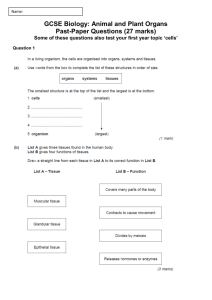
Information TechnologyGCSE/Key Stage 4
advertisement

GCSE Information Technology Page 1 GCSE Information Technology Contents Chapter 0 - Introduction 0.1 About this book 0.2 Applications Used 0.3 Questions/Answers 0.4 Optional Research 0.5 Bookmarks Chapter 1 - Introduction to Information Technology 1.1 Definitions for this Chapter 1.2 Information Technology - Defined 1.3 Digital vs. Analogue Chapter 2 - Information and Data 2.1 Definitions for this Chapter 2.2 Information and Data 2.3 Data Types 2.4 Character Sets 2.5 Coding Data 2.6 Processing Information Chapter 3 - Computers and Types of Processing 3.1 Definitions for this Chapter 3.2 What makes up a Computer? 3.3 Types of Computer 3.4 Types of Processing Chapter 4 - Capturing and Inputting Data 4.1 Definitions for this Chapter 4.2 Data Capture 4.3 Inputting Data Chapter 5 - User Interfaces 5.1 Definitions for this Chapter 5.2 User Interfaces Chapter 6 - Outputting Data 6.1 Definitions for this Chapter 6.2 What is an output device? 6.3 Monitors 6.4 Printers 6.5 Other Output Methods Chapter 7 - Storing Data 7.1 Definitions for this Chapter 7.2 Storage 7.3 How a disc works 7.4 Accessing Storage 7.5 Files 7.6 Security of files Chapter 8 - Applications Software 8.1 Definitions for this Chapter 8.2 Software, Programs and Applications Software 8.3 Types of Application Package 8.4 Deciding which package to buy Page 2 GCSE Information Technology Contents 8.5 Some typical packages 8.6 Communication between packages Chapter 9 -Word Processing 9.1 Definitions for this Chapter 9.2 Introduction to Word Processing 9.3 Margins 9.4 Indents 9.5 Tabs 9.6 Blocks of text Chapter 10 - Databases 10.1 Definitions for this Chapter 10.2 What is a database? 10.3 Setting up a database 10.4 Using a database Chapter 11 - Spreadsheets 11.1 Definitions for this Chapter 11.2 Models 11.3 Spreadsheets Chapter 12 - Graphics 12.1 Definitions for this Chapter 12.2 Graphics Chapter 13 - Communications and Networks 13.1 Definitions for this Chapter 13.1 Introduction to Communications and Networks 13.3 Types of Network Chapter 14 - Control Systems 14.1 Definitions for this Chapter 14.2 What is a Control System? 14.3 Communicating with the devices 14.4 What can the computer control? 14.5 Feedback 14.6 Turtles and LOGO Chapter 15 - Developing Systems 15.1 Definitions for this Chapter 15.2 The System Life Cycle Chapter 16 - Documentation 16.1 Definitions for this Chapter 16.2 Types of documentation 16.3 Flowcharts Chapter 17 - The impact of IT 17.1 Definitions for this Chapter 17.2 A brief History 17.3 The effect IT have had on our lives Chapter 18 - Your Coursework Project 18.1 Introduction 18.2 What shall I do for my coursework? 18.3 How do I do my coursework? Chapter 99 - Answers to Questions Page 3 GCSE Information Technology Chapter 0 - Introduction Chapter 0 - Introduction 0.1 About this book This book is for Information Technology GCSE Key Stage 4. It is known as a short course. This means, in order to get a GCSE certificate the students have to continue with their IT studies to convert the course into a GCSE for Information Systems. Alternatively, they can combine Information Technology with another subject to give a combined GCSE. This book covers the syllabuses for all examination boards. 0.2 Applications Used This book was written using Microsoft Office (Word 6, Excel 5 and Access 2). The screen shots are taken from these packages. However, the book does not assume the student is using any particular package. The author would like to thank Microsoft for permission to use the screen shots. 0.3 Questions/Answers Most sections have questions at the end. These check the students understanding of the material just presented. The teacher can obviously choose which questions to use and can incorporate their own. Suggested answers to the questions are given in Chapter 99. For obvious reasons, the students should not be given access to this chapter. 0.4 Optional Research At the end of each chapter there is normally an ‘optional research’ section. This material is not examinable but could be used as exercises for students who show a strong interest in IT. 0.5 Bookmarks In order to make this book as easy to use as possible ‘bookmarks’ have been placed at the start of each chapter. If you use Word to read this book you can use the Edit/Bookmark menu to display a dialogue box; like this: You can now select the Chapter you want to go to and Click on Go To. Page 4 GCSE Information Technology Chapter 1 - Introduction to Information Technology Chapter 1 - Introduction to Information Technology 1.1 Definitions for this Chapter Information Technology (IT) : Describes the equipment and software used to process information. It is not only used when talking about computers. Digital : Describes something which can be in a known numbers of states. Analogue : Describes something which is continuously variable - for example sound or the level of a river. 1.2 Information Technology - Defined The term Information Technology (IT) is used to describe the equipment we use to process information and the software we use to carry out those processes. A calculator is an example of IT. It is a piece of technology that processes numbers that we enter into it. A telephone is another example. It processes the sounds that we make so that they can be understood by somebody, perhaps, on the other side of the world. Of course, a computer is another (and perhaps the most common) example of IT. It is also probably the most versatile example of IT as it can be used as a Word Processor, a Database, a Spreadsheet; in fact a computers uses are also unlimited. There are generally considered to be five main areas of IT; these being: 1. Handling Information : This includes sorting data, searching for data and carrying out analysis on data. This is typically done by a database program but many other types of program also carry out these operations. 2. Communicating Data : Using IT it is possible to send data around the world by telephone lines, radio waves - even microwaves. Before this technology was available it could be weeks or even months, before you could get access to information on the other side of the world. 3. Measuring and Control : This area of IT allows a machine to interact with the outside world and act on the input it receives. For example, a car production line is able to sense when a car body is in a certain position and weld together the relevant parts of the car. 4. Presenting Information : IT is useless unless the output of the various processes is presented in a form we understand. Word Processors, Desk Top Publishers even the television - takes raw data and presents it in a format we can understand and find attractive. 5. Modelling the Real World : Using simulations we can see what happens if we do something without having to do it for real. The government, for example, may run a simulation to see what would happen if they were to raise interest rates. Spreadsheet applications are often used to build models of, say, a company’s accounts. Page 5 GCSE Information Technology Chapter 1 - Introduction to Information Technology Q.1.2 Questions Q.1.2.1 Give three examples of IT, that you use every day. Q.1.2.2 Looking at the five main areas of IT, above, give one example of each area that you use in everyday life 1.3 Digital vs. Analogue In IT you will often hear the term digital and occasionally the term analogue. But what do they mean? Digital : If something can be in one or more specific states it is said to be digital. For example, a light switch is either on or off - it cannot be in between. This could be described as a digital device. Another example are the coins in your pocket. They can only take certain values. A single coin cannot represent a value of, say, seven pence. Analogue : If something varies continuously it is said to be an analogue device. For example, a river is analogue as its level is constantly changing. Another example is a television signal. The picture is represented by a constantly varying signal which eventually arrives at your TV set. Q.1.3 Questions Q.1.3.1 Would you consider the following digital or analogue? i The music coming from a speaker ii The price of postage stamps iii Whether a bank account is in credit or debit (in the black or in the red)? iv The different combinations of colours a traffic light can have Q.1.3.2 Give an example of something which is digital and something which is analogue? Page 6 GCSE Information Technology Chapter 2 - Information and data Chapter 2 - Information and Data 2.1 Definitions for this Chapter Information : Facts and knowledge that has meaning. Data : Information that is held in a form that can be processed. Data Type : Describes how a piece of data can be used and stored. Data Processing Cycle : The sequence of events that is used to process information. 2.2 Information and Data Information and data are fundamental to IT. Everything we consider in this book is somehow related to Information and Data. But what is the difference between the two terms? As can be seen in the definitions (above), information has some sort of meaning whereas data is information in a form in which it can be processed. Here are some examples: Information A telephone directory. A company report. A class register showing who has attended each day. A letter produced on a word processor. Data The names which are in a telephone directory. A company report stored in a word processor document. A list of students in a class. Notice how the information has meaning. By comparison, the data does not have meaning; at least not until we do something to convert it (process it). For example, a company report stored on your computer does not have meaning. But if we apply a process to it (in the form of a Word Processor) we can print something that does have meaning. Sometimes it is not always easy to decide if something is information or data. A list of students in a class could be information if all you wanted to know was who was in the class. But if you wanted to know who has attended each day the data would need to be processed so that it is a class register. In some cases data and information is different depending on who is looking at it. If you cannot read French, a book written in that language is just data but it is information to somebody who understands the language as they can make sense of the words. Page 7 GCSE Information Technology Chapter 2 - Information and data Q.2.2 Questions Q.2.2.1 Give two examples of information? Q.2.2.2 Give two examples of data? Q.2.2.3 Whether something is information or data sometimes depends on who is looking at it. Give two examples where this could be the case and say who would regard it as information and who would regard it as data? 2.3 Data Types A data type describes how data is processed and stored. The number 3.67 is a numeric data type. Being numeric we can perform calculations on it. We could, for example, add 34.78 to it. The characters ‘computer’ is a string data type. It makes no sense to add 34.78 to the word computer. As well as dictating the operations that can be performed on the data, the data type also defines how the data is stored. Numeric values are normally stored in a special format that makes calculations easier for a computer to do. 2.3.1 Examples of Data Types These are some of the common data types. There are others and, sometimes, you are allowed to define your own. Character String Numeric Integer A single letter, punctuation character or number. For example ‘a’, ‘!’ and ‘3’. There are also special characters which cannot be printed or seen on the screen. If you are printing a report and the printer starts a new page a ‘Form Feed’ control character has been sent to the printer. Although you cannot see a ‘Form Feed’ on the screen it is still a character. There are also other characters which are simple graphics. Using these you can get special effects such as drawing a border around a screen. A series of characters. For example, “This is a string”. A string that contains both letters and numbers is sometimes referred to as an alphanumeric data type A number. For example 12.45, -678.98, +5.89234 A whole number. For example 12, 19862, 100861 Page 8 GCSE Information Technology Chapter 2 - Information and data Q.2.3 Questions Q.2.3.1 Look at the following data and say which data type best describes it i 12 ii a iii aa iv -34.98 v A telephone number vi Your age vii Your Christian Name 2.4 Character Sets A character set is a complete set of characters used for a specific purpose. The character set for a computer typically consists of 256 characters (called the ASCII (pronounced askey) character set). This contains all the characters that your computer uses. It includes all the numbers, letters and punctuation symbols. It also includes many other characters; some of which are not printable (for example a form feed character). Q.2.4 Questions Q.2.4.1 What characters do you think make up the character set of the English language? Q.2.4.2 What is the character set for all the non-vowel characters in the English alphabet. 2.5 Coding Data You already use codes in your everyday life without even realising it. A date such as 21/07/61 is a code for 21st July 1961. A time given as 21:15 is a code for a quarter past nine in the evening. Your bank account number is a code that represents your account within the bank. Computers also use codes to store data. Some of the reasons for this are as follows. It uses less space. An international company might use a two character code to represent a country rather than the full name of the country; say ‘UK’ instead of ‘United Kingdom’. It makes the data easier to handle. In the above example manipulating “UK” is easier (and faster) than having to manipulate “United Kingdom” It is more consistent. Users are less likely to make a mistake entering ‘UK’ rather than ‘Unitex Kingdom’ (see what I mean?) The computer is able to perform validation easier as there are only a certain number of codes. By contrast you might enter ‘United Kingdom’, ‘Britain’ or ‘England’ to represent the same country. Of course, there are problems with using codes. Probably the main one is the fact that the user has to be familiar with the codes being used or else keep looking them up. Page 9 GCSE Information Technology Chapter 2 - Information and data However this is not so much of a problem these days as the computer themselves can assist in the process and make the codes being used almost invisible to the users. Q.2.5 Questions Q.2.5.1 Give three examples of where you use codes in your daily life, almost without realising it. Q.2.5.2 If you were asked to introduce a coding scheme for the Premier Division Football teams how would you do it? As well as devising a coding scheme what else would you need to think about? 2.6 Processing Information Computers are all about processing information (normally called Information Processing). There is a typical sequence of events in processing information called the data processing cycle. The normal sequence of events is; 1. Data Collection is the collection of data from whichever source you are using. It might be a survey conducted on the High Street, figures from company accounts or the names of people who will be attending school next term. 2. Data Input is inputting the data into the computer. How and where you input the data will depend on the type of data, the equipment you have available and the type of software you are using. As the data is input it is checked (validated) and stored on the computer in a suitable format for later processing. The concept of a data type (covered above) is important in the input phase of the data processing cycle. 3. Processing is converting the data from one form to another. Maybe, a set of company accounts for a High Street retailer needs to be sorted into some sort of order. Maybe you want to use the data you have inputted to produce summary information by adding up all the figures for each store to give one total. 4. Output is concerned with producing output from the data in a form acceptable to the person processing the data. Maybe the output will be a set of company accounts ready to submit to the tax office. Maybe, for a supermarket, it will be bar code labels that they will put on the shelves, together with a price for each item. This cycle continues so that after you have produced the output you will go back to the beginning and collect more input. For example, a supermarket will receive deliveries and sell goods. This data has to be collected and input to the computer on a daily basis. Q.2.6 Questions Q.2.6.1 Consider a class register. Identify what happens to it during the various phases of the data processing life cycle. Page 10 GCSE Information Technology Chapter 2 - Information and data R.2 Optional Further Research R.2.1 The ASCII character set is the most commonly used character set. What does ASCII stand for? EBCIDIC is another common character set. What does EBCIDIC stand for? Get a copy of the ASCII character set and find out how many control characters there are. R.2.2 What code is used to uniquely identify a book? What does each part of the code represent? R.2.3 A light switch could be described as a binary device. What is meant by binary and why is it important with regards to computers? Page 11 GCSE Information Technology Chapter 3 - Computers and Types of Processing Chapter 3 - Computers and Types of Processing 3.1 Definitions for this Chapter Computer : A device that processes data that has had input put into it. The processing is done via a series of fixed instructions, usually called a program. Central Processing Unit : The main part of the computer which controls all the other parts of the computer. RAM : Random Access Memory. Temporary storage in a computer that holds programs and data. ROM : Read Only Memory. Similar to RAM but you cannot write to the memory. Normally stores programs which never change. Discs : Used for permanent storage of data. There are three types of disc; Hard Discs, Floppy Discs and CD-ROM’s. Hardware : The physical pieces of equipment that make up a computer. Software : The instructions that tell the computer what to do. Personal Computer (PC) : A computer used by one person at a time. Mainframe Computer : Large computers that can look after many jobs and users at the same time. Minicomputer : A computer that is more powerful than a PC but not as powerful as a mainframe. Usually runs many jobs and has many people attached to it at the same time. Stand-Alone system : A computer used by one person at a time. Multi-User system : A computer used by many people at the same time. Real Time Processing : A computer that reacts to input as soon as it receives it. Interactive Processing : You communicate with the computer and it responds; like a two way conversation. 3.2 What makes up a Computer? Before we start to look at the things that computers can do it is useful to know what a computer is and identify the various parts that make up a computer. What we are about to discuss is a typical computer. Computers are built using Hardware and Software. The best definition we have ever heard for Hardware is “If you kick it, it clangs.” From this you might be able to work out that hardware are all the physical bits and pieces like the screen, the keyboard, the mouse and the computer case. Software is what makes it all work. Software are the instructions to the computer that tell it what to do. Software is often referred to as programs or applications. Every computer has a Central Processing Unit (CPU). This is the main part of the computer and it controls everything the computer does; including looking after access to devices (such as printers) which are not part of the CPU. Memory is used by the computer to store data. There are three main types of memory Page 12 GCSE Information Technology Chapter 3 - Computers and Types of Processing RAM (Random Access Memory - also called Read Write Memory). This memory is used as a temporary storage area. It is temporary as the contents of RAM is lost when the computer is switched off. RAM is used to hold programs that the computer is currently processing and also to hold data which the program is using. ROM (Read Only Memory). This type of memory is like RAM except it can only be read; unlike RAM which can be read and written to. ROM is put into the computer by the manufacturer and it typically contains programs that are used by the system itself. For example, the program that recognises when you press a key on the keyboard could be in ROM. Backing Store, which is normally in the form of a disc or a magnetic tape. There are three types of disc; Hard disc, Floppy Disc and CD-ROM. Hard discs are situated inside the main case of the computer and are used for day to day storage. Floppy discs can be put into the computer and then have data copied onto it; either for security purposes or so the data can be transferred to another computer. CD-ROM’s are read only and are usually used to distribute software. Magnetic tape works in the same way as a cassette recorder except that it records computer data rather than music or sounds. All discs and tapes are persistent media in that they retain the information on them even if the power is switched off. Peripherals are anything that is outside the main case. For example a screen or a printer. Q.3.2 Questions Q.3.2.1 If some data is in RAM why should you regularly copy the data to a disc drive? Q.3.2.2 What is one advantage of distributing software (programs) on CD-ROM as opposed to using floppy discs? Q.3.2.3 From the following list decide if each item is hardware or software? i A Floppy Disc ii A Word Processing Program iii A Computer Game iv A Joystick 3.3 Types of Computer There are three main types of computer 3.3.1 Personal Computers As the name suggests a Personal Computer (or PC) is for personal use. It is normally used by one person (a single user system). In a school you will almost certainly be using PC’s. The majority of people in large companies have PC’s on their desks. Page 13 GCSE Information Technology Chapter 3 - Computers and Types of Processing 3.3.2 Mainframe Computers These are large computers that cost millions of pounds. They are used by large companies and government departments such as the tax office. Mainframes have large memories and storage capacities and often run 24 hours a day. Mainframes are capable of looking after many jobs at the same time and have many people using them at the same time. Many PC’s in companies are connected to the mainframe. Mainframes often hold all the information about the business and its customers which is accessed by PC’s which are on the employees’ desks. A mainframe is often in a secure area and has to be in an air-conditioned room due to the amount of heat it generates. Mainframe computers are known as multi-user systems as many people can use the computer at the same time. 3.3.3 Minicomputers Minicomputers come somewhere in between PC’s and mainframes. They are less powerful than mainframes but are used when a PC is not powerful enough for the required job. Like mainframes, minicomputers often have PC’s attached to them so that the data can be accessed from people’s desks. Minicomputers are usually multi-user systems. Q.3.3 Questions Q.3.3.1 What do you think is a disadvantage of a multi-user system? Q.3.3.2 What do you think is a disadvantage of a single-user system? 3.4 Types of Processing Computers can do various types of processing. In this section we are going to consider some of them. 3.4.1 Real Time Processing If a computer is reacting to input as soon as it arrives and then producing some form of output as soon as it has processed the data then it is known as a real time system; that is, it’s processing the data in real time. A bank cash machine is operating in real time. You are asking for money, your account is checked and money is given to you providing you have sufficient funds. An aeroplane is an even better example. If it is flying under automatic pilot it is certainly operating in real time. If it gets too close to the ground it must do something quickly. It is no good waiting ten minutes, finishing another job before it gets to the input that says “the ground is fast approaching.” Because real time processing requires the computer to always be able to process any input, real time processing is normally done on a dedicated computer so that is does not get side-tracked by other, less important, tasks. Page 14 GCSE Information Technology Chapter 3 - Computers and Types of Processing 3.4.1 Interactive Processing If you sit at a computer and type an instruction and then receive a reply you are using the computer in an interactive mode. If the computer is also being used by other people, for example a mainframe computer at a bank, you may have to wait for the computer to get around to processing your input and replying to you. But you will receive a reply eventually. If you are using a stand-alone computer (where you are the only person using it) the reply could be almost immediate, unless you have asked the computer to carry out a task that takes it a long time. Most things you will be doing on a PC are examples of interactive processing. For example, typing a letter using a Word Processor is an interactive task. Q.3.4 Questions Q.3.4.1 Do you think the following are interactive or real time processes, or both; i A flight simulator ii Using a calculator iii Booking a holiday at a Travel Agents iv A Crossword Puzzle on a computer Q.3.4.2 When you buy a train ticket you can reserve a seat. Do you think the train operator could use a single user system to provide this service? If not, why not? R.3 Optional Further Research R.3.1 There may be somebody at your school who will open up a computer case and let you see inside. You may be able to identify the RAM, ROM and CPU. Do not open the case yourself. It is dangerous and you may cause damage to yourself and to the computer. R.3.2 By using utilities on your computer you will be able to find out how much RAM and disc space are installed on your computer. You can also find out how much data can be stored on a CD-ROM. R.3.3 Find out the name of a large company in your area that uses a large mainframe computer. See if a visit can be arranged. Find out how the memory size and disc capacity of their mainframe compares with a PC at your school. Page 15 GCSE Information Technology Chapter 4 - Capturing and Inputting Data Chapter 4 - Capturing and Inputting Data 4.1 Definitions for this Chapter Data Capture : Obtaining data that is then fed into a computer. Bar Code : A series of black and white stripes which represent numbers and letters. Magnetic Stripe : A strip of magnetically coated material. The strip contains information which can be read by a reader. Optical Mark Reading (OMR) : A system that read marks made on paper (typically crosses or filling in boxes). The position of the marks represent the data. Optical Character Recognition (OCR) : Converting marks on paper into characters, for example, hand-writing. Magnetic Ink Character Recognition (MICR) : Characters printed in a special way with magnetic ink which can then be read by a special reader. Digitising : Convert an image or sound from analogue to digital. The digital representation can more easily be stored on computer. Scanning : Digitising an image (e.g. photograph, logo etc.) so that it can be stored on computer. Scanner : The equipment used for scanning. 4.2 Data Capture Data is being captured all the time and much of it ends up on a computer. These are just some of the ways data is captured. 4.2.1 Data Capture Forms If you open a bank account you have to supply your name and address and various other details. The form you fill in is a data capture form. It is capturing data about yourself. If you buy a new radio you normally have to fill in a guarantee card in case something goes wrong with it. This is another example of a data capture form. The benefit of using a form is that the form is produced by the company so that data is presented in a standardised form. An enhancement to the basic data capture form is a form that is produced specifically for you. If you belong to a book club your order form is pre-printed with your name and address and your account number. When you return your order they know who you are from the information already present on the form. 4.2.2 Questionnaires You will often find examples of questionnaires in the High Street when you are stopped by somebody and asked to answer a few questions. Designing a good questionnaire is very difficult. Some of the points you need to bear in mind are (and there are many others); What type of questions should you ask; multi-choice questions, questions where the person being interviewed can give an opinion, questions which can have more than one answer? Page 16 GCSE Information Technology Chapter 4 - Capturing and Inputting Data Who is the questionnaire aimed at? Are you likely to get bias results if you only interview people aged between 18 and 30? Are the questions clear and unambiguous? Will the questions be asked personally or will they be sent through the post? Q.4.2 Questions Q.4.2.1 Collect five examples of forms that are designed to capture data. Say what you think are the good and bad points about each form. Design your own form to collect data about your classmates. How does your form compare to others in your class? Q.4.2.2 Give three examples of data capture forms where the form has already been pre-printed with details about yourself. Q.4.2.3 Design a simple questionnaire and try it out on people at school (both students and teachers). What problems did you encounter? What could you have done to reduce these problems? 4.3 Inputting Data Data Capture is closely related to Data Input. Some of the methods of inputting data are explained below. 4.3.1 Using the keyboard Using the keyboard is probably the most common method of inputting data into a computer. If you write a letter on a Word Processor you will almost certainly use this method. 4.3.2 Mouse A mouse is almost as common as a keyboard due to the rise in popularity of Graphical User Interfaces. You communicate with the computer by moving a pointer around the screen and then clicking one of the mouse buttons to carry out some task. Mice, typically, have two or three buttons. 4.3.3 Bar Codes You probably have seen bar codes being used in supermarkets (you can also see them on books and magazines). Most goods you buy are marked with a bar code and these are scanned at the till. The bar code identifies the goods and the computer returns the price you have to pay. Note that the price is not part of the bar code otherwise every shop would have to charge the same price. The numbers that are represented by the bar code are printed underneath the code. This is so the numbers can be input manually if the bar code cannot be read. Page 17 GCSE Information Technology Chapter 4 - Capturing and Inputting Data 4.3.4 Magnetic Strips Magnetic strips are most commonly found on bank cards. If you look at the back of a bank card you can see the strip. It holds information about the owner which is read when it is inserted into the cash point (or swiped through a machine). Magnetic strips are also used in other places and you are asked to consider these as part of the questions. 4.3.5 OMR, OCR and MICR OMR (Optical Mark Reading), OCR (Optical Character Reading) and MICR (Magnetic Ink Character Recognition) are all examples where the data is read from a form by the computer or by a document reader which is specially designed to do the job. OMR reads marks made on a form and ‘understands’ the data because the mark was made in a specific place on the form. OMR is being used when you are asked to complete a multiple choice examination. You may have thought that an examiner had to mark each form (if you had thought about it at all). In fact the papers are probably being marked automatically using OMR to check if you have made the correct choices. OCR is used to read hand-written characters and to try to understand what they represent. It is quite a complicated thing to do. To see why this is so, get ten of your friends to write down the same sentence and look at the difference in the writing. It is difficult for a computer to interpret all of these reliably. It is for this reason that you are often asked to use block capitals or are given spaces in which to write each character. If you look at a cheque you will see a series of characters printed at the bottom. Not only are they a strange shape but they are also magnetised. Being magnetic they can be read by special equipment. This is an example of MICR. The reason MICR is used is to reduce fraud. If normal characters, with normal ink, were used it would mean that a fraudulent cheque was relatively easy to produce. Not a good idea for a bank. 4.3.6 Touching the screen Some screens allow you to point at them and the action taken by the computer depends on where you touch the screen. To assist you to touch the right part of the screen, pictures are often used to guide you to the correct area. You may have seen this type of data input at Tourist Information Points or Railway Stations. An adaptation of this method is touching the screen with a pen or ‘stylus’. Page 18 GCSE Information Technology Chapter 4 - Capturing and Inputting Data 4.3.7 Scanning If you wish to store a picture (such as a photograph or a logo) on a computer the most common method of inputting it is to scan it. This is done with a scanner that converts the image into a form that can be stored on the computer. That is it digitises it. There are two main types of scanners. Hand-held scanners are moved across the picture. They are cheap and portable. With a flat-bed scanner the image is laid on the scanner itself. These are more expensive but allow better quality images to be captured. Scanners are also used to read characters that are then processed by OCR software. 4.3.8 Human Speech Human Speech is input to a computer via a microphone. The sound, like images, are converted to a form which is suitable for storage on a computer. 4.3.9 Sensors It is possible to have a variety of sensors connected to a computer. For example, a thermometer could be connected which tells the computer the temperature. The computer can use this information to control something like a central heating system. Q.4.3 Questions Q.4.3.1 Next time you are in your local town see how many different ways you can find that retailers capture data. Q.4.3.2 Apart from cheque and cash cards where else would you find a magnetic strip? Q.4.3.3 As long as you are aged sixteen or over you can go into thousands of shops, pay one pound and see OMR in action. What would you be doing? Q.4.3.4 Give one advantage and disadvantage of OMR, OCR and MICR Q.4.3.5 Can you think of another type of input device that is commonly used to play games? R.4 Optional Further Research R.4.1 Try to arrange a visit to a local company. Ask them how many different ways they collect data from their customers. R.4.2 A computer keyboard is often called a “QWERTY” keyboard. Why is this? And why is a keyboard laid out this way? R.4.3 How many keys on a computer keyboard actually display a character on the screen when it is pressed? What are the other keys used for? R.4.4 All books have an ISBN number which is represented as a barcode somewhere on the book (normally on the back cover). What do the various parts of the ISBN number represent? Page 19 GCSE Information Technology Chapter 5 - User Interface Chapter 5 - User Interfaces 5.1 Definitions for this Chapter User Interface : How a person communicates with a computer Command Line Interface : A type of interface where the user types commands (via a keyboard) to the computer. Command Line Prompt : The characters which are displayed inviting you to type something. Graphical User Interface : A type of interface where a graphical interface is used. The interface normally consists of menus, icons (pictures) and windows. A mouse, as well as the keyboard, is used to enter commands. 5.2 User Interfaces The User Interface is the way in which you communicate with a computer and the way the computer communicates back to you. There are two main types of User Interface; Command Line Interfaces and Graphical User Interfaces. 5.2.1 Command Line Interfaces An example of a Command Line Interface is shown below. Explanations are provided for the most important aspects of this interface. This is a command that has been typed in. This is the output of the command This is the prompt, waiting for the next command to be typed This particular screen is showing the DIR command being used on an IBM compatible PC. The DIR command gives a listing of files which match the file specification. In this case it is any files with an extension of BAT. Page 20 GCSE Information Technology Chapter 5 - User Interface 5.2.2 Graphical User Interface Graphical User Interfaces (GUI’s - pronounced Gooey) present the user with a graphical representation that the user manipulates using the mouse and keyboard. There are four main parts to a GUI; these being; Windows. This is where information is displayed. Windows can be made bigger and smaller and moved around the screen. Icons. These are little pictures which the user can click on (with the mouse pointer) to perform certain actions. For example, you might click on a printer icon to print a document. Menus. Windows may optionally have menus. They are normally situated across the top of the window and they drop down when you click on them. (Note that Acorn machines, which you may have used, have pop up menus which appear when you click another mouse button). Pointer. This is an arrow on the screen which represents the mouse. When you move the mouse the pointer moves. To perform an action you move the pointer to the relevant part of the screen and then click the mouse. Here is an example of a Graphical User Interface. In fact it was the GUI being used whilst writing this book Page 21 GCSE Information Technology Chapter 5 - User Interface Icon Menu Window Pointer Q.5.2 Questions Q.5.2.1 What do you consider the main advantages of a GUI over a Command Line Interface? Q.5.2.2 If you have access to an IBM compatible PC go to the Command Line Interface (the DOS Prompt) and try these commands. What do they do? i DIR ii CLS iii COPY C:\AUTOEXEC.BAT MYFILE.BAT iv PROMPT $T (Note : You may not be allowed access to the DOS prompt. In which case you will be unable to do this question) Q.5.2.3 GUI’s are sometimes called WIMP environments. Why do you think this is? Page 22 GCSE Information Technology Chapter 5 - User Interface R.5 Optional Further Research R.5.1 See if you can arrange a visit to a local company which uses a variety of computers. Identify how many different types of User Interface they use and classify them into Command Line Interface and GUI’s Page 23 GCSE Information Technology Chapter 6 - Outputting Data Chapter 6 - Outputting Data 6.1 Definitions for this Chapter Output Device : A device that receives an electrical signal and converts it to data or information. Pixel (Picture Element) : The smallest unit of information on a monitor. Resolution : The amount of detail (number of pixels) on a monitor. Screen Mode : The mixture of colours, resolution and text/graphics allowed on a monitor. Dot matrix printers : Printers which make up the image on the page by pushing pins against a ribbon to make a series of dots. Ink jet printers : Printers which squirt dots of ink at paper to make up the dots. Laser Printers : Printers which use a laser to produce the image. Impact/Non-Impact printers : Impact printers make contact with the paper. Non Impact printers do not. Character Printer : Printers which print a character at a time. Line Printer : Printers which print a complete line at a time. Page Printer : Printers which produce and print a complete page at a time. Draft Quality : A mode of printing which produces lower quality output but at a faster speed. NLQ (Near Letter Quality) : A mode of printing which produces high quality output but at a slower speed. Plotters : An output device which is normally used to produce line drawings such as plans for a house. Microfiche : Reduced images of pages held on plastic. It could be argued that computers are useless unless we are able to see the results of what they produce. After all why bother collecting data, entering it into the computer and performing various processes on that it if we cannot see the end result. The first part of this chapter (6.1) will consider what an output device is and suggest some devices in everyday use. The remainder of the chapter will look at output devices that are typically connected to computers. 6.2 What is an output device? Calculators, telephones, faxes, supermarket tills (for receipts), hi-fi speakers and train ticket machines are all output devices. In the context of Information Technology an output device is something which receives an electrical signal and produces data or information. All of the above produce output which we regard as information. Output which does not have meaning is said to be data (see chapter 2). A computer controlling a robot would output data. The data would be fed to the robot which it would interpret as an instruction to do something. Page 24 GCSE Information Technology Chapter 6 - Outputting Data Q.6.2 Questions Q.6.2.1 Give examples of two output devices - one which produces information and one which produces data. Do not use examples given in the text and do not use computer output devices. 6.3 Monitors Monitors are the most often used computer output devices. In fact, a computer without a monitor is very unusual (although possible). 6.3.1 Pixel The picture on a monitor is made up of pixels (which is short for picture elements). A pixel is the smallest element on a monitor. It is just like a newspaper photograph which is made up of dots. The dot is the smallest element in the picture. 6.3.2 Resolution The amount of detail that can be displayed on monitor is called its resolution. This is normally measured as the number of pixels it can display. A typical number is 640 pixels by 480 pixels. Some computers allow you to change the resolution. If you use high resolution you have greater detail but it takes more memory to store the image. A lower resolution results in loss of detail but you do not use as much memory. 6.3.3 Screen Modes The number of colours you want to display affects how much memory the computer needs to store the image. For example, it takes more memory to allow for 256 colours as opposed to sixteen colours. You can also decide if you only want to display text, graphics or both. Deciding on the number of colours and whether you want graphics, or just text, allows you to have various screen modes. For example one screen mode might allow sixteen colours, in medium resolution with a graphics display. Different screen modes will allow different mixes of colours, resolution and text/graphics. Q.6.3 Questions Q.6.3.1 Teletext is an example of a screen mode. Would you say that a teletext display needs a high, medium or low resolution monitor? Explain your answer. 6.4 Printers If monitors are the most common output device then printers come a close second. Printers can be classified into three types; dot matrix, inkjet and laser printers. Page 25 GCSE Information Technology Chapter 6 - Outputting Data 6.4.1 Dot Matrix Printers Dot matrix printers work by pushing small pins against a ribbon which, in turn, makes contact with the paper. The pins are arranged in a column. Older printers have nine pins to a column. More modern printers have 24 pins to a column. As the print head (the print head holds the pins) moves across the page the correct character can be printed by firing the pins in the correct sequence. Good quality graphics can be printed (especially with 24 pins printers), although dot matrix printers tend to be slow and noisy. 6.4.2 Ink Jet Printers Dot matrix printers are called impact printers as the print head actually makes contact with the paper (albeit through the ribbon). Ink jet printers are non-impact printers. Instead of making contact with the paper they spray fine jets of ink at the paper. The dots they produce make up the required characters. Instead of having a ribbon, an ink jet printer has a bottle of ink. By putting in a different colour ink bottle you can easily get colour. Some ink jet printers have space for more than one bottle of ink so more than one colour can be printed at the same time. 6.4.3 Laser Printers Laser printers, as their names suggests, work via a laser. Ink (or toner as it is more correctly called) sticks to a light sensitive drum where a laser has touched it. The toner is then transferred to the paper. Laser printers can produce high resolution images. Typically they produce 90,000 dots in a square inch (300x300). This is known as 300 dpi (dots per inch). 600 dpi laser printers are not uncommon these days. Q.6.4 Questions Q.6.4.1 Imagine you are a 24 pin dot matrix printer. Using graph paper show how you would print an “m”, an “a” and an “!”. Q.6.4.2 A printer can either be considered a character printer (where one character is printed at a time), a line printer (where a complete line is printed at a time) or a page printer (where a whole page is printed at a time). Classify a dot matrix printer, an ink jet printer and a laser printer into each of these categories. Q.6.4.3 Many printers have two modes of operation; draft quality and letter quality (sometimes called Near Letter Quality or NLQ). After reading the definitions at the beginning of this chapter how do you think the two modes might be implemented on a dot matrix printer and a laser printer? 6.5 Other Output Methods 6.5.1 Plotters Plotters are most often used for applications which require some form of line drawing, for example; maps, diagrams, plans etc. They usually have a pen which moves over a fixed piece of paper. Different colours are produced by using different colour pens. Page 26 GCSE Information Technology Chapter 6 - Outputting Data 6.5.2 Microfiche Microfiche stores images of paper on a plastic film. The images are held in a much reduced form and you can easily fit thirty pages on one sheet of microfiche which is about fifteen centimetres squared. You might be able to see a sample of microfiche in a book shop where they sometimes hold all the books in print on this medium in order to answer customer queries about books in print. A special reader is needed to look at pages stored on Microfiche. R.6 Optional Further Research R.6.1 There are various types of monitor (often called CGA, EGA, VGA, SVGA etc.). Find out the characteristics of each one with regards its resolution, the number of colours it can be display and the modes in which it can operate. Page 27 GCSE Information Technology Chapter 7 - Storing Data Chapter 7 - Storing Data 7.1 Definitions for this Chapter Main Store : Any Storage that is directly accessible by the CPU; normally RAM and ROM. Backing Store : Any storage that is external to the CPU (typically discs). Read : The process of reading data from backing store and making it available to the CPU. Write : The process of writing data from the CPU to backing store. Access Time : The time taken to read a piece of data requested by the CPU and making it available for processing. Direct Access : The ability to access a piece of data directly without having to read preceding data. Sequential Access : Accessing data in a serial manner. If data is at the end of a file you must read all the other data first. Magnetic Tape : A sequential access backing store device that is normally used to take security copies of data. File : Data or programs that are held on backing store, such as a disc. A file is given a unique name. Directory : A method of grouping like files together. When you place a file on a disc you specify which directory it is to be stored in. Security : Taking a copy of important files so that you can use it should something happen to the original. In Chapter 3 we discussed RAM, ROM and Discs. It might be worth reviewing this chapter before starting this chapter. 7.2 Storage In chapter 3 we briefly looked at some types of storage. In this chapter we will take a closer look at storage. 7.2.1 Main Store The main store of a computer is also known as main memory. It is the storage that is directly available to the CPU. In a typical computer the main store is in the form of RAM and ROM. 7.2.2 Backing Store Backing store is any type of storage that is not directly available to the CPU. For the processor to act upon any data it must be in main store. Therefore, if the CPU needs some data that is on backing store it must first be loaded into main store. The time taken to do this is known as the access time. You should be able to appreciate that the computer will work faster if the data is already in main store as it does not have to be retrieved from backing store. In addition the main store is faster than backing store. Page 28 GCSE Information Technology Chapter 7 - Storing Data The problem is that main store is more expensive than backing store. Therefore there is time/cost trade-off when designing or buying a computer. In chapter 3 we have already talked about three types of backing store (Hard Disc, Floppy Disc and CD-ROM). If you have not done so already try to have a look at each of these types of discs. I am sure you have all seen a CD-ROM. Many people have them at home as part of their hi-fi system. The CD’s used on computers are exactly the same. In fact you can play your music CD’s on a computer. Floppy discs are common place these days and there are probably hundreds within your school. Can you see where the data is stored? A hard disc is more difficult to see. You may have to ask somebody to take the lid off a computer (do not do it yourself - it can be dangerous). To be honest, they are not much to look at; just a metal case with a few wires sticking out. A further type of backing store is magnetic tape. This is similar to a tape recorder but it is connected to the computer and records data rather than music or speech. Magnetic tape is normally used to take security copies of data which is then held away from the computer in case there is a disaster. If your school has a large number of computers there is a high probability that the data is regularly backed up onto a magnetic tape. The tape should then be stored away from the computers or placed in a fire proof safe. This means that if there is a problem with the computer the data is secure and can be re-loaded when the problem is fixed. Q.7.2 Questions Q.7.2.1 How many characters can you store on a 3.5” High Density Floppy Disc? How does this differ from a 3.5” Double Density disc? (Note : this question requires research by the student). Q 7.2.2 Using your knowledge of storage devices what do you think is the best medium for the following types of data; i. A large application distributed to a great many people. ii. An Operating System. iii. A weekly security copy. iv. A copy of a file that you need to take home. v. A letter that you are writing to your friend. 7.3 How a disc works It’s okay saying “data is stored on a disc” but how does a disc work? Inside the protective covering of a floppy disc there is a piece of plastic that can be magnetised. A read/write head moves over the surface of the disc and either reads the magnetic fields or produces a magnetic field which writes data to the disc. Of course there must be some structure to the data so that the computer knows where to find a certain piece of information. Page 29 GCSE Information Technology Chapter 7 - Storing Data This diagram helps explain how a disc is structured. Data is stored on concentric rings called tracks The Disc is a piece of plastic which can be magnetised) Tracks are divided into sectors which actually store the data You can see that a disc is divided into concentric rings called tracks. Each track is further divided into sectors. Each sector can typically hold 512 characters. If the CPU needs data from a disc it can be accessed be specifying the track and the sector where the data has been placed. Similarly, data is written to a disc by specifying the sector and track number where the data is to be written to. 7.4 Accessing Storage There are two main ways you can access the data held on a storage device. 7.4.1 Direct Access A direct access storage device allows immediate access to any piece of the data without having to read all the data which comes before it. Discs and main store are both examples of direct access devices. 7.4.2 Serial Access With a serial access device you have to read all the data until you find the data you require. Magnetic tape is an example of such a device. With a magnetic tape you have to start at the beginning of the tape and read down the tape until you come to the data you require. There is no way to ‘jump’ (directly access) any one piece of data on the tape. In some cases data held on a disc must be accessed in a serial (sometimes called sequential) manner. This is because there is no information stored about the file which enables the CPU to work out where a particular piece of data has been placed on the disc; that is, its track and sector number. Q.7.4 Questions Q.7.4.1 Would you consider a CD-ROM a direct access or a serial device? Q.7.4.2 Give one advantage of a direct access device and one disadvantage. Q.7.4.3 Give an example where direct access would be more suitable over serial access. Page 30 GCSE Information Technology Chapter 7 - Storing Data 7.5 Files 7.5.1 What is a file? Up until now we have been talking about storing data on discs and tapes. We have also looked at how data is actually stored on a disc. But there is one more thing we need to consider: the concept of a file. If we first consider a non-computer system it may be easier to explain what a file is. If you take a look at your school work you will find it is partitioned into various subjects such as English, French and Maths. For each of these subjects you probably have a book that you use for your notes, following examples and carrying out exercises set by the teacher. Each of these books could be considered a file. That is it holds information (and data) about one particular thing. A computer is no different. If you write a letter you save it in a file. That is you give it a name and it is stored on a disc using that filename so that it can be identified later. The program that you used to create the letter (the Word Processor) is held in a another file. So it continues, with files being created for all the different types of information and data you need to store. Each file is given a unique name so that it can be identified later. 7.5.2 Directories On a typical computer there will be hundreds or (more likely) thousands of files. Although each one has a unique name it can still be difficult to find one particular file when you need it. Directories help in organise our data. It groups together files that have a common theme; for example all our Word Processing files or all our programs. The way you group your files together is largely a matter of personal preference, although when you install certain programs they will automatically set up their own directories. The screen shot below shows a number of directories. Note that there are various ways of displaying directories on a computer. This just demonstrates one method. Page 31 GCSE Information Technology Chapter 7 - Storing Data The top-level (or root directory) is the one labelled ‘C:\’. This has a number of subdirectories beneath it including ‘accounts’, ‘acroread’ and ‘agenda’. In addition the ‘accounts’ directory has further sub-directories; these being ‘gk’, ‘hk’ and ‘house’. Each of these directories can contain files within them. The screen shot above shows that the ‘acroread’ directory has been selected. The right hand side of the screen shows the files that are in this directory. Also note that you can have a file with the same name as long as it is in a different directory. This is because the directory name forms part of the unique name which identifies the file. 7.5.3 Structure of a file Every file that you create has some sort of structure to it. This is obvious when you think about it. A Word Processor file, for example, has to have a certain structure so that it knows where to find information about your document such as where a new paragraph starts and where you want a new page to begin. This is known as the internal structure of the file. As a user of the Word Processor you do not need to know anything about this internal structure. That is the job of the program you are using. But there is also another structure to a file that is particularly apparent in a program such as a database. This is the logical structure of the file. This means it is the structure that you see when you use the program. The way it is stored - its internal structure - might (and probably is) completely different. We will look at the logical structure of a file when we consider databases in chapter 10. Page 32 GCSE Information Technology Chapter 7 - Storing Data Q.7.5 Questions Q.7.5.1 The directory structure shown in 7.5.2 can be represented as a tree structure. Draw a tree that represents this structure. 7.6 Security of files 7.6.1 Why do we need to secure files? If we are holding data on computer we need to take certain steps in order to ensure that the data is secure. Some of the reasons why we need to do this are outlined below. The hard disc holding our data might become corrupted. For example, the disc might become damaged so that data cannot be read from it. You might accidentally damage a disc. For example, you might spill a cup of coffee onto a floppy disc or delete a file that you actually need. The computer might suffer a disaster such as fire or flood. Somebody might destroy the data deliberately. This could be done by physically damaging the data or by planting a software version of such vandalism, often called a virus. Alternatively the computer might be accessed by somebody who is unauthorised to do so. These people are known as hackers. A file might be updated incorrectly so that you need to have a previous version available in order to apply the correct processing to it. 7.6.2 Securing Files In order to protect ourselves against the dangers outlined above it is important to take copies of files on a regular basis. This means we have two copies so that if something is wrong with the original copy we have another copy we can use. It is also important to keep the security copy of the file away from the computer which holding the original file. There are many ways to copy files. Users who have a lot of data to secure will probably copy all the data to magnetic tape on a regular basis. Users which have only a small amount of data will often use floppy discs to hold their security copies. There are many programs available that will do your security for you. Some will even do the security at a certain time each day so that you do not forget. In addition, some programs allow you to compress the data as it is secured. This means that the security copy occupies less space than the original file. If you need to use the security copy you will need to expand the data before it is used. Q.7.6 Questions Q.7.6.1 Why is it important for a security copy of a file to be stored away from the computer which has the original file on? Q.7.6.2 Can you think of a disadvantage of compressing data as you take the security copy? Page 33 GCSE Information Technology Chapter 7 - Storing Data R.7 Optional Further Research R.7.1 There are various types of floppy disc. Find out about the different types and how much data each can hold. Note that floppy discs have been available in at least two other sizes other than 3.5”. R.7.2 If your school uses a magnetic tape to backup data find out how frequently the back ups are taken, where they are stored and what, if any, tests have ever been done to ensure the data can be restored if necessary. R.7.3 If you have access to a CD-ROM drive find out how much data can be stored on a CD-ROM. Work out how many floppy discs you would need to store the same information. Also work out if the data on the CD-ROM would fit onto the hard disc installed in the computer. R.7.4 When implementing a backup system you can use a method sometimes known as archiving. Under this system you only secure files which have been created or changed since the last security was taken. Investigate how such a system would work. Page 34 GCSE Information Technology Chapter 8 - Applications Software Chapter 8 - Applications Software 8.1 Definitions for this Chapter Program : Instructions to the computer that tell it what to do and in what order. Programs are written by programmers in a computer language such as BASIC. Software : The term used to describe all types of programs including the operating system, applications software and programs written by the user themselves. Applications Software : Software designed for a specific task, such as Word Processing, which normally has a full set of documentation. Applications Software is sometimes called a package. Evaluation : Looking at software to see if it is suitable for the planned job. Word Processing : A package that allows you to enter, edit and print text and, optionally, a great many other things. Database : An application that allows you to store and retrieve information. Spreadsheet : An application that allows data to be stored in a table format and have calculations performed on that data. Graphics : An application that allows you to produce graphics such as bar charts, pie charts etc. Desk Top Publishing : An application that produces documents suitable for publication. Export/Import Data : Allows one application to produce data suitable for another application (export). An application that reads such data ‘imports’ it. Cut/Copy/Paste : Remove data from an application (Cut) or make a copy of it. The data can then be pasted into another, or the same, application. 8.2 Software, Programs and Applications Software 8.2.1 Programs So far in this book we have been referring to software and programs as if they are the same thing. This is because there is a very fuzzy line between the two terms if, indeed, such a line exists. We can start by considering a program. A program is a sequence of instructions to the computer. It tells the computer what to do and in what order. A program is produced by a programmer who uses a computer language to tell the computer what to do. Some examples of the languages used by programmers include BASIC, FORTRAN, COBOL, C, C++ and LISP. There are many more. 8.2.2 Software Software is a term used to describe programs. However software encompasses others areas such as the Operating System and programs supplied by third parties but as this software is still a sequence of instructions to the computer it can still be considered a program. However when people refer to the Operating System, they normally call it software rather than a program. Page 35 GCSE Information Technology Chapter 8 - Applications Software 8.2.3 Applications Software Applications Software is a little easier to define. It is a collection of programs (or software) that has been designed for a specific task. It normally comes with documentation (often on CD-ROM these days) and support from the supplier. For example, a Word Processor is a piece of applications software. It is a collection of programs that allows you to manipulate words (and usually graphics as well). You will receive some sort of manual that allows you to use the application. You may, optionally, receive some sort of support arrangement that allows you to phone somebody if you have a problem or query. Applications software is often known as a package or simply an application. Q.8.2 Questions Q.8.2.1 Is RAM hardware or software? 8.3 Types of Application Package In the next few chapters we will be looking at three specific applications (Word Processing, Spreadsheets and Databases). However it is important to realise that there are other types of applications packages. 8.3.1 Custom Designed Packages You (or more likely a company) may have a specific requirement that needs a custom built application to be written. For example, an insurance company might consider that it needs to write a package that deals with all its business needs. The package may be written by the company itself or it might use a software house to write it for them. The end result is a custom designed (and written) package. 8.3.2 Common Requirement Packages Word Processing, Spreadsheets and Databases are the three most common uses for computers but there are other packages which people and companies commonly need. For example, many companies use a computer to send invoices and prepare their accounts. There are packages you can buy which have already been written to carry out these tasks. Q.8.3 Questions Q.8.3.1 What do you consider are the advantages and disadvantages of a custom designed package as opposed to buying a package ‘off the shelf’? 8.4 Deciding which package to buy In order to decide which application to buy or to use it has to be evaluated. This means deciding which application is most suitable for the job you plan to do. An insurance company, for example, might evaluate all the packages available before deciding if it will write its own. Page 36 GCSE Information Technology Chapter 8 - Applications Software To carry out the evaluation a company will compile a list of all the things that it needs a package to do. Each package will then be compared against this list to see if it meets the requirements of the insurance company. They may also consider some of the following points as part of the evaluation; Is the package easy to use? Is it supported in case there are problems? Is it updated regularly to cope with things like changes introduced by the government? Does the package come with manuals so that the users can refer to them? Is there a training course available to learn how to use the package? Can the package accept input from and output data to other packages used by the company? Does the package run on the computers used by the company? Is the package reliable? For example, does it validate and reject invalid input? The company may also go and see other companies that are using the package in order to see it in action and find out if it has proved reliable. Once the evaluation has been completed the insurance company will decide which package to buy or whether to write their own package. Q.8.4 Questions Q.8.4.1 If you had to write an essay, what would you look for in a Word Processing Package to assist you? 8.5 Some typical packages In the chapters that follow we will be taking a closer look at some typical applications. This section gives an introduction to the applications we will be looking at and describes when you might use them. 8.5.1 Word Processing A Word Processor is a package that allows you to enter, edit and print text. This book was produced on a Word Processor. Depending on the sophistication of the Word Processor you may be able to change the font and size of the characters as well as perform other actions related to the text. Some Word Processors include options that will check your spelling and even your grammar. You may be able to send a personalised copy of the same letter to all of your friends without having to type a separate letter to each of them (that is, mail merge). You may also be able to include pictures and graphics amongst the text although this is getting close to Desk Top Publishing which produces documents which are suitable for publication. 8.5.2 Databases A database allows data to be stored and retrieved. Once the data has been entered it can be retrieved in a variety of ways. For example, you can retrieve it in some sort of order (that is, sort it) or you can retrieve data that satisfies some criteria (for example, all employees who earn over £12,000). Page 37 GCSE Information Technology Chapter 8 - Applications Software 8.5.3 Spreadsheets A spreadsheet holds data in a table format; as a series of rows and columns. The cells (as they are called) can be related in various ways. For example, one cell might hold a cost price for a particular item. Another cell might hold the VAT rate in force at the current time. Using the information in these two cells you can work out the retail price of the product. If the cost price or the VAT rate changes then the retail price will automatically change. 8.5.4 Graphics A graphics application will produce various types of graphics based upon some data that has been supplied. The data often comes from a spreadsheet or database. Various types of graphics can be produced. For example a simple line graph or a pie chart. Q.8.5 Questions Q.8.5.1 What package would you use for each of the following tasks? i. Writing a report. ii. Preparing company accounts. iii. Keeping information about the products a company supplies. iv. Keeping a class register. Q.8.5.2 Give an example of a use for each of the applications describe above. Say why the application is suitable. 8.6 Communication between packages Many applications allow communication between itself and other applications. This is commonly done by one of two methods. 8.6.1 Importing and exporting One application is able to accept data that has been produced by another application. That is it can import data. To be able to import data the sending application has to be able to export data. That is produce data in a format that another application can read. 8.6.2 Cut/Copy/Paste Within an application you can often highlight a section of the data and then copy the data . This makes a copy of the data in a reserved area (on some systems this is known as the Clipboard or Clipbook). You can now switch to another application and do a paste. This copies the previously copied data into that application. You can also use cut instead of copy. This removes the data from the original application but still makes it available to the other application. Page 38 GCSE Information Technology Chapter 8 - Applications Software R.8 Optional Further Research R.8.1 Being able to communicate between packages via the export/import method often involves using special file formats. Investigate and experiments with the following file formats; Rich Text Format (RTF), Comma Separated Variables (CSV) and ASCII text (TXT). R.8.2 DDE and OLE are yet other ways of using data from one application in another. Find out what these terms mean and investigate how they work. Page 39 GCSE Information Technology Chapter 9 - Word Processing Chapter 9 -Word Processing 9.1 Definitions for this Chapter Word Wrap : The way a Word Processor automatically keeps words on the same line without splitting them. Font : A set of characters of a particular size and design. Margin : The limits at which you are allowed to print text on a page. 9.2 Introduction to Word Processing 9.2.1 A typical Word Processor Word Processing is an application that allows you to enter, edit and print text. This book was written on a Word Processor and you may be using a Word Processor to look at it. The following screen shot shows what a typical Word Processor looks like. You can see that the Word Processor is running in a GUI environment (see chapter 5). The main part of the screen is where text is actually typed. You can see part of this chapter within the window. Page 40 GCSE Information Technology Chapter 9 - Word Processing 9.2.2 Entering Text To enter text you simply type and the text appears where the cursor is positioned (you can see the cursor in the above screen - it is the black line just above ‘9.2’). When entering text you simply keep typing until you reach the end of a paragraph. You only press the ‘ENTER’ key when you reach the end of a paragraph. You do not (and should not) press the ‘ENTER’ key when you are nearing the end of a line as the Word Processor will automatically ‘word wrap’ onto the next line. This means that if there is not enough space to fit a word onto the end of the current line the entire word is placed on the next line. This means you do not have half of a word on one line with the remainder on the next line. 9.2.3 Common features The menus and toolbar (the little pictures below the menu) are there so that you have access to the various facilities within the Word Processor. Some of the common facilities are described below. You can underline text; like this You can make text bold; like this You can make text italic; like this You can change the font style and the size of text; You can centre text on the page; like this You can combine these different styles; font and size). (underline, bold, italic, different 9.2.4 Other Features Some Word Processors will include features such as Spell Checking. If the Spell Checker finds a word it does not recognise it will suggest words that you might choose to take its place. If you select one of these words it will automatically replace the incorrectly spelt word. Here is an example of a spell checker in action. The word ‘schol’ was spelt incorrectly. When it was spell checked it suggested that the word be changed to ‘school’. We were also given a number of other words we could use instead. Page 41 GCSE Information Technology Chapter 9 - Word Processing The buttons on the right (Ignore, Ignore All, Change etc.) allow us to decide what to do. Word Processors contain many other features. Some will even check your grammar and even allow you to type in a word and have it suggest alternatives; that is a Thesaurus. Q.9.2 Questions Q.9.2.1 Using any Word Processor you have access to write at least three paragraphs, with each paragraph occupying at least three lines. Make use of bold, italics and underlining. Also use different fonts and sizes. Print the document. Q.9.2.2 Type the word ‘windws’ (windows without the ‘o’) into a Word Processor. Spell check it. What suggestions are you offered as a replacement word? 9.3 Margins A piece of A4 paper is 21cms wide and 29.7cms high but when you print you do not print right to the edge of the paper. It is the margins that dictate how far in from the edges you print. There are various ways to set margins. One method is to use a dialogue box; like this This particular dialogue sets the margin for a complete document. You simply change the values for the relevant margins (e.g. the left and right). Alternatively we can set margins for individual paragraphs. This is done in a similar way but only affects the selected paragraphs. Note that the Word Processor you use might have a different way of setting the margins but the result will be the same. Page 42 GCSE Information Technology Chapter 9 - Word Processing 9.4 Indents Closely related to margins are indents. This is a method of formatting a paragraph so that the first line of the paragraph is indented. Like this paragraph. Alternatively the second, and subsequent, line can be indented. This means the paragraph will look like this. Can you see the difference between the two. To set indents you can often use a dialogue box similar to that shown above. But you may also be able to use the ruler. This is an area on the screen that is dedicated to changing the layout of the page. This screen shot shows a ruler. This is the ruler. You can “drag” this to change the margin or indent Q.9.4 Questions Q.9.4.1 Using the document you created in Q.9.2.1 change it so that the right and left hand margins are 1cm less than they were originally. Also change the paragraphs so that the first lines are indented by a further 2cm. Print the document. 9.5 Tabs Pressing the ‘TAB’ key (normally the key above ‘Caps Lock’) is a method of arranging text on the page. By pressing the tab key you can jump a certain number of spaces. Typically this is five but you can define your own tabs so that you jump as many spaces as you want. Tabs are useful for creating simple tables and should be used in preference to multiple space characters. 9.6 Blocks of text When working with a Word Processor you often need to work with whole sections of text. For example, you might need to delete a paragraph, move a page or copy a couple of sentences. To do this, Word Processors allow you to highlight a section of text and then work with that section. If your Word Processor allows you to work with a mouse you usually highlight text by clicking and dragging. Once the text is highlighted you can perform the relevant operation on it. Page 43 GCSE Information Technology Chapter 9 - Word Processing Q.9.6 Questions Q.9.6.1 Using the document you created in Q.9.4.1 move the third paragraph so that it becomes the second paragraph. Print the document. R.9 Optional Further Research R.9.1 It was stated in the text that tabs should be used in preference to multiple spaces. Why is this? Hint : It has to do with proportional fonts. Page 44 GCSE Information Technology Chapter 10 - Databases Chapter 10 - Databases 10.1 Definitions for this Chapter Data File : Consists of a collection of records. Record : A collection of fields which relate to one subject, for example all the details about one of your friends. Field : Part of a record that holds one item, e.g. a name, an address, a phone number etc. Key : A field which uniquely identifies a record Database : A large file(s) containing related information which can be accessed in a variety of ways. Query : Specifying to a database program a set of conditions. The records which match the criteria are returned. Expression : Something which returns a single value. This can be a number, a string or a value such as TRUE or FALSE. Logical Operators : Terms such as AND, OR and NOT which can be used within a query to make a single expression. Information Retrieval : Retrieving the information you require (normally via a query) from stored data (usually a database). 10.2 What is a database? Before we look at a computer database let’s just consider what a database is when it is not stored on a computer. A telephone directory is a database. The directory itself can be considered a data file. It is a file that contains related information. The information consists of names, addresses and phone numbers, for all the people in a particular area. The directory (or data file) is split up into a number of records. In this case each record consists of a persons name, their address and their phone number. The individual parts of a record are called fields. In our telephone directory there are three fields; name, address and phone number. Each field will have a data type associated with it (see Chapter 2). One of the fields will be designated as the key field. This is the field that uniquely identifies each record. In the questions for this chapter you are asked to consider what is the key field for a telephone directory. To summarise, a database consists of a data file, the data file contains records, each record has a number of fields; one of which is the key field. The terms datafile and database are almost identical in meaning but the definition of a database is that the data can be accessed in a variety of ways. With a telephone directory you can only access the data using somebody’s surname. If the file was stored on computer it would be possible to search the data to search for a number to see who it belonged to. Of course, the same search is possible with a telephone directory but it would be much too slow to be of practical use. Page 45 GCSE Information Technology Chapter 10 - Databases Q.10.2 Questions Q.10.2.1 What is the key field in a telephone directory? Q.10.2.2 For a school register say what is the datafile, the records, the fields and which field is the key field? Q.10.2.3 Give three examples of when it would be sensible to use a computerised database? 10.3 Setting up a database 10.3.1 Deciding upon and setting up the database structure Let us assume that we want to set up a database to hold information about all the people in the school. When we are setting up a database the first thing we have to do is decide what type of data we want to keep. Here is a list of the data we might want to hold (you would probably want to keep more). Field Name Data Type First Name Surname Date of Birth Phone Number Class Number Text(30) Text(30) Date Text(15) Numeric In deciding on our data we have already made some important decisions. We have named each field and decided which data type we will use to represent it. We can now enter this information into the database so that it knows what type of data to expect. An example of this having been done is shown below. Page 46 GCSE Information Technology Chapter 10 - Databases 10.3.2 Collecting the data Now we have decided on the data we want to keep we need to actually collect it. For our example it is quite an easy process. The school probably has this information already. We just need to collect it altogether so we can enter it into our database. But you may need to find other ways in order to collect the data. For example, you may want a field that holds information about each persons interests or hobbies. To collect this you may need to send out a questionnaire. Some ideas for collecting data were outlined in Chapter 4. 10.3.3 Entering the data Once the database has been set up and the data has been collected we can enter it into the database. You will enter the data one record at a time. Carrying on with the example we started above you may end up with a database that looks like this (though, in real life, there would be more records). First Name John Michael Jane Michele Mark Surname Brown Smart Smithers Sheet Dempster Date of Birth 21/07/83 19/08/83 20/03/83 06/04/83 09/07/83 Phone Number 01987-12345 01987-12303 01962-87614 01962-81762 01987-51482 Class Number 23 14 23 23 14 Once you have entered the data you can add new records, delete records and edit those that are already in the database. Q.10.3 Questions Q.10.3.1 If your school identified its classes by cathedrals (e.g. Salisbury, Canterbury etc.) what change(s) would need to be made to the database definition shown above (section 10.3.1). Q.10.3.2 Create a computer database that holds data about everybody in your class. Decide for yourself what data you want to keep. Next collect that data in whatever way you feel is appropriate, set up the database using appropriate data types and then enter the data you have collected. Produce a print of the database records and also a print showing the database structure. Also hand in your data collection documents. Page 47 GCSE Information Technology Chapter 10 - Databases 10.4 Using a database Once we have our database we can use that data in various ways. 10.4.1 Sorting A database allows you to sort the data so that it appears in some sort of order. For example, we could sort the small database we have been looking up so that it appears in Surname order. Our database will now look like this. First Name John Mark Michele Michael Jane Surname Brown Dempster Sheet Smart Smithers Date of Birth 21/07/83 09/07/83 06/04/83 19/08/83 20/03/83 Phone Number 01987-12345 01987-51482 01962-81762 01987-12303 01962-87614 Class Number 23 14 23 14 23 Of course, we can sort on any of the fields. Depending on what you want to use the database for, it may be sensible to sort the database on the Class Number. 10.4.2 Querying One of the most powerful features of a database is the ability to ask it questions or perform queries. As an example we might want to ask the database to show us all the records for class 23. We would be returned the following records. First Name John Michele Jane Surname Brown Sheet Smithers Date of Birth 21/07/83 06/04/83 20/03/83 Phone Number 01987-12345 01962-81762 01962-87614 Class Number 23 23 23 To ask a query we enter an expression. This is something which returns a single value. In the example given above the expression would be ‘Class Number = 23’. This is an expression which returns a value of TRUE or FALSE. If TRUE is returned the record is displayed. If FALSE is returned the record is not displayed. Therefore ‘Class Number = 23’ is FALSE for class 14 so these records are not displayed. In the database used to produce these examples the query to show all students in class 23 is entered in a window like this: Page 48 GCSE Information Technology Chapter 10 - Databases It is possible to add simple expression together to form more complex queries. This is done using logical operators. For example, you could ask to see all students in class 23 with a surname of Smith. The expression for this would be ‘Class Number = 23 AND Surname = Smith’. The AND is a logical operator. It says that both simple expressions must be TRUE for the entire complex expression to be TRUE. Other logical operators include OR and NOT. 10.4.3 Printing If we have taken the trouble to sort our database and perform queries to extract the information we require it would seem sensible to be able to print it. As well as printing all the records of the database it is also possible just to print the results of a query. Examples of these types of print have been shown above. It is also possible to only print certain fields. You may want to create a telephone list from the database. This requires all the records to be printed but only the Surname, First Name and Telephone Number. We do not require the Date of Birth or the Class Number. The telephone list would look like this. Surname Brown Dempster Sheet Smart Smithers First Name John Mark Michele Michael Jane Phone Number 01987-12345 01987-51482 01962-81762 01987-12303 01962-87614 Notice that we have also moved the Surname field so that it is the first field. This is because you would expect a telephone list to appear in this format. Q.10.4 Questions Q.10.4.1 Using the sample database we have developed in this chapter what expression would you use to search for anybody in class 18 or for anybody with a surname of ‘Jones’. Q.10.4.2 Using the database you created in Q.10.3.2 sort the data on one of the fields, carry out a query and produce a print which does not show all the fields. Hand in three prints showing the results. Also provide a brief description of the field you sorted on and the query you did. R10 Optional Further Research R.10.1 There are many types of database. Two of the most common are a ‘flat-file database’ and a ‘relational’ database. Investigate the differences between the two and make a list of advantages and disadvantages. Which one do you consider best? Page 49 GCSE Information Technology Chapter 11 - Spreadsheets Chapter 11 - Spreadsheets 11.1 Definitions for this Chapter Model : A simulation of something so that it behaves like the real thing. Spreadsheet : A type of program that gives you a table on the screen. You can enter various types of data into a spreadsheet and make relations between the data. Cells : A spreadsheet is made up of rows and columns. The point at which a row and column meet is called a cell. A cell is referenced by its row and column. You enter data into a cell. Formula : A formula is typed into a cell. It is used when you wish to work out the value for that cell from the values in other cells. Relative Reference : A relative reference changes when the cell is copied. That is the cell reference is relative to its position on the spreadsheet. Absolute Reference : An absolute reference stays the same, even if the cell is copied. 11.2 Models 11.2.1 What is a model? Before we look at spreadsheets we are first going to consider the term model, as a spreadsheet is a good example of a model. You will already be familiar with the term model either from its use on the catwalk or when it is used to describe something that looks like another object. For example, you could build a model of a Formula 1 racing car. When creating a model on a computer we are doing something that is not too far removed from building a model of the racing car. We take a real life situation and model it on the computer. A good example, especially for this chapter on spreadsheets, is the financial accounts for a company. If we use a spreadsheet to ‘do the accounts’ we are modelling the accounts on the computer. The accounts actually exist as part of the business. We are simply modelling them on the computer. Although this chapter is mainly about spreadsheets, models are not just applicable to that type of application. Other examples of models are; A Space Invaders type game. This models a world where earth is being attacked by aliens. A car assembly plant that is automated by robots. The computer will have a model of the robot programmed into it. The database we developed in the last chapter. This models the students in a school. Page 50 GCSE Information Technology Chapter 11 - Spreadsheets 11.2.2 Why use a model? There are many reasons for using a model. Some of these reasons are as follows: A model can be made to go faster than real life so we can predict what is going to happen; for example a weather forecast. You can ask ‘what if’ questions. If you have modelled a company on a spreadsheet you can ask what will happen to your profits if you sell less products in the first quarter next year? You can experiment without danger. In a car racing simulation it does not matter if you crash. It can be cheaper. The Army may use a tank simulator to train their drivers rather than risk using a real tank and have it damaged. It can give people access to things they could never do in real life. A museum could model a rare book on computer so that everybody could look at it. The actual book could not be handled by so many people. Systems such as road traffic in a town or the ‘Big Bang’ theory can be modelled to see if we understand how they work by seeing if the model acts in the same way as the real thing. 11.2.3 Disadvantages of using a model The main disadvantage of using a model is that it does not know everything about the situation you are modelling. Your company accounts will not know what will happen to interest rates. In a Virtual Reality game you may only have feeling in your hands as that is the only place on your body where there are sensors which are connected to the model. Q.11.2 Questions Q.11.2.1 Think of three situations which are models of the real world. Where does the model differ from the situation it is modelling? 11.3 Spreadsheets 11.3.1 Introduction to Spreadsheets A spreadsheet is often used to model situations which are based on numeric data. Spreadsheets were originally designed for accountants and they are often used to prepare company accounts (which is a model of the current state of the finances of a company). Page 51 GCSE Information Technology Chapter 11 - Spreadsheets When you use a spreadsheet you are presented with a table; like this: Column Cell Row 1 2 3 4 5 A January B C D 56.71 123.57 The spreadsheet is made up of individual cells. In the spreadsheet above one of the cells contains the value 123.57. The cells are arranged in columns and rows. The columns go down the spreadsheet. The rows go across the spreadsheet. Each column is given a name. In the above example we have the columns A, B, C and D. Similarly the rows are given names (1, 2, 3, 4 and 5). Using the row and column labels it is possible to reference any cell in the spreadsheet. The cell which contains the value 123.57 is in the cell referenced by B3. A spreadsheet can hold three types of data: 1. Numbers. For example, 123.57 2. Text. For example, ‘January’ 3. Formulae, which we will look at in a moment. 11.3.2 Sample Spreadsheet Below is a sample spreadsheet. It models a school outing that is going to visit Manchester United’s Old Trafford Football Ground. A 1 2 3 4 5 B C D School visit to Old Trafford Football Ground Name Brian Dawn Stephen Amount to pay 65.00 65.00 65.00 Page 52 Paid so far 33.54 23.58 5.87 Left to pay GCSE Information Technology Chapter 11 - Spreadsheets Notice the following points The main title has spread over its neighbouring cells. This is because there is not enough space to fit everything into the cell A1. The column widths are different sizes. This is so that we can fit all the data into the cell. For example, the ‘Name’ column is quite wide so that we can fit in a long name. It is possible to adjust the width of any column. You can improve the look of the spreadsheet by using different sizes of fonts and types of alignment. For example, the title is printed in a font size of 14. It is also bold. The column headings are centred within the cell and also printed in bold. The rest of the spreadsheet is printed in the ‘standard’ font size. All the figures have been ‘formatted’ so that they print two decimal places. If we did not do this a value such as 23.90 would show as 23.9 and the 65.00 value would show as 65. The figures have been ‘right aligned’ within the cells. This means they are right up against the right hand edge of the cell. This has been done so that the decimal points line up. We have not entered values into the ‘Left to pay’ cells. Later we will see how to get the spreadsheet to work these out automatically. 11.3.3 Adding a formula So far all we have done is entered data into the spreadsheet. We could achieve exactly the same result with a Word Processor. So why use a spreadsheet? A spreadsheet program gives us the ability to enter a formula into a cell. Let’s take a look at an example: If we type ‘=B3-C3’ into cell D3 the value 31.46 will appear in D3. This is because we are using a formula. A formula always starts with an equals sign (that is how the spreadsheet knows it is a formula) and is followed by a mathematical expression. In this case it is saying “take the value in cell B3 and subtract from it the value in C3”. We can enter the same formula into D4 and D5 to work out how much Dawn and Stephen still have to pay. But we must change the cell references so that we are referring to rows 4 and 5. Our spreadsheet, with the formulae displayed, would look like this: A 1 2 3 4 5 B C D School visit to Old Trafford Football Ground Name Brian Dawn Stephen Amount to pay 65.00 65.00 65.00 Page 53 Paid so far 33.54 23.58 5.87 Left to pay =B3-C3 =B4-C4 =B5-C5 GCSE Information Technology Chapter 11 - Spreadsheets This is what you would actually enter but the actual display would look like this: A 1 2 3 4 5 B C D School visit to Old Trafford Football Ground Name Brian Dawn Stephen Amount to pay 65.00 65.00 65.00 Paid so far 33.54 23.58 5.87 Left to pay 31.46 41.42 59.13 Because the ‘Left to Pay’ values are being calculated by a formula we can change one of the other figures and the ‘Left to Pay’ figure will automatically be updated. For example, if Stephen pays another £20 we would change C5 to 25.87. D5 would automatically change to 39.13. Just to emphasise that point, we do not have to change D5 in any way because it contains a formula, it updates itself. 11.3.4 More on Formulae In a typical spreadsheet application there are many types of formula you can enter. In the above example we have just used subtraction. We could just as easily have used addition, multiplication or division (although it would not make sense in the context of what we are modelling). We can also use functions. These are features of the spreadsheet that do slightly more complex tasks than simple expressions. Before we look at some of the common functions we need to look at how we refer to a group of cells at the same time. At the moment, all we have learnt is how to refer to a single cell (e.g. C4, B3 etc.) but what do we do if we need to refer to all the cells from C3 to C5? To do this we specify the two ends of the range separated (normally) by a colon. So to refer to cells C3 to C5 we use ‘C3:C5’. Now we can look at some of the common functions. SUM : This is by far the most common function. It adds together the values in the specified range. For example, if we entered ‘=SUM(B3:B5)’ in cell B6 of the above spreadsheet the cell will display 195.00. This is exactly the same as using the formula ‘=B3+C3+D3’ but it is shorter, especially when the range of cells becomes large. AVERAGE : Returns the average of the cells in the given range e.g. ‘=AVERAGE(C3:C5)’ would return 40.04 MAXIMUM : Returns the maximum value in the range. ‘=MAXIMUM(C3:C5)’ would return 33.54. MINIMUM : The same as MAXIMUM but returns the minimum number. Note that the name of the functions may be slightly different in the spreadsheet you use. For example, MAXIMUM may be called MAX. Page 54 GCSE Information Technology Chapter 11 - Spreadsheets 11.3.5 Copying Cells Up until now you may have been entering each formula into every cell that requires a formula. There is an easier way. You can enter a formula into one cell and then copy that formula into other cells that require a similar formula. In our example, if we enter a formula into cell D3, we can copy that formula and then paste it into D4 (see 8.6.2 for a description of copy and paste). The spreadsheet automatically changes the cell references in the formula from row 3 to row 4. This is because it assumes you want to work on figures on the same row that the formula is on. And this is nearly always the case. These types of references are called relative references as the cell references change relative to where they are on the spreadsheet. There is another type of reference called an absolute reference. These references are often specified in the format $C$5 (as opposed to C5). If you copy one of these references the cell reference does not change. This type of reference is useful if you have a fixed figure on your spreadsheet (such as the VAT rate). No matter how many times you copy a formula you always want the formula to point to the same cell to find out the current VAT rate. Q.11.3 Questions Q.11.3.1 Look at the Old Trafford spreadsheet in 11.3.2 above and answer the following questions: What value is in cell C4? In what cell is the value ‘Paid so far’? Q.11.3.2 Using a spreadsheet package of your choice set up the Old Trafford spreadsheet as shown in 11.3.2. Try to match the formatting as closely as possible. Hand in a print of the result. Q.11.3.3 Using the spreadsheet you produced in Q.11.3.2 answer these questions. Enter some text into cell B2. What happens and why? Increase the font size of ‘Amount to Pay’ by at least four points. What happens and what can you do to correct it? Change the format of the cells which display numeric values so that a pound sign is automatically displayed (e.g. entering 52.34 is displayed as £52.34). Why is it important not to enter the pound sign when typing in the figures? Q.11.3.4 Using the spreadsheet you have been developing, use the SUM function to show how much all the students have paid so far and how much is still outstanding. Produce a print. Q.11.3.5 What is the benefit of holding something like the VAT rate on the spreadsheet and accessing it via an absolute cell reference? Q.11.3.6 Set up a spreadsheet that models the money you spend each week and what you spend it on. The spreadsheet should have the days of the week down the side and the things you spend your money on across the top. Provide totals for each day and for each item you spend money on. Produce a print. Page 55 GCSE Information Technology Chapter 11 - Spreadsheets R11 Optional Further Research R.11.1 Using a spreadsheet it is easy to produce graphs. Find out how you do this with the spreadsheet that you are using and produce a bar chart and a pie chart from one of the spreadsheets you developed in this chapter. R.11.2 Modify one of the spreadsheets that you have developed for the Manchester United trip so that 10% is added to the money everybody has to pay. The 10% should be held on the spreadsheet and referenced by absolute cell references. Change the 10% to 12.5% and ensure the spreadsheet is updated correctly. Page 56 GCSE Information Technology Chapter 12 - Graphics Chapter 12 - Graphics 12.1 Definitions for this Chapter Graphic : A picture, graph or image that has been produced on a computer. Bitmap : A picture that is built up from pixels. Vector : A picture that is described in terms of points and how those points are joined together. 12.2 Graphics 12.2.1 Introduction Graphics are simply pictures on the computer and as a picture is worth a thousand words they are an important part of Information Technology. However just saying they are pictures on a computer does not really explain the different types of graphics. Here are a few examples. The pictures used in a computer game. Pictures drawn by the computer based on some branch of mathematics. The most famous example is probably fractals. Graphs and Charts that are used to help show how a business is performing. For example, a graph could be produced which shows how sales have increased over the past year. Architects use graphics to represent a building they are working on. This is often called CAD (Computer Aided Design). 12.2.2 How graphics are stored There are two main ways to store graphics on a computer; pixel based formats and vector based formats. If you look at a newspaper picture using a magnifying glass or microscope you will see that the picture is actually made up of small dots. When viewed from far enough away the dots create the picture. This is similar to a pixel based format on a computer. The image is stored as a series of pixels (see chapter 6; especially 6.3.1) and the computer just draws each of the pixels onto the screen to create the picture. It is slightly more complicated than that as the number of colours has an affect on how much space is needed to store each pixel. Also, many pixel based file formats compress the data so that it does not take up so much disc space. But, the concept is quite simple. Each pixel is held which, when displayed, creates a graphic. Vector based graphics work differently. They describe the position of various points that make up the picture and how those points are related. When the graphic is drawn on the screen it uses this information to draw the various lines and points on the screen. Page 57 GCSE Information Technology Chapter 12 - Graphics Q.12.2 Questions Q.12.2.1 If the same image is stored as a pixel based format and as a vector based format, what format do you think would be most suitable to use if the image had to be enlarged? Hint : Try drawing a circle on squared paper and then enlarging it by making each pixel (square) bigger so that it occupies four squares instead of one. R12 Optional Further Research R.12.1 There are many different file formats available; for example GIFF, BMP, JPEG, WMF etc. Find at least six different file format standards and find out in which situations you would use them. Also say if they are pixel based or vector based. Page 58 GCSE Information Technology Chapter 13 - Communications and Networks Chapter 13 - Communications and Networks 13.1 Definitions for this Chapter Data Communication : Communication of data either between two computers or between a computer and a person. Telecommunications : Communicating data over long distances, usually over telephone lines but could also be via satellite, micro waves etc. Facsimile (Fax) : Using a telephone line to transmit documents. Computer Network : Two or more computers that are connected together so they can share data or devices such as printers or CD-ROM’s. Local Area Network (LAN) : A relatively small network of computers. The computers are usually in a single building such as an office or a school. Wide Area Network (WAN) : A network of computers which connect computers over a large area. The computers are often in different towns and even in different countries. Modem : A device which allows a computer to be connected to a telephone line. Modem is short for MOdulator-DEModulator. 13.1 Introduction to Communications and Networks We are all familiar with communication. We do it every day. Some forms of communication are given here. Talking to people. Watching television. Listening to the radio. Reading books. Using a fax machine to transmit documents over telephone lines. Using a telephone. Using teletext to access information supplied by television companies. Communication between computers is just another form of communication. Every time you sit down at a computer you are taking part in a dialogue that is a form of communication. However a computer does not only communicate with people. A computer can also communicate with other computers. Consider a Cash Card Machine. The machine into which you insert your bank card is a small computer but it has to communicate with another computer that holds your account details so that it can check you have enough money in your account before it gives you any money. In order for computers to communicate with one another they have to be connected together. This is done by way of a network. A network can be as simple as a piece of wire joining two computers together or it can be a network that allows the computer to talk to millions of other computers all over the world. Page 59 GCSE Information Technology Chapter 13 - Communications and Networks Some benefits of having computers networked together are given below Computers can share information. It is easy for somebody to pass a copy of a file to somebody else. There is only one source of data. The company can keep all their information on a single computer and let everybody access that data. Devices such as printers and CD-ROM’s can be shared rather than every computer having their own. Disc space requirements can be reduced as applications can be accessed from a central point rather than everybody having their own copy. Maintenance is easier as support personnel can maintain the system via the network. Q.13.2 Questions Q.13.2.1 One of the benefits of a computer network is that it allows everybody to share a common source of data. Why do you think this is important? 13.3 Types of Network There are two main types of network. 13.3.1 Local Area Network (LAN) A Local Area Network (LAN) is a computer network that is located at one location; typically an office or a school. The computers are usually connected together by wires which run around the building. There is normally somebody (or a team) who is responsible for the network and they will ensure everybody can access the parts of the system they are entitled to access but restrict access to the parts they are not authorised to use. Often there are passwords that stops unauthorised people accessing the system. 13.3.2 Wide Area Network (WAN) Wide Area Networks (WAN’s) connect computers together over large distances. It is quite normal to join several LAN’s together via a WAN. A LAN is normally connected via cables that have been run around the building. This is obviously not convenient for WAN’s. Therefore other ways are used to connect WAN’s together. Examples are; Fibre Optic Cables. These are supplied by third party companies and rented to various users. Satellite and Micro Wave links. Telephone lines; either used by dialling up the computer you wish to communicate with or by having a fixed line which is available all the time (often called a leased line). Page 60 GCSE Information Technology Chapter 13 - Communications and Networks It is worth noting that if you wish to communicate using the telephone line you need a Modem (Modulator - Demodulator). This equipment takes the data from the computer and converts it to a form that is suitable for the telephone network. When the data arrives at the receiving computer another modem does a similar operation but this time converts it from the telephone format to a format which the computer can understand. Q.13.3 Questions Q.13.3.1 Think of three business in your local High Street that you think would use a LAN and three that are probably connected to a WAN. Q.13.3.2 The sale of modems has increased in the past few years. They have been sold to people who wish to access the biggest computer network in the world. What is this network? Page 61 GCSE Information Technology Chapter 14 - Control Systems Chapter 14 - Control Systems 14.1 Definitions for this Chapter Control System : Everything that in needed is order to control a particular device. This includes all the hardware and software. Output Port : A point on a computer into which a device can be plugged so that the processor can communicate with the device. Input Port : A point on a computer into which a device can be plugged so that the device can communicate with the processor. Control Signal : A signal from a processor to a device which tells it what to do. Interface : A piece of hardware or software that sits between a processor and a device which allows them to communicate. Converter : A type of interface that converts signals from one form to another so that a processor/device can communicate. Sensor : A detector that monitors on behalf of a device so that signals can be sent to the processor. Feedback : The ability of a device to provide signals to the processor about its current state. LOGO : A computer programming language. Turtle : An electronic turtle or a turtle represented on the computer screen that is controlled by LOGO. Procedure : A series of instructions in a programming language that are grouped together and can be executed by a single instruction. 14.2 What is a Control System? A control system is a combination of everything that is needed to control a certain device. This may involve a computer, some software, some additional hardware and the device being controlled. A good example is a robot. The computer will be running software that tells the robot what to do. There will be some additional hardware that connects the computer and the robot together. The device being controlled is the robot itself, whether just a robotic arm or something that can move around, see things and pick things up. However it is not only external devices that are control systems. A disc drive inside a computer is an example of a control system. The processor sends data to the disc drive together with instructions as to what to do and the disc drive acts upon those instructions and tells the processor when it has finished. There are examples of control systems scattered throughout your house. A washing machine is just one example. Q.14.2 Questions Q.14.2.1 Give examples of three other control systems that you would find in your home. Page 62 GCSE Information Technology Chapter 14 - Control Systems 14.3 Communicating with the devices The computer (or micro-processor) has to have some way of communicating with the device it is controlling. Connection from the computer to the device is made via an output port. This is a point on the computer where you can plug in the device. The computer you use at school will probably have at least two output ports where a mouse and a printer are connected. Control Signals are used to tell the device what to do. In the case of a (simplified) disc drive there will be a control signal that says the data that follows should be written to the disc and another signal that says the disc drive should retrieve some data from the disc. Control signals can take various forms. For example, it could be a change of voltage on a wire or it may be signals sent by radio waves. In some circumstances there may have to be a converter between the computer and the device. This is needed if the pieces of equipment use different signals. For example, the computer may use digital signals and the device may use analogue signals (see Chapter 1; especially 1.2). In this case a Digital-to-Analogue (D-A) Converter is needed to convert digital signals to analogue signals. Similarly an Analogue-to-Digital (A-D) converter will be needed to convert signals being sent from the device to the computer. An A-D (or D-A) converter is an example of a special type of interface that is needed in order to allow the two pieces of equipment to work together. An interface may be needed for other reasons. For example, if the two pieces of equipment operate at different speeds an interface may be needed in order to keep the two pieces of equipment in sync. Q.14.3 Questions Q.14.3.1 Do you think there is a need for any sort of interface between a mouse the processor? 14.4 What can the computer control? Typically a computer can control the following types of devices. A relay switch : A relay is a switch which can be on or off. If the computer was controlling a device such as an electrical socket or a motor, then a relay would be appropriate. An actuator : When an actuator receives a signal it converts it into movement. Disc drives use actuators to position the read/write heads to the required track. It is important that the actuator moves the read/write head the same distance for each pulse of electricity it receives. A motor : An actuator could be used to turn a motor on and off. But a special type of motor, called a stepper motor has to keep receiving signals in order for it to keep going. Every time it receives a signal it moves the motor a small amount. Actuators and stepper motors are closely related. Page 63 GCSE Information Technology Chapter 14 - Control Systems Q.14.4 Questions Q.14.4.1 For a motor which can be turned on and off how many control signals are required? 14.5 Feedback It is possible that the processor just sends signals to a device and that is the end of the matter. But it is more common to have some sort of feedback so that the device can inform the processor about various situations. For example, a printer can tell the processor it is out of paper so that the processor can stop sending information. In order to be able to receive signals from a device the computer must have an input port. This is the same as an output port but allows the computer to receive signals. There also has to be some form of sensor so that the device can detect what is going on. In the case of something like a burglar alarm the sensor will be something that can detect movement. An extension of this idea is to have a device which continuously collects data. The data can be stored on the computer for later analysis or can be analysed as the data is collected so that instant decisions can be made. Q.14.5 Questions Q.14.5.1 Give three examples of control systems that have some form of feedback capability. Q.14.5.2 Think of a system where a device that continuously collects data would be appropriate. 14.6 Turtles and LOGO Your school may have access to a computer language such as LOGO. This language is used to control a turtle. The turtle can either be a real one (or at least an electronic version of one) or a representation of one that appears on the computer screen. You control the turtle with simple instructions (control signals). Page 64 GCSE Information Technology Chapter 14 - Control Systems 14.6.1 Example of LOGO Assuming the turtle is facing North, the following LOGO program will produce a square: No. Program 1 LOGO Instruction Effect 1 2 3 4 5 6 7 8 9 10 PEN DOWN FORWARD 60 RIGHT 90 FORWARD 60 RIGHT 90 FORWARD 60 RIGHT 90 FORWARD 60 RIGHT 90 PEN UP Puts pen down so any movements draw a line Moves the turtle forward 60 steps Turns the turtle 90 degrees Moves the turtle forward 60 steps Turns the turtle 90 degrees Moves the turtle forward 60 steps Turns the turtle 90 degrees Moves the turtle forward 60 steps Turns the turtle 90 degrees Lifts up the pen You may notice that the above program uses the same four instructions four times (FORWARD and RIGHT). We can use the REPEAT statement to replace instructions 2 to 9; like this: REPEAT 4 [FORWARD 60 RIGHT 90] This is saying, repeat the instructions in brackets four times. A further enhancement we could make is to make the instructions for drawing a square into a procedure. This means grouping the instructions together and giving them a name. Now if we want to draw a square we simply use the instruction: SQUARE (or whatever we named the procedure). Q.14.6 Questions Q.14.6.1 If you have access to LOGO run the program 1 from this section. If you do not have LOGO then run the program ‘manually’ (that is, use paper and pencil). Hand in the results. Q.14.6.2 Using the LOGO language write a program that would draw a triangle that has equal sized sides and equal sized angles (that is, an equilateral triangle). Q.14.6.3 What do you think are the main advantages of writing procedures? Page 65 GCSE Information Technology Chapter 14 - Control Systems R14 Optional Further Research R.14.1 If you are interested in programming you might like to look at languages such as BASIC, PASCAL, C or C++. These languages are used within industry and an understanding of them could be important if you wish to take up a career in the computer industry. R.14.2 If you live near an industrial area you might like to arrange a visit to a manufacturing plant that uses computers on, say, a production line. You might like to produce a small project showing how the computers work, what type of control signals are used and if there is any data logging. Page 66 GCSE Information Technology Chapter 15 - Developing Systems Chapter 15 - Developing Systems 15.1 Definitions for this Chapter System Life Cycle : The steps that are followed when developing and maintaining an IT system. Systems Analyst : The person who analyses the current system (if there is one), produces the requirements for the new system and comes up with a design that will meet those requirements. Programmer : The person who writes the programs that have been specified by the systems analyst. Top-down design : The process of breaking tasks down into smaller and smaller tasks until they are easy enough to understand and write programs for. 15.2 The System Life Cycle The system life cycle represents the various stages that an IT system goes through, from the moment it is a twinkle in somebody’s eye to the moment it ceases to be of any use. The system life cycle is very important as it provides a framework which is used to control the development and maintenance of a system and this is very important. Many systems, in large organisations, take hundreds of man years to develop and are very expensive. An investment of this size needs a lot of control to ensure the project is progressing satisfactorily and that the company is getting a good return on their investment. The system life cycle looks like this New Requirement Feasibility Study Maintain Analysis Implement Design Build Each of the following parts of the system life cycle is explained below. Page 67 GCSE Information Technology Chapter 15 - Developing Systems 15.2.1 New Requirement The starting point for any IT system is that somebody has a requirement. It might be to ensure a warehouse never runs out of goods, make sure the customers pay the correct amount for their gas or to install a new set of traffic lights to make the traffic flow better at a certain crossroads. At this stage it is important to state exactly what the problem is. For example, is it to get customers to pay their gas bills on time or is it to make sure they are charged the correct amount ? (It will probably be both of these (and more) but you can see there are two different problems). 15.2.2 Feasibility Study This is a report that says whether the system is feasible or not. It may include some of the following points (and probably more). Some of these points may be discussed in greater detail later in the system life cycle. Is the system cost effective? How much will the system cost to develop and will the company get a return on the investment it plans to make? How long will the system take to develop? If it will take five years can the company wait that long? Will the system be developed by the company’s staff or will an outside company be asked to develop it? Alternatively are there any packages available that can be bought that will do the job? Is the system practical to be implemented as an IT system? For example, if one of the requirements is to be able to communicate with the system via speech is this possible given the current state of technology? How will the company be affected by implementing the system? Will some of the employees have to be made redundant? Will new employees be needed because of the new system? What sort of training will be required; both to develop the system and to allow the company’s employees to use it? On production of the feasibility study the requirements of the proposed system might change or it may even be decided to abandon the project altogether. 15.2.3 Analysis The analysis phase allows the systems analyst (IT people who have the necessary skills to analyse a current system and produce a specification for an IT system) to investigate the system. Page 68 GCSE Information Technology Chapter 15 - Developing Systems The systems analyst will do the following: Look at the current system (whether manual or already an IT system) to see what it does and how it does it. This can be done by reading any documentation available and by observing how the current system operates. Interview the people who use the current system to find out all they can about the system and what their involvement is with it. Interview potential users of the new system to find out what their expectations are. Work out exactly what the new system has to do. Work out what other systems (whether computer based or manual) which the new system has to communicate with. At the analysis stage of the system life cycle no decisions are made as to which hardware and software will be used (although in practise it is often assumed due to hardware and software already being used by the company). 15.2.4 Design The design phase takes all the work that the systems analyst has done and decides how the system should be implemented. Actions carried out at this stage of the system life cycle include: Deciding on the hardware and software to be used. Designing the screens that the user will see. This will also involve deciding on what type of user interface will be used (e.g. command line or graphical). Deciding how data will be stored (e.g. on a database), what data is required and the data type for each data item. Deciding what programs are required and what each program will do. Produce a specification that will allow computer programmers to actually write the programs that will make up the system. In carrying out the design the usual method is to use something called top-down design (sometimes called stepwise refinement). Using this method you start with the top level of the system (e.g. produce gas bills) and gradually break this task down into smaller and smaller units until a task is easy to understand and produce a program for. 15.2.5 Build the system This stage is all about writing the programs and testing the system. Initially a programmer will write the programs that have been specified by the systems analyst during the design stage. The programmer will test the programs to ensure they work as specified. Once the program is working it will be tested with all the other programs that have been written for the system. This is called System Testing. The final stage of testing is called Acceptance System. This is when the future users of the system test it to ensure it meets their requirements. Page 69 GCSE Information Technology Chapter 15 - Developing Systems Also, as part of the new system built, the necessary documentation will be prepared. This will include manuals for the users as well as documentation that allows the system to be more easily maintained. In fact a lot of the system documentation will come from earlier stages of the system life cycle. 15.2.6 Implement Once the system has been acceptance tested, the system is implemented. This phase of the system life cycle might include the following: Loading live data onto the system. This might including keying in data held on manual records, collecting data by some other means (e.g. scanning bar codes) or converting the data from an existing system. Training the users how to use the new system. Moving all the programs to a secure area so that they cannot be tampered with. The system might be implemented for all the company in one go (sometimes called the ‘big bang’ approach) or it might be phased in over a number of weeks or a number of months (often called a phased implementation). 15.2.7 Maintain The ‘maintain’ phase of the system life cycle is really the starting point to enter the cycle again. Somebody will come up with a change that needs to be made to the system. It might be a legal change (e.g. gas for the over 60’s has to be charged at a special rate) or it might be a change in the company’s policy (e.g. high gas users get a special discount). Once the change has been identified the cycle moves into feasibility study and so the cycle continues. When carrying out your coursework project you will need to use elements of the system life cycle. Page 70 GCSE Information Technology Chapter 16 - Documentation Chapter 16 - Documentation 16.1 Definitions for this Chapter Documentation : A means of communicating information about an IT system. Typically the documentation is supplied as a manual but it is often supplied on CD ROM. Flowchart : A form of documentation that graphically represents a process. 16.2 Types of documentation In the previous chapter we briefly mentioned documentation when building a system. During the build stage of the system life cycle it is usual to produce a user manual and a systems manual. 16.2.1 User Manuals The user manual is the documentation that describes how to use the system. It should describe what to do when the users want to achieve a particular result. As an example, take a look at the manual for the word processor you have been using and see if you can find out how to centre text on the screen. This is an example of something you want to do so the user manual should tell you how to do it. The user manual should also tell you what to do if you get an error message (what does it mean and what do you do to recover from it). It may also tell you how to install the software. 16.2.2 System Manuals System Manuals are used by those people who have to maintain the system. The manual describes the system so that future developers can refer to it when deciding what changes have to be made. System manuals are typically split into a number of levels. The top level will describe the whole system (often on a single page). It will say where the system fits into the organisation and what other systems it communicates with. The bottom level of the system manuals will describe each program so that a programmer does not have to look at a program listing and work out what it is trying to do. 16.3 Flowcharts When producing documentation a wide variety of techniques can be used. One technique, called flowcharts, is often used when describing processes. Page 71 GCSE Information Technology Chapter 16 - Documentation A flowchart uses symbols to represent certain operations. Here are some examples Disc File Magnetic Tape General Operation Decision An example of using a flowchart to describe a typical process is as follows. Writing and Posting a Letter Write Letter Buy Stamp No Got a stamp? Yes Stick stamp on envelope Post Letter This is obviously a trivial example but it demonstrates how processes are represented and how decisions are catered for. Page 72 GCSE Information Technology Chapter 16 - Documentation This example shows how file updates are represented. Accept pupil name from keyboard Print Error Message Validate name No Name Okay? Yes Student Database Add name to database Again, this is only a simple example but notice how the student database is updated only after a valid name has been input. Also note that some of the operation boxes have a double line at the top. This shows that this is a high level task that has another flowchart somewhere else which further explains how that particular process works. This is an example of stepwise refinement. Q.16.3 Questions Q.16.3.1 Draw a flowchart of the processes involved in making a cup of tea Q.16.3.2 Draw a flowchart which expands the ‘Validate Name’ Box. Your flowchart should check that both a first name and a surname has been entered and that neither exceed 20 characters in length. R16 Optional Further Research R.16.1 Decide upon a computer program that you wish to write. Before starting to write the program plan it using a flowchart. Try to keep each flowchart to one page and use sub-flowcharts where necessary. Only when you have finished flowcharting process should you write the program using a language of your choice. Once the program is complete ensure the flowchart is updated so that it accurately represents the program. Page 73 GCSE Information Technology Chapter 17 - The impact of IT Chapter 17 - The impact of IT 17.1 Definitions for this Chapter Electronic Funds Transfer (EFT) : Moving money from one bank account to another using data communications between computers. Electronic Data Interchange (EDI) : Moving data from one computer to another, primarily to carry out a business transaction without the need for paper. 17.2 A brief History IT has already had a big effect on our lives; arguably a bigger effect than the Industrial Revolution. It may come as a surprise that IT (using computers) is relatively young. The first working computer was not produced until the 1940’s, with computers not being sold until the fifties. By the 1960’s many large companies had computers and used them for tasks such as payroll and stock control. These computers filled rooms the size of football pitches and they had to be air conditioned due to the amount of heat they generated. To communicate with these computers you normally had to be in the same room and it was usually by means of a teletype terminal. In the 1970’s computers were getting smaller and mini and micro computers were introduced. In addition the visual display unit become a lot more common. In this decade the banks started using MICR to speed up cheque clearance. The 1980’s were a boom time for computers. Personal computers became common place. DOS and Windows (and Microsoft) almost dominated the PC business. The Graphical User Interface (GUI) became the accepted way to communicate with PC’s. The range of software also increased and, as computers became more powerful, the type of work they could do also increased. By the ‘80’s most people would have used a computer (even if they were unaware of it). Washing machines, video recorders, card cash machines and many other devices used a computer of some description. The cashless society, although not with us by the 80’s, looked increasingly more likely as we got used to using Credit and Debit cards. Most medium to large businesses had (and relied) on computers. If the 1980’s saw the rise of the PC, then the 1990’s look like being the decade of communication. The Information Superhighway (the Internet, Cyberspace - call it what you will) has touched many lives and it is now possible to communicate with millions of other computers and people for the price of a local phone call. Computers are also becoming ever more powerful and it is possible, with a multimedia PC, to play video and sound. Many small businesses have computers and many homes have a PC somewhere in their house. Most children use computers at school and are growing up computer literate. Page 74 GCSE Information Technology Chapter 17 - The impact of IT 17.3 The effect IT has had on our lives Here are just a few ways that IT have affected our lives: We are now a more cashless society. We can pay by credit and debit cards. Electronic Funds Transfer (EFT) is also widespread. EFT allows money to be moved from one bank account to another using data communication between computers. The majority of people are paid via EFT. More business is conducted using Electronic Data Interchange (EDI). EDI allows goods and services to be sold without the need for paper forms. For example, you can buy insurance via EDI. You go into an insurance broker and select the policy you want. Your order will go directly to the insurance company and update their database without the need to send any forms. The majority of office workers have a PC on their desk. This allows them to access a lot more information than they could do before and also makes them more effective in their day to day tasks. More personal data about us is held on computers. This helps companies in many ways. One example, is that they can offer us products through the post which we know we have an interest in. The government of the day holds information about us on computers. This can speed up things like payment of Social Security and also help detect fraud. Some people argue it is an invasion of privacy that the government (and companies) hold all this information. Many homes in the country have a PC in their house. This helps students carry out their school work, can help in areas such as the household accounts and can be used for entertainment; such as playing games. Using on-line services such as the Internet we can communicate with people all over the world. It is also possible to shop through these services. Many people are made redundant due to IT being introduced into the workplace. A counter argument is that many IT related jobs are also created so overall it balances out. IT is allowing many people to work from home (tele-work). This means less commuting saving both time and money. But some of the reason for going to work is for the social interaction that takes place. Q.17.3 Questions Q.17.3.1 Consider the statements given in 17.3 above. Choose three. Give a different justification to those already given as to why it is a good thing and also give an opposite viewpoint. Finally, state which viewpoint you agree with. Q.17.3.2 Give another three areas where IT has changed our lives. State whether you think they are a good or bad thing and give your reasons. Q.17.3.3 Many jobs are lost through the introduction of IT into the workplace. Give three reasons why this happens. Q.17.3.4 The Data Protection Act was introduced in 1984. What are the main aims of this act (you need to research this question). Page 75 GCSE Information Technology Chapter 18 - Your Coursework Project Chapter 18 - Your Coursework Project 18.1 Introduction As well as sitting an examination you will also have to produce some coursework which will count towards your overall mark. The coursework is very important. It accounts for 60% of the total mark and should be taken seriously. Before you start your coursework try to do the following: Make sure you know what is required. It is not just about showing that you can use a computer. Typically you will have to show that you have used IT to solve a problem. Try to look at projects from previous years. This will give you some idea of what is required. Once you have decided on your project try to write down the main objective in one or two sentences. If you cannot do this you will gradually get more and more confused about what you are trying to achieve as the project continues. If you can, take a look at the marking scheme. As the project progresses, make sure that you are addressing the areas where marks are awarded. For example, if you create a database it may be pointless entering a thousand records if you can enter just ten records and still pick up full marks for showing that you have developed a system that meets the objectives you set out at the start of the project. 18.2 What shall I do for my coursework? One of the biggest choices you have to make (assuming it is not made for you) is what your coursework will be about. You will probably want to look for a problem that you can use IT to solve. Here is a small list of suggestions but make sure you choose to do something that interests you otherwise you will lose interest half way through. Putting the accounts of a small business onto a spreadsheet. Cataloguing your CD, Record and Tape collection on a database. Keeping a list of all your friends. You could include who you exchange birthday (and Christmas) cards with, when you last sent them a letter, when you last spoke to them on the phone. Managing a knock out competition for a local sports club. Managing the membership details of a local club. This could include sending out letters when membership is due for renewal and keeping track of all the accounts. 18.3 How do I do my coursework? In undertaking your coursework you need to adopt a logical approach. The following is a list of steps you might go through. It is important that you document each stage as these reports can form part of the overall project documentation. Page 76 GCSE Information Technology Chapter 18 - Your Coursework Project 18.3.1 Propose the Project This document will describe to your teacher the problem you are trying to solve. You should include the people who are affected by the project and what benefits they will see once the project has been implemented. Your teacher will have to agree with your project proposal before you are allowed to continue. 18.3.2 Analysis This stage of the project will be a more detailed analysis of the problem. You need to: Interview the people involved to find out exactly what they want. State exactly what the proposed system will do. Define all the data the system will be storing and where and how you will collect it. Define what output will be produced by the system. At this stage of the project you do not say how you will solve the problem. You are simply stating what the problem is and what you need to do in order to solve the problem. 18.3.3 Design the System This is the stage where you say how you will solve the problem. You can investigate potential solutions, evaluate packages and consider what hardware you need. Depending on the project you may have to: Design programs (e.g. produce flowcharts). Define the structure of a database (e.g. say what fields you will use and assign a data type to each one). Plan how a spreadsheet will be developed (e.g. what the rows and columns will represent). Plan out how a letter will look (e.g. the wording of a letter to the member of a club). You may also have to do some work on designing forms for data capture, defining exactly how the output will look and deciding how you will check the data has been entered accurately. 18.3.4 Implement the System During this part of the project you will actually build the system that you have been planning. This might include writing computer programs, setting up a database or spreadsheet or creating various letters and forms on a word processor. It is important that you test the system. This should be done in a logical way. One way of doing this is to decide what input data you will use and then work out what output it will produce. When you enter the planned input you can check to see that you get the expected output. Page 77 GCSE Information Technology Chapter 18 - Your Coursework Project It is important to test every part of the system. Try putting invalid values into the system to see that the system rejects them. Also try putting values that are on the borders of the allowed values. For example, if you write a program that allows the user to input a number between 1 and 100, try putting in 99, 100 and 101. Whilst testing, keep a copy of your results as this can be used in your project documentation. 18.3.5 Document the System If you have been documenting the system as you go along you should have much of the documentation already prepared. You may need to finalise the system documentation and also produce a user manual so that other people can use the system. 18.3.6 Evaluate the System It is important that you produce a report which evaluates your project. Did you meet the original objectives you set yourself? What problems did you have and what did you do to resolve them? What could you do to further improve the system? What would you do different if you did the same project again? Was the project a success? If not, why not? The evaluation ties up all the loose ends of a project and makes sure that you learnt from it. It can also be a good starting point for other people considering a similar project as they can see what problems you had and how you would resolve them if you did it again. You may have noticed that the method suggested above is very similar to the system life cycle (see Chapter 15). You do not have to follow the system life cycle or the procedure outlined above but it is important that you have some plan as to how you will tackle the project. Not only will you be able to check that you are progressing at a suitable pace but it can also give you a framework into which you write your coursework report. Page 78 GCSE Information Technology Chapter 99 - Answers to Questions Chapter 99 - Answers to Questions Q.12 Questions Q.1.2.1 Give three examples of IT, that you use every day. A.1.2.1 There are obviously many answers. Examples are watches, faxes, mobile phones, radios, televisions, washing machines. Q.1.2.2 Looking at the five main areas of IT, above, give one example of each area that you use in everyday life. A.1.2.2 The students can give many examples. Possibilities are: Handling Information : Searching an address book for a friends address. Communicating Data : Phoning up a friend. Measuring and Control : Using a TV remote control. Presenting Information : Writing a school essay. Modelling the Real World : Keeping a school timetable that models your day. Q.1.3 Questions Q.1.3.1 Would you consider the following digital or analogue? i The music coming from a speaker. (analogue) ii The price of postage stamps. (digital) iii Whether a bank account is in credit or debit (in the black or in the red)? (digital) iv The different combinations of colours a traffic light can have. (digital) Q.1.3.2 Give an example of something which is digital and something which is analogue? A.1.3.2 There are many answers. Digital examples include, stations on a TV set and a digital watch. Analogue examples include tuning an old fashioned radio and a clock with hands. Q.2.2 Questions Q.2.2.1 Give two examples of information? A.2.2.1 Almost any answer will do as long as it has meaning to somebody. Q.2.2.2 Give two examples of data? A.2.2.2 Almost any answer will do as long as it can be justified as being data. Q.2.2.3 Whether something is information or data sometimes depends on who is looking at it. Give two examples where this could be the case and say who would regard it as information and who would regard it as data? A.2.2.3 Many answers are acceptable. Two examples are A personal diary written in a code would be information to its owner but only data to anybody else. A news bulletin in English would be information to English speaking people but data to everybody else. Q.2.3 Questions Q.2.3.1 Look at the following data and say which data type best describes it. i 12 (integer) ii a (character) iii aa (string) iv -34.98 (numeric) v A telephone number (string - probably not numeric as there are likely to be spaces and you will not want to perform numeric operations on the data) vi Your age (integer) vii Your Christian Name (string) Page 79 GCSE Information Technology Chapter 99 - Answers to Questions Q.2.4 Questions Q.2.4.1 What characters do you think make up the character set of the English language? A.2.4.1 All the letters (upper and lower case), all the digits and all the punctuation symbols. These should definitely be included. The student may include others. Q.2.4.2 What is the character set for all the non-vowel characters in the English alphabet. A.2.4.2 B through to Z excluding A, E, I, O and U. The student may also include the lower case set as well as the digits and punctuation characters. Q.2.5 Questions Q.2.5.1 Give three examples of where you use codes in your daily life, almost without realising it. A.2.5.1 Almost any sensible answers are acceptable. For example, postcodes, CD ( for CD-ROM), £3.20 (for three pounds and twenty pence) and a Telephone STD code to represent an exchange. Q.2.5.2 If you were asked to introduce a coding scheme for the Premier Division Football teams how would you do it? As well as devising a coding scheme what else would you need to think about? A.2.5.2 There are ten teams in the Premier league so a one character code would be enough. But it might be more sensible to code the teams as two characters so that teams like Liverpool and Leeds (which both start with ‘L’) can use their second letter to identify them. Alternatively, you might use a three character code which fits in with some of the normal football conventions (e.g. QPR for Queens Park Rangers). You need to think about what to do if there is still a clash after the first two (or three characters ). For example, ‘Manchester City’ and ‘Manchester United’. You also need to be aware there that the codes will change as teams are promoted and demoted. Q.2.6 Questions Q.2.6.1 Consider a class register. Identify what happens to it during the various phases of the data processing life cycle. A.2.6.1 Data Collection : Who is attending that class? Data Input : Write the names in the register. Data Processing : Mark attendances and absences. Output : Produce a report on attendance for the Headmaster. Q.3.2 Questions Q.3.2.1 If some data is in RAM why should you regularly copy the data to a disc drive? A.3.2.2 Because data is lost from RAM when the computer is turned off (or if there is a power cut) and unless you copy it to a disc you will lose the data. Q.3.2.2 What is one advantage of distributing software (programs) on CD-ROM as opposed to using floppy discs? A.3.2.2 Possible answers include: It is cheaper as a CD-ROM costs less to post than a number of floppy discs. It is easier to install the software as you do not have to keep swapping floppy discs. You can run programs from CD-ROM so you do not have to use space on your hard disc - this is not usually true of floppy discs. The software providers normally give ‘extras’ away as they have spare space on a CD-ROM. Q.3.2.3 From the following list decide if each item is hardware or software? i A Floppy Disc (Hardware) ii A Word Processing Program (Software) iii A Computer Game (Software) iv A Joystick (Hardware) Page 80 GCSE Information Technology Chapter 99 - Answers to Questions Q.3.3 Questions Q.3.3.1 What do you think is a disadvantage of a multi-user system? A.3.3.1 Possible answers include: If too many people are using the system the response time could be slow. If there is a problem with the system all the users are affected (how do you feel when you can’t get money out of a cash machine due to ‘computer error’ ?) Q.3.3.2 What do you think is a disadvantage of a single-user system? A.3.3.2 Possible answers include: You may not have access to corporate data, which is somewhere else - possibly on the mainframe. Your computer may not be powerful enough to run the software you need in order to do a certain job. Q.3.4 Questions Q.3.4.1 Do you think the following are interactive or real time processes or both? i A flight simulator (both) ii Using a calculator (interactive) iii Booking a holiday at a travel agents (both) iv A crossword puzzle on a computer (interactive) Q.3.4.2 When you buy a train ticket you can reserve a seat. Do you think the train operator could use a single user system to provide this service? If not, why not? A.3.4.2 No. The bookings have to be done on a central, multi-user system so that the same seat is not booked twice. Q.4.2 Questions Q.4.2.1 Collect five examples of forms that are designed to capture data. Say what you think are the good and bad points about each form. Design your own form to collect data about your classmates. How does your form compare to others in your class? A.4.2.1 This is simply a matter of personal taste (although there are recognised good and bad practises used in industry). For example, some students might think it good that boxes are provided for each letter of your name. Others might see this as a restriction on the amount of data that can be input. Q.4.2.2 Give three examples of data capture forms where the form has already been pre-printed with details about yourself. A.4.2.2 There are many examples including gas and electric meter reading forms, TV licenses, Road Tax reminders, Mail Order Shopping orders. Q.4.2.3 Design a simple questionnaire and try it out on people at school (both students and teachers). What problems did you encounter? What could you have done to reduce these problems? A.4.2.3 There are obviously many answers to this questions and many lessons to be learnt. It is almost a mini-project and includes many other subjects as well as Information Technology. Page 81 GCSE Information Technology Chapter 99 - Answers to Questions Q.4.3 Questions Q.4.3.1 Next time you are in your local town see how many different ways you can find that retailers capture data. A.4.3.1 There are many answers including bar codes (and scanning), entering prices into tills, collecting customer requirements on a form, giving an estimate/quotation and approaching customers to ask if they can help. Q.4.3.2 Apart from cheque and cash cards where else would you find a magnetic strip? A.4.3.2 There are many answers including entry cards, London Underground tickets, Credit Cards and Phone Cards. Q.4.3.3 As long as you are aged sixteen or over you can go into thousands of shops, pay one pound and see OMR in action. What would you be doing? A.4.3.3 Entering The National Lottery. Q.4.3.4 Give one advantage and disadvantage of OMR, OCR and MICR. A.4.3.4 There are numerous answers. A sample answer (with two answers in each section) is given below: Advantages (OMR) 1) It is a quick way to collect data. 2) It is less error prone than some other methods. Disadvantages (OMR) 1) The design of the forms can be complicated. 2) The person filling in the form has to follow the instructions precisely. Advantages (OCR) 1) It saves time as the data does not have to be re-type. 2) It can understand hand-written and typed characters. Disadvantages (OCR) 1) There can be a high failure rate in recognition. 2) Characters can be recognised incorrectly. Advantages (MICR) 1) It is difficult to forge. 2) It is a common standard within the financial sector. Disadvantages (MICR) 1) The system only recognises one set of characters (font). 2) MICR systems are expensive. Q.4.3.5 Can you think of another type of input device that is commonly used to play games? A.4.3.5 A joystick. Q.5.2 Questions Q.5.2.1 What do you consider are the main advantages of a GUI over a Command Line Interface? A.5.2.1 There are many answers but you might expect to see these (or variations): It is easier to use (more intuitive). You do not have to remember long strings of commands. Q.5.2.2 If you have access to an IBM compatible PC go to the Command Line Interface (the DOS Prompt) and try these commands. What do they do? i DIR (show all the files in the current directory) ii CLS (Clears the screen) iii COPY C:\AUTOEXEC.BAT MYFILE.BAT (Copies a file) iv PROMPT $T (changes the prompt to the current time) (Note : You may not be allowed access to the DOS prompt. In which case you will be unable to do this question) Q.5.2.3 GUI’s are sometimes called WIMP environments. Why do you think this is? A.5.2.3 WIMP is an acronym for Windows, Icons, Menus and Pointer Page 82 GCSE Information Technology Chapter 99 - Answers to Questions Q.6.2 Questions Q.6.2.1 Give examples of two output devices - one which produces information and one which produces data. Do not use examples given in the text and do not use computer output devices. A.6.2.1 There are many answers. Two acceptable answers, in each category, are Personal Stereo (information), TV Remote Control (data), Printing Press (information) and a Telephone when dialling a number (data). Q.6.3 Questions Q.6.3.1 Teletext is an example of a screen mode. Would you say that a teletext display needs a high, medium or low resolution monitor? Explain your answer. A.6.3.1 Low. The characters are built from ‘chunky’ characters. There is no fine detail and no graphics to talk of. Having said that they achieve some good effects. Q.6.4 Questions Q.6.4.1 Imagine you are a 24 pin dot matrix printer. Using graph paper show how you would print an ‘m’, an ‘a’ and an ‘!’. A.6.4.1 You should receive a grid which is 24 units high. An ‘m’, ‘a’ and ‘!’ should be represented by filling in the relevant squares. If the students use a magnifying glass they will be able to see the individual dots on a page printed with a dot matrix printer. Q.6.4.2 A printer can either be considered a character printer (where one character is printed at a time), a line printer (where a complete line is printed at a time) or a page printer (where a whole page is printed at a time). Classify a dot matrix printer, an ink jet printer and a laser printer into each of these categories. A.6.4.2 Dot matrix printer (character - typically), Ink jet printer (character - typically), Laser (Page). Note : Line printers are normally connected to mainframes where a complete line is printed before the paper is advanced. Q.6.4.3 Many printers have two modes of operation; draft quality and letter quality (sometimes called Near Letter Quality or NLQ). After reading the definitions at the beginning of this chapter how do you think the two modes might be implemented on a dot matrix printer and a laser printer? A.6.4.3 Dot matrix implementation is done by ‘missing’ dots. Laser implementation is done by a printer with not such a high resolution (i.e. less dots per inch). Q.7.2 Questions Q.7.2.1 How many characters can you store on a 3.5” High Density Floppy Disc? How does this differ from a 3.5” Double Density disc? (Note : this question requires research by the student). A.7.2.1 3.5” HD = 1.4 million, 3.5” DD = 750,000 (both approx.) Q 7.2.2 Using your knowledge of storage devices what do you think is the best medium for the following types of data? i. A large application distributed to a great many people (CD-ROM) ii. An Operating System (ROM or Hard Disc) iii. A weekly security copy (Magnetic Tape) iv. A copy of a file that you need to take home (Floppy Disc) v. A letter that you are writing to your friend (Hard Disc or RAM) Page 83 GCSE Information Technology Chapter 99 - Answers to Questions Q.7.4 Questions Q.7.4.1 Would you consider a CD-ROM a direct access or a serial device? A.7.4.1 It is a direct access device but some data may have to be read serially. However it is important that the students recognise it is predominantly a direct access device. Q.7.4.2 Give one advantage of a direct access device and one disadvantage A.7.4.2 It allows fast access to any piece of data. There is an overhead to allow this type of access. Q.7.4.3 Give an example where direct access would be more suitable over serial access. A.7.4.3 There are many examples. One possibility is a library. If somebody borrows a book you would want direct access to the data about that book. If you had to read information about every book the system would be too slow. Q.7.5 Questions Q.7.5.1 The directory structure shown in 7.5.2 can be represented as a tree structure. Draw a tree that represents this structure. A.7.5.1 The start of the tree is shown here: C:\ accounts gk acroread hk Q.7.6 Questions Q.7.6.1 Why is it important for a security copy of a file to be stored away from the computer which has the original file on? A.7.6.1 If there is a disaster such as a fire you need to ensure the security copies remain intact. Q.7.6.2 Can you think of a disadvantage of compressing data as you take the security copy? A.7.6.2 You have to expand the data before you can use it. This takes times and means you have to have access to the program that does the expansion. For example PKZIP (to compress) and PKUNZIP (to expand). Q.8.2 Questions Q.8.2.1 Is RAM hardware or software? A.8.2.1 The electronic chips that make up the RAM are hardware. It can, at any point in time, hold software; along with the data that is being processed. Q.8.3 Questions Q.8.3.1 What do you consider are the advantages and disadvantages of a custom designed package as opposed to buying a package ‘off the shelf’? A.8.3.1 Advantages Does exactly the job you require. Disadvantages More Expensive. It will need supporting. You need to develop and maintain it (e.g. legal requirements). Potentially long time to develop. Q.8.4 Questions Q.8.4.1 If you had to write an essay what would you look for in a Word Processing Package to assist you. A.8.4.1 This is largely a matter of personal opinion but typically the students might say they need a spell checker, something to check their grammar and a Word Processor that can help with the presentation of their finished document. Q.8.5 Questions Page 84 GCSE Information Technology Chapter 99 - Answers to Questions Q.8.5.1 What package would you use for each of the following tasks. i. Writing a report (Word Processor) ii. Preparing company accounts (Spreadsheet) iii. Keeping information about the products a company supplies (Database) iv. Keeping a class register (Database - but Word Processing or Spreadsheets could also be argued) Q.8.5.2 Give an example of a use for each of the applications describe above. Say why the application is suitable. A.8.5.2 There are an infinite number of answers to this questions. The important point is that the student can justify the answer. Q.9.2 Questions Q.9.2.1 Using any Word Processor you have access to, write at least three paragraphs, with each paragraph occupying at least three lines. Make use of bold, italics and underlining. Also use different fonts and sizes. Print the document. A.9.2.1 A document should be presented that meets the specification set out in the question. Q.9.2.2 Type the word ‘windws’ (windows without the ‘o’) into a Word Processor. Spell check it. What suggestions are you offered as a replacement? A.9.2.2 The actual list will depend of the Word Processor and the dictionary being used. The list might include windows, winnow, wind, winds and windy. Q.9.4 Questions Q.9.4.1 Using the document you created in Q.9.2.1 change it so that the right and left hand margins are 1cm less than they were originally. Also change the paragraphs so that the first lines are indented by a further 2cm. Print the document. A.9.4.1 A document should be presented that you can check by inspection against the document handed in for Q.9.2.1. Q.9.6 Questions Q.9.6.1 Using the document you created in Q.9.4.1 move the third paragraph so that it becomes the second paragraph. Print the document. A.9.6.1 A document should be presented that you can check by inspection against the document handed in for Q.9.4.1. Q.10.2 Questions Q.10.2.1 What is the key field in a telephone directory? A.10.2.1 The phone number. Everybody has a different phone number (compared to surname). Q.10.2.2 For a school register say what is the datafile, the records, the fields and which field is the key field? A.10.2.2 Datafile = The register itself. Records = Students name and/or number and if they have attended. Fields = Name and a series of repeating fields which represent a term (or week). Key Field = Students Name and/or number. Other answers are possible. Q.10.2.3 Give three examples of when it would be sensible to use a computerised database? A.10.2.3 There are many possibilities including; an address book, a Christmas card list, a list of birthdays, as well as the uses to which a company would use a database (e.g. stock control). Page 85 GCSE Information Technology Chapter 99 - Answers to Questions Q.10.3 Questions Q.10.3.1 If your school identified its classes by cathedrals (e.g. Salisbury, Canterbury etc.) what change(s) would need to be made to the database definition shown above (section 10.3.1)? A.10.3.1 The Class Number description should be changed (to Class Name?) and its data type changed to Text(20). Q.10.3.2 Create a computer database that holds data about everybody in your class. Decide for yourself what data you want to keep. Next collect that data in whatever way you feel is appropriate, set up the database using appropriate data types and then enter the data you have collected. Produce a print of the database records and also a print showing the database structure. Also hand in your data collection documents. A.10.3.2 You should receive two prints and the data collection documents. These should show the students understanding of how to set up and input data into the database. Q.10.4 Questions Q.10.4.1 Using the sample database we have developed in this chapter what expression would you use to search for anybody in class 18 or for anybody with a surname of ‘Jones’? A.10.4.1 Class Number = 18 OR Surname = ‘Jones’ Q.10.4.2 Using the database you created in Q.10.3.2 sort the data on one of the fields, carry out a query and produce a print which does not show all the fields. Hand in three prints showing the results. Also provide a brief description of the field you sorted on and the query you did. A.10.4.2 You should receive three prints and an explanation of what the student was trying to achieve. You can check the results against the previous database print. Q.11.2 Questions Q.11.2.1 Think of three situations which are models of the real world. Where does the model differ from the situation it is modelling? A.11.2.1 This is a very open question. One possible answer is a name and address book. It models the people you know. It differs in many respects; for example it does not model their height, eye colour etc. Q.11.3 Questions Q.11.3.1 Look at the Old Trafford spreadsheet in 11.3.2 above and answer the following questions. What value is in cell C4? In what cell is the value ‘Paid so far’? A.11.3.1 23.58, C2 Q.11.3.2 Using a spreadsheet package of your choice set up the Old Trafford spreadsheet as shown in 11.3.2. Try to match the formatting as closely as possible. Hand in a print of the result. A.11.3.2 You should receive a print that matches the spreadsheet shown in 11.3.2 (as closely as the package allows). Q.11.3.3 Using the spreadsheet you produced in Q.11.3.2 answer these questions. Enter some text into cell B2. What happens and why? Increase the font size of ‘Amount to Pay’ by at least four points. What happens and what can you do to correct it? Change the format of the cells which display numeric values so that a pound sign is automatically displayed (e.g. entering 52.34 is displayed as £52.34). Why is it important not to enter the pound sign when typing in the figures? A.11.3.3 Part of ‘School visit to Old Trafford Football Ground’ disappears as it can no longer ‘flow’ into cell B2. The cell is no longer big enough to accommodate the data. The cell width will have to be increased. It treats the data in the cell as text. Q.11.3.4 Using the spreadsheet you have been developing, use the SUM function to show how much all the students have paid so far and how much is still outstanding. Produce a print. A.11.3.4 The spreadsheet should have the following figures in the following cells; C6 = 62.99, D6 = 132.01. You might want to check that formulae have been used to generate these figures. Page 86 GCSE Information Technology Chapter 99 - Answers to Questions Q.11.3.5 What is the benefit of holding something like the VAT rate on the spreadsheet and accessing it via an absolute cell reference? A.11.3.5 If the VAT rate changes you only have to change one cell on your spreadsheet and all the other figures are automatically recalculated. Q.11.3.6 Set up a spreadsheet that models the money you spend each week and what you spend it on. The spreadsheet should have the days of the week down the side and the things you spend your money on across the top. Provide totals for each day and for each item you spend money on. Produce a print. A.11.3.6 A spreadsheet should be produced which meets the criteria of the question. The SUM function should be used to work out the totals. Q.12.2 Questions Q.12.2.1 If the same image is stored as a pixel based format and as a vector based format what format do you think would be most suitable to use if the image had to be enlarged? Hint : Try drawing a circle on squared paper and then enlarging it by making each pixel (square) bigger so that it occupies four squares instead of one. A.12.2.1 Vector based graphics are better for scaling as pixel based graphics tend to become ‘jagged’ when enlarged. Q.13.2 Questions Q.13.2.1 One of the benefits of a computer network is that it allows everybody share a common source of data. Why do you think this is important? A.13.2.1 It means there is no duplication of effort in entering and maintaining the data. It also means there is not inconsistency in the data caused by people holding their own files. Q.13.3 Questions Q.13.3.1 Think of three businesses in your local High Street that you think would use a LAN and three that are probably connected to a WAN. A.13.3.1 There are many answers but the best test that can be applied is if the company is part of a national/multi-national company. Then they are likely to be connected to a WAN (e.g. Banks, Building Societies, Insurance Companies, Travel Agents etc.) Companies likely to have a LAN are medium sized self-contained businesses that have a number of computers (e.g. solicitors, estate agents, accountants etc.) Q.13.3.2 The sale of modems have increased in the past few years. They have been sold to people who wish to access the biggest computer network in the world. What is this network? A.13.3.2 The Internet. Q.14.2 Questions Q.14.2.1 Give examples of three other control systems that you would find in your home. A.14.2.1 Possible answers include Video Recorder, CD Player, TV Remote control, an automatic camera and a video camera. Q.14.3 Questions Q.14.3.1 Do you think there is a need for any sort of interface between a mouse the processor? A.14.3.1 Yes. A mouse is an analogue device. Therefore there is a need for an interface. Page 87 GCSE Information Technology Chapter 99 - Answers to Questions Q.14.4 Questions Q.14.4.1 For a motor which can be turned on and off how many control signals are required? A.14.4.1 One or two. There could be two with one being for on and one for off. However one signal could be used with the current state of the motor being reversed each time. Q.14.5 Questions Q.14.5.1 Give three examples of control systems that have some form of feedback capability. A.14.5.1 There are many answers including a computer mouse (tells the processor when it is moving), a burglar alarm (tells the processor when it detects movement), a telephone (tells the processor when somebody is pressing buttons to dial a number) and a central heating system (tells the processor the current temperature). Q.14.5.2 Think of a system where a device that continuously collects data would be appropriate. A.14.5.2 There are many answers. One possible answer is recording temperatures and wind speeds at regular intervals for a weather forecasting system. Q.14.6 Questions Q.14.6.1 If you have access to LOGO run the program 1 from this section. If you do not have LOGO then run the program ‘manually’ (that is, use paper and pencil). Hand in the results. A.14.6.1 You should receive a square which is 60 ‘units’ in size. Q.14.6.2 Using the LOGO language write a program that would draw a triangle that has equal sized sides and equal sized angles (that is, an equilateral triangle). A.14.6.2 One correct program would be: PEN DOWN REPEAT 3 [FORWARD 30 RIGHT 120] PEN UP (The repeat statement could consist of three separate statements) Q.14.6.3 What do you think are the main advantages of writing procedures? A.14.6.3 You do not have to replicate instructions in different parts of the program. This makes it easier to read, easier to maintain and more reliable as the procedure should be fully tested before it is used within a program. Q.16.3 Questions Q.16.3.1 Draw a flowchart of the processes involved in making a cup of tea. A.16.3.1 There are many answers. You should check that the main elements of making tea are present (add milk, add sugar, pour tea, fill kettle etc.) You should also check that there are relevant decisions e.g. Do you take sugar? Do you take milk? Has the kettle boiled? Q.16.3.2 Draw a flowchart which expands the ‘Validate Name’ Box. Your flowchart should check that both a first name and a surname has been entered and that neither exceed 20 characters in length. A.16.3.2 The flowchart will be different for each pupil but they should have common features. They should all have decision boxes checking that the first name and surname has been entered. They should also have decision boxes that check that neither part of the name exceeds 20 characters in length. The flowchart should NOT get the name from the keyboard. This is done on the higher level flowchart and including it in this would mean the user being asked twice. Q.17.3 Questions Q.17.3.1 Consider the statements given in 17.3 above. Choose three. Give a different justification to those already given as to why it is a good thing and also give an opposite viewpoint. Finally, state which viewpoint you agree with. A.17.3.1 The answers the students give are almost immaterial as long as they provide some sort of justification. Page 88 GCSE Information Technology Chapter 99 - Answers to Questions Q.17.3.2 Give another three areas where IT has changed our lives. State whether you think they are a good or bad thing and give your reasons. A.17.3.2 Again, the answers are almost immaterial. The aim of these questions is to make the students consider the implications of IT and not just consider the positive viewpoints. Q.17.3.3 Many jobs are lost through the introduction of IT into the workplace. Give three reasons why this happens. A.17.3.3 There are many answers. Some samples are: People are more efficient now that many companies use an electronic office so less secretaries and clerical staff are needed. Companies who automate their manufacturing process do not need as many people to produce the same amount of goods. Companies which do not keep up with the IT revolution face stiffer competition and may go bankrupt as they cannot compete. Companies such as railway operators and telephone operators rely on computers to monitor their operations and do not need as many people. Industries such as printing have been deeply affected by the IT revolution. The industry has changed almost beyond recognition and require a lot less people. Q.17.3.4 The Data Protection Act was introduced in 1984. What are the main aims of this act (you need to research this question). A.17.3.4 There are eight main principles to this act. 1. The information to be held shall be obtained and processed fairly and lawfully. 2. Personal data shall be held only for one or more specified and lawful purposes. 3. Personal data held for any purpose shall not be used or disclosed in a manner incompatible with that purpose. 4. Personal data shall be adequate, relevant and not excessive in relation to the purpose for which it is being held. 5. Personal data shall be accurate and kept up to date. 6. Personal data shall not be held for longer than is necessary. 7. An individual shall be entitled, without undue delay or expense, to view the data being held about them and, where appropriate, have it amended or deleted. 8. Appropriate security measures should be taken to protect the data. Page 89