COP 6611 – Operating Systems Assignment 1 Sridhar Godavarthy
advertisement

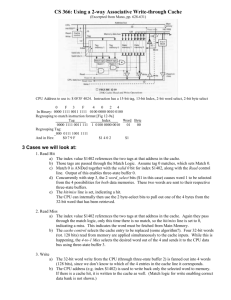
COP 6611 – Operating Systems Assignment 1 Sridhar Godavarthy (U32086851) 1.8) Which of the following instructions should be privileged? a. Set value of timer c. Clear Memory e. Turn off interrupts f. Modify entries in a device-status table g. Switch from user to kernel mode. h. Access I/O Device. 1.9) Some early computers protected the operating system by placing it in a memory partition that could not be modified by either the user job or the operating system itself. Describe two difficulties that you think could arise with such a scheme. a. Any new critical data created by the OS would have to be anyway placed on the writable partition – nullifying its use. b. The operating system can never be updated / patched. 1.13) In a multiprogramming and time-sharing environment, several users share the system simultaneously. This situation can result in various security problems. a) What are two such problems? i) A single process may exhaust all resources unless proper resource management is performed. ii) User programs may overwrite others address spaces without proper memory management. iii) Users may be able to access others file and data without proper file management. iv) User programs may result in fatal system errors which will affect all other users. b) Can we ensure the same degree of security in a time-shared machine as in a dedicated machine? No. No matter how secure an OS is, there are always loopholes and an OS can never be 100% secure. Even if the OS provides for reasonable restrictions, the administrators must fully understand and utilize these resources – which is a very complex task. 1.14) The issue of resource utilization shows up in different forms in different types of Uses. List what resources must be managed carefully in the following settings: COP 6611 – Operating Systems Assignment 1 Sridhar Godavarthy (U32086851) a) Mainframe or minicomputer systems – CPU time, Memory, I/O b) Workstations connected to servers – Network bandwidth, server utilization, file servers, compute servers and print servers c) Hand held computers – Power consumption, Memory usage. 1.17) Describe the differences between symmetric and asymmetric multiprocessing. What are three advantages and one disadvantage of multiprocessor systems? A) In symmetric systems, all processors are peers – in software and hardware. i.e all processors perform all tasks. In asymmetric systems, the processors differ from each other( in software- where has control software and controls the other CPUs. In Hardware- one processor is designed to be good at control and others good at computations). One CPU acts as the master and assigns tasks to the other processors. Advantages: Increased throughput (better performance); Economy of scale (reduction in costs by resource sharing); Increased reliability. Disadvantage: Increased complexity 1.18) How do clustered systems differ from multiprocessor systems? What is required for two machines belonging to a cluster to cooperate to provide a highly available service? A) Clustered systems are two or more individual systems coupled together and may share storage or have a faster interconnect. Multiprocessor systems on the other hand are much more closely coupled and generally use shared memory to communicate. The processors generally share the same system resources. High availability can be achieved by adding a level of redundancy to the system. A software known as the cluster software runs on the system and each machine is monitored ( keep track of process information) by one or more machines. When a machine fails, the monitoring machine takes up its tasks. 1.20) Consider a computer cluster consisting of two nodes running a database. Describe two ways in which the cluster software can manage access to the data on the disk. Discuss the benefits and disadvantages of each. A) Asymmetric clustering – The nodes can be implemented in the hot standby mode with one node performing the database operation and the other node monitoring the first node keeping track of its state. If the first node fails, the second node takes up the operation from where the first one failed. However, in this case, only one node is utilized while the other node’s computation power is wasted Symmetric clustering – In this mode, both nodes perform the operation, and monitor each other. When one fails, the other machine takes up both the operations. In this case, the computation power is utilized, but the system design is very complex – to handle parallel operations and proper locking and synchronization mechanisms between the two nodes. COP 6611 – Operating Systems Assignment 1 Sridhar Godavarthy (U32086851) 1.21) How are network computers different from traditional personal computers? Describe some usage scenarios in which it is advantageous to use network computers. A) Personal computers have all the required resources local to the machine and are capable of handling all requests locally. Network computers have very minimal resources locally( in some cases- known as dumb terminals- only the memory and a processor) and a minimalistic operating system too. They depend on a network server for all their resource requirements. Systems that have a centralized storage that needs to be shared between several clients is a good scenario to use such a setup. For example, a database class whose students need to work on a central database server. 1.22) What is the purpose of interrupts. What are the differences between a trap and an interrupt? Can traps be generated intentionally by a user program? If so, for what purpose? A) Interrupts are used to indicate events ( changes in state, interesting scenarios, freeing of resources, I/O completions, errors) to the Operating System, which usually results in a change in the operating system performing an action. Traps are software generated interrupts, whereas an interrupt is hardware generated. Yes. Traps can be generated intentionally by user programs – All system calls are called by traps. Also, exception handling mechanisms can generate traps to allow the O/S to handle errors. 1.26) Consider an SMP system similar to what is shown in figure Illustrate with an example how data residing in memory could in fact have two different values in each of the local caches. A) Time Operation CPU 1 Cache CPU 2 Cache Memory Location G T BEGIN X X 32 T+t CPU 1 Read G 32 X 32 T + 2t CPU 2 Read G 32 32 32 T + 3t CPU 1 Write G 0 32 0 Assume write through caches. Initially both caches do not cache memory location G. At T + t, the 1st CPU issues a read on G, This causes a miss and fetches the value 32 from main memory into the cache. At T + 2t, CPU2 issues a read on G which again causes a miss and fetches the value 32 from main memory. Now, at T + 3t, CPU 1 issues a write to memory location G. This is a hit and hence the value is updated in cache-1 and also written back to memory. In the absence of mechanisms to notify the Cache of CPU2 of its dirty value, the Cache of CPU2 now has a wrong value – the two caches have two different values for the same memory location. This is shown in red at T + 3t COP 6611 – Operating Systems Assignment 1 Sridhar Godavarthy (U32086851) 1.27) Discuss, with examples, how the problem of maintaining coherence of cached data manifests itself in the following processing environments: a) Single-processor systems – In a multitasking environment, this is not very complicated. Mechanisms should be in place to provide the data from the cache even when requested from a different process. All other principles of caching remain the same. b) Multiprocessor systems – As each processor will have its own cache, there must be a synchronization between the caches of all processors. However, writing back at each access will cause performance degradation. Instead, each cache must communicate with the others and when one cache is invalidated, all other caches must be notified. Another method is to have a central cache control such as a snoopy cache which will manage the synchronization. Only when the block is being removed from the cache should the block be written-back ( for ideal caching- but this is seldom the scenario). c) Distributed systems – As each node has its own local memory, caching is not an issue in this scenario. However, file caching discrepancy is a scenario. To overcome this, any update to a file in any system will result in updates to all replicas. 1.28) Describe a mechanism for enforcing memory protection in order to prevent a program from modifying the memory associated with other programs Allocate memory in a fixed size chunk. If more memory is requested by a process, allocate another chunk. Keep track of chunks allocated to a process and do not allow access outside the allocated memory. A simpler, but performance degrading method would be track each and every block of memory allocated to a process and check the bounds at every access. 1.30) Define the essential properties of the following types of OS: a) Batch – batch operating systems are those where several jobs that are dependent on the output of the previous job –or- completely independent jobs are queued to run on a computer. Earlier, this was done by operators. Such programs usually do not interact with users. Such a system provides a high CPU utilization in single process operating systems. b) Interactive – An OS where each job needs several inputs from the user at different points in time making it unfit for batch processing. Generally, GUIs which require a lot of user interactions utilize this kind of OS. c) Time sharing – The OS is accessed by multiple users simultaneously. It is capable of servicing several users by rapid switching between the various processes. It, handles synchronization of resources and also handles locking mechanisms for parallel access of memory. d) Real time – Such OSs are usually used for a specific purpose. They read information from sensors and must provide a response/action to the sensors within a specified time. The time limit is a hard limit and cannot be broken. COP 6611 – Operating Systems Assignment 1 Sridhar Godavarthy (U32086851) e) Network – The OS and resources reside on a network server and a minimalistic OS is present on other machines. The central OS may either control or support the other machines. f) Parallel – Capable of handling multiple processor scenarios. It is designed to synchronize the processors and handle shared access of resources. Each CPU has the same OS running on it. All resources are common and shared except for memory. g) Distributed – Several machines exist with each system having the same OS. They generally communicate over a LAN. The OS is designed to split up a specific task into multiple components. Each system performs an individual task- generally on the same data. There are no common resources h) Clustered – Several individual nodes are combined into a single system. Each node has its own OS running on it. The OS communicate with each other. They can be designed to monitor each other, operate in parallel or as a hot standby. There are no common resources. I) Handheld – This is a very simple OS which runs on very low power, low memory, very little resources and small display sizes and provide for longer battery life to performance. 1.32) Identify several advantages and several disadvantages of open-source operating systems. Include the types of people who would find each aspect to be an advantage or a disadvantage. A) Advantage For Disadvantage For Advantages: Build on others ideas Independent developers, Students, small businesses Peer reviewed Developers of the software Better quality Community Competitors Less expensive Independent developers, Students, small businesses Competitors Availability of source code to tailor modules to individual needs Anybody who needs to customize the product Competitors, Consultants, Independent developers Improved security as flaws are analyzed by "many eyes" Community Hackers, Cyber thieves Several vendors for same OS Independent developers, small scale businesses Competitors Portable with wider hardware Independent developers, Students, Competitors, COP 6611 – Operating Systems Assignment 1 small businesses Easier licensing Independent developers, Students, small businesses More support in developing stage Independent developers, Students, small businesses Ability to and satisfaction from contributing Independent developers, Students Sridhar Godavarthy (U32086851) manufacturers of OS which work on only their H/W Competitors Disadvantages: Comes without warranty or guarantee Competitors Small businesses Chances for intellectual property infringements Competitors, advocates Small businesses, Independent developers Projects can be abandoned Competitors Small businesses, Independent developers Might not get support when required as there is no obligation Competitors Small Businesses REFERENCES: [1] Silberschatz. Galvin and Gagne, Operating System Concepts 7ed, ©2004, John Wiley & Sons Inc. [2] John L. Hennessy and David A. Patterson, Computer Architecture: A Quantitative Approach 4ed, © 2006, Morgan Kaufmann