Course Outline (Word)
advertisement
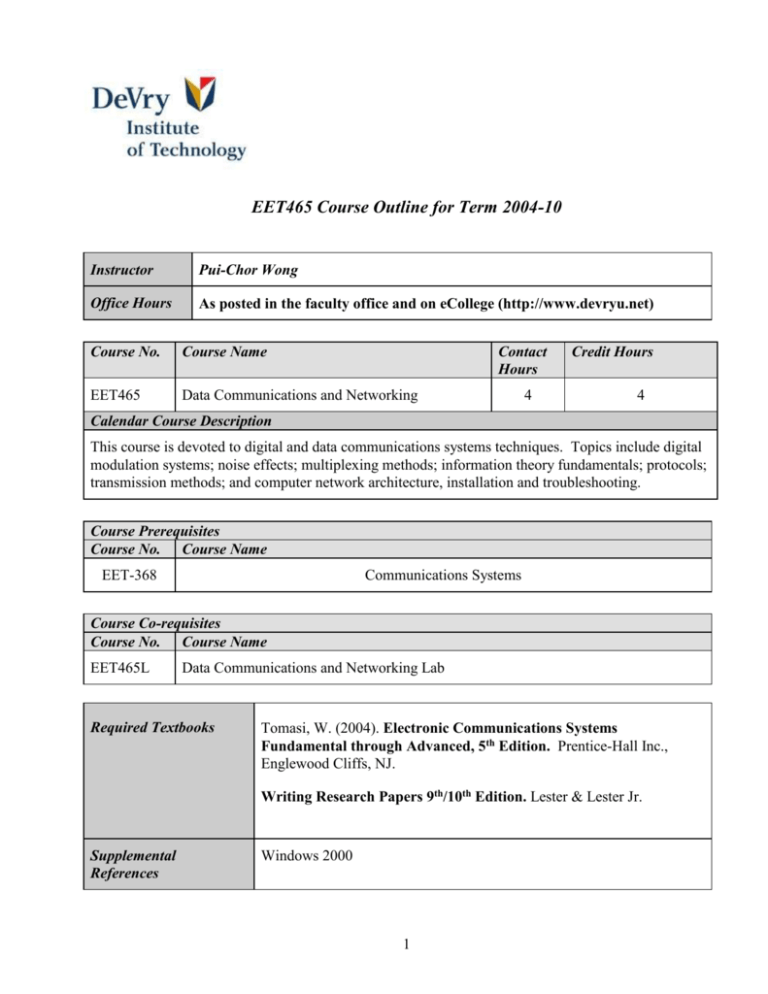
EET465 Course Outline for Term 2004-10 Instructor Pui-Chor Wong Office Hours As posted in the faculty office and on eCollege (http://www.devryu.net) Course No. Course Name Contact Hours EET465 Data Communications and Networking 4 Credit Hours 4 Calendar Course Description This course is devoted to digital and data communications systems techniques. Topics include digital modulation systems; noise effects; multiplexing methods; information theory fundamentals; protocols; transmission methods; and computer network architecture, installation and troubleshooting. Course Prerequisites Course No. Course Name EET-368 Communications Systems Course Co-requisites Course No. Course Name EET465L Data Communications and Networking Lab Required Textbooks Tomasi, W. (2004). Electronic Communications Systems Fundamental through Advanced, 5th Edition. Prentice-Hall Inc., Englewood Cliffs, NJ. Writing Research Papers 9th/10th Edition. Lester & Lester Jr. Supplemental References Windows 2000 1 Major Topics Information Theory – Source and channel coding Digital Communications – Information capacity, FSK,PSK,QAM Introduction to Telecommunications- Local loop signaling, Traffic Engineering Introduction to Networking- Layered Models, Data link layer, Physical layer Multiple Access Protocols Local Area networking Internetworking with TCP/IP Course Evaluation Assignments and Inclass: Quizzes (1 drop): Final Exam: Bonus: 20% 40% 40% 10% 2 Course Terminal Objectives Module I: Information Theory 1. Given the specifications of a communication system including symbol code set, and a band-limited channel, calculate system performance parameters such as symbol probability, average code length, code efficiency and channel capacity. 2. Given a discrete set of symbols such as that of a keyboard, design a uniquely decodeable fixed and variable length source codes which represents the data and compare and contrast the efficiencies of the two codes with each other and with the theoretical limits of the symbol set. 3. Given a stream of source data, implement at least three methods for error detection and/or correction and compare and contrast the cost/benefit of the added bits in terms of throughput. Module II: Digital Communications 1. Given the four major digital modulation schemes (ASK, PSK, FSK, QAM), compare and contrast each with respect to bandwidth requirements and ease of demodulation. 2. Given a PSK or QAM modulation system, draw the constellation diagram and discuss bit-error rate as it relates to the constellation diagram. 3. Given each of the digital modulation schemes, illustrate methods of demodulation so that the original data stream is successfully recovered. 4. Given a communication application with specific power constraints (Eb/No), select a digital modulation method and provide justification. Module III: Introduction To Telecommunications 1. Given a signaling operation (Off-hook, DTMF, dial-tone, etc.) in a local loop, classify the signaling function as alerting, attending, supervisory or testing and show how system control is interpreted. 2. Given the digital hierarchical system of the public switched telephone network, and the required traffic flow between multiple systems, design a system to meet traffic flow using a minimum number of T1 switches and Digital Access and Crossconnect Systems (DACS). 3. Given a specified number of resources and a specified amount of traffic, design a system using Erlang-B tables a specified grade of service (GOS). 4. Given a fully available blocking switch and a cost constraint, calculate the blocking and non-blocking factors for maximum switch throughput using a minimum number of crosspoints. Module IV: Introduction to Networking 1. Given an example network system, interpret the major functions of the network as they relate to the seven layer OSI model and TCP/IP. 2. Given a datalink protocol, demonstrate each step in transmitting a data frame between two adjacent nodes including supervisory frames, information frames, and unnumbered frames. 3. Given a system which utilizes a multiple access protocol such as Ethernet, illustrate data encoding, frame format and methods used for bus contention and collision control. Demonstrate how performance is affect by bus length, probability of transmission and number of stations. Module V: Local Area Networking 1. Given a case study of a small office, design all necessary network configuration, user accounts, workgroups to effectively service the users as defined by the case study. 2. Given a case study of a small network system, design all necessary security precautions needed to limit access as defined by the case study. 3. Given a case study with a defined network configuration, design a printer capability and a method and schedule for backing up the network data. Module VI: Internetworking with TCP/IP 1. Given a network layer protocol, diagram each step in transmitting a sequence of frames between two end users using both connection-oriented and connectionless routing using the Internet Protocol (IP). 2. Using the Transport Control Protocol (TCP) utilized on the Internet, describe how a connection is established, and how data is transferred so that reliable communication is obtained to reach as specified quality of service. 3. Given the Internet, diagram an e-mail connection, such as Eudora using the TCPIP protocol. 4. Given the Internet, describe how HyperText Transfer Protocol (HTTP) is used to provide server side services for the WWW through the use of Web pages. 3 Instructor Notes Assignments are due at the beginning of the class period on the due date. There will be no makeup for assignments and quizzes. Make-up for final examination will be granted under special circumstances such as sickness. In such case, doctor's note will be required. Furthermore, there is no midterm examination. Late assignments (after the due time on the due date) will not be accepted. Classroom Policy 1 Disruption in class will result in being dismissed from the classroom and/or any disciplinary action 2 Any additions as discussed/suggested by the class. Plagiarism is a serious issue and can result in penalties in both course and lab work. On Plagiarism In speaking or writing, plagiarism is the intentional or unintentional act of representing someone else's work as one's own. In addition, plagiarism is defined as using the essential style and manner of expression of a source as if it were one's own. If there is any doubt, the student should consult his or her instructor, or document the source in a footnote or other form of citation. Any statement made without documentation will be interpreted as the student’s own words and may therefore be interpreted as plagiarism. Your work in this course may be submitted to turnitin.com, an online plagiarism-checking service. Turnitin.com operates a secure database and protects your privacy by assigning code numbers, not student names, to all student work stored in its database. The purpose of using this service is to help protect the integrity of a DeVry credential, which in turn helps protects your investment in a DeVry education. We will assume we have your consent to submit gradable work in this course to turnitin.com unless you indicate otherwise. 4 EET465L Course Outline for Term 2004-10 Instructor Pui-chor Wong Office Hours As posted in Academics and on eCollege (http://www.devryu.net) Course No. EET465L Course Name Contact Hours Data Communications and Networking Lab 2 Credit Hours 1 Calendar Course Description Students gain practical experience by constructing digital/data modulation and demodulation circuits. System-performance measurements are made, and experience is provided in troubleshooting defective systems. Local area network installation and troubleshooting are also included. Course Prerequisites Course No. Course Name Course Co-requisites Course No. Course Name EET465 Required Textbooks Supplemental References Data Communications and Networking Instructor supplied lab handout and instruction Course Evaluation Each Lab counts equally towards the final LAB grade. 5 Course Terminal Objectives Module I: Information Theory 1. Given a text file, write a C++ program which will calculate the each symbols probability, calculate the source character set’s entropy, generate a new binary code using Huffman encoding, and finally compress the file using the new huffman code. 2. Given an ASCII text file write a C++ program which will calculate the needed parity bits to be added to generate a valid hamming code word, transmit the character out the serial port to another computer which will regenerate the original ASCII code word. Module II: Digital Communications 1. Using a circuit or an equipment which can generate ASK, FSK, and PSK, analyze the bandwidth generated by each modulation technique and determine the throughput capability on a bandlimited channel. 2. Using a bandlimited channel with a white noise error source, transmit data using FSK, PSK and QAM, analyze the received data and determine the bit error rate as a function of noise. Module III: Introduction To Telecommunications 1. Given a classical telephone, an A/D circuit with variable sampling rate, and a D/A circuit, determine the effects of variable sampling rates on voice quality. 2. Given up to 24 data channels and a specified input data rate, design a system to multiplex and demultiplex the data channels into a T1 frame. Module IV: Introduction to Networking 1. Given a particular data link protocol, such as HDLC, transmit data between two adjacent computers fully implementing the protocol and verify that data was transmitted properly. 2. Using software simulation, simulate data transmission between two adjacent computers and analyze data link performance while varying data-link parameters, such as frame length, window size, and protocol. Module V: Local Area Networking 1. Given a local area network plan, install all software and install all hardware necessary to implement the plan. 2. Using a case study of a small office environment, design and implement a network architecture to allow all users the proper access to network software while maintaining proper security precautions. 3. Using a case study for a small office, set up a printing environment which most effectively utilizes hardware resources and office space. VI: Internetworking with TCP/IP 1. Using a protocol analyzer, monitor the data traffic on a network trunk and create a report on the packet structure, packet function and packet routing employed. 2. Using a computer software, simulate data transmission between two non-adjacent computers and analyze network performance while varying system parameters such as routing algorithms and protocol used. 6 Course Notes Lab attendance is mandatory, and no credit will be given for absentees. Labs will be handed out prior to lab period or made available on the network. A signature (either the Instructor or course F.A.s) is required for each lab and it should reflect the fact that the lab was performed during the lab period. Group work is permitted. (Maximum group size is as indicated by the Instructor) One lab report per group. (The writer of the report should alternate for each report and also be clearly indicated on the report). Lab due dates and times are as indicated in the due date file (465duedate.doc on website and/or network). Late labs will not be accepted. The STANDARD LAB REPORT FORMAT should be used for all reports. A minimum of 1 week will be allotted to each lab. On Plagiarism In speaking or writing, plagiarism is the intentional or unintentional act of representing someone else's work as one's own. In addition, plagiarism is defined as using the essential style and manner of expression of a source as if it were one's own. If there is any doubt, the student should consult his or her instructor, or document the source in a footnote or other form of citation. Any statement made without documentation will be interpreted as the student’s own words and may therefore be interpreted as plagiarism. Your work in this course may be submitted to turnitin.com, an online plagiarism-checking service. Turnitin.com operates a secure database and protects your privacy by assigning code numbers, not student names, to all student work stored in its database. The purpose of using this service is to help protect the integrity of a DeVry credential, which in turn helps protects your investment in a DeVry education. We will assume we have your consent to submit gradable work in this course to turnitin.com unless you indicate otherwise. 7 STANDARD LAB REPORT FORMAT Title Page and abstract Includes: -Title of experiment -Name of course -Name of instructor -Name of author and partner(s) -Date -Adequate motivation Objective/Purpose Tells why the experiment was performed and what results are anticipated. This section often interprets the purpose of the lab experiment as provided by the instructor. Equipment and Parts This is a list of the components and test equipment used to perform the lab experiment. Experimental Data and Observations (Raw Data) Documents (without a detailed analysis) what happened during the performance of the lab. Records and presents the data, tables, charts, calculations and evidence of where this information was derived from (ie. equations, textbooks, class-notes, multimeter, etc). Discussion of Results/ Questions and Answers This is a detailed analysis and discussion of the results of the experiment, plus a comparison of the results with theoretical expectations (ie. Did the data prove or disprove your theory? Why might the lab not have worked?) Any questions posed in the lab handout are answered here. Conclusion Contains a concise description of the conclusions. Includes a statement of whether or not the objectives were met and any recommendations you may have. Note: Your report should be Times New Roman, size 12 fonts. Figures and tables should be labeled properly. 8