The history and Impact of Internet
advertisement

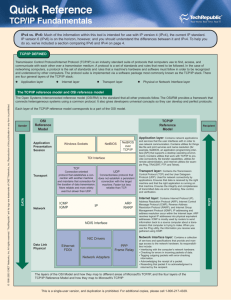
The history and Impact of Internet The Internet may owe its existence to the launch of Sputnik in 1957. This event prompted the US government to set up the Advanced Research Projects Agency (ARPA). ARPA worked with major universities throughout the United States. In order to exchange information a system was developed in 1968 to link major sites in an experimental computer network. The system had to link different types of systems including IBM, DEC, and SDS, running different operating systems. The system became known as the ARPANET, and was successful in allowing different computer systems to communicate. TCP and IP were developed as a layered protocol stack, and together TCP/IP hid the computer types and communication methods from users. Now NSFNet, MILNET, JANET, EUNet, including commercial organizations round the world are part of the Internet, and they all use TCP/IP. TCP/IP is based on a five layer architectural model referred to as the DoD (Department of Defense) model). This is different from the OSI model, but can be compared. Layer 1 (Hardware) is equivalent to the OSI Physical layer, and defines physical aspects of transmitting and receiving packets. Layer 2 (Network Interface) is responsible for packet frame content. Layer 3 (Internet Layer) is equivalent to the OSI Network Layer and is responsible for routing packets between different hosts and networks. Layer 4 (Transport) is equivalent to the OSI Transport layer & Session layer. This layer is responsible for end-end integrity of data packets. Layer 5 (Application) is equivalent to OSI layers 5, 6 and 7. This layer consists of application protocols such as FTP (File Transfer Protocol) , TELNET (Terminal Network Emulation), SMTP (Simple Mail Transfer Protocol), SNMP (Simple Network Management Protocol), DNS (Domain Name Services, NFS (Network File Services), among many others. TCP/IP is not owned by any corporation or individual. TCP/IP is supported on the following plus additional systems not listed here: MS-DOS Personal Computers Apple Macintosh Microsoft Windows 3.1, Windows 95, Windows NT IBM OS/2, AS/400, VM or MVS mainframes UNIX Systems including SCO/Unix. Novell Network Operating Systems Banyan Vines DEC VAX VMS The TCP/IP protocols are defined by RFC's (Request for comments) and are part of the public domain. They may be acquired and reproduced free of charge. For this reason the Internet and use of Internet technologies such as TCP/IP are spreading rapidly, and will soon become as commonplace as the telephone. Many third party developers, consulting firms, and service organizations are creating tools, and providing services to help corporations take advantage of TCP/IP, and other Internet related technologies. What is In-Line Network Encryptor (INE)? The In-Line Network Encryptor (INE), is specifically designed to support IP/Ethernet operating over standard commercial networks, requiring Type 1-Type 4 security. In-Line Network Encryptor for protecting all levels of data-even governmentclassified data up to and including TS/SCI. It provides confidentiality, data integrity, peer identification, authentication and mandatory/discretionary access control services. The INE is software configured using the new INE Configuration Manager and is keyed using material supplied by the NSA Electronic Key Management System (EKMS), for Type 1 product. Physical and electronic key distribution is supported. The In-Line Network Encryptor has these many benefits and features: o o o o o Quick Secure Easy to use Flexible Exportable What is Network Encryption System? (No need to memorise) The Network Encryption System (NES) is a suite of products designed to provide Type I data security for protecting all levels of data up to and including Sensitive Compartmented Information. The NES provides data confidentiality, data integrity, peer identification and authentication, and mandatory/discretionary access control services. The NES Security Platform is configured using the NES Configuration Manager and is keyed using material supplied by the Electronic Key Management System (EKMS). What is Replay? The replay attack is simple. A bad-guy records a communication session between a client and server. Later, it reconnects to the server, and plays back the previously recorded client messages. Digital Signature alone does not any authentication. How can we fix the replay attack? Digital signatures alone do not provide message authentication. The bad guy can record a signed message and resend it (that is replay attack). To prevent this type of attack, digital signatures must be combined with an appropriate means to ensure the uniqueness of the message. The means can be time stamps or nonce. Nonce is a random or non-repeating value that is included in data exchanged by a protocol, usually for the purpose of guaranteeing liveness and thus detecting and protecting against replay attacks message sequence. We now have username , password and fingerprint to authenticate the person, why we still need to worry about the replay attack. The main purpose of authentication is to verify the identity of the person using a service, though it can also be used to prove the identity of the service to the user. The required level of proof will vary depending on the nature of the service, but will usually be based on one or more of the following what you know (for example a username and password) what you have (a smartcard or other token) what you are Most security systems require a combination of at least two of these forms of proof: many tokens require that a password be entered to unlock them. This protects against accidental loss or theft of a token, but cannot prevent deliberate deception where a registered user hands their identity to another person. Any authentication method which is transmitted across a public network may be recorded by any third party with access to the network. If this person can later use the recorded transaction as their own 'authentication' then the method is USELESS. That is why we are still cautious with the replay attacks. What is rewrite attack? It is an attack that modifies an encrypted message's contents without decrypting it first. It means the structure remains unchanged, only part of the contents. For example, the encrypted message is changed form 89^&%ty to 89^&4ty. Below is a message extracted from Mircosoft Web site in 2001: From this message, what is you conclusion. Jan. 29 — After four straight days of outages, Microsoft says its Web sites are operating smoothly now and expects no more difficulties. After fixing the technical glitch that caused accessiblity problems Tuesday and Wednesday, the company beefed up its network security so as to prevent attacks like the ones that blocked access to its sites Thursday and Friday, including the hiring an outside company to run a backup directory for its major Web sites. Based on the above, we now understand the importance of protecting the site. What make the attack possible, as Microsoft is large corporation full of experts? The bad guys or hackers have become more knowledgeable and have developed programs that automate the attacks by simply sending the messages. The programs direct many computers that are connected to the Internet to send traffic to a specific site simultaneously. That allows hackers to overwhelm some of the most prominent sites already designed to handle large amounts of traffic. They can secretly plant their attack programs in other people's computer systems by exploiting those systems' security weaknesses. The programs remain silent until the time of attack. It is difficult to trace where the hacker is. The picture showing the error rate is from http://stacks.msnbc.com/news/520922.asp?cp1=1 Why small business companies are less concerned about escrowed key and agents, while large companies and U.S. government cares this much? Some small businesses companies without their own security professionals, would likely have felt that they had less risk of unauthorized disclosure if they entrusted their backup keys to outside professionals. Other firms, especially large multinationals with their own security staffs, might have made a different calculation and preferred to hold their own keys. The US government cared about this regarding the selection and certification of escrow agents. It is based on the rationale that it would be "beneficial" to criminalize the "abuse of the escrowed key by the escrow agents or others,". The government objectives of "assuring the availability of escrowed keys for properly authorized government officials" in a reliable and timely manner that would not tip off the subject of the investigation is clear.