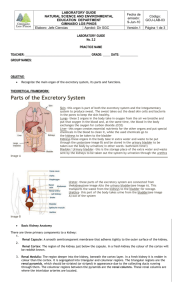
6 cursos de Microsoft Office - Universidad Politécnica de Chiapas
advertisement

Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 1 de 66 RHA 030 Red Hat Linux Computing Essentials Los estudiantes aprenderán ser usuarios eficaces de los sistemas linux, adquiriendo habilidades y comprensión de funciones de la línea de comando, los sistemas de ficheros, los usuarios y los grupos, ambiente de programación, gestión del procesos, editores de textos, usos de la red, buscar y organizar datos, y aplicaciones gráficas. RHA 130 Red Hat Linux Core System Administration Los estudiantes aprenderán ser administradores eficaces de los sistemas linux, dominarán por ejemplo la configuración del hardware y de dispositivos, administración de sistemas de archivo, la administración de usuarios, configuraciones de red, servicios del núcleo, agregar nuevos sistemas linux a una red corporativa, configurar nuevos sistemas para los usuarios finales, y la localización de averías. RHA 230 Red Hat Linux Network Applications Los estudiantes aprenderán a administrar los servicios de red básicos que han hecho a Red Hat Enterprise Linux popular, incluyendo el Apache Web Server, el servicio del servidor de archivos Samba, el Domain Name Server, el agente de transporte del correo de Sendmail, el Network File System (NFS), y más. RHA 250 Red Hat Linux Security Administration Los estudiantes aprenderán a aplicar y administrar políticas de seguridad básicas referente a la autentificación de usuario (PAM incluyendo y NIS) y usar niveles de control de acceso al núcleo por firewalling. Los estudiantes aprenden además destrezas en la administración de SELinux, de la supervisión de sistema, y de aplicar protocolos comunes de encripción (incluyendo infraestructuras de llave pública). DURACIÓN RHA 030 y RHA 130, cada uno se desarrolla durante aproximadamente 60 horas, usando libros de trabajo, lecciones, material de la discusión, ejercicios, herramientas de gestión y exámenes de laboratorio. Cualquier curso se puede enseñar individualmente, en aproximadamente 10 semanas, con 6 horas semanales. RHA 230 y RHA 250, cada uno se desarrolla durante aproximadamente 24 horas, usando libros de trabajo, lecciones, material de la discusión, ejercicios, herramientas de gestión de la clase y exámenes del laboratorio. Cualquier curso se puede enseñar individualmente, en aproximadamente 4 semanas, con 6 horas semanales. Los cursos están diseñados idealmente para que las clases sean llevadas en un laboratorio de computadoras - cada computadora utilizará la última versión de Red Hat Enterprise Linux. El plan de estudios es manejado con material digital, el cual es entregado al inicio del mismo; los libros de trabajo deben presentarse de forma impresa al tomar el curso. Todo el material se encuentra en Inglés, por lo que es recomendable tener entendimiento básico en lectura y comprensión del idioma. TEMARIOS RHA 030 Red Hat Linux Computing Essentials Workbook 1. Quick Tour 1. Logging In 2. The Kernel, Programs, and Processes 3. Examining the Filesystem Workbook 4. System Initialization and Services 1. Boot Sequence Overview 2. The GRUB Bootloader 3. /sbin/init and Run Levels 4. Red Hat Enterprise Linux Service Scripts 5. Troubleshooting the Boot Sequence Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER 4. Running Commands 5. Managing Terminals 6. Getting Help Pretest. Quick Tour Lab Test. Quick Tour Test. Quick Tour Workbook 2. Filesystem Basics 1. Filesystem Navigation 2. Important Directories 3. Managing Files 4. Managing Directories 5. File Names and File Globbing 6. Examining Files 7. Editing Files Pretest. Filesystem Basics Lab Test. Filesystem Basics Test. Filesystem Basics Workbook 3. Users and Groups 1. Linux Users and the /etc/passwd File 2. Linux Groups and the /etc/group File 3. Examining User Information 4. Changing Identity Pretest. Users and Groups Lab Test. Users and Groups Test. Users and Groups Workbook 4. File Ownerships and Permissions 1. Regular File Ownerships and Permissions 2. Changing File Permissions: chmod 3. Changing File Ownerships with chgrp and chown 4. Directory Ownerships and Permissions 5. chmod Revisited: Octal Notation 6. Controlling Default Permissions: umask Pretest. File Ownerships and Permissions Lab Test. File Ownerships and Permissions Test. File Ownerships and Permissions Workbook 5. The Linux Filesystem 1. File Details 2. Hard and Soft Links 3. Directories and Device Nodes 4. Disks, Filesystems, and Mounting 5. Locating Files with locate and find 6. Compressing Files: gzip and bzip2 7. Archiving Files with tar Pretest. The Linux Filesystem Lab Test. The Linux Filesystem Test. The Linux Filesystem Workbook 6. The Bash Shell 1. Introduction to Bash Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 2 de 66 Pretest. System Initialization and Services Lab Test. System Initialization and Services Test. System Initialization and Services Workbook 5. User and Group Administration 1. What Is a User? 2. Adding, Modifying, and Deleting Users 3. Managing Passwords 4. Adding, Modifying, and Deleting Groups 5. Users and the UNIX Filesystem 6. Network Based User Models 7. Customizing the User's Environment Pretest. User and Group Administration Lab Test. User and Group Administration Test. User and Group Administration Workbook 6. Network Configuration 1. Managing Network Interfaces 2. Basic IP Routing and Gateways 3. Configuring DNS Clients 4. Miscellaneous Network Settings 5. Network Diagnostic Utilities Pretest. Network Configuration Lab Test. Network Configuration Test. Network Configuration Workbook 7. System Administration Tools 1. The CUPS print system and system-configprinter 2. CUPS Administration: The Web Interface and Command Line Tools 3. System Logging 4. Periodic Tasks: Managing cron 5. Automated System Maintenance Pretest. System Administration Tools Lab Test. System Administration Tools Test. System Administration Tools Workbook 8. RPM: The Red Hat Package Manager 1. RPM: Installing and Removing Software 2. RPM Queries and Verification 3. Miscellaneous RPM Utilities Pretest. RPM: The Red Hat Package Manager Lab Test. RPM: The Red Hat Package Manager Test. RPM: The Red Hat Package Manager Workbook 9. Kernel Services and Configuration 1. Kernel Modules and Updating Kernels 2. The Network File Systems (NFS) 3. The Automounter 4. Filesystem Quotas 5. Software RAID 6. Logical Volume Management Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER 2. Command Lists and Scripts 3. Bash Variable 4. Command Line Expansion 5. Shell Customizations 6. Sourcing Shell Scripts and Shell Initialization Pretest. The Bash Shell Lab Test. The Bash Shell Test. The Bash Shell Workbook 7. Standard I/O and Pipes 1. Standard In and Standard Out 2. Standard Error 3. Pipes Pretest. Standard I/O and Pipes Lab Test. Standard I/O and Pipes Test. Standard I/O and Pipes Workbook 8. String Processing Tools 1. Text Encoding and Word Counting 2. Finding Text: grep 3. Introduction to Regular Expressions 4. Everything Sorting: sort and uniq 5. Extracting and Assembling Text: cut and paste 6. Tracking differences: diff 7. Translating Text: tr 8. Spell Checking: aspell 9. Formatting Text (fmt) and Splitting Files (split) Pretest. String Processing Tools Lab Test. String Processing Tools Test. String Processing Tools Workbook 9. Managing Processes 1. An Introduction to Processes 2. Process States 3. Process Scheduling: nice and renice 4. Sending Signals 5. Job Control 6. Scheduling Delayed Tasks: at 7. Scheduling Periodic Tasks: cron Pretest. Introduction to Processes Lab Test. Introduction to Processes Test. Introduction to Processes Workbook 10. Network Applications 1. An Introduction to TCP/IP Networking 2. Linux Printing 3. Managing Printfiles 4. Email Overview 5. The Evolution MUA 6. Network Diagnostic Applications 7. Terminal Based Web and FTP Clients Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 3 de 66 Pretest. Kernel Services and Configuration Lab Test. Kernel Services and Configuration Test. Kernel Services and Configuration Workbook 10. The X Windowing System 1. The X Windowing System 2. X Server Configuration 3. X Startup Configuration Pretest. The X Windowing System Lab Test. The X Windowing System Test. The X Windowing System Workbook 11. Troubleshooting 1.Troubleshooting - General Guidelines 2.Things to Check: X server 3. Things to Check: Networking 4. Things to Check: Booting 5. Recovering Systems Using the Rescue Environment 6. Troubleshooting Components Pretest. Troubleshooting Lab Test. Troubleshooting Test. Troubleshooting RHA 230 Red Hat Linux Network Applications Workbook 1. Introduction to Networking Services 1. Red Hat Enterprise Linux Network Services 2. Managing Red Hat Services 3. Managing xinetd Controlled Daemons 4. SELinux: Secure Linux Pretest. Introduction to Networking Services Lab Test. Introduction to Networking Services Test. Introduction to Networking Services Workbook 2. The Apache Web Server 1. Webserver Basics 2. Apache Configuration 3. Apache Configuration: Containers 4. Virtual Hosts 5. The Squid Proxy Server Pretest. The Apache Web Server Lab Test. The Apache Web Server Test. The Apache Web Server Workbook 3. Berkley Domain Name Service (BIND) 1. Introduction to DNS 2. Installing and Configuring BIND 3. BIND Databases and Resource Records 4. More BIND Configuration Pretest. Berkley Domain Name Service (BIND) Lab Test. Berkley Domain Name Service Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER 8. Remote Shell Commands Pretest. Network Applications Lab Test. Network Applications Test. Network Applications Hat Linux Emisión: 25 de agosto de 2008 Revisión: 01 Página: 4 de 66 (BIND) Test. Berkley Domain Name Service (BIND) Workbook 11. Supplements 1. Advanced Shell Scripting 2. Character Encoding and Internationalization 3. The RPM Package Manager RHA 130 Red Administration Código: UPCH-R-102.RG-08 Core System Workbook 1. Red Hat Enterprise Linux Installation 1. The Red Hat Linux Installer: Anaconda 2. Anaconda Stage 2: The Installer Proper 3. Network Based Installations, and Other Installer Topics 4. Using Kickstart to Automate Installations Pretest. Red Hat Enterprise Linux Installation Lab Test. Red Hat Enterprise Linux Installation Test. Red Hat Enterprise Linux Installation Workbook 2. Hardware and Device Configuration 1. Hardware Overview 2. PCI Devices 3. USB and Other Hot Pluggable Devices 4. Filesystem Device Nodes 5. Performance Monitoring Pretest. Hardware and Device Configuration Lab Test. Hardware and Device Configuration Test. Hardware and Device Configuration Workbook 3. Linux Filesystem Management 1. Disk Recognition and Partitioning 2. Creating and Managing Filesystems 3. Mounting Filesystems 4. The /etc/fstab File 5. Managing Swap Space 6. Miscellaneous Filesystem Management Commands 7. SELinux: Secure Linux Pretest. Linux Filesystem Management Lab Test. Linux Filesystem Management Test. Linux Filesystem Management Workbook 4. The Network File Service (NFS) and DHCP 1. NFS Servers 2. The Dynamic Host Configuration Protocol Pretest. The Network File Service (NFS) and DHCP Lab Test. The Network File Service (NFS) and DHCP Test. The Network File Service (NFS) and DHCP Workbook 5. Samba 1. Introducing the Samba Service 2. Samba Global Configuration 3. Samba Shares Pretest. Samba Lab Test. Samba Test. Samba Workbook 6. Sendmail 1. Overview of Email Delivery 2. Managing Sendmail 3. Configuring Sendmail Pretest. Sendmail Lab Test. Sendmail Test. Sendmail RHA 250 Red Hat Linux Security Administration Workbook 1. Introduction and User Authentication Workbook 2. System Monitoring Workbook 3. Network and Service Access Controls Workbook 4. Securing Data Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro Código: UPCH-R-102.RG-08 PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Emisión: 25 de agosto de 2008 Revisión: 01 Página: 5 de 66 PROGRAMA DE CAPACITACION Y CERTIFICACION SUN CERTIFIED JAVA PROGRAMMER (SCJP) Esta certificación esta orientada para programadores de lenguaje Java en los conceptos fundamentals. Para obtener esta certificación el alumno debe de completar un examen de certificación. No es necesario tener la certificación Sun Certified Java Associate para presentar este examen. Curso Fundamentals of the Java Programming Language Java Programming Language Taller de preparación para el examen Sun Certified Programmer for the Java 2 Platform, Standard Edition 5.0 (CX-310-055) Código SL-110-SE6 Modalidad Presencial Duración 40 SL-275-SE6 Presencial Presencial 40 8 ¿Qué incluye la solución? 2 curso oficiales de SUN presenciales 1 taller de certificación 2 simuladores de cada examen de certificación 1 exámenes de certificación con opción de 2 Los precios aplican para grupos mínimos de 12 personas. El servicio se otorgara en cualquier ciudad capital estatal del país PROGRAMA DE CAPACITACION Y CERTIFICACION SUN CERTIFIED JAVA DEVELOPER (SCJD) Esta certificación esta orientada para programadores de lenguaje Java avanzados. Para obtener esta certificación el alumno debe de completar dos elementos: Pasar un examen de certificación. Como requisite los candidates deben primero estar certificados como Sun Certified Programmer (SCJP), de cualquier versión. Pero no es necesario tener la certificación Sun Certified Java Associate para presenter este examen. Curso Object-Oriented Analysis and Design Using UML Java Programming Language Workshop Taller de preparación para el examen Sun Certified Programmer for the Java 2 Platform, Standard Edition 5.0 (CX-310-055) Código OO-226 Modalidad Presencial Duración 40 SL-285 Presencial Presencial 40 8 ¿Qué incluye la solución? 2 curso oficiales de SUN presenciales 1 taller de certificación 2 simuladores de cada examen de certificación 1 exámenes de certificación con opción de 2 Los precios aplican para grupos mínimos de 12 personas. El servicio se otorgara en cualquier ciudad capital estatal del país Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 6 de 66 CONTENIDOS Curso Fundamentals of the Java Programming Language No. SL-110-SE6 The Fundamentals of the Java Programming Language course provides students with an excellent choice for beginning to learn programming using the Java programming language. This course is intended for students with little or no programming experience. The course teaches the significance of object-oriented programming, the keywords and constructs of the Java programming language, and the steps required to create simple Java technology programs. Students taking this course can receive a solid basis in the Java programming language upon which to base continued work and training. The course features the Java Platform, Standard Edition 6 (Java SE 6) platform, and uses the Java SE Development Kit 6 (JDK 6) product. Metodología: Presencial Al finalizar el curso el participante será capaz de: Demonstrate knowledge of Java technology, the Java programming language, and the product life cycle Use various Java programming language constructs to create several Java technology applications Use decision and looping constructs and methods to dictate program flow Implement intermediate Java technology programming and object-oriented (OO) concepts in Java technology programs Prerequisitos: Create programs using a procedural language, such as C, or a scripting language, such as Perl Create and edit text files using a text editor Use a World Wide Web (WWW) browser Solve logic problems Describe the concept of a variable Execute commands using a command-line interface Course Content Module 1 - Explaining Java Technology Describe key concepts of the Java programming language List the three Java technology product groups Summarize each of the seven stages of the product life cycle Module 2 - Analyzing a Problem and Designing a Solution Analyze a problem using object-oriented analysis Design classes from which objects will be created Module 3 - Developing and Testing a Java Technology Program Identify the four components of a class in the Java programming language Use the main method in a test class to run a Java technology program from the command line Compile and execute a Java technology program Module 4 - Declaring, Initializing, and Using Variables Identify the use the syntax for variables and define the syntax for a variable List the eight Java programming language primitive data types Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 7 de 66 Declare, initialize, and use variables and constants according to Java programming language guidelines and coding standards Modify variable values using operators Use promotion and type casting Module 5 - Creating and Using Objects Declare, instantiate, and initialize object reference variables Compare how object reference variables are stored in relation to primitive variables Use a class (the String class) included in the Java Software Developer Kit (SDK) Use the Java 2 Platform, Standard Edition (J2SE[TM]) class library specification to learn about other classes in this application programming interface (API) Module 6 - Using Operators and Decision Constructs Identify relational and conditional operators Create if and if/else constructs Use the switch construct Module 7 - Using Loop Constructs Create while loops Develop for loops Create do/while loops Module 8 - Developing and Using Methods Describe the advantages of methods and define worker and calling methods Declare and invoke a method Compare object and static methods Use overloaded methods Module 9 - Implementing Encapsulation and Constructors Use encapsulation to protect data Create constructors to initialize objects Module 10 - Creating and Using Arrays Code one-dimensional arrays Set array values using length attribute and a loop Pass arguments to the main method for use in a program Create two-dimensional arrays Module 11 - Implementing Inheritance Define and test your use of inheritance Explain abstraction Explicitly identify class libraries used in your code Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 8 de 66 Curso Java Programming Language No. SL-275-SE6 The Java Programming Language course provides students with information about the syntax of the Java programming language; object-oriented programming with the Java programming language; creating graphical user interfaces (GUIs), exceptions, file input/output (I/O), and threads; and networking. Programmers familiar with object-oriented concepts can learn how to develop Java technology applications. The course features the Java Platform, Standard Edition 6 (Java SE 6) platform, and utilizes the Java SE Development Kit 6 (JDK 6) product. The students perform the course lab exercises using the NetBeans Integrated Development Environment (IDE) 5.5. Metodología: Presencial Al finalizar el curso el participante será capaz de: Create Java technology applications that leverage the object-oriented features of the Java language, such as encapsulation, inheritance, and polymorphism Execute a Java technology application from the command line Use Java technology data types and expressions Use Java technology flow control constructs Use arrays and other data collections Implement error-handling techniques using exception handling Create an event-driven graphical user interface (GUI) using Swing components: panels, buttons, labels, text fields, and text areas Implement input/output (I/O) functionality to read from and write to data and text files and understand advanced I/O streams Create a simple Transmission Control Protocol/Internet Protocol (TCP/IP) networked client that communicates with a server through sockets Create multithreaded programs Prerequisitos: Be competent in creating programs in any programming language or have SE6: Fundamentals of the Java Programming Language course. Create and edit text files using a text editor completed the SL-110- Course Content Module 1 - Getting Started Examine Java technology Analyze a simple Java technology application Execute a Java technology application Module 2 - Object-Oriented Programming Define modeling concepts: abstraction, encapsulation, and packages Discuss Java technology application code reuse Define class, member, attribute, method, constructor, and package Use the access modifiers private and public as appropriate for the guidelines of encapsulation Invoke a method on a particular object Use the Java technology API online documentation Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 9 de 66 Module 3 - Identifiers, Keywords, and Types Use comments in a source program Distinguish between valid and invalid identifiers Recognize Java technology keywords List the eight primitive types Define literal values for numeric and textual types Define the terms primitive variable and reference variable Declare variables of class type Construct an object using new Describe default initialization Describe the significance of a reference variable State the consequence of assigning variables of class type Module 4 - Expressions and Flow Control Distinguish between instance and local variables Describe how to initialize instance variables Recognize, describe, and use Java software operators Distinguish between legal and illegal assignments of primitive types Identify boolean expressions and their requirements in control constructs Recognize assignment compatibility and required casts in fundamental types Use if, switch, for, while, and do constructions and the labeled forms of break and continue as flow control structures in a program Module 5 - Arrays Declare and create arrays of primitive, class, or array types Explain why elements of an array are initialized Explain how to initialize the elements of an array Determine the number of elements in an array Create a multidimensional array Write code to copy array values from one array to another Module 6 - Class Design Define inheritance, polymorphism, overloading, overriding, and virtual method invocation Use the access modifiers protected and the default (package-friendly) Describe the concepts of constructor and method overloading Describe the complete object construction and initialization operation Module 7 - Advanced Class Features Create static variables, methods, and initializers Create final classes, methods, and variables Create and use enumerated types Use the static import statement Create abstract classes and methods Create and use an interface Module 8 - Exceptions and Assertions Define exceptions Use try, catch, and finally statements Describe exception categories Identify common exceptions Develop programs to handle your own exceptions Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 10 de 66 Use assertions Distinguish appropriate and inappropriate uses of assertions Enable assertions at runtime Module 9 - Collections and Generics Framework Describe the general purpose implementations of the core interfaces in the Collections framework Examine the Map interface Examine the legacy collection classes Create natural and custom ordering by implementing the Comparable and Comparator interfaces Use generic collections Use type parameters in generic classes Refactor existing non-generic code Write a program to iterate over a collection Examine the enhanced for loop Module 10 - I/O Fundamentals Write a program that uses command-line arguments and system properties Examine the Properties class Construct node and processing streams, and use them appropriately Serialize and deserialize objects Distinguish readers and writers from streams, and select appropriately between them Module 11 - Console I/ O and File I/O Read data from the console Write data to the console Describe files and file I/O Module 12 - Building Java GUIs Using the Swing API Describe the JFC Swing technology Define Swing Identify the Swing packages Describe the GUI building blocks: containers, components, and layout managers Examine top-level, general-purpose, and special-purpose properties of container Examine components Examine layout managers Describe the Swing single-threaded model Build a GUI using Swing components Module 13 - Handling GUI-Generated Events Define events and event handling Examine the Java SE event model Describe GUI behavior Determine the user action that originated an event Develop event listeners Describe concurrency in Swing-based GUIs and describe the features of the SwingWorker class Module 14 - GUI-Based Applications Describe how to construct a menu bar, menu, and menu items in a Java GUI Understand how to change the color and font of a component Module 15 - Threads Define a thread Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 11 de 66 Create separate threads in a Java technology program, controlling the code and data that are used by that thread Control the execution of a thread and write platform-independent code with threads Describe the difficulties that might arise when multiple threads share data Use wait and notify to communicate between threads Use synchronized to protect data from corruption Module 16 - Networking Develop code to set up the network connection Understand TCP/IP Use ServerSocket and Socket classes to implement TCP/IP clients and servers Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 12 de 66 ¿Qué incluye la solución? 6 cursos de Microsoft Office 6 cursos de Microsoft Office E-Learning Curriculum 6 simuladores del examen de certificación 2 exámenes de certificación con opción de 2 oportunidades Soporte 1-800 Los precios incluyen IVA Los precios aplican para grupos mínimos de 12 personas El servicio se otorgará en cualquier ciudad capital estatal del país Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 13 de 66 Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 14 de 66 ¿Qué incluye la solución? 4 cursos de Microsoft Official E-Learning Curriculum 3 cursos presenciales del Microsoft Official Curriculum 3 sesiones de reforzamiento 1 taller de certificación 2 simuladores de cada examen de certificación con 2 oportunidades cada uno 2 exámenes de certificación con opción de 2 oportunidades cada uno Soporte 1-800 Los precios incluyen IVA Los precios aplican para grupos mínimos de 12 personas El servicio se otorgará en cualquier ciudad capital estatal del país 2541 Core Data Access with Microsoft Visual Studio 2005 Introduction This three-day instructor-led workshop provides students with the knowledge and skills to develop dataaccess applications by using the Microsoft .NET Framework and Microsoft Visual Studio 2005. The workshop describes how to access and update data in a database by using ADO.NET. The workshop also describes how to create, read, and write XML data. Audience This workshop is intended for corporate and Independent Software Vendor (ISV) application developers who have a desire to learn more about specific technology areas in distributed application development. At Workshop Completion After completing this workshop, students will be able to: Connect to databases and read data. Query and update databases by using commands. Perform transactional operations. Perform disconnected operations programmatically. Perform disconnected operations by using Visual Studio 2005 wizards. Perform XML operations on disconnected data. Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 15 de 66 Read and write XML data. Process XML data by using the Document Object Model DOM. Prerequisites Before attending this workshop, students must: Be able to manage a solution environment using the Visual Studio 2005 integrated development environment IDE and tools Understand the .NET Framework 2.0 and the Common Language Runtime Be able to program an application using a .NET Framework 2.0 compliant language Know how to make assemblies available to other applications Have a good understanding of basic relational database concepts Be able to use basic SQL commands Have a good understanding of XML including XML declaration, elements, attributes, and namespaces Be able to explain XML schema concepts Workshop Outline Unit 1: Connecting to Databases and Reading Data This unit introduces the fundamental skills required to connect to a database and read data from the database. It describes how to use ADO.NET data providers to connect to various different kinds of databases, and how to execute a query that returns a scalar value from the database. It also describes how to use connection pooling to achieve scalability, and how to handle connection events and exceptions. Lessons What Is ADO.NET? The Process for Connecting to a Database and Reading Data What Is Connection Pooling? Lab 1: Connecting to Databases and Reading Data Exercise 1. Connecting to a Database Exercise 2. Saving a Connection String Securely in an Application Configuration File Exercise 3. Retrieving Data from a Database Exercise 4. Handling Connection Events and Exceptions Exercise 5. Configuring and Using Connection Pooling (if time permits) After completing this unit, students will be able to: Describe the key features of ADO.NET. Explain the process for connecting to a database and reading data from a database. Describe the benefits of connection pooling. Connect to a database. Save a connection string securely in an application configuration file. Retrieve data from a database. Handle connection events and exceptions. Unit 2: Querying and Updating Databases by Using Commands This unit describes how to create and run commands that return a scalar value, return a result set, update data in the database, or update the schema of the database. It also describes how to create and run parameterized commands. Lessons ADO.NET Commands Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 16 de 66 The Process for Passing Parameters into Commands Lab 2: Querying and Updating Databases by Using Commands Exercise 1. Creating and Running Query Commands Exercise 2. Creating and Running Parameterized Commands Exercise 3. Creating and Running Update Commands Exercise 4. Using Globalized Formats for Storing and Accessing Data (if time permits) After completing this unit, students will be able to: List the different types of ADO.NET commands. Explain the process for creating and executing parameterized commands. Create and run query commands. Create and run parameterized commands. Create and run update commands. Unit 3: Performing Transactional Operations This unit describes how to manage transactions in a .NET application at the middle tier. It describes how to write ADO.NET code to start, commit, and rollback local transactions. It also describes how to specify an appropriate isolation level for a transaction, and how to enlist in distributed transactions. Lessons What Is a Transaction? The Process for Managing Local Transactions The Process for Managing Distributed Transactions Isolation Levels Lab 3: Performing Transactional Operations Exercise 1. Performing Data Updates within a Transaction Exercise 2. Choosing an Appropriate Isolation Level for a Transaction Exercise 3. Enlisting in a Distributed Transaction Exercise 4. Managing Transactions in the Data Tier (if time permits) After completing this unit, students will be able to: Describe the concept of transactional operations. Explain the process for managing a local transaction. Explain the process for managing a distributed transaction. Describe the effect of setting the isolation level for a transaction. Perform data updates within a transaction. Choose an appropriate isolation level for a transaction. Enlist in a distributed transaction. Unit 4: Performing Disconnected Operations Programmatically This unit describes how to create and use DataSets programmatically. It describes how to create DataSet, DataTable, and DataColumn objects, how to populate a DataSet manually, and how to load and save data by using a DataAdapter. It also describes how to create in-memory views on data by using a DataView. Lessons What Is the ADO.NET Disconnected Model? The Process for Loading and Saving Data in a DataSet What Are DataViews? Lab 4: Performing Disconnected Operations Programmatically Exercise 1. Creating a DataSet Programmatically Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 17 de 66 Exercise 2. Populating and Saving a DataSet Exercise 3. Adding, Modifying, and Deleting Data in a DataSet Exercise 4. Merging DataSets Exercise 5. Creating and Using DataViews (if time permits) After completing this unit, students will be able to: Describe the ADO.NET disconnected data model. Explain the process for loading and saving data in a DataSet. Describe how to use DataViews to provide a view on data. Create a DataSet programmatically. Populate and save a DataSet. Add, modify, and delete data in a DataSet. Merge DataSets. Unit 5: Performing Disconnected Operations by Using Visual Studio 2005 Wizards This unit describes how to create typed DataSets, DataAdapters, and TableAdapters by using the TableAdapter Configuration Wizard and the Data Source Configuration Wizard in Visual Studio 2005. It also describes how to write type-safe code to access data in a typed DataSet. Lessons Comparing Untyped DataSets with Typed DataSets What Are Table Adapters? Demonstration: Creating a Typed DataSet by Using Visual Studio 2005 Wizards Lab 5: Performing Disconnected Operations by Using Visual Studio 2005 Wizards Exercise 1. Creating a Typed DataSet by Using the DataSet Designer Exercise 2. Loading, Displaying, and Saving Data in a Typed DataSet Exercise 3. Adding Code to a Typed DataSet Exercise 4. Creating a Typed DataSet by Using the Data Source Configuration Wizard Exercise 5. Adding Queries to a Table Adapter (if time permits) After completing this unit, students will be able to: Explain the differences between untyped DataSets and typed DataSets. Explain how table adapters work in conjunction with data tables in a typed DataSet. Describe the process for creating a typed DataSet by using Visual Studio 2005 Wizards. Create a typed DataSet by using the DataSet Designer. Load, display, and save data in a typed DataSet. Add code to a typed DataSet. Create a typed DataSet by using the Data Source Configuration Wizard. Unit 6: Performing XML Operations on Disconnected Data This unit describes how to read and write DataSets in XML format. It describes how to read and write data only, schema only, or a combination of the two. It also describes how to read and write a DataSet as a DiffGram, so that modifications to the data can be retained when the DataSet is serialized to XML format. Lessons XML Representations of DataSets What Are DiffGrams? Lab 6: Performing XML Operations on Disconnected Data Exercise 1. Saving a DataSet as XML Data Exercise 2. Loading a DataSet from XML Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 18 de 66 Exercise 3. Saving and Loading DataSet Schema Information After completing this unit, students will be able to: Describe scenarios in which you can represent a DataSet as XML data. Explain how a DiffGram retains information about modifications to a DataSet. Save a DataSet as XML data. Load a DataSet from XML. Save and load DataSet schema information. Unit 7: Reading and Writing XML Data This unit describes how to use the XmlReader and XmlWriter classes to serially read and write XML data. It describes how to read elements, attributes, and text content in an XML document, and perform validation against an XML schema. It also describes how to create an XML document and write elements, attributes, namespace declarations, and text content. Lessons The Process for Serially Reading XML Data The Process for Serially Writing XML Data Lab 7: Reading and Writing XML Data Exercise 1. Writing XML Data by Using XmlWriter Exercise 2. Reading XML Data by Using XmlReader After completing this unit, students will be able to: Describe the process for serially reading XML data. Describe the process for serially writing XML data. Write XML data by using XmlWriter. Read XML data by using XmlReader Unit 8: Processing XML Data by Using DOM This unit describes how to process XML data in memory by using the Document Object Model (DOM). It describes how to load an XML document into a DOM tree, and validate the XML document against an XML schema. It also describes how to read existing XML content, modify XML content, and save the DOM tree to an XML document. Lessons What Is DOM? What Are DOM Trees? Types of XML Nodes in a DOM Tree Lab 8: Processing XML Data by Using DOM Exercise 1. Reading XML Data by Using DOM Exercise 2. Writing XML Data by Using DOM After completing this unit, students will be able to: Explain what DOM is and describe how to process XML data in memory by using DOM. Explain what a DOM tree is and describe how to represent XML documents as a DOM tree. List the types of nodes in a DOM tree. Read XML data by using DOM. Modify XML data by using DOM. Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 19 de 66 Advanced Data Access with Microsoft Visual Studio 2005 Workshop 2542: Two days; Instructor-Led Introduction Elements of this syllabus are subject to change. This two-day instructor-led workshop provides students with the knowledge and skills needed to use advanced data access features and techniques in the Microsoft .NET Framework and Microsoft Visual Studio 2005. The workshop describes how to access data and how to implement database functionality by using Microsoft ADO.NET 2.0 and Microsoft SQL Server 2005. The workshop also describes how to locate, edit, and transform XML by using XPath and Extensible Style sheet Language for Transformations (XSLT). Audience This workshop is intended for corporate and Independent Software Vendor (ISV) application developers who have a desire to learn more about specific technology areas in distributed application development. At Workshop Completion After completing this workshop, students will be able to: Minimize and handle database operation conflicts. Handle large objects. Enhance database performance. Create managed code objects for SQL Server 2005. Query XML by using XPath. Transform XML by using XSLT style sheets. Prerequisites Before attending this workshop, students must: Have attended or studied Workshop 2541, Core Data Access with Microsoft Visual Studio 2005, or possess equivalent knowledge and skills. Know how to use delegates. Be able to use database stored procedures, triggers, and aggregates. Be able to explain XPath concepts and basic syntax. Be able to explain XSLT style sheet concepts. Workshop Outline Unit 1: Minimizing and Handling Database Operation Conflicts This unit describes how to minimize data access conflicts, and how to handle these conflicts when they occur. It describes how to implement optimistic concurrency in the ADO.NET disconnected model, and how to implement optimistic concurrency by using the various isolation levels available in SQL Server 2005. Lessons Why Do Data Conflicts Arise? Isolation Levels Available in SQL Server 2005 Guidelines for Using SQL Server 2005 Isolation Levels Lab 1: Minimizing and Handling Database Operation Conflicts Exercise 1. Reading Committed Data by Using Locks Exercise 2. Reading Committed Data by Using Statement-Level Snapshots Exercise 3. Reading Committed Data by Using Transaction-Level Snapshots Exercise 4. Handling Data Concurrency by Using ADO.NET After completing this unit, students will be able to: Explain why data conflicts arise. Describe the isolation levels that are available in SQL Server 2005. Describe the guidelines for using SQL Server 2005 isolation levels. Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 20 de 66 Read committed data by using locks. Read committed data by using statement-level snapshots. Read committed data by using transaction-level snapshots. Handle data concurrency by using ADO.NET. Unit 2: Handling Large Objects This unit describes how to read and write large values efficiently to a SQL Server database. It describes how to read large binary values and large text values by using SequentialAccess for a SqlDataReader. It also describes how to write large binary values and large text values, and how to conserve resources when writing large values. Lessons What Are Binary Large Objects and Character Large Objects? The Process for Reading Large Objects from a Database The Process for Writing Large Objects to a Database Lab 2: Handling Large Objects Exercise 1. Reading Large Values from SQL Server Exercise 2. Writing Large Values to SQL Server Exercise 3. Conserving Resources When Writing Large Values to SQL Server After completing this unit, students will be able to: Describe binary large objects and character large objects. Explain the process for reading large objects from a database. Explain the process for writing large objects to a database. Read large values from SQL Server. Write large values to SQL Server. Conserve resources when writing large values to SQL Server. Unit 3: Enhancing Database Performance This unit describes how to enhance database performance by using new features available in ADO.NET 2.0. The unit describes how to perform asynchronous data operations, create multiple active result sets, perform batch updates, and perform bulk copies. Lessons ADO.NET Enhancements in the .NET Framework 2.0 SQL Server Provider Statistics Lab 3: Enhancing Database Performance Exercise 1. Accessing Multiple Result Sets Concurrently Exercise 2. Performing Asynchronous Data Access Operations Exercise 3. Performing a Batch Update Exercise 4. Performing a Bulk Data Copy After completing this unit, students will be able to: Describe the ADO.NET enhancements in Microsoft .NET Framework 2.0. Describe the support for run-time statistics in the .NET Framework Data Provider for SQL Server. Access multiple result sets concurrently. Perform asynchronous data access operations. Perform a batch update. Perform a bulk data copy. Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 21 de 66 Unit 4: Creating Managed Code Objects for SQL Server 2005 This unit describes how to create database objects for SQL Server 2005 in a .NET Framework programming language. It describes how to create stored procedures, triggers, user-defined functions, aggregates, and user-defined types in managed code. Additionally, it describes how to deploy an assembly that contains managed objects into SQL Server 2005, and how to declare database objects to reference the managed objects. Lessons The Benefits of Creating Managed Code Objects Demonstration: The Process for Importing an Existing Assembly into SQL Server 2005 Demonstration: The Process for Implementing Managed Code Objects in SQL Server 2005 Lab 4: Creating Managed Code Objects for SQL Server 2005 Exercise 1. Creating Managed Stored Procedures and Triggers Exercise 2. Creating Managed User-Defined Functions Exercise 3. Creating a Managed Aggregate Exercise 4. Creating a Managed User-Defined Type Exercise 5. Importing Existing Assemblies into SQL Server 2005 (if time permits) After completing this unit, students will be able to: Describe the benefits of creating managed code objects for SQL Server 2005. Explain the process for importing an existing assembly into SQL Server 2005. Explain the process for implementing managed code objects in SQL Server 2005. Create managed stored procedures and triggers. Create managed user-defined functions. Create a managed aggregate. Create a managed user-defined type. Unit 5: Querying XML by Using XPath This unit describes how to use XPath in a .NET Framework application. It describes how to create an XPathNavigator object on an XML document, and how to locate content and evaluate expressions by using the XPathNavigator object. Additionally, it describes how to edit XML data by using the XPathNavigator object. Lessons The XPath Data Model The Process for Selecting and Editing XML Data by Using XPathNavigator The Process for Evaluating XPath Expressions by Using XPathNavigator Lab 5: Querying XML by Using XPath Exercise 1. Selecting XML Data by Using XPathNavigator Exercise 2. Evaluating XPath Expressions by Using XPath Navigator Exercise 3. Creating and Using Compiled XPath Expressions Exercise 4. Editing XML Data by Using XPathNavigator After completing this unit, students will be able to: Describe the XPath data model. Explain the process for selecting and editing XML data by using XPathNavigator. Explain the process for evaluating XPath expressions by using XPathNavigator. Select XML data by using XPathNavigator. Evaluate XPath expressions by using XPathNavigator. Create and use compiled XPath expressions. Edit XML data by using XPathNavigator. Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 22 de 66 Unit 6: Transforming XML by Using XSLT Style Sheets This unit describes how to transform XML documents in a .NET Framework application. It introduces how to load an XSLT style sheet in an application, and how to execute the style sheet to transform an XML document. The unit also describes how to pass parameters into a style sheet, and how to create and use extension objects. Lessons What Is XSLT? The Process for Executing an XSLT Style Sheet What Are Extension Objects? Lab 6: Transforming XML by Using XSLT Style Sheets Exercise 1. Transforming an XML Document by Using an XSLT Style Sheet Exercise 2. Resolving External Resources During XSLT Processing Exercise 3. Passing Parameters into an XSLT Style Sheet Exercise 4: Creating and Using Extension Objects After completing this unit, students will be able to: Describe the purpose of XSLT. Explain the process for executing an XSLT style sheet. Describe the purpose of extension objects. Transform an XML document by using an XSLT style sheet. Resolve external resources during XSLT processing. Pass parameters into an XSLT style sheet. Create and use extension objects. 2543 Core Web Application Technologies with Microsoft Visual Studio 2005 Introduction This three-day instructor-led workshop provides students with the knowledge and skills to develop Microsoft( ASP.NET 2.0 Web applications using Microsoft Visual Studio( 2005. The workshop focuses on user interfaces, Web site structure and functionality, and implementation details.) Audience This workshop is intended for corporate/ISV application developers who have a desire to learn more about specific technology areas in Web application development. At Workshop Completion After completing this workshop, students will be able to: Create a Web application. Program a Web application. Add and configure server controls for a Web application. Use master pages to establish a common layout for a Web application. Manage state data for a Web application. Access and display data in a Web application. Control access to a Web application. Deploy a Web application. Create a mobile Web application. Prerequisites Before attending this workshop, students must: Be able to manage a solution environment using the Visual Studio 2005 IDE and tools Understand Microsoft .NET Framework 2.0 and the Common Language Runtime Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 23 de 66 Be able to program an application using a .NET Framework 2.0 compliant language Know how to make assemblies available to other applications Have a basic understanding of XML including XML declaration, elements, attributes, and namespaces Have a basic understanding of client-side scripts Have a basic understanding of HTML Workshop Outline Unit 1: Creating a Web Application This unit describes the different types of Web sites that you can create with Visual Studio 2005. It introduces the concept of event handling, and shows how to work with default event handlers for an object. It also explains how to control a Web application through the hierarchy of configuration files. Lessons Visual Studio Web Site Types Default Event Handling in Web Applications Web Configuration Files Lab 1: Creating a Web Application Exercise 1. Creating a New Web Application Exercise 2. Configuring and Building a Web Application After completing this unit, students will be able to: Describe the types of Web sites that they can create with Visual Studio 2005. Describe the concept of a default event handler for an object. Explain how the Machine.Config and Web.Config files control the settings for a Web application. Create a new Web application. Configure and build a Web application. Unit 2: Programming a Web Application This unit introduces the advanced event-handling capabilities of ASP.NET 2.0 and describes how to work with events in Visual Studio 2005. It shows how to work with non-default event handlers and centralized event handlers. It also addresses other common Web programming concepts, including: Detecting the type, version, and capability of the browser being used to view a Web site. Accessing information in an ASP.NET Web Page header. Using the HttpResponse.Write method to provide feedback to users. Handling page-level errors. Lessons Event Handling in Web Applications Browser Capability Detection Page Header Retrieval Page-Level and Application-Level Error Handling Lab 2: Programming a Web Application Exercise 1. Implementing Non-Default Event Handlers Exercise 2. Detecting Browser Capabilities and Setting Page Header Properties Exercise 3. Handling Page-Level Exceptions After completing this unit, students will be able to: Describe various event-handling techniques. Explain how to detect browser types and capabilities. Explain how to access page headers. Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 24 de 66 Describe how to handle page-level errors and application-level errors. Implement advanced techniques for handling events. Implement browser-capability detection. Implement page-header manipulation. Implement page-level and application-level error handling. Unit 3: Adding and Configuring Server Controls This unit explains how to use the HTML controls and Web server controls provided by Visual Studio 2005 and ASP.NET 2.0. It shows how to design and build Web-based user interfaces, and it teaches how to program Web server controls. This unit also describes how the ASP.NET 2.0 postback model works and how it can be used. Lessons HTML Controls and Web Server Controls Types of Web Server Controls Working with Web Server Controls The ASP.NET 2.0 Page Postback Model Lab 3: Adding and Configuring Server Controls Exercise 1. Building Graphical User Interfaces with HTML Controls Exercise 2. Building Graphical User Interfaces with Web Server Controls Exercise 3. Programming Web Server Controls and Working with Postbacks After completing this unit, students will be able to: Explain the differences between HTML controls and Web server controls. Describe the different types of Web server controls. Explain how to use HTML controls and Web server controls. Explain how the postback model of ASP.NET 2.0 works. Create Web-based user interfaces with HTML controls and Web server controls. Write code that interacts with Web server controls. Write code that interacts with the postback model of ASP.NET 2.0. Unit 4: Creating a Common Layout by Using Master Pages This unit explains how to use master pages to define common layouts for Web pages. Master pages provide developers with a new set of features for ensuring consistent page layout. Students will work with master pages and nested master pages in the lab to build a Web application that has a consistent layout and functionality across Web pages. Lessons What Are Master Pages? What Are Content Pages? Nested Master Pages Lab 4: Creating a Common Layout by Using Master Pages Exercise 1. Designing a Master Page Exercise 2. Adding and Configuring Content Pages Exercise 3. Designing Nested Master Pages After completing this unit, students will be able to: Describe the concept of a master page. Describe the concept of a content page. Describe nested master pages. Design master pages. Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 25 de 66 Configure content pages. Design nested master pages Unit 5: Managing State for a Web Application This unit describes the different state management technologies that students can use in ASP.NET 2.0 Web applications. It discusses how controls can retain state data over multiple requests, and then explains how developers can work with this state data. This unit then shows how to store state data in the Application and Session objects provided by ASP.NET 2.0. It also discusses the different session-data storage mechanisms. Finally, this unit explains how to use the Cache object to cache and retrieve state data. Lessons ViewState Properties and ControlState Data Application and Session Objects Strategies for Managing Session State Data The Cache Object Lab 5: Managing State for a Web Application Exercise 1. Configuring ViewState Properties for Web Server Controls Exercise 2. Storing and Retrieving Application and Session State Exercise 3. Implementing Out-of-Process Session State Exercise 4. Storing and Managing State Data in the Cache Object After completing this unit, students will be able to: Describe the ViewState and ControlState data models for Web pages. Describe the Application and Session objects and explain how state data is stored and retrieved in these objects. Describe various session-state data-storage strategies. Describe the Cache object and explain how you can use it to store and manage state data. Configure ViewState properties and ControlState properties for Web server controls. Store and retrieve Application and Session state. Implement out-of-process session state. Store and manage state data in the Cache object. Unit 6: Accessing and Displaying Data This unit describes how to add database connections to the Web.Config file and the benefits that this approach adds when building manageable Web applications. This unit then describes the new data controls for accessing data in a variety of formats. It includes details about using the SqlDataSource control, the XmlDataSource control, and the ObjectDataSource control. This unit also describes how user interface data controls are bound to the data source controls, and it includes a discussion about binding data-aware standard controls to data. Lessons Database Connections and the Web.Config File Relational Data and Data Source Controls XML Data and Data Source Controls Object Data and Data Source Controls Lab 6: Accessing and Displaying Data Exercise 1: Creating and Retrieving Database Connections Exercise 2: Accessing Data by Using SqlDataSource Controls and Data Controls Exercise 3: Accessing Objects as Data with ObjectDataSource Controls Exercise 4: Accessing XML Data by Using XmlDataSource Controls Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 26 de 66 After completing this unit, students will be able to: Explain how to store and retrieve database connections by using the Web.Config file. Explain how to use data source controls to access relational data. Explain how to use data source controls to access XML data. Explain how to use data source controls to access object data. Create and retrieve database connections by using the Web.Config file. Access relational data by using the SqlDataSource control and data controls. Access XML data by using the XmlDataSource control and data controls. Access objects as data by using the ObjectDataSource control and data controls. Unit 7: Controlling Access to a Web Application This unit describes authentication and authorization for Web applications. It also shows how to develop login, sign-up, and other membership pages for Web applications based on the ASP.NET 2.0 Membership system. Lessons Authentication for Web Applications Authorization for Web Applications Site Membership Systems Using the Membership Class Web Site Security Administration Using the Roles Class Lab 7: Controlling Access to a Web Application Exercise 1: Configuring Authentication and Authorization for a Web Application Exercise 2: Implementing a Membership Registration Page Exercise 3: Implementing a Login Page and Adding Login Controls Exercise 4: Creating a Membership Management Administrative User Interface After completing this unit, students will be able to: Describe the authentication methods for Web applications. Describe the authorization methods for Web applications. Describe the main components of a membership system. Describe how to build a security administration interface. Configure authentication and authorization for a Web application. Implement a membership registration page. Implement a login page. Create a membership management administrative user interface. Unit 8: Deploying a Web Application This unit describes three different ways to deploy Web applications: Using the Copy Web Site utility to deploy a Web application in a non-compiled state Using the Publish Web Site utility to deploy a precompiled version of the Web application Building Microsoft Windows( Installer packages to create a redistributable application with full setup logic Lessons The Copy Web Site Utility The Publish Web Site Utility Windows Installer Setup Packages Lab 8: Deploying a Web Application Exercise 1. Deploying a Web Application by Using the Copy Web Site Utility Exercise 2. Precompiling and Deploying a Web Application by Using the Publish Web Site Utility Exercise 3. Building a Windows Installer Package for Deploying a Web Application Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 27 de 66 After completing this unit, students will be able to: Describe how to use the Copy Web Site utility to deploy a Web application. Describe how to use the Publish Web Site utility to precompile and deploy a Web application. Describe how to build Windows Installer packages for deploying a Web application. Deploy a Web application by using the Copy Web Site utility. Precompile and deploy a Web application by using the Publish Web Site utility. Build and run a Windows Installer setup application for deploying a Web application. Unit 9: Making Web Applications Available to Mobile Devices This unit explains how to enable browsers running on mobile devices, such as Pocket PCs and mobile phones, to access pages within your application. Lessons Device Emulators for Mobile Web Forms Mobile Device Detection and Redirection Mobile Web Forms Device-Specific Features in Mobile Web Forms Lab 9: Making Web Applications Available to Mobile Devices Exercise 1. Managing Redirection for Mobile Devices Exercise 2. Designing and Implementing a Mobile Web Form Exercise 3. Designing Device-Specific Features for a Mobile Web Application Exercise 4. Browsing a Mobile Web Application with Specific Device Emulators After completing this unit, students will be able to: Explain how to detect mobile devices and redirect them to an appropriate page in a Web application. Describe mobile Web pages, forms, and mobile controls. Explain how to use device-specific features in mobile Web pages to respond to the different capabilities of mobile devices. Explain how to use device emulators in Visual Studio 2005 to test mobile Web pages. Design and implement mobile Web forms. Design device-specific features for mobile Web pages. 2544 Advanced Web Application Technologies with Microsoft Visual Studio 2005 Introduction This two-day instructor-led workshop provides students with the knowledge and skills to develop Microsoft ASP.NET 2.0 Web applications using Microsoft Visual Studio 2005. The workshop focuses on advanced user interfaces, Web site functionality, and implementation details using the advanced features of ASP.NET 2.0 and Visual Studio 2005. Audience This workshop is intended for corporate or independent software vendor (ISV) application developers who have a desire to learn more about specific technology areas in Web application development. At Workshop Completion After completing this workshop, students will be able to: Build dynamic Web applications. Create controls for Web applications. Optimize Web applications. Build customizable Web applications. Build Web Part pages and Web Parts Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 28 de 66 Prerequisites Before attending this workshop, students must: Have attended or studied Workshop 2543A, Core Web Application Technologies with Visual Studio 2005, or possess equivalent knowledge and skills. Know how to use delegates and events. Know how to improve the security of .NET Framework 2.0 applications. Be able to use instrumentation in code Workshop Outline Unit 1: Building Dynamic Web Applications This unit introduces many different aspects of dynamic Web applications. It includes discussions on creating and configuring controls at run time. It then explains how to build dynamic globalization features into a Web application to ensure that it is localizable, including using localized resources and applying different master page layouts in response to culture and language settings. It concludes with explanations about how to enable dynamic configuration for site administrators. Lessons Dynamic Control Creation Localization and Globalization Dynamic Master Pages Dynamic Web Configuration Lab 1: Building Dynamic Web Applications Exercise 1. Dynamically Adding and Configuring Controls Exercise 2. Dynamically Applying Master Pages Exercise 3. Adding Localization Features Exercise 4. Dynamically Configuring Web Applications After completing this unit, students will be able to: Explain dynamic control creation in ASP.NET 2.0. Add and configure controls dynamically. Explain how to incorporate globalization and localization features into Web applications. Add localization features to a Web application. Describe when and how to implement dynamic master pages. Apply master pages dynamically. Describe dynamic Web configuration scenarios. Dynamically configure Web applications. Unit 2: Creating Controls for Web Applications This unit explains how developers create different types of controls for different scenarios. The different types of controls include user controls, custom Web server controls, composite Web server controls, and templated controls. Lessons User Controls Custom Web Server Controls Composite Web Server Controls Templated Controls Lab 2: Creating Controls for Web Applications Exercise 1. Creating User Controls Exercise 2. Creating Custom Web Server Controls Exercise 3. Creating Composite Web Server Controls Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 29 de 66 Exercise 4. Creating Templated Controls After completing this unit, students will be able to: Describe user controls and the underlying enabling technologies. Create user controls. Describe custom Web server controls and the underlying enabling technologies. Create Web server controls. Describe composite controls and how composite controls are created. Create composite Web server controls. Describe templated controls and the interfaces that enable their implementation. Create templated controls Unit 3: Optimizing Web Application Performance This unit introduces topics that will help you improve the performance of Web applications. It describes how the Page Scripting Object Model can help reduce the number of round trips for communication between the server and the browser, and then explains how tracing and instrumentation can be used to monitor and, therefore, improve the performance of a Web application. The unit discusses how caching and asynchronous processing can help increase Web application performance; it then highlights some considerations that developers must address if the Web application is to be deployed in a Web farm environment. Lessons The Page Scripting Object Model Tracing and Instrumentation in Web Applications ASP.NET 2.0 Caching Techniques Asynchronous Processing in Web Applications Web Farm Development Considerations Lab 3: Optimizing Web Application Performance Exercise 1. Accessing the Page Scripting Object Model Exercise 2. Implementing ASP.NET Caching Techniques Exercise 3. Implementing Tracing and Instrumentation Techniques in Web Applications Exercise 4. Implementing Asynchronous Processing in Web Applications After completing this unit, students will be able to: Describe the Page Scripting Object Model. Access Page Scripting Object Model functionality. Explain how to use tracing and instrumentation to monitor and improve the performance of a Web application. Implement tracing and instrumentation in Web applications. Describe ASP.NET 2.0 caching techniques. Implement ASP.NET 2.0 caching techniques. Explain how asynchronous processing can lead to improved performance for Web applications. Implement asynchronous processing in Web applications. Describe strategies for dealing with session state management issues when deploying Web applications in a Web farm environment. Develop Web applications for Web farm environments. Unit 4: Implementing Personalization and Themes in Web Applications This unit introduces building customizable functionality into a Web application by adding personalization support. It discusses using the personalization features of ASP.NET 2.0 to provide this functionality. In addition, it discusses applying themes to Web applications and allowing users to choose color schemes to personalize their experience in using the Web application. It concludes by explaining how to include features that enable users to personalize themes. Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 30 de 66 Lessons ASP.NET 2.0 Personalization Features Theme Support in ASP.NET 2.0 Lab 4: Implementing Personalization and Themes in Web Applications Exercise 1. Configuring Personalization Exercise 2. Implementing Personalization Functionality Exercise 3. Adding Themes to the Web Application Exercise 4. Implementing Personalized Themes After completing this unit, students will be able to: Describe the personalization features provided by ASP.NET 2.0. Describe ASP.NET 2.0 theme support. Configure personalization for a Web application. Implement personalization features. Add themes to a Web application. Implement customizable themes. Unit 5: Building Web Part Pages and Web Parts This unit introduces the concept of a Web part, and describes how it is used in portal pages and other scenarios. It introduces the concept of a Web part page, and discusses how a Web part page contains some Web parts that provide the user interface, along with other controls that manage the Web part infrastructure. Additionally, it introduces the advanced features of connected Web parts and discusses scenarios where they are typically used. Lessons What Is a Web Part? What Is a Web Part Page? Connected Web Parts Lab 5: Building Web Part Pages and Web Parts Exercise 1. Creating a Web Part Page Exercise 2. Creating a Web Part Exercise 3. Creating Connected Web Parts After completing this unit, students will be able to: Describe what a Web Part is and the purpose of Web Parts. Describe the components of a Web Part page and identify scenarios when Web Part pages are useful features of Web applications. Describe the more advanced features of Web Parts, including connections between Web Parts. Create Web Part pages. Create Web Parts. Create connected Web Parts. Core Foundations of Microsoft .NET 2.0 Development Course 2956A: Three days; Instructor-Led Preliminary Course Syllabus Introduction Elements of this syllabus are subject to change. Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 31 de 66 This three-day instructor-led course provides students with the enabling knowledge and skills required to create Microsoft .NET Applications with Visual Studio 2005. Students learn how to develop advanced .NET applications. Audience The audience for this course consists of Application Developers with the skills to develop business applications by using Visual Studio 2005 with either Visual Basic .NET or Visual C#. At Course Completion After completing this course, students will gain the skills to: Develop applications that use system types and collections. Implement service processes, threading, and application domains in a .NET Framework application. Embed configuration, diagnostic, management, and installation features into a .NET Framework application. Implement serialization and input/output functionality in a .NET Framework application. Prerequisites Before attending this course, students must be able to: Understand the purpose and components of the .NET 2.0 Framework and the Common Language Runtime. Understand the components of typical .NET 2.0 applications. Understand and use .NET Framework 2.0 Common Type System (CTS) and how to use variable types including dates/times, numbers, strings, objects and arrays. Use basic file IO classes from the Framework such as StreamReader, StreamWriter, Directory, DirectoryInfo, File and FileInfo. Use basic Framework provided type conversions. Use basic Framework provided text conversion and manipulations including StringBuilder. Use classes with the System.Collections namespace. Use the System.Math class. Basic language syntax for decision structures, loop structures, declaring and using variables. Write code using language specific functionality such as the My. classes for Visual Basic. Understand classes and objects, methods, properties and functions. Write code to implement overridden methods. Understand the class hierarchy present in the .NET Framework 2.0. Write code to declare a class. Write code to create an instance of a class. Write code to compare if an object is equal to another object. Write code to dispose of an object. Understand the lifecycle of an object. Write code to handle exceptions via a try-catch block Write code to implement static methods and properties. Opening and closing solutions. Opening and closing projects. Adding projects to a solution. Removing projects from a solution. Creating new project types. Adding new and existing files to a project. Compile a project. Carry out basic project debugging. Use the object browser. Use the help system especially provided to help VB6.0 developers migrate to .NET. Understand assemblies and how they relate to deployment. Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 32 de 66 Understand and create a deployment project. Be able to create deployment wizards using the Deployment Setup wizard. Select an appropriate deployment project based on the application. Important: This learning product will be most useful to people who are already working in the job role of an application developer and who intend to use their new skills and knowledge on the job immediately after training. Microsoft Certified Professional Exams No Microsoft Certified Professional exams are associated with this course currently. Course Materials The student kit includes a comprehensive workbook and other necessary materials for this class. The following software is provided in the student kit: Student CD Course Outline Module 1: Implementing System Types and Interfaces In this module, students learn about the purpose of system types in the .NET Framework and implementation of special system types introduced in the .NET Framework 2.0. Students also learn about the purpose of interfaces in developing .NET Framework applications. Finally, students learn how to implement system types and interfaces. Lessons Examining Primary System Types Working with Special System Types Working with Interfaces Lab: Implementing System Types and Interfaces After completing this module, students will be able to: Explain the purpose of base system types. Implement generics, Nullable types, exception classes, and attributes. Implement comparison interfaces and the IConvertible, ICloneable, IFormattable, and IDisposable interfaces. Module 2: Implementing Collections and Generics In this module, students learn the basic information on how to work with primary collections, generic collections, specialized collections, and collection base classes. Lessons Examining Collections and Collection Interfaces Working with Primary Collection Types Working with Generic Collections Working with Specialized Collections Working with Collection Base Classes Lab: Implementing Collections and Generics After completing this module, students will be able to: Describe the purpose of collections and collection interfaces. Implement the various classes available in the .NET Framework 2.0. Implement generic list types, collections, dictionary types, and linked-list types. Implement the specialized string and named collection classes. Implement collection base classes and dictionary base types. Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 33 de 66 Module 3: Configuring and Installing Assemblies In this module, students learn how to create, share, install, and configure assemblies in the .NET Framework. Students also learn how to perform installation tasks related to assembly installation. Lessons Working with an Assembly Sharing an Assembly by Using the Global Assembly Cache Installing an Assembly by Using Installation Types Configuring an Assembly by Using Configuration Type Performing Installation Tasks Lab: Configuring and Installing Assemblies After completing this module, students will be able to: Describe the purpose of an assembly and explain how to create the same. Share an assembly by using the global assembly cache. Install an assembly by using the Installer, AssemblyInstaller, ComponentInstaller, InstallerCollection, and InstallContext classes and the InstallEventHandler delegate available in the .NET Framework 2.0. Configure an assembly by using the Configuration, Configuration Element, Configuration Section classes and the configuration base types available in the .NET Framework 2.0. Perform various installation tasks related to assembly installation. Module 4: Monitoring and Debugging Applications In this module, students learn how to manage event logs and application processes. Students also learn how to monitor application performance, debug and trace applications, and embed management information and events in the .NET Framework applications. Lessons Managing an Event Log Working with Application Processes Managing Application Performance Debugging Applications Tracing Applications Embedding Management Information and Events Lab: Monitoring and Debugging Applications After completing this module, students will be able to: Describe event logs and explain how to manage them. Manage application processes by retrieving a list of all processes running on the current system, information about the current process, and a list of all modules used by a process, and by starting and stopping an application process. Monitor and customize application performance by using the Windows Performance Monitor and the performance counter classes available in the .NET Framework 2.0. Debug applications by using the Visual Studio 2005 Debugger, the Debugger, Debug, StackFrame and StackTrace classes, and the Debugger attributes available in the .NET Framework 2.0. Trace applications by using the Trace, TraceSource, Trace Switch, Trace Listener, and CorrelationManager classes available in the .NET Framework 2.0. Embed management information and events in the .NET Framework 2.0 applications. Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 34 de 66 Module 5: Reading and Writing Files In this module, students learn how to manage drives, directories, and files. Students also learn how to work with streams, text, and strings. Finally, students learn how to compress, decompress, and search for patterns within file contents. Lessons Managing the File System Working with Byte Streams Compressing and Protecting Stream Information Managing Application Data Manipulating Strings Efficiently Working with Regular Expressions Lab: Reading and Writing Files After completing this module, students will be able to: Manage the file system by using the Path, File, FileInfo, Directory, DirectoryInfo, DriveInfo, and FileSystemWatcher classes. Work with byte streams by using the Stream, FileStream, MemoryStream, and BufferedStream classes. Compress and protect stream information by using the DeflateStream, GZipStream, IsolatedStorageFile, and IsolatedStorageFileStream classes. Manage application data by using the TextReader, TextWriter, StreamReader, StreamWriter, StringReader, StringWriter, BinaryReader, and BinaryWriter classes. Manipulate strings efficiently by using the StringBuilder class. Work with regular expressions by using the regular expression classes. Module 6: Serializing Data In this module, students learn how to serialize objects into binary and Simple Object Access Protocol (SOAP) formats. The students also learn how to serialize objects into custom XML and how to create custom serialization classes. Lessons Generating Serialized Binary and Soap Formats Generating Serialized XML Formats Creating Custom Serialization Classes Lab: Serializing Data After completing this module, students will be able to: Serialize objects into binary and SOAP formats by using the BinaryFormatter and SoapFormatter classes. Serialize objects into custom XML formats by using the XmlSerializer class, the IXmlSerializable interface, and the XML serialization attributes and delegates. Create custom serialization classes by using serialization types and interfaces, formatter classes, event handler attributes, and the ObjectManager class. Module 7: Implementing Delegates and Events In this module, students learn the concepts of delegates and events and their uses in the .NET framework. Lessons Controlling Interaction Between Components by Using Delegates Controlling Interaction Between Components by Using Events Lab: Implementing Delegates and Events Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 35 de 66 After completing this module, students will be able to: Control interaction between components by using the Delegate class. Control interaction between components by using the Event statement, the EventHandler delegate, and the EventArgs class. Advanced Foundations of Microsoft .NET 2.0 Development Course 2957A: Three days; Instructor-Led Preliminary Course Syllabus Introduction Elements of this syllabus are subject to change. This three-day instructor-led course provides students with the enabling knowledge and skills required to create Microsoft .NET Applications with Visual Studio 2005. Students learn how to develop secured .NET applications. Audience The audience for this course consists of Application Developers with the skills to develop business applications by using Visual Studio 2005 with either Visual Basic .NET or Visual C#. At Course Completion After completing this course, students will gain the skills to: Improve the security of .NET Framework applications by using the .NET Framework 2.0 security features. Implement interoperability, reflection, and mailing functionality in a .NET Framework application. Implement globalization, drawing, and text manipulation functionality in a .NET Framework application. Prerequisites Before attending this course, students must be able to: Understand the purpose and components of the .NET 2.0 Framework and the Common Language Runtime. Understand the components of typical .NET 2.0 applications. Understand and use .NET Framework 2.0 Common Type System (CTS) and how to use variable types including dates/times, numbers, strings, objects and arrays. Use basic file IO classes from the Framework such as StreamReader, StreamWriter, Directory, DirectoryInfo, File and FileInfo. Use basic Framework provided type conversions. Use basic Framework provided text conversion and manipulations including StringBuilder. Use classes with the System.Collections namespace. Use the System.Math class. Basic language syntax for decision structures, loop structures, declaring and using variables. Write code using language specific functionality such as the My. classes for Visual Basic. Understand classes and objects, methods, properties and functions. Write code to implement overridden methods. Understand the class hierarchy present in the .NET Framework 2.0. Write code to declare a class. Write code to create an instance of a class. Write code to compare if an object is equal to another object. Write code to dispose of an object. Understand the lifecycle of an object. Write code to handle exceptions via a try-catch block Write code to implement static methods and properties. Opening and closing solutions. Opening and closing projects. Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 36 de 66 Adding projects to a solution. Removing projects from a solution. Creating new project types. Adding new and existing files to a project. Compile a project. Carry out basic project debugging. Use the object browser. Use the help system especially provided to help VB6.0 developers migrate to .NET. Understand assemblies and how they relate to deployment. Understand and create a deployment project. Be able to create deployment wizards using the Deployment Setup wizard. Select an appropriate deployment project based on the application. Important: This learning product will be most useful to people who are already working in the job role of an application developer and who intend to use their new skills and knowledge on the job immediately after training. Microsoft Certified Professional Exams No Microsoft Certified Professional exams are associated with this course currently. Course Materials The student kit includes a comprehensive workbook and other necessary materials for this class. The following software is provided in the student kit: Student CD Course Outline Module 1: Creating Globalized Applications In this module, students are introduced to the benefits of globalization and localization. Students also learn about the globalization and localization techniques. Lessons Culture Information by Using Globalization Classes Creating a Custom Culture Working with Primary Encoding Classes Working with Advanced Encoding Classes Lab: Creating Globalized Applications After completing this module, students will be able to: Work with culture information by using the CultureInfo, RegionInfo, DateTimeFormatInfo, NumberFormatInfo, and CompareInfo classes. Create a custom culture by using the CultureAndRegionInfoBuilder class. Encode characters by using the Encoding, EncodingInfo, ASCIIEncoding, UTF8Encoding, and UnicodeEncoding classes. Handle failure events by using the Encoder, EncoderFallback, Decoder, and DecoderFallback classes. Module 2: Working with GDI+ in Windows-based Applications In this module, students learn how to use the Graphics Device Interface (GDI+) in applications that are based on Windows Forms by using the .NET Framework. Lessons Working with Graphics, Brushes, Pens, Colors, and Fonts Manipulating the Shapes and Sizes of Graphical Objects Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 37 de 66 Working with Images, Bitmaps, and Icons Lab: Working with GDI+ in Windows-based Applications After completing this module, students will be able to: Create graphical objects by using the Graphics, Pen, Brush, and Font classes and Color types. Manipulate the shapes and sizes of graphical objects by using the Point and Size types. Add images and icons to the drawing surface by using the Image, Bitmap, and Icon classes. Module 3: Implementing Code Access Security In this module, students learn about the code access security mechanisms that can help protect applications not only against untrusted users, but also against some of the subtler problems of malicious code, which may be executed unsuspectingly by trusted users. Lessons Configuring Code Access Security Managing Security Policy Managing Permissions Managing Access Control Managing User Identity Information Lab: Implementing Code Access Security After completing this module, students will be able to: Configure code access security by using the .NET Framework 2.0 Configuration tool and Evidence types. Manage security policy by using the SecurityManager, Code Group, PolicyLevel, PolicyStatement, Condition, IApplicationTrustManager, and IMembershipCondition types. Manage permissions by using the CodeAccessPermission, PermissionSet, and NamedPermissionSet classes and security permission types. Manage access control by using the access control list (ACL) and resource security classes. Manage user identity information by using the GenericIdentity, GenericPrincipal, WindowsIdentity, WindowsPrincipal, Identity Reference, and WindowsImpersonationContext classes. Module 4: Implementing Cryptography In this module, students learn about the new cryptographic types offered by the .NET Framework 2.0, and significant enhancements to the existing types that support symmetric and asymmetric encryption and hashing. Students also learn how to use cryptographic types in .NET Framework applications to ensure secure communication and the protection of sensitive data. Lessons Encrypting Data Hashing Data Extending the Cryptographic Behavior Lab: Implementing Cryptography After completing this module, students will be able to: Encrypt data by using symmetric and asymmetric algorithm classes and the SslStream class. Hash data by using Message Digest Algorithm 5 (MD5), Secure HashAlgorithm 1 (SHA1), and Hashbased Message Authentication Code (HMAC) classes. Extend the cryptographic behavior by using CryptoStream, CryptoConfig, ProtectedData, ProtectedMemory, CspParameters, CryptoAPITransform, and RandomNumberGenerator classes. Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 38 de 66 Module 5: Interoperating Between COM Components and Assemblies In this module, students learn how to create .NET Framework applications that can communicate with COM components and unmanaged DLLs. Students also explore how to use COM components in a .NET Framework application and design your .NET Framework application so that it can be called by a COM component. Lessons Accessing COM Components by Using Interop Services Exposing an Assembly to COM Components by Using Interop Services Accessing COM Components by Using Platform Invocation Services Lab: Interoperating Between COM Components and Assemblies After completing this module, students will be able to: Access COM components by using Interop services. Expose an assembly to COM components by using Interop services. Access COM components by using Platform Invocation Services. Module 6: Working with Service Applications and E-mail Messages In this module, students learn how the .NET Framework simplifies the process of creating service applications by providing the classes necessary to create, install, debug, and monitor service applications. Students also learn how to send e-mail messages from your service application. Lessons Working with a Windows Service Application Working with E-mail Messages Lab: Working with Service Applications and E-mail Messages After completing this module, students will be able to: Manage a Windows service application by using the ServiceBase, ServiceInstaller, ServiceProcessInstaller, and ServiceController classes. Work with e-mail messages by using the MailMessage, MailAddress, MailAddressCollection, MailAttachment, SmtpClient, SmtpException, and SmtpFailedRecipientException classes and the SendCompleteEventHandler delegate. Module 7: Working with Type Metadata In this module, students learn how to retrieve the type metadata for an assembly. Students also learn how to use attributes to control the metadata that is created for their assembly. Finally, students also learn how to dynamically create assemblies at runtime by using the builder classes in the System.Reflection namespace. Lessons Working with Type Metadata by Using Pre-defined Assembly Classes Working with Assemblies Dynamically by Using Custom Classes Lab: Working with Type Metadata After completing this module, students will be able to: Work with type metadata by using the Assembly, MemberInfo, MethodBody, and LocalVariableInfo types and assembly attributes. Work with assemblies dynamically by using builder classes and binding types. Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 39 de 66 Module 8: Creating Multithreaded Applications and Application Domains In this module, students learn about several classes in the System.Threading namespace, provided by the .NET Framework, to manage threads of execution. Lessons Managing Threads in a Synchronous Environment Synchronizing Threads Managing Threads in an Asynchronous Environment Working with Application Domains Lab: Creating Multithreaded Applications and Application Domains After completing this module, students will be able to: Manage threads in a synchronous environment by using the Thread and ThreadPool classes. Synchronize threads by using the Monitor, Mutex, ReaderWriterLock, Semaphore, EventWaitHandle, RegisteredWaitHandle, and Interlocked classes. Manage threads in an asynchronous environment by using asynchronous, execution context, SynchronizationContext, and thread exception types. Work with application domains by using the AppDomainSetup and AppDomain classes. Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 40 de 66 2778 Writing Queries Using Microsoft SQL Server 2008 Transact-SQL (3 days) Introduction Elements of this syllabus are subject to change. This 3-day instructor led course provides students with the technical skills required to write basic TransactSQL queries for Microsoft SQL Server 2008. Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 41 de 66 Audience This course is intended for SQL Server database administrators, implementers, system engineers, and developers who are responsible for writing queries. At Course Completion After completing this course, students will be able to: Describe the uses of and ways to execute the Transact-SQL language. Use querying tools. Write SELECT queries to retrieve data. Group and summarize data by using Transact-SQL. Join data from multiple tables. Write queries that retrieve and modify data by using subqueries. Modify data in tables. Query text fields with full-text search. Describe how to create programming objects. Use various techniques when working with complex queries. Prerequisites Before attending this course, students must have: Logical database design. Physical database design. How data is stored in tables (rows and columns). Data integrity concepts. Relationships between tables and columns (primary key and foreign key, one-to-one, one-to-many, and many-to-many). Basic knowledge of the Microsoft Windows operating system and its core functionality. For example, how to use Windows Explorer, open and save files, and what a client/server application interaction means. Course Outline Module 1: Getting Started with Databases and Transact-SQL in SQL Server 2008 The student will be introduced to how client/server architecture works, and examine the various database and business tasks that can be performed by using the components of SQL Server 2008. The student will also be introduced to SQL Server database concepts such as relational databases, normalization, and database objects. In addition, the student will learn how to use T-SQL to query databases and generate reports. Lessons Lesson 1: Overview of SQL Server 2008 Lesson 2: Overview of SQL Server Databases Lesson 3: Overview of the SQL Language Lesson 4: Syntax Elements of T-SQL Lesson 5: Working with T-SQL Scripts Lesson 6: Using T-SQL Querying Tools Lab: Getting Started with Databases and Transact-SQL in SQL Server 2008 Exercise 1: (Level 200) Exploring SQL Server Management Studio Exercise 2: (Level 200) Executing Queries in SQL Server Management Studio Exercise 3: (Level 200) Examining a Database Diagram in SQL Server Management Studio Exercise 4: (Level 200) Using Excel to Generate a Report from a SQL Server Database Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 42 de 66 After completing this module, students will be able to: Describe the architecture and components of SQL Server 2008. Describe the structure of a SQL Server database. Explain the basics of the SQL language. Describe the syntax elements of T-SQL. Explain how to manage T-SQL scripts. Use T-SQL querying tools to query SQL Server 2008 databases. Module 2: Querying and Filtering Data The students will be introduced to the basic Transact-SQL (T-SQL) statements that are used for writing queries, filtering data, and formatting result sets. Lessons Lesson 1: Using the SELECT Statement Lesson 2: Filtering Data Lesson 3: Working with NULL Values Lesson 4: Formatting Result Sets Lesson 5: Performance Considerations for Writing Queries Lab: Querying and Filtering Data Exercise 1 (Level 200): Retrieving Data by Using the SELECT Statement Exercise 2 (Level 200): Filtering Data by Using Search Conditions Exercise 3: (Level 200) Using Functions to Work with NULL Values Exercise 4: (Level 200) Formatting Result Sets Exercise 5: (Level 200) Rewriting Queries for Performance After completing this module, students will be able to: Retrieve data by using the SELECT statement. Filter data by using different search conditions. Explain how to work with NULL values. Format result sets. Describe the performance considerations that affect data retrieval. Module 3: Grouping and Summarizing Data The students will learn to group and summarize data when generating reports in Microsoft SQL Server 2008 by using aggregate functions and the COMPUTE clause. Lessons Lesson 1: Summarizing Data by Using Aggregate Functions Lesson 2: Summarizing Grouped Data Lesson 3: Ranking Grouped Data Lesson 4: Creating Crosstab Queries Lab: Grouping and Summarizing Data Exercise 1: (Level 200) Summarizing Data by Using Aggregate Functions Exercise 2: (Level 200) Summarizing Grouped Data Exercise 3: (Level 200) Ranking Grouped Data Exercise 4: (Level 200) Creating Crosstab Queries After completing this module, students will be able to: Summarize data by using aggregate functions. Summarize grouped data by using the GROUP BY and COMPUTE clauses. Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 43 de 66 Rank grouped data. Create cross-tabulation queries by using the PIVOT and UNPIVOT clauses. Module 4: Joining Data from Multiple Tables The students will learn to write joins to query multiple tables, as well as limiting and combining result sets. Lessons Lesson 1: Querying Multiple Tables by Using Joins Lesson 2: Applying Joins for Typical Reporting Needs Lesson 3: Combining and Limiting Result Set Lab: Joining Data from Multiple Tables Exercise 1: (Level 200) Querying Multiple Tables by Using Joins Exercise 2: (Level 200) Applying Joins for Typical Reporting Needs Exercise 3: (Level 200) Combining and Limiting Result Sets After completing this module, students will be able to: Query multiple tables by using joins. Apply joins for typical reporting needs. Combine and limit result sets. Module 5: Working with Subqueries The students will be introduced to basic and correlated subqueries and how these compare with joins and temporary tables. The students will also be introduced to using common table expressions in queries. Lessons Lesson 1: Writing Basic Subqueries Lesson 2: Writing Correlated Subqueries Lesson 3: Comparing Subqueries with Joins and Temporary Tables Lesson 4: Using Common Table Expressions Lab: Working with Subqueries Exercise 1: (Level 200) Writing Basic Subqueries Exercise 2: (Level 200) Writing Correlated Subqueries Exercise 3: (Level 200) Comparing Subqueries with Joins and Temporary Tables Exercise 4: (Level 200) Using Common Table Expressions After completing this module, students will be able to: Write basic subqueries. Write correlated subqueries. Compare subqueries with joins and temporary tables. Use common table expressions in queries. Module 6: Modifying Data in Tables The students will be able to modify the data in tables by using the INSERT, DELETE, and UPDATE statements. In addition, students will examine how transactions work in a database, the importance of transaction isolation levels, and how to manage transactions. Lessons Lesson 1: Overview of Transactions Lesson 2: Inserting Data into Tables Lesson 3: Deleting Data from Tables Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 44 de 66 Lesson 4: Updating Data in Tables Lab: Modifying Data in Tables Exercise 1: (Level 200) Inserting Data into Tables Exercise 2: (Level 200) Deleting Data from Tables Exercise 3: (Level 200) Updating Data in Tables Exercise 4: (Level 200) Working with Transactions After completing this module, students will be able to: Describe transactions. Insert data into tables. Delete data from tables. Update data in tables. Module 7: Querying Metadata, XML, and Full-Text Indexes The students will learn to query semi-structured and unstructured data. The students will also learn how SQL Server 2008 handles XML data and will query XML data. The students will also be introduced to full-text indexing in SQL Server 2008. Lessons Lesson 1: Querying Metadata Lesson 2: Overview of XML Lesson 3: Querying XML Data Lesson 4: Overview of Full-Text Indexes Lesson 5: Querying Full-Text Indexes Lab: Querying Metadata, XML, and Full-Text Indexes Exercise 1: (Level 200) Querying Metadata Exercise 2: (Level 200) Querying XML Data Exercise 3: (Level 200) Creating and Querying Full-Text Indexes After completing this module, students will be able to: Query metadata. Describe the functionality of XML. Query XML data. Describe the functionality of full-text indexes. Query full-text indexes. Module 8: Using Programming Objects for Data Retrieval The students will be introduced to user-defined functions and executing various kinds of queries by using user-defined functions. The students will be introduced to SQL Server views that encapsulate data and present users with limited and relevant information. In addition, the students will be introduced to SQL Server stored procedures and the functionalities of the various programming objects. The students will learn how to perform distributed queries and how SQL Server works with heterogeneous data such as databases, spreadsheets, and other servers. Lessons Lesson 1: Encapsulating Expressions by Using User-Defined Functions Lesson 2: Encapsulating Queries by Using Views Lesson 3: Overview of Stored Procedures Lesson 4: Writing Distributed Queries Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 45 de 66 Lab: Using Programming Objects for Data Retrieval Exercise 1: (Level 300) Creating User-Defined Functions Exercise 2: (Level 200) Creating Views Exercise 3: (Level 300) Writing Distributed Queries After completing this module, students will be able to: Encapsulate expressions by using user-defined functions. Encapsulate queries by using views. Explain how stored procedures encapsulate T-SQL logic. Write distributed queries Module 9: Using Advanced Querying Techniques The students will be introduced to best practices for querying complex data. The students will also examine how to query complex table structures such as data stored in hierarchies and self-referencing tables. The students will analyze the recommended guidelines for executing queries and how to optimize query performance. Lessons Lesson 1: Considerations for Querying Complex Data Lesson 2: Querying Complex Table Structures Lesson 3: Writing Efficient Queries Lesson 4: Using Different Techniques for Complex Queries Lesson 5: Maintaining Query Files Lab: Using Advanced Querying Techniques Exercise 1: (Level 300) Breaking up a Complex Business Reporting Requirement Exercise 2: (Level 300) Writing Complex Queries Exercise 3: (Level 300) Rewriting Complex Queries After completing this module, students will be able to: Explain the recommendations for querying complex data. Query complex table structures. Write efficient queries. Use various techniques when working with complex queries. Maintain query files. Implementing a Microsoft SQL Server 2005 Database Course 2779: Five days Introduction Elements of this syllabus are subject to change. This five-day instructor-led course provides students with the knowledge and skills to implement a Microsoft SQL Server 2005 database. The course focuses on teaching individuals how to use SQL Server 2005 product features and tools related to implementing a database. Audience This course is intended for IT Professionals who want to become skilled on SQL Server 2005 product features and technologies for implementing a database. At Course Completion After completing this course, students will be able to: Create databases and database files. Create data types and tables. Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 46 de 66 Use XML-related features in Microsoft SQL Server 2005. Plan, create, and optimize indexes. Implement data integrity in Microsoft SQL Server 2005 databases by using constraints. Implement data integrity in Microsoft SQL Server 2005 by using triggers. Implement views. Implement stored procedures. Implement functions. Implement managed code in the database. Manage transactions and locks. Use Service Broker to build a messaging-based solution. Use Notification Services to generate and send notifications. Prerequisites Before attending this course, students must have: Basic knowledge of the Microsoft Windows operating system and its core functionality. Working knowledge of Transact-SQL. Working knowledge of relational databases. Some experience with database design. In addition, it is recommended, but not required, that students have completed: Course 2778: Writing Queries Using Microsoft SQL Server 2005 Transact-SQL. Course Outline Module 1: Creating Databases and Database Files This module explains how to create databases, filegroups, schemas, and database snapshots. Lessons Creating Databases Creating Filegroups Creating Schemas Creating Database Snapshots Lab 1: Creating Databases and Database Files Creating a Database Creating Schemas Creating a Database Snapshot After completing this module, students will be able to: Create databases. Create filegroups. Create schemas. Create database snapshots. Module 2: Creating Data Types and Tables This module explains how to create data types and tables. It also describes how to create partitioned tables. Lessons Creating Data Types Creating Tables Creating Partitioned Tables Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 47 de 66 Lab 2: Creating Data Types and Tables Creating Data Types Creating Tables Creating Partitioned Tables After completing this module, students will be able to: Create new data types. Create new tables. Create partitioned tables Module 3: Using XML This module explains how to use the FOR XML clause and the OPENXML function. It also describes how to use the xml data type and its methods. Lessons Retrieving XML by Using FOR XML Shredding XML by Using OPENXML Introducing XQuery Using the xml Data Type Lab 3: Using XML Mapping Relational Data and XML Storing XML Natively in the Database Using XQuery with xml Methods After completing this module, students will be able to: Retrieve XML by using the FOR XML clause. Shred XML by using the OPENXML function. Use XQuery expressions. Use the xml data type. Module 4: Creating and Tuning Indexes This module explains how to plan, create, and optimize indexes. It also describes how to create XML indexes. Lessons Planning Indexes Creating Indexes Optimizing Indexes Creating XML Indexes Lab 4: Creating and Tuning Indexes Creating Indexes Tuning Indexes Creating XML Indexes After completing this module, students will be able to: Plan indexes. Create indexes. Optimize indexes. Create XML indexes. Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 48 de 66 Module 5: Implementing Data Integrity by Using Constraints This module explains how to implement constraints and provides an overview of data integrity. Lessons Data Integrity Overview Implementing Constraints Lab 5: Implementing Data Integrity by Using Constraints Creating Constraints Disabling Constraints After completing this module, students will be able to: Describe the options for enforcing data integrity in SQL Server 2005. Implement data integrity in SQL Server 2005 databases by using constraints. Module 6: Implementing Data Integrity by Using Triggers and XML Schemas This module explains how to implement triggers and XML schemas. Lessons Implementing Triggers Implementing XML Schemas Lab 6: Implementing Data Integrity by Using Triggers and XML Schemas Creating Triggers Implementing XML Schemas After completing this module, students will be able to: Implement data integrity in SQL Server 2005 databases by using triggers. Implement data integrity in SQL Server 2005 databases by using XML schemas. Module 7: Implementing Views This module explains how to create views. Lessons Introduction to Views Creating and Managing Views Optimizing Performance by Using Views Lab 7: Implementing Views Creating Views Creating Indexed Views Creating Partitioned Views After completing this module, students will be able to: Describe the purpose of views. Create and manage views. Explain how to optimize query performance by using views. Module 8: Implementing Stored Procedures This module explains how to create stored procedures and functions. It also describes execution plans, plan caching, and query compilation. Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 49 de 66 Lessons Implementing Stored Procedures Creating Parameterized Stored Procedures Working With Execution Plans Handling Errors Lab 8: Implementing Stored Procedures Creating Stored Procedures Working With Execution Plans After completing this module, students will be able to: Implement stored procedures. Create parameterized stored procedures. Work with execution plans. Handle errors in stored procedures. Module 9: Implementing Functions This module explains how to create functions. It also describes how to control the execution context. Lessons Creating and Using Functions Working with Functions Controlling Execution Context Lab 9: Implementing Functions Creating Functions Controlling Execution Context After completing this module, students will be able to: Create and use functions. Work with functions. Control execution context. Module 10: Implementing Managed Code in the Database This module explains how to implement managed database objects. Lessons Introduction to the SQL Server Common Language Runtime Importing and Configuring Assemblies Creating Managed Database Objects Lab 10: Implementing Managed Code in the Database Importing an Assembly Creating Managed Database Objects After completing this module, students will be able to: Identify appropriate scenarios for managed code in the database. Import and configure assemblies. Create managed database objects. Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 50 de 66 Module 11: Managing Transactions and Locks This module explains how to use transactions and the SQL Server locking mechanisms to meet the performance and data integrity requirements of your applications. Lessons Overview of Transactions and Locks Managing Transactions Understanding SQL Server Locking Architecture Managing Locks Lab 11: Managing Transactions and Locks Using Transactions Managing Locks After completing this module, students will be able to: Describe how SQL Server 2005 transactions use locks. Execute and cancel a transaction. Describe concurrency issues and SQL Server 2005 locking mechanisms. Manage locks. Module 12: Using Service Broker This module explains how to build a messaging-based solution with Service Broker. Lessons Service Broker Overview Creating Service Broker Objects Sending and Receiving Messages Lab 12: Using Service Broker (Optional) Creating Service Broker Objects Implementing the Initiating Service Implementing the Target Service After completing this module, students will be able to: Describe Service Broker functionality and architecture. Create Service Broker objects. Send and receive Service Broker messages. Module 13: Using Notification Services (Optional) This module explains how to develop applications that generate and send timely messages to subscribers. Lessons Introduction to Notification Services Developing Notification Services Solutions After completing this module, students will be able to: Describe how Notification Services operates. Develop a Notification Services application. Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 51 de 66 Maintaining a Microsoft SQL Server 2005 Database Course 2780B: Five days Introduction Elements of this syllabus are subject to change. This five-day instructor-led course provides students with the knowledge and skills to maintain a Microsoft SQL Server 2005 database. The course focuses on teaching individuals how to use SQL Server 2005 product features and tools related to maintaining a database. Audience This course is intended for IT Professionals who want to become skilled on SQL Server 2005 product features and technologies for maintaining a database. At Course Completion After completing this course, students will be able to: Install and configure SQL Server 2005. Manage database files. Backup and restore databases. Manage security. Monitor SQL Server. Transfer data into and out of SQL Server. Automate administrative tasks. Replicate data between SQL Server instances. Maintain high availability. Prerequisites Before attending this course, students must have: Basic knowledge of the Microsoft Windows operating system and its core functionality. Working knowledge of Transact-SQL. Working knowledge of relational databases. Some experience with database design. In addition, it is recommended, but not required, that students have completed: Course 2778: Writing Queries Using Microsoft SQL Server 2005 Transact-SQL. Course 2779: Implementing a Microsoft SQL Server 2005 Database. Course Outline Module 1: Installing and Configuring SQL Server 2005 This module explains how to plan for and install SQL Server 2005, how to manage a SQL Server 2005 installation, and how to use the SQL Server 2005 administrative tools. Lessons Preparing to Install SQL Server Installing SQL Server 2005 Managing a SQL Server 2005 Installation Lab 1: Installing and Configuring SQL Server 2005 Performing an Installation Managing SQL Server After completing this module, students will be able to: Explain how to prepare the hardware and other resources necessary to install SQL Server 2005. Install SQL Server 2005. Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 52 de 66 Manage and configure a SQL Server 2005 installation. Module 2: Managing Databases and Files This module explains how to manage databases and files. Lessons Planning Databases Creating Databases Managing Databases Lab 2: Managing Databases and Files Creating a Database Monitoring and Managing Filegroup Usage Viewing Database Metadata After completing this module, students will be able to: Plan how to implement a database that meets an organization's requirements. Create a SQL Server database. Manage a SQL Server database. Module 3: Disaster Recovery This module explains how to plan and implement a backup and restore strategy. Lessons Planning a Backup Strategy Backing Up User Databases Restoring User Databases Performing Online Restore Operations Recovering Data from Database Snapshots System Database and Disaster Recovery Lab 3: Disaster Recovery Implementing a Backup Strategy Restoring and Recovering a Database Performing Piecemeal Backup and Restore Operations Restoring the master Database After completing this module, students will be able to: Plan a backup strategy for a database. Back up user databases. Restore user databases from backups. Restore data in a user database while it is online. Recover data for a user database from a database snapshot. Restore and recover systems databases. Module 4: Managing Security This module explains how to manage principals, securables, and permissions, and how to implement cryptography in a SQL Server database. Lessons Overview of SQL Server Security Protecting the Server Scope Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 53 de 66 Protecting the Database Scope Managing Keys and Certificates in SQL Server Lab 4: Managing Security Creating Logins and Assigning Server-Scope Permissions Creating and Managing Users Using a Certificate to Protect Data After completing this module, students will be able to: Describe how SQL Server manages security. Protect SQL Server at the server level. Protect SQL Server databases. Use keys and certificates to protect SQL Server objects. Module 5: Monitoring SQL Server This module explains how to monitor SQL Server performance and activity. Lessons Viewing Current Activity Using System Monitor Using SQL Server Profiler Using DDL Triggers Using Event Notifications Lab 5: Monitoring SQL Server Monitoring SQL Server Performance Tracing SQL Server Activity Implementing DDL Triggers After completing this module, students will be able to: Examine the current activity in a SQL Server instance. Use System Monitor to obtain performance data about your computer and the instances of SQL Server running on your computer. Use SQL Server Profiler to trace server and database activity. Implement DDL triggers that enable you to audit changes to the structure of database objects. Use event notifications to capture and monitor significant events for a SQL Server instance. Module 6: Transferring Data This module explains how to transfer and transform data. Lessons Overview of Data Transfer Introduction to SQL Server Integration Services Using SQL Server Integration Services Features of SQL Server Integration Services Lab 6: Transferring Data Creating an SSIS Package Deploying an SSIS Package Using SSIS to Extract Data, Perform Lookups, Sort, and Split Data After completing this module, students will be able to: Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 54 de 66 Describe the problems surrounding data transfer and the tools that SQL Server 2005 provides to perform data transfer. Describe the purpose of SQL Server Integration Services. Use SQL Server Integration Services to transfer data into a SQL Server database. Module 7: Automating Administrative Tasks This module explains how to use the SQL Server Agent to automate administrative tasks. Lessons Automating Administrative Tasks in SQL Server 2005 Configuring the SQL Server Agent Creating Jobs and Operators Creating Alerts Managing Multiple Servers Managing SQL Server Agent Security Lab 7: Automating Administrative Tasks Configuring SQL Server Agent Creating Operators and Jobs Creating Alerts After completing this module, students will be able to: Define SQL Server 2005 administrative tasks and schedule these tasks to run automatically. Configure SQL Server Agent to support automatic task scheduling. Script tasks by using SQL Server jobs, and define operators for managing these jobs. Define alerts to warn operators about events raised by SQL Server. Define and manage administrative tasks that span multiple servers. Configure SQL Server Agent security. Module 8: Implementing Replication This module explains the purpose of replication, introduces the concepts underpinning replication, and describes how to implement replication in several common scenarios. Lessons Overview of Replication Implementing Replication Configuring Replication in Some Common Scenarios Lab 8: Implementing Replication Creating a Publication Creating a Subscription Implementing HTTP Merge Replication After completing this module, students will be able to: Describe replication and its components. Configure and implement replication. Use replication to meet the requirements of some common scenarios. Module 9: Maintaining High Availability This module explains how to implement high availability technologies with SQL Server 2005. Lessons Introduction to High Availability Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 55 de 66 Implementing Server Clustering Implementing Database Mirroring Implementing Log Shipping Implementing Peer-to-Peer Replication Lab 9: Configuring Database Mirroring to Support Failover Implementing Distributed High Availability After completing this module, students will be able to: Describe the factors affecting database availability. Explain how to implement clustering to support fast failover of computers running Microsoft SQL Server instances. Describe how to use SQL Server mirroring to implement a software solution for fast failover. Describe how to implement log shipping to support fast recovery of a standby SQL Server database. Explain how to use peer-to-peer replication to implement high availability in a distributed environment. Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 56 de 66 Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 57 de 66 6425A: Configuring Windows Server 2008 Active Directory Domain Services (5 days) Note: You are viewing a Preliminary Course Syllabus. This course is not yet available. Because some parts of the course are currently in development, some elements of this syllabus are subject to change. Introduction Elements of this syllabus are subject to change. This five-day instructor-led course provides to teach Active Directory Technology Specialists with the knowledge and skills to configure Active Directory Domain Services in a distributed environment, implement Group Policies, perform backup and restore, and monitor and troubleshoot Active Directory related issues. Audience The primary audience for this course are AD Technology Specialists, Server Administrators, and Enterprise Administrators who want to learn how to implement AD in a distributed environment, secure domains using Group Policies, and perform backup, restore, and monitor and troubleshoot AD configuration to ensure trouble free operation. At Course Completion After completing this course, students will be able to implement and configure Active Directory domain services in their enterprise environment. Prerequisites Before attending this course, students must have: Basic understanding of networking. Intermediate understanding of network operating systems. An awareness of security best practices. Basic knowledge of server hardware. A+ or equivalent knowledge Some experience creating objects in Active Directory. Foundation course (6424A) or equivalent knowledge. Basic concepts of backup and recovery in a Windows Server Environment. Course Outline Module 1: Installing Active Directory Domain Services This module explains how to install and configure Active Directory Domain Services and install and configure a read-only domain controller. Lessons Installing Active Directory Domain Services Deploying Read-Only Domain Controllers Configuring AD DS Domain Controller Roles Lab: Implementing Read-Only Domain Controllers Exercise 1: Evaluating Forest and Server Readiness for Installing an RODC Exercise 2: Installing and Configuring an RODC Exercise 3: Configuring AD DS Domain Controller Roles After completing this module, students will be able to: Install Active Directory Domain Services. Deploy Read-Only Domain Controllers. Configure AD DS Domain Controller Roles. Module 2: Configuring DNS for AD DS This module explains how to configure Domain Name Services (DNS) for Active Directory Domain Services. Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 58 de 66 Lessons Overview of Active Directory Domain Services and DNS Integration Configuring Active Directory Integrated Zones Configuring Read Only DNS Lab: Configuring AD DS and DNS Integration Exercise 1: Configuring Active Directory Integrated Zones Exercise 2: Configuring Read-Only DNS Zones After completing this module, students will be able to: Describe Active Directory Domain Services and DNS Integration. Configure Active Directory Integrated Zones. Configure Read Only DNS. Module 3: Configuring Active Directory Objects and Trusts This module explains how to configure Active Directory Objects and Trusts. Lessons Configuring Active Directory Objects Automating AD DS Object Management Delegating Administrative Access to AD DS Objects Configuring AD DS Trusts Lab: Configuring Active Directory Objects and Trusts Exercise 1: Configuring AD DS Objects Exercise 2: Automating the Management of AD DS Objects Exercise 3: Delegating Control of AD DS Objects Exercise 4: Configuring AD DS Trusts After completing this module, students will be able to: Configure Active Directory Objects. Automate AD DS object management. Delegate Administrative access to AD DS objects. Configure AD DS trusts. Module 4: Configuring Active Directory Sites and Replication This module explains how to configure Active Directory Objects and Trusts. Lessons Overview of AD DS Replication Configuring Active Directory Domain Services Sites Configuring and Monitoring AD DS Replication Lab: Configuring Active Directory Sites and Replication Exercise 1: Configuring AD DS Sites and Subnets Exercise 2: Configuring AD DS Replication Exercise 3: Monitoring AD DS Replication After completing this module, students will be able to: Describe AD DS replication. Configure Active Directory Domain Services sites. Configure and monitor AD DS replication. Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 59 de 66 Module 5: Creating and Configuring Group Policies This module explains how to create and configure group policies. Lessons Overview of Group Policies Configuring the Scope of Group Policy Objects Evaluating the Application of Group Policy Objects Managing Group Policy Objects Delegating Administrative Control of Group Policies Lab: Creating and Configuring GPOs Exercise 1: Creating Group Policy Objects Exercise 2: Managing the Scope of GPO Application Exercise 3: Verifying GPO Application Exercise 4: Managing GPOs Exercise 5: Delegating Administrative Control of GPOs After completing this module, students will be able to: Describe Group Policies. Configure the scope of Group Policy objects. Evaluate the application of Group Policy objects. Manage Group Policy objects. Delegate administrative control of Group Policies. Module 6: Configuring User Environments Using Group Policies This module explains how to configure user environments using Group Policies. Lessons Configuring Group Policy Settings Configuring Scripts and Folder Redirection Using Group Policies Configuring Administrative Templates Deploying Software Using Group Policy Lab Configuring User Environments Using Group Policies Exercise 1: Configuring Scripts and Folder Redirection Exercise 2: Configuring Administrative Templates Exercise 3: Distributing Software Using Group Policies Exercise 4: Verifying GPO Application After completing this module, students will be able to: Configure Group Policy settings. Configure scripts and folder redirection Using Group Policies. Configure administrative templates. Deploy software using Group Policy. Module 7: Implementing Security Using Group Policies This module explains how to implement security using Group Policies. Lessons Configuring Security Policies Implementing Fine-Grained Password Policies Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 60 de 66 Restricting Group Membership and Access to Software Managing Security Using Security Templates Lab: Implementing Security by Using Group Policies Exercise 1: Configuring Domain Security Settings Exercise 2: Implementing Fine-Grained Password Policies Exercise 3: Configuring Restricted Groups and Software Restriction Policies Exercise 4: Configuring Security Templates Exercise 5: Verifying the Security Configuration After completing this module, students will be able to: Configure security settings. Implement fine-grained password policies. Restrict group membership and access to software. Manage security using security templates. Module 8: Implementing an Active Directory Domain Services Monitoring Plan This module explains how to implement Active Directory Domain Services monitoring plan. Lessons Monitoring Active Directory Domain Services Using Event Viewer Monitoring Active Directory Domain Servers by Using Reliability and Performance Monitor Configuring Active Directory Domain Services Auditing Lab: Monitoring Active Directory Domain Services Exercise 1: Monitor AD DS by Using Event Viewer Exercise 2: Monitor AD DS by Using Performance and Reliability Monitor Exercise 3: Configure AD DS Auditing After completing this module, students will be able to: Monitor Active Directory Domain Services using Event Viewer. Monitor Active Directory Domain servers using reliability and performance monitor. Configure Active Directory Domain Services Auditing. Module 9: Implementing an Active Directory Domain Services Maintenance Plan This module explains how to implement an Active Directory Domain Services maintenance plan. Lessons Maintaining the AD DS Domain Controllers Backing Up Active Directory Domain Services Restoring Active Directory Domain Services Lab: Implementing an Active Directory Domain Services Maintenance Plan Exercise 1: Maintaining AD DS Domain Controllers Exercise 2: Backing Up AD DS Exercise 3: Performing a Non-Authoritative Restore of the AD DS Database Exercise 4: Performing an Authoritative Restore of the AD DS Database Exercise 5: Restoring Data By Using the AD DS Snapshot Viewer After completing this module, students will be able to: Maintain the AD DS Domain Controllers. Back up the Active Directory Domain Services. Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 61 de 66 Restore the Active Directory Domain Services. Module 10: Troubleshooting This module explains how to troubleshoot Active Directory Domain Services, Domain Name Service, and Active Directory replication. Lessons Troubleshooting Active Directory Domain Services Troubleshooting DNS Integration with AD DS Troubleshooting AD DS Replication Lab: Troubleshooting Active Directory, DNS, and Replication Issues Exercise 1: Troubleshooting Authentication and Authorization Errors Exercise 2: Troubleshooting the Integration of DNS and AD DS Exercise 3: Troubleshooting AD DS Replication After completing this module, students will be able to: Troubleshoot Active Directory Domain Services. Troubleshoot DNS integration with AD DS. Troubleshoot AD DS replication. Module 11: Troubleshooting Group Policy Issues This module explains how to troubleshoot the application of group policy objects. Lessons Introduction to Group Policy Troubleshooting Troubleshooting Group Policy Application Troubleshooting Group Policy Settings Lab: Troubleshooting Group Policy Issues Exercise 1: Troubleshooting Group Policy Applications Exercise 2: Troubleshooting Group Policy Settings After completing this module, students will be able to: Describe Group Policy troubleshooting. Troubleshoot Group Policy application. Troubleshoot Group Policy Settings. Module 12: Implementing an Active Directory Domain Services Infrastructure This module explains how to implement an Active Directory Domain Services Infrastructure. Lessons Overview of the AD DS Deployment Lab: Deploying Active Directory Domain Services Exercise 1: Deploying Active Directory Domain Services Exercise 2: Deploying AD DS Sites Exercise 3: Implementing Group Policies Exercise 4: Verifying the AD DS Deployment Exercise 5: Testing the AD DS Disaster Recovery Plan After completing this module, students will be able to: Implement an Active Directory Domain Services infrastructure. Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 62 de 66 6426A: Configuring Identity and Access Solutions with Windows Server 2008 Active Directory (3 days) Note: You are viewing a Preliminary Course Syllabus. This course is not yet available. Because some parts of the course are currently in development, some elements of this syllabus are subject to change. Introduction Elements of this syllabus are subject to change. This three-day instructor-led course provides the knowledge and skills that IT Professionals need to configure identity and access solutions with Windows Server 2008 Active Directory. Audience The audience for this course is IT Professionals interested in IDA solutions in their enterprise environment. Most students will be IT professionals who are responsible for integrating applications and platforms with enterprise directory and security services while increasing access to a growing number of customers and partners. At Course Completion After completing this course, students will be able to: Describe identity and access solutions. Configure Active Directory Certificate Services. Deploy and manage certificates. Configure Active Directory Lightweight Directory Services. Configure Active Directory Federation Services. Configure Active Directory Rights Management Services. Maintain access management solutions. Troubleshoot identity and access solutions. Prerequisites This course requires that students meet the following prerequisites: Technical knowledge equivalent to 6424: Fundamentals of Microsoft Server 2008 Active Directory Technical background knowledge and hands-on experience of Active Directory Domain Services (AD DS from the AD TS foundation exam). This includes technical knowledge equivalent to 6425A: Configuring Windows Server 2008 Active Directory Domain Services Course Outline Module 1: Exploring Identity and Access Solutions After completing this module, students will be able to explore identity and access solutions. Lessons Overview of Identity and Access Management Active Directory Server Roles in Identity and Access Management Identity Lifecycle Manager Lab: Exploring Identity and Access Solutions 2008 Exploring how Active Directory server roles will provide identity and access management solutions After completing this module, students will be able to: Describe identity and access management. Identify Active Directory server roles in identity and access management. Understand Identity Lifecycle Manager. Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 63 de 66 Module 2: Configuring Active Directory Certificate Services After completing this module, students will be able to configure Active Directory Certificate Services. Lessons Overview of Public Key Infrastructure Deploying a Certification Authority Hierarchy Installing Active Directory Certificate Services Managing a Certification Authority Lab: Configuring Active Directory Certificate Services Installing AD CS as an Enterprise Root CA Installing Enterprise Subordinate CA Configuring CA Configuring AD CS After completing this module, students will be able to: Describe Public Key Infrastructure. Deploy a Certification Authority hierarchy. Install Active Directory Certificate Services. Manage a Certification Authority. Module 3: Deploying and Managing Certificates After completing this module, students will be able to deploy and manage certificates. Lessons Deploying Certificates by Using AD CS Deploying Certificates by Using Autoenrollment Revoking Certificates Configuring Certificate Templates Configuring Certificate Recovery Lab: Deploying and Managing Certificates Issuing and Automating the Issuing of Certificates by Using AD CS Managing Enrollment Revoking Certificates Configuring and Issuing Certificate Templates Configuring Certificate Recovery After completing this module, students will be able to: Deploy certificates by using AD CS. Use autoenrollment to deploy certificates. Revoke certificates. Configure certificate templates. Configure certificate recovery. Module 4: Configuring Active Directory Lightweight Directory Services After completing this module, students will be able to configure Active Directory Lightweight Directory Services. Lessons Installing and Configuring AD LDS Configuring AD LDS Instances Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 64 de 66 Configuring AD LDS Replication Configuring AD LDS Integration with AD DS Lab: Configuring Active Directory Lightweight Directory Services Installing and Configuring AD LDS Creating AD LDS Partitions and Instances Configuring AD LDS Replication Discussions about Exercise 1-3 results After completing this module, students will be able to: Install and configure AD LDS. Configure AD LDS instances. Configure AD LDS replication. Configure AD LDS integration with AD DS. Module 5: Configuring Active Directory Federation Services After completing this module, students will be able to configure Active Directory Federation Services. Lessons Overview of AD FS AD FS Deployment Scenarios Deploying AD FS Implementing AD FS Claims Lab: Configuring AD FS Installing AD FS in the Partner and Account Organization Configuring AD FS Proxy Servers Configuring Web Application Server Configuring Claims Aware Application Testing the Functionality of AD FS Installing Identity Management for UNIX (Server-only) After completing this module, students will be able to: Describe AD FS. Understand AD FS deployment scenarios. Deploy AD FS. Implement AD FS claims. Module 6: Configuring Active Directory Rights Management Services After completing this module, students will be able to configuring Active Directory Rights Management Services. Lessons Overview of AD RMS Installing and Configuring AD RMS Server Components Administering AD RMS Implementing AD RMS Trust Policies Lab: Configuring Active Directory Rights Management Services Installing and Configuring AD RMS Configuring ADRMS Client Settings and AD RMS Templates Testing AD RMS Functionality Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 65 de 66 After completing this module, students will be able to: Describe AD RMS. Install and configure AD RMS server components. Administer AD RMS. Implement AD RMS trust policies. Module 7: Maintenance of Access Management Solutions After completing this module, students will be able to maintain access management solutions. Lessons Support for AD CS Maintenance of AD LDS Long-term support for AD FS Preservation of AD RMS Lab: Maintaining Access Management Solutions Maintaining AD CS Maintaining AD LDS Maintaining AD FS Maintaining AD RMS After completing this module, students will be able to: Support AD CS. Maintain AD LDS. Provide long-term support for AD FS. Preserve AD RMS. Module 8: Troubleshooting Identity and Access Solutions After completing this module, students will be able to Design Active Directory disaster recovery in Windows Server 2008. Lessons Troubleshooting AD CS Troubleshooting AD LDS Troubleshooting AD FS Troubleshooting AD RMS Lab: Troubleshooting Active Directory Server Roles Troubleshooting AD CS Troubleshooting AD LDS Troubleshooting AD FS Troubleshooting AD RMS After completing this module, students will be able to: Troubleshoot AD CS. Troubleshoot AD LDS. Resolve AD FS issues. Solve AD RMS problems. Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas Tipo de documento: Registro PROGRAMA DE CAPACITACIÓN DE CURSOS A OFRECER Código: UPCH-R-102.RG-08 Emisión: 25 de agosto de 2008 Revisión: 01 Página: 66 de 66 Documento controlado por medios electrónicos. Para uso exclusivo de la Universidad Politécnica de Chiapas