast information about our activities and associations for later search. The trove of phone and email metadata to which the NSA now has access would make gun registration unnecessary as the government would already possess enough information to identify most gun owners. n19 This information grab reverses the fundamental premise of “government by the people” and turns the people into subjects of our rulers Barnett 2015 (Randy, Carmack Waterhouse Professor of Legal Theory, Georgetown University Law Center. Director, Georgetown Center for the Constitution; “Security Vs. Freedom: Contemporary Controversies: The Thirty-Third Annual Federalist Society National Student Symposium On Law And Public Policy -- 2014: Why The NSA Data Seizures Are Unconstitutional”; Harvard Journal of Law & Public Policy; 38 Harv. J.L. & Pub. Pol'y 3; Winter 2015 – JRS) [*3] Due to the unauthorized leaks of classified information, we have come to learn that the National Security Agency (NSA), an executive branch arm of the U.S. military, has established several data collection programs. In this article, I am not going to get into the details of these programs. Instead, I will limit my focus to what I consider to be the serious constitutional problem with any such program, regardless of the details: the fact that the NSA is demanding that private companies, with which virtually all Americans contract to provide their voice communications, turn over the records of every phone call that is made on their systems. n1 This metadata is then stored on NSA super computers for later analysis. n2 In this article, I am not going to address the legality of this program under existing statutes. Jim Harper of the Cato Institute and I have argued in an amicus brief that the NSA data collection program is illegal because it is not authorized by Section 215 of the Foreign Intelligence and Surveillance Act as it was modified by the USA PATRIOT Act. n3 Section 215 of the PATRIOT Act allows the Foreign Intelligence Surveillance Court (FISC) to issue orders requiring the production of tangible things upon satisfactory application by the FBI. The statutory language specifies that an application for a Section 215 order must include "a statement of facts showing that there are reasonable grounds to believe that the tangible things sought are relevant to an authorized investigation . . . ." n4 Because we maintain that Section 215 orders must be "relevant" to an already existing investigation, in our brief we contended that orders for the seizure of bulk metadata on every American for future analysis to uncover evidence of wrong doing are not authorized by the statute and are therefore illegal. n5 So far, however, the two federal district court judges who have considered challenges to the program in the Southern District of New York and in the District of Columbia have both held that, because Congress has not waived its sovereign immunity to allow the legality of Section 215 orders to be challenged in federal court, federal courts lack jurisdiction to hear a statutory challenge. n6 For this reason, this matter may need to be addressed by Congress. But these same two judges also held that citizens have standing to bring constitutional challenges to the collection of the telephone companies' records of their phone calls. n7 So my focus here will be limited to the constitutional issue raised by these blanket seizures of the private data on all Americans. Although the only surveillance program that has been challenged thus far concerns phone records, n8 the principle offered to support this data seizure applies as well to all other business records of our dealings, including our credit card transactions. Indeed, in upholding the constitutionality of the program, Judge William Pauley of the Southern District of New York cited cases that held that "an individual has no constitutionally protected expectation of privacy" in bank records, records given to an accountant, subscriber information provided to an internet service provider, and information from a home computer [*5] that is transmitted over the Internet or by email. n9 Imagine the chilling effect on liberty if everyone knew that the government is in possession of all this data about their private transactions on its super computers. The relationship between the citizens of the United States and their supposed agents or servants in government would be fundamentally reversed, turning We the People into mere subjects of our rulers. So there is a lot more at stake here than just this particular bulk data seizure program. With the challenge to the Affordable Care Act, we not only wanted to stop Obamacare from being implemented-which sadly we failed to do--we also wanted to defeat the limitless constitutional arguments that were being offered in its defense. In this effort, I am pleased to say we succeeded. n10 Now , we need to think very hard about whether these blanket data seizure programs comport with the Fourth Amendment before, not after, the government decides it needs to seize data about every facet of our personal lives. Unrestrained security apparatus threatens permanent loss of American freedom Glennon 2014 (Michael J.; Professor of International Law, Fletcher School of Law and Diplomacy, Tufts University; Harvard National Security Journal; 5 Harv. Nat'l Sec. J. 1; “National Security and Double Government”; Professor of International Law, Fletcher School of Law and Diplomacy, Tufts – JRS) There is validity to this intuition and no dearth of examples of the frustration confronted by Madisonians who are left to shrug their shoulders when presented with complex policy options, the desirability of which cannot be assessed without high levels of technical expertise. International trade issues, for example, turn frequently upon esoteric econometric analysis beyond the grasp of all but a few Madisonians. Climate change and global warming present questions that depend ultimately upon the validity of one intricate computer model versus another. The financial crisis of 2008 posed similar complexity when experts insisted to hastily-gathered executive officials and legislators that—absent massive and immediate intervention—the nation’s and perhaps the world’s entire financial infrastructure would face imminent collapse.516 In these and a growing number of similar situations, the “choice” made by the Madisonians is increasingly hollow; the real choices are made by technocrats who present options to Madisonians that the Madisonians are in no position to assess. Why is national security any different? It is different for a reason that I described in 1981: the organizations in question “do not regulate truck widths or set train schedules. They have the capability of radically and permanently altering the political and legal contours of our society.”517 An unrestrained security apparatus has throughout history been one of the principal reasons that free governments have failed. The Trumanite network holds within its power something far greater than the ability to recommend higher import duties or more windmills or even gargantuan corporate bailouts : it has the power to kill and arrest and jail , the power to see and hear and read peoples’ every word and action, the power to instill fear and suspicion, the power to quash investigations and quell speech, the power to shape public debate or to curtail it, and the power to hide its deeds and evade its weak-kneed overseers. It holds, in short, the power of irreversibility. No democracy worthy of its name can permit that power to escape the control of the people. NSA surveillance creates a dangerous potential for tyranny Brand, 2015 (Jeffrey S., Dean and Professor Emeritus and Chairman of the Center for Law and Global Justice, University of San Francisco School of Law. Dean, University of San Francisco School of Law, 1999-2013. A.B., University of California, Berkeley, 1966; J.D., University of California, Berkeley, 1969; “Eavesdropping on Our Founding Fathers: How a Return to the Republic's Core Democratic Values Can Help Us Resolve the Surveillance Crisis”; Harvard National Security Journal; 6 Harv. Nat'l Sec. J. 1 – JRS) Indeed, the ability to participate in and affect the political debate and process lies at the heart of Lesson Five. Throughout the FISA debates, this fact was stated dramatically over and over again, sometimes in dire tones by people with access to America’s deepest held secrets such as Senator Frank Church, whose committee reports in the wake of Watergate remain seminal sources to this day. His analysis is stark, declaring that surveillance powers could: at any time be turned around on the American people, and no American would have any privacy left, such is the capability to monitor everything: telephone conversations, telegrams, it doesn’t matter. There would be no place to hide . . . The NSA could “impose total tyranny [and] we must see to it this agency and all agencies that possess this technology operate within the law and under proper supervision, so that we never cross that abyss. That is the abyss from which there is no return.211 Senator Muskie put it more diplomatically at the very first hearing after the Watergate break-in: In our democracy, the decision to invade the privacy of an American citizen or of anyone living in America must be made with a full regard for the constitutional rights which could thus be jeopardized. Such a decision should not be made lightly or arbitrarily by the Executive Branch . . . . It is government’s first responsibility to safeguard the rights and liberties of its citizens.212 Representative Drinan perhaps put it most cogently: It should be remembered too that the liberty of the people is at least as important as the marginal increment in intelligence information which we acquire through the inherently indiscriminate method of electronic surveillance. As the District Judge in the Pentagon Papers case cogently observed: “The security of the nation is not at the ramparts alone. Security also lies in the value of our free institutions.” 213 Urgent court action key to stop democracy’s extinction Brand, 2015 (Jeffrey S., Dean and Professor Emeritus and Chairman of the Center for Law and Global Justice, University of San Francisco School of Law. Dean, University of San Francisco School of Law, 1999-2013. A.B., University of California, Berkeley, 1966; J.D., University of California, Berkeley, 1969; “Eavesdropping on Our Founding Fathers: How a Return to the Republic's Core Democratic Values Can Help Us Resolve the Surveillance Crisis”; Harvard National Security Journal; 6 Harv. Nat'l Sec. J. 1 – JRS) Finally, in 2013, the FISA court received an additional layer of insulation from review when the Supreme Court decided Clapper v. Amnesty International. n82 In Clapper, the Court rejected an opportunity to rule on the constitutional merits of many of the post-9/11 changes to FISA by holding that the plaintiffs lacked standing to bring the action. In a 5-4 opinion authored by Justice Alito, the Court held that plaintiffs' fear that they would be subject to surveillance in the future was "too speculative" to establish standing. n83 Ultimately, new laws, amendments to FISA, secret rulings of the FISA court, and Clapper are partially responsible for landing us where we are today--in a surveillance environment in which it is possible for the government to collect data on essentially every phone call made in the United States. In fact, in light of all of these changes, it would be unfair to place all of the blame on the drafters of the original FISA statute for the Act's inability to weather the 9/11 storm and the concurrent technology revolution. Nonetheless, the reality is that even without the Patriot Act, the FAA, and Clapper, FISA was destined to implode because of fundamental flaws in its structure. FISA may have been ambushed by subsequent events but it is not blameless for its own demise. FISA may no longer be recognizable relative to its initial incarnation, but the seeds of its destruction in its original structure surely are and they shed light on the lessons that FISA teaches for the future. It is to those flaws and those lessons that we now turn. Time is of the essence. After the Supreme Court's decision in Clapper, one commentator wrote: "Absent a radical sea change from the courts, or more likely intervention from the Congress, the coffin is slamming shut on the ability of private citizens and civil liberties groups to challenge government counterterrorism policies." n84 That ominous prognosis punctuates the urgency of learning from the past if we are to halt the march toward democracy's extinction, a march led by the very institutions that the Framers created to sustain it. Insert privacy and tyranny impacts (Insert democracy/war/modeling impact?) Contention Three – Executive Domination Security justifications edge out the judiciary and disrupt checks and balances – and the executive grabs more unilateral control Husain 2014 (Waris Husain, Esq., adjunct professor at Howard University School of Law, faculty adviser for Goler Teal Butcher International Moot Court Team, currently pursuing his S.J.D. at American University Washington College of Law, writing a comparative dissertation focusing on the Supreme Courts of the United States, Pakistan and India, LL.M. in international human rights and international business from Washington College of Law, JD Howard University, BA in government from the College of William and Mary; “Surveillance And Law Enforcement: Tools In The Fight Against Terror In A Comparative Study Of The United States And Pakistan”; 21 ILSA J Int'l & Comp L 25; ILSA Journal of International & Comparative Law, Fall 2014 – JRS) A. Conclusion The continued proliferation of terrorism and the growing trend of governments overriding their citizens' protections for a fair trial and privacy require new methods that both ensure a nation's safety and uphold its humanitarian, constitutional, and international values. The General Assembly of United Nations affirmed that, [R]espect for human rights and the rule of law [is] the fundamental basis for the fight against terrorism . . . . [Member States] reaffirm[ed] that the promotion and protection of human rights for all and respect for the rule of law are essential to all components of the Strategy, and recognized that effective counterterrorism measures and the protection of human rights are not conflicting goals, but complementary and mutually reinforcing. n212 [*57] Therefore, it is incumbent upon nations to deal with terrorism in a similar manner as other long running domestic criminal problems. Nations like the United States and Pakistan must try to strike the fine balance between security and freedom. In the alternative, if one is to concede the invocations of the emergency rule that legitimize wholesale abrogation of fundamental civil rights under certain circumstances, three phenomena will occur concurrently, as they have been in the United States and Pakistan recently. The executive branch will expand categorizations of "national security" to be able to exclusively, secretively, and unilaterally control more parts of the government, thereby disturbing the system of checks and balances. The judicial branch will continue to both compromise its own power by deferring to the executive branch, and lose institutional power through the passage of antijudiciary and anti-terrorism legislation like the PATRIOT Act. Lastly, if current trend concerning the suspension of constitutional protections for terrorism continues, it will challenge the jurisprudence developed for over 200 years concerning the right of citizens to privacy, dignity, information, and a fair trial. These phenomena have led to a breakdown of limitations for government officials wishing to monitor their citizens. In the United States, the warrant requirement was required for electronic surveillance but this prerequisite approval from a judge vanished for certain citizens with the passage of laws like the PATRIOT Act and the PAA. Additionally, anti-terrorism legislation has led to an increased scope of monitoring by intelligence gathering institutions such as the CIA, even though the Church Committee found that these institutions could not be entrusted with the power to intrude on citizens' right to privacy. In Pakistan, while there have been warrant requirements for physical searches, there was an absence of legislation concerning modem electronic surveillance. The Fair Trial Act attempts to pull surveillance from the shadows into the rule of law by requiring intelligence officials and police to seek judicial approval before wiretapping of any suspect. However, critics argue that the Act goes too far in granting intelligence agencies, known for their political manipulation and brutal activities, the right to impede the right to privacy for invalid reasons. Critics of the criminal enforcement model argue that civilian courts are ineffective at battling terrorism because they have standards of proof that cannot be met due to the nature of terrorism. However, the illegal practices of intelligence agencies in Pakistan and the United States are a primary cause for the inability of courts to prosecute individuals. These suspects might in fact be terrorists, but have been subject to illegal treatment by the government, requiring most of the evidence collected against them to be set aside by the Court in accordance with constitutional protections. Therefore, when considering modem methods of electronic surveillance, one must [*58] keep in the mind the end goal of prosecuting suspects with admissible and legally obtained evidence. Giving in to secrecy means unchecked executive power Brand, 2015 (Jeffrey S., Dean and Professor Emeritus and Chairman of the Center for Law and Global Justice, University of San Francisco School of Law. Dean, University of San Francisco School of Law, 1999-2013. A.B., University of California, Berkeley, 1966; J.D., University of California, Berkeley, 1969; “Eavesdropping on Our Founding Fathers: How a Return to the Republic's Core Democratic Values Can Help Us Resolve the Surveillance Crisis”; Harvard National Security Journal; 6 Harv. Nat'l Sec. J. 1 – JRS) Lesson Five is certainly related to Lesson One (Pay Attention to the Core Values of the Republic). A government of the people, by the people, and for the people is a core value distilled by Lincoln and known to every schoolchild in America. As basic and obvious as it may seem, its relevance to questions about next steps in the surveillance debate cannot be overstated. The simple fact is that secrecy has bred distance between the government and the governed in profound ways. Indeed, we have arrived at a point in our history where government actions related to intelligence gathering are only discernable if an individual commits a criminal act—Edward Snowden being the prime current example. While people disagree about his motives and how he should be viewed and treated, few would argue with the fact that but for Snowden’s actions, the microscope under which we currently have placed our surveillance policies would not exist. That fact should tell us something: The government is acting in ways that do not respect Lincoln’s words, which we drill into our children as a first lesson in civics. The response to these assertions is that the threat is so extraordinary and the pace of technology so breathtaking that there is nothing that can or should be done to curb the government’s expanding surveillance practices. Yes, the argument goes, transparency in a democracy is important, and yes, the people should participate in the decision-making that affects their lives and rights, particularly the rights to expression and privacy, but those aspirations must give way if we are to protect our democratic values. Absolute secrecy and the pervasive gathering of information, aided by revolutionary technologies that keep us safe, the argument concludes, are necessary imperatives. In reality, to accept that argument is to end the argument. Such reductionist logic can only result in the unbridled, unchecked authority of the Executive Branch. It has the ring of the argument made during the Vietnam War that “we had to burn the village in order to save it.”198 It also assumes that the middle ground that FISA sought to achieve in 1978, and which hopefully we continue to search for today, does not exist. SQ surveillance chills congressional oversight of the executive – and an unchecked executive is the most dangerous of all human conditions Slobogin, March 2015 (Christopher, Milton Underwood Professor of Law, Vanderbilt University Law School, has been cited in almost 3,000 law review articles and treatises and more than 100 judicial opinions, including three U.S. Supreme Court decisions, Fulbright Scholar, J.D., LL.M. University of Virginia, A.B. Princeton University; “Symposium Issue: The Future of National Security Law: Standing and Covert Surveillance; Pepperdine Law Review; 42 Pepp. L. Rev. 517 – JRS) Perhaps most significantly, surveillance can compromise the political process even at the upper reaches of government. In March 2014, for instance, Senator Dianne Feinstein, chair of the Senate Select Intelligence Committee, complained about suspected (but unproven) CIA hacking into her office computers.125 Under Clapper, she would not have standing to bring a claim against the CIA. But in drafting emails and documents the Senator and her staff undoubtedly now think twice about what they are saying, especially about executive branch powers. This chilling effect is the kind of concrete impact that should lead to standing under political process theory. As Senator Feinstein stated in reaction to the incident, “[T]he CIA’s search may well have violated the separation of powers principles embodied in the U.S. Constitution, including the speech and debate clause. It may have undermined the constitutional framework essential to effective congressional oversight of intelligence activities or any other government function.”126 Along the same lines, commentators have speculated that members of Congress have curbed their efforts to regulate surveillance because of their fear of it.127 Some have even suggested that President Obama has been similarly constrained.128 Glenn Greenwald summarized the impact of secret panvasive surveillance as “the ultimate imbalance, permitting the most dangerous of all human conditions: the exercise of limitless power with no transparency or accountability.”129 In contrast, the types of suits that are typically stymied by standing requirements do not seek to protect the pillars of democracy. Claims alleging environmental damage or misuse of taxpayer funds raise important issues. But they are not aimed at protecting the integrity of the political process. Challenges to covert surveillance ultimately address the structure of government, not its products.130 Insert presidential powers bad impacts Plan: the Supreme Court of the United States should decide that warrantless collection of metadata from the electronic communications [and/or the content of electronic communications] of persons inside the United States violates the Fourth Amendment. Contention Four – the plan solves Fourth Amendment should extend to metadata – it is no different than preventing the government from sifting through the papers and personal effects protected inside your home Rasley, June 2, 2015 (George, CHQ Editor; “Can You "Compromise" On The Constitution?”; http://www.conservativehq.com/article/20390-can-you-compromise-constitution -- JRS) Former Virginia Attorney General Ken Cuccinelli and our colleague Mark Fitzgibbons have published a new op-ed on the Fourth Amendment in the Washington Examiner and it makes a point that has been all too overlooked in the debate over the future of the Patriot Act and other Obama Fourth Amendment abuses. "Americans do not and cannot trust government to be benevolent - nor should they. This is part of the reason our Constitution was written as it was in the first place. And this truth has been proven again and again in modern times, by so many recent official misdeeds and falsehoods coming from the mouthpieces of government - including prosecutorial misconduct that has had grave consequences and serious criminal penalties for its victims." What makes the Patriot Act debate stand out say Cuccinelli and Fitzgibbons is that some people in positions of responsibility deny that there is even a Fourth Amendment problem with arbitrarily collecting the metadata of all customer records from telephone companies. This mass collection is not merely an expansion of power beyond previous Fourth Amendment interpretation they say, it also sets dangerous precedent that all metadata is subject to government's taking without a warrant signed by a judge after a showing of probable cause that the law may have been violated. "Metadata" is everywhere observe Fitzgibbons and Cuccinelli. It runs our websites and social media pages and underlies the accounting and financial records of businesses. Government is already banging on both of these doors, with the Federal Communications Commission trying to seize control of the Internet and the Consumer Financial Protection Agency claiming blank-check authority over business records. A metadata "exception" to the Fourth Amendment could give government unchecked power over business, free speech, freedom of association, religious liberty and more. Making matters worse, they say more than 300 federal statutes authorize government agencies to issue "administrative subpoenas" unilaterally. Bypassing neutral judges and probable cause, government agencies may obtain private records of individuals and businesses, Fourth Amendment be damned. The Constitution's Bill of Rights was written in broad strokes in the context of the era. The First Amendment freedom of the press, naturally extended to radio, then television, neither of which existed when the Bill of Rights was adopted. The Fourth Amendment's protections of "papers and effects," which are private records and property, should naturally extend to metadata. The government's authority to reach metadata of persons and merchants should be read in this originalist context. To preserve the Fourth Amendment, certain reforms would be useful in clarifying it for the 21st Century, and correcting mistakes of judicial, executive and legislative interpretation. First, there should be no presumption that private records in the possession of private third parties may be taken by the government without probable cause. Also, all warrants - and that includes administrative subpoenas - should be issued only by neutral judges or magistrates to preserve the separation of powers inherent in the Fourth Amendment. Because warrants are issued in chambers, there is no danger in matters of national security conclude Cuccinelli and Fitzgibbons. This would seem to be the time for constitutionalists in Congress to strike and to rein-in the abuses of the Fourth Amendment that have gradually built-up like barnacles on our right to be secure in our persons, houses, papers, and effects, against unreasonable searches and seizures, but Congress it seems is headed in the wrong direction. Now that Senator Rand Paul has almost singlehandedly stopped the reauthorization of Section 215 of the Patriot Act and its metadata collection program the USA Freedom Act is being touted as the appropriate "compromise" between security and liberty. The problem with the USA Freedom Act is that rather than perfect the Fourth Amendment by clarifying its application to data, it would appear to legalize some of the abuses to which constitutionalists object -- particularly judge-less warrants. Historical and textual analysis supports the plan Milligan 2014 (Luke M.; law professor at Univ. of Louisville; “The Forgotten Right to Be Secure”; Hastings Law Journal, Vol. 65:713, Apr 2014; http://ssrn.com/abstract=2302850 – JRS) This Article locates a solution to the problem of regulatory delay in the text of the Constitution. 13 The Fourth Amendment has traditionally been interpreted by courts to safeguard a mere right to not be subjected to unreasonable searches or seizures.14 In other words, the Amendment is read to guarantee nothing beyond the right to be “spared” an unreasonable search or seizure.15 In 2013, the Supreme Court reaffirmed the conventional “spared” reading of the Fourth Amendment in Clapper v. Amnesty International.16 In Clapper, all nine Justices agreed that communications surveillance programs do not violate an individual’s Fourth Amendment rights before the government succeeds in “intercepting” or “acquiring” that individual’s communications.17 The Court made clear, once again, that the Fourth Amendment is not violated by attempts or threats to conduct an unreasonable search or seizure.18 Nor are an individual’s Fourth Amendment rights violated by the existence of a vast surveillance program that happens to spare the individual claimant. 19 The Fourth Amendment can be read, however, to safeguard more than a right to be “spared” an unreasonable search or seizure.20 The Amendment provides for “[t]he right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures.”21 Unlike its textual counterparts (such as “search,” “seizure,” and “unreasonable”), the “to be secure” phraseology remains largely forgotten: it is treated on mere occasion by commentators;22 and it has been left undefined in the case law.23 Historical and textual analyses of “to be secure,” however, suggest the existence of a Fourth Amendment right to “protection” against unreasonable searches and seizures, and perhaps a right to be “free from fear” against such government action. Support for these interpretations of “to be secure” rest in the dictionary definitions of “secure,”24 the structure of the Fourth Amendment,25 and founding-era discourse concerning searches and seizures, which regularly emphasized the harms attributable to the potentiality of unreasonable searches and seizures.26 Plan key to accountable democracy Barnett 2015 (Randy, Carmack Waterhouse Professor of Legal Theory, Georgetown University Law Center. Director, Georgetown Center for the Constitution; “Security Vs. Freedom: Contemporary Controversies: The Thirty-Third Annual Federalist Society National Student Symposium On Law And Public Policy -- 2014: Why The NSA Data Seizures Are Unconstitutional”; Harvard Journal of Law & Public Policy; 38 Harv. J.L. & Pub. Pol'y 3; Winter 2015 – JRS) III. CONCLUSION Let me conclude by noting that, without the recent leaks, the American public would have no idea of the existence of these programs, and it still cannot be certain of their scope. n72 Every day seems to bring new revelations about domestic surveillance by federal agencies. The secrecy of these surveillance programs is inconsistent with a republican form of government in which the citizens are the principals or masters, and those in government their agents or servants. For the people to control their servants, they must know what their servants are doing. Moreover, until these two district courts found--over the government's objections--that citizens had standing to challenge the constitutionality of the bulk-data seizure programs, n73 their constitutionality had been assessed solely in secret by the FISC that Congress established to scrutinize the issuance of particular business record subpoenas and warrants. n74 The secrecy of these programs, and the proceedings by which their constitutionality is being assessed, make it impossible to hold elected officials and appointed bureaucrats accountable. Internal governmental checks, and even secret congressional oversight, are no substitute for the sovereign people being the ultimate judge of their servants' conduct in office. But such judgment and control is impossible without the information that secret programs conceal. If these blanket seizures of privately-held data are upheld as constitutional, it would constitute an unprecedented legal and constitutional sea change. It is not a policy that should emerge from an advisory panel of judges to which the people are not privy. The American people are no longer the subjects of King George and his general warrants. Nor should we be subjected to these modern-day general warrants by those who are supposed to be our servants, not our masters. Fourth amendment protection is the last chance Blass 2015 (Megan; J.D. Candidate 2015, University of California, Hastings College of the Law; “The New Data Marketplace: Protecting Personal Data, Electronic Communications, and Individual Privacy in the Age of Mass Surveillance Through a Return to a Property-Based Approach to the Fourth Amendment”; Hastings Constitutional Law Quarterly; 42 Hastings Const. L.Q. 577 – JRS) The Relevant Statues Fail to Protect the Public When Agencies Exceed Their Authority Under the Statutes In Jewel v. National Security Agency, a lawsuit filed by the Electronic Frontier Foundation (“EFF”), a putative class of plaintiffs made up of AT&T customers sought legal and equitable relief for violations of federal constitutional rights, FISA, and ECPA.30 They alleged that the NSA, in cooperation with AT&T, engaged in the collection of communications passing through AT&T’s network at its Folsom Street Facility without satisfying the FISA and ECPA requirements of reasonable suspicion that the target is a foreign power or agent and reasonable suspicion that the information is relevant to a criminal investigation or to an investigation to protect against international terrorism and spying.31 Many of the EFF’s allegations are supported by credible evidence and have been admitted, to some extent, by the government.32 This lawsuit and other lawsuits filed over the last five years demonstrate that, regardless of the constitutionality of FISA or ECPA, FISA and ECPA provide little protection for the public when the government refuses to adhere to them.33 ECPA and FISA are supposed to limit the collection and use of personal data and electronic communications.34 The National Security Agency’s mass surveillance programs, conducted pursuant to ECPA and FISA, however, have swept up massive amounts of data and content that would be ancillary to any individual application for a wiretap. While this is a tremendous invasion of privacy, the crux of the constitutional issue is that limits on the use of that data and information have proven to be ineffective. So, not only is the NSA abrogating its front end responsibilities and obligations under ECPA and FISA in operation of its mass surveillance programs, the data and content are in turn being improperly utilized in ordinary criminal prosecutions without any fallback protection from the Fourth Amendment. Failure to comply with FISA and the ECPA is what makes the Court’s Fourth Amendment jurisprudence so critical. The Fourth Amendment is the legal protection of last resort where Congress’s statutory protections have failed. It is the ultimate backstop.35 Judicial hard power solves Setty, 2015 (Sudha, Professor of Law and Associate Dean for Faculty Development & Intellectual Life, Western New England University School of Law; Harlan Fiske Stone Scholar from Columbia Law School and A.B. in History, concentration in comparative civil rights, with honors from Stanford University; Stanford Journal of International Law; Winter 2015; 51 Stan. J Int'l L. 69; “Surveillance, Secrecy, and the Search for Meaningful Accountability” – JRS) “If the PCLOB is able to exert some degree of soft power in influencing national security decisionmaking, then the judiciary represents hard power that could be used to force the protection of civil liberties where it might not otherwise occur. The FISC should be reformed to include a public advocate lobbying on behalf of privacy concerns, making the process genuinely adversarial and strengthening the FISC against charges that it merely rubber stamps applications from the intelligence community. n190 Article III courts need to follow the lead of Judge Leon in Klayman in conceptualizing privacy as broad and defensible, even in a world where electronics-based communication is dominant and relatively easy for the government to collect. If the judicial defense of privacy were combined with the possibility of liability for violations of that privacy, it is likely that this would incentivize increased selfpolicing among the members of the intelligence community.” The executive and legislative branches can’t solve – they don’t have the capability and it would be a political reversal Setty, 2015 (Sudha, Professor of Law and Associate Dean for Faculty Development & Intellectual Life, Western New England University School of Law; Harlan Fiske Stone Scholar from Columbia Law School and A.B. in History, concentration in comparative civil rights, with honors from Stanford University; Stanford Journal of International Law; Winter 2015; 51 Stan. J Int'l L. 69; “Surveillance, Secrecy, and the Search for Meaningful Accountability” – JRS) In late March 2014, the Obama administration announced that it would propose legislation to dismantle the bulk collection program, leaving metadata in the exclusive possession of telecommunications companies and requiring FISC authorization prior to the NSA accessing the metadata. n48 The type and scope of legislative restrictions were debated extensively in 2014, but no bill was passed, leaving open the question of whether any additional legislative control will be exerted by Congress - if not, the status quo of executive control over the scope and intrusiveness of the program will continue. n49 Section 215 of the Patriot Act, arguably providing statutory authorization of the NSA Metadata Program, is set to expire in July 2015, a deadline that is sure to prompt legislative debate on whether to renew the program, curtail the authority granted to the administration, or eliminate the program altogether. The effect of any legislation in curtailing intrusive surveillance practices is yet to be seen, but the fact that the administration has already shifted its public willingness to improving protections of privacy and civil liberties and increase transparency when compatible with intelligence gathering interests, is noteworthy as well. n50 Assessment of whether those changes will be meaningful must wait for further developments, particularly as it may be institutionally and politically difficult for the president and Congress to shift course dramatically in the face of still-existing terrorist threats and the political pressure created by the public perception of those threats. n51 The primary message from the Obama administration since the Snowden disclosures has been that the administration itself is best suited to address whether and to what extent any recommended changes to NSA surveillance were appropriate, n52 and that the Snowden disclosures themselves have been unnecessary, [*80] illegal, and counterproductive to both the intelligence gathering programs themselves and the public discourse. n53 However, there is no indication that any of the accountability measures now being promoted by the administration would have existed or gained significant purchase but for the Snowden public disclosures. n54 The various institutional accountability mechanisms that currently exist within the executive branch do not appear to be equipped to consider concerns stemming from intelligence community insiders who have a fuller understanding than the public of the scope and nature of surveillance programs and who question the basic premise or constitutionality of programs such as the NSA metadata collection. To the contrary, there are indications that some within the NSA have actively attempted to avoid oversight by the Department of Justice. n55 The Office of the Inspector General for the NSA, appointed by and reporting to the director of the NSA, n56 is suited to deal with allegations of statutory and policy compliance violations, but not with a large scale systemic complaint about privacy and accountability such as that of Snowden. n57 Other potential avenues for accountability, such as the Office of the Inspector General for the Defense Department, are rendered irrelevant by the lack of information access. n58 In fact, the extreme secrecy that surrounded these surveillance programs, even within the administration, suggests that many existing executive branch mechanisms were, in the time before the Snowden disclosures, not engaged in effective oversight. Ext: Tyranny/Democracy Unfettered surveillance crushes freedom and privacy Brand, 2015 (Jeffrey S., Dean and Professor Emeritus and Chairman of the Center for Law and Global Justice, University of San Francisco School of Law. Dean, University of San Francisco School of Law, 1999-2013. A.B., University of California, Berkeley, 1966; J.D., University of California, Berkeley, 1969; “Eavesdropping on Our Founding Fathers: How a Return to the Republic's Core Democratic Values Can Help Us Resolve the Surveillance Crisis”; Harvard National Security Journal; 6 Harv. Nat'l Sec. J. 1 – JRS) To stress the importance of the relationship of the government to the governed is not a novel concept. The debates during the 1970s that led to FISA eloquently articulated its importance in the context of intelligence gathering. On June 23, 1975, Senator Tunney opened the Joint Hearings words that could have easily been uttered in 2014: The need for [these] hearings is overwhelming. Technological developments are arriving so rapidly and are changing the nature of our society so fundamentally that we are in danger of losing the capacity to shape our own destiny. This danger is particularly ominous when the new technology is designed for surveillance purposes, for in this case the tight relationship between technology and power is most obvious. Control over the technology of surveillance conveys effective control over our privacy, our freedom, and our dignity—in short, control over the most meaningful aspects of our lives as free human beings.199 Tunney’s position was clear: “Our concern (is that) that powerful new technologies . . . will destroy the Constitution’s delicate balance between the powers of the State and the rights of individuals.”200 of his Special Subcommittee on Science, Technology and Commerce of the Senate Judiciary Committee with Tunney demanded answers to the same questions that are relevant today: “We want to know who, if anyone, controls surveillance technology. And can we assure American taxpayers that their scarce dollars are being spent for their benefit and not for the creation of an Orwellian nightmare that will haunt them and their children for decades to come?”201 Moreover, Tunney’s frustration with the answers that had been forthcoming echoed the frustration that many feel today: “To date our investigations have been discouraging. No one seems to be in charge. New technologies are developed and seem to be allowed to speak without thought for their future social and political ramifications or for the ease with which they can be surreptitiously abused.” 202 Senator Tunney’s focus, as the name of his subcommittee implied, was on the impact of science and technology on democratic institutions. The conversation about the relationship of the government to the governed, however, extended well beyond those confines. It was also about the abuse of political power in the time of Watergate when, in Senator Kennedy’s words, a “blanket of fear” had swept the country.203 Senator Tunney, in his opening remarks quoted New York Times columnist James Reston, who had connected the dots between technology, power, and the protection of our right, as citizens, to participate in our democracy. Reston observed that “what has happened here over the last postwar generation is that the scientific capacity to use the arts of wartime espionage on private citizens has greatly expanded while the political capacity to control all this has actually declined.”204 In sum, the ultimate threat lay in the inability of citizens to participate in the decisions that affect their lives—a threat understood by those who supported and opposed S. 1566. Senator Kennedy, the bill’s chief proponent, who had split with Senator Tunney over the legislation, fully understood that the ability of a citizen to participate in our democracy was at stake. In November 1977, when he presented the Judiciary Committee’s report regarding S. 1566 to the full Senate, Kennedy spoke directly to his concerns about the “chilling effect” of surveillance on the populace at large, noting: The exercise of political freedom depends in large measure on citizens’ understanding that they will be able to be publicly active and dissent from official policy, within lawful limits, without having to sacrifice the expectation of privacy that they rightfully hold. Arbitrary or uncontrolled use of warrantless electronic surveillance can violate that understanding and impair that public confidence so necessary to an uninhibited political life.205 Neither Tunney nor Kennedy was tone deaf to the need for national security to protect the nation from foreign threats. Tunney acknowledged the importance of technology for national security purposes, even lauding it: “The arrival of the ‘electronic battlefield’ promises to increase our security against foreign aggressors and . . . can even become a technological aid in the pursuit of peace. [Indeed] law enforcement experts tell us that computers and electronics will . . . reduce the threats posed by organized crime and terrorists.”206 Panvasive surveillance risks tyranny Slobogin, March 2015 (Christopher, Milton Underwood Professor of Law, Vanderbilt University Law School, has been cited in almost 3,000 law review articles and treatises and more than 100 judicial opinions, including three U.S. Supreme Court decisions, Fulbright Scholar, J.D., LL.M. University of Virginia, A.B. Princeton University; “Symposium Issue: The Future of National Security Law: Standing and Covert Surveillance; Pepperdine Law Review; 42 Pepp. L. Rev. 517 – JRS) VI. CONCLUSION If panvasive surveillance cannot be challenged in court, it could well continue indefinitely despite its real threat to democratic institutions. Despite all of the hullabaloo occasioned by Edward Snowden's disclosures, the NSA appears to be continuing its large-scale surveillance and Congress has yet to propose serious limitations on it. n162 Although President Obama has put a few new restrictions on the NSA's programs, n163 to date there have been few judicial assessments of their constitutional status, and Clapper stands as an obstacle to challenges to all but the most obviously panvasive government actions. While the limitations on standing may make sense in some types of cases, challenges to panvasive surveillance should be treated differently than most other generalized claims. The separation of powers, Fourth Amendment, and First Amendment concerns about this surveillance go to the core of American democracy. The Court's decision in De Jonge v. Oregon, decided almost eight decades ago, makes the point in language that still resonates in this post-9/11 era: The greater the importance of safeguarding the community from incitements to the overthrow of our institutions by force and violence, the more imperative is the need to preserve inviolate the [*548] constitutional rights of free speech, free press and free assembly in order to maintain the opportunity for free political discussion, to the end that government may be responsive to the will of the people and that changes, if desired, may be obtained by peaceful means. Therein lies the security of the Republic, the very foundation of constitutional government. n164 Unwarranted surveillance broadly stifles fundamental liberties and undermines "the very foundation of constitutional government." Government is no longer functioning as the framers of the Constitution imagined it should if political discourse, individual creativity, outspokenness and non-conformity are not allowed to flourish. This state of affairs threatens rather than sustains the notion of separate but equal governmental powers, because it diminishes the vitality of the legislative function, improperly enhances the executive function, and ignores the judiciary's role as a regulator of law enforcement through determinations of cause. Standing doctrine, meant to ensure each branch of government is allowed to do its job, should not prevent courts from ensuring that the other branches actually do it. Strong and independent judiciary key to SOP and freedom Brand, 2015 (Jeffrey S., Dean and Professor Emeritus and Chairman of the Center for Law and Global Justice, University of San Francisco School of Law. Dean, University of San Francisco School of Law, 1999-2013. A.B., University of California, Berkeley, 1966; J.D., University of California, Berkeley, 1969; “Eavesdropping on Our Founding Fathers: How a Return to the Republic's Core Democratic Values Can Help Us Resolve the Surveillance Crisis”; Harvard National Security Journal; 6 Harv. Nat'l Sec. J. 1 – JRS) The importance of an independent judiciary to maintaining effective checks and balances necessary to sustain the Republic has often been cited from the likes of Thomas Jefferson to Andrew Jackson to modern figures who occupy varying positions along the political spectrum. Thomas Jefferson surely understood the need for an independent judiciary despite being the most vocal of the Founding Fathers about the dangers of judicial overreach: The dignity and stability of government in all its branches, the morals of the people and every blessing of society depend so much upon an upright and skillful administration of justice, that the judicial power ought to be distinct from both the legislative and executive and independent upon both, that so it may be a check upon both, as both should be checks upon that.140 Consider Jackson: “All the rights secured to the citizens under the Constitution are worth nothing, and a mere bubble, except guaranteed to them by an independent and virtuous Judiciary.”141 A bevy of modern commentators on all points on the political spectrum echo similar thoughts from the likes of Caroline Kennedy (“The bedrock of our democracy is the rule of law and that means we have to have an independent judiciary, judges who can make decisions independent of the political winds that are blowing”142) to President George W. Bush’s Solicitor General Ted Olson (“[I]n this country we accept the decisions of judges, even when we disagree on the merits, because the process itself is vastly more important than any individual decision. Our courts are essential to an orderly, lawful society [which] would crumble if we did not respect the judicial process and the judges who make it work.”143) to conservative columnist Charles Krauthammer (“Let us have a bit of sanity here. One of the glories of American democracy is the independence of the judiciary. The deference and reverence it enjoys are priceless assets and judicial independence and supremacy are necessary checks on the tyranny of popular majorities.”144). Taken together, the Federalist papers’ formula for the separation of powers demanded a precarious balance that required vigilance to maintain. Hamilton and Madison put it this way: “A dependence on the people is, no doubt, the primary control on the government; but experience has taught mankind the necessity of ‘auxiliary precautions.’”145 The separation of powers detailed in the new Constitution has proved to be effective and durable and the necessary auxiliary precautions that Hamilton and Madison envisioned. FISA, however, would prove to be otherwise. War powers justification threatens civil liberties indefinitely Barnett 2015 (Randy, Carmack Waterhouse Professor of Legal Theory, Georgetown University Law Center. Director, Georgetown Center for the Constitution; “Security Vs. Freedom: Contemporary Controversies: The Thirty-Third Annual Federalist Society National Student Symposium On Law And Public Policy -- 2014: Why The NSA Data Seizures Are Unconstitutional”; Harvard Journal of Law & Public Policy; 38 Harv. J.L. & Pub. Pol'y 3; Winter 2015 – JRS) II. WHAT ABOUT THE WAR POWER AND NATIONAL SECURITY? Some who defend the NSA surveillance programs would say that these programs should not be constrained by the Fourth and Fifth Amendments as domestic law enforcement is because they are exercises of the President's inherent power as Commander in Chief, or pursuant to the Congressional Authorization for Use of Military Force against the terrorist organizations that attacked us on September 11th. As such, the FISA procedures impose greater constraints on surveillance than was constitutionally required, even to the some defenders have said that it may well have been a mistake to in-elude [*17] the judiciary within these procedures rather than let the President take full political responsibility for the use and abuse of such measures. This objection is a formidable one, requiring serious analysis of the scope and limits of both the President's executive power and Congress's resolution authorizing the use of military force. But let me offer some preliminary thoughts. We can identify two legal models of constitutional powers. Call these the "domestic model" that empowers the government to protect the rights of its citizens from being violated by other members of the community; and the "wartime model" that is designed to protect the rights of American citizens from being violated by foreign enemy powers. Constitutional point of including judicial and Congressional oversight of such surveillance. Indeed, protections against abuses of these powers vary. Consider that our military may kill enemy combatants in the field without any "due process of law" and may indefinitely incarcerate prisoners of war for the duration of hostilities. Neither of these measures can constitutionally be done to American citizens domestically in time of peace or war. Nor can they be done to foreign Those who would justify these programs under the war power are abandoning the domestic model. Therefore, any reliance on Katz's "reasonable expectation of privacy" doctrine, or Smith's "third-party doctrine," are make-weights and merely confuse the issue. You cannot defend the program using the "third-party" doctrine and then, when pressed on that argument, change the subject to the war power. Any war power argument must stand and fall on its own. Perhaps for this reason, in its recent brief in the ACLU's challenge to the NSA data seizures, the government did not assert the war power and never denied that the Fourth Amendment applied to this situation. Although the nationals in peacetime. government does rely on a "national security" theory of why the program is "reasonable" under the Fourth Amendment, even if it could be said to be reasonable to seize the phone records of every American in the interest of national security, this rationale cannot justify using the NSA data for domestic law enforcement purposes--as we are learning may well have occurred--or any other comparable data collection program that is used for domestic law enforcement purposes. That such mission creep has already occurred, albeit in secret, underscores the danger of allowing such bulk data seizures in the first place. [*18] That defenders of this program will alternate between the domestic and war models of constitutional power signals that the conflict in which we are currently engaged does not fit neatly within either. The domestic model assumes that government is using its police powers to protect the rights of its citizens from others who are also members of the community. When citizens are accused of violating the rights of others that define the social compact, they deserve the benefit of the doubt before they are subjected to punishment. And we must be very careful to protect the civil liberties of the people from those in law enforcement who would abuse this police power to protect the public safety. The war model assumes that government is using its military power to protect the rights of its citizens from threats posed by foreign powers, in particular the armies of foreign governments. Unlike persons who are accused of domestic crimes, the soldiers of a foreign power are not entitled to the protections of the Fourth and Fifth Amendments. But these war powers do not stretch into perpetuity and are typically limited to a geographically confined theater of combat. Wars between nations have both a beginning and end, and extraordinary war powers expire with the conflict that necessitated their use. If the "cold war" between the United States and the USSR muddied the distinction If the battle ground is considered to include the territory of the United States, the enemy is hidden among the population, and such conflicts know no definitive end, adherence to the war power model threatens to completely subsume the protections of civil liberties afforded by the domestic model. In essence, the means of war are then turned against the People themselves to identify an enemy within. Even if some blending between the domestic and war powers of the Congress and the President, what is sometimes called the "long war" against radical Islamic NGOs has threatened its collapse. of the models is warranted and that is what the original FISA and Patriot Acts were attempting to accomplish, it makes it all the more essential that the government not exceed the limits Construing Section 215 as broadly as the government now urges, and the FISA court has ruled in its secret opinions, threatens the very balance between the wartime and domestic models that Congress was presumably trying to strike. For this reason, the courts should avoid the constitutional issues by [*19] holding that Section 215 of the PATRIOT Act does not authorize the bulk seizure of the telephone and defined by these statutes. email communications records of all Americans. AT SQ solves – surveillance still massive The feds still collect tons of domestic communications without a warrant Vladeck, June 1, 2015 (Stephen, Professor of Law at American University Washington College of Law, teaching and research focus on federal jurisdiction, constitutional law, and national security law, nationally recognized expert on the role of the federal courts in the war on terrorism, has been published in Harvard Law Review and the Yale Law Journal, B.A. summa cum laude with Highest Distinction in History and Mathematics from Amherst College, JD Yale Law School; “Forget the Patriot Act – Here Are the Privacy Violations You Should Be Worried About”; http://foreignpolicy.com/2015/06/01/section-215-patriot-act-expiressurveillance-continues-fisa-court-metadata/ -- JRS) But whatever the merits of the competing sides in this debate, the larger problem is that this conversation has missed the forest for a very small — and largely irrelevant — tree. In fact, from the perspective of individual privacy rights, the phone records program is much less problematic than the government’s other authorities to conduct mass surveillance under Executive Order 12333 and the 2008 FISA Amendments Act. And so, in focusing on how to “fix” Section 215, we’ve given short shrift to the far more significant problems raised by these other authorities — and, just as importantly, the broader lessons we should be taking away from the surveillance reform conversation that Snowden started. To understand the significance of these other authorities, it’ll help to describe their aims: Executive Order 12333, issued in 1981, is directed at the overseas interception of communications — both metadata and content — of non-citizens outside the United States, who, under a 1990 Supreme Court decision, categorically lack Fourth Amendment rights. The 2008 FISA Amendments Act was enacted to close a loophole that new technology had helped to create, where non-citizens outside the United States were nevertheless communicating through servers or other telecommunications infrastructure located stateside, which the government could not surveil under the executive order. Ordinarily, the government needs a warrant before collecting the content of domestic communications, one based upon a judge’s determination that there’s good reason to believe a particular individual either is engaged in the commission of a crime or is an agent of a foreign power. But Executive Order 12333 and the 2008 FISA statute, by focusing on individuals who fall outside the Fourth Amendment, capitalize on the lack of constitutionally required individualized assessments and instead allow the government to engage in bulk collection of such information — as if it were using an industrial vacuum cleaner to pick up individual particles of dirt. It’s easy to see how these authorities could cause diplomatic headaches (as, for example, with the contretemps surrounding U.S. surveillance of German Chancellor Angela Merkel’s cell phone). But most commentators have assumed that, at least legally, the validity of these programs turns on their overseas focus. After all, if the government is only targeting the communications of noncitizens outside the United States, what could possibly be the constitutional objection? The answer, we now know, has everything to do with technology. Although the government is only allowed to “target” non-citizens outside the United States, it is inevitable, given how it collects information under both of these regimes, that the communications of U.S. citizens and non-citizens lawfully present in the United States will also be collected, albeit “incidentally,” as the government puts it. After all, when thousands of unrelated emails and other electronic communications are bundled together in a packet that travels through an Internet switch that’s physically located in the United States (for the 2008 statute) or overseas (for Executive Order 12333), it’s simply not possible for the government to only collect the communications between non-U.S. citizens and leave the others untouched, any more so than it’s possible for a vacuum to segregate particles of dirt. To be sure, the U.S. government doesn’t dispute that it routinely collects the communications of U.S. citizens. Instead, it has argued that any potential for abuse is mitigated by so-called “minimization requirements” — procedural rules that require the relevant intelligence agency to take steps to avoid the improper retention and use of communications collected under these authorities. More than 300 federal statutes authorize domestic surveillance – the NSA is unchecked even post-Freedom Act Cuccinelli and Fitzgibbons, June 1, 2015 (Ken Cuccinelli is the former attorney general of Virginia. Mark Fitzgibbons is co-author with Richard Viguerie of The Law That Governs Government: Reclaiming The Constitution From Usurpers And Society's Biggest Lawbreaker; “NSA and how the Fourth Amendment stops government abuses”; http://www.washingtonexaminer.com/nsa-and-how-the-fourth-amendment-stops-governmentabuses/article/2565387 -- JRS) The debate surrounding the sunset of section 215 of the Patriot Act is a historic moment for the Fourth Amendment, which protects Americans from unreasonable searches and seizures of their persons, houses, papers and effects. Americans do not and cannot trust government to be benevolent — nor should they. This is part of the reason our Constitution was written as it was in the first place. And this truth has been proven again and again in modern times, by so many recent official misdeeds and falsehoods coming from the mouthpieces of government — including prosecutorial misconduct that has had grave consequences and serious criminal penalties for its victims. For example, when the Benghazi attack occurred, killing four American diplomats, the Obama administration lied and blamed a maker of an anti-Muslim film. And it is bad enough to see the IRS claiming to have "lost" emails and allowing hackers to steal private taxpayer information from its systems. But that seems tame compared to other malicious, targeted abuses of power against individuals, businesses and property. What makes the Patriot Act debate stand out is that some people in positions of responsibility deny that there is even a Fourth Amendment problem with arbitrarily collecting the metadata of all customer records from telephone companies. This mass collection is not merely an expansion of power beyond previous Fourth Amendment interpretation. It also sets dangerous precedent that all metadata is subject to government's taking without a warrant signed by a judge after a showing of probable cause that the law may have been violated. "Metadata" is everywhere. It runs our websites and social media pages and underlies the accounting and financial records of businesses. Government is already banging on both of these doors, with the Federal Communications Commission trying to seize control of the Internet and the Consumer Financial Protection Agency claiming blank-check authority over business records. A metadata "exception" to the Fourth Amendment could give government unchecked power over business, free speech, freedom of association, religious liberty and more. Making matters worse, more than 300 federal statutes authorize government agencies to issue "administrative subpoenas" unilaterally. Bypassing neutral judges and probable cause, government agencies may obtain private records of individuals and businesses, Fourth Amendment be damned. Those who know history know that government's power and lawlessness inevitably expands unless stopped or reversed. Magna Carta, which turns 800 on June 15, the Declaration of Independence and the United States Constitution are examples of documents that came about when people rebelled against government lawlessness and reclaimed legal authority over government. These documents are celebrated as monuments of freedom because they place government under control of the rule of law. They demonstrate that government is best when there is paramount law controlling its behavior — when there is a separation of powers, checks and balances and accountability to the people. Everyone understands the desire to keep America safe, but Americans are annoyed and troubled that some people in positions of power refuse even to acknowledge the Fourth Amendment problem with the Patriot Act and the collection of metadata. Section 215 is a drop in the bucket – SQ data collection still pernicious and comprehensive Vladeck, June 1, 2015 (Stephen, Professor of Law at American University Washington College of Law, teaching and research focus on federal jurisdiction, constitutional law, and national security law, nationally recognized expert on the role of the federal courts in the war on terrorism, has been published in Harvard Law Review and the Yale Law Journal, B.A. summa cum laude with Highest Distinction in History and Mathematics from Amherst College, JD Yale Law School; “Forget the Patriot Act – Here Are the Privacy Violations You Should Be Worried About”; http://foreignpolicy.com/2015/06/01/section-215-patriot-act-expiressurveillance-continues-fisa-court-metadata/ -- JRS) To be sure, the U.S. government doesn’t dispute that it routinely collects the communications of U.S. citizens. Instead, it has argued that any potential for abuse is mitigated by so-called “minimization requirements” — procedural rules that require the relevant intelligence agency to take steps to avoid the improper retention and use of communications collected under these authorities. The government’s defense, as we’ve come to learn, is flawed in two vital respects: First, as several since-disclosed opinions from the FISA Court have made clear, the government’s minimization requirements under the 2008 statute were often too skimpy, allowing the retention and use of information that both the statute and the Fourth Amendment prohibit. Second — and perhaps more importantly — even where the minimization rules were legally sufficient, there have been numerous instances in which government officials violated them, with the FISA Court only discovering the abuses after they were voluntarily reported by Justice Department lawyers. As a result, the government collected and retained a large volume of communications by U.S. citizens that neither Congress nor the Constitution allowed it to acquire. More alarmingly, with regard to collection under Executive Order 12333, there isn’t any similar judicial review (or meaningful congressional oversight), which means that it has entirely been up to the government to police itself. As State Department whistleblower John Napier Tye explained last summer, there is every reason to doubt that such internal accountability has provided a sufficient check. In his words, “Executive Order 12333 contains nothing to prevent the NSA from collecting and storing all … communications … provided that such collection occurs outside the United States in the course of a lawful foreign intelligence investigation.” To put the matter bluntly, whereas the Section 215 debate has addressed whether the government can collect our phone records, Executive Order 12333 and the 2008 FISA Amendments Act allow the government to collect a lot of what we’re actually saying, whether on the phone, in our emails, or even to our search engines. There is no question that, from a privacy perspective, these programs are far more pernicious than what’s been pegged to Section 215.There is no question that, from a privacy perspective, these programs are far more pernicious than what’s been pegged to Section 215. There is also no question that such collection raises even graver constitutional questions than the phone records program. Whereas there is an open debate over our expectation of privacy in the metadata we voluntarily provide to our phone companies, there’s no doubt that we have an expectation of privacy in the content of our private communications. Why, then, has all the fuss been around Section 215 and the phone records program, while the far more troubling surveillance authorities provided by Executive Order 12333 and the 2008 FISA Amendments Act have flown under the radar? Freedom Act only addressed a paper cut – uncontrolled data collection is inevitable without the plan Vladeck, June 1, 2015 (Stephen, Professor of Law at American University Washington College of Law, teaching and research focus on federal jurisdiction, constitutional law, and national security law, nationally recognized expert on the role of the federal courts in the war on terrorism, has been published in Harvard Law Review and the Yale Law Journal, B.A. summa cum laude with Highest Distinction in History and Mathematics from Amherst College, JD Yale Law School; “Forget the Patriot Act – Here Are the Privacy Violations You Should Be Worried About”; http://foreignpolicy.com/2015/06/01/section-215-patriot-act-expiressurveillance-continues-fisa-court-metadata/ -- JRS) But whatever the reason for our myopic focus on Section 215, it has not only obscured the larger privacy concerns raised by these other authorities, but also the deeper lessons we should have taken away from Snowden’s revelations. However much we might tolerate, or even embrace, the need for secret government surveillance programs, it is all-but-inevitable that those programs will be stretched to — and beyond — their legal limits. That’s why it’s important not only to place substantive limits upon the government’s surveillance authorities, but also to ensure that they are subject to meaningful external oversight and accountability as well. And that’s why the denouement of Section 215 debate has been so disappointing. This should have been a conversation not just about the full range of government surveillance powers, including Executive Order 12333 and the 2008 FISA Amendments Act, but also about the role of the FISA Court and of congressional oversight in supervising those authorities. Instead, it devolved into an over-heated debate over an over-emphasized program. Congress has tended to a paper cut, while it ignored the internal bleeding. Not only does the expiration of Section 215 have no effect on the substance of other surveillance authorities, it also has no effect on their oversight and accountability. Reaching some degree of closure with regard to the phone records program may leave many with the impression that America has concluded a meaningful and productive national debate over surveillance reform. We haven’t. And although the 2008 FISA Amendments Act is also set to expire — on December 31, 2017 — the debate over Section 215 leaves little reason to believe that we’ll have it then, either. NSA info gathering is massive Blass 2015 (Megan; J.D. Candidate 2015, University of California, Hastings College of the Law; “The New Data Marketplace: Protecting Personal Data, Electronic Communications, and Individual Privacy in the Age of Mass Surveillance Through a Return to a Property-Based Approach to the Fourth Amendment”; Hastings Constitutional Law Quarterly; 42 Hastings Const. L.Q. 577 – JRS) The National Security Agency is Collecting an Unprecedented Variety and Quantity of Personal Data, Virtual Information, and Electronic Communications The National Security Agency conducts so much domestic surveillance that it would be easier to answer the question “what isn’t the National Security Agency collecting” than to detail every facet of the Agency’s intelligence gathering programs.8 Recently, its PRISM and XKeyscore programs garnered notoriety. Through these programs, the National Security Agency has collected massive amounts of personal data and information, including the contents of e-mails, stored data, and internet traffic.9 Even without PRISM and XKeyscore, the National Security Agency collects more than 250 million internet communications each year.10 Moreover, even the Supreme Court has acknowledged the tremendous capability of the government to conduct this surveillance.11 NSA has panvasive access to all internet communication -- violates the 1st and 4th amendments and SOP, but immune from Court review Slobogin, March 2015 (Christopher, Milton Underwood Professor of Law, Vanderbilt University Law School, has been cited in almost 3,000 law review articles and treatises and more than 100 judicial opinions, including three U.S. Supreme Court decisions, Fulbright Scholar, J.D., LL.M. University of Virginia A.B. Princeton University; “Symposium Issue: The Future of National Security Law: Standing and Covert Surveillance; Pepperdine Law Review; 42 Pepp. L. Rev. 517 – JRS) Thanks to Edward Snowden, the federal government—up to and including President Obama—has been forced to confirm up every phone number we text and call, and is then subjecting this “metadata” to queries to determine which numbers link with known or suspected terrorists .9 Press reports suggest that the NSA is also engaging in numerous other types of “panvasive” surveillance (that is, that the National Security Agency is vacuuming surveillance that cuts across wide swaths of the population with no particularized reason to suspect any given subject of terrorist activity or other wrongdoing).10 F. Michael Maloof of WND has asserted that “[t]he National Security Agency already has access to all the content of intercepted emails and phone calls, not just the ‘metadata’ such as who contacted who[m], when and where.”11 Glenn Greenwald, the Guardian journalist who is Snowden’s main conduit to the outside world, has described XKeyscore, “[a] top secret National Security Agency program” that purportedly “allows analysts to search with no prior authorization through vast databases containing emails, online chats and the browsing histories of millions of individuals.”12 Via a program code-named “Optic Nerve,” the NSA and its British counterpart reportedly have been amassing webcam images of millions of Yahoo users since at least 2008.13 A newly disclosed malware program known as “Turbine” allegedly allows the NSA to hack into computers, computer networks, and phone networks. 14 Today Turbine affects thousands of people but it is predicted to soon to reach “millions.”15 One calculation holds that the NSA “touches” roughly half of all Internet communications and that, because 68% of those communications are spam, the agency may have access to all meaningful communication on the Internet. 16 Most of this surveillance takes place without any type of judicial authorization, 17 or is authorized only by the Foreign Intelligence Surveillance Court (FISC), which operates in secret.18 Although regulation of these practices has recently ramped up, even today the decision about what to collect and what to target and query is largely in the hands of executive agency officials.19 Thus, good arguments can be made that much, if not all, of this surveillance is unconstitutional under the Fourth Amendment, the First Amendment, separation of powers doctrine, or some combination thereof.20 But these arguments may never be fully fleshed out in the courts because of the Supreme Court’s standing doctrine. Just one AT&T facility gave NSA access to 10% of all US internet communications Blass 2015 (Megan; J.D. Candidate 2015, University of California, Hastings College of the Law; “The New Data Marketplace: Protecting Personal Data, Electronic Communications, and Individual Privacy in the Age of Mass Surveillance Through a Return to a Property-Based Approach to the Fourth Amendment”; Hastings Constitutional Law Quarterly; 42 Hastings Const. L.Q. 577 – JRS) The NSA has also been operating a program similar to PRISM involving upstream collection of communications on AT&T’s network.18 In one particular instance, the NSA installed a special room at AT&T ’s Folsom Street Facility in San Francisco, where all communications passing through the facility were “split,” or redirected through the special room, so that they could be collected before reaching their destination.19 Upstream collection was not limited to international communications or communications where one party to the communication was located abroad.20 With this one facility, the NSA had access to 10% of all domestic internet communications in the United States.21 Courts are deferring to the NSA Setty, 2015 (Sudha, Professor of Law and Associate Dean for Faculty Development & Intellectual Life, Western New England University School of Law; Harlan Fiske Stone Scholar from Columbia Law School and A.B. in History, concentration in comparative civil rights, with honors from Stanford University; Stanford Journal of International Law; Winter 2015; 51 Stan. J Int'l L. 69; “Surveillance, Secrecy, and the Search for Meaningful Accountability” – JRS) After the terrorist attacks of September 11, 2001, U.S. surveillance efforts were ramped up, in part due to the perception that intelligence agencies failed to garner vital information that could have prevented the attacks. n5 There was significant disagreement as to whether the failure was due primarily to legal constraints n6 or primarily to an inability to synthesize and analyze the available intelligence accurately and thoroughly. n7 The 9/11 Commission agreed with the latter view, concluding that the inability of intelligence agencies to learn about and prevent the attacks of September 11 was not attributable to a lack of legal authority. n8 Nonetheless, the legal and policy constraints on intelligence gathering were loosened significantly in the wake of the September 11 attacks. As discussed below, the PATRIOT Act arguably authorized the collection and storage of domestic telephony and internet metadata n9 and the collection and content searches [*73] of substantial amounts of foreign telephone and internet communications, n10 thereby giving the intelligence community a much larger "haystack" of information from which to attempt to glean details of emerging and ongoing terrorist threats. n11 This shift generated critiques from civil libertarians and lawmakers, n12 but critics have been largely unable to secure significant and lasting victories in curtailing surveillance powers, either through judicial action n13 or legislative initiative. However, the tenor of the public debate became more contentious in June 2013, when then-National Security Agency (NSA) contractor Edward Snowden began revealing classified documents detailing the scope of NSA surveillance on foreign and U.S. persons in order to prompt public scrutiny and debate over the programs. Snowden revealed, among many other things, that the NSA was engaged in the practice of collecting and retaining the metadata of all U.S. telephone customers for five years (the "NSA Metadata Program"), and had been running searches through that metadata when there was a "reasonable, articulable suspicion" that a particular telephone number was associated with potential terrorist activity. n14 This program - with its broad scope, lack of particularized suspicion, and lengthy duration of data retention - provides a useful vehicle through which to analyze the question of meaningful accountability over warrantless government surveillance more generally. n15 Snowden's revelations over the year following the publication of his initial disclosure continued to foster debate and demands for [*74] better oversight of the NSA. n16 The administration initiated various review mechanisms, n17 Congress convened oversight hearings, n18 and the public engaged in a vigorous debate as to the legality, efficacy, and morality of the NSA's activities, particularly the bulk collection and retention for several years of telephony and internet metadata of U.S. persons. This collection has been described at times as lawless, n19 yet the architecture constructed to support arguments as to the domestic legality n20 and constitutionality of the NSA Metadata Program is extensive. On a purely constitutional level, some have asserted that inherent Article II power confers on the executive branch expansive surveillance powers based on a view that the United States continues to be on a post-9/11 war footing. n21 From a legislative perspective, a significant number of statutes, such as the Authorization for the Use of Military Force [*75] (AUMF), n22 provisions of the USA PATRIOT Act (PATRIOT Act), n23 the Protect America Act and the FISA Amendments Act of 2008 (FAA) n24 were enacted by Congress and interpreted by the NSA as providing ample legal authority for the capture and storage of data. n25 Compounding these statutory authorities, the executive branch has likely sought its own nonpublic legal guidance in the form of secret legal opinions from the Office of Legal Counsel memoranda n26 and other Department of Justice memoranda defending the legality and efficacy of the surveillance program. n27 The surveillance and data collection that are part of the NSA Metadata Program have been largely validated by two forms of relatively weak judicial review: Article III courts have, until recently, largely refused to hear the merits of cases challenging the government surveillance, instead finding that plaintiffs are unable to satisfy the standing requirement, n28 or dismissing suits at the pleadings stage due to invocations of the state secrets privilege by the government. n29 The Foreign Intelligence Surveillance Court (FISC), tasked with determining the legality of many of the government's surveillance requests, has largely acquiesced to the government's requests over the years. n30 Cases litigated after the Snowden revelations of June 2013 suggest, however, that the judicial deference offered to the government in many previous counterterrorism cases may be curtailed in light of public attention and critique of the NSA Metadata Program, as well as a [*76] reinvigorated judicial embrace of the privacy protections embodied in the Fourth Amendment. n31 Surveillance is pervasive today and FISA doesn’t check Brand, 2015 (Jeffrey S., Dean and Professor Emeritus and Chairman of the Center for Law and Global Justice, University of San Francisco School of Law. Dean, University of San Francisco School of Law, 1999-2013. A.B., University of California, Berkeley, 1966; J.D., University of California, Berkeley, 1969; “Eavesdropping on Our Founding Fathers: How a Return to the Republic's Core Democratic Values Can Help Us Resolve the Surveillance Crisis”; Harvard National Security Journal; 6 Harv. Nat'l Sec. J. 1 – JRS) The notion of the separation of powers assumes that each branch of government is accountable to the citizenry for its actions. Where a proper balance of power among the branches exists, accountability is achievable. Absent a proper balance, accountability is unlikely. Senator Bayh had hoped that FISA would demonstrate that “all three branches of Government can share responsibility for the most sensitive intelligence activities” and show that “our system of checks and balances will continue to work as the framers of the Constitution intended.”178 In fact, FISA’s judicial structure doomed the effort to failure, creating instead a lack of Executive Branch accountability for its actions—the polar opposite of what the Congress sought in the months and years following Watergate. Today the naiveté of the chief proponents of FISA is painfully obvious. For example, responding to charges that the FISA court’s secrecy would undermine its integrity and the ability to check Executive Branch actions, Senator Kennedy responded in ways that future events would prove devastatingly inaccurate: There is no “judicial secrecy” today [at the time of FISA’s consideration], because the courts are not part of the process at all. It is the executive branch that exercises the secret and uncontrolled discretion, free from any statutory restraint. And even if a lenient judge is quick to rubberstamp 99 out of 100 applications, the everpresent possibility that this application will be the one rejected by the court should act as an effective deterrent for abuses.179 That hoped-for deterrent would not come to pass. Surveillance programs with names like Stellar Wind, Terrorist Surveillance Program, and PRISM speak volumes about the pervasiveness of surveillance in today’s America. The FISA court’s inability to say “no” to requests from the Executive Branch is best demonstrated by statistics detailing how frequently the court grants and denies warrant applications. In the thirty-three years from 1979 to 2012, the FISA court granted 33,942 requests for warrants and denied only eleven, compiling a denial rate of three tenths of one percent of the total warrants requested.180 In the twenty-two years prior to the September 11, 2001 attacks, the court approved 14,036 warrants and did not reject any. The eleven denials came after 2002, but in the ten-year period from 2002 to 2012, the court granted 19,906 warrants, 6,804 more warrants granted than in the twenty-one years preceding the attacks. As noted, former FISA court judge James Robertson, now a critic of the court and a proponent for its reform, denied that the court acted as a “rubber stamp.”181 The statistics, however, overwhelmingly suggest otherwise. Senator Kennedy’s hoped for a deterrent proved to be a pipedream. Ext: Scotus review coming/circuit split/uniqueness Constitutional challenges coming Flumenbaum and Karp, June 24, 2015 (Martin Flumenbaum and Brad S. Karp are members of Paul, Weiss, Rifkind, Wharton & Garrison. Philip S. May, a litigation associate at the firm, assisted in the preparation of this column; “Government Collection of Telephone Metadata Exceeds Statute's Authority”; New York Law Journal; http://www.newyorklawjournal.com/id=1202730150541/Government-Collection-of-TelephoneMetadata-Exceeds-Statutes-Authority#ixzz3eTbTl25G – JRS) Constitutional Claims. Plaintiffs also mounted constitutional challenges to the program, arguing that even if the telephone metadata program was authorized by statute, it violated the First and Fourth Amendments. Because the court found the program exceeded its statutory authorization, the court did not analyze plaintiffs' First Amendment claims and discussed the Fourth Amendment claims without reaching a conclusion. In discussing the Fourth Amendment implications of the telephone metadata program, the court noted the particularly complicated notions of privacy following the Supreme Court's decision in U.S. v. Jones,21 in which five of the Supreme Court justices, speaking through concurring opinions, suggested that a surveillance program that takes into account large amounts of information generated in the digital age by carrying out routine tasks might violate the Fourth Amendment. The court also noted that, at the time the case was decided, Congress was debating the U.S. Freedom Act of 2015, which had just passed the House Judiciary Committee, and could moot the issues presented by the telephone metadata program in its current form. Judge Sack's Concurrence. Sack issued a concurring opinion to "offer[ ] several additional observations about the import of [the] decision."22 Sack observed that because the court's decision turned on the statutory authority for the program rather than its constitutionality, Congress could overturn the decision by explicitly authorizing such a program. Sack also discussed the challenges the FISC and all Article III courts face in closing their doors to adjudicate issues of classified and sensitive materials. He discussed the importance of adversary proceedings in our court system, even when the courtroom doors must be sealed to the general public, analogizing FISC hearings to the Pentagon Papers case.23 Conclusion While Congress has now passed the U.S. Freedom Act of 2015, debate rages over the degree to which national security should subordinate individual liberties in keeping the nation safe. The Second Circuit's ruling in American Civil Liberties Union v. Clapper, as the first appellate court to issue a decision regarding Section 215, underscores the concerns many have with large-scale surveillance programs and secret court proceedings. Moreover, the program as authorized by the Freedom Act may itself be subject to constitutional challenges as outlined here, and the courts may be called upon once again to determine the legality of future surveillance programs. Fourth amendment claims being pushed now Harclerode, June 23, 2015 (Kelsey, J.D., UF Levin College of Law (Expected 2016), B.A., University of Florida, Political Science and Women's Studies; “How USA Freedom Impacts Ongoing NSA Litigation”; https://www.eff.org/deeplinks/2015/06/how-usa-freedom-impacts-ongoing-nsa-litigation -- JRS) First Unitarian v. NSA solely targets the NSA’s bulk collection of telephone records. In First Unitarian, EFF is pursuing First Amendment, Fourth Amendment, and statutory challenges to this program, so the passage of USA Freedom will have an impact on our claims. While the court denied EFF’s most recent request for a hearing, EFF will continue to pursue these claims to ensure that the court fully considers the issues raised by the NSA’s phone records program. Jewel v. NSA is EFF’s longest-standing case against the NSA’s dragnet surveillance. Jewel challenges the NSA’s bulk collection of telephony metadata, the collection of Internet metadata, and Internet content surveillance. USA Freedom addresses the bulk collection of telephony metadata, but it notably neglects the collection of Internet communications under Section 702 of the FISA Amendment Act. The court ruled for the government on EFF’s Fourth Amendment challenge to the collection of Internet content (and EFF is appealing this decision in the Ninth Circuit), but the court has yet to rule on the constitutionality or permissibility of the mass surveillance of telephone records. In addition to pursuing our appeal in the Ninth Circuit, EFF will continue to push forward on our other claims in the district court. Expect similar issues to arise in other NSA spying cases that EFF has supported as an amicus— Klayman v. Obama and ACLU v. Clapper. Currently, Klayman is under review following oral argument in the D.C. Circuit, which is considering the district court’s ruling that the bulk collection of telephone records is likely unconstitutional. Klayman recently filed a supplemental brief stressing the importance of the appeal continuing despite USA Freedom given the NSA’s “pattern of illegal and unconstitutional acts for an extended period of time.” Meanwhile, the Second Circuit’s historic ruling in Clapper not only held the bulk collection of telephone records exceeded congressional authorization, it also directly raised the possibility of Congress addressing the NSA’s reliance on Section 215 of the Patriot Act for its telephone records program. Congress has since spoken with the passage of USA Freedom, so the extent of the Second Circuit’s deference to Congress relating to the 180-day transition period will be a significant issue as it considers supplemental briefing from the parties on whether the ACLU’s claim is moot. SCOTUS already changing 4th amendment analysis Raysman and Brown, June 9, 2015 Richard Raysman is a partner at Holland & Knight and Peter Brown is the principal at Peter Brown & Associates; “How Has Digital Ubiquity Affected Fourth Amendment Law?”; New York Law Journal; http://www.newyorklawjournal.com/id=1202728535476/How-Has-Digital-Ubiquity-Affected-FourthAmendment-Law#ixzz3eVZI52AM http://www.newyorklawjournal.com/id=1202728535476/How-Has-Digital-Ubiquity-Affected-FourthAmendment-Law#ixzz3eVYB5zo9 – JRS) Pick up pretty much any 21st century smart phone, tablet or PC, and in minutes, a treasure trove of information about its owner can be uncovered. Missives to a significant other, photos from summer vacation, browsing history that spans years; all of this information, generally considered of the most intimate nature, is easily accessible with even a rudimentary technical knowledge of the device's operating system. Needless to say, unwanted disclosure of such information can be highly damaging. Perhaps in no situation can such disclosure be as injurious as when the recipient of the information is a representative of law enforcement. Given the protection from an unreasonable search and seizure enumerated in our constitution that give ballast to notions of privacy and autonomy, questions have arisen from the Founding as to when a law enforcement search can square with these rights, particularly when it is effectuated without the imprimatur of a warrant. That the aforementioned devices now function as virtual warehouses of information has exacerbated the tension between effective policing and privacy rights deemed inseparable from the notion of ordered liberty . The Supreme Court confronted this tension in its previous term, and came down decidedly in favor of the privacy interests in Riley v. California, 134 S. Ct. 2473 (2014). Chief Justice John Roberts, in writing for a unanimous court, held that because "cell phones differ in both a quantitative and qualitative sense from other objects" kept on an arrestee's person, greater privacy interests are potentially impinged by the search of a cell phone. Accordingly, Fourth Amendment analysis must be sculpted in a way so as to recognize that a search incident to an arrest can now reveal exponentially more personal, and often incriminating, information. SCOTUS is starting to rule in favor of civil liberties Kent, May 2015 (Andrew, Professor, Fordham Law School; Faculty Adviser to the Center on National Security at Fordham Law; J.D., Yale Law School, A.B., Harvard College, formerly Climenko Fellow at Harvard Law School, attorney in private practice, and federal judicial clerk; “Essay: Disappearing Legal Black Holes And Converging Domains: Changing Individual Rights Protection In National Security And Foreign Affairs”; Columbia Law Review; 115 Colum. L. Rev. 1029 – JRS) B. Role and Self-Conception of the Supreme Court and Federal Judiciary Certain institutional changes within the U.S. government, notably the rise to prominence and power of the Supreme Court, seem conceptually and historically linked to convergence and closing of legal black holes. Today, the Court's fairly aggressive vision of judicial supremacy, especially in the area of individual rights, is clearly supportive of further convergence and closing of legal black holes. In Marbury v. Madison, the Court sketched a very limited role for judicial review. First, the Court emphasized that its duty and power to say what the law was could properly be exercised only in service of the court's duty to provide a remedy for violations of an individual's private right. n206 Second, the Court broadly described categories of "political" issues that could not be decided judicially but lay within the "constitutional or legal discretion" of another branch. n207 And, famously, the Court exercised the power of judicial review in service of limiting the Court's power in the particular case before it and ducking confrontation with the President and Congress. But in a gradual process spanning centuries, the modern imperial Court emerged from these humble beginnings. Only two acts of Congress were declared unconstitutional in the entire period prior to the Civil War (in Marbury and Dred Scott). n208 The pace quickened over the subsequent decades. As of 2002, a Government Printing Office publication had counted 157. n209 The Court barely maintains any longer the fiction that it decides constitutional issues only when it unavoidably must to protect an individual's private rights. It is often very self-conscious and forthright about its modern role of declaring constitutional doctrines and rules that will operate prospectively as binding rules of law applicable [*1070] to all government actors facing circumstances within the scope of those rules or doctrines. n210 The scope, density, and ambition of the modern Court's constitutional jurisprudence are astounding. It is difficult to think of any important area of social, political, economic, or educational life that entirely evades its reach. The Court is less and less willing to see any zones of U.S. government activity as categorically immune to judicial review and oversight. n211 At the Supreme Court level, if not yet in the lower federal courts, the scope of things considered nonjusticiable political questions has shrunk. Out of quasi-departmentalist beginnings, the modern Court has decided that it "alone among the three branches has been allocated the power to provide the full substantive meaning of all constitutional provisions." n212 The modern Court's supremacy is widely accepted. "Governments at all levels . . . have essentially acceded to the Supreme Court's demand in Cooper v. Aaron that the constitutional doctrines and rules announced by the Court in its decisions be treated as equivalent to the Constitution itself." n213 For this enormously powerful and self-confident modern Court, it must seem increasingly quaint to hear the government argue in national security and foreign affairs cases that the judiciary lacks competence or authority to decide a given issue. n214 As has been widely recognized, the Court has also shifted the focus and intensity of its judicial review over time. One salient change is the shift that became most obvious in the late 1930s and 1940s, and was noted by the Court itself in, among other places, the famous footnote in the Carolene Products decision. n215 As the Court moved toward a more deferential posture to legislative and executive action when reviewing moved quite strongly to protect civil rights and civil law [*1071] in the economic and regulatory spheres, it has liberties. Circuit split on cell phones will spark SCOTUS review Daskal 2015 (Jennifer, Founding Editor of Just Security, prof at American University Washington College of Law, degrees from Brown University, Harvard Law School, and Cambridge University (where she was a Marshall Scholar), formerly fellow and adjunct professor at Georgetown Law Center, counsel to the Assistant Attorney General for National Security at the Department of Justice 2009-11, served on the Department of Defense and Justice-led Detention Policy Task Force, senior counterterrorism counsel at Human Rights Watch, staff attorney for the Public Defender Service for the District of Columbia, and clerk for the Honorable Jed S. Rakoff, her articles on humanitarian law, military commissions, and noncustodial detention have appeared in the University of Pennsylvania Law Review, the Journal of International Criminal Law, and Cornell Law Review. She has published op-eds in The New York Times, Washington Post, International Herald Tribune, LA Times, and Salon.com, and she has offered comment for the BBC, C-Span, CNN, MSNBC, and NPR; “Top 10 National Security Cases to Watch in 2015”; January 1, 2015; http://justsecurity.org/18762/top-10-national-security-cases-watch-2015/United States v. Graham – JRS) Among the many cases percolating through the courts involving the use of cell site geo-location data, one case to definitely watch is that of United States v. Graham. Argued before the Fourth Circuit in December, the case challenges the government’s warrantless collection of historical cell cite location data for a whopping 221 days. At issue is whether or not the suspect retains a reasonable expectation of privacy in the data even though it had been transmitted to a third party doctrine – the cell phone provider. The 11th Circuit addressed an analogous issue in United States v. Davis, concluding that the government does need a warrant to collect historical cell site data. (See Jennifer Granick’s discussion of the case here.) And it’s an issue that’s been addressed by the Third Circuit as well. My prediction: A Circuit split, if one develops, will spark Supreme Court review. (See Orin Kerr’s discussion of some related cases here.) Several cases upcoming – they’ll be like dominoes Farivar 2015 (Cyrus, senior business editor at Ars Technica, has reported for The Economist, Wired, The New York Times, Deutsche Welle English, the Canadian Broadcasting Corporation, Public Radio International, National Public Radio, the Australian Broadcasting Corporation, B.A. in Political Economy from the University of California, Berkeley and M.S. from the Columbia University Graduate School of Journalism; January 1, 2015; http://arstechnica.com/tech-policy/2015/01/if-the-supreme-court-tackles-the-nsa-in2015-itll-be-one-of-these-five-cases/ -- JRS) Klayman filed his federal lawsuit at the District of Columbia District Court on June 6, 2013, the day after the first published disclosures from the Snowden leaks. That initial revelation showed that Verizon routinely handed over all metadata on its customers to the NSA. So as a Verizon customer, Klayman argued that his constitutional rights—not to mention the rights of all other Verizon customers—were violated as the result of this data handover. The government relied on the third-party doctrine in its defense. Judge Richard Leon, a Republican appointee, agreed with Klayman’s argument. As he wrote in a December 16, 2013 memorandum opinion: Indeed, the question in this case can more properly be styled as follows: when do present-day circumstances—the evolutions in the Government's surveillance capabilities, citizens' phone habits, and the relationship between the NSA and telecom companies—become so thoroughly unlike those considered by the Supreme Court 34 years ago that a precedent like Smith simply does not apply? The answer, unfortunately for the government, is now. … In sum, the Smith pen register and the ongoing NSA Bulk Telephony Metadata Program have so many significant distinctions between them that I cannot possibly navigate these uncharted Fourth Amendment waters using as my North Star a case that predates the rise of cell phones. Unlike any of the other metadata-related cases thus far, Judge Leon ordered the government to immediately halt the Bulk Telephony Metadata Program and to destroy "any such metadata in its possession that was collected through the bulk collection program." However, he noted, "in light of the significant national security interests at stake in this case and the novelty of the constitutional issues, I will stay my order pending appeal." In early November 2014, Klayman arrived at that appeal. The case was heard again, this time before the District of Columbia Circuit Court of Appeals. A ruling is expected in the forthcoming months. Klayman is likely the first domino. There are a few other current cases making similar claims , and one is from June 2013 in fact. Like Klayman, Smith v. Obama argues that the government is violating plaintiff Anna Smith's rights by routinely collecting her metadata. Initially, a lower federal court in Idaho found that Smith "has no expectation of privacy in the telephone numbers that she dials." The case was heard at the 9th Circuit Court of Appeals in Seattle in December, and that appellate court is likely to rule sometime early in 2015. Jones and Riley signal the Court is aware of the need for change Farivar 2015 (Cyrus, senior business editor at Ars Technica, has reported for The Economist, Wired, The New York Times, Deutsche Welle English, the Canadian Broadcasting Corporation, Public Radio International, National Public Radio, the Australian Broadcasting Corporation, B.A. in Political Economy from the University of California, Berkeley and M.S. from the Columbia University Graduate School of Journalism; January 1, 2015; http://arstechnica.com/tech-policy/2015/01/if-the-supreme-court-tackles-the-nsa-in2015-itll-be-one-of-these-five-cases/ -- JRS) Before outlining the relevant cases, it's important to note the government's general justification for the legality of bulk metadata collection: the third-party doctrine. This theory was codified most recently from a 1979 Supreme Court decision in Smith v. Maryland. In the case, the court found that individuals do not have an inherent privacy right to data that has already been disclosed to a third party. So with telecom data for instance, the government has posited that because a call from one person to another forcibly transits Verizon’s network, those two parties have already shared that data with Verizon. Therefore, the government argues, such data can't be private, and it’s OK to collect it. But legal experts say that recent surveillance and privacy Supreme Court decisions could lead the courts to reconsider. The first Snowden revelation (published in June 2013) was that Verizon (and presumably other telecom firms) are routinely handing over all call records to the NSA. The metadata records include the date, times, and lengths of the calls. In October 2013, the third-party doctrine was upheld. A Foreign Intelligence Surveillance Act Court (FISA Court) judge ruled that there was no privacy interest in such metadata collected and analyzed by the NSA. In short, if it's OK to collect third-party data on one person, it's OK to collect it on a bunch of people. Put another way, where one individual does not have a Fourth Amendment interest, grouping together a large number of similarly situated individuals cannot result in a Fourth Amendment interest springing into existence ex nihilo. In sum, because the Application at issue here concerns only the production of call detail records or "telephony metadata" belonging to a telephone company, and not the contents of communications, Smith v. Maryland compels the conclusion that there is no Fourth Amendment impediment to the collection. Furthermore, for the reasons stated in—and discussed above, this Court finds that the volume of records being acquired does not alter this conclusion. Indeed, there is no legal basis for this Court to find otherwise. But consider two recent Supreme Court cases: United States v. Jones (2012) and Riley v. California (2014). Both were decided by rare unanimous opinions, and both indicate an awareness that modern tech has changed reasonable privacy. Jones determined that law enforcement does not have the authority to place a GPS tracker on a suspect without a warrant. Meanwhile, the court found in Riley that law enforcement cannot search a person’s phone incident to arrest without a warrant. "[These cases] are strong signs that the Supreme Court is aware that rules that were created in a period of time when the court analyzed targeted surveillance do not blindly apply where the government is collecting huge quantities of information," Patrick Toomey, an attorney with the American Civil Liberties Union, told Ars. "As the quantity expand, a new constitutional analysis arises. We think the same type of principle applies here. Smith v. Maryland is one suspect’s data over three days as opposed to the information contained in everyone’s call records contained for 10 years or more." For his part, the EFF's Rumold agreed with this reasoning. "Riley signals that the Supreme Court recognizes that technological distinctions matter, and we can't blindly apply old precedent to new technology," he added. "Jones, or at least the concurrences in Jones, signal that the scope and duration of surveillance makes a difference for constitutional purposes. Those twin principles put much of the NSA's domestic spying programs on pretty unsound constitutional footing." 4th amendment status of cell phones unsettled Hawn, June 15, 2015 (Jeff; BA International relations American University; “Balancing security and privacy in a mobile world”; http://www.rcrwireless.com/20150615/devices/mobile-world-balance-security-privacy -- JRS) WASHINGTON – Decades after they were invented and became a staple of everyday life, mobile phones are finally finding a clear legal footing in U.S. courts. Mobile technology has spurred a multiyear global debate touching on issues such as privacy, freedom of speech, civil rights and international relations. An American citizen’s right to privacy is guaranteed in the Bill of Rights by the Fourth Amendment, and that privacy is extended to wired telephones by Katz vs. The United States. Mobile phones have proved to be an entirely different kettle of fish because of the multimedia aspect, since they are not landlines and they do not just transmit point-to-point, real-time voice messages. Mobile phones transmit and retain a whole host of information, which can be directly relevant to criminal activity or terrorism. Simply treating cellphones as wireless telephones has been insufficient to answer nagging legal questions, especially in the post 9/11 world and given the sweeping surveillance powers given to the U.S. intelligence community under the Patriot Act. Over the last few years, however, mobile phones have begun to carve out their own legal niche separate from landlines. In 2014, the U.S. Supreme Court ruled in Riley v. California that in order to search a mobile phone confiscated in an arrest, law enforcement officials must first obtain a warrant. Chief Justice John Roberts noted in the majority opinion: “Modern cell phones are not just another technological convenience. With all they contain and all they may reveal, they hold for many Americans ‘the privacies of life.’ The fact that technology now allows an individual to carry such information in his hand does not make the information any less worthy of the protection for which the founders fought.” Less than a year later, the Second Circuit Court of Appeals ruled in ACLU v. Clapper that section 215 of the Patriot Act, which allowed for the collection of mobile phone metadata, was unconstitutional. The ruling was seen by many as spurring Congress to pass the Freedom Act, which shifted the burden of bulk collection from the intelligence community – where the data therein could be accessed at will – to the wireless service providers, who now have to retain the data for an unspecified amount of time so it can be accessed by the government with a proper warrant. Shifting the burden has left deep concerns and unanswered questions. Key among those is who is issuing the warrants? Currently, warrants for any kind of international communication are issued to federal agents by the Foreign Intelligence Surveillance Court, a rotating panel of 11 judges whose identities are secret and who meet in Washington, D.C. The proceedings of these meetings are also secret. In response to what is perceived by many as a continued invasion of privacy, several tech companies have started to look at encrypting phone data, which has caused the government to begin to look at diluting such encryption so it is still accessible to law enforcement. From a letter sent to the Obama administration by several technology leaders and civil rights groups: “More than undermining every American’s cybersecurity and the nation’s economic security, introducing new vulnerabilities to weaken encrypted products in the U.S. would also undermine human rights and information security around the globe. If American companies maintain the ability to unlock their customers’ data and devices on request, governments other than the United States will demand the same access, and will also be emboldened to demand the same capability from their native companies. The U.S. government, having made the same demands, will have little room to object.” Despite a growing consensus that cellphones are a staple of modern society and that the data contained on them are entitled to certain specific protections, it will be years before the law answers all the questions surrounding the issue, and in the meantime the pace of technology continues to advance. Protections will be an uphill battle in court Farivar 2014 (Cyrus, has reported for The Economist, Wired, The New York Times, Deutsche Welle English, the Canadian Broadcasting Corporation, Public Radio International, National Public Radio, the Australian Broadcasting Corporation, B.A. in Political Economy from the University of California, Berkeley and M.S. from the Columbia University Graduate School of Journalism; “Surveillance Watchdog Concludes Metadata Program Is Illegal, ‘Should End’”; Jan 23, 2014; http://arstechnica.com/techpolicy/2014/01/surveillance-watchdog-concludes-metadata-program-is-illegal-should-end/ -- JRS) Legal experts are divided as to whether Judge Leon’s appellate counterparts, who are all also Republican appointees, will be willing to challenge the government’s view. "The three judges who will be hearing the Klayman appeal on the DC Circuit skew conservative," Ruthann Robson, a constitutional law professor at the City University of New York, told Ars. "Interestingly, Judge Sentelle and Judge Brown, who are both on Klayman's panel, were also on the panel that voted in favor of the constitutionality of the Military Commissions Act, which was later declared unconstitutional by the United States Supreme Court in Boumediene v. Bush. But one judge, Judge David Sentelle, who is known as a national security expert, joined the DC Circuit's opinion, another judge, Judge Janice Rogers Brown, a conservative with a decided libertarian bent, dissented. The third judge on Klayman's panel is the 78-year-old Stephen Williams, appointed by Ronald Reagan." Brian Owsley, himself a former federal district judge in Texas and now a law professor at Indiana Tech, told Ars that he didn’t think that partisan politics was a good predictor of outcomes. "There are people on both the right and the left who are finding common ground in voicing a myriad of privacy concerns." However, Radack, Snowden’s lawyer, thinks Klayman will face an uphill battle. "Judges Brown and Sentelle are the more conservative justices on the panel and are very likely to defer to agency authority in this case as they have in the past (Sentelle wrote an opinion in 2010 arguing that the right of habeas corpus does not extend to those detained at Bagram airbase)," she said by e-mail. "Though Judge Williams is the least conservative and more sophisticated on these issues, he is also likely to defer to the NSA." Radack added that the two recent unanimous Supreme Court decisions in favor of privacy—the Riley case and the 2012 case, United States v. Jones, which found that police cannot warrantlessly install a GPS tracker on a car—"bolster Judge Leon’s argument that the 1979 Smith v. Maryland case should no longer be controlling precedent on questions about the legality of government surveillance." Federal courts are split on metadata – will go to Supreme Court Cohn 2014 (Marjorie; law prof at Thomas Jefferson, past president of the National Lawyers Guild, and deputy secretary general of the International Association of Democratic Lawyers, author of Drones and Targeted Killing; “Metadata Collection: Fourth Amendment Violation”; JURIST - Forum, Jan. 15, 2014; http://jurist.org/forum/2014/01/marjorie-cohn-nsa-metadata.php -- JRS) The government has admitted it collects metadata for all of our telephone communications, but says the data collected does not include the content of the calls. In response to lawsuits challenging the constitutionality of the program, two federal judges issued dueling opinions about whether it violates the Fourth Amendment's prohibition on unreasonable searches and seizures. Judge Richard J. Leon, of the US District Court for the District of Columbia, held that the metadata program probably constitutes an unconstitutional search and seizure. Judge William H. Pauley III, of the US District Court for the Southern District of New York, determined that it does not violate the Fourth Amendment. Leon's opinion Leon wrote, "Because the Government can use daily metadata collection to engage in 'repetitive surreptitious surveillance of a citizen's private goings on,' the 'program implicates the Fourth Amendment each time a government official monitors it.'" The issue is "whether plaintiffs have a reasonable expectation of privacy that is violated when the Government indiscriminately collects their telephony metadata along with the metadata of hundreds of millions of other citizens without any particularized suspicion of wrongdoing, retains all of that metadata for five years, and then queries, analyzes, and investigates that data without prior judicial approval of the investigative targets. If they do—and a Fourth Amendment search has thus occurred—then the next step of the analysis will be to determine whether such a search is 'reasonable.'" The first determination is whether a Fourth Amendment "search" has occurred. If so, the second question is whether that search was "reasonable." The judicial analyses of both Leon and Pauley turn on their differing interpretations of the 1979 U.S. Supreme Court decision, Smith v. Maryland. In Smith, a robbery victim reported she had received threatening and obscene phone calls from someone who claimed to be the robber. Without obtaining a warrant, the police installed a pen register, which revealed a telephone in the defendant's home had been used to call the victim. The Supreme Court held that a person has no reasonable expectation of privacy in the numbers dialed from his telephone because he voluntarily transmits them to his phone company. Leon distinguished Smith from the NSA program, saying that whether a pen register constitutes a "search" is "a far cry from the issue in [the NSA] case." Leon wrote, "When do present-day circumstances—the evolution of the Government's surveillance capabilities, citizens' phone habits, and the relationship between the NSA and telecom companies—become so thoroughly unlike those considered by the Supreme Court thirty-four years ago that a precedent like Smith simply does not apply? The answer, unfortunately for the Government, is now." Then Leon cited the 2012 Supreme Court case of United States v. Jones, in which five justices found that law enforcement's use of a GPS device to track the movements of a vehicle for nearly a month violated a reasonable expectation of privacy. "Significantly," Leon wrote, "the justices did so without questioning the validity of the Court's 1983 decision in United States v. Knotts, that the use of a tracking beeper does not constitute a search because '[a] person travelling in an automobile on public thoroughfares has no reasonable expectation of privacy in his movements from one place to another.'" Leon contrasted the short-range, short-term tracking device used in Knotts with the constant monthlong surveillance achieved with the GPS device attached to Jones's car. Unlike the "highly-limited data collection" in Smith, Leon noted, "[t]he NSA telephony metadata program, on the other hand, involves the creation and maintenance of a historical database containing five years' worth of data. And I might add, there is the very real prospect that the program will go on for as long as America is combating terrorism, which realistically could be forever!" He called the NSA program "effectively a joint intelligence-gathering operation [between telecom companies and] the Government." "[T]he almost-Orwellian technology that enables the Government to store and analyze the phone metadata of every telephone user in the United States is unlike anything that could have been conceived in 1979," Leon exclaimed, calling it "the stuff of science fiction." He cited Justice Scalia's opinion in Kyllo v. United States, which held the use of a thermal imaging device, that measures heat waste emanating from a house, constitutes a "search." Justice Scalia was concerned about increasing invasions of privacy occasioned by developing technology. Leon wrote, "I cannot imagine a more 'indiscriminate' and 'arbitrary invasion' than this systematic and high-tech collection and retention of personal data on virtually every single citizen for purposes of querying and analyzing it without prior judicial approval." Quoting Justice Sotomayor's concurrence in Jones, Leon noted the breadth of information our cell phone records reveal, including "familial, political, professional, religious, and sexual associations." Having determined that people have a subjective expectation of privacy in their historical record of telephony metadata, Leon turned to whether that subjective expectation is one that society considers "reasonable." A "search" must ordinarily be based on individualized suspicion of wrongdoing in order to be "reasonable." One exception is when there are "special needs," beyond the need for ordinary law enforcement (such as the need to protect children from drugs). "To my knowledge, however, no court has ever recognized a special need sufficient to justify continuous, daily searches of virtually every American citizen without any particularized suspicion," Leon wrote. "In effect," he continued, "the Government urges me to be the first nonFISC judge to sanction such a dragnet." Leon stated that fifteen different FISC judges have issued 35 orders authorizing the metadata collection program. But, Leon wrote, FISC Judge Reggie Walton determined the NSA has engaged in "systematic noncompliance" and repeatedly made misrepresentations and inaccurate statements about the program to the FISC judges. And Presiding FISC Judge John Bates noted "a substantial misrepresentation [by the government] regarding the scope of a major collection program." Significantly, Leon noted that "the Government does not cite a single instance in which analysis of the NSA's bulk metadata collection actually stopped an imminent attack, or otherwise aided the Government in achieving any objective that was time-sensitive in nature." Pauley's analysis of the Fourth Amendment issue was brief. He explained that prior to the September 11th terrorist attacks, the NSA intercepted seven calls made by hijacker Khalid al-Mihdhar to an al-Qaeda safe house in Yemen. But the overseas signal intelligence capabilities the NSA used could not capture al-Mihdhar's telephone number identifier; thus, the NSA mistakenly concluded that al-Mihdhar was not in the United States. Pauley wrote: "Telephony metadata would have furnished the missing information and might have permitted the NSA to notify the Federal Bureau of Investigation (FBI) of the fact that al-Mihdhar was calling the Yemeni safe house from inside the United States." "If plumbed," Pauley noted, the telephony metadata program "can reveal a rich profile of every individual as well as a comprehensive record of people's association with one another." He noted, "the Government acknowledged that since May 2006, it has collected [telephony metadata] for substantially every telephone call in the United States, including calls between the United States and a foreign country and calls entirely within the United States." But, unlike Leon, Pauley found Smith v. Maryland controls the NSA case. He quoted Smith: "Telephone users ... typically know that they must convey numerical information to the telephone company; that the telephone company has facilities for recording this information; and that the telephone company does in fact record this information for a variety of legitimate business purposes." Thus, Pauley wrote, when a person voluntarily gives information to a third party, "he forfeits his right to privacy in the information." While Leon's distinction between Smith and the NSA program turned on the breadth of information collected by the NSA, Pauley opined, "The collection of breathtaking amounts of information unprotected by the Fourth Amendment does not transform that sweep into a Fourth Amendment search." And whereas Leon's detailed analysis demonstrated how Jones leads to the result that the NSA program probably violates the Fourth Amendment, Pauley failed to meaningfully distinguish Jones from the NSA case, merely noting that the Jones court did not overrule Smith. Leon's decision is the better-reasoned opinion. Looking ahead This issue is headed to the Court of Appeals. From there, it will likely go the Supreme Court. The high court checked and balanced President George W. Bush when he overstepped his legal authority by establishing military commissions that violated due process, and attempted to deny constitutional habeas corpus to Guantanamo detainees. It remains to be seen whether the court will likewise refuse to cower before President Barack Obama's claim of unfettered executive authority to conduct dragnet surveillance. If the court allows the NSA to continue its metadata collection, we will reside in what can only be characterized as a police state. Klayman outcome will be high profile Farivar 2014 (Cyrus, has reported for The Economist, Wired, The New York Times, Deutsche Welle English, the Canadian Broadcasting Corporation, Public Radio International, National Public Radio, the Australian Broadcasting Corporation, B.A. in Political Economy from the University of California, Berkeley and M.S. from the Columbia University Graduate School of Journalism; “A top appeals court to hear why NSA metadata spying should stay or go”; Nov 4, 2014; http://arstechnica.com/tech-policy/2014/11/topappeals-court-to-hear-why-nsa-metadata-spying-should-stay-or-go/ -- JRS) Civil libertarians and privacy activists are closely watching the case to see if the appellate court upholds the landmark lower court order. Since Klayman originally filed his lawsuit, there have been a few notable policy and legal decisions that could push the appeals court in his favor. Specifically, the Supreme Court has taken a stronger view of digital privacy than it has in the past. Earlier this year, in a unanimous decision in the Riley v. California case, the nine justices found that law enforcement must get a warrant before they search someone’s cellphone. On the policy side, both the Congressionally mandated Privacy and Civil Liberties Oversight Board (PCLOB) and the president’s Review Group on Intelligence and Communications Technologies (RGICT) recommended that the metadata collection program should end as they currently exist. PCLOB, in particular, concluded in January 2014 that the government’s metadata collection program "lacks a viable legal foundation under Section 215 [of the Patriot Act], implicates constitutional concerns under the First and Fourth Amendments, raises serious threats to privacy and civil liberties as a policy matter, and has shown only limited value… As a result, the board recommends that the government end the program." The RGICT recommended that the NSA not be allowed to hold all that metadata in-house. Either way, both conclusions are simply advisory— they are not binding law by any means. The metadata program still functions in essentially the same way that it did before the American public heard of Edward Snowden. "Over the last year, the government’s privacy boards have taken the view that this unusually intrusive program is unnecessary," Patrick Toomey, an attorney with the American Civil Liberties Union (ACLU), told Ars. "I’m hopeful that [the appellate court] will find that this is unconstitutional. Judge Leon was persuaded that bulk surveillance is a way of collecting information that raised a significant violation of a reasonable expectation of privacy and the Constitution." Will conservative judges be swayed? Lower courts are divided Greenhouse 2014 (Linda, Pulitzer Prize winner, Senior Research Scholar in Law, the Knight Distinguished Journalist in Residence, and Joseph Goldstein Lecturer in Law at Yale Law School, NYT writer on the Supreme Court and the law since 1978, BA Radcliffe (Harvard) and Masters from Yale Law; “We’ve Got Your Number”; Jan. 22, 2014; http://www.nytimes.com/2014/01/23/opinion/greenhouse-weve-got-yournumber.html?_r=0 – JRS) This case, Smith v. Maryland, was no big deal in its day. (And the defendant in the garden-variety case that led to the decision was no criminal mastermind -- he was making harassing calls from his home phone.) The majority opinion was only 11 pages long. There were three dissenting votes, but the dissenting opinions lacked passion. After Justice Blackmun circulated his final draft in June 1979, Chief Justice Warren E. Burger responded by agreeing that “the urge for privacy does not rise to the level of a constitutionally protected right.” The chief justice added that “Congress could require a warrant but the Constitution does not.” He ended his note with a lighthearted P.S.: “I’m going to use a public phone for my calls to my bookie.” Thirty-five years later, telephones and their users’ privacy concerns are obviously no joking matter. They are the question of the hour. Constitutional challenges to the National Security Agency’s bulk telephone data collection produced opposing Federal District Court rulings last month, and the issue appears destined for the Supreme Court. Meanwhile, the justices last week accepted two cases with less obvious national security implications but much greater relevance to many Americans: whether the police need a warrant in order to search the contents of a cellphone of a person they have just arrested. These cases, United States v. Wurie and Riley v. California, will probably be argued in April and decided in June. All the cases will be dissected in minute detail in the coming months, but that’s not my goal here. I’m interested in the ultimate answers, of course, but what I find most intriguing at the moment is watching how judges respond to the challenge of figuring out how old precedents fit with new realities. The fit is awkward at best; the Supreme Court’s description of a pen register -- “a mechanical device that records” on a paper tape “the numbers dialed on a telephone by monitoring the electrical impulses caused when the dial on the telephone is released” -- reads like something from Alexander Graham Bell’s laboratory. Differing conclusions about whether the old cases are even relevant, let alone controlling, have divided the lower courts, state as well as federal. For anyone interested in how the law develops in a system ostensibly governed by precedent, the progress of these cases promises to be the best show in town. Ext: Blanket collection violates 4th Amendment Blanket collection violates 4th amendment – allowing it is an unprecedented constitutional change Barnett and Harper 2013 (Randy E. Barnett, Carmack Waterhouse Professor of Legal Theory at the Georgetown University Law Center, director of Georgetown Center for the Constitution, formerly a prosecutor in States’ Attorney’s Office in Chicago, represented the National Federation of Independent Business in its 2011 constitutional challenge to the Affordable Care Act, argued the 2004 medical marijuana case of Gonzalez v. Raich before the U.S. Supreme Court, won 2008 Guggenheim Fellowship in Constitutional Studies, publications include more than one hundred articles and reviews, as well as nine books, including Restoring the Lost Constitution: The Presumption of Liberty, Oxford Introductions to U.S. Law: Contracts, Contracts: Cases and Doctrine, and Constitutional Law: Cases in Context, B.A., Northwestern, J.D., Harvard; Jim Harper Global Policy Counsel of the Bitcoin Foundation, Senior Fellow at Cato, formerly counsel to committees in both the U.S. House and Senate, and provided government relations counsel to PayPal, VeriSign, and other companies in tech, telecom and e-commerce, original member of the U.S. Department of Homeland Security’s Data Privacy and Integrity Advisory Committee, co-edited the book Terrorizing Ourselves: How U.S. Counterterrorism Policy Is Failing and How to Fix It, J.D. from UC Hastings College of Law; “Why NSA’s Bulk Data Seizures Are Illegal and Unconstitutional”; Oct. 21, 2013; http://www.fed-soc.org/publications/detail/why-nsas-bulk-data-seizures-are-illegal-and-unconstitutional -- JRS) II. The NSA’s Section 215 Bulk Data Collection Orders are Unconstitutional A. Blanket Data Seizures Are Modern Day General Warrants The Fourth Amendment has two parts: First, “The right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated.”6 And second, “no warrants shall issue, but upon probable cause, supported by oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized.”7 The Fourth Amendment was adopted to prevent general or nonspecific warrants. The Fourth Amendment requires the things to be searched or seized under a warrant to be described “particularly.”8 But the order issued to Verizon under the NSA data collection program requires the company to produce “on an ongoing daily basis … all call detail records.”9 Because they are not “particular,” such orders are the modern incarnation of the “general warrants” issued by the Crown to authorize searches of American colonists. As with general warrants, blanket seizure programs subject the private papers of innocent people to the risk of searches and exposure, without their knowledge and with no realistic prospect of a remedy. The Founders thought that the seizure of “papers” for later perusal or “searching” was an abuse distinct from, but equivalent to, the use of general search warrants, which is why “papers” was included in the Fourth Amendment in addition to “effects” or personal property.10 [A]t the heart of Whig opposition to seizing papers was the belief that any search of papers, even for a specific criminal item, was a general search. It followed that any warrant to sift through documents is a general warrant, even if it is specific to the location of the trove and the item to be seized.11 Allowing blanket seizures of privately-held data would constitute an unprecedented legal and constitutional sea change that should be undertaken, if at all, only after robust public debate and a constitutional amendment that is itself worded specifically enough to govern the executive branch in the future. It advisory panel of judges to which the People are not privy. is not a policy that should emerge from an Tech has changed the calculus – people reasonably expect to keep their data private Donohue 2013 (Laura K.; professor at Georgetown University Law Center and director of Georgetown’s Center on National Security and the Law; “NSA surveillance may be legal — but it’s unconstitutional”; June 21, 2013; http://www.washingtonpost.com/opinions/nsa-surveillance-may-be-legal--but-itsunconstitutional/2013/06/21/b9ddec20-d44d-11e2-a73e-826d299ff459_story.html -- JRS) As a constitutional matter, the Supreme Court has long held that, where an individual has a reasonable expectation of privacy, search and seizure may occur only once the government has obtained a warrant, supported by probable cause and issued by a judge. The warrant must specify the places to be searched and items to be seized. There are exceptions to the warrant requirement. In 1979 the court held that the use of a pen register to record numbers dialed from someone’s home was not a search. The court suggested that people who disclose their communications to others assume the risk that law enforcement may obtain the information. More than three decades later, digitization and the explosion of social-network technology have changed the calculus. In the ordinary course of life, third parties obtain massive amounts of information about us that, when analyzed, have much deeper implications for our privacy than before. As for Section 702 of FISA, the Supreme Court has held that the Fourth Amendment does not protect foreigners from searches conducted abroad. But it has never recognized a foreign intelligence exception to the warrant requirement when foreign-targeted searches result in the collection of vast stores of citizens’ communications. Americans reasonably expect that their movements, communications and decisions will not be recorded and analyzed by the government. A majority of the Supreme Court seems to agree. Last year, the court considered a case involving 28-day GPS surveillance. Justice Samuel Alito suggested that in most criminal investigations, long-term monitoring “impinges on expectations of privacy.” Justice Sonia Sotomayor recognized that following a person’s movements “reflects a wealth of detail about her familial, political, professional, religious, and sexual associations.” The FISC is supposed to operate as a check. But it is a secret court, notorious for its low rate of denial. From 1979 to 2002, it did not reject a single application. Over the past five years, out of nearly 8,600 applications, only two have been denied. Allowing mass collection is bad precedent – makes a mockery of 4th Amendment Granick and Sprigman 2013 Jennifer Stisa Granick, director of civil liberties at the Stanford Center for Internet and Society; Christopher Jon Sprigman, professor at the University of Virginia School of Law; “The Criminal N.S.A”; June 27, 2013 http://www.nytimes.com/2013/06/28/opinion/the-criminalnsa.html?pagewanted=all&_r=0 – JRS) The Fourth Amendment obliges the government to demonstrate probable cause before conducting invasive surveillance. There is simply no precedent under the Constitution for the government’s seizing such vast amounts of revealing data on innocent Americans’ communications. The government has made a mockery of that protection by relying on select Supreme Court cases, decided before the era of the public Internet and cellphones, to argue that citizens have no expectation of privacy in either phone metadata or in e-mails or other private electronic messages that it stores with third parties. This hairsplitting is inimical to privacy and contrary to what at least five justices ruled just last year in a case called United States v. Jones. One of the most conservative justices on the Court, Samuel A. Alito Jr., wrote that where even public information about individuals is monitored over the long term, at some point, government crosses a line and must comply with the protections of the Fourth Amendment. That principle is, if anything, even more true for Americans’ sensitive nonpublic information like phone metadata and social networking activity. We may never know all the details of the mass surveillance programs, but we know this: The administration has justified them through abuse of language, intentional evasion of statutory protections, secret, unreviewable investigative procedures and constitutional arguments that make a mockery of the government’s professed concern with protecting Americans’ privacy. It’s time to call the N.S.A.’s mass surveillance programs what they are: criminal. Cloud computing changes the equation – we’re not talking about a purse anymore Raysman and Brown, June 9, 2015 (Richard Raysman is a partner at Holland & Knight and Peter Brown is the principal at Peter Brown & Associates; “How Has Digital Ubiquity Affected Fourth Amendment Law?”; New York Law Journal; http://www.newyorklawjournal.com/id=1202728535476/How-Has-Digital-Ubiquity-Affected-FourthAmendment-Law#ixzz3eVZI52AM -- JRS) Moreover, the increasing prevalence of cloud computing has further complicated the scope of privacy interests vast quantities of personal data are now accessible via remote servers often run by third-party providers. See Com. v. Stem, 96 A.3d 407 (Pa. Super. Ct. 2014) (citing Riley to conclude a warrantless search of a cell phone was unconstitutional; later expressing qualms about the warrantless search of data located in the cloud). Data stored in the cloud can be accessed unbeknownst to the user, which creates further hurdles in an attempt to redress any invasion of privacy occurring as a result of access to the data. In the past, any remote search of a container, such as a purse, was necessarily limited to the size of the container. With associated with a digital data device, as respect to even the most limited digital storage devices, this is hardly so. Blanket collection is unconstitutional Barnett and Harper 2013 (Randy E. Barnett, Carmack Waterhouse Professor of Legal Theory at the Georgetown University Law Center, director of Georgetown Center for the Constitution, formerly a prosecutor in States’ Attorney’s Office in Chicago, represented the National Federation of Independent Business in its 2011 constitutional challenge to the Affordable Care Act, argued the 2004 medical marijuana case of Gonzalez v. Raich before the U.S. Supreme Court, won 2008 Guggenheim Fellowship in Constitutional Studies, publications include more than one hundred articles and reviews, as well as nine books, including Restoring the Lost Constitution: The Presumption of Liberty, Oxford Introductions to U.S. Law: Contracts, Contracts: Cases and Doctrine, and Constitutional Law: Cases in Context, B.A., Northwestern, J.D., Harvard; Jim Harper Global Policy Counsel of the Bitcoin Foundation, Senior Fellow at Cato, formerly counsel to committees in both the U.S. House and Senate, and provided government relations counsel to PayPal, VeriSign, and other companies in tech, telecom and e-commerce, original member of the U.S. Department of Homeland Security’s Data Privacy and Integrity Advisory Committee, co-edited the book Terrorizing Ourselves: How U.S. Counterterrorism Policy Is Failing and How to Fix It, J.D. from UC Hastings College of Law; “Why NSA’s Bulk Data Seizures Are Illegal and Unconstitutional”; Oct. 21, 2013; http://www.fed-soc.org/publications/detail/why-nsas-bulk-data-seizures-are-illegal-and-unconstitutional -- JRS) Conclusion In a republican form of government based on popular sovereignty, the people are the principals or masters and those in government are their agents or servants. For the people to control their servants, they must know what their servants are doing. The secrecy of these programs, and the proceedings by which their constitutionality is assessed, make it impossible to hold elected officials and appointed bureaucrats accountable. Internal governmental checks, and even secret congressional oversight, are no substitute for the sovereign people being the ultimate judge of their servants’ conduct in office. Such judgment and control is impossible without the information that secret programs conceal. Without the recent leaks, the American public would have no idea of the existence of these programs, and it still cannot be certain of their scope. What we do know reveals that these programs are contrary to statute, and unconstitutional under any theory. The American people need relief from this unprecedented surveillance of them by their servants. Blanket collection is like a general warrant Barnett 2015 (Randy, Carmack Waterhouse Professor of Legal Theory at the Georgetown University Law Center, director of Georgetown Center for the Constitution, formerly a prosecutor in States’ Attorney’s Office in Chicago, represented the National Federation of Independent Business in its 2011 constitutional challenge to the Affordable Care Act, argued the 2004 medical marijuana case of Gonzalez v. Raich before the U.S. Supreme Court, won 2008 Guggenheim Fellowship in Constitutional Studies, publications include more than one hundred articles and reviews, as well as nine books, including Restoring the Lost Constitution: The Presumption of Liberty, Oxford Introductions to U.S. Law: Contracts, Contracts: Cases and Doctrine, and Constitutional Law: Cases in Context; “Security Vs. Freedom: Contemporary Controversies: The Thirty-Third Annual Federalist Society National Student Symposium On Law And Public Policy -- 2014: Why The NSA Data Seizures Are Unconstitutional”; Harvard Journal of Law & Public Policy; 38 Harv. J.L. & Pub. Pol'y 3; Winter 2015 – JRS) I. BLANKET DATA SEIZURES ARE MODERN DAY GENERAL WARRANTS The Fourth Amendment has two parts. First, "The right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated." n11 And second, "no warrants shall issue, but upon probable cause, supported by oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized." n12 We know that the Fourth Amendment was adopted to prevent, among other things, what were called "general" or non-specific warrants, which were blanket authorizations for British authorities to search for contraband wherever they might choose. In response to this abuse, the Fourth Amendment requires [*6] the things to be searched or seized under a warrant to be described "particularly." n13 With this in mind, the problem with the data collection orders issued to Verizon and other telecommunications companies becomes obvious. These orders require the company to produce "on an ongoing daily basis . . . all call detail records." n14 Because they are not "particular," such orders are the modern incarnation of the general warrants issued by the Crown. As with general warrants, blanket seizure programs subject the private information of innocent people to the risk of searches and exposure, without their knowledge and with no realistic prospect of a remedy. Ext: 4th Amendment solves Metadata should be seen as “papers and effects” under the 4th Amendment Cuccinelli and Fitzgibbons, June 1, 2015 (Ken Cuccinelli is the former attorney general of Virginia. Mark Fitzgibbons is co-author with Richard Viguerie of The Law That Governs Government: Reclaiming The Constitution From Usurpers And Society's Biggest Lawbreaker; “NSA and how the Fourth Amendment stops government abuses”; http://www.washingtonexaminer.com/nsa-and-how-the-fourth-amendment-stops-governmentabuses/article/2565387 -- JRS) The Constitution's Bill of Rights was written in broad strokes in the context of the era. The First Amendment freedom of the press, naturally extended to radio, then television, neither of which existed when the Bill of Rights was adopted. The Fourth Amendment's protections of "papers and effects," which are private records and property, should naturally extend to metadata. The government's authority to reach metadata of persons and merchants should be read in this originalist context. To preserve the Fourth Amendment, certain reforms would be useful in clarifying it for the 21st Century, and correcting mistakes of judicial, executive and legislative interpretation. First, there should be no presumption that private records in the possession of private third parties may be taken by the government without probable cause. Also, all warrants — and that includes administrative subpoenas — should be issued only by neutral judges or magistrates to preserve the separation of powers inherent in the Fourth Amendment. Because warrants are issued in chambers, there is no danger in matters of national security. In Virginia, we have participated in promoting a "21st Century Fourth Amendment" that includes these needed reforms and more, including tightening the definition of probable cause to ensure valid laws are being enforced. These originalist reforms make sense for all the states, and even for the federal government, in protecting our security from Orwellian government. Analogy to sifting through papers supports the plan Husain 2014 (Waris Husain, Esq., adjunct professor at Howard University School of Law, faculty adviser for Goler Teal Butcher International Moot Court Team, currently pursuing his S.J.D. at American University Washington College of Law, writing a comparative dissertation focusing on the Supreme Courts of the United States, Pakistan and India, LL.M. in international human rights and international business from Washington College of Law, JD Howard University BA in government from the College of William and Mary; “Surveillance And Law Enforcement: Tools In The Fight Against Terror In A Comparative Study Of The United States And Pakistan”; 21 ILSA J Int'l & Comp L 25; ILSA Journal of International & Comparative Law, Fall 2014 – JRS) B. Recommendations The general recommendation to both the United States and Pakistan regarding surveillance laws is to reevaluate the way in which the government and its intelligence agencies interpret the balance between security and privacy. There should be an increased reliance on the historical protections afforded to citizens through physical searches by analogizing them to modern surveillance practices. Both Pakistan and the United States have developed laws and common law practices that require the state to respect the privacy of its citizens by limiting the scope of its searches, which should be respected by intelligence agencies in battling terrorism. Along with respecting the rights of the citizen, the investigating authorities must also respect the right of the judicial branch to be involved throughout the surveillance process in order to hold the authorities accountable for their duty to uphold the security-privacy balance. The warrant requirement is an embodiment of this right, and should continue to be applied for terrorism cases in both Pakistan, through the Fair Trial Act, and the United States, through the FISA courts. For the United States, the executive branch and FISA courts themselves should reconsider easing the burden of proof for investigating authorities dealing with terrorism, and should maintain the "probable cause" standard or something near it in order to allow the government to investigate properly without intruding on the rights of citizens. In Pakistan, the Fair Trial Act should either be amended or interpreted by the Supreme Court as requiring proof of probable cause for warrant requesting agencies, rather than the "reasonable suspicion" standard currently in place. The wall between criminal investigation and intelligence gathering should be reconstructed in order to limit the scope of surveillance that international intelligence agencies can engage in domestically. For the United States, there needs to be a restructuring of the surveillance process to prohibit the CIA from being able to either receive warrants from the FISA courts to monitor citizens, or worse, to do so without a warrant. The FBI and local police authorities should continue to share information and conduct surveillance in pursuit of criminal prosecutions. In Pakistan, the Fair Trial Act should be reexamined to place a greater emphasis on the power of local police in investigating terrorist plots through electronic surveillance, shifting this power out of the hands of the nation's intelligence agencies like the lSI. Further, while the target of warrant should likely not be informed of the government's monitoring as is required in physical searches, there must [*59] be something that holds intelligence agencies and police accountable for their actions. These officials often rely on governmental immunity to avoid punishment for carrying out abuses of the surveillance process. Therefore, a personal enforcement mechanism is the only way to hold these individuals accountable. Both countries should consider allowing the same judicial body that grants warrants the power to hold intelligence officers in contempt of court if they are attempting to abuse the warrant process, either by bringing frivolous requests or failing to abide by the limitations required by the warrant. Lastly, maintaining a proper balance between constitutional rights and the duty of the state to investigate and prosecute terrorism will require a vigilant judicial body and a more respectful executive branch. Judges have been silenced in many ways in the age of terrorism either fearing for their personal safety as in Pakistan, or the risk of allowing another terrorist attack to occur due to inadequacies in the judicial process, as in the United States. However, just as in all other criminal cases, the job of the judiciary is to hold the state accountable for when it wishes to invade the privacy or freedom guaranteed to its citizens. Holding the state accountable for its duties does not equate to co-opting or assisting terrorism, but rather, is an ideological assault against the lawless nature of terrorist methodologies. As guardians of the Constitution, the judicial branch must be reinvigorated regarding issues of privacy and modem surveillance, rather than conceding to fear-mongering and anti-judicial principles advocated by anti-terrorism hawks. History and plain text supports the plan Milligan 2014 (Luke M.; law professor at Univ. of Louisville; “The Forgotten Right to Be Secure”; Hastings Law Journal, Vol. 65:713, Apr 2014; http://ssrn.com/abstract=2302850 – JRS) The Fourth Amendment can be read, however, to safeguard more than a right to be “spared” an unreasonable search or seizure.20 The Amendment provides for “[t]he right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures.”21 Unlike its textual counterparts (such as “search,” “seizure,” and “unreasonable”), the “to be secure” phraseology remains largely forgotten: it is treated on mere occasion by and textual analyses of “to be secure,” however, suggest the existence of a Fourth Amendment right to “protection” against unreasonable searches and seizures, and perhaps a right to be “free from fear” against such government action. Support for these interpretations of “to be secure” rest in the dictionary definitions of “secure,”24 the structure of the Fourth Amendment,25 and founding-era discourse concerning searches and seizures, which regularly emphasized the harms attributable to the potentiality of unreasonable searches and seizures.26 commentators;22 and it has been left undefined in the case law.23 Historical Standing and judicial review solves Correia 2014 (Evan R. C.; J.D. Candidate, May 2015, Temple University Beasley School of Law; “Note & Comment: Pulling Back The Veil Of Secrecy: Standing To Challenge The Government's Electronic Surveillance Activities”; Temple Political & Civil Rights Law Review; 24 Temp. Pol. & Civ. Rts. L. Rev. 185; Fall 2014 – JRS) The Klayman and ACLU v. Clapper decisions demonstrate the potential for the judiciary to subject government surveillance to meaningful scrutiny. n306 Specifically, there must be a review process that is open and adversarial, as opposed to the one-sided, closed hearings before the FISC in which judges consider only arguments from the government and operate in secret. n307 However, even if both suits ultimately succeed on appeal, the impact would likely affect only the government's collection of metadata. Measures must be adopted to facilitate meaningful judicial review of other government surveillance programs rather than [*214] the present reliance on the disclosure of classified material. In the field of electronic surveillance, the role of the judiciary is essential to ensuring a proper separation of powers and protecting individuals from "unreasonable searches and seizures" by the government as provided by the Fourth Amendment. n308 Conclusion Looking back at the events of 2013, in light of the extensive legislative history of government electronic surveillance, one can see the problems currently facing those who seek to challenge the constitutionality of the government's activities. While the Snowden leaks revealed the scope of some, but certainly not all, of the government's electronic surveillance, the Supreme Court's decision in Clapper will remain a significant obstacle for future litigants who do not have evidence of the kind leaked by Snowden. The leak's role in the establishment of the panel and the filing of Klayman and ACLU v. Clapper are important to the protection of privacy rights. However, they are not aimed at fixing the underlying problem: that government surveillance programs have been effectively isolated from meaningful judicial review. The only way to properly remedy the issue is to reform the system as a whole, in a manner that would provide future litigants with the proof necessary to establish standing and subject secret government surveillance to judicial review. This does not mean a system that discloses classified material which could potentially jeopardize national security. Rather, it means a system where an adversarial process creates the proper balance between national security and the protection of individual privacy. NSA needs an overhaul – 4th amendment property rights solve Blass 2015 (Megan; J.D. Candidate 2015, University of California, Hastings College of the Law; “The New Data Marketplace: Protecting Personal Data, Electronic Communications, and Individual Privacy in the Age of Mass Surveillance Through a Return to a Property-Based Approach to the Fourth Amendment”; Hastings Constitutional Law Quarterly; 42 Hastings Const. L.Q. 577 – JRS) While discussion over the intelligence gathering programs administered by the National Security Agency exploded in 2013, concern over domestic spying is hardly a recent phenomenon.5 As early as 1975, in the aftermath of the Watergate scandal, members of Congress were concerned about the National Security Agency’s intelligence gathering programs.6 Even then, members of Congress feared that the National Security Agency’s intelligence gathering programs would be turned towards United States citizens and used in domestic spying operations.7 Almost forty years later, such fears have come true. The 2013 leaks generated more questions than answers. What remains true is that the constitutional and regulatory framework governing personal data and electronic communications needs an overhaul. In an era of intrusive domestic surveillance, individuals should own property rights in their personal data and electronic communications in order to receive the protection they are truly entitled to under the Fourth Amendment. People conceive of their data as property – plan key to trust in government and integrity of 4th Amendment Blass 2015 (Megan; J.D. Candidate 2015, University of California, Hastings College of the Law; “The New Data Marketplace: Protecting Personal Data, Electronic Communications, and Individual Privacy in the Age of Mass Surveillance Through a Return to a Property-Based Approach to the Fourth Amendment”; Hastings Constitutional Law Quarterly; 42 Hastings Const. L.Q. 577 – JRS) The Court Can Easily Apply Its Current Jurisprudence to Vested Property Rights in Personal Data and Electronic Communications The ease with which the Court’s existing trespass jurisprudence can be applied to personal data and electronic communications demonstrates that vesting property rights in those intangibles in order to facilitate application of the trespass theory will provide more Fourth Amendment protection. Analyzing surveillance of e-mail and other electronic communications under a trespass theory would be novel in the criminal context, but not in the civil context, which further demonstrates the ease by which the Court could apply its trespass theory of the Fourth Amendment to electronic communications and personal effects.99 A return to a property basis is valuable for additional reasons, however. C. Property Law Concepts More Accurately Represent Public Conceptions of Electronic Communications, Personal Data, and Other Intangible Internet-Based Information Property law is a good fit for electronic communications and personal data for several reasons. First of all, people conceive of their emails and personal data as property.100 Like tangible personal effects, individuals generally have the right to exclude others from accessing their digital communications and personal data, even when it is in the custody of a third party, such as a hospital or financial institution.101 Harmony between the law and public expectations of what the law should be is important for the integrity of the Fourth Amendment, the courts, and our judicial system. As Lon Fuller articulated in his famous book, The Morality of Law, there is a reciprocal relationship between the government and the public, and where the public does not feel the laws are just or that the government will honor them, the citizen’s fidelity to the law will be tested.102 If people conceive of their personal data and electronic communications as property, then a congruent legal framework would vest individuals with property rights in that content, or as Patricia Mell describes it, their “electronic persona.”103 Paradoxically, while individuals may conceive of their personal data and electronic communication as property, the ability to restrict access and the disclosure restrictions and procedures imposed upon third parties in possession of such personal information are largely rooted in concepts of privacy, not property.10 4th amendment justifies standing for surveillance cases Slobogin, March 2015 (Christopher, Milton Underwood Professor of Law, Vanderbilt University Law School, has been cited in almost 3,000 law review articles and treatises and more than 100 judicial opinions, including three U.S. Supreme Court decisions, Fulbright Scholar, J.D., LL.M. University of Virginia, A.B. Princeton University; “Symposium Issue: The Future of National Security Law: Standing and Covert Surveillance; Pepperdine Law Review; 42 Pepp. L. Rev. 517 – JRS) Consider, first, Professor Luke Milligan’s interpretation of the first eight words of the Fourth Amendment, to wit, “[t]he right of the people to be secure” against unreasonable searches and seizures.102 Pointing to colonial dictionaries, case law, legislation and literature, Professor Milligan argues that the Fourth Amendment’s choice of the words “[t]he right of the people” and “to be secure,” combined with the colonists’ clear disdain for general warrants, demonstrates that the framers were as worried about the oppression caused by a regime of unreasonable searches as they were about preventing particular searches.103 Thus, contrary to the Court’s statements in Clapper and Laird, Professor Milligan concludes that the Constitution guarantees not only freedom from unreasonable searches and seizures but also freedom from the fear of such searches and seizures .104 In other words, the Fourth Amendment’s history, structure and text demonstrate that the Fourth Amendment has preemptive as well as sanctioning power. Acceptance of that argument does not necessarily mean that every United States citizen ought to have standing to challenge a statute on a chilling theory. To assure the efficient use of judicial resources, adequate advocacy and the other positive attributes associated with the case and controversy requirement, plaintiffs should have to show, as the plaintiffs in Clapper did,105 that the government has officially adopted an unregulated surveillance program that has affected their communications in specifiable ways. More specifically, plaintiffs should only have standing if they can show: (1) the existence of a surveillance program that does not adhere to traditional Fourth Amendment constraints (i.e., a warrant based on particularized probable cause),106 which (2) causes a significant, concrete and reasonable (i.e., not a “fanciful” or “paranoid”) modification of the plaintiffs’ typical methods of communicating with other people, particularly (given the Fourth Amendment’s focus) their private methods of communicating. For prudential reasons, the plaintiffs might also be required to demonstrate that (3) the inhibited activity is not criminal in nature and that (4) the covert nature of the surveillance program means that it is not likely to be challenged through another judicial forum. Fourth amendment already changing – privacy should trump law enforcement for blanket collection Raysman and Brown, June 9, 2015 Richard Raysman is a partner at Holland & Knight and Peter Brown is the principal at Peter Brown & Associates; “How Has Digital Ubiquity Affected Fourth Amendment Law?”; New York Law Journal; http://www.newyorklawjournal.com/id=1202728535476/How-Has-Digital-Ubiquity-Affected-FourthAmendment-Law#ixzz3eVZI52AM http://www.newyorklawjournal.com/id=1202728535476/How-Has-Digital-Ubiquity-Affected-FourthAmendment-Law#ixzz3eVYB5zo9 – JRS) Conclusion As Riley and its progeny epitomize, Fourth Amendment jurisprudence has been permanently altered as a result of the proliferation of data storage devices, namely smart phones and PCs. After all, some of the most forceful language from the majority opinion in Riley elucidates why a search of a purse versus an examination of a hard drive is an irreconcilable dissimilarity. The implications for privacy interests and law enforcement prerogatives are now continuously subject to rapid revision. Some exceptions to the Fourth Amendment warrant requirement remain unchecked, while others appear anachronistic. The exceptions contingent on the consent or prior search of a device remain largely intact, as whether by choice or not, one's privacy interests in personal information, no matter how damning or testimonial, is diminished once it has been divulged to someone other than law enforcement. However, even when such interest is weakened, the breadth and depth of information that can be gleaned from a cursory glance at contacts, messages, files, and metadata, even during an ostensibly targeted search as in Lichtenberger, warrants a reassessment of law enforcement rights to this information, even after it is no longer technically private. What is most apparent is that privacy interests associated with these devices have been reappraised, and subsequently heightened. As the Chief Justice opined in Riley, modern cell phones are hardly "just another technological convenience," and in fact could contain and reveal "the privacies of life." Accordingly, such gateways to the most intimate components of one's life must be evaluated with a greater emphasis on retaining that privacy, even at the expense of the ability of law enforcement to combat crime. Precisely how much such ability will be constricted remains largely uncertain, but the trend heretofore has favored the accused, even in milieus in which governmental interests are reiterated to be at their apogee. Using providers with privacy policies should be evidence of an expectation of privacy Barnett 2015 (Randy, Carmack Waterhouse Professor of Legal Theory, Georgetown University Law Center. Director, Georgetown Center for the Constitution; “Security Vs. Freedom: Contemporary Controversies: The Thirty-Third Annual Federalist Society National Student Symposium On Law And Public Policy -- 2014: Why The NSA Data Seizures Are Unconstitutional”; Harvard Journal of Law & Public Policy; 38 Harv. J.L. & Pub. Pol'y 3; Winter 2015 – JRS) And with regard to information of our private activity that is entrusted to third parties, the Court should now recognize that, when consumers enter into terms of service contracts, whether with telecommunications companies, banks, or credit card companies, containing privacy assurances, they "reasonably expect" their information to be used solely in ways specified in those policies. n61 As Justice Marshall observed in his dissenting opinion in Smith, "[t]hose who disclose certain facts to a bank or phone company for a limited business purpose need not assume that this information will be released to other persons for other purposes." n62 When people put their information behind passwords, they "reasonably expect" it to be private, every bit as much as Mr. Katz did when he shut the door to the public phone booth. n63 As Justice Sotomayor noted in her concurring opinion in Jones, the third-party doctrine "is ill suited to the digital age, in which people reveal a great deal of information about themselves to third parties in the course of carrying out mundane tasks." n64 The NSA's program of "pen registers for everyone" has shown how the conventional reading of Katz's "reasonable expectation of privacy" test is patently unsuited for the age of mass storage of data accessed in secret and analyzed by super computers. SOP justifies standing SOP concerns justify standing Slobogin, March 2015 (Christopher, Milton Underwood Professor of Law, Vanderbilt University Law School, has been cited in almost 3,000 law review articles and treatises and more than 100 judicial opinions, including three U.S. Supreme Court decisions, Fulbright Scholar, J.D., LL.M. University of Virginia A.B. Princeton University; “Symposium Issue: The Future of National Security Law: Standing and Covert Surveillance; Pepperdine Law Review; 42 Pepp. L. Rev. 517 – JRS) This Article describes and analyzes standing doctrine as it applies to covert government surveillance, focusing primarily on practices thought to be conducted by the National Security Agency (NSA), although the analysis could also apply to covert domestic surveillance programs, such as fusion centers.6 Part II of the Article describes the current state of standing law in the covert surveillance context. The Supreme Court has made challenges to this type of surveillance very difficult, on the ground that they intrude upon the power of the legislative and executive branches. Part III of this Article explains why this view misconstrues the nature of claims that contend covert surveillance practices are unconstitutional. Whether based on the Fourth Amendment’s prohibition on unreasonable searches and seizures or the First Amendment’s guarantee against abridgements of speech and association, these claims seek to ensure that the political branches carry out their proper roles. Specifically, in contrast to most types of generalized claims that are routinely dismissed on standing grounds, these cases seek to ensure that the legislative branch does not grant, and the executive branch does not usurp, power that can undermine the foundations of the democratic process. Relying on the process theory of John Hart Ely, this part demonstrates why litigants who can show that their ability to participate in the political process has been compromised by covert surveillance should have standing to make these constitutional claims even if they cannot prove the surveillance has been directed at them. SOP issues justify judicial review Slobogin, March 2015 (Christopher, Milton Underwood Professor of Law, Vanderbilt University Law School, has been cited in almost 3,000 law review articles and treatises and more than 100 judicial opinions, including three U.S. Supreme Court decisions, Fulbright Scholar, J.D., LL.M. University of Virginia, A.B. Princeton University; “Symposium Issue: The Future of National Security Law: Standing and Covert Surveillance; Pepperdine Law Review; 42 Pepp. L. Rev. 517 – JRS) The separation of powers rationale for a narrow standing requirement is the more potent of the two. If judicial review of decisions by the other branches is to be minimized, then a narrow standing doctrine is an effective method of doing so. That is the gravamen of Clapper. 77 Indeed, one could argue that the separation of powers rationale for a narrow standing doctrine is stronger in the context of panvasive surveillance than in many other settings. When a government action affects virtually everyone, the popularly-elected legislative branch could be said to be the best source of any remedy sought.78 The generalized grievance rule noted above is a means of implementing this notion.79 It results in a denial of standing when the relief sought “no more directly and tangibly benefits [the plaintiff] than it does the public at large.”80 Thus, the Court has often denied standing in so-called taxpayer lawsuits, as well as in suits involving claims that the environment or other general interests have been harmed by governmental action or inaction.81 As the Supreme Court stated in FEC v. Akins, 82 “the Court has sometimes determined that where large numbers of Americans suffer alike, the political process, rather than the judicial process, may provide the more appropriate remedy for a widely shared grievance.”83 When the widely shared grievance has to do with the proper functioning of the political process itself, however, the calculus should change. Akins itself recognized this point. That case involved a claim that the government had erroneously categorized an organization as a “political committee” for election campaign purposes, resulting in the plaintiffs’ inability to force the organization to abide by statutory spending reporting requirements.84 In deciding that the plaintiffs had standing to pursue this claim, the Court stated that where the asserted injury is “directly related to voting, the most basic of political rights,” then “the fact that it is widely shared does not deprive Congress of constitutional power to authorize its vindication in the federal courts.”85 Akins suggests that when the plaintiffs’ claim is directed at the functioning of the political process rather than at a statute or action that results from that process, standing requirements should be relaxed. SOP justifies standing independent of 1st and 4th amendments Slobogin, March 2015 (Christopher, Milton Underwood Professor of Law, Vanderbilt University Law School, has been cited in almost 3,000 law review articles and treatises and more than 100 judicial opinions, including three U.S. Supreme Court decisions, Fulbright Scholar, J.D., LL.M. University of Virginia, A.B. Princeton University; “Symposium Issue: The Future of National Security Law: Standing and Covert Surveillance; Pepperdine Law Review; 42 Pepp. L. Rev. 517 – JRS) The political process theory of constitutional interpretation might provide such an explanation. As laid out by John Hart Ely in Democracy and Distrust, political process theory dictates a narrow vision of judicial review when courts are interpreting vague provisions like the Equal Protection and Due Process Clauses.113 But while Ely thought courts should resist gleaning substantive meaning from amorphous constitutional language, he argued that courts should still be quite willing to protect “participational values” associated with voting, political involvement, government transparency, and the like.114 Those are the values, Ely argued, “(1) with which our Constitution has preeminently and most successfully concerned itself, (2) whose ‘imposition’ is not incompatible with, but on the contrary supports, the American system of representative democracy, and (3) that courts set apart from the political process are uniquely situated to ‘impose.’”115 According to Ely, the Constitution establishes “a process of government,” to wit, representative democracy.116 The role of the judiciary in this constitutional scheme is to discern when the democratic process is not functioning properly. Echoing the language in footnote four of United States v. Carolene Products Co.,117 Ely emphasized that any legislative or executive action that undermines interests “essential to political participation” should be declared unconstitutional by the courts.118 As developed in the next section, this language describes a separation of powers principle that could provide a merits ground, independent of the Fourth and First Amendments, for challenging certain types of government actions. But it also is relevant to standing analysis; more specifically, it anticipates the holding in Akins, 119 without the constricting requirement that Congress authorize the suit. Political process theory dictates that citizens whose participation in the political process is concretely affected by a government action should be able to challenge it. If one adopts this political process perspective in thinking about standing to challenge covert practices like the NSA’s metadata program, the question then becomes how covert surveillance might affect this participation. Professor Richards provides a hint with his observation that “unconstrained surveillance, especially of our intellectual activities, threatens a cognitive revolution that cuts at the core of the freedom of the mind that our political institutions presuppose.”120 This is a chilling argument, but a chilling argument framed in terms of its impact on the political process, not on individual rights. Standing requirements are supposed to protect SOP Slobogin, March 2015 (Christopher, Milton Underwood Professor of Law, Vanderbilt University Law School, has been cited in almost 3,000 law review articles and treatises and more than 100 judicial opinions, including three U.S. Supreme Court decisions, Fulbright Scholar, J.D., LL.M. University of Virginia, A.B. Princeton University; “Symposium Issue: The Future of National Security Law: Standing and Covert Surveillance; Pepperdine Law Review; 42 Pepp. L. Rev. 517 – JRS) Standing doctrine in federal court places a heavy burden on plaintiffs to show that the government action claimed to be illegal had, is having, or will have a direct effect on them. The plaintiff must show a “concrete and particularized” harm that is “actual or imminent, not conjectural or hypothetical,” that is “fairly traceable” to the defendant’s conduct, and that is “likely” to be redressed by a favorable decision.64 Additionally, the plaintiff’s claim must assert his or her own interest, not the interest of a third party,65 state something more than a “generalized grievance” aimed merely at assuring the government abides by the law,66 and fall within the “zone of interests” protected by the relevant statute.67 According to the Supreme Court, these standing requirements exist for two reasons. First, they implement Article III of the Constitution, which limits federal court jurisdiction to certain “Cases” and “Controversies.”68 The case-and-controversy requirement helps ensure that litigants advocate the case diligently, maximizes efficient use of scarce judicial resources, limits judicial inquiries into those matters most conducive to investigation through the adversarial process, and minimizes the issuance of advisory opinions unelucidated by a specific fact pattern.69 The second reason for the standing requirement, and the one emphasized in Clapper, is the desire to prevent “the judicial process from being used to usurp the powers of the political branches.”70 As the Court stated in Raines v. Byrd, 71 the Court’s standing inquiry “has been especially rigorous when reaching the merits of the dispute would force us to decide whether an action taken by one of the other two branches of the Federal Government was unconstitutional.”72 In the covert surveillance context, the first rationale should not carry much weight. As in Clapper, the parties will often be composed of lawyers and human rights activists, who can be counted on to pursue their constitutional claims aggressively.73 Amicus briefs can and will fill any gaps in constitutional argumentation left by the parties, at least at the ultimate appellate stages of the litigation.74 Further, if the challenge is a facial one or is aimed at the surveillance program as a whole (e.g., an attack on the bulk collection process or on the hop rule75), any ambiguity about how the program worked in a particular instance against a particular plaintiff will not affect the ability of the court to resolve the issues raised. If and when the courts determine that the program is constitutional on its face, as-applied challenges could be subject to more demanding standing requirements, analogous to what Clapper imposed, or to limitations in the discovery process.76 Slobogin, March 2015 (Christopher, Milton Underwood Professor of Law, Vanderbilt University Law School, has been cited in almost 3,000 law review articles and treatises and more than 100 judicial opinions, including three U.S. Supreme Court decisions, Fulbright Scholar, J.D., LL.M. University of Virginia, A.B. Princeton University; “Symposium Issue: The Future of National Security Law: Standing and Covert Surveillance; Pepperdine Law Review; 42 Pepp. L. Rev. 517 – JRS) One response to standing arguments based on the insights of scholars like Milligan and Richards is that they ignore the close relationship between standing and the scope of the right in question.131 Indeed, when the Fourth Amendment is the basis for the claim, the Supreme Court has explicitly conflated standing with the Amendment’s substance. In Rakas v. Illinois, 132 the Court stated that the decision as to whether a defendant can make a Fourth Amendment claim “forthrightly focuses on the extent of a particular defendant’s rights under the Fourth Amendment, rather than on any theoretically separate, but invariably intertwined concept of standing.”133 If a government action is not a Fourth Amendment “search” vis-à-vis the litigant, Rakas held, then the litigant lacks standing to challenge it. If that reasoning is the correct approach to standing, then in cases challenging covert surveillance on Fourth or First Amendment grounds everything rides on whether the surveillance, as it operates in the way the plaintiff describes it, infringes the plaintiff’s reasonable expectations of privacy or speech and association interests.134 While such a finding would presumably be made in the Clapper case, which involved the alleged interception of the content of overseas phone calls,135 it is less certain in connection with collection and querying of metadata. The Fourth Amendment is only meant to protect reasonable expectations of privacy.136 Supreme Court case law to date strongly suggests that any privacy one might expect in one’s metadata or Internet activity is unreasonable, because we assume the risk that third parties to which we knowingly impart information (here phone companies and Internet service providers) will in turn divulge it to the government.137 The same type of analysis might limit standing in cases brought under the First Amendment. As the Court intimated in Clapper, 138 one could conclude that even if speech and association are inhibited by surveillance, that inhibition proximately results from the individual’s choices, not from anything the government has done to the individual.139 On this view, even if an individual can show that he or she was targeted, standing to contest surveillance does not exist unless and until the government uses the seized information against the individual, because otherwise a colorable claim that a constitutionally cognizable interest was infringed cannot be made. Slobogin, March 2015 (Christopher, Milton Underwood Professor of Law, Vanderbilt University Law School, has been cited in almost 3,000 law review articles and treatises and more than 100 judicial opinions, including three U.S. Supreme Court decisions, Fulbright Scholar, J.D., LL.M. University of Virginia, A.B. Princeton University; “Symposium Issue: The Future of National Security Law: Standing and Covert Surveillance; Pepperdine Law Review; 42 Pepp. L. Rev. 517 – JRS) The Clapper plaintiffs wanted to argue that interception of phone calls under section 702 of FISA violated both the Fourth Amendment and the First Amendment.90 They contended they had standing to make these claims because their concern about having their overseas conversations intercepted by the NSA compromised their ability to “locate witnesses, cultivate sources, obtain information, and communicate confidential information to their clients.”91 They also alleged that, as a result of their concern about the NSA’s surveillance, they had “ceased engaging” in phone and email communications with certain people, and that they had undertaken “costly and burdensome measures” to protect confidentiality of their communications.92 In short, the plaintiffs argued that Section 702 of FISA “chilled” their communications overseas. The Second Circuit granted standing on the ground that the plaintiffs’ fear of surveillance was not “fanciful, paranoid, or otherwise unreasonable.”93 But the Supreme Court disagreed. A five-member majority concluded that “such a fear is insufficient to create standing,”94 most prominently citing Laird v. Tatum, 95 a Supreme Court decision that had denied standing to plaintiffs wanting to challenge what they hypothesized were the military’s efforts to investigate and compile dossiers on them.96 The Laird Court concluded that the ability to challenge a government surveillance practice cannot be derived from a “chilling effect aris[ing] merely from the individual’s knowledge that a governmental agency was engaged in certain activities or from the individual’s concomitant fear that, armed with the fruits of those activities, the agency might in the future take some other and additional action detrimental to that individual.”97 Taken literally, this language would deny standing not only on Clapper’s facts, but even if the plaintiffs had been able to show that their calls had been intercepted;98 only use of the intercepts against them would trigger standing under Laird. Whether the Court meant to sanction that result is not clear. But at a minimum Clapper and Laird appear to firmly reject any standing argument based on the claim that the challenged government program inhibits certain types of behavior, absent a further showing that the government has or “certainly” will take more direct action against the challengers.99 That the Court really meant “certainly” was brought home by the fact that it refused to find standing despite the dissent’s persuasive arguments that there was a “very high likelihood” the government had used and would continue to use section 702 as authority to intercept at least some of the plaintiffs’ communications.100 What the majority failed to recognize is that, while the chilling effect described by the Clapper plaintiffs did not definitively prove their calls had been intercepted, it “certainly” undermined the political process that, according to Clapper, standing doctrine is meant to protect.101 Two recent articles provide the building blocks for this argument. Slobogin, March 2015 (Christopher, Milton Underwood Professor of Law, Vanderbilt University Law School, has been cited in almost 3,000 law review articles and treatises and more than 100 judicial opinions, including three U.S. Supreme Court decisions, Fulbright Scholar, J.D., LL.M. University of Virginia A.B. Princeton University; “Symposium Issue: The Future of National Security Law: Standing and Covert Surveillance; Pepperdine Law Review; 42 Pepp. L. Rev. 517 – JRS) 90. Clapper v. Amnesty Int’l USA, 133 S. Ct. 1138, 1146 (2013). The plaintiffs also argued that section 702 violated Article III’s case and controversy requirement and separation of powers principles by allowing the Foreign Intelligence Surveillance Court to issue a warrant in the absence of a case or controversy. See Amnesty Int’l USA v. McConnell, 646 F. Supp. 2d 633, 642–43 (S.D.N.Y. 2009), vacated sub nom. Amnesty Int’l USA v. Clapper, 638 F.3d 118 (2d Cir. 2011), Standing in national security cases key to protect SOP Slobogin, March 2015 (Christopher, Milton Underwood Professor of Law, Vanderbilt University Law School, has been cited in almost 3,000 law review articles and treatises and more than 100 judicial opinions, including three U.S. Supreme Court decisions, Fulbright Scholar, J.D., LL.M. University of Virginia A.B. Princeton University; “Symposium Issue: The Future of National Security Law: Standing and Covert Surveillance; Pepperdine Law Review; 42 Pepp. L. Rev. 517 – JRS) Part V of the paper briefly addresses some objections to these arguments in favor of standing, the primary one of which is that national security matters should be handled differently than other cases. In fact, as recent allegations about the effects of executive branch spying on members of Congress and the press accentuate,7 it is precisely national security cases that most dramatically raise political process issues requiring the attention of the judiciary. These cases bring home the point that standing doctrine should be structured so that the courts have a role in ensuring the continued viability and independence of the legislative and executive branches, goals that the Court says standing doctrine is designed to enhance. As Chief Justice Roberts has said, albeit in a decision outside the standing context, “[T]he obligation of the Judiciary [is] not only to confine itself to its proper role, but to ensure that the other branches do so as well.”8 SQ standing precludes review SQ standing requirements make federal surveillance immune from judicial review Slobogin, March 2015 (Christopher, Milton Underwood Professor of Law, Vanderbilt University Law School, has been cited in almost 3,000 law review articles and treatises and more than 100 judicial opinions, including three U.S. Supreme Court decisions, Fulbright Scholar, J.D., LL.M. University of Virginia A.B. Princeton University; “Symposium Issue: The Future of National Security Law: Standing and Covert Surveillance; Pepperdine Law Review; 42 Pepp. L. Rev. 517 – JRS) By all reports, covert government surveillance activities—surveillance programs meant to be kept secret from the expanded tremendously in scope since September 11, 2001.1 Because much of this surveillance is conducted without a warrant or probable cause, it may violate the Fourth Amendment or some other constitutional provision.2 But to make that argument in court a litigant must have standing, which according to the Supreme Court exists only when the challenger can make a plausible claim of “injury” that is “concrete, particularized, and actual or imminent; fairly traceable to the challenged action; and redressable by a favorable ruling.”3 Precisely because much modern-day surveillance is covert, this demanding standing test may be impossible to meet.4 If so, unconstitutional surveillance programs may be immune from judicial review.5 general public—have SQ standing rules preclude judicial review Slobogin, March 2015 (Christopher, Milton Underwood Professor of Law, Vanderbilt University Law School, has been cited in almost 3,000 law review articles and treatises and more than 100 judicial opinions, including three U.S. Supreme Court decisions, Fulbright Scholar, J.D., LL.M. University of Virginia A.B. Princeton University; “Symposium Issue: The Future of National Security Law: Standing and Covert Surveillance; Pepperdine Law Review; 42 Pepp. L. Rev. 517 – JRS) The Court’s recent decision in Clapper v. Amnesty International USA21 involved a challenge to section 702 of the Patriot Act, which allows the NSA to intercept communications of non-U.S. persons outside the United States in the absence of individualized suspicion.22 Despite the plaintiffs’ showing that they routinely made overseas calls to parties likely to be targeted under section 702, the Court denied them standing because they could not show that their calls were in fact intercepted and thus could not prove that the injury they alleged due to the surveillance was either “actual” or “certainly impending.”23 As the outcome in Clapper illustrates, because NSA surveillance is, by design, covert, the standing requirement that plaintiffs allege a “concrete” injury can pose a serious obstacle to parties trying to challenge it.24 The majority in Clapper nonetheless insisted that “our holding today by no means insulates [section 702] from judicial review.”25 It noted that the Foreign Intelligence Surveillance Act requires that the government give notice when it “intends to use or disclose [any] information obtained or derived from [electronic surveillance]” in a criminal prosecution, and pointed out that, armed with such notice, the defendant could mount a challenge to section 702.26 The more intrusive the surveillance, the harder it is to get standing Slobogin, March 2015 (Christopher, Milton Underwood Professor of Law, Vanderbilt University Law School, has been cited in almost 3,000 law review articles and treatises and more than 100 judicial opinions, including three U.S. Supreme Court decisions, Fulbright Scholar, J.D., LL.M. University of Virginia, A.B. Princeton University; “Symposium Issue: The Future of National Security Law: Standing and Covert Surveillance; Pepperdine Law Review; 42 Pepp. L. Rev. 517 – JRS) Many of the NSA’s other surveillance regimes either do not engage in any bulk collection or appear to follow a more limited version of the twostep collection and query procedure used in the metadata program.54 If so, proof that a particular plaintiff has suffered or will suffer actual injury will be harder to establish even for challengers of the first-stage data collection process. And, in contrast to Judge Leon’s characterization of the metadata query process in Klayman , the query process in these other surveillance programs is much more likely to start with the particular “identifier” or “suspect” than with a perusal of the general database,55 meaning that any given plaintiff will probably be unable to prove that he has been subject to the second stage of the surveillance. In fact, under Clapper, when surveillance is covert there is almost an inverse relationship between the intrusiveness of the surveillance visited on a target and the ability of potential targets to obtain standing. If the government covertly zeroes in on the content of person’s phone call, email, or bank records, it is usually relying on some type of suspicion, however attenuated, a fact which, by definition, means the query will not have the panvasive nature that bolsters the case for standing vis-a-vis the NSA’s bulk collection program. That means that, in the absence of notice, no individual will be able to provide more than “speculation” as to whether he or she has been targeted. Other possible mechanisms for challenging the metadata program and related programs are unlikely to pick up the slack. Of course, as it has with communications interceptions, Congress could grant standing (and require the predicate notice) to those criminal defendants who are aggrieved by metadata surveillance.56 But because these programs are even more covert than the Section 702 warrant-based interceptions involved in Clapper—and given the government’s penchant for engaging in “parallel construction”57— the chances of such notice would probably be slim to none.58 Congress could also create a special advocate in the Foreign Intelligence Surveillance Court to represent the interests of those whose information is queried, a procedure endorsed by President Obama’s special commission and included in the administration’s recently proposed legislation.59 But whether such an advocate’s office could be counted on to overcome its governmental provenance and the nonchalance that can come from proceeding in secret to develop into a vigorous advocate for individual constitutional claims is at best unclear.60 Moreover, the advocate’s ability to appeal an adverse decision by the FISC is tenuous.61 SQ rules preclude challenge to USFG surveillance Slobogin, March 2015 (Christopher, Milton Underwood Professor of Law, Vanderbilt University Law School, has been cited in almost 3,000 law review articles and treatises and more than 100 judicial opinions, including three U.S. Supreme Court decisions, Fulbright Scholar, J.D., LL.M. University of Virginia, A.B. Princeton University; “Symposium Issue: The Future of National Security Law: Standing and Covert Surveillance; Pepperdine Law Review; 42 Pepp. L. Rev. 517 – JRS) In sum, the federal government is engaged in widespread surveillance that, under current law as construed by the Supreme Court, may not be challengeable as a practical matter. Programs that could be blatantly unconstitutional might be allowed to continue unless and until the legislature or the executive branch decides to shut them down.62 The Supreme Court has made clear that standing need not be granted simply because unconstitutional government action may otherwise be immune from judicial review.63 But any government practice that has occasioned as much controversy as the NSA’s surveillance ought to be subject to such review if a plausible standing argument can be made. The next two parts of this Article proffer such arguments. Smith v Maryland destroys 4th Amendment Smith eviscerated 4th amendment protections Blass 2015 (Megan; J.D. Candidate 2015, University of California, Hastings College of the Law; “The New Data Marketplace: Protecting Personal Data, Electronic Communications, and Individual Privacy in the Age of Mass Surveillance Through a Return to a Property-Based Approach to the Fourth Amendment”; Hastings Constitutional Law Quarterly; 42 Hastings Const. L.Q. 577 – JRS) The Supreme Court’s Fourth Amendment Jurisprudence Does Not Adequately Protect the Rights and Interests of the Public Because it Excludes Modern Means of Communication and Data Generated Through the Use of Web-Based Applications While the NSA continues to disregard statutes such as FISA and ECPA, the public is left with little protection by way of the Constitution as currently interpreted by the Supreme Court. The Constitution, which sets the floor for government behavior where Fourth Amendment rights are implicated, provides almost no protection from unreasonable searches and seizures or the use of evidence illegally obtained by the NSA in criminal prosecutions.36 The Fourth Amendment states: The right of the people to be secure in their persons, houses, papers, and effects against unreasonable searches and seizures, shall not be violated, and no warrants shall issue, but upon probable cause, supported by oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized.37 The text of the Fourth Amendment enumerates different property items, the enumeration of which has given rise to a longstanding property-based approach to the Fourth Amendment.38 As early as 1886, the Court interpreted a search under the Fourth Amendment as occurring when the government violated a property interest, such as physical intrusion into the home or review of one’s personal documents.39 While the Court has explicitly refrained from overruling this trespass theory of the Fourth Amendment, it is no longer the only controlling doctrine.40 In Katz v. United States, the Court took steps to adopt a privacybased approach to the Fourth Amendment instead of a formalistic propertybased approach.41 In Katz, the majority, led by Justice Stewart, held that the Fourth Amendment protects people, not just constitutionally protected areas, and accordingly, that a search takes place where the government violates an individual’s privacy.42 The Katz approach that the Court has adopted since rendering a decision in the case is actually the approach articulated by Justice Harlan in his concurring opinion in Katz. 43 The often-cited rule as formulated by Harlan, and adopted by the Court, states that a search occurs when there is an intrusion upon an expectation of privacy that society is prepared to recognize as reasonable.44 Katz seems to be a reasonable expansion of Fourth Amendment protection on its face; after all, it sought to protect people as well as property. In attempting to interpret a reasonable expectation of privacy, the Court has faltered. In Smith v. Maryland, a pen register, which is a device that records the numbers dialed on a phone, was used to investigate Michael Lee Smith for the purposes of a criminal prosecution.45 Under Katz and its progeny, a person does not have a legitimate expectation of privacy in information voluntarily disclosed to a third party.46 The Court held that the use of the pen register was not a search within the meaning of the Fourth Amendment because Smith did not have a reasonable expectation of privacy in the numbers he dialed, as they were transmitted through a third party.47 Smith has serious implications in the digital age.48 The third party doctrine eviscerates Fourth Amendment protection under Katz in the modern age. Through one decision, the Court brought nearly all modern methods and modes of communication outside the operation of the Fourth Amendment.49 Through its holding in Smith v. Maryland, the Court did not just refuse to extend Fourth Amendment protection in one particular instance or create an exception. Smith made it such that surveillance and investigation involving collection or review of communications or data that have passed through an internet service provider, a precondition satisfied anytime the internet is involved, do not constitute searches.50 As Justice Sotomayor pointed out in her concurrence in United States v. Jones, the third party doctrine is “ill suited to the digital age, in which people reveal a great deal of information about themselves to third parties in the course of carrying out mundane tasks.”51 Without a reasonable expectation of privacy in the data and communications collected by the NSA, the alternative source of Fourth Amendment protection is the Court’s classic trespass theory. Absent congressional intervention in the form of legislation vesting property rights in electronic communications and personal information, the Court’s trespass theory fails to provide any protection either.52 Metadata isn’t a pen register – Smith should not control Barnett 2015 (Randy, Carmack Waterhouse Professor of Legal Theory, Georgetown University Law Center. Director, Georgetown Center for the Constitution; “Security Vs. Freedom: Contemporary Controversies: The Thirty-Third Annual Federalist Society National Student Symposium On Law And Public Policy -- 2014: Why The NSA Data Seizures Are Unconstitutional”; Harvard Journal of Law & Public Policy; 38 Harv. J.L. & Pub. Pol'y 3; Winter 2015 – JRS) [*10] In its briefs, the government intimates that the NSA is subjecting the data to computer analysis to reveal suspicious patterns. n41 But others have defended the retention of this data simply to facilitate future searches of records pursuant to later investigations. n42 Once in possession of the data, however, the federal government can use it the same way British authorities used papers seized with general warrants for later perusal to see if they revealed anything criminal. The NSA data seizures make possible fishing expeditions into the phone calling patterns of nearly all Americans, except for terrorists, who will now avoid using their phones. n43 If this is the result, then there must be a flaw somewhere in the constitutional doctrine that produced it. And indeed the fault lies in the misuse of the "third-party doctrine" as well as in Katz's problematic concept of the reasonable expectation of privacy. B. Misapplying Katz and Smith The key to understanding the flaw in the government's theory is to remember that the Fourth Amendment was, above all else, the solution to the problem of general or nonspecific warrants. n44 In Smith v. Maryland, n45 a pen register was placed by the phone company on a particular person about whom there was a reasonable suspicion--though perhaps not probable cause for seeking a search warrant. n46 Indeed, previous applications of the third party doctrine to business records, such [*11] as bank records or emails, have concerned investigations of a particular person or company. n47 So the first problem is that Smith v. Maryland is being stretched to cover a situation that is radically different than the law enforcement practice the Court was addressing there, and in subsequent cases. Because this ongoing blanket data seizure of every phone record in the country is unprecedented, the rationale of Smith cannot automatically be extended to this situation. This was the position taken by Judge Richard Leon of the District Court of the District of Columbia in his opinion finding that the NSA program violated the Fourth Amendment. "The question before me," he wrote, is not the same question that the Supreme Court confronted in Smith. To say the least, "whether the installation and use of a pen register constitutes a 'search' within the meaning of the Fourth Amendment,'-- under the circumstances addressed and contemplated in that case--is a far cry from the issue in this case. n48 For Judge Leon, the question to be decided today is: When do present-day circumstances --the evolutions in the government's surveillance capabilities, citizens' phone habits, and the relationship between the NSA and telecom companies--become so thoroughly unlike those considered by the Supreme Court thirty-five years ago that a precedent like Smith simply does not apply? The answer, unfortunately for the Government, is now. n49 While lower courts are certainly bound to follow Supreme Court precedent, they are not required to extend general statements made by the Court in one situation to an entirely different context. Lower courts are supposed to grapple with applying existing doctrine to new situations, and this includes identifying the limits of existing doctrine given the circumstances in which it arose. The crucial constitutional difference between Smith and all the "third-party" business records cases is particularity: the difference between a general warrant that the Fourth Amendment [*12] was enacted to prohibit, and a reasonable particularized search or seizure, which is all the Supreme Court has ever purported to authorize. n50 Court dodges the question using Smith v. Maryland Crocker and Reitman July 1 2015 (Andrew Crocker, staff attorney on the Electronic Frontier Foundation’s civil liberties team, BA and JD from Harvard, formerly worked at Berkman Center for Internet and Society, the American Civil Liberties Union’s Speech, Privacy, and Technology Project, and the Center for Democracy and Technology, M.F.A. in creative writing from New York University; Rainey Reitman, director of the activism team at the Electronic Frontier Foundation, Chief Operating Officer and co-founder of the Freedom of the Press Foundation, winner of 2013 Hugh M. Hefner First Amendment Award in Journalism, BA Bard College; https://www.eff.org/deeplinks/2015/07/same-old-fisa-court-thoughts-opinion-extending-masssurveillance-6-more-months -- JRS) The court thumbs its nose at the Second Circuit’s view that bulk telephone metadata surveillance is illegal. In a landmark decision in May, the U.S. Court of Appeals for the Second Circuit found in ACLU v Clapper that mass surveillance of telephone records was never authorized by the Patriot Act. Although appellate court decisions are usually given significant weight by district courts, the FISA Court pointed out it isn’t obligated to follow the Second Circuit’s decisions and criticized reasoning in ACLU v. Clapper. Most troublingly, the court largely doubled down on the wildly expansive interpretation of the word “relevance” in Section 215 from previous FISA Court opinions. Although nothing required it to reach the same conclusion as the Second Circuit, the FISA Court’s unnecessary dismissiveness is reminiscent of some of its one-sided opinions of old. In light of the FISA Court’s opinion, the ACLU said it will ask the Second Circuit for an injunction stopping the program from going back into effect. Third party doctrine trumps constitutional concerns. The FISA Court also dismissed all constitutional concerns with the program as it has in the past by repeatedly citing the same outdated Supreme Court case, Smith v Maryland, that has been the bane of digital rights advocates for decades. This is a case from the 1970s that found that people who use the telephone don’t have an expectation of privacy because they are sharing the fact that they are making a phone call with the telephone company itself, and thus the government has a right to access data about what phone calls are made and to whom without a judge-issued search warrant. Because the Second Circuit found that the program wasn’t authorized by the Patriot Act, it did not reach the constitutional issue, but it indicated there were significant constitutional concerns. Even so, we’re hopeful that in one of the pending lawsuits challenging the program, including EFF’s case Smith v. Obama, ACLU v. Clapper, or Klayman v. Obama, a circuit court will disagree with the FISA Court and issue a ruling soon holding that the program is in fact unconstitutional. AT Katz and Smith Katz and Smith shouldn’t apply to metadata Barnett 2015 (Randy, Carmack Waterhouse Professor of Legal Theory, Georgetown University Law Center. Director, Georgetown Center for the Constitution; “Security Vs. Freedom: Contemporary Controversies: The Thirty-Third Annual Federalist Society National Student Symposium On Law And Public Policy -- 2014: Why The NSA Data Seizures Are Unconstitutional”; Harvard Journal of Law & Public Policy; 38 Harv. J.L. & Pub. Pol'y 3; Winter 2015 – JRS) But there is a big difference between what happened in Smith and what the NSA orders are doing . In Smith, a robbery victim had described to the police both her attacker and a 1975 Monte Carlo she saw near the scene of the robbery. n30 Afterward, she began receiving threatening and obscene phone calls from a man who said he was the robber. n31 During one phone call, the man asked her to step out onto her front porch, where she saw the 1975 Monte Carlo moving slowly past her home. n32 Later, the police spotted a man who met the victim's description of [*9] her attacker driving a 1975 Monte Carlo in her neighborhood. n33 By tracing the license plate number, police learned that the car was registered in the name of petitioner, Michael Lee Smith. n34 They then asked the phone company to install a pen register at its central offices to record the numbers dialed from the telephone at his home. n35 Although the police did not obtain a warrant, hey certainly had a reasonable suspicion that Mr. Smith had engaged in illegal activity. n36 If the constitutionality of the NSA's bulk data seizure programs is to be justified as akin to a pen register under Smith, however, then these programs amount to installing a pen register on every American without any suspicion that a person, whose phone activities are now stored on the NSA's supercomputers, has done anything wrong. n37 In essence, every American is to be treated the way Michael Lee Smith was treated in Smith v. Maryland. n38 But unlike the pen register on his phone line that lasted just a few days, each of us would have pen registers on our phone every day for the rest of our lives. In the old days, the government had to go to the third party to request the pen register be installed, n39 which preserved a record of what it was doing. Moreover, had it tried to collect such information on everyone, the very massiveness of such a data trove would have itself prevented the government from storing it or doing much of anything else with it. Today, however, enormous quantities of data can be kept digitally in huge NSA facilities. n40 Plan is consistent with Katz – metadata has an expectation of privacy similar to the closed door of the phone booth Barnett 2015 (Randy, Carmack Waterhouse Professor of Legal Theory, Georgetown University Law Center. Director, Georgetown Center for the Constitution; “Security Vs. Freedom: Contemporary Controversies: The Thirty-Third Annual Federalist Society National Student Symposium On Law And Public Policy -- 2014: Why The NSA Data Seizures Are Unconstitutional”; Harvard Journal of Law & Public Policy; 38 Harv. J.L. & Pub. Pol'y 3; Winter 2015 – JRS) C. Reconsidering Katz But when this case does get back to the Supreme Court--as I hope it will if Congress does not alter the practice as it recently failed to do n51--the Court should also reconsider the "reasonable expectation of privacy" concept of Katz. As Justice Alito observed two terms ago in his concurring opinion in the GPS tracker case of United States v. Jones, n52 the "Katz expectation-of-privacy test... involves a degree of circularity, and judges are apt to confuse their own expectations of privacy with those of the hypothetical reasonable person to which the Katz test looks." n53 In addition, "the Katz test rests on the assumption that this hypothetical reasonable person has a well-developed and stable set of privacy expectations." n54 We should all remember that the "reasonable expectations" language that now dominates the academic literature and case law actually appears, not in the majority opinion of the Court in Katz, but in a soloconcurrence by Justice Harlan. n55 In contrast with Justice Harlan's concurrence, Justice Stewart's majority opinion in Katz properly rested on the physical protection that the defendant had given to his oral communications when he stepped into a phone booth and closed the door. n56 "What a person knowingly exposes to the public," he wrote "even in his own home or office, is not a subject of Fourth Amendment protection. But what he seeks to preserve as private, even in an area accessible to the public, may be constitutionally protected." n57 What Katz "sought to exclude when he entered the booth," Justice Stewart continued, was not the intruding eye--it was the uninvited ear. He did not shed his right to do so simply because he made his calls from a place where he might be seen. No less than an individual in a business office, in a friend's apartment, or in a taxicab, a person in a telephone booth may rely upon the protection of the Fourth Amendment. One who occupies it, shuts the door behind him, and pays the toll that permits him to place a call is surely entitled to assume that the words he utters into the mouthpiece will not be broadcast to the world. n58 Rather than airy and untethered judicial speculations about "reasonable expectations," the courts should return to the traditional--and more readily administrable--property and contract rights focus of Fourth Amendment protection that was reflected in the majority opinion in Katz. Courts should examine how people employ devices that function like the walls of the home, or the phone booth in Katz, to conceal digital information and preserve their privacy. An inquiry into the physical and legal barriers people have placed around their information, for example, by using passwords to restrict access to their email, or entering into terms of service contracts with third parties that include privacy protections, can generally answer whether they have held it close, and establish the threshold of personal security that the Fourth Amendment requires a warrant to cross. No distinction should be made between sealing a letter before handing it to the postman, taking a phone call in a secluded phone booth, password-protecting one's email, or selecting a communications company with a privacy policy. In short, the "reasonable expectation of privacy" test reverses the inquiry required by the Fourth Amendment. For good reason, the Fourth Amendment uses a possessive pronoun--"their"--to describe the "persons, houses, papers, and effects" it protects. People's ownership of themselves and their things is an essential counterweight to state power. And by availing themselves of the law of property and contract, people create their own zones of privacy. In short, first comes property and contract, then comes privacy. With this in mind, let us return to Katz. Plan is consistent with US v Jones, which extended the Katz protections Barnett 2015 (Randy, Carmack Waterhouse Professor of Legal Theory, Georgetown University Law Center. Director, Georgetown Center for the Constitution; “Security Vs. Freedom: Contemporary Controversies: The Thirty-Third Annual Federalist Society National Student Symposium On Law And Public Policy -- 2014: Why The NSA Data Seizures Are Unconstitutional”; Harvard Journal of Law & Public Policy; 38 Harv. J.L. & Pub. Pol'y 3; Winter 2015 – JRS) In reality, the physical and legal barriers people place around their information define both their actual and "reasonable" expectations of privacy and should provide the doctrinal touch-stone of the search warrant requirement. Two terms ago in United States v. Jones, the Supreme Court took an important step in this direction when it held that the "reasonable expectation of privacy" formulation from Katz does not supplant the protection of one's property from unreasonable searches, but instead adds additional protections to these. n59 "[T]he Katz reasonable-expectation-of-privacy test," wrote Justice Scalia, "has been added to, not substituted for, the common-law trespassory test." n60 Katz is unworkable – SCOTUS justices are privileged and have no clue what “society” considers reasonable (this also says Smith v. Maryland should be overruled) Blass 2015 (Megan; J.D. Candidate 2015, University of California, Hastings College of the Law; “The New Data Marketplace: Protecting Personal Data, Electronic Communications, and Individual Privacy in the Age of Mass Surveillance Through a Return to a Property-Based Approach to the Fourth Amendment”; Hastings Constitutional Law Quarterly; 42 Hastings Const. L.Q. 577 – JRS) IV. A Trespass Approach to the Fourth Amendment is Preferable to Katz and Any Attempts to Reform a Privacy Based Theory of the Fourth Amendment Criticism of the third party doctrine among scholars and legal practitioners is nothing new .112 Since the original revelation of the government’s warrantless wiretapping programs there has been a flurry of scholarship declaring the end of privacy and examining reasonable expectations of privacy under Katz.113 Privacy theory and jurisprudence is en vogue right now, but it will never provide as satisfactory of a solution to what ails the Fourth Amendment as a trespass theory.114 This is because the Katz doctrine was not a workable standard to begin with.115 The only way that Katz, a judicially created standard, can be rehabilitated, is if the Court, of its own volition, chooses to explicitly or implicitly overturn precedent such as Smith v. Maryland. 116 To square the reasonable expectations of privacy in various scenarios with the public’s actual expectations of privacy in the digital age would require the Court to hear and decide many cases, some of which have not even begun to wind their way through the courts, and could never wind their way through the courts at the same rate of ever-evolving technology. Ultimately, Katz should not be rehabilitated because it was not a workable doctrine to begin with. First, the Court is in a poor position to determine what privacy expectations society is prepared to recognize as legitimate.117 Progress has been made in diversifying the bench, but Supreme Court justices still come from a particularly privileged segment of society and apply precedent crafted over hundreds of years by an even less diverse bench.118 Of the current justices, all nine attended Ivy League law schools, primarily Harvard and Yale.119 The continued existence of an Ivy League track to the judiciary ensures that the justices are not from backgrounds or currently in positions that allow them to truly understand what the public and everyday Americans, Justice Harlan’s “society,” consider reasonable.120 Additionally, the method of determining a reasonable expectation of privacy is subject to wide variation depending on the methodology used to calculate it.121 The NSA mass surveillance programs are now public knowledge, so it would be technically unreasonable for the public to maintain a reasonable expectation of privacy in their personal data and electronic communications. Clearly, applying the standard in that way would result in an untenable and absurd result. Nonetheless, that is the very logic that animates the Court’s original collapsing of the concepts of secrecy and privacy in Smith v. Maryland. 122 Numbers dialed are “content” and they’re private under Katz -- Justice Stewart’s Smith v Maryland dissent explains Barnett 2015 (Randy, Carmack Waterhouse Professor of Legal Theory, Georgetown University Law Center. Director, Georgetown Center for the Constitution; “Security Vs. Freedom: Contemporary Controversies: The Thirty-Third Annual Federalist Society National Student Symposium On Law And Public Policy -- 2014: Why The NSA Data Seizures Are Unconstitutional”; Harvard Journal of Law & Public Policy; 38 Harv. J.L. & Pub. Pol'y 3; Winter 2015 – JRS) Indeed, it is useful to remember that Justice Stewart, the author of Katz, actually dissented in Smith v. Maryland. "I think that the numbers dialed from a private telephone--like the conversations that occur during a call," he wrote, are within the constitutional protection recognized in Katz. It seems clear to me that information obtained by pen register surveillance of a private telephone is information in which the telephone subscriber has a legitimate expectation of privacy. The information captured by such surveillance emanates from private conduct within a person's home or office--locations that without question are entitled to Fourth and Fourteenth Amendment protection. Further, that information is an integral part of the telephonic communication that, under Katz, is entitled to constitutional protection, whether or not it is captured by a trespass into such an area. n65 Presciently for purposes of analyzing the significance of installing pen registers for everyone, he added, The numbers dialed from a private telephone--although certainly more prosaic than the conversation itself--are not with-out "content." Most private telephone subscribers may have their own numbers listed in a publicly distributed directory, but I doubt there are any who would be happy to have broad-cast to the world a list of the local or long distance numbers they have called. This is not because such a list might in some sense be incriminating, but because it easily could reveal the identities of the persons and the places called, and thus reveal the most intimate details of a person's life. n66 When one has arranged one's affairs using physics, or the laws of property and contract, to conceal information from preying eyes, government agents may not use surreptitious means or novel technologies like thermal imaging to defeat those arrangements without obtaining a warrant that conforms to the requirement of the Fourth Amendment. n67 For this reason, the Court was correct in the 2001 case of Kyllo v. United States n68 to hold that police officers conducted a search when they used [*16] a thermal-imaging device to detect heat emanating from a private home, even though they committed no trespass. n69 Putting oneself behind closed doors creates a zone of privacy into which the police ought not intrude without a warrant. As Justice Kagan explained last year in her concurring opinion in Florida v. Jardines, n70 which involved the use of a drug sniffing dog, "[i]t is not surprising that in a case involving a search of a home, property concepts and privacy concepts should so align. The law of property 'naturally enough influence[s]' our 'shared social expectations' of what places should be free from governmental incursions." n71 Smith v. Maryland need not be reversed to distinguish its application from the radically different practice of installing pen registers for everyone. Whereas Smith concerned a particularized search that may well be "reasonable" under the Fourth Amendment, the NSA bulk-data seizure program is the modern-day equivalent of the general warrant that strikes at the very heart of the Fourth Amendment's requirement of particularity. Both the third-party doctrine of Smith and the "reasonable expectation of privacy" approach of Katz need to be adapted to modern circumstances. CP answers Congressional oversight fails – the executive branch lies to Congress Setty, 2015 (Sudha, Professor of Law and Associate Dean for Faculty Development & Intellectual Life, Western New England University School of Law; Harlan Fiske Stone Scholar from Columbia Law School and A.B. in History, concentration in comparative civil rights, with honors from Stanford University; Stanford Journal of International Law; Winter 2015; 51 Stan. J Int'l L. 69; “Surveillance, Secrecy, and the Search for Meaningful Accountability” – JRS) The extent of congressional knowledge regarding the NSA Metadata Program is not fully known to the public and has been the subject of significant debate. Nonetheless, even assuming that Congress was sufficiently informed as to the potential reach of the PATRIOT Act with regard to surveillance n59 and, therefore, that the statutory authority for the bulk data collection and storage was sound, the ability of Congress to effect significant and meaningful ex post oversight appears to be severely limited. Historically, congressional hearings and investigations have been a powerful tool to rein in executive branch overreaching. n60 However, it seems that the extreme secrecy surrounding the NSA surveillance programs undermined the efficacy of these oversight powers, to the point that they may have been reduced to an ersatz form of accountability. One prominent example stems from a Senate oversight hearing on March 12, 2013, in which Senator Ron Wyden specifically asked Director of National Intelligence James Clapper if the NSA was systematically gathering information on the communications of millions of Americans. n61 Clapper denied this, yet subsequent revelations confirmed that the broad scope of the data collection included metadata for telephonic communications, as well as content data for emails, texts, and other such writings. n62 After public discussion of the discrepancy in his testimony, Clapper commented that he gave the "least most untruthful" answer possible under the circumstances. n63 Senator Wyden expressed disappointment and frustration that even while under oath at an oversight hearing, Clapper misled the Senate. n64 The ability for congressional oversight is further hampered by a general lack of access to information about the details of the NSA Metadata Program n65 and lack of ability to discuss publicly whatever knowledge is shared with Congress. n66 In fact, it remains unclear whether senators, including Dianne Feinstein, Chair of the Senate Intelligence Committee, knew of the lapses in NSA procedure until after such information was leaked to news sources . n67 Further revelations indicate that administration statements made to Congress even after the Snowden disclosures were not entirely accurate. n68 These examples are not determinative, but taken together, they raise significant doubt to the extent of accurate information regarding surveillance programs being made available to congressional oversight committees, and whether the oversight committees can function as effective accountability measures n69 without the benefit of illegally leaked information such as the Snowden disclosures. FISC can’t solve – need external review Setty, 2015 (Sudha, Professor of Law and Associate Dean for Faculty Development & Intellectual Life, Western New England University School of Law; Harlan Fiske Stone Scholar from Columbia Law School and A.B. in History, concentration in comparative civil rights, with honors from Stanford University; Stanford Journal of International Law; Winter 2015; 51 Stan. J Int'l L. 69; “Surveillance, Secrecy, and the Search for Meaningful Accountability” – JRS) The FISC differs from Article III courts in numerous ways: Its statutory scope is limited to matters of foreign intelligence gathering; its judges are appointed in the sole discretion of the Chief Justice of the United States Supreme Court; its proceedings are secret; its opinions are often secret or are published in heavily [*83] redacted form; and its process is not adversarial as only government lawyers make arguments defending the legality of the surveillance being contemplated. n70 Many of these differences bring into doubt the legitimacy of the court, its ability to afford adequate due process regarding civil liberties concerns, and its ability to uphold the rule of law in terms of government accountability. Compounding this legitimacy deficit is the FISC's own loosening of the relevance standard under Section 215 of the PATRIOT Act such that the FISC has found that bulk data collection without any particularized threat or connection to terrorism is legally permissible. n71 Historically, the FISC has rejected NSA surveillance applications too infrequently to be considered a substantial check on government overreach as an ex ante matter. n72 As an ex post matter, it is unclear to what extent the FISC's work guarantees any meaningful accountability over NSA surveillance activities. On the one hand, because the FISC lacks an adversarial process and has no independent investigatory authority, the FISC only addresses ex post compliance problems when the government itself brings the problem to the court's attention. n73 As such, FISC judges rely on the statements of the government as to the government's own behavior and lack the authority to investigate the veracity of the government's representations. n74 For example, in 2011, the FISC found one aspect of the surveillance program - brought to its attention months after the program went into effect n75 - to be unconstitutional. n76 Additionally, in one declassified opinion, the FISC critiques the NSA's sloppy overcollection of metadata of U.S. communications, and questions the efficacy of bulk data collection as a national security measure. n77 At point, the FISC sanctioned the NSA for overreaching in one [*84] saving all metadata and running daily metadata against an "alert list" of approximately 17,800 phone numbers, only 10% of which had met FISC's legal standard for reasonable suspicion. n78 On such occasions, the administration has modified problematic aspects of the surveillance and continued forward without further impediment by the FISC. n79 On the other hand, the fact that the NSA itself has brought potential compliance incidents to the notice of the FISC n80 indicates at least some internal policing of these programs. However, this is hardly an effective substitute for external review and accountability mechanisms that would ensure that consistent controls are in place. Further, the self-reporting of these compliance incidents does not in any way allow for discourse over the larger structural questions surrounding the surveillance programs. FISC oversight fails – lack of information and fear of being blamed for terrorist attack Setty, 2015 (Sudha, Professor of Law and Associate Dean for Faculty Development & Intellectual Life, Western New England University School of Law; Harlan Fiske Stone Scholar from Columbia Law School and A.B. in History, concentration in comparative civil rights, with honors from Stanford University; Stanford Journal of International Law; Winter 2015; 51 Stan. J Int'l L. 69; “Surveillance, Secrecy, and the Search for Meaningful Accountability” – JRS) Finally, the ability of the FISC to act as an effective check on NSA overreaching is severely limited by the secrecy and lack of information available to the FISC judges. Judge Reggie B. Walton, formerly the Chief Judge of the FISC, lamented that "the FISC is forced to rely upon the accuracy of the information that is provided to the Court ... . The FISC does not have the capacity to investigate issues of noncompliance ... ." n81 The ability of the NSA to not only gather and retain bulk metadata, but also to build in backdoor access into data files despite private encryption efforts has been largely sanctioned by the FISC based on NSA representations as to the seriousness of the security threats posed to the nation. n82 In an environment in which there is a tremendous fear of being held responsible for any future terrorist attack that might occur on U.S. soil, n83 and in which there is a information deficit for those outside of the intelligence community, the FISC has consistently deferred to the NSA's assertions and has not been able to act as an effective accountability mechanism. Congress won’t solve – lack of public pressure and inside information Setty, 2015 (Sudha, Professor of Law and Associate Dean for Faculty Development & Intellectual Life, Western New England University School of Law; Harlan Fiske Stone Scholar from Columbia Law School and A.B. in History, concentration in comparative civil rights, with honors from Stanford University; Stanford Journal of International Law; Winter 2015; 51 Stan. J Int'l L. 69; “Surveillance, Secrecy, and the Search for Meaningful Accountability” – JRS) Although Congress could launch a large-scale investigation into the programs Snowden disclosed, like the Church Committee in its time, n176 its ability to serve effectively as an ongoing accountability mechanism over intelligence gathering in the manner of a parliament seems unlikely. For the political and structural reasons discussed above, the apparatus of national security policy-making is somewhat intentionally insulated from Congress. On the one hand, the benefit of this structural arrangement is that it may facilitate expertise and efficient decision-making, but a key effect is also that this apparatus is not really accessible to the other branches of government or the public. n177 This consolidation of decision-making authority in the executive branch, plus the difference between congressional and parliamentary access to executive branch information, accounts for a different potential for legislative oversight in the United States as compared to the United Kingdom and India. Further, the lack of widespread and sustained public pressure [*100] on Congress n178 toward reform suggests that a meaningful increase in legislative oversight of the intelligence community will not occur in the near future. AT CP with internal NSA reform – can’t solve, just looks like it could solve Setty, 2015 (Sudha, Professor of Law and Associate Dean for Faculty Development & Intellectual Life, Western New England University School of Law; Harlan Fiske Stone Scholar from Columbia Law School and A.B. in History, concentration in comparative civil rights, with honors from Stanford University; Stanford Journal of International Law; Winter 2015; 51 Stan. J Int'l L. 69; “Surveillance, Secrecy, and the Search for Meaningful Accountability” – JRS) Leaks like that of Snowden, combined with rigorous and responsible press coverage, can provide some level of constraint on and accountability over intelligence community activity. n179 However, the tendency toward public inertia and the possibility that democratic institutions will not actually provide a substantive check on the surveillance apparatus n180 suggest weakness in relying solely on this approach. Further, the crackdown on leaking and the treatment of whistleblowers as criminals, even prior to Snowden's disclosures, n181 combined with heightened security measures, means that reliance on leaking as a meaningful structural check is misplaced. Tinkering with the structure inside of the NSA also seems to achieve more in terms of burnishing a veneer of accountability rather than creating genuine oversight. It is hard to understand how various proposed reforms, such as appointing a civilian to oversee the NSA n182 or creating a more adversarial internal review process within the NSA, n183 would increase accountability and transparency . For the executive branch, it seems more likely that pressure from business and corporate interests trying to retain consumer business n184 may shape NSA parameters for mass data collection and domestic surveillance in some respects, n185 but will likely not lead to institutional or structural changes as to the government's approach to surveillance without additional pressure from the public. 1st Amendment SQ already chilling journalism Slobogin, March 2015 (Christopher, Milton Underwood Professor of Law, Vanderbilt University Law School, has been cited in almost 3,000 law review articles and treatises and more than 100 judicial opinions, including three U.S. Supreme Court decisions, Fulbright Scholar, J.D., LL.M. University of Virginia, A.B. Princeton University; “Symposium Issue: The Future of National Security Law: Standing and Covert Surveillance; Pepperdine Law Review; 42 Pepp. L. Rev. 517 – JRS) (**“Fourth Estate” is another term for the press/media) That different framing should make a difference in standing analysis. As the plaintiffs’ reactions in Clapper demonstrate, political participation can be compromised by legitimate fears concerning covert surveillance.121 Even more significantly, the Fourth Estate, crucial to maintaining a vibrant democracy, has been affected by the government’s surveillance practices. A 2013 survey of journalists and other writers found that, in the wake of Snowden’s disclosures, “24% have deliberately avoided certain topics in phone or email conversations.”122 A more recent report, based on a survey of forty-six journalists and forty-two lawyers, concluded that “journalists and their sources, as well as lawyers and their clients, are changing their behavior in ways that undermine basic rights and corrode democratic processes.”123 This report noted that “[s]everal journalists likened the current reporting atmosphere to what one might find in more authoritarian countries.”124 1st amendment should provide standing for surveillance cases Slobogin, March 2015 (Christopher, Milton Underwood Professor of Law, Vanderbilt University Law School, has been cited in almost 3,000 law review articles and treatises and more than 100 judicial opinions, including three U.S. Supreme Court decisions, Fulbright Scholar, J.D., LL.M. University of Virginia, A.B. Princeton University; “Symposium Issue: The Future of National Security Law: Standing and Covert Surveillance; Pepperdine Law Review; 42 Pepp. L. Rev. 517 – JRS) A similar rule might be derived from the First Amendment’s language stating that freedom of speech and association should not be “abridg[ed].”107 To abridge means “to lessen the strength or effect of.”108 As many scholars have noted, surveillance has precisely that effect on communication and related activities .109 Professor Neil Richards has recently argued, for instance, that “the fear of being watched causes people to act and think differently from the way they might otherwise.”110 A considerable empirical literature backs up the claim that “panvasive surveillance” leads individuals “to make choices that conform to mainstream expectations.”111 Because unconstrained surveillance can lead to “self-censorship, in terms of speech, action, or even belief,” Richards contends that people should have standing to challenge this type of surveillance on First Amendment grounds.112 Although Richards does not go into any detail about the specifics of this standing proposal, the above Fourth Amendment formulation might work just as well in the First Amendment context. The arguments from Professors Milligan and Richards are the beginning of a rejoinder to the Court’s decision in Clapper. But one might still ask how their arguments are, at bottom, any different from the chilling argument rejected by the Court in Clapper and Laird. Without further elaboration, they are not. What is needed is an explanation of why unregulated surveillance undermines the political system that standing doctrine ostensibly is meant to preserve.