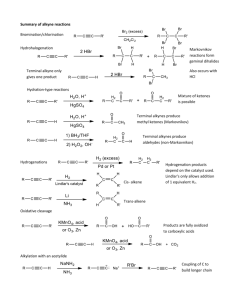
EE40206 Examination Solution 1998/9
advertisement

1) During design, information and resources can be protected in a given environment, and weaknesses can be compromised, more easy to manage During operation, resource matrix approach (RMA) has to be developed to manage the covert channels (explain RMA) [3 marks each total 6 marks] 2) System consists of a host that communicates with a collection of terminals in a manner that uses key managed encryption protocols to ensure secrecy of all information passed The host maintains a collection of session keys that dynamically generated for each communication session with a terminal and a collection of terminal keys that are fixed for the set of terminals Each terminal has its fixed terminal keys The host maintains a cryptographic facility that contains master keys to encrypt and decrypt terminal and session keys [2/7 marks] Each terminal maintains its own cryptographic facility Notation: Ek(cleartext) is cleartext encrypted using key K and Dk is ciphertext decrypted using key K [1/7 marks] The terminal communicate directly with the host and a new session key is generated for each communication session Since the host and each terminal contain the terminal key, it is used in private key protocol to distribute the session key. Both the host and terminal can encrypt and decrypt the terminal key using the master terminal key or the specific terminal key at each terminal. Each session is established. Each time a new session is established, the host updates its session key table with a new encrypted entry Emsk(new session key) where msk is the secret master key for session keys communication between host and terminal can thus follow a simple key managed protocol using the session key, where messages sent from the host to a terminal i would be of the form Eski(message) [where ski is the session key for i] and messages received from a terminal i would be deciphered by computing Dski(message) [2/7 marks] Step 6: recover message Dski(Eski(Mih)) Step 4: Dmsk(Emsk(ski)) or Dtki(Etki(ski)) Step 1: transmission of msk or Tki via secure means Host hold: msk, Tk’s and sk’s Terminal i Tki or msk generate Step 2: Session key Step 6: recover message Dski(Eski(Mhi)) Step 3: Emsk(ski) or ETki(ski) Eski(Mhi) Eski(Mih) Step 5: Message M Secure Terminal/Host Communications (Repeat steps 2 to 6 for new transmission) [2/7 marks] 3) Permutation: the positions of athe plaintext letters in the message are simple rearranged. E.g. THINK becomes HKTNI Substituion:n input bits representing a character are transposed into one of the other character in the set. E.g. 000 to 011 and 001 to 111 etc. Expansion:an n-bit character is expanded into a (n+k)-bit character in a defined format to increase the searching space of the characters. E.g. 000 to 10001 etc. [2 each total 6 marks] 4) I Xi 0 1 2 3 4 5 6 7 Ai Bi 8 11 8 3 2 1 0 1 0 1 -1 3 -4 11 Yi 0 1 0 1 -2 3 -8 END p= p=5 5 q=3 0 1 2 1 2 e= 3 3 or using the ed = 1 (mod(f(n)) approach [4 /6 marks] Let 7=7, 3 =3, C=12, 4 =4, encrypt each data individually, C(7)= C(3)= C(C)= C(4)= For checking only 13 12 3 4 Plaintext P^3 P^3/(p*q) Cipher 7 343 22 13 3 27 1 12 12 1728 115 3 4 64 4 4 0 0 0 0 Cipher P^11 P^11/(p*q) Plaintext 13 1792160394037 119477359602 7 12 743008370688 49533891379 3 3 177147 11809 12 4 4194304 279620 4 Any example above [2/6 marks]