Caldicott - Acute Trusts Knowledge base
advertisement

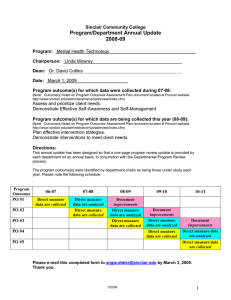
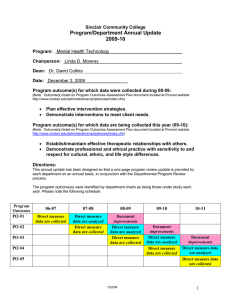
Information Security Assurance – Mental Health Trusts Knowledge base guidance Requirement 309 Does the MHT have adequate procedures in place to ensure the availability of information processing facilities, communications services and data? Application systems should contain audit trails or activity logs and should validate data entered or output. Routine procedures should be established for carrying out an agreed system back-up strategy taking back-up copies of data and rehearsing their timely restoration, logging events and faults and, where appropriate, monitoring the equipment environment. This requirement addresses ISO/IEC 17799 (revised 2005) controls ref 10.5 & 12.2 Information backup The MHT ensures that business data and software applications are regularly backedup using suitable technology. MHTs must develop a risk based back-up strategy that documents the procedures to be followed for each relevant information asset. MHTs that use the services of third parties for data backup should ensure arrangements conform to MHT information governance standards. Business data is that entered by users into systems, such as patient data, or other files created and saved by users. Networked data stored on servers should normally be backed up on minimum of a daily basis by the system administrator or through automatic process. Back-up media for the previous week (or as locally agreed) should be compiled and stored securely at a remote location to the server from which it was created. Consideration should be given to storing media in a different building or site to ensure they are protected if the location where the server is located is damaged causing disruption or unavailability. Data back-up strategy is a local decision, however, best practice indicates that a month’s worth of data should be compiled and stored securely at a different location from the server. The weekly and monthly tapes should be stored to protect them from unauthorised access and environmental threats such as heat, cold, magnetic fields and liquids i.e. in a safe that is fire and water resistant. All tapes should be clearly marked to show the date the data was captured and the origin of the data. Instructions for backup should be made available in writing and more than one person should know how to carry out the backup and restore. A log should be kept of all start and finish times of backups, failed attempts and remedial actions, who carried out the backup and who has had access to the tapes. Media should only be used for the period recommended by the manufacturer. Media should be regularly tested to ensure data can be successfully recovered. Redundant media should be securely destroyed. Page 1 of 3 Information that is not networked should be backed up on a daily basis and the media clearly labelled and stored securely. Computers get stolen and hard drives fail without warning so it is particularly important that users with data stored on individual workstations are aware of this. Where possible, data should be stored on networked servers and no critical data should be stored on stand-alone equipment. Local workstations should be configured so that the network drive is set as the default for the storage of data. Input data validation Computerised systems can be designed that allow control over what access a user has, limited fields for entering data and an audit trail showing what information was entered, by whom and when. Data can also be retrieved following system interrupts or failures if appropriate backup arrangements have been planned and put in place. Authentic data input is the direct responsibility of the person inputting the data, supported by their line manager. All systems will include validation processes at data input to check in full or in part the acceptability of the data. Systems should report all data errors together with a helpful reason for the error or rejection to facilitate its correction. Error correction should be done at source of input as soon as it is detected. Such correction is increasingly important as systems are linked and errors can be rapidly transmitted between systems. Any loss or corruption of data should be reported immediately to the relevant system manager. The reporting process should involve invoking incident recording and management mechanisms. Control of internal processing All systems should be designed to include controls that check for information corruption that has resulted from processing errors or other possibly deliberate acts. These controls should include: Functions that are used to implement changes to existing information. Procedures to prevent programs running in the wrong order or running after the failure of a prior process. Programs to recover from failures. Protection against attacks that use buffer overruns/overflows. Output data validation Within systems that process highly structured data, functions can be included to check the consistency of the data. Where a high level of integrity is essential, systems should carry out cross-checking between identical records stored in alternative repositories and/or carry out some form of checksum check to ensure continued data integrity. Integrity of data transmission can be assured by using cryptographic techniques but the validity of the data will depend upon checks carried out at input. In some instances it may be necessary to institute manual processes such as batch testing in order to provide a level of assurance as to the validity of data entering, Page 2 of 3 processed and output by a system. The responsibilities of the system users with respect to checking data validity at input and output should be considered and defined. All user training should emphasise the importance of inputting accurate data. Improvement plans Level 1 The MHT has documented an action plan to ensure appropriate procedures and controls are in place to maintain the integrity and availability of information processing facilities, communications services and data held. Level 2 The MHT is implementing planned controls to ensure appropriate procedures are in place to maintain the integrity and availability of information processing facilities, communications services and data held. Level 3 The MHT has implemented and regularly reviews its documented controls and procedures, and regularly tests its back-up and recovery arrangements. Requirement checklist IS_MHT_309_V4_Checklist 06-05-12.doc Key Guidance Document(s) BS ISO/IEC 17799:2005 & BS ISO/IEC 27001: 2005 BS7799-2:2005 Note that only NHS Information Governance Toolkit (IGT) administrators may download a copy of the standards for their organisation. The administrator must be logged on to download the standards. NHS Connecting for Health Good Practice Guidelines Destruction of Data and Media containing Sensitive Data Exemplar materials Information Backup Comprehensive 57 page document covering procedures to backup data, test that back-ups work, storage of backed-up data and restoration of lost data Operator & Fault Logs 10 page example process for recording and maintaining a faults log Secure Disposal of Equipment 4 page document with process for disposal or storage of IT equipment Page 3 of 3