1.3 Target Systems
advertisement

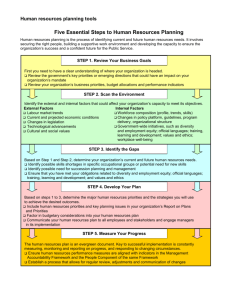
BBT INC. Vulnerability Assessment &Penetration Test Report Eric Gibson Jr Joseph Pavlik Rajani Gunda R.E.J. 4/26/2012 Table of Contents 1 - EXECUTIVE SUMMARY 1.1 - Project Objective 1.2 - Scope 1.3 - Target Systems 1.4 - Network Testing Methodology 1.5 - Tools 1.6 - Network Diagram 1.7 - Network Diagram (DNS Resolution) 1.8 - Network Vulnerability Assessment (Authenticated) 1.9 - Network Vulnerability Assessment (Unauthenticated) 3 3 4 4 5 5 6 7 8 8 2 - FINDINGS 2.1 - 70.61.60.122 2.1.1 - Target Analysis 2.1.2 - Vulnerabilities 2.2 - 70.61.60.125 2.2.1 - Target Analysis 2.2.2 - Vulnerabilities 2.3 - 70.61.60.123 2.3.1 - Target Analysis 2.3.2 - Vulnerabilities 2.4 - 70.61.60.124 2.4.1 - Target Analysis 2.4.2 - Vulnerabilities 2.5 - 70.61.60.126 2.5.1 - Target Analysis 2.5.2 - Vulnerabilities 9 9 10-11 10-11 12 12 13 13 14 14 3 - RECOMMENDATIONS 3.1 - Software 3.2 - 70.61.60.122 3.3 - 70.61.60.125 15 16 16-17 4 - CONCLUSION 18 5 - PENETRATION TESTING LOG 19-20 R.E.J. | BBT Penetration Test 2012 2 1.0 - Executive Summary BBT, Inc. requested the services of R.E.J to conduct their bi-annual penetration testing. This executive summary contains the results of the PENTEST that was performed during the time period of April 5th 2012 through May 1st of 2012. This report contains confidential information surrounding the amount of security risk within the BBT, Inc. network infrastructure. At the request of BBT Inc., R.E.J analysts have conducted authorized reconnaissance, network mapping and vulnerability testing in an effort to report findings to BBT, Inc. The results are intended to be an overall assessment of the conditions at the time of testing and do not necessarily reflect current conditions. 1.1 Project Objective The objective of BBT Inc.’s network assessment is to determine the overall security of the network by analyzing all IPs given to R.E.J analysts. For testing, R.E.J analyst performed a number of tests as authenticated users (with log-in supplied credentials), as well as unauthenticated users. R.E.J. | BBT Penetration Test 2012 3 1.2 Scope Attack Systems Description IP Address Target Environment (include any 3rd party systems/networks – written permission must have been obtained in advance by the target organization) Description IP Address(es) Scan? 70.61.60.122-126 Yes Assessment Type Will any part of the assessment be performed against a live production environment? Assessment Timeline List any black-out dates or times. Is this a “black box” vulnerability scan If not, what are the approved login credentials for an authenticated scan? YES May 1st 2012 April 3rd 2012 April 4rd 2012 NO - Greybox Both (ask on April 17th) Local Admin accounts Testing Techniques Ping sweep of network ranges Dangerous/Unsafe checks allowed Internal reconnaissance activities requested External reconnaissance activities requested YES YES YES YES Governance What is the policy regarding viewing data (including Notify of any sensitive information found. potentially sensitive/confidential data)? Will target organization personnel observe the testing NO team? 1.3 Target Systems Target Environment (include any 3rd party systems/networks – written permission must have been obtained in advance by the target organization) Description IP Address(es) Scan? 70.61.60.122 Yes 70.61.60.123 Yes 70.61.60.124 Yes 70.61.60.125 Yes 70.61.60.126 Yes R.E.J. | BBT Penetration Test 2012 4 1.4 Network Testing Methodology Conduct reconnaissance Scanning & enumeration Identify all points of access within the network infrastructure Report findings Present recommendations The following diagram illustrates the process used for performing the network assessment: 1.5 Tools Activity Port Scanning & Footprinting Web Application Enumeration Vulnerability Assessment Network Penetration Test Vulnerability Research & Verification Tool Nmap, Netcat, google Nessus, Qualys HydraGTK, Metasploit, Cain & Abel, Medusa www.metasploit.com, cve.miter.org, www.uscert.gov R.E.J. | BBT Penetration Test 2012 5 1.6 Network Diagram R.E.J. | BBT Penetration Test 2012 6 1.7 Network Diagram (DNS Resolution) R.E.J. | BBT Penetration Test 2012 7 1.8 Network Vulnerability Assessment - Authenticated Qualys Application Scan 7 Application Vulnerabilities 1.9 Network Vulnerability Assessment - Unauthenticated 1.9 Network Vulnerability Assessment - Unauthenticated Nessus Network Scan 1 Critical vulnerability was discovered 1 High vulnerability was discovered 3 Medium vulnerabilities were discovered 1 Low vulnerability was discovered R.E.J. | BBT Penetration Test 2012 8 2.0 - FINDINGS 2.1 Target IP: 70.61.60.122 Operating System: Linux (Backtrack) Total Open Ports: 9 Port 22 111 21 25 80 111 143 443 8080 Protocol tcp tcp tcp tcp tcp udp tcp tcp tcp Service Name ssh rpc-portmapper ftp smtp www rpc-portmapper imap https www Attacks Attempted HydraGTK: Brute force attack used to gain access to the ssh server. This program uses a password list to guess the username and password and manually tries combinations to gain access to the machine. Our attempts were unsuccessful. Medusa: Another brute force attack used to gain access to the ssh server. This program also uses a password list to guess the username and password and manually tries combinations to gain access to the machine. Our attempts were unsuccessful. DoS Attack: We were able to find a Denial of Service Exploit that coincided with the version of OpenSSH this server was running. This exploit was called “OpenSSH <= 4.3 p1 (Duplicate Block) Remote Denial of Service Exploit.” Our attempts were questionable. We received a IP “cookie” but were unclear of the next steps. Vulnerabilities Port 22 Synopsis: The remote service offers an insecure cryptographic protocol. Description: The remote SSH daemon supports connections made using the version 1.33 and/or 1.5 of the SSH protocol. Risk Factor: Medium Port 22 Synopsis: The remote service uses the default username for authentication. Description: The remote service utilizes the default username ‘root’ for authentication. A remote user can login as the root user to the SSH server. Risk Factor: Medium R.E.J. | BBT Penetration Test 2012 9 2.2 Target IP: 70.61.60.125 Operating System: Windows Total Open Ports: 4 Port 3389 5000 69 123 Protocol tcp tcp udp udp Service Name msrdp www tftp ntp Attacks Attempted MS12-020: We attempted to exploit the recently discovered vulnerability in Microsoft RDP using RDPKill and a python script found in the Exploit Database. Exploit appeared successful. We could not connect to the server after running the attack. Server may have gone down or denied access to us at that point. Vulnerabilities Port 69 Synopsis: The remote host has probably been compromised. Description: A TFTP server is running on this port. However, while trying to fetch "/etc/passwd", we got an MS executable file. Many worms are known to propagate through TFTP. This is probably a backdoor. Port 3389 Risk Factor: Critical Synopsis: The remote Windows host could allow arbitrary code execution. Description: Arbitrary remote code vulnerability exists in the implementation of the Remote Desktop Protocol (RDP) on the remote Windows host. The vulnerability is due to the way that RDP accesses an object in memory that has been improperly initialized or has been deleted. If RDP has been enabled on the affected system, an unauthenticated, remote attacker could leverage this vulnerability to cause the system to execute arbitrary code by sending a sequence of specially crafted RDP packets to it. This plugin also checks for a denial of service vulnerability in Microsoft Terminal Server. Note that this script does not detect the vulnerability if the 'Allow connections only from computers running Remote Desktop with Network Level Authentication' setting is enabled or the security layer is set to 'SSL (TLS 1.0)' on the remote host. Risk Factor: High Port 3389 Synopsis: It may be possible to get access to the remote host. Description: The remote version of the Remote Desktop Protocol Server (Terminal Service) is vulnerable to a man-in-the-middle (MiTM) attack. The RDP client makes no effort to validate the identity of the server when setting up R.E.J. | BBT Penetration Test 2012 10 encryption. An attacker with the ability to intercept traffic from the RDP server can establish encryption with the client and server without being detected. A MiTM attack of this nature would allow the attacker to obtain any sensitive information transmitted, including authentication credentials. This flaw exists because the RDP server stores a hardcoded RSA private key in the mstlsapi.dll library. Any local user with access to this file (on any Windows system) can retrieve the key and use it for this attack. Risk Factor: Medium Port 3389 Port 3389 Synopsis: The remote host is using weak cryptography. Description: The remote Terminal Services service is not configured to use strong cryptography. Using weak cryptography with this service may allow an attacker to eavesdrop on the communications more easily and obtain screenshots and/or keystrokes. Risk Factor: Medium Synopsis: The remote host is not FIPS-140 compliant. Description: The encryption setting used by the remote Terminal Services service is not FIPS-140 compliant. Risk Factor: Low Software Vulnerabilities (Authenticated Scan) Windows Firewall – Disabled Windows XP Professional Service Pack 1 - Support retired Internet Explorer 6.0.2800.1106 – Insecure Version Adobe Flash Player 10.0.22.87 – Insecure Version Adobe Reader 9.3.0.148 – Insecure Version Windows Media Player 9.0.0.2980 – Insecure Version Apple QuickTime 6.5.1.0 – Insecure Version R.E.J. | BBT Penetration Test 2012 11 2.3 Target IP: 70.61.60.123 Operating System: N/A Total Open Ports: 5 Port 25 80 143 443 8080 Protocol tcp tcp tcp tcp tcp Service Name smtp http imap https www Vulnerabilities N/A R.E.J. | BBT Penetration Test 2012 12 2.4 Target IP: 70.61.60.124 Operating System: N/A Total Open Ports: 6 Port 21 25 80 143 443 110 Protocol tcp tcp tcp tcp tcp tcp Service Name ftp smtp http imap https pop3 Vulnerabilities N/A R.E.J. | BBT Penetration Test 2012 13 2.5 Target IP: 70.61.60.126 Operating System: N/A Total Open Ports: 7 Port 21 25 80 110 143 443 8080 Protocol tcp tcp tcp tcp tcp tcp tcp Service Name ftp smtp http pop3 imap https http Attacks Attempted VNC: At one point during our reconnaissance, we found that a port running VNC was open. However, after returning to the server we could not get consistent nMap scans because the server appeared to go down several times. Need to investigate more at a future time to establish which VNC service was running. We have several exploits waiting to run pending more information. Vulnerabilities N/A R.E.J. | BBT Penetration Test 2012 14 3.0 - RECOMMENDATIONS Software Recommendations During target analysis of host 70.61.60.126, there were a number of applications that pose a risk to the machine and could make it possible for an attacker to compromise the host via the insecure application. Below is a list of the unsecure applications complete with recommendations on how to resolve each issue. Windows Firewall – Disabled Enable the Windows firewall on the host machine. Windows XP Professional Service Pack 1 - Support retired Install Windows 7 and perform all MS required updates. Internet Explorer 6.0.2800.1106 – Insecure Version Upgrade IE browser to latest compatible version which is 9.0 Adobe Flash Player 10.0.22.87 – Insecure Version Upgrade to the latest Flash Player version which is 11.2 Adobe Reader 9.3.0.148 – Insecure Version Upgrade to latest Adobe Reader X version 10.1.2 Windows Media Player 9.0.0.2980 – Insecure Version Upgrade to latest Windows Media Player which is version 12.0 Apple QuickTime 6.5.1.0 – Insecure Version Upgrade to latest QuickTime version which is 7.7.1 R.E.J. | BBT Penetration Test 2012 15 Host-Specific Recommendations Target IP: 70.61.60.122 Port- 22: Medium Attack: The remote service offers an insecure and cryptographic protocol. Recommendation: Disable compatibility with version 1 of the protocol. Port- 22: Medium Attack: The remote service utilizes the default username ‘root’ for authentication. A remote user can login as the root user to the SSH server. Recommendation: Many brute force attacks use the ‘root’ username to try and gain access to the target host machine. Disable remote login as the root user. Before disabling this option, you may want to setup another account with root privileges. Target IP: 70.61.60.125 Port-69: Critical Attack: The remote host is compromised. TFTP Backdoor detection. Recommendation: TFTP uses UDP on port 69, and since TFTP is insecure and should never be used across the internet anyway that’s compelling reason to block egressing UDP traffic on that port. Port- 3389: High Attack: The remote windows host could allow arbitrary code execution. Recommendation: Apply appropriate patches provided by Microsoft to vulnerable systems immediately after appropriate testing. Block the TCP port 3389 at the network perimeter. Disable the Terminal Services, Remote Desktop, Remote Assistance, and Windows Small Business Server 2003 Remote Web Workplace features if not required. Enable Network Level authentication on systems running supported version of Windows, Vista, Windows 7, Windows Server 2008 and Windows Server 2008 and Windows Server R2. Port-3389:Medium Attack: The remote host is using weak cryptography. Terminal Services Encryption level is medium. Recommendation: Administrator of windows 2000 servers and Windows XP servers who have enabled the Remote desktop should apply the Patch. Block port 3389 at the firewall would be protected against this attack. Port -3389: Medium Attack: It may be possible to get access to the remote host. Recommendation: Force the use of SSL as a transport layer for this service if supported, or/and select the Allow connections only from computers running Remote Desktop with Network Level Authentication setting if it is available. R.E.J. | BBT Penetration Test 2012 16 Port -3389: Low Attack: The remote host is not FIPS-140 compliant. Recommendation: Change RDP encryption level: to 4 FIPS compliant. R.E.J. | BBT Penetration Test 2012 17 4.0 - Conclusion Outlined above you will see several security issues that could have devastating impacts for your company, if exploited. A few of the risks are critical and severe; these should be addressed in a timely manner. Other risks are not as severe, but should be looked into none the less. If the issues are confronted, your company should see a substantial increase in security. That said, an organization’s information and confidentiality is imparity to its success and survival. Several policies should to put into place to maintain your company’s data integrity and security. Security flaws will continue to develop as exploits are discovered. With this, your company should continue to make improvements and policies to address future issues. We have enjoyed working with BBT evaluate your information technology security. If there should be any questions or you require further information, please contact any of the agents that worked with your company. R.E.J. | BBT Penetration Test 2012 18 5.0 – Penetration Testing Log Target Date Attempt result Other Information Analyst 70.61.60.122 70.61.60.123 70.61.60.124 5-Apr Nessus Scan 5-Apr Nessus Scan 5-Apr Nessus Scan Host Up Host Down Host Down 9 Ports up Vulnerabilities found 5 Ports up 6 Ports up EGJ EGJ EGJ 70.61.60.125 5-Apr Nessus Scan Host Up 4 Ports up Vulnerabilities found EGJ 70.61.60.126 70.61.60.122 70.61.60.123 70.61.60.124 70.61.60.125 70.61.60.126 5-Apr 5-Apr 5-Apr 5-Apr 5-Apr 5-Apr Host Up Host Up Host Down Host Down Host Up Host Up 70.61.60.122 Nessus Scan Nmap Scan Nmap Scan Nmap Scan Nmap Scan Nmap Scan HydraGTK Brute 10-Apr Force Attack 70.61.60.122 70.61.60.123 70.61.60.124 10-Apr Nessus Scan 10-Apr Nessus Scan 10-Apr Nessus Scan Host Up Host Down Host Down 70.61.60.125 10-Apr Nessus Scan Host Up 70.61.60.126 70.61.60.122 70.61.60.123 70.61.60.124 70.61.60.125 70.61.60.126 10-Apr 10-Apr 10-Apr 10-Apr 10-Apr 10-Apr Host Up Host Up Host Down Host Down Host Up Host Up 7 Ports up Vulnerabilities found 9 Ports up 5 Ports up 6 Ports up 4 Ports up 7 Ports up need to put together a better password list file 9 Ports up Vulnerabilities found 5 Ports up 6 Ports up 4 Ports up Vulnerabilities found 7 Ports up Vulnerabilities found 9 Ports up 5 Ports up 6 Ports up 4 Ports up 7 Ports up 70.61.60.122 17-Apr RDPKill Exploit Successful Can no longer connect to server 70.61.60.122 70.61.60.125 70.61.60.125 70.61.60.122 70.61.60.122 70.61.60.123 70.61.60.124 17-Apr 17-Apr 24-Apr 24-Apr 24-Apr 24-Apr 24-Apr Nessus Scan Nmap Scan Nmap Scan Nmap Scan Nmap Scan Nmap Scan Medusa Brute Force Attack Qualys Scan Cain & Abel Exploit DoS Exploit Nessus Scan Nessus Scan Nessus Scan R.E.J. | BBT Penetration Test 2012 Unsuccessful Unsuccessful Successful Unsuccessful Unsuccessful Successful Successful Successful Used new password list 7 Vulnerabilities found Next steps unknown Final scan - 9 ports up Final scan - 5 ports up Final scan - 6 ports up EGJ EGJ EGJ EGJ EGJ EGJ EGJ, JP, RG RG RG RG RG RG RG RG RG EGJ EGJ JP EGJ EGJ JP JP EGJ, RG EGJ, RG EGJ, RG 19 70.61.60.125 70.61.60.126 24-Apr Nessus Scan 24-Apr Nessus Scan R.E.J. | BBT Penetration Test 2012 Successful Successful Final scan - 4 ports up Final scan - 7 ports up EGJ, RG EGJ, RG 20