Sample Exam
advertisement

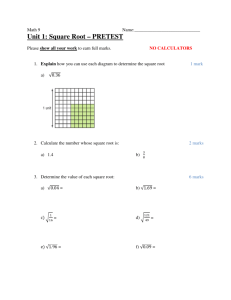
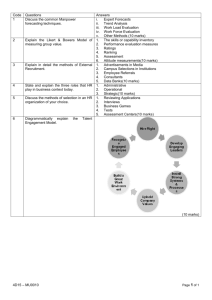
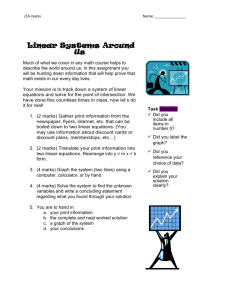
PART A (12 MARKS – 1 mark each correct answer) Are the following statements TRUE or FALSE? (There is no need to justify your answers or rewrite the question. Write your answers in the examination booklet provided) 1. In the 1970s, user identification and authorization to the ARPANET system were nonexistent. 2. A sequential attack selects specific accounts to attack and uses a list of commonly used passwords with which to guess, instead of random combinations. 3. Ethics are based on fixed moral attitudes or customs of a particular group. 4. Likelihood is the overall rating of the probability that a specific vulnerability within an organization will be successfully attacked. 5. Operational feasibility examines how well the proposed information security alternatives will contribute to the efficiency, effectiveness, and overall operation of an organization. 6. In general, issue-specific security policies do not require frequent updates. 7. The full backup only archives the files that have been modified that day, and thus requires less space and time than the differential backup. 8. A person’s date of birth is an example of a good password to use as it would be difficult for others to guess. 9. ID cards and badges are NOT foolproof, and they can be easily duplicated, stolen, and modified. 10. Planners do not need to estimate the expected non-capital expenses for the completion of the task, subtask, or action item. 11. Familiarity with (as opposed to formal experience with) a technology is usually sufficient for an applicant to land an interview for a technical security position. 12. Help desk personnel need to be trained to recognize a security problem as distinct from other system problems. PART B (TOTAL 12 MARKS - 1 mark each correct answer) Answer the following multiple choice questions, in the examination booklet provided, by selecting the letter that matches the answer. (There is no need to justify your answers or rewrite the question) 1. The C.I.A. triangle is solely based on three characteristics that describe the utility of information, ____. (a) controllability, integrity, and availability (b) confidentiality, integrity, and availability (c) connectivity, integrity, and availability (d) creativity, integrity, and availability (e) none of the above 2. The application of computing and network resources to try every possible combination of options of a password is called a(n) ____ attack. (a) combination (b) orderly (c) sequential (d) random (e) brute force 3. Which of the following U.S. government agencies is responsible for signal, electronic communications intelligence and information system security? (a) NIPC (b) NSA (c) Secret Service (d) CIA (e) Environmental Protection 4. Larger organizations use the dynamic host control protocol (DHCP) within TCP/IP that ____. (a) keeps track of the IP addresses within the corporation (b) reassigns IP numbers to devices as needed (c) automatically detects IP addresses (d) reassigns well known port numbers (e) All of the above 5. The calculation of the value associated with the most likely loss from an attack which is based on the value of the asset and the expected percentage of loss that would occur from a particular attack is called ____. (a) ALE (b) ARO (c) SLE (d) NRO (e) SLA Part B continued 6. ________ controls address the tactical and technical issues related to designing and implementing security in the organization, as well as issues related to examining and selecting the technologies appropriate to protecting information. (a) Management (b) Server (c) Operational (d) Technical (e) Security 7. Which of the following stages in the business impact analysis (BIA) intends to identify the functional areas of the organization and prioritize them to determine which are most vital to the continued operations of the organization? (a) Threat attack identification (b) Attack success scenario (c) Business unit analysis (d) Potential damage assessment (e) None of the above 8. ____ is a popular symmetric encryption cryptosystem based on the Data Encryption Algorithm (DEA), which uses a 64-bit block size and a 56-bit key. (a) Advanced Encryption Standard (AES) (b) Triple DES or 3DES (c) Data Encryption Standard (DES) (d) Superior Encryption Standard (SES) (e) Blowfish 9. Based on the feedback loop shown in the figure above, corrective action is required when ____. (a) the estimate was flawed AND performance has lagged (b) EITHER the estimate was flawed OR performance has lagged (c) only the estimate was flawed, BUT NOT when performance has lagged (d) performance has lagged, BUT NOT when the estimate was flawed (e) None of the above Part B continued 10. In case of power outage, a(n) ____ is a backup power source for major computer systems. (a) RUS (b) UPS (c) STS (d) PPS (e) ATM 11. A(n) ____ can determine the level of trust the business places in the individual. (a) asset search (b) resume (c) IPSec (d) background check (e) address check 12. Which of the following components of the risk assessment (RA) documents the proposed project, including network changes, application changes, and other issues or faults? (a) Background (b) Scope (c) IRP and DRP planning elements (d) Introduction (e) All of the above PART C Attempt All Questions (41 MARKS) Question 1 (9 marks) (a) What is the difference between a vulnerability and exposure? (2 marks) (b) How can dual controls, such as two-person confirmation, reduce the threats from acts of human error and failure? What other controls can reduce this threat? (3 marks) (c) Calculate the risk ratings for the following scenarios: (i.) A router has a value score of 200 and has one vulnerability. This vulnerability has a likelihood 0.95 (i.e. 95%) with no current controls and that assumption and date are 90% accurate i.e. 10% (0.1) uncertain. (ii.) For the router in (a) above a control has been put in place that addresses 50% (0.5) of its risk. What is the new risk rating? Has the control reduced risk? (4 marks) Question 2 (8 marks) (a) Why is a Cost Benefit Analysis (CBA) important when planning for security? (2 marks) (b) Compare and contrast a disaster recovery plan (DRP) and a business continuity plan (BCP)? (3 marks) (c) What is the difference between security education and security training? Which is preferable for employees already in security positions? (3 marks) Question 3 (11 marks) (a) What are the six major continuity strategies that can be used for a BCP? (3 marks) (b) Why do many organizations ban port-scanning activities on their internal networks? Why would ISPs ban outbound port scanning by their customers? (3 marks) (c) With the aid of a diagram(s) describe the major function(s) of two of the major categories of Firewalls? (5 marks) PART C continued Question 4 (13 marks) (a) Your organization is planning a lights-out server room in the data centre. Describe the fire control system(s) you would include in that room and give reasons for their use. (A lights-out room functions without human beings through the automation of functions.) (5 marks) (b) With the aid of a diagram briefly describe the four layers of the bull’s-eye model for security project planning. (3 marks) (c) Why shouldn’t you show a prospective employee secure areas during interviews? (2 marks) (d) Briefly describe the major classes of data sources which give information/intelligence on security threats, threat agents, vulnerabilities and attacks. (3 marks)