Using Microsoft AuthenticodeTMTechnology with “Luna
advertisement

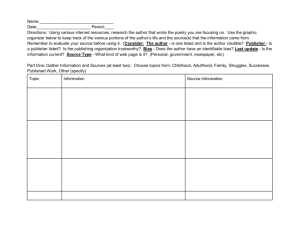
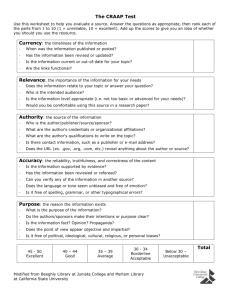
Using Microsoft Authenticode Technology with “Luna Cryptographic Services for Microsoft Windows” TM Realizing the Possibilities of Internet Software Distribution WHAT IS AUTHENTICODE? When customers buy software in a store, the source of that software is obvious. Customers can tell who published the software, and they can see whether the package has been opened. These factors enable customers to make decisions about what software to purchase and how much to "trust" those products. When customers download software from the Internet, the most they see is a message warning them about the dangers of using the software. The Internet lacks the subtle information provided by packaging, shelf space, shrink wrap, and the like. Without an assurance of the software's integrity, and without knowing who published the software, it's difficult for customers to know how much to trust software. It's difficult to make the choice of downloading the software from the Internet. The solution to these issues is Microsoft's Authenticode coupled with Digital IDs from VeriSign, Microsoft's preferred provider of digital certificate services, as well SafeNet’s “Luna Cryptographic Services for Microsoft Windows”, the Ultimate Trust in Hardware-secured key generation and storage. Authenticode, through the use of digital signatures, enables software developers to include information about themselves and their code with their programs. When customer download software signed with Authenticode and verified by VeriSign, they can be assured of: • Content Source: The software really comes from the publisher who signed it. • Content Integrity: The software has not been altered or corrupted since it was signed. Users benefit from this software accountability because they know who published the software and that the code has not been tampered with. In the extreme case that software performs unacceptable or malicious activity on their computers, users can also pursue recourse against the publisher. This accountability and potential recourse serve as a strong deterrent to the distribution of harmful code. Developers and Webmasters benefit from Authenticode because it puts trust in their name and makes their products harder to falsify. By signing code, developers build a trusted relationship with users, who then learn to confidently download signed software from that publisher or Web site. With Microsoft Authenticode, developers can create exciting Web pages using signed ActiveX™ controls, signed Java™ applets, or other signed executables. And users can make educated decisions about what software to download, knowing who published the software and that it has not been tampered with. WHO NEEDS A SOFTWARE PUBLISHER ID? Any publisher who plans to distribute code or content over the Internet or over corporate extranets risks impersonation and tampering. VeriSign Software Publisher IDs for Authenticode Technology protects against these hazards. Authenticode is currently used to sign 32-bit .exe files (PE files), .cab files, .ocx files, and .class files. In particular, if you are distributing active content (such as ActiveX controls) for use with such Microsoft end user applications as Internet Explorer, Exchange, Outlook, or Outlook Express, you will want to sign code using Authenticode. VeriSign offers A Class 3 Digital ID designed for Commercial Software Publishers. These are companies and other organizations that publish software. This class of Digital IDs provides greater assurance about the identity of a publishing organization and is designed to represent the level of assurance provided today by retail channels for software. WHAT DOES AUTHENTICODE LOOK LIKE TO CONSUMERS? Microsoft client applications, such as Internet Explorer, Exchange, Outlook, and Outlook Express, come with security features which incorporate Authenticode. These applications are often used to obtain other pieces of software. In a component model such as ActiveX or Java this happens frequently, often without the end user being aware of it. For example, when a user visits a Web page that uses executable files to provide animation or sound, code is often downloaded to the end user’s machine to achieve the effects. While this may provide substantial value, users risk downloading viruses or code from a disreputable publisher. If an end user of one of these applications encounters an unsigned component distributed via the Internet, the following will occur: • If the application's security settings are set on "High," the client application will not permit the unsigned code to load. • If the application's security settings are set on "Medium," the client application will display a warning like this screen: By contrast, if a user encounters a signed applet or other code, the client application will display a screen like the following: Through Authenticode, the user is informed: 1. Of the true identity of the publisher (in this case Microsoft Corporation). 2. Of a place to find out more about the control (in this example MSN Versioning Control). 3. That the authenticity of the above information is provided by VeriSign. Users can choose to trust all subsequent downloads of software from the same publisher. They can also choose to trust all software published by Commercial Publishers (see above) that have been certified by VeriSign. Simply by clicking the "More Info" button, users can inspect the certificate and verify its validity: TECHNICAL OVERVIEW What is a Digital ID? A Digital ID (also known as a digital certificate) is a form of electronic credentials for the Internet. Similar to a driver's license, employee ID card, or business license, a Digital ID is issued by a trusted third party to establish the identity of the ID holder. The third party who issues certificates is known as a Certification Authority (CA). Digital ID technology is based on the theory of public key cryptography. In public key cryptography systems, every entity has two complementary keys--a public key and private key--which function only when they are held together. Public keys are widely distributed to users, while private keys are kept safe and only used by their owner. Any code digitally signed with the publisher's private key, can only be successfully verified using the complementary public key. Another way to look at this is that code successfully verified using the publisher's public key (which is sent along with the digital signature), can only have been digitally signed using the publisher's private key (thus authenticating the source of the code), and has not been tampered with. For more information on public keys and private keys, please see Introduction to Public Key Cryptography). The purpose of a Digital ID is to reliably link a public/private key pair with its owner. When a CA such as VeriSign issues Digital IDs, it verifies that the owner is not claiming a false identity. Just as when a government issues you a passport it is officially vouching for the fact that you are who you say you are, when a CA issues you a digital certificate it is putting its name behind the statement that you are the rightful owner of your public/private key pair. Certification Authorities Certification Authorities, such as VeriSign, are organizations that issue digital certificates to applicants whose identity they are willing to vouch for. Each certificate is linked to the certificate of the CA that signed it. As the Internet's leading Certification Authority, VeriSign has the following responsibilities: 1. Publishing the criteria for granting, revoking, and managing certificates. 2. Granting certificates to applicants who meet the published criteria. 3. Managing certificates (for example, enrolling, renewing, and revoking them). 4. Storing VeriSign's root keys in an exceptionally secure manner. 5. Verifying evidence submitted by applicants. 6. Providing tools for enrollment. 7. Accepting the liability associated with these responsibilities. 8. Time stamping digital signatures. How does Authenticode work with VeriSign Digital IDs? Authenticode relies on industry standard cryptography techniques such as X.509 v3 certificates and PKCS #7 and #10 signature standards. These are well-proven cryptography protocols, which ensure a robust implementation of code signing technology. Developers can use the WinVerifyTrust API, upon which Authenticode is based, to verify signed code in their own Win32 applications. Authenticode uses digital signature technology to assure users of the origin and integrity of software. In digital signatures, the private key generates the signature, and the corresponding public key validates it. To save time, the Authenticode protocols use a cryptographic digest, which is a one-way hash of the document. The process is outlined below 1. Publisher obtains a Software Developer Digital ID from VeriSign. 2. Publisher creates code. 3. Using the SIGNCODE.EXE utility, the publisher: o Creates a hash of the code, using an algorithm such as MD5 or SHA, o Encrypts the hash using his/her private key, o Creates a package containing the code, the encrypted hash, and the publisher's certificate. 4. The end user encounters the package. 5. The end user's Microsoft browser examines the publisher's Digital ID. Using the VeriSign root Public Key, which is already embedded in Authenticode-enabled applications, the end user browser verifies the authenticity of the Software Developer Digital ID (which is itself signed by the VeriSign root Private Key). 6. Using the publisher's public key contained within the publisher's Digital ID, the end user browser decrypts the signed hash. 7. The end user browser runs the code through the same hashing algorithm as the publisher, creating a new hash. 8. The end user browser compares the two hashes. If they are identical, the browser messages that the content has been verified by VeriSign, and the end user has confidence that the code was signed by the publisher identified in the Digital ID, and that the code hasn't been altered since it was signed. The entire process is seamless and transparent to end users, who see only a message that the content was signed by its publisher and verified by VeriSign. Timestamping Because key pairs are based on mathematical relationships which can theoretically be "cracked" with a great deal of time and effort, it is a well-established security principle that digital certificates should expire. Your VeriSign Digital ID will expire one year after it is issued. However, most software is intended to have a lifetime of longer than one year. To avoid having to resign software every time your certificate expires, VeriSign and Microsoft introduced a timestamping service. Now, when you sign code, a hash of your code will be sent to VeriSign to be timestamped. As a result, when your code is downloaded, clients will be able to distinguish between: • Code signed with an expired certificate, which should NOT be trusted, and • Code signed with a certificate which was valid at the time the code was signed, but which has subsequently expired. This code SHOULD be trusted. This means that you will not need to worry about resigning code when your Digital ID expires. VeriSign is the only certification authority offering the time stamping service. This service is free to all VeriSign Commercial and Individual Software Publisher ID customers. THE SIX STEPS TO SIGNING CODE Signing Code is an easy six-step process. By following the instructions below, you will be signing code in no time. Step 1: Make Sure that you Are Running the Correct Versions of all Tools: These include: • Internet Explorer 4.0 or later • Internet Client SDK These tools are all available free of charge at: http://digitalid.verisign.com/developer/ms_pick.htm Step 2: Apply for a Software Publisher's ID for Authenticode from VeriSign Go to http://digitalid.verisign.com/developer/ms_pick.htm for instructions on obtaining a Software Publisher's Digital ID. The Verign “Enrollment” page should appear. If you haven’t done so already, you should download the “Client Software Developer’s kit” that applies to your current Internet Explorer browser version. Upon completion of the downloading of the “Internet Client Software Developer’s kit”, select the “Code Signing Digital ID for Microsoft Authenticode” to begin the process. You will now enter the “Verisign Code Signing Digital ID” for Microsoft Authenticode page! Complete the required information! In order to use “Luna Cryptographic Services for Microsoft Windows”, you will need to do the following: Specify the Cryptographic Service Provider Name as “Luna Cryptographic Services for Microsoft Windows” and make sure the Private Key Path and File Name specify nothing. A private key will be generated on the Luna Token. This key is never sent to VeriSign, so if you lose this private key, you will be unable to sign code. If this key is lost or stolen, please contact VeriSign immediately. We recommend the use of the Luna CA3 Token, which provides the capability to securely backup private keys. Step 3: Pick up your Digital ID Once you have completed the application process, VeriSign will take a number of steps to verify your identity. For commercial publishers, VeriSign does a considerable amount of background checking. As a result, it will take approximately 3-5 days to verify your information and issue a Digital ID. At the end of this process, VeriSign will send you an e-mail containing a PIN (Personal Identification Number). Follow the instructions in this e-mail to pick up your Digital ID. Save your Digital ID as a file (e.g. MyCredentials.spc). Please note that you must use the same machine to apply for and obtain your Digital ID. You can then use the private key and Digital ID to sign files on a different machine. Step 4: Prepare your Files to be Signed If you are building any PE file (.exe, .ocx, .dll or other), you need not do anything special. For cab files, you need to add the following entry to your .ddf file before creating the cab file: Set ReservePerCabinetSize=6144 Step 5. Sign your Files You can now sign your .exe, or .cab, .ocx, or .dll file. To sign, you will use the SIGNCODE.EXE utility included in the ActiveX SDK. You will also need your Digital ID file (generally called MyCredentials.spc) and the SafeNet Luna Token containing your private key. To use SignCode.exe built-in wizard with the SafeNet HSM solution: 1) Specify the file for signing 2) Select custom signing option 3) Select the Signature Certificate file IE. .spc 4) Select the private key like the following: Note: Key Container Name can be any name you specify! 5) Select the hash algorithm 6) Select additional Certificates (Optional), otherwise leave as default 7) Enter optional data description 8) Add timestamp to data. Currently the address is http://timestamp.verisign.com/scripts/timstamp.dll (Yes timstamp.dll is correct spelling) 9) Finally click Finished Step 6: Test Your Signature. The Microsoft SDK contains a utility called chktrust.exe. This may be used to check your signature before distributing your file. To test a signed .exe, .dll or .ocx file, run chktrust filename To test a signed cab file, run chktrust -c cabfilename.cab If your signing process was OK, this will bring up a certificate. Congratulations, you have just digitally signed your file. When this file is downloaded from a Web site by Internet Explorer, it will display the same certificate to the user. If the file is tampered with in any way after it has been signed, the user will be notified and given the option of refusing installation. CONCLUSION Microsoft and VeriSign are committed to making the Internet a secure and viable platform for commerce and the distribution of content. With Authenticode and VeriSign's Software Publisher Digital IDs, your code will be as safe and trustworthy to your customers as it would be if you shrinkwrapped it and sold it off a store shelf. For more information on Software Publisher IDs for Microsoft Authenticode, including pricing, availability, and Frequently Asked Questions, please visit www.verisign.com/developers For more information on Authenticode, ActiveX, or other Microsoft Security technologies, please visit www.microsoft.com/security/default.asp S u b m it E n ro lm e n t F o rm IE u s e s s e le c te d C S P to g e n e ra te k e y p a ir P u b lic k e y is s e n t to V e ris ig n fo r c e rtific a tio n V e ris ig n R e c e ive s E n ro lm e n t V e ris ig n S e rv e r re tu rn s w e b p a g e d ire c tin g IE to g e n e ra te a k e y p a ir If th e M S B a s e C S P is u s e d , g e n e ra tio n is d o n e in s o ftw a re a n d th e p riv a te k e y is s to re d in a ".p vk " file o n th e w o rk s ta tio n . U s in g th e L u n a C S P , th e k e y p a ir is g e n e ra te d o n th e L u n a T o k e n a n d th e p riva te k e y re m a in s o n th e to k e n a t a ll tim e s . V e ris ig n ve rifie s th a t th e p u b lic k e y a n d p riva te k e y c o rre s p o n d u s in g a "p ro o f o f p o s s e s s io n " c h e c k V e ris ig n s e n d s e -m a il w ith d ire c tio n s fo r p ic k in g u p "d ig ita l ID " P ic k u p "d ig ita l ID " SafeNet Overview SafeNet (NASDAQ: SFNT) is a global leader in information security. Founded more than 20 years ago, the company provides complete security utilizing its encryption technologies to protect communications, intellectual property, and digital identities, and offers a full spectrum of products including hardware, software, and chips. ARM, Bank of America, Cisco Systems, the Departments of Defense, and Homeland Security, Microsoft, Samsung, Texas Instruments, the U.S. Internal Revenue Service, and scores of other customers entrust their security needs to SafeNet. For more information, visit www.safenet-inc.com. w w w . s a f e n e t - i n c . c o m Corporate Headquarters: 4690 Millennium Drive, Belcamp, Maryland 21017 USA Tel: +1 410.931.7500 or 800.533.3958 email: info@safenet-inc.com Phone USA and Canada (800) 533-3958 Phone Other Countries (410) 931-7500 Fax (410) 931-7524 E-mail info@safenet-inc.com Website www.safenet-inc.com ©2004 SafeNet, Inc. This document contains information that is proprietary to SafeNet, Inc. No part of this document may be reproduced in any form without prior written approval by SafeNet. SafeNet shall have no liability for errors, omissions or inadequacies in the information contained herein or for interpretation thereof. The opinions expressed herein are subject to change without notice. Australia +61 3 9882 8322 Brazil +55 11 4208 7700 Canada +1 613.723.5077 China +86 10 885 19191 Finland +358 20 500 7800 France +33 1 41 43 29 00 Germany +49 18 03 72 46 26 9 Hong Kong +852.3157.7111 India +91 11 26917538 Japan +81 45 640 5733 Korea +82 31 705 8212 Mexico +52 55 5575 1441 Netherlands +31 73 658 1900 Singapore +65 6297 6196 Taiwan +886 2 27353736 UK +44 1276 608 000 U.S. (Massachusetts) +1 978.539.4800 U.S. (Minnesota) +1 952.890.6850 U.S. (New Jersey) +1 201.333.3400 U.S. (Virginia) +1 703.279.4500 U.S. (Irvine, California) +1 949.450.7300 U.S. (San Jose, California) +1 408.452.7651 U.S. (Torrance, California) +1 310.533.8100 Distributors and resellers located worldwide.