Laura Kier Submission for Errata IT Essentials Fifth Edition Page
advertisement

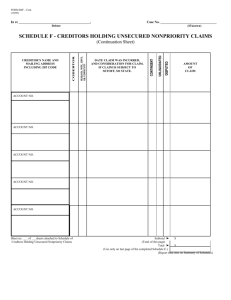
Laura Kier Submission for Errata IT Essentials Fifth Edition Page 321, Table 6-4, line 14, change “a secure” to “an unsecured” as indicated below. ***Begin table 6-4 Table 6-4 Common Network Protocols and Ports Protocol TCP/IP Port NA NetBEUI/NetBIOS 137,139,150 HTTP 80 HTTP 443 FTP 20/21 SSH 22 Telnet 23 POP3 110 IMAP 143 SMTP 25 LDAP 389 SNMP 161 SMB 445 Description A suite of protocols used to transport data on the internet A small, fast protocol designed for a workgroup network that requires no connection to the Internet A communication protocol that establishes a request/response connection on the Internet Uses authentication and encryption to secure data as it travels between the client and Web server. Provides services for file transfer and manipulation Securely connects to a remote network device Connects to a remote network device Downloads email messages from an email server Downloads email messages from an email server Sends email in a TCP/IP network Accesses information directories Manages and monitors devices on a network Provides shared access SFTP 115 DNS 53 RDP 3389 ***End table 6-4 ***Please insert a worksheet icon here to files, printers, and communication between points on a network Provides a secure an unsecured file transfer service Resolves host names to IP addresses Used to provide access to a remote computer