Beaconhouse School System O' Level – PECHS Campus Southern
Beaconhouse School System
O’ Level – PECHS Campus
Southern Region
Computer Science 2210 – Paper I – Question Bank
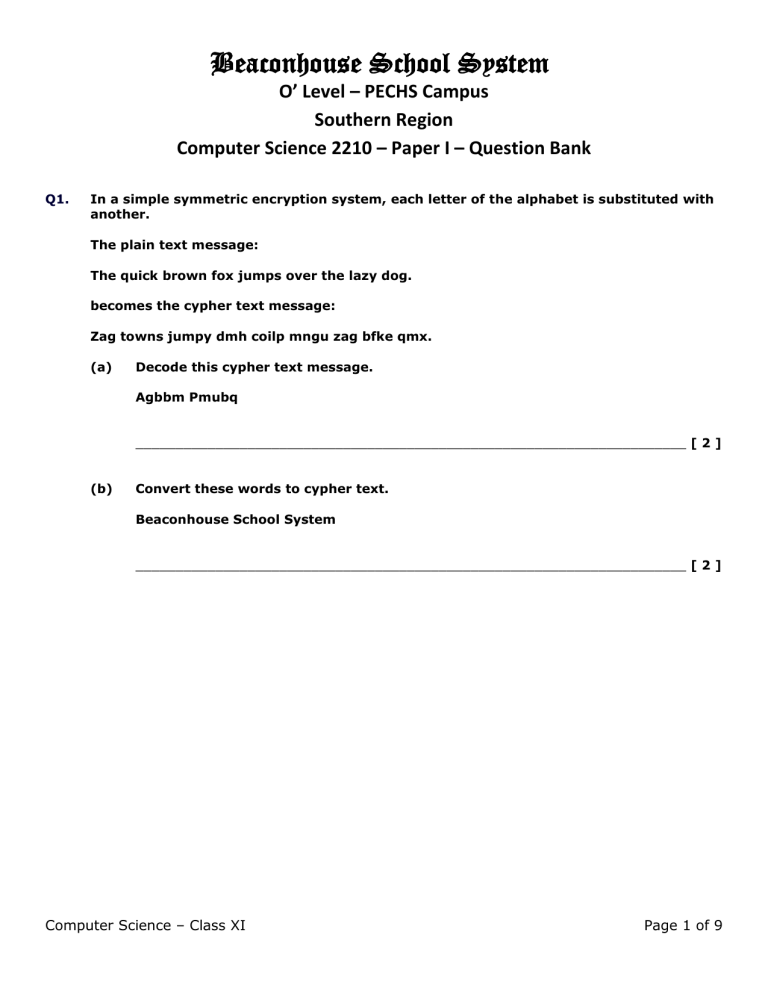
Q1. In a simple symmetric encryption system, each letter of the alphabet is substituted with another.
The plain text message:
The quick brown fox jumps over the lazy dog. becomes the cypher text message:
Zag towns jumpy dmh coilp mngu zag bfke qmx.
(a) Decode this cypher text message.
Agbbm Pmubq
_____________________________________________________________________ [ 2 ]
(b) Convert these words to cypher text.
Beaconhouse School System
_____________________________________________________________________ [ 2 ]
Computer Science – Class XI Page 1 of 9
Q2. A digital light meter has a 3-digit LCD. The value of each digit on the instrument display
is stored as a 4-bit binary number in a register.
For example:
(a) What value is shown on the display if the 4-bit binary registers contain:
(b) What would be stored in the 4-bit binary registers if the display shows:
[ 3 ]
Computer Science – Class XI
[ 3 ]
Page 2 of 9
Q3. When a key is pressed on the keyboard, the computer stores the ASCII representation of the character typed into main memory.
The ASCII representation for A is 65 (denary), for B is 66 (denary), etc.
There are two letters stored in the following memory locations:
(a) Show the contents of Location 1 and Location 2 as binary.
Location 1 ___________________________________________________________ [ 1 ]
Location 2 ___________________________________________________________ [ 1 ]
(b) Show the contents of Location 1 and Location 2 as hexadecimal.
(c)
Location 1 ___________________________________________________________ [ 1 ]
Location 2 ___________________________________________________________ [ 1 ]
The following machine code instruction is stored in a location of main memory:
Convert this binary pattern into hexadecimal.
_________________________________________________________________________
_________________________________________________________________________
_________________________________________________________________________
_________________________________________________________________________
_________________________________________________________________________
_________________________________________________________________________
_________________________________________________________________________
_____________________________________________________________________ [ 3 ]
Computer Science – Class XI Page 3 of 9
Q4. Five security or data loss issues are shown on the left-hand side.
Five possible methods of data recovery or protection are shown on the right.
Draw a line to match each definition/description of Issues to the most appropriate
Methods of Data Recovery.
[ 4 ]
Computer Science – Class XI Page 4 of 9
Q5. A computer will only operate if three switches R, S and T are correctly set. An output signal (X = 1) will occur if R AND S are both ON OR if R is OFF AND S AND T are ON.
Design a logic network and draw the truth table for this network.
R S T X
1
1
1
1
1
0
1
1
0
0
1
0
0
0
0
0
1
1
0
0
1
0
1
0
[ 8 ]
Computer Science – Class XI Page 5 of 9
Q6. Four types of data storage media and four descriptions are shown in the table below.
Tick (_) the appropriate boxes in the table to match each data storage medium to its most suitable description.
Q7. Name a suitable hardware device to enable automatic data capture in each of the following applications. Each device must be different.
[ 4 ]
Computer Science – Class XI
[ 3 ]
Page 6 of 9
Q8. An aeroplane uses three separate computer systems to monitor and control the flight
process while in auto pilot mode.
a) Explain the advantages of using three computers rather than just one.
_________________________________________________________________________
_________________________________________________________________________
_________________________________________________________________________
_____________________________________________________________________ [ 2 ] b) Sensors are used to measure air speed. The readings are sent to the three computers.
Describe how the sensors and computers are used to control the aeroplane’s speed in auto pilot mode.
_________________________________________________________________________
_________________________________________________________________________
_________________________________________________________________________
_________________________________________________________________________
_________________________________________________________________________
_________________________________________________________________________
_________________________________________________________________________
_________________________________________________________________________
_________________________________________________________________________
_____________________________________________________________________ [ 4 ]
Computer Science – Class XI Page 7 of 9
Q9. Give three tasks carried out by an operating system.
i) ______________________________________________________________________
______________________________________________________________________ ii) ______________________________________________________________________
______________________________________________________________________ iii) ______________________________________________________________________
__________________________________________________________________ [ 3 ]
Computer Science – Class XI Page 8 of 9
Q10. A company selling CDs uses a unique 6-digit identification number for each CD title. The
right-most digit (position 1) is a check digit.
The validity of the number and check digit is calculated as follows:
multiply each digit by its digit position
add up the results of the multiplications
divide the answer by 11
if the remainder is 0, the identification number and check digit are valid a) Show whether the following identification numbers are valid or not. You must show how you arrived at your answer.
8 2 0 1 5 6
Working __ ____________________________________________________________
______________________________________________________________________
______________________________________________________________________
______________________________________________________________________
__________________________________________________________________ [ 2 ]
Valid or not valid? ___________________________________________________ [ 1 ] b) Find the check digit for the following identification number:
5 0 2 4 1 __
Working __ ____________________________________________________________
______________________________________________________________________
______________________________________________________________________
______________________________________________________________________
__________________________________________________________________ [ 2 ]
Check digit: ________________________________________________________ [ 1 ]
Computer Science – Class XI Page 9 of 9