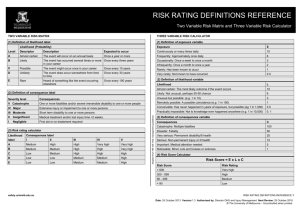
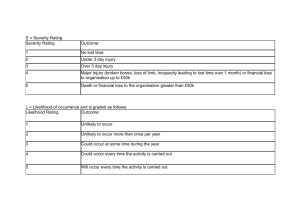
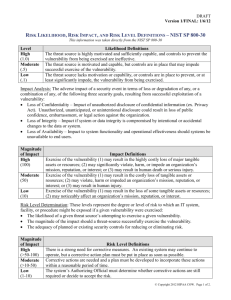
Vulnerability Assessment Process
advertisement

Vulnerability Assessment Process Coleman Kane Coleman.Kane@ge.com January 14, 2015 Security Vulnerability Assessment Assessment Process – 1 / 12 Vulnerability Assessment Vulnerability Assessment Methodology: OWASP Approach Basic Heuristic Step 1: Identify Risk(s) Step 2: Estimating Likelihood Step 2: Likelihood (Threat Agent) Step 2: Likelihood (Vulnerability Factors) Step 3: Estimating Impact Step 4: Determine the Risk Rating Step 5: Remediation Planning Step 6: Customizing Risk Rating Assessment is the practice of discovering the vulnerabilties posed by an environment, determining their negative risk impact, and documenting these observations for future planning. In some cases, this may drive modifications to a network or business practice to eliminate the vulnerability or reduce its exposure. In other cases, one might implement montioring to notify in the event that an identified vulnerability is being exploited in the environment. Security Vulnerability Assessment Assessment Process – 2 / 12 Methodology: OWASP Approach Vulnerability Assessment Methodology: OWASP Approach Basic Heuristic Step 1: Identify Risk(s) Step 2: Estimating Likelihood Step 2: Likelihood (Threat Agent) Step 2: Likelihood (Vulnerability Factors) Step 3: Estimating Impact Step 4: Determine the Risk Rating Step 5: Remediation Planning Step 6: Customizing Risk Rating ■ Actively developing field ■ As many methodologies as commercial providers ■ OWASP approach describes six steps to develop a risk analysis Security Vulnerability Assessment Assessment Process – 3 / 12 Basic Heuristic Vulnerability Assessment Methodology: OWASP Approach Basic Heuristic Step 1: Identify Risk(s) Step 2: Estimating Likelihood Step 2: Likelihood (Threat Agent) Step 2: Likelihood (Vulnerability Factors) Step 3: Estimating Impact Step 4: Determine the Risk Rating Step 5: Remediation Planning Step 6: Customizing Risk Rating Generalized equation: ■ Risk = Likelihood * Impact ■ Identify what exposures you would like to assess the risk of ■ use the process to calculate the Likelihood / Impact of those exposures Security Vulnerability Assessment Assessment Process – 4 / 12 Step 1: Identify Risk(s) Vulnerability Assessment Methodology: OWASP Approach Basic Heuristic Step 1: Identify Risk(s) Step 2: Estimating Likelihood Step 2: Likelihood (Threat Agent) Step 2: Likelihood (Vulnerability Factors) Step 3: Estimating Impact Step 4: Determine the Risk Rating Step 5: Remediation Planning Step 6: Customizing Risk Rating Determine what exposure you are concerned about. Some considerations for this: ■ What might a breach objective be? ■ Who might attempt, vs. who would not? ■ What aspects of your business should be in scope / out of scope? ■ What type of attack is in/out of scope? ■ What would your loss cost be? Coming up with realistic and well-defined scenarios/scopes that you are developing to will ensure the assessment is meaningful for your business cases. Security Vulnerability Assessment Assessment Process – 5 / 12 Step 2: Estimating Likelihood Vulnerability Assessment Methodology: OWASP Approach Basic Heuristic Step 1: Identify Risk(s) Step 2: Estimating Likelihood Step 2: Likelihood (Threat Agent) Step 2: Likelihood (Vulnerability Factors) Step 3: Estimating Impact Step 4: Determine the Risk Rating Step 5: Remediation Planning Step 6: Customizing Risk Rating Two primary contributors to this: ■ Threat Agent factors ■ Vulnerability factors Come up with rating criteria, and a scoring system (for example, 0-9) Security Vulnerability Assessment Assessment Process – 6 / 12 Step 2: Likelihood (Threat Agent) Vulnerability Assessment Methodology: OWASP Approach Basic Heuristic Step 1: Identify Risk(s) Step 2: Estimating Likelihood Step 2: Likelihood (Threat Agent) Step 2: Likelihood (Vulnerability Factors) Step 3: Estimating Impact Step 4: Determine the Risk Rating Step 5: Remediation Planning Step 6: Customizing Risk Rating Better adversaries are expected to have greater success in successfully exposing you. You may grade your adversaries based upon arbitrarily-selected, applicable criteria. ■ Skill level: Red teaming skills(9), Network programming skills (7), Scritping skills (4), No skills (1) ■ Motive: Funding level, priority level - Nation-state (9), Criminal activity (6), Opporutnist (3) ■ Opportunity: Situational characteristics to increase (9) or decrease (0) the likelihood of attacking ■ Size: Size of threat agent group, resourcing which can be applied to the attack: Lone actor (1), Small team (3), Army unit (7), Internet-scale (9) Security Vulnerability Assessment Assessment Process – 7 / 12 Step 2: Likelihood (Vulnerability Factors) Vulnerability Assessment Methodology: OWASP Approach Basic Heuristic Step 1: Identify Risk(s) Step 2: Estimating Likelihood Step 2: Likelihood (Threat Agent) Step 2: Likelihood (Vulnerability Factors) Step 3: Estimating Impact Step 4: Determine the Risk Rating Step 5: Remediation Planning Step 6: Customizing Risk Rating ■ Ease of discovery / Security-through-obscurity ■ Ease of exploit ■ Awareness ■ Intrusion detection / instrumentation Many of these items are under direct control of the entity being assessed, and therefore provide the starting measurements for improvement projects Security Vulnerability Assessment Assessment Process – 8 / 12 Step 3: Estimating Impact Vulnerability Assessment Methodology: OWASP Approach Basic Heuristic Step 1: Identify Risk(s) Step 2: Estimating Likelihood Step 2: Likelihood (Threat Agent) Step 2: Likelihood (Vulnerability Factors) Step 3: Estimating Impact Step 4: Determine the Risk Rating Step 5: Remediation Planning Step 6: Customizing Risk Rating ■ Technical impact, losses of: Confidentiality, integrity, availability, accountability ■ Business impact: Financial damage, Reputational damage, Non-compliance, Privacy violation Security Vulnerability Assessment Assessment Process – 9 / 12 Step 4: Determine the Risk Rating Vulnerability Assessment Methodology: OWASP Approach Basic Heuristic Step 1: Identify Risk(s) Step 2: Estimating Likelihood Step 2: Likelihood (Threat Agent) Step 2: Likelihood (Vulnerability Factors) Step 3: Estimating Impact Step 4: Determine the Risk Rating Step 5: Remediation Planning Step 6: Customizing Risk Rating Use the Impact & Vulnerability computations earlier to calculate an average value for the purpose of reporting the risk rating. Reporting options: ■ May choose Low/Medium/High/Critical level descriptors ■ May want to apply weightings to certain criteria ■ May want to report where recipient is in relation to peers ■ Frequency of activity/breaches at current risk rating level Security Vulnerability Assessment Assessment Process – 10 / 12 Step 5: Remediation Planning Vulnerability Assessment Methodology: OWASP Approach Basic Heuristic Step 1: Identify Risk(s) Step 2: Estimating Likelihood Step 2: Likelihood (Threat Agent) Step 2: Likelihood (Vulnerability Factors) Step 3: Estimating Impact Step 4: Determine the Risk Rating Step 5: Remediation Planning Step 6: Customizing Risk Rating Determine what to fix. Using the vulnerability ratings, you can scope improvment projects based upon lower-scoring vulnerability factors. Options can be reported alongside implementation costs to assist in project selection and planning. Security Vulnerability Assessment Assessment Process – 11 / 12 Step 6: Customizing Risk Rating Vulnerability Assessment Methodology: OWASP Approach Basic Heuristic Step 1: Identify Risk(s) Step 2: Estimating Likelihood Step 2: Likelihood (Threat Agent) Step 2: Likelihood (Vulnerability Factors) Step 3: Estimating Impact Step 4: Determine the Risk Rating Step 5: Remediation Planning Step 6: Customizing Risk Rating Competing principles: ■ Threat landscape is not a constant, but an ever-changing dynamic system ■ Assessment is most meaningful when it can be kept constant across multiple measurement cycles As time goes on, you’ll want to use knowledge of reported activity to inform changes. Possibly overlay "old" and "new" rating systems in reports, to illustrate ongoing improvement while ensuring that reporitng is kept up to date Security Vulnerability Assessment Assessment Process – 12 / 12