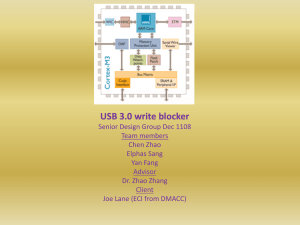
Conventional memory
advertisement

Core Module Conventional memory Conventional memory is the first 640 kilobytes of an IBM PC's memory. Prior to extended memory specifications such as Expanded Memory Specification (EMS), Extended Memory Specification (XMS), and High Memory Area (HMA), real mode applications could use only this part of the memory. Even when extended memory is present, real-mode applications have to be specially programmed to use it using a complex system of overlays; consequently, many applications continued to use only conventional memory. History As DOS applications grew larger and more complex in the late 1980s, it became common practice to free up as much conventional memory as possible by moving device drivers and Terminate and Stay Resident programs (TSRs) into Upper Memory Blocks (UMBs). For older real mode operating systems (OSes) such as MS-DOS, it was often worthwhile to tune the system to load drivers and other system components into UMBs (chunks of extended memory remapped into the Upper Memory Area (UMA)) in order to leave as much conventional memory as possible free for running large applications. With modern operating systems and 32-bit machines the distinction between conventional and extended memory is rarely relevant, since all memory can be accessed uniformly in protected mode. 640 KB barrier The 640 KB barrier is an aspect of the IBM PC and compatibles when running under MS-DOS which could only address up to 640 KB of memory for running applications. This is due to limitations of the original IBM PC, which used the Intel 8088 CPU. The term refers to the size of the PC's conventional memory. The 8088 and 8086 were only capable of addressing 1 MB of memory, of which IBM reserved the upper 384 KB for system purposes — the Upper Memory Area. This left only the lower 640 KB for user programs and data. At the time of the PC's release in 1981, 640 KB would have seemed more than plenty for the typical user. Keep in mind that the most popular home computer of that era, the Commodore 64, had only 64 KB, of which only 38 KB were available to the user. To maintain compatibility with older OSes, the 640 KB barrier remained part of the PC design even after the 8088 had been replaced with the Intel 286 processor, which could address up to 16 MB of memory. It is still present in IBM PC compatibles today if they are running MS-DOS. Overcoming the barrier The barrier was only overcome with the arrival of DOS extenders, which allowed DOS applications to run in Extended Memory, but these were not very widely used. The first PC operating systems to integrate such technology were Compaq DOS 3.31 (via CEMM) and Windows/386 2.1, both released in 1988. Windows applications did not suffer from the 640 KB barrier. 1 Core Module Prior to DOS extenders, if a user installed additional memory and wished to use it under DOS, they would first have to install and configure drivers to support either Expanded Memory Specification (EMS) or Extended Memory Specification (XMS) random access memory (RAM), and applications could only store data in the additional space, not executable code. One technique used on early IBM XT computers with Monochrome Display Adapter (MDA) or Color Graphics Adapter (CGA) displays was to add more memory to the motherboard and use a custom address decoder programmable read-only memory (PROM) chip to make it appear at 640 KB; this moved the barrier to 704 KB[1]. Memory managers on 386-based systems (such as QEMM or MemoryMax in DR-DOS) could achieve the same effect, adding conventional memory at 640 KB and moving the barrier to 704 KB or 736 KB. Only CGA could be used in this situation, because enhanced graphics adapter (EGA) used this memory for itself. The AllCard, an add-on memory management unit (MMU) for XT-class computers, allowed normal memory to be mapped into the A0000-EFFFF (hex) address range, giving up to 952 KB for DOS programs. Programs such as Lotus 1-2-3, which accessed video memory directly, needed to be patched to handle this memory layout. Therefore, the 640 KB barrier was removed at the cost of hardware compatibility. Extended memory Extended memory refers to memory above the first megabyte of address space in an IBM PC with an 80286 or later processor. Extended memory is only available on PC's based on the Intel 80286 or higher processor. Only these chips can access more than 1MB of RAM. On a 286 or better PC equipped with more than 640KB of RAM, the additional memory would generally be re-mapped above the 1MB boundary, making all of it available to programs running in Protected mode. Even without such remapping, machines with more than 1MB of RAM would have access to memory above 1MB. Extended memory is available in real mode only through EMS, UMB, XMS, or HMA; only applications executing in protected mode can use extended memory directly. In this case, the extended memory is provided by a supervising protected-mode operating system such as Microsoft Windows. The processor makes this memory available through the Global Descriptor Table and one or more Local Descriptor Tables (LDTs). The memory is "protected" in the sense that memory segments assigned a local descriptor cannot be accessed by another program because that program uses a different LDT, and memory segments assigned a global descriptor can have their access rights restricted, causing a hardware trap (typically a General Protection Fault) on violation. This prevents programs running in protected mode from interfering with each other's memory. A protected-mode operating system such as Windows can also run real-mode programs and provide expanded memory to them. The DOS Protected Mode Interface is Microsoft's prescribed method for an MS-DOS program to access extended memory under a multitasking environment. Expanded memory 2 Core Module Expanded Memory was a trick invented around 1984 that provided more memory to bytehungry, business-oriented MS-DOS programs. These were typically spreadsheets and databases running on the original IBM PC, and on its successors like the IBM AT. Both machines used real mode memory architecture, which only allowed programs to use 1 megabyte of address space, of which only up to 640 KiB was reserved for use. The idea behind expanded memory was to use part of the remaining 384 KiB, normally dedicated to communication with peripherals, for program memory as well. In order to fit potentially much more memory than the 384 KiB of free address space would allow, a banking scheme was devised, where only selected portions of the additional memory would be accessible at the same time. Originally, a single 64 KiB window of memory was possible; later this was made more flexible. Applications had to be written in a specific way in order to access expanded memory. This insertion of a memory window into the peripheral address space could originally be accomplished only through specific expansion boards, plugged into the ISA expansion bus of the computer. Famous 1980's expanded memory boards were AST RAMpage, IBM PS/2 80286 Memory Expansion Option, AT&T Expanded Memory Adapter and the Intel Above Board. Given the price of RAM during the period, up to several hundred dollars per megabyte, and the quality and reputation of the above brand names, an expanded memory board was very expensive. Later, some motherboards of Intel 80286-based computers implemented an expanded memory scheme that did not require add-on boards. Typically, software switches determined how much memory should be used as expanded memory and how much should be used as extended memory. Beginning in 1987, the built-in memory management features of Intel 80386 processor freely modeled the address space when running legacy real mode software, making hardware solutions unnecessary. Expanded memory could be simulated only by the software. A more efficient way to access address space beyond 640KiB on 80286 and later processors, was by using the DOS Protected Mode Interface (DPMI). DOS extenders were drivers that allowed applications to run in protected mode. Rather than trying to access more memory through banking tricks, the drivers switched the processor into protected mode when running the application program, and back to real mode when accessing MS-DOS services. This allowed programs to directly access all memory which was configured as extended memory. The use of expanded memory by applications diminished through the early 1990s, as DOS extenders became more prevalent. Details An expanded memory board being a hardware peripheral, it needed a software device driver, which exported its services. Such a device driver was called "expanded memory manager". Its name was variable; the previously mentioned boards used remm.sys (AST), ps2emm.sys (IBM), aemm.sys (AT&T) and emm.sys (Intel) respectively. Later, the expression became associated with software-only solutions requiring the 80386 processor, for example Quarterdeck's QEMM (see below). Expanded memory was a common term for several incompatible technology variants. The Expanded Memory Specification (EMS) was developed jointly by Lotus, Intel, and Microsoft, 3 Core Module so this specification was sometimes referred to as "LIM EMS". EEMS, a competing expanded memory management standard, was developed by AST Research, Quadram and Ashton-Tate. It allowed to also remap some or all of the lower 640 kB of memory, so that entire programs could be switched in and out of the extra RAM. The two standards were eventually combined as LIM EMS 4.0. Software emulations The first software expanded memory management (emulation) program was probably CEMM, available in November 1987 with Compaq DOS 3.31. A popular and well-featured commercial solution was Quarterdeck's QEMM. A contender was Qualitas' 386MAX. Functionality was later incorporated into MS-DOS 4.01 in 1989 and into DR-DOS 5.0 in 1990, as EMM386. Software expanded memory manager in general offered additional, but closely related functionality. Notably, they could create ordinary memory areas (Upper Memory Blocks) in the high 384 KiB of real mode address space and provided tools for loading small programs, typically TSRs inside ("loadhi" or "loadhigh"). Interaction between extended memory, expanded memory emulation and DOS extenders ended up being regulated by the XMS, VCPI and DPMI specifications. Certain emulation programs did not rely on motherboard or 80386 features at all. Instead, they reserved 64 KiB of the base RAM for the expanded memory window, where they copied data to and from extended memory or hard disk when application programs requested page switches. This was programmatically easy to implement but performance was low. This technique was offered by AboveDisk from Above Software and by several shareware programs. Upper Memory Area The Upper Memory Area (UMA) is a feature of the design of IBM PC-compatible x86 computers. It is the feature that creates the 640K barrier. IBM reserved the uppermost region of the PC memory map for ROM, RAM on peripherals and memory-mapped input/output (I/O). This region is called the UMA and lies above Conventional memory, between 640 KiB and the 1 MB maximum addressable limit of the original PC's 8088 CPU. For example, the monochrome video memory area runs from &A000 to &A7FF. However, even with video RAM, the ROM BIOS and I/O ports for expansion cards, much of this 384 KiB of address space was unused - even when a 64 KiB window was reserved for the Expanded Memory Specification "frame" address into which EMS RAM was bank-switched. For example, on most PCs, all or most of the area from &C800 to &EFFF is normally unused. Usage in PC operating systems The next stage in the evolution of DOS was for the OS itself to become aware of UMBs and the High Memory Area. This occurred with the release of DR-DOS 5.0 in 1990. DR-DOS' built-in memory manager, EMM386.EXE, could perform most of the basic functionality of QEMM and comparable programs. 4 Core Module Where DR-DOS scored over the combination of an older DOS plus QEMM was that the DRDOS kernel itself and almost all of its data structures could be loaded into high memory, plus all of its associated components into UMBs. This left virtually all the base memory free, allowing configurations with up to 620K out of 640K free. Configuration was not automatic - free UMBs had to be identified by hand, manually included in the line that loaded EMM386 from CONFIG.SYS, and then drivers and so on had to be manually loaded into UMBs from CONFIG.SYS and AUTOEXEC.BAT. This configuration was not a trivial process. As it was largely automated by the installation program of QEMM, this program survived on the market; indeed, it worked well with DR-DOS' own HMA and UMB support and went on to be one of the best-selling utilities for the PC. This functionality was copied by Microsoft with the release of MS-DOS 5.0 in June 1991. Eventually, even more DOS data structures were moved out of conventional memory, allowing up to 635K out of 640K to be left free. For a period in the early 1990s, manual optimisation of the DOS memory map became a highlyprized skill, allowing for the largest applications to run on even the most complex PC configurations. The technique was to first create as many UMBs as possible, including remapping allocated but unnecessary blocks of memory, such as the monochrome display area on colour machines. Then, DOS' many subcomponents had to be loaded into these UMBs in just the correct sequence as to use the blocks of memory as efficiently as possible, allowing for the fact that some TSR programs required additional memory while loading which was freed up again once loading was complete. Fortunately there were few dependencies amongst these modules, so it was possible to load them in almost any sequence. Exceptions were that to successfully cache CD-ROMs, most disk caches had to be loaded after any CD-ROM drivers, and that the modules of most network stacks had to be loaded in a certain sequence, essentially working progressively up through the layers of the OSI model. (It is perhaps interesting to note that conceptually similar lines of enquiry are today being followed in efforts to make modern multitasking OSs boot faster. See the External Links section for more.) With the addition of a DOS multitasker such as Quarterdeck's DESQview, multiple sessions could be started at once, each with 600-odd K of free memory and all sharing access to DOS and its associated drivers and facilities. The increasing popularity of Windows 3.0 made this less relevant, as Windows applications were not affected by DOS' base memory limits, but DOS programs running under Windows (with Windows itself acting as a multitasking manager) were still thus constrained. With the release of Windows 95, it became less relevant still, as this version of Windows provides much of the functionality of the DOS device drivers to DOS applications running under Windows, such as CD, network and sound support; the memory map of Win95 DOS boxes was automatically optimised. However, not all DOS programs could execute in this environment. Specifically, programs that tried to directly switch from real mode to protected mode, wouldn't work as this wasn't allowed in the virtual 8086 mode it was running in (actually, this point is now being addressed by upcoming virtualization technologies such as Vanderpool and Pacifica for the x86 CPUs). Also, programs that tried making the switch using VCPI API (which was introduced to allow DOS programs that needed protected mode to enter it from the virtual 8086 mode set up by a memory manager, as described above) didn't work in Windows 95. Only the DPMI API for switching to protected mode was supported. 5 Core Module Upper Memory on the IBM XT On IBM XT computers, it was possible to add more memory to the motherboard and use a custom address decoder PROM to make it appear in the upper memory area [1]. As with the 386based upper memory described above, the extra RAM could be used to load TSR files, or as a RAM disk. x86 PC systems which did not have the UMA The existence of the Upper Memory Area and thus the 640 KiB barrier are artifacts of the design of the IBM PC and thus any computer compatible with it - in other words, all IBM PC Compatible systems. However, there have been many other computers based on Intel or other x86 processors which were not compatible with the PC and thus did not have an upper memory area and no 640 KiB barrier. For more information, see the article on Non-PC compatible x86 computers. High Memory Area The High Memory Area (HMA) is the RAM area consisting of the first 64 kilobytes (KB), minus 16 bytes, of the extended memory on an IBM PC or compatible microcomputer. By a strange design glitch the Intel 80286 and subsequent processors can actually address 17×64 KB minus 16 bytes of memory (from 0000:0000 to FFFF:FFFF (equivalent to the memory address FFFF0 + FFFF = 10FFEF), written in PC memory segment notation with hexadecimal numbers) in real mode. In the Intel 8086 and Intel 8088 processors, unable to handle more than 1 megabyte of memory, addressing wrapped around, that is, address FFFF:0010 was equivalent to 0000:0000. In order to allow running existing MS-DOS programs which relied on this feature on their newer IBM PC AT computers, IBM added special circuitry on the motherboard to simulate the wrapping around. This circuit was a simple logic gate which could disconnect the microprocessor's addressing line A20 from the rest of the motherboard. This gate could be controlled, initially through the keyboard controller, to allow running programs which wanted to access the entire RAM. So-called A20 handlers could control the addressing mode dynamically, thereby allowing programs to load themselves into the 1024–1088 KB region and run in real mode. The first user of the HMA among Microsoft products was Windows/286 2.1 in 1988, which introduced the HIMEM.SYS device driver. Starting with versions 5.0 of DR-DOS (1990) and of MS-DOS (1991), parts of the operating system could be loaded into HMA as well, freeing up to 46 KB of conventional memory. Other components, such as device drivers and TSRs, could be loaded into the Upper Memory Area. BIOS 6 Core Module Phoenix AwardBIOS on a standard PC BIOS, in computing, stands for Basic Input/Output System or Basic Integrated Operating System. BIOS refers to the software code run by a computer when first powered on. The primary function of BIOS is to prepare the machine so other software programs stored on various media (such as hard drives, floppies, and CDs) can load, execute, and assume control of the computer. This process is known as booting up. BIOS can also be said to be a coded program embedded on a chip that recognises and controls various devices that make up the computer. The term BIOS is specific to personal computer vendors. Among other classes of computers, the generic terms boot monitor, boot loader or boot ROM are commonly used. While the name BIOS is an acronym, it may also be a play on the Greek word βιος (bios), meaning life. The term first appeared in the CP/M operating system, describing the part of CP/M loaded during boot time that interfaced directly with the hardware (CP/M machines usually had a simple boot loader in ROM, and nothing else). Most versions of DOS have a file called "IBMBIO.COM" or "IO.SYS" that is analogous to the CP/M disk BIOS. How the BIOS boots The BIOS runs off the onboard PROM, EPROM or, most commonly, flash memory when the computer is powered on and it initializes and sometimes performs diagnostic tests on the hard drive, memory, video, chipset and other hardware. Subsequently, it typically decompresses itself from the BIOS memory space into the system main memory and starts executing from there. Nearly all BIOS implementations can optionally execute a setup program interfacing the nonvolatile BIOS memory (CMOS). This memory holds user-customizable configuration data (time, date, hard drive details, etc.) accessed by BIOS code. The 80x86 source code for early PC and AT BIOS was included with the IBM Technical Reference Manual. In most modern BIOS implementations, users select which device boots first: CD, hard disk, floppy disk, flash keydrive, and the like. This is particularly useful for installing operating systems or booting to Live CDs, and for selecting the order of testing for the presence of bootable media. Some BIOSes allow the user to select the operating system to load (e.g. load another OS from the second hard disk), though this is more often handled by a second-stage boot loader. 7 Core Module BIOS as firmware ROM with BIOS BIOS is sometimes called firmware because it is an integral part of the system hardware. Before 1990 or so BIOSes were held on ROM chips that could not be altered. As their complexity and the need for updates grew, BIOS firmware was stored on EEPROM or flash memory devices that can be easily upgraded by the user. This EEPROM chip sits on a FWH interface, but a newer interface named SPI is also emerging and in some newer boards EEPROM chips are already sitting on an SPI interface. However, an improperly executed or aborted BIOS update can render the computer or device unusable. To avoid BIOS corruption, some new motherboards have a backup BIOS ("Dual BIOS" boards). Also, most BIOSes have a "boot block" which is a portion of the ROM that runs first and is not updateable. This code will verify that the rest of the BIOS is intact (via checksum, hash, etc.) before jumping to it. If the boot block detects that the main BIOS is corrupt, then it will typically boot to a floppy so that the user can try flashing again, hopefully with a better image. Hardware manufacturers frequently issue BIOS updates to upgrade their products and remove bugs. The BIOS boot specification If the expansion ROM wishes to change the way the system boots (such as from a network device or a SCSI adapter for which the BIOS has no driver code), it can use the BIOS Boot Specification (BBS) API to register its ability to do so. Once the expansion ROMs have registered using the BBS APIs, the user can select among the available boot options from within the BIOS's user interface. This is why most BBS compliant PC BIOS implementations will not allow the user to enter the BIOS's user interface until the expansion ROMs have finished executing and registering themselves with the BBS API... The Fall and Rise of the BIOS Older operating systems such as DOS called on the BIOS to carry out most input-output tasks within the PC; with the introduction of newer operating systems such as Microsoft Windows and Linux, the BIOS was relegated to principally providing initial hardware setup, and bootstrapping. Once it was up and running, the operating system didn't have to rely on the BIOS for much. In recent years, however, by way of systems such as ACPI, the BIOS has taken on more complex functions such as aspects of power management, hotplug, thermal management etc. This has led to renewed reliance on the BIOS by operating system producers, and an increase in complexity in the BIOS code. Read-only memory 8 Core Module An EPROM. The small quartz window admits ultraviolet light during erasure. Read-only memory (ROM) is a class of storage media used in computers and other electronic devices. Because it cannot (easily) be written to, its main uses lie in the distribution of firmware (software that is very closely related to hardware, and not likely to need frequent upgrading). Modern semiconductor ROMs typically take the shape of IC packages, i.e. "computer chips", not immediately distinguishable from other chips like RAMs but for the text printed on the chips. "ROM" in its strictest sense can only be read from, but all ROMs allow data to be written into them at least once, either during initial manufacturing or during a step called "programming". Some ROMs can be erased and re-programmed multiple times, although they are still referred to as "read only" because the reprogramming process involves relatively infrequent, complete erasure and reprogramming, not the frequent, bit- or word at a time updating that is possible with RAM (random access memory). Types of ROMs Semiconductor based Classic mask-programmed ROM chips are written to during production and cannot change content afterwards. But there are other types of non-volatile solid-state memory: PROMs (Programmable Read-Only Memory) can be written to (programmed) via a special device, a PROM programmer. The writing often takes the form of permanently destroying or creating internal links (fuses or antifuses) with the result that a PROM can only be programmed once. EPROMs (Erasable Programmable Read-Only Memory) can be erased by exposure to ultraviolet light then rewritten via an EPROM programmer. Repeated exposure to ultraviolet light will eventually destroy the EPROM but it generally takes many (greater than 1000) exposures before the EPROM becomes unusable. EPROMs can be easily identified by the circular 'window' in the top which allows the UV light to enter. Once programmed, this window is typically covered by a label to prevent accidental erasure. EAROMs (Electrically Alterable Read-Only Memory) can be modified a bit at a time, but writing is intended to be an infrequent operation; most of the time the memory is used as a ROM. EAROM may be used to store critical system setup information in a non-volatile way. For many applications, EAROM has been supplanted by CMOS RAM backed-up by a lithium battery. EEPROM such as Flash memory (Electrically Erasable Programmable Read-Only Memory) allow the entire ROM (or selected banks of the ROM) to be electrically erased (flashed back to zero) then written to without taking them out of the computer (camera, MP3 player, etc.). Flashing is much slower (milliseconds) than writing to RAM (nanoseconds) (or reading from any ROM). By applying write protection, read/write memory may be turned (temporarily) into readonly memory. 9 Core Module Other technologies There are also other types of non-volatile memory that are not solid-state chips: A CD-ROM is a kind of compact disc. A CD-ROM is Read Only, hence the name, while CD-R is Write-Once-Read-Many (analogous to a PROM), and CD-RW is Read/Write (analogous to an EEPROM). Diode matrix ROM, which was used in small amounts in many computers in the 1960s as well as keyboard encoders for terminals. This ROM was programmed by installing discrete semiconductor diodes at selected locations between a matrix of word line traces and bit line traces on a printed circuit board. Resistor, capacitor, or transformer matrix ROM was used in many computers until the 1970s. Like the diode matrix ROM, it was programmed by placing components at selected locations between a matrix of word lines and bit lines. The ENIAC Function Tables were resistor matrix ROM, programmed by manually setting rotary switches. Various models of the IBM System/360 and complex peripherial devices stored their microcode in either capacitor (called BCROS – Balanced Capacitor Read Only Storage on the 360/50 & 360/65 or CCROS – Card Capacitor Read Only Storage on the 360/30) or transformer (called TROS – Transformer Read Only Storage on the 360/40 and others) matrix ROM. Core rope was a form of transformer matrix ROM technology used where size and/or weight were critical. This was used in NASA/MIT's Apollo Spacecraft Computers, DEC's PDP-8 computers, and other places. This type of ROM was programmed by hand by weaving "word line wires" inside or outside of ferrite transformer cores. The perforated metal character mask ("stencil") in Charactron cathode ray tubes was used as ROM to shape a wide electron beam to form a selected character shape on the screen either for display or overlay on a video signal. Various mechanical devices have been used as ROM in early computing equipment. A machined metal plate was used this way in the dot matrix printers on the IBM 026 and IBM 029 key punchs. Speed of ROMs Reading speed Although this has varied over time, today, large RAMs can be read faster than most large ROMs. Therefore ROM content that is used often is sometimes copied to RAM and subsequently read from there (shadowed). Writing speed For those types of ROMs that can be written to or electrically altered, the writing speed is always much slower than the reading speed and it may require unusual voltages, the movement of jumper plugs to apply write-enable signals, and/or special lock/unlock command codes written to the EAROM/Flash ROM. EPROM/EEPROM/EAROM lifetime Because they are written by forcing electrons through a layer of electrical insulation onto a floating transistor gate, re-writeable ROMs will only withstand a limited number of write cycles 10 Core Module before the insulation is permanently damaged. In very old EAROMs, this damage could occur in as few as 1,000 write cycles. In modern Flash EEPROMs, the life may be in excess of 10,000 or even 100,000 cycles, but it is by no means infinite. It is partially for this reason (as well as their limited, more-expensive capacity) that Flash ROMs are unlikely to completely supplant magnetic disk drives in the near future. The reading life of a ROM is not limited by the number of cycles performed. The reading life of EPROMs, EAROMs, and EEPROMs may be limited by charge leakage from the floating gates of the storage transistors, especially at high temperatures or in high radiation environments. Masked ROMs or fused PROMs do not suffer from this effect; once a 1 or 0, always a 1 or 0 (although fuse re-growth was once a problem in early fused PROMs). ROM images The contents of video game console ROM cartridges can be extracted with special software, creating files known as "ROM images" for use in emulators. Very often, these ROM images contain copyrighted software and there exists a large scene involving the illegal distribution and trade of such software. In such circles, the term "ROM images" is sometimes shortened simply to "ROMs" or sometimes changed to "romz" to highlight the connection with "warez". The term, originally from a time when most console games were distributed on cartridges containing ROM chips, eventually became so popular that it was also applied to games distributed on CD-ROMs which is still correct, though straying somewhat from the original meaning, and even to floppy disks which is technically incorrect. The unauthorised copying/distribution of copyrighted software is a violation of copyright laws, however. CMOS Static CMOS Inverter Complementary-symmetry/metal-oxide semiconductor (CMOS) ("see-moss", IPA:['si.mɜs]), is a major class of integrated circuits. CMOS chips include microprocessor, microcontroller, static RAM, and other digital logic circuits. The words "complementary-symmetry" refer to the fact that the design uses symmetrical pairs of p-type and n-type MOSFET transistors for logic functions, only one of which is switched on at any time. Two important characteristics of CMOS devices are high noise immunity and low static power supply drain. Significant power is only drawn when its transistors are switching between on and off states; consequently, CMOS devices do not produce as much heat as other forms of logic such as TTL. CMOS also allows a high density of logic functions on a chip. 11 Core Module The phrase "metal-oxide-semiconductor" is a reference to the nature of the fabrication process originally used to build CMOS chips. That process created field effect transistors having a metal gate electrode placed on top of an oxide insulator, which in turn is on top of a semiconductor material. Instead of metal, today the gate electrodes are almost always made from a different material, polysilicon, but the name CMOS nevertheless continues to be used for the modern descendants of the original process. (See also MOSFET.) A chip with a large number of CMOS transistors packed tightly together is sometimes known as CHMOS (for "Complementary High-density metal-oxide-semiconductor"). The combination of MEMS sensors with digital signal processors on one single CMOS chip is sometimes known an CMOSens. Development history CMOS circuits were invented in 1963 by Frank Wanlass at Fairchild Semiconductor. The first CMOS integrated circuits were made by RCA in 1968 by a group led by Albert Medwin. Originally a low-power but slow alternative to TTL, CMOS found early adopters in the watch industry and in other fields where battery life was more important than speed. Some twenty-five years later, CMOS has become the predominant technology in digital integrated circuits. This is essentially because area occupation, operating speed, energy efficiency and manufacturing costs have benefited and continue to benefit from the geometric downsizing that comes with every new generation of semiconductor manufacturing processes. In addition, the simplicity and comparatively low power dissipation of CMOS circuits have allowed for integration densities not possible on the basis of bipolar junction transistors. Standard discrete CMOS logic functions were originally available only in the 4000 series of logic integrated circuits. Later many functions in the 7400 series began to be fabricated in CMOS, NMOS, BiCMOS or another variant. Early CMOS circuits were very susceptible to damage from electrostatic discharge (ESD). Subsequent generations were thus equipped with sophisticated protection circuitry that helps absorb electric charges with no damage to the fragile gate oxides and PN-junctions. Still, antistatic handling precautions for semiconductor devices continue to be followed to prevent excessive energies from building up. Manufacturers recommend using antistatic precautions when adding a memory module to a computer, for instance. On the other hand, early generations such as the 4000 series that used aluminum as a gate material were extremely tolerant of supply voltage variations and operated anywhere from 3 to 18 volts DC. For many years, CMOS logic was designed to operate from the then industrystandard of 5 V imposed by TTL. By 1990, lower power dissipation was usually more important than easy interfacing to TTL, and CMOS voltage supplies began to drop along with the geometric dimensions of the transistors. Lower voltage supplies not only saved power, but allowed thinner, higher performance gate insulators to be used. Some modern CMOS circuits operate from voltages below one volt. In the early fabrication processes, the gate electrode was made of aluminum. Later CMOS processes switched to polycrystalline silicon ("polysilicon"), which can better tolerate the high temperatures used to anneal the silicon after ion implantation. This means that the gate can be put on early in the process and then used directly as an implant mask producing a self aligned gate (gates that are not self aligned require overlap which increases device size and stray 12 Core Module capacitance). As of 2004 there is some research into using metal gates once again, but all commonly used processes have polysilicon gates. There is also a great deal of research going on to replace the silicon dioxide gate dielectric with a high-k dielectric material to combat increasing leakage currents. Power-on self-test Power-on self-test (POST) is the common term for a computer's, router's or printer's pre-boot sequence. Though the same basic sequence is present on all computer architectures, it may go by different names such as initial program load (IPL), booting, or bootstrapping. The term POST, however, has become popular in association with and as a result of the proliferation of the PC. It can be used as a noun when referring to the code that controls the pre-boot phase or when referring to the phase itself. It can also be used as a verb when referring to the code or the system as it progresses through the pre-boot phase. Alternatively this may be called "POSTing". General internal workings On the PC, the main duties of POST are handled by the BIOS, which may hand some of these duties to other programs designed to initialize very specific peripheral devices, notably for video and SCSI initialization. These other duty-specific programs are generally known collectively as option ROMs or individually as the video BIOS, SCSI BIOS, etc. The principal duties of the main BIOS during POST are as follows: verify the integrity of the BIOS code itself determine the reason POST is being executed find, size, and verify system main memory discover, initialize, and catalog all system buses and devices pass control to other specialized BIOSes (if and when required) provide a user interface for systems configuration identify, organize, and select which devices are available for booting construct whatever system environment that is required by the target OS The BIOS will begin its POST duties when the CPU is reset. The first memory location the CPU tries to execute is known as the reset vector. In the case of a cold boot, the northbridge will direct this code fetch (request) to the BIOS located on the system flash memory. For a warm boot, the BIOS will be located in the proper place in RAM and the northbridge will direct the reset vector call to the RAM. During the POST flow of a contemporary BIOS, one of the first things a BIOS should do is determine the reason it is executing. For a cold boot, for example, it may need to execute all of its functionality. If, however, the system supports power savings or quick boot methods, the BIOS may be able to circumvent the standard POST device discovery, and simply program the devices from a preloaded system device table. The POST flow for the PC has developed from a very simple, straightforward process to one that is complex and convoluted. During POST, the BIOS must integrate a plethora of competing, evolving, and even mutually exclusive standards and initiatives for the matrix of hardware and OSes the PC is expected to support. However, the average user still knows the POST and BIOS only through its simple visible memory test and setup screen. 13 Core Module Fundamental structure In the case of the IBM PC compatible machines, the main BIOS is divided into two basic sections. The POST section, or POST code, is responsible for the tasks mentioned above, and the environment POST constructs for the OS is known as the runtime code, the runtime BIOS, or the runtime footprint. Primarily these two divisions can be distinguished in that POST code should be flushed from memory before control is passed to the target OS while the runtime code remains resident in memory. This division may be a misleading oversimplification, however, as many Runtime functions are executed while the system is POSTing. Error reporting The original IBM BIOS reported errors detected during POST by outputting a number to a fixed I/O port address, 80. Using a logic analyzer or a dedicated POST card, an interface card that shows port 80 output on a small display, a technician could determine the origin of the problem. (Note that once an operating system is running on the computer, the code displayed by such a board is often meaningless, since some OSes, e.g. Linux, use port 80 for I/O timing operations.) In later years, BIOS vendors used a sequence of beeps from the motherboard-attached loudspeaker to signal error codes. Original IBM POST error codes 1 short beep - Normal POST - system is OK 2 short beeps - POST error - error code shown on screen No beep - Power supply or system board problem Continuous beep - Power supply, system board, or keyboard problem Repeating short beeps - Power supply or system board problem 1 long, 1 short beep - System board problem 1 long, 2 short beeps - Display adapter problem (MDA, CGA) 1 long, 3 short beeps - Enhanced Graphics Adapter (EGA) 3 long beeps - 3270 keyboard card POST AMI BIOS beep codes 1 - Memory refresh timer error 2 - Parity error in base memory (first 64 KiB block) 3 - Base memory read/write test error 4 - Mother board timer not operational 5 - Processor error 6 - 8042 Gate A20 test error (cannot switch to protected mode) 7 - General exception error (processor exception interrupt error) 8 - Display memory error (system video adapter) 9 - AMI BIOS ROM checksum error 10 - CMOS shutdown register read/write error 11 - Cache memory test failed POST beep codes 14 Core Module Beeps Meaning Steady, short beep Power supply may be bad Long continuous beep tone Power supply bad or not plugged into motherboard correctly Steady, long beeps Power supply bad No beep Power supply bad, system not plugged in, or power not turned on One long, two short beeps Video card failure IBM POST diagnostic code descriptions 100 to 199 - System board 200 to 299 - Memory 300 to 399 - Keyboard 400 to 499 - Monochrome display 500 to 599 - Color/graphics display 600 to 699 - Floppy-disk drive or adapter 700 to 799 - Math coprocessor 900 to 999 - Parallel printer port 1000 to 1099 - Alternate printer adapter 1100 to 1299 - Asynchronous communication device, adapter, or port 1300 to 1399 - Game port 1400 to 1499 - Color/graphics printer 1500 to 1599 - Synchronous communication device, adapter, or port 1700 to 1799 - Hard drive and/or adapter 1800 to 1899 - Expansion unit (XT) 2000 to 2199 - Bisynchronous communication adapter 2400 to 2599 - EGA system-board video (MCA) 3000 to 3199 - LAN adapter 4800 to 4999 - Internal modem 7000 to 7099 - Phoenix BIOS chips 7300 to 7399 - 3.5-inch disk drive 8900 to 8999 - MIDI adapter 11200 to 11299 - SCSI adapter 21000 to 21099 - SCSI fixed disk and controller 21500 to 21599 - SCSI CD-ROM system Booting 15 Core Module An Internet payphone loading Windows XP In computing, booting is a bootstrapping process that starts operating systems when the user turns on a computer system. A boot sequence is the set of operations the computer performs when it is switched on that load an operating system. Boot loader Most computer systems can only execute code found in the memory (ROM or RAM); modern operating systems are mostly stored on hard disks (occasionally LiveCDs, USB flash drives, and the like). Just after a computer has been turned on, it doesn't have an operating system in memory. The computer's hardware alone cannot perform the complex actions of which an operating system is capable, such as loading a program from disk; so a seemingly irresolvable paradox is created: to load the operating system into memory, one appears to need to have an operating system already loaded. The solution to the paradox involves using a special small program, called a bootstrap loader or boot loader. This program doesn't have the full functionality of an operating system, but is tailormade to load enough other software for the operating system to start. Often, multiple-stage boot loaders are used, in which several small programs summon each other, until the last of them loads the operating system. The name bootstrap loader comes from the image of one pulling oneself up by one's bootstraps (see bootstrapping). Early programmable computers had toggle switches on the front panel to allow the operator to place the bootloader into the program store before starting the CPU. This would then read the operating system in from an outside storage medium such as paper tape, punched card, or an old fixed head disk drive. Pseudo-assembly code for the bootloader might be as simple as the following eight instructions: 0: 1: 2: 3: 4: 5: 6: 7: set the P register to 8 check paper tape reader ready if not ready, jump to 1 read a byte from paper tape reader to accumulator if end of tape, jump to 8 store accumulator to address in P register increment the P register jump to 1 A related example is based on a loader for a 1970's Nicolet Instrument Corporation minicomputer. Note that the bytes of the second-stage loader are read from paper tape in reverse order. 0: set the P register to 106 16 Core Module 1: 2: 3: 4: 5: 6: check paper tape reader ready if not ready, jump to 1 read a byte from paper tape reader to accumulator store accumulator to address in P register decrement the P register jump to 1 The length of the second stage loader is such that the final byte overwrites location 6. After the instruction in location 5 executes, location 6 starts the second stage loader executing. The second stage loader then waits for the much longer tape containing the operating system to be placed in the tape reader. The difference between the boot loader and second stage loader is the addition of checking code to trap paper tape read errors, a frequent occurrence with the hardware of the time, which in this case was an ASR-33 teletype. In modern computers the bootstrapping process begins with the CPU executing software contained in ROM (for example, the BIOS of an IBM PC) at a predefined address (the CPU is designed to execute this software after reset without outside help). This software contains rudimentary functionality to search for devices eligible to participate in booting, and load a small program from a special section (most commonly the boot sector) of the most promising device. Boot loaders may face peculiar constraints, especially in size; for instance, on the IBM PC and compatibles, the first stage of boot loaders must fit into the first 446 bytes of the Master Boot Record, in order to leave room for the 64-byte partition table and the 2-byte AA55h 'signature', which the BIOS requires for a proper boot loader. Some operating systems, most notably pre-1995 Macintosh systems from Apple Computer, are so closely interwoven with their hardware that it is impossible to natively boot an operating system other than the standard one. A common solution in such situations is to design a bootloader that works as a program belonging to the standard OS that hijacks the system and loads the alternative OS. This technique was used by Apple for its A/UX Unix implementation and copied by various freeware operating systems and BeOS Personal Edition 5. Second-stage boot loader NTLDR – A second stage boot loader The small program is most often not itself an operating system, but only a second-stage boot loader, such as NTLDR, LILO or GRUB. It will then be able to load the operating system proper, and finally transfer execution to it. The system will initialize itself, and may load device drivers and other programs that are needed for the normal operation of the OS. 17 Core Module The boot process is considered complete when the computer is ready to interact with the user or the operating system is capable of running ordinary applications. Typical modern PCs boot in about a minute (of which about 15 seconds are taken by the preliminary boot loaders, and the rest by loading the operating system), while large servers may take several minutes to boot and to start all services - to ensure high availability, they bring up some services before others. Most embedded systems must boot almost instantly -- for instance, waiting a minute for the television to come up is not acceptable. Therefore they have their whole operating system in ROM or flash memory, so it can be executed directly. BIOS boot devices A boot device is any device that must be initialized prior to loading the operating system. This includes the primary input device (keyboard), the primary output device (display), and the initial program load device (floppy drive, hard drive, CD-ROM, USB flash drive, etc.). (An IPL device is any device in the system that can boot and load an operating system, a stand alone utility (i.e. memtest86+) or even a boot loader; in old AT machines, this is the floppy drive or hard drive.) In a modern BIOS, the user can select one of several interfaces from which to boot. These include: hard disk, floppy, SCSI, CDROM, Zip, LS-120, a network interface card using PXE, or USB (USB-FDD, USB-ZIP, USB-CDROM, USB-HDD). For example, one can install Microsoft Windows on the first hard disk and Linux on the second. By changing the BIOS boot device, the user can select the operating system to load. Boot sequence on standard PC (IBM-PC compatible) A PC going through its boot sequence Upon starting, a personal computer's x86 CPU runs the instruction located at the memory location F000:FF00 (on 286s and 386SXs, the base of the code segment is actually 0xFF0000 and on 386s it is 0xFFFF0000) of the BIOS. This memory location is close to the end of system memory. It contains a jump instruction that transfers execution to the location of the BIOS startup program. This program runs a Power-On Self Test (POST) to check that devices the computer will rely on are functioning; it also initializes these devices. Then, the BIOS goes through a preconfigured list of devices until it finds one that is bootable. If it finds no such device, an error is given and the boot process stops. If the BIOS finds a bootable device, it loads and executes its 18 Core Module boot sector. In the case of a hard drive, this is referred to as the master boot record (MBR) and is often not operating system specific. Usually, the MBR code checks the partition table for an active partition. If one is found, the MBR code loads that partition's boot sector and executes it. The boot sector is often operating system specific, however in most operating systems its main function is to load and execute a kernel, which continues startup. If there is no active partition or the active partition's boot sector is invalid, the MBR may load a secondary boot loader and pass control to it and this secondary boot loader will select a partition (often via user input) and load its boot sector, which usually loads the corresponding operating system Kernel. Other kinds of boot sequence Some other processors have other kinds of boot modes; most digital signal processors have the following boot modes: Serial mode boot Parallel mode boot HPI boot Warm boot or soft reboot (as opposed to hard reboot) refers to an abridged start up which does not require that power be removed and reapplied. Random reboot Random reboot is a non-technical term referring to an unintended (and most likely: undesired) reboot for which the cause is not immediately evident to the user. Such reboots may occur due to a multitude of software and / or hardware problems. Computer bus In computer architecture, a bus is a subsystem that transfers data or power between computer components inside a computer or between computers and typically controlled by device driver software. Unlike a point-to-point connection, a bus can logically connect several peripherals over the same set of wires. Each bus defines its set of connectors to physically plug devices, cards or cables together. Early computer buses were literally parallel electrical buses with multiple connections, but the term is now used for any physical arrangement that provides the same logical functionality as a parallel electrical bus. Modern computer buses can use both parallel and bit-serial connections, and can be wired in either a multidrop (electrical parallel) or daisy chain topology, or connected by switched hubs, as in the case of USB. Address bus An address bus is (part of) a computer bus, used by CPUs or DMA-capable units for communicating the physical addresses of computer memory elements/locations that the requesting unit wants to access (read/write). The width of an address bus, along with the size of addressable memory elements, determines how much memory can be accessed. For example, a 16-bit wide address bus (commonly used in 19 Core Module the 8-bit processors of the 1970s and early 1980s) reaches across 2 to the power of 16 = 65,536 = 64K memory locations, whereas a 32-bit address bus (common in today's PC processors) can address 4,294,967,296 = 4G locations. In most microcomputers the addressable elements are 8-bit bytes (so a "K" in that case is equal to a "KB", i.e. a kilobyte), while there are also many examples of computers with larger "chunks" of data as their minimum physically addressable elements, notably mainframes, supercomputers, and some workstation CPUs. RS-232 In telecommunications, RS-232 is a standard for serial binary data interconnection between a DTE (Data terminal equipment) and a DCE (Data communication equipment). It is commonly used in computer serial ports. A similar ITU-T standard is V.24. RS is an abbreviation for "Recommended Standard". Scope of the standard The Electronic Industries Alliance (EIA) standard RS-232-C as of 1969 defines: Electrical signal characteristics such as voltage levels, signaling rate, timing and slewrate of signals, voltage withstand level, short-circuit behavior, maximum stray capacitance and cable length Interface mechanical characteristics, pluggable connectors and pin identification Functions of each circuit in the interface connector Standard subsets of interface circuits for selected telecom applications The standard does not define such elements as character encoding (for example, ASCII, Baudot or EBCDIC), or the framing of characters in the data stream (bits per character, start/stop bits, parity). The standard does not define bit rates for transmission, although the standard says it is intended for bit rates less than 20,000 bits per second. Many modern devices can exceed this speed (38,400 and 57,600 bit/s being common, and 115,200 and 230,400 bit/s making occasional appearances) while still using RS-232 compatible signal levels. History This standard originally specified the connection between an electromechanical teletypewriter and a modem. When electronic terminals (smart and dumb) began to be used, they were often designed to be interchangeable with teletypes, and so supported RS-232. The C revision of the standard was issued in 1969 in part to accommodate the electrical characteristics of these devices. Since application to such devices as computers, printers, digitizer tables, test instruments, and so on were not envisioned in the standard, designers implementing an RS-232 compatible interface on their equipment often interpreted the requirements idiosyncratically . Common problems were non-standard pin assignment of circuits on connectors, and incorrect or missing control signals. The lack of adherence to the standards produced a thriving industry of breakout boxes, patch boxes, test equipment, books, and other aids for the connection of disparate equipment. 20 Core Module Later personal computers (and other devices) started to make use of the standard so that they could connect to existing equipment. For many years, a RS-232-compatible port was a standard feature for serial communications, such as modem connections, on many computers. It remained in widespread use into the late 1990s, and while it has largely been supplanted by other interface standards in computer products, it is still used to connect legacy peripherals, industrial equipment (such as based on PLCs), and console ports. The standard has been renamed several times during its history as the sponsoring organization changed its name, and has been variously known as EIA RS 232, EIA 232, and most recently as TIA 232. The standard continues to be revised and updated by the EIA and since 1988 the Telecommunications Industry Association (TIA[2]). Revision C was issued in a document dated August 1969. Revision D was issued in 1986. The current revision is TIA-232-F Interface Between Data Terminal Equipment and Data Circuit-Terminating Equipment Employing Serial Binary Data Interchange, issued in 1997. Changes since Revision C have been in timing and details intended to improve harmonization with the CCITT standard V.24, but equipment built to the current standard will interoperate with older versions. Limitations of the standard Because the application of RS-232 has extended far beyond the original purpose of interconnecting a terminal with a modem, successor standards have been developed to address the limitations. Issues with the RS-232 standard include: The large voltage swings and requirement for positive and negative supplies increases power consumption of the interface and complicates power supply design. The voltage swing requirement also limits the upper speed of a compatible interface. Single-ended signalling referred to a common signal ground limit the noise immunity and transmission distance. Multi-drop (meaning a connection between more than two devices) operation of an RS232 compatible interface is not defined; while multi-drop "work-arounds" have been devised, they have limitations in speed and compatibility. Asymmetrical definitions of the two ends of the link make the assignment of the role of a newly developed device problematical; the designer must decide on either a DTE-like or DCE-like interface and which connector pin assignments to use. The handshaking and control lines of the interface are intended for the setup and takedown of a dial-up communication circuit; in particular, the use of handshake lines for flow control is not reliably implemented in many devices. While the standard recommends a connector and pinout, the connector is large by current standards. Role in modern computing In the book "PC 97 Hardware Design Guide" [1], Microsoft deprecated support for the RS-232 compatible serial port of the original IBM PC design. Today, RS-232 is very gradually being superseded in personal computers by USB for local communications. Compared with RS-232, USB is faster, has lower voltage levels, and has connectors that are simpler to connect and use. Both protocols have software support in popular operating systems. USB is designed to make it easy for device drivers to communicate with hardware, and there is no direct analog to the terminal programs used to let users communicate directly with serial ports. However, USB is a more complex standard, requiring more software to support the protocol used. Serial ports of 21 Core Module personal computers were also often used to directly control various hardware devices, such as relays or lamps, since the control lines of the interface could be easily manipulated by software. This isn't feasible with USB which requires some form of receiver to decode the serial data. Many personal computers intended for office use ship with "legacy-free" motherboards without any RS-232 serial ports. However, RS-232 is still quite common in point-of-sale (cash drawers, barcode and magnetic stripe readers), amateur electronics and industrial measurement and remote-control devices, so computers made for such applications are still equipped with RS-232 ports. RS-232 was standard for so long that the circuits needed to control a serial port became very cheap and often exist on a single small microchip, sometimes together with circuitry for a parallel port. Many motherboards and desktop systems provide these ports even though they may not be used, simply because it costs the manufacturer very little to include them. Small-formfactor systems and laptops, however, often do not include them in order to conserve space. As an alternative, USB docking ports are available which can provide connectors for a keyboard, mouse, one or more serial ports, and one or more parallel ports. Corresponding device drivers are required for each USB-connected device to allow programs to access these USB-connected devices as if they were the original directly-connected peripherals. Network equipment such as manageable switches and routers usually have an RS-232 port to be used for configuration of the device. It's a problem for some network administrators that most new laptops don't have an RS-232 port (though one can of course use a USB-to-serial dongle). It is also possible to connect RS-232 devices via ethernet and WLAN device drivers, that act as network servers. Some manufacturers even have virtual serial port drivers available Standard details In RS-232, data is sent as a time-series of bits. Both synchronous and asynchronous transmissions are supported by the standard. Each circuit only operates in one direction, that is, signalling from a DTE to the attached DCE or the reverse. Since transmit data and receive data are separate circuits, the interface can operate in a full duplex manner, supporting concurrent data flow in both directions. The standard does not define character framing within the data stream, or character encoding. The most common arrangement, nearly universal in personal computers, is an asynchronous link sending seven or eight bits. When used in this way, the bit order consists of a start bit, seven or eight data bits sent least significant bit first, an optional parity bit, and a stop bit. The steady state of the line is called the Marking state. The start of a new character is signaled by a change to the Space state. The digital ones and zeros are then transmitted serially onto the line by switching between the Mark and Space state ending with a final stop bit which is a transition back to the Marking state. Mechanical teleprinters often required extra time to ready themselves for the next character, so many systems could be arranged to send two stop bits. Historically, teleprinter and related devices used ASCII in the US, or various character codes elsewhere. Some very old teleprinters and Telex systems use Baudot code. 22 Core Module Voltage levels The RS-232 standard defines the voltage levels that correspond to logical one and logical zero levels. Signals are plus or minus 3 to 15 volts. The range near zero volts is not a valid RS-232 level; logic one is defined as a negative voltage, the signal condition is called marking, and has the functional significance of OFF. Logic zero is positive, the signal condition is spacing, and has the function ON. The standard specifies a maximum open-circuit voltage of 25 volts; signal levels of ±5 V, ±10 V, ±12 V, and ±15 V are all commonly seen depending on the power supplies available within a device. Circuits driving an RS-232-compatible interface must be able to withstand indefinite short circuit to ground or to any voltage level up to 25 volts. The slew rate, or how fast the signal changes between levels, is also controlled. Connectors RS-232 devices may be classified as Data Terminal Equipment (DTE) or Data Communications Equipment (DCE); this defines which wires will be sending and receiving each signal. The standard recommended but did not make mandatory the common D-subminiature 25 pin connector. In general, terminals have male connectors with DTE pin functions, and modems have female connectors with DCE pin functions. Other devices may have any combination of connector gender and pin definitions. Presence of a 25 pin D-sub connector does not necessarily indicate an RS-232C compliant interface. For example, on the original IBM PC, a male D-sub was an RS-232C DTE port (with a non-standard current loop interface on reserved pins), but the female D-sub connector was used for a parallel Centronics printer port. Some personal computers put non-standard voltages or signals on their serial ports. The standard specifies 20 different signal connections. Since most devices use only a few signals, smaller connectors can be used. For example, the 9 pin DE-9 connector was used by most IBM-compatible PCs since the IBM PC AT, and has been standardized as TIA-574. More recently, modular connectors have been used. Most common are 8 pin RJ-45 connectors. Standard EIA/TIA 561 specifies a pin assignment, but the "Yost Serial Device Wiring Standard" invented by Dave Yost is common on Unix computers and newer devices from Cisco Systems. Many devices don't use either of these standards. 10 pin RJ-50 connectors can be found on some devices as well. Digital Equipment Corporation defined their own DECconnect connection system which was based on the Modified Modular Jack connector. This is a 6 pin modular jack where the key is offset from the center position. As with the Yost standard, DECconnect uses a symmetrical pin layout which enables the direct connection between two DTEs. Pinouts (DTE relative) The following table lists the commonly used RS-232 signals and common pin assignments (see also RS-485 for different standard with the same connectors): Signal DB-25 DE-9 (TIA-574) EIA/TIA 561 Yost RJ-50 MMJ Common Ground 7 5 4 4,5 6 3,4 Transmitted Data (TD) 2 3 6 3 8 2 Received Data (RD) 3 2 5 6 9 5 4 3 2 7 1 Data Terminal Ready (DTR) 20 23 Core Module Data Set Ready (DSR) 6 6 1 7 5 6 Request To Send (RTS) 4 7 8 1 4 - Clear To Send (CTS) 5 8 7 8 3 - Carrier Detect (DCD) 8 1 2 7 10 - Ring Indicator (RI) 22 9 1 - 2 - The signals are labeled from the standpoint of the DTE device; TD, DTR, and RTS are generated by the DTE and RD, DSR, CTS, DCD, and RI are generated by the DCE. The ground signal is a common return for the other connections; it appears on two pins in the Yost standard but is the same signal. Connection of pin 1 (protective ground) and pin 7 (signal reference ground) is a common practice but not recommended. Use of a common ground is one weakness of RS-232. If the two pieces of equipment are far enough apart or on separate power systems, the ground will degrade between them and communications will fail; this is a difficult condition to trace. Note that EIA/TIA 561 combines DSR and RI, and the Yost standard combines DSR and DCD. Cables Since the standard definitions are not always correctly applied, it is often necessary to consult documentation, test connections with a breakout box, or use trial and error to find a cable that works when interconnecting two devices. Connecting a fully-standard-compliant DCE device and DTE device would use a cable that connects identical pin numbers in each connector (a socalled "straight cable"). "Gender changers" are available to solve gender mismatches between cables and connectors. Connecting devices with different types of connectors requires a cable that connects the corresponding pins according to the table above. Cables with 9 pins on one end and 25 on the other are common, and manufacturers of equipment with RJ-45 connectors usually provide a cable with either a DB-25 or DE-9 connector (or sometimes interchangeable connectors so they can work with multiple devices). Connecting two DTE devices together requires a null modem that acts as a DCE between the devices by swapping the corresponding signals (TD-RD, DTR-DSR, and RTS-CTS). This can be done with a separate device and two cables, or using a cable wired to do this. One feature of the Yost standard is that a null modem cable is a "rollover cable" that just reverses pins 1 through 8 on one end to 8 through 1 on the other end. For configuring and diagnosing problems with RS-232 cables, a "breakout box" may be used. This device normally has a female and male RS-232 connector and is meant to attach in-line; it then has lights for each pin and provisions for interconnecting pins in different configurations. RS-232 cables may be built with connectors commonly available at electronics stores. The cables may be between 3 and 25 pins; typically 4 or 6 wires are used. Flat RJ (phone-style) cables may be used with special RJ-RS232 connectors, which are the easiest to configure. The reason that a minimal two-way interface can be created with only 3 wires is that all the RS232 signals share a common ground return. The use of unbalanced circuits makes RS-232 susceptible to problems due to ground potential shifts between the two devices. RS-232 also has relatively poor control of signal rise and fall times, leading to potential crosstalk problems. RS232 was recommended for short connections (15 meters or less). RS-232 interface cables are not usually constructed with twisted pair because of the unbalanced circuits. 24 Core Module While the control lines of the RS 232 interface were originally intended for call setup and takedown, other "handshakes" may be required by one or the other device. These are used for flow control, for example, to prevent loss of data sent to a serial printer. For example, DTR is commonly used to indicate "device ready". Pins may also be "jumpered" or routed back within the connector. For example a pin saying "are you ready?" from device A might be wired to the pin saying "I'm ready" on device A if device B did not transmit such a signal. Common handshake pins are DTR, DSR, DCD, and RTS/CTS. Seldom used features The EIA-232 standard specifies connections for several features that are not used in most implementations. Their use requires the 25-pin connectors and cables, and of course both the DTE and DCE must support them. Signal rate selection The DTE or DCE can specify use of a "high" or "low" signaling rate. The rates as well as which device will select the rate must be configured in both the DTE and DCE. The prearranged device selects the high rate by setting pin 23 to ON. Loopback testing Many DCE devices have a loopback capability used for testing. When enabled, signals are echoed back to the sender rather than being sent on to the receiver. If supported, the DTE can signal the local DCE (the one it is connected to) to enter loopback mode by setting pin 18 to ON, or the remote DCE (the one the local DCE is connected to) to enter loopback mode by setting pin 21 to ON. The latter tests the communications link as well as both DCE's. When the DCE is in test mode it signals the DTE by setting pin 25 to ON. A commonly used version of loopback testing doesn't involve any special capability of either end. A hardware loopback is simply a wire connecting complementary pins together in the same connector. See loopback. Loopback testing is often performed with a specialized DTE called a Bit Error Rate Tester (BERT). Timing signals Some synchronous devices provide a clock signal to synchronize data transmission. The timing signals are provided by the DCE on pins 15 and 17. Pin 15 is the transmitter clock; the DTE puts the next bit on the data line (pin 2) when this clock transitions from OFF to ON (so it is stable during the ON to OFF transition when the DCE registers the bit). Pin 17 is the receiver clock; the DTE reads the next bit from the data line (pin 3) when this clock transitions from ON to OFF. Alternatively, the DTE can provide a clock signal on pin 24 for both transmitted and received data. Again, data is changed when the clock transitions from OFF to ON and read during the ON to OFF transition. Secondary channel 25 Core Module Data can be sent over a secondary channel (when implemented by the DTE and DCE devices), which is equivalent to the primary channel. Pin assignments are described in following table: Signal Pin Common Ground 7 (same as primary) Secondary Transmitted Data (STD) 14 Secondary Received Data (SRD) 16 Secondary Request To Send (SRTS) 19 Secondary Clear To Send (SCTS) 13 Secondary Carrier Detect (SDCD) 12 Related standards Other serial signalling standards may not interoperate with standard-compliant RS-232 ports. For example, using the TTL levels of +5 and 0 V puts the mark level in the undefined area of the standard. Such levels are sometimes used with NMEA-compliant GPS receivers and depth finders. 20 mA current loop uses the absence of 20 mA current for high, and the presence of current in the loop for low; this signaling method is often used for long-distance and optically isolated links. Connection of a current-loop device to a compliant RS-232 port requires a level translator; current-loop devices are capable of supplying voltages in excess of the withstand voltage limits of a compliant device. However, the original IBM XT serial port card implemented a 20 mA current-loop interface, which was never emulated by other suppliers of plug-compatible equipment. Other serial interfaces similar to RS-232: RS-422 (a high-speed system similar to RS-232 but with differential signalling) RS-423 (a high-speed system similar to RS-422 but with unbalanced signalling) RS-449 (a functional and mechanical interface that used RS-422 and RS-423 signals - it never caught on like RS-232 and was withdrawn by the EIA) RS-485 (a descendant of RS-422 that can be used as a bus in multidrop configurations) MIL-STD-188 (a system like RS-232 but with better impedance and rise time control) EIA-530 (a high-speed system using RS-422 or RS-423 electrical properties in an EIA232 pinout configuration, thus combining the best of both; supersedes RS-449) TIA-574 (standardizes the 9-pin D-subminiature connector pinout for use with EIA-232 electrical signalling, as originated on the IBM PC/AT) Ethernet Ethernet is a large and diverse family of frame-based computer networking technologies for local area networks (LANs). The name comes from the physical concept of the ether. It defines a number of wiring and signaling standards for the physical layer, two means of network access at the Media Access Control (MAC)/data link layer, and a common addressing format. 26 Core Module Ethernet has been standardized as IEEE 802.3. Its star-topology, twisted-pair wiring form became the most widespread LAN technology in use from the 1990s to the present, largely replacing competing LAN standards such as Coaxial-cable Ethernet, Token Ring, FDDI, and ARCNET. In recent years, WiFi, the wireless LAN standardized by IEEE 802.11, has been used instead of Ethernet in many installations. General description A 1990s Ethernet network interface card. This is a combo card that supports both coaxial-based 10BASE2 (BNC connector, left) and Twisted-pair-based 10BASE-T (RJ-45 connector, right). Ethernet was originally based on the idea of computers communicating over a shared coaxial cable acting as a broadcast transmission medium. The methods used show some similarities to radio systems (though there are major differences, like the fact that it is much easier to detect collisions in a cable broadcast system than a radio broadcast). The common cable providing the communication channel was likened to the ether and it was from this reference that the name 'Ethernet' was derived. From this early and comparatively simple concept Ethernet evolved into the complex networking technology that today powers the vast majority of local computer networks. The coaxial cable was later replaced with point-to-point links connected together by hubs and/or switches in order to reduce installation costs, increase reliability, and enable point-to-point management and troubleshooting. StarLAN was the first step in the evolution of Ethernet from a coaxial cable bus to a hub-managed, twisted pair network. The advent of twisted-pair wiring enabled Ethernet to become a commercial success. On top of the physical layer Ethernet stations communicate to each other by sending each other data packets, small blocks of data that are individually sent and delivered. As with other IEEE 802 LANs, each Ethernet station is given a single 48-bit MAC address, which is used both to specify the destination and the source of each data packet. Network interface cards (NICs) or chips normally do not accept packets addressed to other Ethernet stations. Adapters generally come programmed with a globally unique address but this can be overridden either to avoid an address change when an adapter is replaced or to use locally administered addresses. Despite the huge changes in Ethernet from a thick coaxial cable bus running at 10 Mbit/s to point-to-point links running at 1 Gbit/s and beyond, the different variants remain essentially the same from the programmer's point of view and are easily interconnected using readily available inexpensive hardware. This is because the frame format remains the same, even though network access procedures are radically different. Due to the ubiquity of Ethernet, the ever-decreasing cost of the hardware needed to support it and the reduced panel space needed by twisted pair Ethernet, most manufacturers now build the 27 Core Module functionality of an Ethernet card directly into PC motherboards obviating the need for installation of a separate network card. More advanced networks Simple switched Ethernet networks still suffer from a number of issues: They suffer from single points of failure; e.g., if one link or switch goes down in the wrong place the network ends up partitioned. It is possible to trick switches or hosts into sending data to your machine even if it's not intended for it, as indicated above. It is possible for any host to flood the network with broadcast traffic forming a denial of service attack against any hosts that run at the same or lower speed as the attacking device. They suffer from bandwidth choke points where a lot of traffic is forced down a single link. Some Managed switches offer a variety of tools to combat these issues including: spanning-tree protocol to maintain the active links of the network as a tree while allowing physical loops for redundancy. Various port protection features (as it is far more likely an attacker will be on an end system port than on a switch-switch link) VLANs to keep different classes of users separate while using the same physical infrastructure. fast routing at higher levels (to route between those VLANs). Link aggregation to add bandwidth to overloaded links and to provide some measure of redundancy, although the links won't protect against switch failure because they connect the same pair of switches. Varieties of Ethernet The first Ethernet networks, 10BASE5, used thick yellow cable with vampire taps as a shared medium (using CSMA/CD). Later, 10BASE2 Ethernet used thinner coaxial cable (with BNC connectors) as the shared CSMA/CD medium. The later StarLAN 1BASE5 and 10BASE-T used twisted pair connected to Ethernet hubs with RJ-45 connectors. Currently Ethernet has many varieties that vary both in speed and physical medium used. Perhaps the most common forms used are 10BASE-T, 100BASE-TX, and 1000BASE-T. All three utilize twisted pair cables and RJ-45 connectors. They run at 10 Mbit/s, 100 Mbit/s, and 1 Gbit/s, respectively. However each version has become steadily more selective about the cable it runs on and some installers have avoided 1000baseT for everything except short connections to servers. Fiber optic variants of Ethernet are commonly seen connecting buildings or network cabinets in different parts of a building but are rarely seen connected to end systems for cost reasons. Their advantages lie in performance (fiber versions of a new speed almost invariablly come out before copper), distance (up to tens of kilometers with some versions) and electrical isolation. 10gigabit Ethernet is becoming more popular in both enterprise and carrier networks, with discussions starting on 40G and 100G Ethernet. 28 Core Module Through Ethernet's history there have also been RF versions of Ethernet, both wireline and wireless. The currently recommended RF wireless networking standards, 802.11 and 802.16, are not based upon Ethernet. History Ethernet was originally developed as one of the many pioneering projects at Xerox PARC. A common story states that Ethernet was invented in 1973, when Robert Metcalfe wrote a memo to his bosses at PARC about Ethernet's potential. But Metcalfe claims Ethernet was actually invented over a period of several years. In 1976, Metcalfe and his assistant David Boggs published a paper titled Ethernet: Distributed Packet-Switching For Local Computer Networks. The experimental Ethernet described in that paper ran at 3 Mbit/s, and had 8-bit destination and source address fields, so Ethernet addresses weren't the global addresses they are today. By software convention, the 16 bits after the destination and source address fields were a packet type field, but, as the paper says, "different protocols use disjoint sets of packet types", so those were packet types within a given protocol, rather than the packet type in current Ethernet, which specifies the protocol being used. Metcalfe left Xerox in 1979 to promote the use of personal computers and local area networks (LANs), forming 3Com. He convinced DEC, Intel, and Xerox to work together to promote Ethernet as a standard, the so-called "DIX" standard, for "Digital/Intel/Xerox"; it standardized the 10 megabits/second Ethernet, with 48-bit destination and source addresses and a global 16-bit type field. The standard was first published on September 30, 1980. It competed with two largely proprietary systems, token ring and ARCNET, but those soon found themselves buried under a tidal wave of Ethernet products. In the process, 3Com became a major company. Metcalfe sometimes jokingly credits Jerry Saltzer for 3Com's success. Saltzer cowrote an influential paper suggesting that token-ring architectures were theoretically superior to Ethernetstyle technologies. This result, the story goes, left enough doubt in the minds of computer manufacturers that they decided not to make Ethernet a standard feature, which allowed 3Com to build a business around selling add-in Ethernet network cards. This also led to the saying "Ethernet works better in practice than in theory," which, though a joke, actually makes a valid technical point: the characteristics of typical traffic on actual networks differ from what had been expected before LANs became common in ways that favor the simple design of Ethernet. Add to this the real speed/cost advantage Ethernet products have continually enjoyed over other (Token, FDDI, ATM, etc.) LAN implementations and we see why today's result is that "connect the PC to the network" means connect it via Ethernet. Even when the PC is connected by Wi-Fi, nearly all Wi-Fi gear uses Ethernet for connecting to the rest of the network. Metcalfe and Saltzer worked on the same floor at MIT's Project MAC while Metcalfe was doing his Harvard dissertation, in which he worked out the theoretical foundations of Ethernet. Universal Serial Bus 29 Core Module The USB "trident" Icon The USB (Type A and B) Connectors A Male USB plug (Type A) Universal Serial Bus (USB) is a serial bus standard to interface devices. It was designed for computers such as PCs and the Apple Macintosh, but its popularity has prompted it to also become commonplace on video game consoles, PDAs, cellphones; and even devices such as televisions and home stereo equipment, and portable memory devices. The radio spectrum-based USB implementation is known as Wireless USB. Overview A USB system has an asymmetric design, consisting of a host controller and multiple daisychained devices. Additional USB hubs may be included in the chain, allowing branching into a tree structure, subject to a limit of 5 levels of branching per controller. No more than 127 devices, including the bus devices, may be connected to a single host controller. Modern computers often have several host controllers, allowing a very large number of USB devices to be connected. USB cables do not need to be terminated. Because of the capability of daisy-chaining USB devices, early USB announcements predicted that each USB device would include a USB port to allow for long chains of devices. In this model, computers would not need many USB ports, and computers shipped at this time typically had only two. However, for economical and technical reasons, daisy chaining never became widespread. To reduce the necessity of USB hubs, computers now come with a large number of USB ports, typically six. USB was designed to allow peripherals to be connected without the need to plug expansion cards into the computer's ISA, EISA, or PCI bus, and to improve plug-and-play capabilities by allowing devices to be hot-swapped (connected or disconnected without powering down or rebooting the computer). When a device is first connected, the host enumerates and recognises it, and loads the device driver it needs. 30 Core Module A USB hub USB can connect peripherals such as mice, keyboards, gamepads and joysticks, scanners, digital cameras, printers, external storage, networking components, etc. For many devices such as scanners and digital cameras, USB has become the standard connection method. USB is also used extensively to connect non-networked printers, replacing the parallel ports which were widely used; USB simplifies connecting several printers to one computer. As of 2004 there were about 1 billion USB devices in the world. As of 2005, the only large classes of peripherals that cannot use USB, because they need a higher data rate than USB can provide, are displays and monitors, and high-quality digital video components. Standardization The design of USB is standardized by the USB Implementers Forum (USB-IF), an industry standards body incorporating leading companies from the computer and electronics industries. Notable members have included Apple Computer, Hewlett-Packard, NEC, Microsoft, Intel, and Agere. The USB specification is at version 2.0 (with revisions) as of 2006. Hewlett-Packard, Intel, Lucent, Microsoft, NEC, and Philips jointly led the initiative to develop a higher data transfer rate than the 1.1 specification. The USB 2.0 specification was released in April 2000 and was standardized by the USB-IF at the end of 2001. Previous notable releases of the specification were 0.9, 1.0, and 1.1. Equipment conforming with any version of the standard will also work with devices designed to any of the previous specifications (backwards compatibility). Smaller USB plugs and receptacles, called Mini-A and Mini-B, are also available, as specified by the On-The-Go Supplement to the USB 2.0 Specification. The specification is at revision 1.0a (Jan 2006). Technical details PCB mounting female USB connectors USB connects several devices to a host controller through a chain of hubs. In USB terminology devices are referred to as functions, because in theory what we know as a device may actually host several functions, such as a router that is a Secure Digital Card reader at the same time. The 31 Core Module hubs are special purpose devices that are not officially considered functions. There always exists one hub known as the root hub, which is attached directly to the host controller. USB endpoints actually reside on the connected device: the channels to the host are referred to as pipes These devices/functions (and hubs) have associated pipes (logical channels) which are connections from the host controller to a logical entity on the device named an endpoint. The pipes are synonymous to byte streams such as in the pipelines of Unix, however the term endpoint is also (sloppily) used to mean the entire pipe, even in the standard USB documentation. These endpoints (and their respective pipes) are numbered 0-15 in each direction, so a device/function can have up to 32 active pipes, 16 inward and 16 outward. (The OUT direction shall be interpreted out of the host controller and the IN direction is into the host controller.) Each endpoint can transfer data in one direction only, either into or out of the device/function, so each pipe is uni-directional. Endpoint 0 is however reserved for the bus management in both directions and thus takes up two of the 32 endpoints — all USB devices are required to implement endpoint 0, so there is always an inward and an outward pipe numbered 0 on any given device. In these pipes, data is transferred in packets of varying length. Each pipe has a maximum packet length, typically 2n bytes, so a USB packet will often contain something on the order of 8, 16, 32, 64, 128, 256, 512 or 1024 bytes. The pipes are also divided into four different categories by way of their transfer type: control transfers - typically used for short, simple commands to the device, and a status response, used e.g. by the bus control pipe number 0 isochronous transfers - at some guaranteed speed (often but not necessarily as fast as possible) but with possible data loss, e.g. realtime audio or video interrupt transfers - devices that need guaranteed quick responses (bounded latency), e.g. pointing devices and keyboards bulk transfers - large sporadic transfers using all remaining available bandwidth (but with no guarantees on bandwidth or latency), e.g. file transfers When a device (function) or hub is attached to the host controller through any hub on the bus, it is given a unique 7 bit address on the bus by the host controller. 32 Core Module USB Enumeration Trace The host controller then polls the bus for traffic, usually in a round-robin fashion, so no device can transfer any data on the bus without explicit request from the host controller. The interrupt transfers on corresponding endpoints does not actually interrupt any traffic on the bus, they are just scheduled to be queried more often and in between any other large transfers, thus "interrupt traffic" on a USB bus is really only high-priority traffic. USB device descriptors are hierarchical and quite complex. This UML diagram tries to give an entity relation between the different descriptors: the lower left device descriptor is highest in the hierarchy, this has configuration descriptors, which have interface descriptors, which have interface settings which in turn hold the actual endpoints. To access an endpoint, a hierarchical configuration must be obtained. The device connected to the bus has one (and only one) device descriptor which in turn has one or more configuration descriptors. These configurations often correspond to states, e.g. active vs. low power mode. Each configuration descriptor in turn has one or more interface descriptors, which describe certain aspects of the device, so that it may be used for different purposes: for example, a camera may have both audio and video interfaces. These interface descriptors in turn have one default interface setting and possibly more alternate interface settings which in turn have endpoint descriptors, as outlined above. An endpoint may however be reused among several interfaces and alternate interface settings. The hardware that contains the host controller and the root hub has an interface toward the programmer which is called Host Controller Device (HCD) and is defined by the hardware implementer. In practice, these are hardware registers (ports) in the computer. At version 1.0 and 1.1 there were two competing HCD implementations. Compaq's Open Host Controller Interface (OHCI) was adopted as the standard by the USB-IF. However, Intel subsequently created a specification they called the Universal Host Controller Interface (UHCI) and insisted other implementers pay to license and implement UHCI. VIA Technologies licensed the UHCI standard from Intel; all other chipset implementers use OHCI. The main difference between OHCI and UHCI is the fact that UHCI is more software-driven than OHCI is, making UHCI slightly more processor-intensive but cheaper to implement (excluding the license fees). The dueling implementations forced operating system vendors and hardware vendors to develop and test on both implementations which increased cost. During the design phase of USB 2.0 the USB-IF insisted on only one implementation. The USB 2.0 HCD implementation is called the Extended Host Controller Interface (EHCI). Only EHCI can support high-speed transfers. Each 33 Core Module EHCI controller contains four virtual HCD implementations to support Full Speed and Low Speed devices. The virtual HCD on Intel and Via EHCI controllers are UHCI. All other vendors use virtual OHCI controllers. On Microsoft Windows platforms, one can tell whether a USB port is version 2.0 by opening the Device Manager and checking for the word "Enhanced" in its description; only USB 2.0 drivers will contain the word "Enhanced." On Linux systems, the lspci -v command will list all PCI devices, and a controllers will be named OHCI, UHCI or EHCI respectively, which is also the case in the Mac OS X system profiler. On BSD systems, dmesg will show the detailed information hierarchy. USB signaling Pin numbers (looking at socket): Pin assignments Pin Function 1 VBUS (4.75–5.25 V) 2 D− 3 D+ 4 GND USB signals are transmitted on a twisted pair of data cables, labelled D+ and D−. These collectively use half-duplex differential signaling to combat the effects of electromagnetic noise on longer lines. D+ and D− operate together; they are not separate simplex connections. Transmitted signal levels are 0.0–0.3 V for low and 2.8–3.6 V for high. Transfer speed USB supports three data rates. 34 Core Module A Low Speed rate of 1.5 Mbit/s (183 KiB/s) that is mostly used for Human Interface Devices (HID) such as keyboards, mice, and joysticks. A Full Speed rate of 12 Mbit/s (1.5 MiB/s). Full Speed was the fastest rate before the USB 2.0 specification and many devices fall back to Full Speed. Full Speed devices divide the USB bandwidth between them in a first-come first-served basis and it is not uncommon to run out of bandwidth with several isochronous devices. All USB Hubs support Full Speed. A Hi-Speed rate of 480 Mbit/s (57 MiB/s). Though Hi-Speed devices are commonly referred to as "USB 2.0", not all USB 2.0 devices are Hi-Speed. A USB device should specify the speed it will use by correct labeling on the box it came in or sometimes on the device itself. The USB-IF certifies devices and provides licenses to use special marketing logos for either "Basic-Speed" (low and full) or High-Speed after passing a compliancy test and paying a licensing fee. All devices are tested according to the latest spec, so recently-compliant Low Speed devices are also 2.0. Hi-Speed devices should fall back to the slower data rate of Full Speed when plugged into a Full Speed hub. Hi-Speed hubs have a special function called the Transaction Translator that segregates Full Speed and Low Speed bus traffic from Hi-Speed traffic. The Transaction Translator in a Hi-Speed hub (or possibly each port depending on the electrical design) will function as a completely separate Full Speed bus to Full Speed and Low Speed devices attached to it. This segregation is for bandwidth only; bus rules about power and hub depth still apply. Data Encoding The USB standard uses the NRZI system to encode data, and uses bit stuffing for logic 1 transmission more than six bits long (put 0 logic after six bits of logic 1). NRZI (non-return to zero, inverted) encoding method does not change the signal for transmission of a logic 1, but the signal level is inverted for each change to a logic 0. Mini USB signaling USB Mini-A, B plugs showing pin numbers (Not drawn to scale) Mini-A (left) Rounded, Mini B (Right) Square Mini USB connector pinout Pin Function 35 Core Module 1 VBUS (4.4–5.25 V) 2 D− 3 D+ 4 ID 5 Ground Most of the pins of a mini USB connector are the same as a standard USB connector, except pin 4. Pin 4 is called ID and is connected to pin 5 for a mini-A. This indicates if a device supporting usb on the go (with a mini AB socket) should initially act as host, in the mini B this is open circuit. The Mini A also has an additional piece of plastic inside to prevent insertion into slave only device. USB connectors Clip art image of a connector The connectors which the USB committee specified were designed to support a number of USB's underlying goals, and to reflect lessons learned from the varied menagerie of connectors then in service. In particular: The connectors are designed to be robust. Many previous connector designs were fragile, with pins or other delicate components prone to bending or breaking, even with the application of only very modest force. The electrical contacts in a USB connector are protected by an adjacent plastic tongue, and the entire connecting assembly is further protected by an enclosing metal sheath. As a result USB connectors can safely be handled, inserted, and removed, even by a small child. The encasing sheath and the tough moulded plug body mean that a connector can be dropped, stepped upon, even crushed or struck, all without damage; a considerable degree of force is needed to significantly damage a USB connector. It is difficult to incorrectly attach a USB connector. Connectors cannot be plugged-in upside down, and it is clear from the appearance and kinesthetic sensation of making a connection when the plug and socket are correctly mated. However, it is not obvious at a glance to the inexperienced user (or to a user without sight of the installation) which way round a connector goes, so it is often necessary to try both ways. The connectors are particularly cheap to manufacture. 36 Core Module The connectors enforce the directed topology of a USB network. USB does not support cyclical networks, so the connectors from incompatible USB devices are themselves incompatible. Unlike other communications systems (e.g. RJ-45 cabling) gender-changers are never used, making it difficult to create a cyclic USB network. A moderate insertion/removal force is specified. USB cables and small USB devices are held in place by the gripping force from the receptacle (without the need for the screws, clips, or thumbturns other connectors require). The force needed to make or break a connection is modest, allowing connections to be made in awkward circumstances or by those with motor disabilities. The connector construction always ensures that the external sheath on the plug contacts with its counterpart in the receptacle before the four connectors within are connected. This sheath is typically connected to the system ground, allowing otherwise damaging static charges to be safely discharged by this route (rather than via delicate electronic components). This means of enclosure also means that there is a (moderate) degree of protection from electromagnetic interference afforded to the USB signal while it travels through the mated connector pair (this is the only location when the otherwise twisted data pair must travel a distance in parallel). In addition, the power and common connections are made after the system ground but before the data connections. This type of staged make-break timing allows for safe hot-swapping and has long been common practice in the design of connectors in the aerospace industry. The USB standard specifies relatively low tolerances for compliant USB connectors, intending to minimize incompatibilities in connectors produced by different vendors (a goal that has been very successfully achieved). Unlike most other connector standards, the USB spec also defines limits to the size of a connecting device in the area around its plug. This was done to avoid circumstances where a device complied with the connector specification but its large size blocked adjacent ports. Compliant devices must either fit within the size restrictions or support a compliant extension cable which does. The USB 1.0, 1.1 and 2.0 specifications define two types of connectors for the attachment of devices to the bus: A, and B. The USB 2.0 specification also introduces the mini-B connector, for smaller devices such as PDAs, mobile phones or digital cameras. All connectors are mechanically incompatible, with an A connector always used on the upstream (host) end, and a B connector always used on the downstream (device) end. Hosts and devices include connectors (female) while cables contain plugs (male). Thus all compliant USB cables have an A plug on one end, and either a B or Mini-B on the other end. The A-plug is approximately 4x12 mm, the B-plug is approximately 7x8 mm, and the B-mini plug is approximately 3x7 mm. However, the mechanical layer has changed in some examples. For example, the IBM UltraPort is a proprietary USB connector located on the top of IBM's laptop LCDs. It uses a different mechanical connector while preserving the USB signaling and protocol. Other manufacturers of small items also developed their own small form factor connector, and a wide variety of these have appeared. For specification purposes, these devices were treated as having a captive cable. An extension to USB called USB On-The-Go allows a single port to act as either a host or a device - chosen by which end of the cable plugs into the socket on the unit. Even after the cable is hooked up and the units are talking, the two units may "swap" ends under program control. This facility targets units such as PDAs where the USB link might connect to a PC's host port as a device in one instance, yet connect as a host itself to a keyboard and mouse device in another instance. USB On-The-Go has therefore defined two small form factor connectors, the mini-A and mini-B, and a universal socket (mini-AB), which should stop the proliferation of proprietary designs. 37 Core Module Wireless USB is a standard being developed to extend the USB standard while maintaining backwards compatibility with USB 1.1 and USB 2.0 on the protocol level. The maximum length of a USB cable is 5 meters; greater lengths require hubs. USB compared to other standards Storage A Flash Drive, a typical USB mass-storage device USB implements connections to storage devices using a set of standards called the USB massstorage device class. This was initially intended for traditional magnetic and optical drives, but has been extended to support a wide variety of devices. USB is not intended to be a primary bus for a computer's internal storage: buses such as ATA (IDE) and SCSI fulfill that role. However, USB has one important advantage in making it possible to install and remove devices without opening the computer case, making it useful for external drives. Today, a number of manufacturers offer external, portable USB hard drives, or empty enclosures for drives, that offer performance comparable to internal drives. These external drives usually contain a translating device that interfaces a drive of conventional technology (IDE, ATA, SATA, ATAPI, or even SCSI) to a USB port. Functionally, the drive appears to the user just like another internal drive. Human-interface devices (HIDs) USB to PS/2 adaptor for a mouse As of 2006, most PCs and motherboards have at least one USB port, but still retain PS/2 keyboard and mouse connectors. AT keyboard connectors are less frequently found. Motherboards for non-portable PCs usually have a number of USB 2.0 high-speed ports, some available at the back of the computer case, others requiring USB sockets on the front or rear of the computer to be connected via a cable to a header on the motherboard. Joysticks, keypads, 38 Core Module tablets and other human-interface devices are also progressively migrating from MIDI, PC game port, and PS/2 connectors to USB. Mice and keyboards are frequently fitted with USB connectors, but are generally supplied with a small USB-to-PS/2 adaptor so that they can be used with either USB or PS/2 ports. Version history USB USB 1.0 FDR: Released in November 1995, the same year that Apple adopted the IEEE 1394 standard known as FireWire. USB 1.0: Released in January 1996. USB 1.1: Released in September 1998. USB 2.0: Released in April 2000. The major feature of this standard was the addition of high-speed mode. This is the current revision. USB 2.0: Revised in December 2002. Added three speed distinctions to this standard, allowing all devices to be USB 2.0 compliant even if they were previously considered only 1.1 or 1.0 compliant. This makes the backwards compatibility explicit, but it becomes more difficult to determine a device's throughput without seeing the symbol. As an example, a computer's port could be incapable of USB 2.0's hi-speed fast transfer rates, but still claim USB 2.0 compliance (since it supports some 39