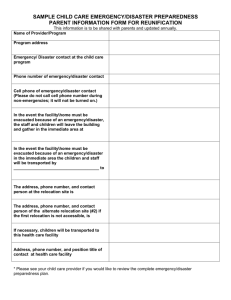
Disaster Recovery Plan
advertisement

1 DigiKnight Backup and Recovery Plan 2006 Robert Drake, Rick Osgood, Josh Wisman, Matt Smith, Chris Saltzman, Kevin Bunch, Alexander Andrews 2 Table of Contents DigiKnight Backup and Recovery Plan 2006 ............................................................ 1 Table of Contents ....................................................................................................... 2 Introduction ..............................................................Error! Bookmark not defined. Executive Summary ................................................................. Error! Bookmark not defined. Letter to the President ................................................................................................................4 Stakeholders: ..............................................................................................................................5 Department Scopes .................................................................................................... 7 Administration Department Scope .............................................................................................7 Sales Department Scope ............................................................................................................8 Research & Development Department Scope............................................................................9 Purchasing Department Scope .................................................................................................10 Administration/Purchasing Skill Matrix by Job Process .........................................................11 IT Skill Matrix by Job Process.................................................................................................12 Security/Purchasing/Shipping Skill Matrix by Job Process ....................................................13 Risk Assessments ..................................................................................................... 14 Layer One Assessment .............................................................................................................14 Layer Two Assessment ............................................................................................................15 Layer Three Assessment ..........................................................................................................17 Layer Four Assessment ............................................................................................................18 Layer Five Assessment ............................................................................................................20 FEMA Assessment...................................................................................................................21 Supplier Risk Assessment Form ..............................................................................................23 Vital Disaster Information ....................................................................................... 24 Emergency Telephone List ......................................................................................................24 First Alert Information Sheet ...................................................................................................25 Customer Analysis Form .........................................................................................................27 Computer Vendor Information Sheet.......................................................................................28 Critical Data List ......................................................................................................................29 Document Recovery Equipment Checklist ..............................................................................30 Insurance Provider Contact List: .............................................................................................32 Key Tracking Form ..................................................................................................................33 Backup Supply Companies ......................................................................................................36 Supplier Notification Checklist................................................................................................38 Hot Site Information ................................................................................................................40 Emergency Operations Center Information Sheet ...................................................................41 Emergency Operations Center Supply Sheet ...........................................................................43 Emergency Responsibility Chart .............................................................................................44 Disaster Recovery Procedures ................................................................................. 45 Restore Plan .............................................................................................................................45 File Retention Plan:..................................................................................................................47 Disaster Confirmation and Declaration Report........................................................................48 3 Maintenance Priority Ranking .................................................................................................50 Paper Records Recovery ..........................................................................................................51 Customer Disaster Notification................................................................................................53 Supply Chain Breakdown ........................................................................................................53 Family Employee Statement Policy .........................................................................................54 The Interim Plan....................................................................................................... 55 Backup Plan .............................................................................................................................55 Organizational Contact Information ........................................................................................58 Keys .........................................................................................................................................60 Test Scenarios & Continued Maintenance............................................................... 61 Power Outage Test Scenario ....................................................................................................61 Nature Based Test Scenario .....................................................................................................62 CD / Paper Plan Update Checklist ...........................................................................................64 Intranet Document Maintenance Checklist ..............................................................................65 Tabletop Test: Mudslides .........................................................................................................66 Paralipomenon ......................................................................................................... 67 DigiKnight Memo ....................................................................................................................67 Interim Plan Memo ..................................................................................................................68 Backup Memo ..........................................................................................................................69 Disaster Center Memo .............................................................................................................70 Raid Memo...............................................................................................................................71 Diagram 1: A Common Lan ....................................................................................................73 Sabotage Memo .......................................................................................................................74 Stress Memo.............................................................................................................................75 Test Memo ...............................................................................................................................76 Maintenance Memo .................................................................................................................76 Recovery Team Memo .............................................................................................................77 Glossary ...................................................................................................................................78 4 Letter to the President Robert Drake IT Department Editor 480-755-0829 Dear Mr. Smith: As you are no doubt aware, a disaster recovery documentation project has been created by a few of us members from the IT department. We realize this project may force us to divert time from other assignments and duties, but we fervently believe that DigiKnight Technologies needs this project in order to be prepared for an emergency situation. Within our company, there are dozens of separate, vital processes that if delayed, destroyed, or disrupted would cause significant interference to the continuation of standard business practices. It is our belief that it is in everyone’s best interest for there be plans in place should a disastrous event occur. With your approval we intend to document these vital processes, review all previous safety or emergency procedures, create further plans to secure these vital processes, assign individuals to different tasks during an emergency, and train all employees in emergency responses. We also intend to centralize all necessary contact information for law enforcement, suppliers, insurance, customers, employees, and all other relevant individuals. Our intent is that by preparing this document we will be more secure in the case of an emergency. We intend to prepare for man-made disasters, natural disasters, and even more mundane, but no less disruptive things, such as one of our suppliers going out of business. Our hope is to provide a document that is complete enough to serve in any disruptive situation of sufficient scope, but keep our project small enough that it remains effective. I believe that we are more than capable of this, but we will need the support of yourself, as well as that of the managers of each department, for this to be truly successful. At first only a few of us in IT, but eventually individuals from each department, will have to spend time away from other assignments. There may be some expense for training, planning software, research, and accessory items. We do not predict these will be excessive. Despite these limited expenses we believe that the benefit from this plan may very well be profitable in the long-term. The time saved, the equipment protected, and the people secured, could possibly outweigh the expenses a thousand times over. It is difficult to predict a massive emergency, but even if the future only holds many smaller disturbances, as we hope it does, this document will facilitate quick resolutions to problems that would otherwise require a great deal more time and effort. The organization this project provides will be useful if there is any massive emergency and the training we intend to perform will no doubt be invaluable. It is for these reasons that we request your support for our disaster recovery project. This project is a long-term endeavor. Our initial time frame for a complete document is around three months. As we pursue this project a more exact date will be determined. Even upon the ultimate 5 completion of this document it will be necessary for an individual to be tasked with keeping it up-to-date and periodically running new training exercises. New individuals will need to be familiarized with the document as well. The scope of this project requires support from the top of the company to be successful. We hope to complete this project in a timely and efficient manner for the benefit of the entire corporation and seek your approval. Should you have any questions pertaining to our disaster planning please contact the project’s leader, Josh Wisman, Robert Drake (myself), Rick Osgood, the documenter, Matt Smith, Kevin Bunch, Alexander Andrews, or Christopher Saltzman. Stakeholders: The stakeholders for this project are as follows: CEO: Carlton Smith Objectives: Assure that the company has a recovery plan in place for any event that could significantly harm business productivity. Administration Manager: Mark Saunders Objective: Assure the safety of all employees in the event of a disaster. Sales Manager: Diane Ford Objective: Sustain a minimum quality of service during a disaster. Understand all disaster procedures relevant to the sales department. Manufacturing Manager: Linda Kraemer Objective: Sustain a minimum quality of service during a disaster. Understand all disaster procedures relevant to the manufacturing department. R&D Manager: Carlton Bowden Objective: Decrease the probability of adverse effects on the R&D department and ongoing projects. Maintenance Manager: Michael Winters Objective: Understand all disaster procedures relevant to the maintenance department. Acquire a functional knowledge of all each course of action to be taken in the event of different disasters to preserve different types of equipment put under their department. Advertising Manager: Michael Churchill Objective: Acquire a functional knowledge of all each course of action to be taken in the event of different disasters. Prepare possible marketing statements to be made in the event of a disaster. Shipping Manager: Kenneth Gilliam 6 Objective: Sustain a minimum quality of service during a disaster. Maintain a backup list of buyers. Purchasing Manager: Katherine Cavenaugh Objective: Sustain a minimum quality of service during a disaster. Maintain a backup list of suppliers. Security Manager: Brett Kelcey Objective: Acquire a functional knowledge of all each course of action to be taken in the event of different disasters. Assure the safety of all employees in the event of a disaster. IT Manager: Alicia McKellips Objective: Protect critical IT resources. Assure the availability of working off-site back ups and an adequate procedure for their use in the event of a disaster. All stake holders are upper management and representative of all departments. Each has an objective they wish accomplished from this project. It is the responsibility of the managers to relay relevant information to the employees under them. This will assist the efficient completion of the Disaster recovery and backup plan. 7 Department Scopes Administration Department Scope Administration Department Responsibilities The Administration Department is responsible for organizing people and resources to our company’s goals and objectives. Included within the administrative department are both the decision makers and leaders. Administration assigns responsibilities to managers of each department and those managers then assign employees to uphold these responsibilities. Administration also does most of the planning for future responsibilities. Administration has all hiring and firing privileges. Administration Department Location The Administration Department is located in Building One. It is a small single story building of roughly 2000 square feet. At the entrance is a reception desk for guests visiting the facility. There is also a security guard post at the front door. There are a total of five offices, as well as bathrooms, and a medium sized conference room. This is the only building in which two or more departments do not share the building. Relevant Administration Department Assets Administration Computers – 10 These computers are the ones used by company administration for such tasks as basic word processing and spreadsheets. They are relatively simple machines, and are purchased from Compaq. They have the following specifications: 2.2 GHz Pentium 4 Processors 1024 MB of RAM 100 GB SATA Hard Drive Built-In Video Card Gigabit Network Card 17 Inch Monitor Windows XP Administration Key List Administration has no need to go anywhere but within its own building. All employees are issues sequentially numbered keys marked ADMN (For example, the first employee is the key ADMN-1). Thus Administration only has keys to the Administration building. Administration Personnel and Contact Department Phone: 415-555-8643 Manager: Mark Saunders Rod Hatherly Bea Holdeman Susan Marcotte Kendra Bell 8 Dillon Sommer Sales Department Scope Sales Department Responsibilities The Sales Department is responsible for purchasing all equipment necessary for other departments. This is a vital process that keeps departments supplied and operational. The Sales Department is also responsible for keeping track of orders and shipments. In this, the Sales Department, works closely with the Shipping Department to assure that all sales are promptly delivered. Sales also maintains contracts with companies DigiKnight sells and purchases through. This process is important in keeping expenditures down as well as selling as our services. Any maintenance required this department is brought to the Maintenance Department. Sales Department Location The Sales Department is housed in building two along with R&D, Shipping, Purchasing, and Advertising. It is two stories with usable floor space roughly double to that of the administrative building. Sales and Shipping are located on the bottom floor along with a security guard post. The top floor is home to the R&D Department and the Purchasing Department. Instead of having individual offices for each employee, the Sales department consists of a single room with cubicles set up to give each employee a working location. This enhances team communication and makes optimum use of available space. Relevant Sales Department Assets Sales Computers – 15 These computers are used by the sales staff and mainly contain sales data. Each of the nine sales associates has an individual computer. There are 3 computers that are currently unused and the remaining three are used as a local database for the sales members. The computers are purchased from Dell and have the following specifications: 2.7 GHz Pentium 4 Processors 1024 MB of RAM 200 GB SATA Hard Drive Built-In Video Card Gigabit Network Card 21 Inch Monitor Windows XP Sales Key List Each member of the sales department has keys to both the Administrative Building and the building housing the Sales Department. The keys for this department are marked SLS accompanied by a number. Sales Personnel and Contact Department Phone: 415-555-6312 Manager: Diane Ford Halle Branson 9 Natasha Lowe Thomas Baird Lorna Hastings Dwayne Roby Pam Millard Katie Barnes Leonard Filby Helen Reese Research & Development Department Scope Research & Development Department Responsibilities Research & Development is a small part of DigiKnight. R&D focuses mainly on new production methods as well as ways to reduce production costs. The staff stays in close contact with other manufacturing locations in order to keep up-to-date with the latest technology. Research & Development Location The Research & Development department is located in building two along with the Sales, Shipping, Purchasing and Advertising departments. R&D shares the top floor with the purchasing department. The R&D department is in one large room divided by cubicles to give employees personal space. Research & Development Department Assets Research & Development Computers – 3 These computers are high performance systems capable of running the latest CAD software. There is no need for each individual to have a system. As such there are only three workstations. The systems are custom built by Boldata Technology of Fremont CA. They have the following specifications: 3.2 GHz Pentium 4 Processors 2048 MB of RAM 450 GB SATA Hard Drive Quatro Pro Video Card Gigabit Network Card Dual 21 Inch Monitors Windows XP Research & Development Key List Each member of R&D has keys to the entire facility. Their keys are marked MNF accompanied by a number. Research & Development Personnel and Contact Department Phone: 415-555-3223 Manager: Carlton Bowden Carlton Bowden 10 Kurt Gossard Sam Jarosz Corey Bogdan Anne Mcloskey Purchasing Department Scope Purchasing Department Responsibilities The purchasing department is responsible for the acquisition of new products and materials necessary for business at DigiKnight that are of a sufficient expense that they cannot be purchased with individual employee credit cards. Essentially any purchases which require checks to be cut or the company to be billed are the purview of the purchasing department. Recommendations for purchases will be made by the appropriate department (example: IT recommends computers). Purchase authorization will be completed by the appropriate departmental managers. At this point, a PO (purchase order) is generated, which is sent to the purchasing department. Employees of the purchasing department then cut a check if needed, set up a billing account with the vendor, or otherwise process bills. Purchasing Department Location The Purchasing Department is located in Building One. There are five employees, each equipped with a Windows PC workstation. A central laser printer is used by this department for their various needs. Relevant Departmental Assets Computers – 5 Dell Optiplex Desktops 1.7 GHz Pentium 4 Processors 512 MB of RAM 40 GB SATA Hard Drive 17 Inch LCD Monitor Windows XP IBM Infoprint 1140 Laser Printer Keys Department head has a key to the purchasing office Department Members Manager: Jim Thompson Chris Bellors Jessica Curry Coral Gates Allan Simmons 11 DigiKnight Technologies Inc. 2725 E. Technology Ave, Freemont, CA 94536 Administration/Purchasing Skill Matrix by Job Process Administration Employee Mark Saunders Rod Hatherly Bea Holdeman Susan Marcotte Kendra Bell Dillon Sommer Purchasing Katherine Cavenaugh Shay Robertson Robert White Ian Wolf Prepared for the: Administration & Purchasing Departments Maintain Company Increase Reputation Paperwo rk Company Communication Hiring Employees Employee Retention 10 9 9 9 9 7 8 8 8 9 7 7 9 8 9 5 6 6 6 4 7 6 6 7 5 5 4 5 5 5 8 5 6 6 5 7 Maintain Purchasing Records Maintain Contacts Paperwo rk Keep Supplies Steady On Call Availability Train Other Employees 10 10 9 10 10 10 5 4 4 5 2 2 7 7 8 8 6 7 6 6 8 7 7 6 Scoring: blank = No knowledge 1 = Familiarity 5 = Highest score for subject knowledge but lacking experience at this company 10 = Complete mastery of subject and local processes 12 DigiKnight Technologies Inc. 2725 E. Technology Ave, Freemont, CA 94536 IT Skill Matrix by Job Process IT Maintain Network Repair Systems Automation Prepared for the: IT & Research & Development Departments Communication Hiring Employees Train Other Employees Alicia McKellips Luke McDowel 10 10 6 9 8 5 5 7 Allan Smith 5 7 8 8 Joesph Webber 9 5 5 6 Robert Wildhorn 3 7 9 9 Paperwork Documentation R&D Maintain Current Make Contacts Knowledge W/ Other Companies Carlton Bowden Kurt Gossard 10 10 9 10 7 9 8 8 Sam Jarosz 8 9 6 9 Corey Bogdan 4 5 7 9 Anne Mcloskey 6 6 8 10 10 Scoring: blank = No knowledge 1 = Familiarity 5 = Highest score for subject knowledge but lacking experience at this company 10 = Complete mastery of subject and local processes 10 13 DigiKnight Technologies Inc. 2725 E. Technology Ave, Freemont, CA 94536 Security/Purchasing/Shipping Skill Matrix by Job Process Security Brett Kelcey Frank Arrons Joanna Clark Purchasing Katherine Cavenaugh Shay Robertson Robert White Shipping Prepared for the: Security, Purchasing, and Shipping Departments Communication Prevent Theft Prevent Violent Acts 9 9 8 8 6 6 5 9 10 5 8 8 8 7 4 Maintain Current Knowledge Make Contacts W/ Other Companies Paperwork Keep Reciepts 10 10 7 7 6 4 9 8 4 3 8 10 Maintain Current Knowledge Make Contacts W/ Other Companies Paperwork Keep Reciepts Training Alertness 10 9 4 Response Times Keep Inventory Steady Kenneth 10 10 7 7 9 Gilliam Derrick Cunningha 7 6 9 8 5 m Evan 4 4 7 10 4 McAllister Scorin blank = No knowledge g: 1 = Familiarity and Some Competance 5 = Highest score for subject knowledge but lacking experience at this company, well trained 10 = Complete mastery of subject and local processes, Quick Response To isses 14 Risk Assessments Layer One Assessment We are based in Fremont, California in which there are several major external risks to be considered. Risks such as natural disasters affect everything from equipment, to employees, to our customers. Natural Disasters Earthquakes Earthquakes are a major risk in California, including Fremont. Depending on the magnitude of the earthquake, it could destroy the entire facility. If the entire facility were to be destroyed, our customers would move on to someone else to produce their software which would also destroy our business. This risk is the number one risk for DigiKnight considering probability and outcome of these earthquakes. The chances of a 5.0 earthquake hitting Fremont in the next year is around 11%. The chances of that in the next five years is 50%. A 5.0 earthquake surely wouldn’t destroy but things like power outages, electrical damage, or other moderate risks to the facility are certainly at risk. The chance of a 7.5 magnitude earthquake in the next five years is only 3%. However, this is an earthquake that could destroy the entire facility. The 1906 earthquake in San Francisco was around 7.9 that killed an estimated 700-3000 people. There hasn’t been an earthquake of that size around major cities in California since then, so the amount of damage could be much higher. A big killer of these large earthquakes is fire that usually comes along afterwards. With so much electrical equipment falling apart, the risk of fire is rather high. Earthquakes a risk to every part of our company including: employees, equipment, documents, and anything else inside the facility. Fire A fire can happen anywhere but the risk of a fire in Fremont is more likely than most places in the country. Fremont can have high temperatures which deteriorate equipment faster and increase the risk of fires. This is not a huge risk but certainly is a noticeable one. However, earthquakes can easily cause fires especially on the hotter days. A large fire could easily destroy our facility unless action is taken very quickly to contain it. Just like with earthquakes, everything in the facility is at risk during a fire. This risk is second to earthquakes. Thunderstorms The risk of thunderstorms in Fremont is rather low but it should still be considered. Lightning can cause electrical damage without even striking the facility. Man-Made Risks 15 Man-made risks could be just about anything. Rather than preparing for specific risks, prepare for the outcome of these risks such as a road block. If a road is blocked from a collision, road construction, police investigation, or other things, it is a risk that needs to be considered. Chemical spills are a possibility anywhere but depending on your surrounding businesses the risk increases or decreases heavily. Pipelines are break and if happens to break under or near your facility, you will most likely have to evacuate. Bomb threats are a risk in which you will have to evacuate everyone and lose a large amount of production and money. What if a bomb actually explodes? This risk has a very low probability but the outcome could be devastating. A risk that came up recently is illegal immigrants protesting in the streets and having the certain days when no Hispanics will work or buy any products that day. In Fremont, a decent population of the people are Hispanic so a lot of production is lost on these days. These are everyday risks that can be a huge risk or small risk. Suppliers With all these risks considered our suppliers must also be applied to our suppliers. If our suppliers were to go out of business we would need to have a backup supplier already on hand or act fast and find one. This is a moderate risk for DigiKnight. It should be an easy fix, but while we are finding a new supplier production time is lost. Layer Two Assessment We currently have no plans for any layer two risks. We are susceptible to a power outage or a loss of vital infrastructure such as fire, telephone, and water. This document will assess each layer two risk in detail. Electricity In the event of an electrical outage, we have no backup lighting. This is especially dangerous should an evacuation be necessary. The company will also need some battery backup in order to have adequate time to shutdown our servers and workstations. Surge protection is needed in the event of a thunder storm. Telephones If there is an electrical outage, base telephones will work fine. They should be used in order to report an electrical outage to the power station and also if needed for an emergency. There may be a telephone outage if a telephone pole is knocked down. Cell phones should be used if there is a telephone outage to report the outage and also be used if an emergency call is needed. Water We need to make sure that nothing expensive is below ground level to help prevent water damage should our building flood. We also need to plan for mudslides that may delay employees and partners in arriving to work. We also have a water-based cooling system. We need to assure to that any leak or failure in the cooling system can be reported quickly. Should it go down overheating will damage our workstations and servers quickly. We need to plan a backup system for drinking water and also sanitation if our water company has any problems. 16 We should have a reserve of water for drinking and a backup plan for sanitation. There is no danger of any ice damages. Climate Control If the climate control went out during the summer, the business may have to be shutdown for a short period of time. There is a danger of heat stroke and/or exhaustion if it is hot inside the building. If the cooling system goes out the servers and workstations may have to be shutdown. Fire Fire is always a risk. There should be flame retardant window shades, carpet, ceiling tiles, etc. The speed fire spreads should be accounted for in the evacuation plan. We currently possess a sprinkler system that automatically activates when a fire is detected. This will help prevent any further fire and smoke damage, but may harm some electrical components. The server room should have a system that will release carbon dioxide when a fire is detected. There should be an estimated response time for the local fire department to reach our building in case they are needed. Structural The building should be inspected to make sure that there are no visible flaws that may cause harm to a person or equipment. The building will need to be looked over for simple weather details like faulty roofing for leaks, poorly sealed windows for heating/cooling costs, etc. Sprinkler systems for fires need to be inspected to make sure that water does not seep into important records or equipment on the floors below. The water pipes should be inspected to make sure that they seem sound and locate all of the emergency shutoff valves. The valves should then be tested to make sure that they will work. The building should also be inspected to make sure it is grounded so if it is struck by lightning. This will help prevent damages to the building, people, and equipment. Security There will be a security group that will help with trespassing, workplace violence, sabotage, loss prevention, and other threats. Having an independent company manage this will help reduce our company’s burden. The security team will be briefed on all emergency procedures and will be the main point of contact for any emergency services. All security personnel will know the evacuation plans if needed. Medical There will be basic medic kits in the break rooms for things like cuts, headaches, and any other minor injuries. If there is any type of sickness or injury that cannot be easily resolved with basic medical supplies, an ambulance will be called to have an EMT dispatched. There is a small chance of a serious or fatal accidents occurring in our facility. There is a chance of electrocution via our electronic equipment and some of our heavier manufacturing supplies could crush individuals. These types of accidents can be prevented with basic electrical education and assuring that all equipment is adequately secured. 17 DigiKnight Technologies Inc. 2725 E. Technology Ave, Freemont, CA 94536 # of Buildings: 3 Layer Three Assessment Layer 3 – Data Systems Date: Likelihood 0 - 10 Impact 0 - 10 Restoration Time 1 - 10 1 4 1 2 1 7 1 3 1 10 10 7 2 5 1 2.66 2 4 1 2.33 2 8 2 4 2 3 1 2 2 3 1 2 Servers 4 8 9 7 PCs 4 6 6 5.33 Grouping Risk Electrical Supply Loss of Power to Building One Loss of Power to Building Two Loss of Power to Building Three Telecommunications System Loss of telecommunications for Sales Department Loss of telecommunications for Research and Development Loss of telecommunications Shipping Loss of telecommunications Purchasing Loss of telecommunications Advertising Score Data Communications Network Routers/Firewall 2 10 5 5.66 18 Layer Four Assessment The company has ten major departments. These departments are divided by the different tasks and personnel working in those departments. As such, the risk of each individual department varies. Each department is listed along with a short description of that department’s risks. Corporate Administration: The Admin department carries few risks, but should these risks be exploited, the damage could be overwhelming. The administration holds key information with regards to the wellbeing of the company as well as an overview of all ongoing and upcoming projects. It is also the department which controls the others. In light of this, all executives and managers should be well versed in safe practices regarding information and its safe keeping. Also, no company files of any kind should be allowed to leave the premises of the building and all corporate e-mails should be sent to addresses within the company’s own e-mail server. No information should be sent to someone’s home address. Sales: The sales department is mainly in charge of relations with the customer/client. This means that they have direct access to information, not only belonging to the company, but to those whom we do business with. This information should be considered very sensitive and important. If that information is not well protected it could be harmful, not only to our company, but our clients as well. All sales associates should know the importance of safeguarding information. Also, a password policy should be in place for all those who have ready access to customer information. Manufacturing: Manufacturing has access to most current projects in place. They hold key information about all products important to the company. Should data of that kind be leaked, it could cause major damage to the company, as well as for any clients. The manufacturing floor should be monitored for anyone trying to get a product off the premises. All employees should be checked at punchin and at punch-out. Advertising: Advertising has access to information pertaining to not only current projects, but also upcoming ones not yet announced. This poses a risk to the company should the information be leaked. This information should be secured and all employees should know the importance of safeguarding privileged information. Also, e-mail correspondence about new projects should be kept within the company’s network. No e-mail to home addresses 19 Shipping: The shipping department is in charge of getting the product to the customers. This entails that they have access to the private addresses of our customers. This information should be kept as secure as possible. It should also be backed up on a regular basis. In addition, the same password policy should be in place here as in the sales department. Purchasing: This department has access to company accounts to purchase needed supplies and equipment. The information used by this department should be kept as secure as possible. I suggest that not more than two employees in this department have direct access to the information and a password policy should be in place. Also, the data should be backed up daily and be monitored for tampering from outside sources. Security: The security department is in charge of the physical security around and in each of the buildings. They, in turn, have access to every room in each building. This poses a specific risk of robbery should the keys used for the buildings be lost of stolen. I recommend using an electronic key card system, as it is more secure. The keys used should be numbered and locked in a secure place when not in use. Electronic keys can be cycled on a regular basis so that should a key be lost of stolen, it may not be used after a certain time. Also, all security employees should undergo an in depth background check. IT: The IT department should be kept the most secure. This department has access to all information on every computer on the company’s network. IT employees also have access to the physical hardware on the network as well as administrative rights to employee folders. Server rooms should be locked and monitored with security cameras. Only one key should be issued to the manager of the department. A password policy should be in place for all employees who have access to admin logins. All hardware, not in use, should be kept in a secure location. 20 Layer Five Assessment As a system administrator, the things necessary for me to do my job are essentially the same as those required for the general health and security of the DigiKnight network itself. Electricity: Because the network is critical to normal operations of the company, and my position is responsible for the health of the network, the continued operation of my position is critical. As a result, my workstation will need to be connected to the main UPS (Uninterruptible Power System) in the server room. As this system is itself powered by a failsafe generator in the event of a major power failure, I will be able to continue operating in the event of a power failure. This will allow me to properly shut down servers remotely, initiate an emergency backup if necessary, etc. Telephones: Most employees as well as myself have cellular telephones, so the business will not suffer critically if the phone system is down for a period of time. As no catastrophic natural disasters are likely in Phoenix, the likelihood of cellular networks going down at the same time as the landline system is extremely unlikely. However in the event this does happen, all senior managers will be equipped with satellite telephones for use in extreme emergencies. Water: All external water must necessarily be kept out of the server room at all times. As a result the server room is located on the second floor and is secured by watertight doors which remain closed at all times for other reasons. Fire suppression systems do not use water. Climate Control: Server room temperature is maintained at 68 degrees at all times. In the event of power failure, the UPS system or generators will kick on and allow for the maintenance of a safe temperature until the servers can be properly shut down. Fire: In addition to a standard manual-pull fire alarm, there will be an air-aspirating fire detection system. Depending on the size of the room, one or many manually operated fire extinguishers will be installed. They will each be inspected monthly and maintained if necessary. Dry chemical fire extinguishers will be preferable, and a system will be in place to cut power to the room in the event of a fire alarm. An undetermined amount of time depending on the size of the room and expected number of occupants will be calculated as a delay before fire suppression systems activate. Security: The server room has one entry point, which is a watertight, bullet proof steel door. The one window to the right of the door is made of bulletproof glass. 21 FEMA Assessment To: Task Coordinator Josh Wisman From: Editor Robert Drake As requested, I reviewed the FEMA reports for the Bay Area to determine what natural disasters were most relevant to the construction of our disaster recovery document. FEMA reported that our area could experience severe storms, flooding, mudslides, landslides, earthquakes, and severe freezes. Wildfires were also consistently reported in California, but I believe our position in an urban environment mitigates that possibility. Of these, the most relevant are earthquakes, flooding, and mudslides. All three have occurred repeatedly as per FEMA’s list of California’s disasters. Alternatively, severe freezing is a rare occurrence. Nevertheless, we should review our insurance policy to see if cracked or exploded pipes are included. The rarity of this disaster means that, in my opinion, we should relegate it to the general disaster plan rather than a separate section. I believe that severe storms should also be included in the general disaster plan. If the storm causes flooding than the appropriate response steps will be within the flood plan. If the damage caused by the storm is not flooding then the general disaster plan would be the better response. Landslides and mudslides are similar and should be included as a single plan. Ultimately our three disaster-specific plans should be earthquakes, flooding, and mudslides. It would be prudent for us to determine what insurance we have in each of these situations. It would also be useful for us to contact a structural engineer to determine the likelihood of our infrastructure being adversely affected by an earthquake or mudslide. In both situations we can expect that some amount of cleanup will be necessary, but we need to determine if the damage caused by such an event is likely to be more catastrophic or less so. Aside from insurance, we need to create detailed plans for each emergency. We need to keep an up-to-date list of all company assets so that should a catastrophic event occur we will be able to file for appropriate damages. Further we need to know how to protect these assets. In the event of an earthquake there is the possibility for fire. We need to include our fire prevention and fire emergency steps within our earthquake disaster plan. Flooding also requires a specific plan for the protection of our assets. Due to the great possibility of flooding within this geographic area it may be necessary for us to purchase flood insurance. If our present insurance does not include flood damage, especially that related to severe storms, we need to purchase ancillary insurance to cover that eventuality. Due to the extreme nature of earthquakes training will be particularly important. There is a high likelihood that medical assistance will be needed. Many key individuals may be out of communication with a large earthquake so each individual needs a high level of experience to the earthquake disaster plan. Evacuation procedures should be written. It would be advisable for us to review these procedures with law enforcement. Mudslides will also require evacuation plans. It is far less likely that key individuals will be out of contact for a mudslide, but the time necessary to evacuate may be much shorter. Therefore training and testing of the procedures in place will be just as, if not more, important for this disaster. Our final addition to the documentation of these disasters is how we proceed should our suppliers or customers be adversely affected. Most likely this information will be included in a 22 separate section of the document, but we should note the possibility that we could lose a substantial number of our co-companies if a large earthquake were to take place. Hopefully this information will serve our overall documentation project. If you wish to review the FEMA disaster reports they can be found at http://www.fema.gov/news/disasters_state.fema?id=6 23 DigiKnight Technologies Inc. 2725 E. Technology Ave, Freemont, CA 94536 Supplier Risk Assessment Form Date: Likelihood 0 - 10 Impact 0 - 10 Alternative Sources 1 - 10 Score The Tech Geek 3 6 9 162 Disc Makers 3 3 9 81 Dub-It Media Services 3 3 9 81 3 3 9 81 3 7 6 126 Boxes ISSI Business Solutions Customized Packaging Solutions Inc. The Packaging House, Inc. 3 4 6 72 Paper JC Paper 3 9 5 135 Dell Computers Dell 1 2 3 6 HP Computers HP 2 2 3 12 General Computers Bold Data 4 2 3 24 3 3 3 27 3 6 2 36 Dell Computer Repair Dell 1 4 4 16 HP Computer Repair HP General Computer Repair Boldata Software Tech Support We Sell Software Inc. 2 4 4 32 4 4 4 64 2 4 4 32 Item Supplier Raw Materials Blank DVD / CD / Cases Blank DVD / CD / Cases Blank DVD / CD / Cases Blank DVD / CD / Cases Boxes Services Copy / Fax machine Repair Office Equip Inc Production Machine Repair We Fix’Em Inc Infrastructure Phone Ma Bella 3 7 4 84 Electricity Bill’s Electric Company 4 9 1 36 3 5 6 90 5 7 6 210 2 3 6 36 Plumbing Pipes Plus Air Conditioning/Heating Air Surplus Pest Control Russ’ Roach Ranch 24 Vital Disaster Information DigiKnight Technolgies Inc. 2725 E. Technology Ave, Freemont, CA 12345 # of Buildings: 3 Emergency Telephone List Internal Security Electrical/Gas Water Heating & Air Conditioning Legal Phone Number Brett Kelcey (Manager Security) ext: 0170 415-555-3852 Michael Winters (Manager Maintenance) ext: 0400 415-555-3970 Michael Winters (Manager Maintenance) ext: 0400 415-555-3970 Michael Winters (Manager Maintenance) ext: 0400 415-555-3970 Mark Saunders (Manager) 0180 415-555-8643 External Fire Department 510-494-4200 Local, Emergency 911 Police/Sheriff 510-790-6800 Local, Emergency 911 Ambulance 510-797-1111 Local, Emergency 911 Hospital 510-797-1111 Local, Emergency 911 Electrical Company Natural Gas Company Mission Valley Electric 510-657-6180 TXU Energy Services 510-226-5777 Telephone Company Impact Communications 510-659-8488 Long Distance Company Impact Communications 510-659-8488 Internet Service Provider Charter Communications Inc. 888-438-2427 25 First Alert Information Sheet DigiKnight Technologies Inc. 2725 E. Technology Ave, Freemont, CA 94536 # of Buildings: 3 Name Mark Saunders Main Phone 415-555-8643 Order of Contact Department Administration Main Fax 415-555-2622 1 Title Manager E-mail MSaunders@dk.com Reason: Name Alicia McKellips Main Phone 415-555-8352 Order of Contact Department IT Main Fax 415-555-2622 2 Title Manager E-mail AMcKellips@dk.com Reason: Name Brett Kelcey Main Phone 415-555-3852 Order of Contact Department Security Main Fax 415-555-2622 3 Title Manager E-mail BKelcey@dk.com Reason: Name Carlton Smith Main Phone 415-555-7841 Order of Contact Department CEO Main Fax 415-555-2622 4 Title CEO E-mail CSmith@dk.com Reason: Name Michael Winters Main Phone 415-555-3970 Order of Contact Department Maintenance Main Fax 415-555-2622 5 Title Manager E-mail MWinters@dk.com Reason: Name Linda Kraemer Main Phone 415-555-6161 Order of Contact Department Manufacturing Main Fax 415-555-2622 6 Title Manager E-mail LKraemer@dk.com Reason: Name Carlton Bowden Main Phone 415-555-3223 Order of Contact Department Research & Development Main Fax 415-555-2622 7 Title Manager E-mail CBowden@dk.com Reason: Name Kenneth Gilliam Main Phone 415-555-6431 Order of Contact Department Shipping Main Fax 415-555-2622 8 Title Manager E-mail KGilliam@dk.com 26 Reason: Name Diane Ford Main Phone 415-555-6312 Order of Contact Department Sales Main Fax 415-555-2622 9 Title Manager E-mail DFord@dk.com Reason: Name Katherine Cavenaugh Main Phone 415-555-3298 Order of Contact Department Purchasing Main Fax 415-555-2622 10 Title Manager E-mail KCavenaugh@dk.com Reason: Name: Michael Churchill Main Phone 415-555-3131 Order of Contact Department Advertising Main Fax 415-555-2622 11 Title Manager E-mail MChurchill@dk.com Reason: Above is a list of the important managers in the event of a disaster. The order of contact reflections each manager’s importance and relevant skills in a disaster situation. Administration is first because they have the best overview of the entire corporation as well as all the contact data and authority. IT is next since they have the most experience with disaster operations. Security follows since they provide a necessary service in a disaster. Following that the CEO should be contacted. If the disaster has already passed or is less severe he may be called first, but the first three contacts she be notified if the disaster is ongoing or very serious. The rest of the contacts refer to relative importance in a disaster. Maintenance is useful in getting all systems back up and running. Manufacturing needs to maintain production as best as possible. Research and Development potentially has the most to lose in a disaster. Shipping, Sales, Purchasing, and Advertising are relatively unimportant in a disaster, hence they are called last. 27 DigiKnight Technologies Inc. 2725 E. Technology Ave, Freemont, CA 94536 Customer Analysis Form Goods Category/Type Critical Times Criticality Salespers on Electronic Arts JIT Critical Times Critical Times Contra ct High Volum e Main Product Peak Seas on Least Season Accessori es Peak Season Least Season Spare Parts Peak Season $100k 50k Units Madde n 07 Sum mer Spring Madden Contest Cd Summer Spring Madden Controlle r Summe r 75k Units Prince of Persia Fall Spring Na Fall Spring Na Fall 25k Units Grand Theft Auto 3 Fall Spring Na Fall Spring Na Fall 5k Units Star Wars Empire at War Wint er Spring Lightsabe r Winter Spring Darth Vadar Mask Winter 120k Units Zelda Wint er Spring Wii Winter Spring Wii Controlle r Winter 10k Units Street Fighter Spri ng Fall Movies Spring Fall Na Spring 20k Units Titan Quest Fall Spring Movies Fall Spring Na Fall 50k Units Spy Hunter Sum mer Spring Na Summer Spring Na Summe r 30k Units X-Men Legend s Fall Spring Na Fall Spring Na Fall 10k Units Na Spri ng Fall Game Genie Spring Fall Naa Spring $150k Ubisoft $50k Take-Two $10k LucasArts $240k Nintendo $20k Capcom $40k THQ $100k Midway $60k Activision Codemast ers $20k L ea st S ea so n S pr in g S pr in g S pr in g S pr in g S pr in g F al l S pr in g S pr in g S pr in g F al l 28 DigiKnight Technologies Inc. 2725 E. Technology Ave, Freemont, CA 94536 Computer Vendor Information Sheet Date Compiled: System Type July 5, 2006 # Purchased Last Purchased Compiled By: Purchase From Contact Info Joshua Wisman Service Contract (circle one) Administr ative Workstati ons 10 5-1-06 Compaq 800-282-6672 Yes No Sales Workstati ons 15 5-1-06 Dell 1-800-WWWDELL Yes No R&D Workstati ons 3 5-1-06 Boldata Technologies 800-923-2653 Yes No Shipping Workstati ons 4 5-1-06 HP 800-282-6672 Yes No Purchasin g Workstati ons 3 5-1-06 HP 800-282-6672 Yes No Advertisin g Workstati ons 5 5-1-06 HP 800-282-6672 Yes No IT Workstati ons 10 5-1-06 Dell 1-800-WWWDELL Yes No IT Servers 4 5-1-06 Dell 1-800-WWWDELL Yes No Comments Purchase new workstatio ns biyearly Purchase new workstatio ns biyearly Free phone support but only hardware warranties Purchase new workstatio ns biyearly Purchase new workstatio ns biyearly Purchase new workstatio ns biyearly Purchase new workstatio ns yearly Purchased new as needed 29 Critical Data List Computer Backups (Optical Media) – BUSINESS CRITICAL – Computer backups are critical data. When backups are lost data is in jeopardy of being unrecoverable. Losing backups is the same as not creating backups. Replacing backups is not very hard. It does however take a substantial amount of time. If the backups are lost they need to be replaced as soon as possible. Employee Personal E-mail Accounts – NONCRITICAL – Employee personal email accounts are not of high importance. The company has both business emails and personal emails so contacting the person is not difficult. Of course there are many other ways to contact someone other than through email such as their phone, which is our database as well. Employee Business E-mail Accounts – NONCRITICAL – This is about the same as the personal emails. There are other ways to contact people if they are needed. E-Mail Correspondence w/ customers – CRITICAL – Our customers are where we get our profit. If we do not respond to the customer emails they will take their business elsewhere. E-mail Correspondence w/ suppliers – SENSITIVE – This isn’t as critical as it is with customers because if we don’t respond to our suppliers email they will probably call us up because we are the ones paying them. It is still important to keep in contact with suppliers. Company Website Design – SENSITIVE – The actual design is not of high importance, but the better the website is, the more customers we will gain. Some people dismiss bad looking sites instantly and move on to the next one. This is not what we want happening with our website design. Customer Database – CRITICAL – This is our money and we need to know how to keep in contact with our customers if something were to come up. The customer database for our company is of higher importance than most companies. We don’t have hundreds of customers; we have several that give us a lot of revenue each. Supplier Database – CRITICAL – We need to know who is supplying us with what. Even though we are essentially a supplier ourselves, we will still need supplies. If something breaks we need to know immediately who to contact in order to get the missing part. Corporate Database – CRITICAL – This is our database that tells all about what supplies we have to who we are going to give supplies. It should show our employees as well with their personal information and salaries etc. Losing our corporate database would be an extreme situation especially when payday comes. Customer Payment Information (including Credit Cards) – CRITICAL – This is definitely critical. If we don’t have our customers’ payment information we will not be able to bill. If we do not receive any money the company goes bankrupt and it disappears. 30 DigiKnight Technologies Inc. 2725 E. Technology Ave, Freemont, CA 94536 # of Buildings: 3 Document Recovery Equipment Checklist Location Supplier Daytime Phone # Flashlights Building 1 Wal-Mart #2989 (510) 651-3301 Flashlight Batteries Building 1 Wal-Mart #2989 (510) 651-3301 Mops and Buckets Building 1 Wal-Mart #2989 (510) 651-3301 Squeegees Building 1 Wal-Mart #2989 (510) 651-3301 Sponges Building 2 Wal-Mart #2989 (510) 651-3301 Carts Building 1 Home Depot (510) 490-0191 Folding Tables Building 2 Wal-Mart #2989 (510) 651-3301 First Aid Kit Building 2 Wal-Mart #2989 (510) 651-3301 Protective Masks/Glasses Building 3 Wal-Mart #2989 (510) 651-3301 Rubber Boots Building 3 Wal-Mart #2989 (510) 651-3301 Rubber Gloves Building 3 Wal-Mart #2989 (510) 651-3301 Paper Towels Building 2 Wal-Mart #2989 (510) 651-3301 Plastic Trash Bags Various Sizes of Polystyrene Bags Building 2 Wal-Mart #2989 (510) 651-3301 Building 2 Wal-Mart #2989 (510) 651-3301 Waxed or Freezer Paper Building 2 Wal-Mart #2989 (510) 651-3301 Absorbent Paper Building 3 Wal-Mart #2989 (510) 651-3301 Building 3 Home Depot (510) 490-0191 General Items After Hours Phone # (510) 6513301 (510) 6513301 (510) 6513301 (510) 6513301 (510) 6513301 (510) 4900191 (510) 6513301 (510) 6513301 Individual Equipment (510) 6513301 (510) 6513301 (510) 6513301 Drying & Cleaning Material (510) 6513301 (510) 6513301 (510) 6513301 (510) 6513301 (510) 6513301 Containment Material Sand Bags (510) 4900191 31 Heavy Plastic Sheeting Building 3 Home Depot (510) 490-0191 Scissors Building 1 Wal-Mart #2989 (510) 651-3301 Duct Tape Building 1 Wal-Mart #2989 (510) 651-3301 (510) 4900191 (510) 6513301 (510) 6513301 32 Insurance Provider Contact List: In the event that the company’s insurance provider should be contacted there are some steps that should be done before the call is made. Listed below are the information that should be on hand before the call is made: 1. What is the reason for the call? a. Is the reason something the insurance company can help with. b. Make sure it is not something that a manager can handle. 2. Make sure that you have the company’s member number and any other authentication information before calling. 3. If the call is about an employee make sure to have that employees’ information on hand as well as any other information that might be asked about the situation. During the call to the insurance company: 1. Get the customer support operators name or ID number. 2. If they ask for you name or employee number, give it to them. 3. Relay the information about your inquiry to them and write down all information they give you. After the call is over: 1. Replace any files pulled for informational use. 2. Take all information written down and place it in the corresponding file. For example if the inquiry was about an employee put the information given in that employees file. 3. The date and time of the call should be logged in the corresponding file as well and should also be logged in the phone record list. 33 DigiKnight Technologies Inc. 2725 E. Technology Ave, Freemont, CA 94536 # of Buildings: 3 Key Tracking Form Key Label Key # Key Owner (The Department the Employee Works In) Key Works For LIST ALL AREAS Date Last Verified 1 Mark Saunders ADMN-1 Admin 6-15-06 2 Rod Hatherly ADMN-2 Admin 6-15-06 3 Bea Holdeman ADMN-3 Admin 6-15-06 4 Susan Marcotte ADMN-4 Admin 6-15-06 5 Kendra Bell ADMN-5 Admin 6-15-06 6 Dillon Sommer ADMN-6 Admin 6-15-06 7 Diane Ford SLS-1 Admin, Sales 6-15-06 8 Halle Branson SLS-2 Admin, Sales 6-15-06 9 Natasha Lowe SLS-3 Admin, Sales 6-15-06 10 Thomas Baird SLS-4 Admin, Sales 6-15-06 11 Lorna Hastings SLS-5 Admin, Sales 6-15-06 12 Dwayne Roby SLS-6 Admin, Sales 6-15-06 13 Pam Millard SLS-7 Admin, Sales 6-15-06 14 Katie Barnes SLS-8 Admin, Sales 6-15-06 15 Leonard Filby SLS-9 Admin, Sales 6-15-06 16 Helen Reese SLS-10 Admin, Sales 6-15-06 17 Linda Kraemer MNF-1 All 6-15-06 34 18 Jessica Talen MNF-2 All 6-15-06 19 Andrew Saunders MNF-3 All 6-15-06 20 Cassie Johnson MNF-4 All 6-15-06 21 Annette Watson MNF-5 All 6-15-06 22 Marty Kitzman MNF-6 All 6-15-06 23 Carlton Bowden MNF-7 All 6-15-06 24 Kurt Gossard MNF-8 All 6-15-06 25 Sam Jarosz MNF-9 All 6-15-06 26 Corey Bogdan MNF-10 All 6-15-06 27 Anne Mcloskey MNF-11 All 6-15-06 28 Michael Winters MNF-12 All 6-15-06 29 Bell Rosenburg MNF-13 All 6-15-06 30 Adam Loudy MNF-14 All 6-15-06 31 Katelin Griffin MNF-15 All 6-15-06 32 Lance Addams MNF-16 All 6-15-06 33 Jeffery DeVane MNF-17 All 6-15-06 34 Michael Churchill ADV-1 Sales 6-15-06 35 Aaron McDowel ADV-2 Sales 6-15-06 36 Owen Mill ADV-3 Sales 6-15-06 37 Allison Bell ADV-4 Sales 6-15-06 38 Rebecca McClintock ADV-5 Sales 6-15-06 39 Jessica Williams ADV-6 Sales 6-15-06 40 Brett Kelcey SEC-1 All 6-15-06 41 Frank Arrons SEC-2 All 6-15-06 35 42 Joanna Clark SEC-3 All 6-15-06 43 Martin Burns SEC-4 All 6-15-06 44 Alicia McKellips IT-1 All 6-15-06 45 Luke McDowel IT-2 All 6-15-06 46 Allan Smith IT-3 All 6-15-06 47 Joseph Webber IT-4 All 6-15-06 48 Robert Wildhorn IT-5 All 6-15-06 36 Backup Supply Companies In the event of a key supplier being unable to keep up with our demands for a product that is vital to the success of our company we must have a backup list of potential suppliers for each product. Having a predetermined list of companies to turn to when one supplier is unable to keep up with demands will prevent confusion and maintain our company’s operations without suffering losses due to another company’s inability to meet demands. Since we produce games and coordinate shipping around the world our key product is cases for the games. For that reason we need to have more secondary suppliers for DVD/CD cases than any other product. A list of companies to turn to in case The Tech Geek is unable to produce DVD/CD cases at the rate in which we need are: http://www.discmakers.com 7905 N. Route 130 Pennsauken, NJ 08110-1402 Toll Free: 800-468-9353 Local: 856-663-9030 Dub-It Media Services – Secondary Supplier Hollywood Sales Office 1110 North Tamarind Avenue Hollywood, California 90038 1-888-99DUB-IT Local: 323-993-9570 ISSI Business Solutions– Secondary Supplier 22122 20th Ave SE #152 Bothell, WA 98021 Toll Free: 1-800-660-3586 Local phone: 425-483-4801 Another product DigiKnight needs to continue normal operation is boxes for packaging software. The primary supplier of boxes is Customized Packaging Solutions based out of Sacramento, CA. In case of an emergency then a company to fall back onto for our packaging needs is: The Packaging House, Inc. 6330 North Pulaski Road Chicago, Illinois 60646-4594 1-800-966-1808 The final product DigiKnight needs to continue operating normally is a paper supplier for box inserts. The primary supplier of paper for box inserts is JC Paper based out of Fremont, CA. For an emergency supplier of paper for box inserts contact: Koolprint 37 6750 West Loop South Suite 140 Bellaire, TX 77401 1-888-352-1800 http://www.koolprint.com 38 DigiKnight Technologies Inc. 2725 E. Technology Ave, Freemont, CA 12345 # of Buildings: 3 Supplier Notification Checklist Current Suppliers Give Name / Contact Info for EACH COMPANY Tech Geek CDs/DVDs/Cases Disc Makers (secondary supplier) Dub-It Media Services - CDs/DVDs/Cases CDs/DVDs/Cases (secondary) 1-800-456-0825 1-800-468-9353 1-888-99DUB-IT ISSI Business Solutions CDs/DVDs/Cases (secondary) 1-800-660-3586 Customized Packaging Solutions Inc - Boxes 8333 24th Avenue P.O. Box 278060 Sacramento, CA 95826 The Packaging House, Inc – Boxes (secondary) 1-800-966-1808 JC Paper - Paper (510) 413-4700 Step # Step Comments 1 Fill out order form If we don’t fill out these forms our supplies won’t know what to send us. 2 Customized Packing Solution Inc phone number 3 Find Specific contacts 4 Secondary suppliers 5 Supplier problems We currently do not have the phone number for Customized Packing Solutions Inc. If we want to contact them we need it. We do not have something telling us a specific contact person to talk to for each supplier. We only have their phone number. Are our secondary suppliers still aware we may need them at anytime? Are any of our suppliers having monetary issues or something else that would affect us? Comp leted Done 39 6 Supplier disaster recovery 7 Paper secondary supplier Do our suppliers have a good disaster recovery plan? If they have a disaster it will of course affect us as well. We need a secondary supplier of paper in case something happened between us and JC Paper. 40 Hot Site Information The equipment needed for the hot site backup location will be identical to the main sites equipment. The four servers will be duplicated for the hot site and will be given updates on user information from the off site backup facility. The servers’ hardware will consist of: Dual 3.2 GHz Processors 4 GB of RAM 3 X 500 GB Hard Drive (configured to RAID 5) Windows Server 2003 Dual Gigabit Network Cards 15 Inch Monitor This is the exact hardware specs for the four servers on the main site. Since this is making a partial duplicate of the main site network, the price for this type of plan will be high. The benefits of making a site like this are in the event of a disaster where our main site goes down for an unknown period of time this site can be brought up with minimal time lost. Also, with having the most recent backups on hand there will be minimal loss of data when going from the main site to the backup. With the only main drawback being the cost, there shouldn’t be any reason not to implement this type of backup system as the pros greatly outweigh the cons in this situation. 41 DigiKnight Technologies Inc. 2725 E. Technology Ave, Freemont, CA 94536 # of Buildings: 3 Emergency Operations Center Information Sheet Primary Emergency Operations center Digiknight EOC Site Digiknight Technologies Inc. Building 1 2725 E. Technology Ave, Freemont, CA 94536 415-555-2668 415-555-2622 Site Name Site Location Site Address Telephone Number Fax Number Contacts Name Mark Saunders Telephone Number 415-555-8643 ext 0180 Fax Number 415-555-2622 Name Telephone Number Fax Number Brett Kelcey 415-555-3852 ext 0170 415-555-2622 Comments Comments Mark is the Administrative contact for this facility. Brett is the head security guard in this building. He can be contacted if Administration is unavailable. Alternate Emergency Operations center Tech Geek EOC Site The Tech Geek warehouse 48965 Warm Springs Blvd Fremont, CA 94539 1-800-456-0825 Site Name Site Location Site Address Telephone Number Fax Number Contacts Name Telephone Number Fax Number John Foreman 510-226-9075 510-226-9076 Name Telephone Number Fax Number Maria Woo 510-226-9074 510-226-9076 Comments Comments Primary contact at The Tech Geek. Secondary Contact at The Tech Geek. 42 43 Emergency Operations Center Supply Sheet 1. Flashlights/glow sticks/strobe signal light with spare batteries 2. First aid kits 3. Waterproof ponchos/rain gear 4. Bottled water 5. Sign in sheet/ Employee checklist 6. Towels 7. AM/FM Radio 8. Local area maps 9. Pens/Pencils (Small office set) 10. Rope/parachute cord 11. Garbage bags Flashlights will be important in almost any natural disaster. Most of the disasters that can occur can/will cause power outages. Next are first aid kits which are important as well. If someone should be injured immediate care can be administered. Rain gear should be kept in plenty stock, enough for everyone. Water and the sign in sheet are next. Water should be stored if the Operations center becomes a refuge where people must stay for an extended period of time. The sign in sheet should be completed at an opportune time and checked against an employee checklist to see who is present and who is not. Towels are important as they have many uses in different situations. AM/FM radios are important to have so that news repots and updates on the situation can be heard. Maps of the local area should be kept as well in case people have to move to an unfamiliar place and need to get their bearings. A small office set should be kept with pens and other stationary as these items might come in handy. Rope/parachute cord can be used in many different ways and should be kept at hand in case needed. Garbage bags like the towels and rope can be used in many different ways even as spare rain gear. 44 DigiKnight Technologies Inc. 2725 E. Technology Ave, Freemont, CA 94536 # of Buildings: 3 Emergency Responsibility Chart Position Purpose of Position Responsibilities Disaster Containment Manager Contain Disasters Minimize structural and personal damage Facility Engineering Manager Facility/Utility Recovery Bring equipment back online after a disaster Purchasing Staff Maintain Department Recover full operations Public Relations Coordinator Press Contact Create a news report Human Resource Staff Account for Personnel Account for personnel when a disaster strikes Security Manager Loot and Salvage Protection Secure facility during/after disaster Vital Records Manager Secure Vital Records Secure before disaster Recover after disaster Materials Manager Maintain Department Recover full operations Sales Manager Maintain Department Recover full operations 45 Disaster Recovery Procedures Restore Plan The restore plan implements all of our backup solutions and most people should be able to understand our restore plan. We now know what backup solutions we will be using and the restore plan can be created. Our hardware solution will be RAID level 5 which is an excellent choice. Our software solution is SOS online backup, which we will use for our users’ computers. We can archive our data at our off-site solution with tape backups. This restore plan tells how DigiKnight will implement these different backups by explaining certain policies and procedures. Our servers need RAID level 5 as soon as possible. The data on our servers is probably the most important so we need to get that backed first. RAID is only being used on the servers because using it for host machines would be a waste of money. Once RAID is setup you don’t have to mess around with it anymore because it does the work itself. The first thing to do is to buy a RAID controller and put it in the server. The motherboard must support RAID 5 and the controller also must support RAID level 5. A good controller to buy is PROMISE FastTrak SX4300 PCI-X SATA II Controller Card RAID 0/1/5/10. It supports RAID 5 and also uses SATA II and PCI express. The minimum number of hard drives is three for RAID 5 but four drives would give better performance and faster speeds. If you have more drives, you have a higher chance of two of the drives failing at the same time. When this happens RAID 5 dies on those drives. Only one drive can fail at once. This is why four is a good choice and not some unusually high number. The controller I chose has four connectors so using four drives should work well. Now we can connect the controller to the motherboard and start sliding in the four drives. The four drives connect the four slots on the RAID controller rather than to the motherboard since the controller is already connected to the motherboard. Start up the computer and hit CNTRL-F when prompted by Promise. Set it to RAID 5 and the leave it at the default amount of data for each stripe block. Also enable FastInit for this card because it will be really slow if you don’t. Those are the important options. There may be other options that should most likely be left to default. Save the changes and reboot. Insert the Windows CD and hit F6 to install “Third party SCSI or RAID drivers.” Now insert the CD that came with the RAID controller and the drivers should be installed. Create a partition around 10GBs for the Windows files and use the rest for data. Now you’re set. RAID 5 is installed and working. Use speed test software to see if RAID 5 is working properly. Something like PCMark would work fine for this test, even if it does test more than just RAID. SOS Online Backup is the software backup we will be using on our users’ systems. The first thing to do is to buy the software. SOS offers business accounts which come up as $1800 a year for 100GBs. I don’t think DIgiKnights would need more 46 than 100GBs of backup just for the users. Text files really don’t take up a huge amount of data so I say we purchase the 50GBs for $950. If we need more we can always buy more. Once we buy the software from SOS they will give us the software to install. Users should have their own accounts created and not share with others. This software enables users to share their backed up data easily so sharing an account for that reason should not be considered. So we install the software on each users computer, create an account for each user to log in to so their data is backed up and they can recover when needed. Then we pay SOS either monthly or annually. Either way it is the same price. Users need to know how to recover data. This way if they are missing something they can simply login, search for the file, and restore to their system. Teaching a user how to do this should not take more than ten minutes. Our off-site solution is tape backups. For tape backups, we don’t need to backup our users files, only the sever files. The users’ files are already off-site on SOS’s servers. If two drives of RAID 5 fail we will lose the data that was lost unless we have tape backups. Of course these are off-site so in case of a fire or some other catastrophe we will have these tapes to save us. A good tape drive to buy is Quantum DLT 1 Tape Drive. It costs $849 and holds up to 80GBs per tape at 21GBs an hour. Since tape backups aren’t our primary backups we do not need a super fast drive. We are just using this drive to archive our data and to keep it off-site in case something was to happen to the facility. Tapes also need to be purchased along with a cleaning kit for the drive. Every other week tape backups should be created of the new data. It may need to changed to once a month if the amount of new data is not a significant amount. The tapes should be brought to the off-site location and labeled correctly the day the tape backup was created. Creating tape backups involves a lot of waiting considering the one we are purchasing isn’t a high end drive. One person needs to setup what data needs to be copied and then let the drive do its thing and go back to their normal schedule. This preferably should be an IT person that works by doing what task “needs to be done today.” Implementing this restore plan can be done by a lot of people but should be done by the professionals at DigiKnights. The combination of RAID, SOS, and off-site tape backups is really a good one that keeps all data at DigiKnights safe. Every part of the organization’s data is backed up and also off-site somewhere. One thing that should not be forgotten is to test the backups. This applies to the tape backups more than anything else. If these tape backups aren’t tested and there is a fire at the facility and all our servers are gone, DigiKnights will be in a load of trouble. Just having backups doesn’t mean they will work. SOS should also work well with users but I’m sure there will be users who will not like it or blame causing them to lose files. This restore plan fits DigiKnights very well and should keep them safe for a long time. 47 File Retention Plan: All files that have private information with relation to the company’s employees, financial outlook, business strategy, and clients will be kept in a secure location(s) for a minimum of three years. When it is time to get rid of old information the documents will be incinerated or deleted when dealing with information stored on electronic media. With the exception of client information, this will be the procedure for all documents that are destroyed when they pass the three year mark. Client info will be destroyed as well, but only after being offered to the client first and with their understanding that should they not take the documents, they will be permanently destroyed. Breakdown of documents that should be kept: Employee records Legal documents such as Deeds, Power of attorneys, and contracts of any kind. Client information records All financial transaction records between the company and employees, outside contractors, and clients. 48 DigiKnight Technologies Inc. 2725 E. Technology Ave, Freemont, CA 94536 # of Buildings: 3 Disaster Confirmation and Declaration Report Page 1 Disaster Classification Of 2 Page(s) Catastrophic / Major / Minor Description: Loss of all electrical power to all three buildings of the organization. Confirming Manager Confirming Source (1) Name Alicia McKellips Name(s) Brett Kelcey Department IT Title(s) Manager of Security Telephone 415-555-8352 Telephone 415-555-3852 Fax Fax Confirming Source (2) Confirming Source (3) Name(s) Mark Saunders Name(s) Linda Kraemer Title(s) Manager of Administration Title(s) Manager of Manufacturing Telephone 415-555-8643 Telephone 415-555-6161 Fax Fax Comments: Unknown the extent of time the buildings will be without power. Backup generators only capable of running the production facility long enough to properly shut all equipment, avoid further problems from arising. In the event of a catastrophic event contact Alicia Mckellips, IT manager, who is capable of officially declaring when a problem has become a disaster and organizing the emergency operations center. Alicia McKellips will designate orders to the department heads on what to do 49 and where to go. Emergency response team should have a predetermined meeting place and await Alicia McKellips orders on how to proceed. If Alicia McKellips is unreachable, contact one of the following managers: Brett Kelcey manager of security, Mark Saunders manager of administration, or Linda Kraemer manager of manufacturing. Any of the previously mentioned managers are a confirming source for a disaster and will be able to either contact Alicia McKellips or act in her absence. Each of the managers that have been chosen to be a confirming source were chosen for a specific reason. Alicia McKellips is the confirming manager since she is the head of the emergency operations center. Brett Kelcey has been chosen as a confirming source since he is the manager of security. As manager of security he has access to the entire local facility and therefore a good confirming source. Mark Saunders is manager of the administration department and therefore is in essence the head manager of DigiKnight especially building one. If anything should happen in building number one Mark Saunders should be contacted first hence the reason for his being a confirming source for the entire local facility. Finally Linda Kraemer, manager of manufacturing, has been chosen for the same reasoning that Mark Saunders was chosen. Linda Kraemer is the manager of building number three and hence the decision maker for that building. If a disaster should occur contact one of the above mentioned managers or meet at the predetermined destination. At the predetermined destination one of the managers will be able to confirm there has indeed been a disaster and will begin working with Alicia Mckellips on setting up the emergency operations center. 50 DigiKnight Technologies Inc. 2725 E. Technology Ave, Freemont, CA 94536 # of Buildings: 3 Maintenance Priority Ranking Ranking (Top Priorities First) Maintenance Process 1 Check for Broken Equipment 2 Test your backups 3 Test fire alarms 4 Fire extinguishers 5 Check for leaks 6 Test backup equipment 7 Check locks 8 Empty Trash/Clean floors 9 Check for humid areas 10 Pest control Reason for Ranking DigiKnight has a lot of technical equipment and if something breaks it needs to be replaced as soon as possible, otherwise lots of production time is lost (which is money). What’s the point in making backups of important data if you don’t whether it works or not? If your data becomes corrupted and you find out the backups don’t work, this will cost the company more money and you won’t have a job anymore. This doesn’t have to be done often but you need to know that the fire alarm works. If there is a fire and everyone is still sitting at their desks people could easily die and the facility would be burn down much faster without the fire department being aware immediately. Make sure you have fire extinguishers. Fire extinguishers can put out what could become the DigiKnight’s death. Make sure no water is getting in especially if it is actually raining at the time. Leaks still need to be checked for often because they can cause a good amount of damage to your equipment. This is things such as backup lights that would be used in the emergency operations center. Make sure that if a disaster occurs the backup equipment you have in place will actually function. DigiKnight can’t have random people coming into their facility taking whatever information they can find. The facility needs to be clean otherwise there will be garbage/germs everywhere and people will start calling in sick which means DigiKnight will lose money. If mold starts to grow you have to know about it because the earlier you know about it the easier it is go get rid of. If you keep checking for leaks this probably won’t become a problem. If there is an infestation present, pest control can be called and will deal with it fast. Otherwise call in pest control to clean twice a year or so. 51 11 AC Filters Air conditioning filters need to changed for cleaner air. Paper Records Recovery Water Damage: Paper is fragile especially when wet. Thus it must be handled with care. There are several ways to handle water damage. The first is air drying. Air drying is most suitable for smaller quantities of items. It is just not efficient enough to properly dry larger quantities. All items should be placed in a room with a humidifier keeping the humidity below 20%. The higher the humidity the more likely mold will grow. Room temperature should be kept below 70 degrees. Fans must be going in the room at all times to keep the air circulated. This greatly helps to prevent mold. For books, you want to take each book and stand it up on its end, open at a 90 degree angle. Place unfolded sheets of paper towels between groups of pages. You can also put one under the books. Periodically change the paper towels and flip the books over onto their opposite end. After the drying process books will most likely have to be rebound. Paper documents can be hung up on a drying line or laid out on sheets of drying paper. They should not be stacked more than 1/4inch high. The next method of recovering water damaged documents is freeze drying. Freeze drying can dry a much larger amount of items. They are literally placed in a freezer and frozen. The freezer must be kept between -10 degrees Fahrenheit and -40 degrees Fahrenheit. While freeze drying works better than air-drying and eliminates the chances of mold, it can take 4 to 18 months to finish the drying process. Another method of saving documents from water damage is vacuum drying. With this method, items are placed in a chamber where a vacuum is introduced and the temperature is brought to just above freezing. This method can cause a lot of distortion in books, and also is not good for photographs. For larger quantities of damaged items, it is more cost effective than air drying. The last method of drying is vacuum freeze drying. With this method, the damaged items have to be transported to a special facility via refrigerated truck. There, they are placed in a vacuum chamber and frozen until dry. This method is often so good that books do not have to be re-bound. However it is not so great for photographs. Fire Damage: Documents that have been damaged by fire are also very fragile. They should be placed on absorbent paper to remove any moisture left in them. Carry any documents by the absorbent paper, not by the document itself. Any documents that are not critical should be discarded. Other documents can be photocopied if possible. Books have a tendency to be less flammable than a sheet of paper. This is because there is no space for air in between the pages. Even if parts of books are damaged or destroyed it may be possible to recover the rest. In really bad cases there are companies that deal with fire damage. They can attempt to remove charring and have specialized deodorization techniques to remove the smell left behind from smoke. 52 Sewage Damage: Any documents damaged by a sewage leak need to be decontaminated. Document recovery specialists have special decontamination solution that they use on the documents before they dry them. This must be done otherwise when the documents have dried, substances will remain inside of the fibers of the paper and can be toxic. 53 Customer Disaster Notification This is to notify you that DigiKnight Technologies Inc. has experienced a serious incident. A (insert incident) occurred that has temporarily halted shipping and production. This may impact your order by late shipments. A detailed recovery assessment is now underway. We will contact you again within 24 hours with a full update to the situation and any impact it may have on your open orders. Thank you for standing by us in this moment of adversity. If you have any questions, please contact Michael Churchill at 415-555-3970 x0400. Supply Chain Breakdown Jim Thompson issued the following statement today regarding the problems caused at Digiknight due to the recent hurricane in Louisiana: “I met with Steve Gibson and Cody Belkin at Principal Metrics, our chief supplier of electronics components today to discuss the severe interruption of shipments. Because the main production facility is located in New Orleans, it effectively no longer exists as a viable operation. The facility has been heavily damaged by the storm and electricity has not yet been restored to the region. Even if the plant had power, it is unlikely that the facility is in any condition to manufacture anything, much less sensitive electronic devices. The company is still taking orders and producing parts at a smaller secondary facility in Kentucky, but obviously, order turnaround is extremely reduced. While we at Digiknight wish to remain loyal to Principal Metrics, for the security of our business and the welfare of our customers, we must now establish a relationship with a new vendor who is capable of meeting our production demands. To that end we have entered in to discussions with several reputable organizations and will be selecting one as a business partner by the end of the week. Until we are able to able to return to normal operating levels, we ask that our customers and partners who depend on our services be as patient as possible considering recent events. While we value our relationship with each and every one of our customers and hope that they will all stay on board with Digiknight, we realize that some customers may find it necessary as we have to find a new vendor. We hope that upon return to normal production levels, those customers who turn to another vendor consider returning to Digiknight. It is estimated that the New Orleans facility used by Principal Metrics will not be operating at full capacity for a minimum of one month. We will be in contact with the production manager there on a frequent basis and will keep our customers as up to date as possible with their progress. In the interim, we invite you to contact our Public Relations Representative, Jessica Curry. She will be devoting her full attention to this issue and is happy to answer any questions that customers, press, or other interested parties may have. 54 Sincerely, Jim Thompson Division Manager Digiknight Family Employee Statement Policy To the families of our valued employees, In light of the recent disaster that has affected many of our daily lives; we at DigiKnight Technologies extend our deepest sympathies to all that have experienced the disaster. Our employees and their families are an important part of our company family and we will be there to support in any way we can. We will make it our goal to help with the recovery efforts and should anyone need aid we have set up a support line for such inquiries. Listed below are help lines setup by our company and other relief agencies. Again we want our employees and their families to know they are not alone and DigiKnight will be there to aid in any way we can. Greatest Respects, DigiKnight Management Staff DigiKnight Relief Helpline: 1-800-567-8843 Red Cross Helpline: 1-800-RED-CROSS Government Relief Helpline: 1-800-WHATS-GOINGON 55 The Interim Plan Backup Plan In order to decide what products should be used for backing up our data and assets we first need to research what products would work best for us. Certain solutions may not suit our organization very well but would work well for others. This is why a number of solutions will be compared to find the best one for our organization. I will compare three hardware solutions, three software solutions, three off-site solutions, and make my recommendation for which solution is the best of each category. The first hardware solution I will discuss is RAID. RAID stands for redundant array of independent disks. RAID has multiple levels that have different functions and I am choosing RAID level 5. RAID level 5 gets the biggest bang for the buck. Other higher level RAID levels are more efficient but are much more expensive and also expensive to implement. RAID level 5 works using many of the other qualities of lower level RAID levels. First you need three drives to implement RAID level 5. Data is separated into multiple pieces and each piece is placed on a different drive along with the parity on a different drive. This way if a drive fails it will it can combine the blocks on the working drives along with the parity block to get the data back. RAID level 5 is also one of the faster levels of RAID. It has the highest read data transaction rate. The best thing about RAID is that it does not require human intervention. A big problem with backups can be human error but with RAID, humans don’t have to do anything other than implement it. I found a 4.2TB (16 300GB Drives) RAID level 5 SATA II rackmount for $7000. RAID should be used for server backups and not for personal computers. One of the best things about RAID is that the data is always ready to be restored and is being backed up all the time. In most cases data will be backed up once a day and if something new is created that day and is lost in the same day, there may not be a backup of it unless of course RAID is being used in this situation. The second hardware solution is tape backups. Tape backups are a simple process. Tape drives are used to copy as much data possible onto them which is the backup of your data. It is an actual physical tape that will need to be stored somewhere. Tape backups have been used for some time and have rather slow transfer rates. Faster tape backups can be bought but it comes at a price of course. HP sells a StorageWorks DAT 40GB Tape Drive for $1124. This tape drive stores only 40 GB of data but can transfer at up to 23GBs an hour. Some of the different types of tape drives are DAT, DLT, AIT, and LTO. LTO has the highest storage per tape and the fastest transfer rate. LTO can go at up to 216 GB an hour for 400 GB tapes. These tape drives cost $4000 with each tape costing $36. Tapes aren’t the most reliable backup so they need to be kept clean and in a safe area. Doing tape backups manually starts up the human error process. Everyone can have a bad day and not pay attention to what they are doing and can easily destroy an entire tape backup. I will say right now that tape drives are good for archiving all your data. All of these tape drives use a SCSI interface. 56 The third hardware solution is using any sort of removable media other than tape drives. This can include anything from floppies, Zip drives, CDRs, DVDRs, and external hard drives. This is used more in small businesses and also has the human error factor to it. Writing your data to CD-Rs or DVD-Rs can take a long time seeing as how the transfer rate is rather slow. CDs and DVDs can’t hold a lot of data so that is definitely another disadvantage there. External hard drives would be the best choice for removable media but it transfers would still take a long time and do it all manually. That is worst part about using removable media for backups; everything has to be done manually. There is no automated way to do it. If you use CDs or DVDs there will be a lot of them and they will need to be labeled properly. Considering CDRWs and DVDRWs would also be a smart thing. The rewritable media would be better overtime but it is expensive. However if you want to archive it all you shouldn’t buy rewritable media. All of these hardware solutions will also include a power backup system. A large UPS system should be purchased and APC sells an “industrial” UPS that is designed for “equipment in harsh industrial environments. “ APC says it works well for manufacturing floors, process automation, and control rooms. Considering DigiKnight does a lot of manufacturing so this should suit us well. It is very important to have some sort of backup power to keep the process going until it can be effectively stopped. It is also important for a meeting in the Emergency Operations Center. We need a UPS to support our computers as well. If the power goes out there needs the UPS needs to have enough power so we can save the data that is currently in the RAM before the computers are properly shutdown. The first software solution is Acronis True Image. The main purpose of Acronis True Image is to of course make exact images of your hard drive. You can store this on anything from a CD to an external hard drive. This makes storing data on your tapes or other removable media much easier. Also, it comes with its own DVD burner. Apparently it takes “15 minutes” to back up your entire drive to an external drive. Whether or not this is the image creating process or the transfer process is not known. The official website of the product doesn’t show the speed of creating the image which means it’s either slow or most products are the same. Either way Acronis is only $50 which isn’t bad at all. It has other features such as editing an image but these other features aren’t very important. The next software is solution is SOS online backup. This is different from Acronis. This works by installing SOS on the client’s computer and telling SOS which files to backup. You then set a time for SOS to backup the data, probably nighttime, and then during that time SOS will backup the files to a global network of SOS datacenters. SOS will only send files that have changed and will not keep sending the same files every night. This will save a lot of time if it actually works. A lot of backup software will keep backing up the same files no matter the case and not check for new or modified files. It will send the files in compressed format to reduce the transfer size. The options for backing up files can get very specific which reduces backing up non wanted files. Although why would someone have files that they do not want to backup? When you 57 end up losing your data from a virus a failed hard drive you open up the program, login, and select the files you want to recover. When the data is backed up it is encrypted on the user’s computer, again when it is sent, and encrypted when it is resting in storage. SOS also has some share feature to share any data with someone who has an email address. Unlike Acronis, SOS requires a monthly fee. This makes it much more expensive and considering off-site capabilities, it is probably worth the money spent. The third software solution is LiveVault Online Backup Service. This is very similar to SOS online backup but there are differences. With LiveVault, your data is continuously backed up when your data changes. It seems as though this would cause problems with computers slowing down since every time a new file is created it will begin backing up the file. However they are trying to achieve what RAID does and have your data safe 24/7. Just like with SOS the data is stored in an off-site datacenter. You can login to any web browser and whichever computer the login is for, that computer will now be accessible for LiveVault options through your web browser. Prices are not given because they want to you do the trial but it is a monthly price. I didn’t read anything about encryption which isn’t good. The first off-site solution is tape backups. I have already discussed tape backups a lot as a hardware solution so I’ll discuss how it would help as an off-site solution. Tape backups are very good for archiving A LOT of data. Some of these tapes can hold an incredible amount of GBs and archiving your data for many years is a good idea. Some day could come when you are in court and something is needed to prove innocence. Tape backups don’t have to be your main source of data backup but they can be your off-site choice. The backups will need to be delivered the off-site facility as soon as possible after the backups are created. Tape backups shouldn’t take up too much space if the large size versions are used. These tapes need to be kept somewhere clean and safe and they need to be tested. Having backups that do not work is a large waste of time and money. The second off-site solution is SOS online backup. I have also already talked about this product and it isn’t a hardware backup. This solution is extremely easy. If the facility burned down and you used SOS for all your systems there shouldn’t be a problem when it comes to lost data. You will just need to login to the software and choose what files you want to recover. The only thing that could possibly be hard about using SOS is the paying the monthly fee. Other than that it is safe because of the three tiered encryption method. This encryption may slow things down but it is secure. The third off-site option is LiveVault Online Backup Service. I have talked about this as well. It works the same as SOS except it backs up data instantly as it changes. The recommended hardware solution is RAID level 5. I think RAID is much more efficient than tape backups and removable media is just a joke compared to RAID and tape backups. Tape backups removable media created solely for backups so they will be better than any removable media out there. RAID is better than tape backups because it does not require human intervention and it is alive and ready to restore any 58 lost data 24/7. With tape backups that data isn’t backed up until it is actually transferred. RAID is there waiting to fix any failed drives. RAID cannot back up the entire organization though because there needs to be some sort of off-site solution. RAID probably costs slightly less than tape backups in terms of capacity and paying people to do the tape backups. Once RAID is implemented you really don’t have to mess around it with much anymore. It is good to go. The recommended software solution is SOS online backup. First of all Acronis doesn’t do much. It just creates and image for you to place on some removable media. There are free programs out there that can do this if it is really needed. SOS and LiveVault come much closer than Acronis. The primary reason SOS is better is because it uses three levels of encryption. LiveVault just sends all your files unencrypted to the LiveVault datacenter. LiveVault brags about its “24/7 backup” but this seems as a disadvantage to daily backups. When you create a file, LiveVault will start creating a backup of it and slowing everything down. This will happen a lot which means lost production which means lost money. Since RAID is being used for the servers this wouldn’t be a bad choice to backup data on users’ computers. The recommended off-site solution is tape backups. Even though I didn’t choose tape backups as the hardware solution, they are still great for archiving your data. If you wanted to keep all your data for years with SOS or LiveVault you would be paying a monthly fee the entire time. With tape backups you just buy the drive and the tapes. These tapes however would be used to backup critical files first and foremost and the files on users’ computers will be on the SOS off-site datacenter. Why make tape backups of if they are already off-site somewhere else? Tape backups are a great solution for critical server files and configurations. Organizational Contact Information Department Employee Dept. Phone Extension Administration Administration Sales Sales Manufacturing Manufacturing R&D R&D Maintenance Maintenance Advertising Advertising Shipping Mark Saunders Rod Hatherly Diane Ford Halle Branson Linda Kraemer Jessica Talen Carlton Bowden Kurt Gossard Michael Winters Bell Rosenburg Michael Churchill Aaron McDowel Kenneth Gilliam 415-555-8643 415-555-8643 415-555-6312 415-555-6312 415-555-6161 415-555-6161 415-555-3223 415-555-3223 415-555-3970 415-555-3970 415-555-3131 415-555-3131 415-555-6431 0180 0181 0200 0201 0150 0151 0100 0101 0400 0141 0160 0161 0130 59 Shipping Purchasing Purchasing Security Security IT IT Derrick Cunningham Katherine Cavenaugh Shay Robertson Brett Kelcy Frank Arrons Alicia McKellips Luke McDowell 415-555-6431 415-555-3298 415-555-3298 415-555-3852 415-555-3852 415-555-8352 415-555-8352 0131 0120 0121 0170 0171 0190 0191 60 Keys Keys are important to DigiKnight Technologies. Controlling access to certain parts of the facility is not a difficult task but it must be done correctly. Documentation should show who has access to what parts of the facility. In the case of passwords, this information doesn’t necessarily need to be documented. In fact, since Administrators have access to everyone’s password they should not be documented. Another consideration is what rights and privileges users have on the network. For instance, accounting should not be allowed to read or modify all documents on the network. Using traditional keys versus electronic keys is an issue that has come up in a lot of companies. Electronic keys are superior in many ways but also have their disadvantages. Traditional keys are very cheap and are something you carry with you. Electronic keys can be something you are, meaning something such as biometrics. Keycard IDs are essentially the same as traditional keys easier to keep track of. Unfortunately they are more expensive to set up. Certain people may have problems with keeping track of multiple traditional keys, but keeping track of one key card should not be a huge problem. If you require people to wear their key card and show it all times the chances of them losing it drops significantly. If certain people tend to “lose” their keys a lot, they should no longer be given keys. Something should be changed so they can access what they need to without the risk of a random person finding a key to access this information. Biometrics is another access control method that is far more secure than traditional keys and key cards. People do not have to carry an object with them to gain access when biometrics is used. The authentication is part of their body such as fingerprints, or eye retina. The reason why biometrics are not used much today is because of the cost. Nevertheless It is well worth investing in a simple fingerprint authenticator for the critically important assets of DigiKnight Technologies. Passwords are the least “secure” form of authentication. However, passwords should be always be used as a multiple form of authentication. The more keys/passwords put onto something the more secure it becomes. The passwords given should be complex using letters (in lower case and upper case), numbers, and special characters. They should be at least ten characters in length and a new password should be given out every 60-90 days. Passwords are obviously the cheapest form of the authentication and require very little effort to implement. Passwords should not be relied on to secure the most important assets of DigiKnight Technologies. 61 Test Scenarios & Continued Maintenance DigiKnight Technologies Inc. 2725 E. Technology Ave, Freemont, CA 94536 Power Outage Test Scenario Date Prepared 8/2/06 The Test will be conducted on: Scenario Leader: Alicia McKellips 10/15/06 The Test will last for 4 Hours Description: In this scenario it is imagined that an automobile accident down the road resulted in a power outage for anyone in the area. Since this is a business area and the power company workers already know the location of the problem, the power should return fairly soon. Servers must be shut down properly to avoid any data loss. The proper department employees must contact the power company to find out what is going on as well as contact any customers that may have a concern. Customers that may have delayed shipments are especially important to contact. The manager from every department will participate in the testing of this scenario as it applies to everyone. Each manager must know what their employees should be doing. This includes employees that are not directly involved with recovery. Safety precautions must also be taken to be sure that no employee gets hurt stumbling around in the dark. Everyone should know to keep doors closed since if the power is out, the AC is out as well. Purpose: Power outages are common occurrences for anyone on the power grid. If the power goes out the entire business will be shut down and production will be suspended until it is restored. This is a major concern for DigiKnight. Everyone must know how to deal with this situation to get the maximum amount of work done while also trying to restore power. Servers must also be shut down properly or data loss may result. Employees must know what to do or they may not remain calm and may be unable to assist in the recovery process. Understanding is critical to recovery and maximum productivity. Major Individuals Involved Alicia McKellips Mark Saunders Brett Kelcey Katherine Cavenaugh Kenneth Gilliam Michael Churchill Michael Winters Carlton Bowden Linda Kraemer 62 Diane Ford DigiKnight Technologies Inc. 2725 E. Technology Ave, Freemont, CA 94536 Date Prepared 8-6-06 Scenario Leader: Mark Saunders Nature Based Test Scenario The Test will be conducted on: 8-21-06 The Test will last for 5 hours Description: This is an earthquake test because an earthquake is the most likely large disaster to happen at DigiKnight Technologies. This test will involve everyone at the facility. The test earthquake is a large earthquake that could possibly destroy the facility, which is what we need to test for. Everyone in the manufacturing rooms will be told to get out of those rooms into the closest department rooms to them. The manufacturing rooms have the largest equipment and the first thing to do is get away from large equipment. People will attempt to exit the building as fast as possible in an orderly fashion. This means people closest to exits of the facility should leave immediately. If someone is in a room where are all exits are blocked of they should take cover under something that can break the fall any other objects. Purpose: The purpose of this is to obviously keep people alive. Since this test earthquake is assumed to be a large one that could destroy the facility our first priority is to get people out of the building. Saving equipment will be hard to do but some things may help. All computers, servers, or other data will need to be left behind. We will lose the actual hardware but we will still have our data backed up off site. The building and other large equipment should be insured so that is another reason why people come first. Sure the equipment brings us more money but lawsuits can come up if people start dying when there was a way to keep them alive. This test won’t be easy to emulate because earthquakes don’t last a long time so everything needs to be done immediately. Since things have to be done so quickly, it needs to be tested so everyone knows exactly what to do in case of an earthquake. Major Individuals Involved 63 Mark Saunders – Administration Manager Linda Kraemer – Manufacturing Manager Carlton Smith – CEO Michael Winters – Maintenance Manager Brett Kelcey – Security Manager Alicia McKellips – IT Manager Administration staff 64 DigiKnight Technolgies Inc. 2725 E. Technology Ave, Freemont, CA 12345 # of Buildings: 3 CD / Paper Plan Update Checklist Process # Process Title Purpose 1 Burn new revision to discs. Discs are to be distributed to employees so that each employee can have a copy of the disaster recovery plan. 2 Clearly label discs with the date. Mislabeled discs may result with someone referring to an older version of the plan. 3 Collect old copies. This helps prevent employees from being unsure of which revision to refer too. 4 Hand out new copies. This step provides each necessary employee with an updated copy of the disaster plan. 5 Email users. This step allows for any employees that may have been skipped to be sure they receive a copy of the new plan. 6 Destroy old discs. This prevents the old copies from being mistakenly referred too while also preventing anyone from outside the company from being able to read the plan. 65 DigiKnight Technologies Inc. 2725 E. Technology Ave, Freemont, CA 12345 # of Buildings: 3 Intranet Document Maintenance Checklist Process # Process Title Purpose 1 Server up? If the server isn’t up there won’t be an Intranet to look at the plan. 2 Plan on the Intranet Now that the server is up, the plan should be on the Intranet or people can’t find the plan. 3 All pieces of the plan The whole plan needs to be on the Intranet, it can’t be bits and pieces. If anything is left out people could spend a lot of time looking for something that isn’t there. 4 Update Access 5 Updated? 6 Organized 7 Update Notes Someone should be noting when the intranet is updated and what the update was at that time. 8 Access to Intranet Not all random people should have access to this intranet. This is a bigger priority in other cases, but in terms of looking at a backup plan, this isn’t the top priority at all. 9 Typos, Grammar, etc. Grammar, typos, and other things should be corrected in the plan. Not everyone should have access to update the plan because everyone would have their own little suggestions that may be realistic or just jokes The plan should be updated on the intranet because if someone else has the updated plan but the intranet does not, people will be doing the different things. Plus the updates are to help the plan work better. The intranet needs to be organized so people can find where the actual plan is go directly to the part they need to find. 66 Tabletop Test: Mudslides 1. Confirm a meeting with President: We need to talk to the President. He has to write off on all testing. Although this is a tabletop test only we will be taking a large percentage of the managers from their daily tasks. This is something that requires confirmation from the highest levels. 2. Send Email to every manager: We need to contact all relevant individuals of a meeting. 3. Confirm an RSVP for each manager: We need to make sure there are no major conflicts with the managers. Any managers who we don’t get an RSVP from need be contacted in person. 4. Choose a leader for the test: Someone needs to be given responsibility for the complete organization of the test. This person needs to be familiar with all aspects of the company. A person experienced in mudslides will be especially useful. 5. Plan the tabletop test: Before the test even begins we need to create an agenda. This includes what topics will be discussed, what results we expect to achieve, and everything else related to the test. This section includes researching all relevant information on mudslides. Copies should be made in preparation for the tabletop test. 6. Prepare physical supplies. Things like cups, water, donuts, paper, folders, all need to be grouped in one area before the test. If these things are not in place before-hand time will be wasted during the actual test. Since we are already decreasing productivity this is unacceptable. 7. Make a final confirmation. The day before the planned testing every manager should again be contacted. Testing is important and every individual needs to be there. 8. Hold the meeting. This stage is for the actual tabletop test. Mudslides should be discussed. The disaster recovery document should be reviewed. The entire emergency procedure for mudslides needs to be discussed. Errors should be noted and full documentation of the meeting should be collected. 9. Debrief. After the meeting the core recovery team members should review the changes to be made to the document. A final report should be given to the President. If a small scenario testing scenario is planned the above steps should be repeated again on a larger scale. 67 Paralipomenon DigiKnight Memo Kevin Brunch IT Department Team Member Dear DigiKnight Technologies Incorporated Employee: As of June 4th, 2006, DigiKinight Technologies Incorporated will begin a project to create a working document establishing the plans and procedures to follow in the event of a disaster affecting the company’s network infrastructure. The recovery document will be a step by step process to follow for each department and will contain a different plan of action for an array of disaster scenarios. Although some departments may already possess a recovery document, this project will include all departments as well as how each department will interact with others in the event of a disaster. The project is will end no later than August the 7th of 2006. During the length of the project a minimum of one person per department will be needed to participate in the creation of the recovery document. However, every member of the team will not be required to attend each meeting. Only days in which input from your department is needed will members be required to attend. The project team is scheduled to meet twice a week on Mondays and Wednesday s from 4:30 to 5:30 p.m. The department manager for each department will decide as to which team member will be able to participate in the project. The member from each department will need to have full knowledge of the function and procedures of the department. They do not need to be the most experienced or head of the department. The project team member must be knowledgeable enough to provide input as to what actions and plans are applicable and useful to their department. Each project team member will also need to be capable of researching any additional information about the department for specific disaster issues. Any employees with previous experience with disasters recovery are encouraged to speak with their department managers about potentially helping with the project. Although some departments may already have a recovery plan it is important to create a disaster recovery plan that encompasses all aspects of the company in one document. While one department may have created a recovery plan it will not be take into account outside issues or the totality of business continuity. A universal disaster recovery plan is needed. Any previous disaster plans that have been created by individual departments will be used in the planning of the organization-wide disaster recovery plan. The organization-wide disaster recovery plan shall incorporate all previous disaster planning into a detailed plan of action useful should virtually any situation that may occur. Without a detailed list of procedures the only plan of action is to ad lib the recovery process, which inevitably leads to mistakes. There are many items to consider during the planning of the disaster recovery plan. It must be planned thoroughly. In the event of a disaster how long could the department continue to 68 operate before having to shut down? Who will execute the plans? How much warning time is there before the disaster occurs? These are just a few items the project team must consider, not only for each department, but for the entire company as well. Each department will have different requirements in different disaster scenarios. Such is why one person per department will be needed to participate in the creation of the disaster recovery document. During the next few months we will appreciate all assistance and cooperation with the project team. If you wish to be a member of the project team please contact your department manager. Any comments, questions, or concerns about the project can be direct to your department manager or to the project lead, Joshua Wisman. Thank you, Project Team Interim Plan Memo Sir, As the Disaster Recovery and Management Team compiles the Disaster Recovery Plan I would like to suggest and recommend that we concurrently design and implement an Interim Plan in the event of an incident before the completion of the Disaster Recovery Plan. It would be highly unfortunate and damaging if the company was caught “with its pants down” and suffered a heavy loss from a disaster of some sort while it was in the progress of compiling a disaster recovery plan. To that end, I suggest the following steps: 1. 2. 3. Form a separate sub-team to compile the Interim Plan Task this team with assessing the immediate disaster recovery needs of the company. The team will need to do the following things: Compile a list of key personnel and contact information Collect a complete set of keys to all critical areas and passwords Compile a list of service contracts and appropriate contact information Compile a list of vendors and appropriate contact information Complete a walk-around asset inventory Compile a software asset list Compile a list of critical business processes Compile a prioritized list of critical restoration activities Compile a list of any toxic materials stored and their locations Compile a list of all emergency equipment and its locations Compile a list of all first responders (EMT, fire) 4. 5. Assign the team the job of compiling all of the above information in to a cohesive, interim disaster plan Test the plan Designing a plan such as this for short-term needs will help protect the company in the event of a disaster strike before the completion of the main plan. It is absolutely essential to protect the company and its interests now, not in six or nine months when the full plan is finished. The goal is to complete this plan in no less than one month’s time. 69 Thank you Chris Saltzman Backup Memo Dear Mr. Smith: Our company creates and uses a wide variety of important data including customer information, Research & Development Projects, as well as private financial information. Were this data to be lost our company would be hurt dramatically. It is for this reason that we have prepared a backup plan. Each computer contains, at least in part, vital data. Certain computers do however have more important data that require different backup strategies. Thus we have different backup plans implemented specifically for each department. The plans are as follows. Administration Department: 10 Computers. The Purchasing Department’s primary records are contained with the server database. There is no department specific backups. Sales Department: 15 Computers. These computers contain the majority of the short term financial records. This data is potentially extremely important. While we would like to backup each computer, that is financial prohibitive. We suggest that the Sales department turn one of their computers into a server. We can then perform a full Grandfather-Father-Son backup on that single server. Monthly full backups would be archived. Weekly full backups would be saved for a month. Over the week differential backups would facilitate the speed of data recovery should the backups be necessary. Until we can convert one of these computers to a server we intend to perform daily incremental backups and a single full monthly backup that is saved offsite. Restoring that data could potentially be extremely time consuming, hence our plan to add a storage server. Research & Development: 3 Computers. R&D contains some of our most vital information. As above, all computes will be protected with a full GFS system. Since speed is not necessary the “son” backups will be incremental instead of differential. Shipping Department: 4 Computers. The shipping department keeps a record of shipments made and received. While this data is important most of it can be reconstructed as necessary. Also their data along with the Purchasing department is almost all contained with the IT servers. As such there are no special backups for this department. Purchasing Department: 3 Computers. The Purchasing Department’s primary records are contained with the server database. There is no department specific backups. Advertising Department: 5 computers. The advertising department keeps track of past, ongoing, and future advertising. Contained within the computers are the artwork and slogans related to this task. In an emergency this data is not strictly necessary, but we have decided that occasional backups may facilitate a faster return to “normalcy”. Thus we have decided to perform weekly full backups that are maintained on-site. A yearly backup will be archived. IT Department: 10 Computers. These computers save all their files to the servers. The workstations contain minimal information. There will be no IT backups for the workstations on a scheduled basis. IT Department: 4 Servers. The servers contain the most important information in the company. To maintain server usage only one server will be backed-up at a time. On Monday 70 Evening Server One will have a full backup. One Tuesday Server Two, Wednesday Server Three, and Thursday Server Four. Every third backup will be sent offsite. Regarding all backups tapes: Each tape will be labeled with the department and computer that the backup is for. Each backup will be tested immediately to confirm its success and usability. Archived backups will be sent via truck to the offsite location. Onsite backups will be kept within a cabinet located within IT. Since we already possess Traven tape drives all backups will be made on Traven tapes. The Purchasing department is responsible for purchasing as necessary. Our offsite backup location will possess two working Traven drives in the event that a disaster destroys our drives. A member of IT to be chosen, will be responsible for performing the backups as part of his job duties. The above is a summary of our backup plan. Should you have any questions pertaining to our disaster planning please contact the project’s leader, Josh Wisman, Robert Drake (myself), Rick Osgood, the documenter, Matt Smith, Kevin Bunch, Alexander Andrews, or Christopher Saltzman. Thank you, Project Team Disaster Center Memo Sir, I wrote to you several weeks ago to bring to your attention and discuss with you the necessity of an Interim Disaster Recovery Plan. I thank you for your time and consideration of this matter and ask that you devote the same attention to the subject of this letter as well. An important component in the Disaster Recovery Plan of DigiKnight is the establishment of an off-site Emergency Operations Center. In short, a facility located in a different region outfitted with the capabilities of running the business-critical operations of the company should the main facility be disabled or otherwise unusable. The most important function of this emergency facility will be communications. The facility will be a center point for all disaster recovery and management communications. The three most important functions of the EOC will be as follows: 1. 2. 3. Command and Control Operational Control Recovery Planning To this end, it will be necessary to locate the facility somewhere far enough away to be unaffected by any large-scale disaster that strikes Phoenix, but close enough to provide close recovery support for the main facility. Northern Arizona is unacceptable because of heavy snows during the winter. The DRP team recommends a facility in Sierra Vista, a small town in 71 Southern Arizona. Because of the proximity to Fort Huachaca, we may be able to enlist the support of the military. The EOC will require the following six capabilities and types of equipment: 1. 2. 3. 4. 5. 6. Electricity Emergency Lighting Readily Available Sanitary Facilities Medical Kits Office Supplies PC Workstations and Printers with a network To facilitate a steady supply of electricity, the EOC will require a generator or generators of appropriate capacity to ensure an uninterrupted power flow. To support redundancy, the most critical servers and workstations will also be connected to a UPS device. Emergency lighting systems will be tied in to the generator and there will also be flashlights with regularly replaced batteries stationed throughout the facility. Some sort of standing arrangement will be made with a local sanitation company to provide an appropriate number of chemical toilets. Well-stocked medical kits will also be stowed along with flashlights. Thank you Chris Saltzman Raid Memo Carlton Smith, When disaster strikes, the most irreplaceable part of our company lies within the computer systems themselves. Data is the one thing that cannot be replaced if it is lost. Therefore we must be assured that it is safe. All information on a computer gets stored on the hard disk. When the hard disk fails the data is lost. Even if thousands of dollars were to be spent on professional data recovery there is no guarantee that all of the data would be recovered. One thing that can save our data and our time is RAID. RAID stands for Redundant Array of Inexpensive Disks. There are many different implementations of RAID but the method best suited for our company is probably disk mirroring or duplexing, both called RAID 1. Disk mirroring is simple enough to understand. Essentially it uses multiple hard disks to store the same data. Everything that gets written to one hard disk also gets written to the other. That way if one hard disk fails, the other one contains an exact replica of every single file that was on the original. 72 With RAID, all hard disks are connected to at least one RAID controller. The computer sees all of the disks as one device. The beautiful thing about this system is that if one disk fails, the other one can take over immediately. The system does not crash and nothing has to be replaced or repaired before the systems can continue running. It just works. If RAID 1 is used with duplexing, even a RAID controller can fail without bringing down the system. Duplexing is where each hard disk is connected to its own controller. This provides for maximum protection. Consider the fact that any hard drive can fail at any moment. This is especially so if the drive is running a lot. In our case this is very much so. If one of the server’s drives fail all of the data on that disk is gone. Even if we have a hard copy of every digital document money and time will have to be spent re-entering everything back into the computer. It is just not practical. Not to mention that any production involved with that server comes to a complete stop. Anyone that needs access to the resources that server provides now has to wait for it to come back up. With RAID if one of the drives fails or even if one of the drive controllers fails our data is safe. And as an added bonus production doesn't miss a beat. The other drive takes over as if nothing has happened. All that has to be done is to replace the bad drive with a new good one and the system takes care of the rest. As you can plainly see, RAID 1 is a great idea for DigiKnight. With almost all important data being stored digitally, steps must be taken to prevent that data from being lost or damaged. RAID is the answer. While it can't provide protection against other types of disasters such as fire or water, it will efficiently protect our data from a much more likely disaster; drive failure. It is a problem that must be addressed as soon as possible to prevent a crippling blow to DigiKnight. Sincerely, The Disaster Recovery Plan Team 73 Diagram 1: A Common Lan 74 Sabotage Memo Sir, In addition to my previous three memos regarding the progression of the Disaster Recovery Plan, there is another issue that I need to discuss with you. Because of the critical nature of many of the records we keep here at Digiknight, I need to discuss possible vectors and types of sabotage that may occur. Although our records are kept in a relatively secure area, several people do have access to them. Because of the possibility of a disgruntled employee, industrial espionage, or simply random vandalism, it is important to discuss this issue as soon as possible. Before writing this memo, I have attempted to think of any reasonably possible type of sabotage that may occur to our records and how we might go about preventing each one, or at least minimizing the damage, should it occur. Potential Types of Sabotage Fire Water Other physical damage such as shredding or tearing Random Theft Targeted Theft Intentional mixing-up of records Intentional mislabeling of records Intentional replacing of a document or documents with other(s) From looking at this list, I see basically two types of threats: those depending on access and those resulting from random natural or intentionally caused natural vectors. There are several countermeasures common to each of these possible threats. To minimize damage from any sort of loss, the most important thing is to have digital backups of every single important record. If this is accomplished, it doesn’t matter what records are burned or destroyed, the company can always print more. As far as the access-based threats, the solution here is to significantly restrict access. Only those people with a legitimate and continuous need should have access to the records storage area. When another employee has a temporary need for access, it should go through one of the permanent-access employees. When this is not feasible, the temporary-need employee should be accompanied by a permanent-access employee while he or she accesses records. This covers internal threats. As far as external ones (thieves, industrial espionage, vandals) go, there is no such thing as a perfectly secure anything. What we can best hope to do is to 75 secure our records area with card readers, sturdy doors with hinges on the inside of the room, and other such physical security measures. To help minimize fire damage (and subsequent water damage), dry chemical fire suppression systems should be installed. Thank you Chris Saltzman Stress Memo Sir, An important factor to consider in our preparation for a major disaster is the human one. It is extremely important to protect and plan for the security of our physical assets, but what use are they without our human ones. Following a disaster, during the recovery phase, people will be upset, confused, and looking for answers and explanations. They will need a support network. To this end, I recommend that we devise plans for disaster and grief counselors to be on site immediately after the disaster occurs and the area is safe. Employees will be unusually stressed and may need the services of professional counselors to deal with what has happened. If coworkers are injured or killed they may be unwilling to return to work in. They will want to know why the incident happened, what is being done, and could it happen again. Many employees will be unwilling to admit how upset they are to other employees or supervisors for fear of appearing weak or unable to handle the pressure. Therefore it will also be necessary to offer private sessions with the disaster counselors with the assurance of confidentiality. Employees who were absent during the disaster will be confused and want to know exactly what happened, why, to whom, and they may feel left out for having not been around during the event. Employees will want to feel as if their role in recovering from the disaster is important, that they have a place, and that they matter and contribute in a significant way. It would probably be prudent to plan on one counselor for every 20 employees. Of course not all employees will wish to partake of their services, either because they genuinely do not need to, or because they would be embarrassed to do so. However, it is critical to have support for everybody who needs it, assuming everybody will need it. After the first couple of days when the need is more accurately assessed, the number of counselors on scene can be adjusted appropriately. It is my hope that you will carefully consider the points made in this memo and authorize the addition of disaster and grief counselors to the preparations included in the disaster recovery plan and budget. 76 Sincerely, Chris Saltzman Test Memo Test Team Members, In light of the recent completion of the test phase of your nature-based test scenario, management has concluded that further evaluation should be preformed. This task should be relatively quick given the amount of data collected during the actual test. The evaluation should include post-testing thoughts and ideas from all participants. Also, there should be an employee who was not part of the testing brought in to review the information to make sure it is: 1) Understandable to those who have no part in the testing. 2) Is purely based on factual information with no influence from team members who have a vested interest in the projects success. The team is advised to finish the evaluation as soon as possible so that conclusive facts can be recorded and saved. Management has given an estimated completion time of two weeks. Should the need to extend that time frame occur please call any of the management staff so a new time frame can be decided upon. Sincerely, DigiKnight Management Staff Maintenance Memo Even though the disaster recovery and backup plan is complete, the need to keep the plan up to date is also of great importance. Changes in all aspects of the company and the rest of the world will have adverse effects on how our plan will need to function in the future. Changes within the company itself could make the plan we have in place now ineffective. If the company changes its business outlook or company goals, the plan will have to change accordingly to fit the needs of the company once more. World events can also have an impact on how effective our recovery plan is. Weather changes, government changes, and things of that nature can have effects on how our company conducts business. Thus, the disaster and recovery plan must be able to adapt to supplement the changes that will eventually take place. Some things that can be done to help with the plans adaptive-ness should be to leave space for any kind of changes. Do not keep the plan under lock and key. By letting new information into the plan it can be kept up to date with whatever changes take place in the company. Also, by having a history of the different changes made to the plan it can be easier to keep track of old information. 77 Keeping the disaster recovery plan up to date will help the company be ready for any new types of events we did not think of in the beginning. Having a plan that can adapt to different times will keep our company safe no matter what course it takes in the future. Recovery Team Memo Dear Sir: Right now we have a core disaster planning team of six people. Over the last three months we have researched every aspect of disaster planning and recovery. We have made contacts within the company, gained an understanding of every relevant procedure, and formulated a large document with the purpose of preparing this company for a disaster. This document is nearing completion. As we have mentioned previously it will require constant updating and testing to remain useful. While you may be tempted to break our team up and return us to our home departments I believe that you should not. In creating this document we have not only gained incredible experience that will be invaluable in keeping this document viable, but we have also gained a report among each other. We have an impeccable working environment that is professional, efficiency, and effective. You may want to replace our positions with newer, less experienced, and ultimately cheaper employees. These individuals may be able to maintain the document, but not with the same skill and dedicated that I believe we have shown. In allowing us to create this document you have shown an intense desire to see our company protected from unavoidable disasters. This was an incredible first step, but our knowledge will be required to maintain your goal. Newer members will lack the experience to make appropriate additions. It will take them months to determine the layout of the document. They will be forced to ask veteran members for names, phone numbers, and information. Associates we have worked with will lack the same relationship that we have built. Replacing us may seem cheaper and easier, but will ultimately prove less effective than if you were to keep us. Since this project began our original positions in various departments have been filled by others. These individuals have gained familiarity and talent our former positions. To return us now is liable to throw cogs into already effective departments. Since our original task is completed and all we need to do now is update we will have more time. We can use this to assist underhanded departments as needed, but it would be unwise to remove us from the disaster recovery team. Ultimately the decision rests entirely with you. It has been a pleasure creating this disaster recovery document regardless of your choice, but I humbly recommend that you consider my proposal and keep this team together. As a group we will maintain the disaster recovery document and bring our company forward into the future. 78 Thank you, Josh Wisman & the Disaster Recovery Team Glossary Emergency Operations Center – An emergency operations center is a physical location in which important decision makers can meet to discuss disaster recovery. This physical location can be a place that is set aside solely for the use as an emergency operations center or it can be an office that is currently in use for something else. The emergency operations center does not have to be in the company’s actual facility either. A restaurant or someone’s house can also be the emergency operations center. A place that is open all day long would fit best. It is important that all people needed to be at the emergency operations center know where it is. Command and Control – The decision makers need to be leaders during a disaster because if they aren’t some other random people will try to be. Command and control is simply the people in charge actually controlling the situation during a disaster. They have to make quick decisions in order to tell everyone what they need to do. Operational Control – Operation control is making decisions for things such as ordering food or water for people that need it. The main difference between “command and control” and “operational control” is controlling people versus doing certain duties. Operational control also involves gathering information for managers and other decision makers. Operational Control is usually what someone is told to do from the emergency operation center. Recovery Planning – Recovery planning is planning what to do in the event of a disaster. You must plan ahead of time because you actually have the TIME to make many decisions. When a disaster occurs there needs to be a recovery plan so the right decision is made instantly and the people in the emergency operations center can discuss anything that isn’t in the recovery plan. Containment Team – The containment team is a team of people that is formed as soon as there is a disaster. They containment team’s job is to minimize the damage the disaster is causing. If there is a fire, this team will try to save as much equipment as they can. They definitely cannot save everything and they are much different from the recovery team which I’ll talk about next. Recovery Team 79 – The recovery team will try to restore the facility to working ability as fast as possible. There needs to be a recovery team leader to inform the rest of the team of what to do. This is much more important for the recovery team than it is for the containment team because the containment team doesn’t have time for planning. The recovery team can start restoring the facility when the disaster is still happening. As long as no more damage will be done to that specific part of the facility recovery can begin. The recovery team shouldn’t have to recover something twice over. Application Software – Program written for a specific application to perform functions specified by users. Business Critical Data – Data that a business can not operate without. Client/Server Network – Network in which the server directs communication traffic to all users that are connected to it. Cold Site – Location in which to store data. However the location has no equipment or communication ability prior to need of data, and requires substantial time in which to setup. Differential Backup – Method of backing up files by performing a full system backup and then performing an incremental backup. Full System Backup – Method of backing up files by backing up every file and folder on the server being backed up. Hot Site – Location in which data is stored. The location has complete equipment and communication ability, and requires little time to be up and running. Incremental Backup – Method of backing up files by only backing up files and folders that have changed since the previous full system backup. 80 Load Balancing – Used to evenly separate network traffic among a number of servers to prevent one server from becoming overloaded. Mirrored Site – An exact replica of the IT and communications center of an organization. In the event of a disaster to the main IT facility the mirrored site will immediately take over to minimize down time. Mirroring – The process of writing the same data to more than one disk, creating an exact replica of data, as a fail safe should one disk fail. Mobile Site – Mobile location with IT and communication abilities. Used as a backup in the event of a disaster to the main communication center. Amount of time required to become operational varies with each mobile site. Noncritical Data – Data that a business could due without and not cause harm to its bottom line. Parity – A form of striping with a minimum of three disk, to achieve data redundancy without the waste of space that is caused by mirroring. Peer to Peer Network – Network that treats all processors equally and is used primarily in small networks. RAID – (Redundant Array of Inexpensive Disks) used to provide fault tolerance to disk storage systems. Sensitive Data – Data that a business wishes to be kept secret, and would be deferential to a business if it were to fall into the hands of competitors. 81 Striping – The process of taking a single piece of information and writing a portion of it on one disk and the next portion on a separate disk and so on until the piece of information is complete. System Software – Program that manage the computer’s resources, communications and peripheral devices. Warm Site – Location in which to store data. The location has partial equipment and communication ability prior to need of data, and requires a medium amount of time in which to setup. Tabletop Test–A tabletop test is the first step is testing a disaster recovery document. Since other testing types can be highly intrusive and almost always effect productivity it is vital to begin the testing phase by planning everything out. That is what the tabletop test is for. Absolutely everything related to the other tests should be gone over and analyzed within this phase. It is likely that continuity errors and contradictions within the document will be noticed and can be changed. Small typos are likely to be noticed along with similar documentation changes. As the group looks over each document the order they should be presented will quickly become obvious. This sort of meeting also allows department managers and other individuals outside the project to be brought in. These individuals can be prepped for the larger types of testing so that it goes soother and less productivity is lost. Small Problem Testing–Small Problem testing involves testing each department or only an individual problem. This form of testing does not test entire business and does not give an overview of how the entire business body will perform, but it does fine-tune the procedures for a group of individuals or for a single process. Since small problem testing is larger it will be required that high level approval is acquired. Before testing even begins everything needs to be planned in advance (usually through tabletop testing.) All relevant individuals need to be notified and plans need to be place in case the testing does not go as planned. Time also needs to be set aside to evaluate the testing. This evaluation, which will include meetings with participating staff members, will help make changes to the disaster recovery document. Furthermore the participating individuals will now have some training should a disaster happen. It is important that small problem testing be performed regularly. Full-Scale Testing–Full-Scale Testing is when everything is completely tested. This is a massive undertaking and only the highest authorization will allow this sort of event to proceed. Everyone needs to be 82 onboard and ready. Even more so than with small problem testing all aspects of the operating need to be planned in minute detail. This sort of testing demonstrates how unified and cohesive the company is in total. Every department and every process will undergo an evaluation. This is the ultimate trail for the disaster recovery document over an actual disaster. Experienced project managers should be brought it prior to the test to make sure every contingency from success to every type of failure is addressed adequately. Due to the size of this sort of testing the damage caused by inappropriate procedures could be financially catastrophic. This testing is intensive training for the entire company. Other than an actual disaster, this is the only testing procedure that fully challenges every department and individual.